Содержание
- Cisco ASDM
- Описание
- ASA Security Device Manager (ASDM) installation
- Release Notes for Cisco ASDM, 7.16(x)
- Available Languages
- Download Options
- Release Notes for Cisco ASDM, 7.16(x)
- Important Notes
- System Requirements
- ASDM Java Requirements
- Release Notes for Cisco ASDM, 7.15(x)
- Available Languages
- Download Options
- Release Notes for Cisco ASDM, 7.15(x)
- Important Notes
- System Requirements
- ASDM Java Requirements
- ASDM Compatibility Notes
- Install an Identity Certificate for ASDM
- Increase the ASDM Configuration Memory
- Increase the ASDM Configuration Memory in Windows
- Increase the ASDM Configuration Memory in Mac OS
- ASA and ASDM Compatibility
- VPN Compatibility
- New Features
- New Features in ASDM 7.15(1.150)
- Released: February 8, 2022
- New Features in ASA 9.15(1) /ASDM 7.15(1)
- Released: November 2, 2020
- Upgrade the Software
- ASA Upgrade Path
Cisco ASDM
Описание
Establish, configure, monitor, and troubleshoot Cisco firewall appliances with the unified control suite. It provides full access to the standard system integration and scanning scenarios, the interface features quick parameter adjustment options. Real-time logs are kept.
Вы можете бесплатно скачать Cisco ASDM 10.10.20.4 с нашего сайта. Наша антивирусная программа проверила эту загрузку и признала ее полностью «чистой» от вирусов.
Javaws.exe, asdm-launcher.exe или CiscoASDM.exe — наиболее скачиваемые имена файлов для установщика этого ПО. Разработчик этой бесплатной программы — Cisco Systems, Inc.
ПО может распространяться под таким названием, как «ASDM on». Самые популярные версии среди пользователей ПО 10.8, 10.7 и 10.6.
Эта бесплатная программа устанавливается на Windows 7, 64-бит версию. Программа принадлежит к категории Безопасность, а точнее к подкатегории Анивирус.
Cisco ASDM is a simple, GUI-Based Firewall Appliance Management tool. This program helps you to quickly configure, monitor, and troubleshoot Cisco firewall appliances and firewall service modules. It provides setup wizards that help you configure and manage Cisco firewall devices, powerful real-time log viewer and monitoring dashboards, as well as handy troubleshooting features and powerful debugging tools.
Мы предлагаем оценить другие программы, такие как Multi Virus Cleaner, VirIT eXplorer Lite или Disk Password Protection, которые часто используются вместе с Cisco ASDM.
Источник
ASA Security Device Manager (ASDM) installation
ASA Security Device Manager (ASDM) is a configuration tool included with the ASA. It has an easy-to-use Web-based management interface and enables network administrators to quickly configure, monitor, and troubleshoot Cisco firewall appliances.
Before enabling ASDM on your ASA device, you need to obtain the ASDM image. Next, you need to enable ASDM on your device. Here is how it can be done:
1. Copy the downloaded ASDM image file to your firewall using TFTP:
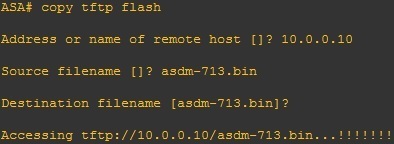
2. Configure ASA to load ASDM at next reboot using the asdm image flash:ASDM FILENAME command:
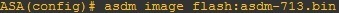
3. Enable the http server and identify the management station that will be used to configure the appliance:
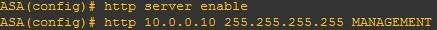
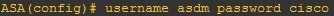
4. Create a user on the device:
5. Save your configuration using the write command and reload the device.
6. Open your browser and go to the IP address of the ASA device (you should use the HTTPS protocol):
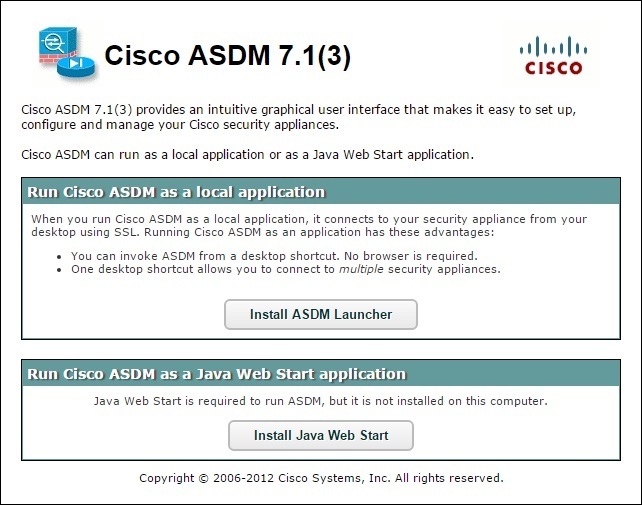
7. Click on the Install ASDM Launcher and Run ASDM button to install ASDM (NOTE – if you don’t have JAVA JRE installed, install it first). If prompted for credentials, enter the username and password you’ve configured earlier:
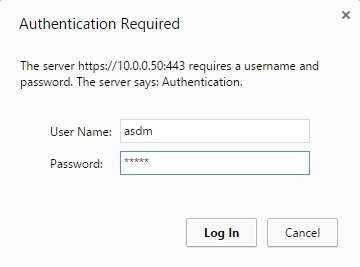
7. Run the downloaded installer and finish the wizard. When the installation is completed, you can start using ASDM to manage your ASA:
Источник
Release Notes for Cisco ASDM, 7.16(x)
Available Languages
Download Options
Release Notes for Cisco ASDM, 7.16(x)
This document contains release information for Cisco ASDM Version 7.16(x) for the Cisco ASA series.
Important Notes
SNMPv3 users using MD5 hashing and DES encryption are no longer supported, and the users will be removed when you upgrade to 9.16(1)—Be sure to change any user configuration to higher security algorithms using the snmp-server user command before you upgrade.
SSH host key action required in 9.16(1)—In addition to RSA, we added support for the EDDSA and ECDSA host keys for SSH. The ASA tries to use keys in the following order if they exist: EDDSA, ECDSA, and then RSA. When you upgrade to 9.16(1), the ASA will fall back to using the existing RSA key. However, we recommend that you generate higher-security keys as soon as possible using the crypto key generate < eddsa | ecdsa >command. Moreover, if you explicitly configure the ASA to use the RSA key with the ssh key-exchange hostkey rsa command, you must generate a key that is 2048 bits or higher. For upgrade compatibility, the ASA will use smaller RSA host keys only when the default host key setting is used. RSA support will be removed in a later release.
RSA keys using that are smaller than 2048 cannot be generated in 9.16(1)—You can no longer generate RSA keys smaller than 2048 using the crypto key generate rsa command.
For SSH, existing smaller keys can continue to be used after upgrading, but we recommend that you upgrade to a larger size, or to a higher security key type.
For other features, existing certificates signed with RSA key sizes smaller than 2048 cannot be used in ASA 9.16.1 and later. You can use the crypto ca permit-weak-crypto command to allow use of existing smaller keys, but even with this command, you cannot generate new smaller RSA keys..
ssh version command removed in 9.16(1)—This command has been removed. Only SSH version 2 is supported.
SAMLv1 feature removed in 9.16(1)—Support for SAMLv1 was removed.
Cisco announces the feature deprecation for Clientless SSL VPN effective with ASA version 9.17(1). Limited support will continue on releases prior to 9.17(1). Further guidance will be provided regarding migration options to more robust and modern solutions (for example, remote Duo Network Gateway, AnyConnect, remote browser isolation capabilities, and so on).
No support in ASA 9.15(1) and later for the ASA 5525-X, ASA 5545-X, and ASA 5555-X—ASA 9.14(x) is the last supported version. For the ASA FirePOWER module, the last supported version is 6.6.
For the Firepower 1010, invalid VLAN IDs can cause problems—Before you upgrade to 9.15(1) or later, make sure you are not using a VLAN for switch ports in the range 3968 to 4047. These IDs are for internal use only, and 9.15(1) includes a check to make sure you are not using these IDs. For example, if these IDs are in use after upgrading a failover pair, the failover pair will go into a suspended state. See CSCvw33057 for more information.
Chacha-poly ciphers—AnyConnect has an updated list of supported cryptographic algorithms: AnyConnect Secure Mobility Client Features, Licenses, and OSs, Release 4.10, which are proposed to the ASA when starting TLS-based VPN traffic.
System Requirements
This section lists the system requirements to run this release.
ASDM Java Requirements
Источник
Release Notes for Cisco ASDM, 7.15(x)
Available Languages
Download Options
Release Notes for Cisco ASDM, 7.15(x)
This document contains release information for Cisco ASDM Version 7.15(x) for the Cisco ASA series.
Important Notes
No support in ASA 9.15(1) and later for the ASA 5525-X, ASA 5545-X, and ASA 5555-X—ASA 9.14(x) is the last supported version. For the ASA FirePOWER module, the last supported version is 6.6.
Cisco announces the feature deprecation for Clientless SSL VPN effective with ASA version 9.17(1). Limited support will continue on releases prior to 9.17(1). Further guidance will be provided regarding migration options to more robust and modern solutions (for example, remote Duo Network Gateway, AnyConnect, remote browser isolation capabilities, and so on).
For the Firepower 1010, invalid VLAN IDs can cause problems—Before you upgrade to 9.15(1), make sure you are not using a VLAN for switch ports in the range 3968 to 4047. These IDs are for internal use only, and 9.15(1) includes a check to make sure you are not using these IDs. For example, if these IDs are in use after upgrading a failover pair, the failover pair will go into a suspended state. See CSCvw33057 for more information.
ASDM Cisco.com Upgrade Wizard failure on Firepower 1000 and 2100 in Appliance mode in 9.13—The ASDM Cisco.com Upgrade Wizard does not work for upgrading from 9.13 ( Tools > Check for ASA/ASDM Updates ). The wizard can upgrade ASDM from 7.13, but the ASA image upgrade is grayed out. (CSCvt72183) As a workaround, use one of the following methods:
Use Tools > Upgrade Software from Local Computer for both ASA and ASDM.
Upgrade ROMMON for ASA 5506-X, 5508-X, and 5516-X to Version 1.1.15 or later—There is a new ROMMON version for these ASA models (May 15, 2019); we highly recommend that you upgrade to the latest version. To upgrade, see the instructions in the ASA configuration guide.
Caution: The ROMMON upgrade for 1.1.15 takes twice as long as previous ROMMON versions, approximately 15 minutes. Do not power cycle the device during the upgrade. If the upgrade is not complete within 30 minutes or it fails, contact Cisco technical support; do not power cycle or reset the device.
Upgrade ROMMON for the ISA 3000 to Version 1.0.5 or later——There is a new ROMMON version for the ISA 3000 (May 15, 2019); we highly recommend that you upgrade to the latest version. To upgrade, see the instructions in the ASA configuration guide.
Caution: The ROMMON upgrade for 1.0.5 takes twice as long as previous ROMMON versions, approximately 15 minutes. Do not power cycle the device during the upgrade. If the upgrade is not complete within 30 minutes or it fails, contact Cisco technical support; do not power cycle or reset the device.
SAMLv1 feature deprecation—Support for SAMLv1 is deprecated.
Low-Security Cipher Removal in ASA 9.15(1)—Support for the following less secure ciphers used by IKE and IPsec have been removed:
Diffie-Hellman groups: 2 and 24
Encryption algorithms: DES, 3DES, AES-GMAC, AES-GMAC-192, AES-GMAC-256, NULL, ESP-3DES, ESP-DES, ESP-MD5-HMAC
Hash algorithms: MD5
Low-security SSH and SSL ciphers have not yet been removed.
Before you upgrade from an earlier version of ASA to Version 9.15(1), you must update your VPN configuration to use the ciphers supported in 9.15(1), or else the old configuration will be rejected. When the configuration is rejected, one of the following actions will occur, depending on the command:
The command will use the default cipher.
The command will be removed.
Fixing your configuration before upgrading is especially important for clustering or failover deployments. For example, if the secondary unit is upgraded to 9.15(1), and the removed ciphers are synced to this unit from the primary, then the secondary unit will reject the configuration. This rejection might cause unexpected behavior, like failure to join the cluster.
IKEv1: The following subcommands are removed:
crypto ikev1 policy priority:
IKEv2: The following subcommands are removed:
crypto ikev2 policy priority:
IPsec: The following subcommands are removed:
crypto ipsec ikev1 transform-set name esp-3des esp-des esp-md5-hmac
crypto ipsec ikev2 ipsec-proposal name
protocol esp integrity md5
crypto ipsec profile name
set pfs group2 group24
Crypto Map: The following subcommands are removed:
crypto map name sequence set pfs group2
crypto map name sequence set pfs group24
crypto map name sequence set ikev1 phase1-mode aggressive group2
Re-introduction of CRL Distribution Point configuration—The static CDP URL configuration option, that was removed in 9.13(1), was re-introduced in the match-certificate command.
Restoration of bypass certificate validity checks option—The option to bypass revocation checking due to connectivity problems with the CRL or OCSP server was restored.
The following subcommands were restored:
revocation-check crl none
revocation-check ocsp none
revocation-check crl ocsp none
revocation-check ocsp crl none
System Requirements
This section lists the system requirements to run this release.
ASDM Java Requirements
ASDM is not tested on Linux.
Note
Table 1. ASA and ASA FirePOWER: ASDM Operating System and Browser Requirements
Requires Strong Encryption license (3DES/AES) on ASA
Smart licensing models allow initial access with ASDM without the Strong Encryption license.
ASDM requires an SSL connection to the ASA. You can request a 3DES license from Cisco:
In the Licensing Portal, click Get Other Licenses next to the text field.
Choose IPS, Crypto, Other. from the drop-down list.
Type ASA in to the Search by Keyword field.
Enter the serial number of the ASA, and follow the prompts to request a 3DES/AES license for the ASA.
Self-signed certificate or an untrusted certificate
Firefox and Safari
When the ASA uses a self-signed certificate or an untrusted certificate, Firefox and Safari are unable to add security exceptions when browsing using HTTPS over IPv6. See https://bugzilla.mozilla.org/show_bug.cgi?id=633001. This caveat affects all SSL connections originating from Firefox or Safari to the ASA (including ASDM connections). To avoid this caveat, configure a proper certificate for the ASA that is issued by a trusted certificate authority.
SSL encryption on the ASA must include both RC4-MD5 and RC4-SHA1 or disable SSL false start in Chrome.
For Internet Explorer 9.0 for servers, the “ Do not save encrypted pages to disk ” option is enabled by default (See Tools > Internet Options > Advanced ). This option causes the initial ASDM download to fail. Be sure to disable this option to allow ASDM to download.
Install an Identity Certificate for ASDM
When using Java 7 update 51 and later, the ASDM Launcher requires a trusted certificate. An easy approach to fulfill the certificate requirements is to install a self-signed identity certificate. You can use Java Web Start to launch ASDM until you install a certificate.
See Install an Identity Certificate for ASDM to install a self-signed identity certificate on the ASA for use with ASDM, and to register the certificate with Java.
Increase the ASDM Configuration Memory
ASDM supports a maximum configuration size of 512 KB. If you exceed this amount you may experience performance issues. For example, when you load the configuration, the status dialog box shows the percentage of the configuration that is complete, yet with large configurations it stops incrementing and appears to suspend operation, even though ASDM might still be processing the configuration. If this situation occurs, we recommend that you consider increasing the ASDM system heap memory.
Increase the ASDM Configuration Memory in Windows
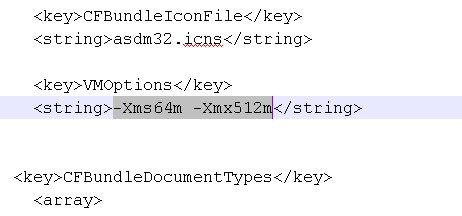
To increase the ASDM heap memory size, edit the run.bat file by performing the following procedure.
Procedure
Go to the ASDM installation directory, for example C:Program Files (x86)Cisco SystemsASDM.
Edit the run.bat file with any text editor.
Save the run.bat file.
Increase the ASDM Configuration Memory in Mac OS
To increase the ASDM heap memory size, edit the Info.plist file by performing the following procedure.
Procedure
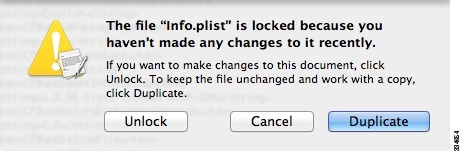
If this file is locked, you see an error such as the following:
Click Unlock and save the file.
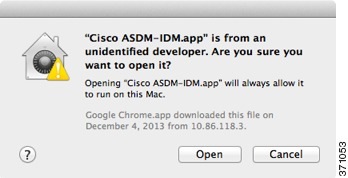
If you do not see the Unlock dialog box, exit the editor, right-click the Cisco ASDM-IDM icon, choose Copy Cisco ASDM-IDM, and paste it to a location where you have write permissions, such as the Desktop. Then change the heap size from this copy.
ASA and ASDM Compatibility
For information about ASA/ASDM software and hardware requirements and compatibility, including module compatibility, see Cisco ASA Compatibility.
VPN Compatibility
New Features
This section lists new features for each release.
|
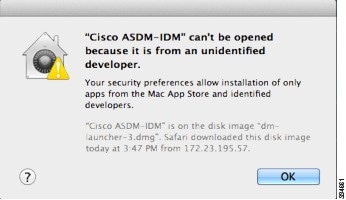
Microsoft Windows (English and Japanese): See Windows 10 in ASDM Compatibility Notes if you have problems with the ASDM shortcut. Server 2016 and Server 2019 (ASA management only; ASDM management of the FirePOWER module is not supported. You can alternatively use Firepower Management Center to manage the FirePOWER module when using ASDM for ASA management.) No support for Windows 7 32-bit Apple OS X 10.4 and later Yes (64-bit version only) ASDM Compatibility NotesThe following table lists compatibility caveats for ASDM. » This app can’t run on your PC» error message. When you install the ASDM Launcher, Windows 10 might replace the ASDM shortcut target with the Windows Scripting Host path, which causes this error. To fix the shortcut target: Windows opens the directory with the shortcut icon. Change the Target to: C:WindowsSystem32wscript.exe invisible.vbs run.bat On OS X, you may be prompted to install Java the first time you run ASDM; follow the prompts as necessary. ASDM will launch after the installation completes. OS X 10.8 and later You need to allow ASDM to run because it is not signed with an Apple Developer ID. If you do not change your security preferences, you see an error screen.
|
|---|
New, changed, and deprecated syslog messages are listed in the syslog message guide.
New Features in ASDM 7.15(1.150)
Released: February 8, 2022
There are no new features in this release.
New Features in ASA 9.15(1) /ASDM 7.15(1)
Released: November 2, 2020
ASAv for the Public Cloud
We introduced the ASAv for the following Public Cloud offerings:
Oracle Cloud Infrastrucure (OCI)
Google Cloud Platform (GCP)
No modified screens.
ASAv support for Autoscale
The ASAv now supports Autoscale for the following Public Could offerings:
Amazon Web Services (AWS)
Autoscaling increases or decreases the number of ASAv application instances based on capacity requirements.
No modified screens.
ASAv for Microsoft Azure support for Accelerated Networking (SR-IOV).
The ASAv on the Microsoft Azure Public Cloud now supports Azure’s Accelerated Networking (AN), which enables single root I/O virtualization (SR-IOV) to a VM, greatly improving its networking performance.
No modified screens.
Changes to PAT address allocation in clustering. The PAT pool flat option is now enabled by default and it is not configurable.
The way PAT addresses are distributed to the members of a cluster is changed. Previously, addresses were distributed to the members of the cluster, so your PAT pool would need a minimum of one address per cluster member. Now, the master instead divides each PAT pool address into equal-sized port blocks and distributes them across cluster members. Each member has port blocks for the same PAT addresses. Thus, you can reduce the size of the PAT pool, even to as few as one IP address, depending on the amount of connections you typically need to PAT. Port blocks are allocated in 512-port blocks from the 1024-65535 range. You can optionally included the reserved ports, 1-1023, in this block allocation when you configure PAT pool rules. For example, in a 4-node cluster, each node gets 32 blocks with which it will be able to handle 16384 connections per PAT pool IP address compared to a single node handling all 65535 connections per PAT pool IP address.
Note that if you configure port block allocation (the block-allocation PAT pool option), your block allocation size is used rather than the default 512-port block. In addition, you cannot configure extended PAT for a PAT pool for systems in a cluster.
New/Modified screens: NAT PAT Pool configuration.
XDMCP inspection disabled by default in new installations.
Previously, XDMCP inspection was enabled by default for all traffic. Now, on new installations, which includes new systems and reimaged systems, XDMCP is off by default. If you need this inspection, please enable it. Note that on upgrades, your current settings for XDMCP inspection are retained, even if you simply had it enabled by way of the default inspection settings.
High Availability and Scalability Features
Disable failover delay
When you use bridge groups or IPv6 DAD, when a failover occurs the new active unit waits up to 3000 ms for the standby unit to finish networking tasks and transition to the standby state. Then the active unit can start passing traffic. To avoid this delay, you can disable the waiting time, and the active unit will start passing traffic before the standby unit transitions.
New/Modified screens: Configuration > Device Management > High Availability and Scalability > Failover > Enable switchover waiting for peer state
Multicast IGMP interface state limit raised from 500 to 5000
The multicast IGMP state limit per interface was raised from 500 to 5000.
New/Modified commands: igmp limit
ASDM support for unique MAC address generation for single context mode
You can now enable unique MAC address generation for VLAN subinterfaces in single context mode in ASDM. Normally, subinterfaces share the same MAC address with the main interface. Because IPv6 link-local addresses are generated based on the MAC address, this feature allows for unique IPv6 link-local addresses. CLI support was added in ASA 9.8(3), 9.8(4), and 9.9(2) and later.
New/Modified screen: Configuration > Device Setup > Interface Settings > Interfaces
DDNS support for the web update method
You can now configure an interface to use DDNS with the web update method.
New/Modified screens: Configuration > Device Management > DNS > Dynamic DNS
Modifications to Match Certificate commands to support static CRL Distribution Point URL
The static CDP URL configuration commands allowed CDPs to be mapped uniquely to each certificate in a chain that is being validated. However, only one such mapping was supported for each certificate. This modification allows statically configured CDPs to be mapped to a chain of certificates for authentication.
Administrative and Troubleshooting Features
Manual import of node secret file from the RSA Authentication Manager for SDI AAA server groups.
You can import the node secret file that you export from the RSA Authentication Manager for use with SDI AAA server groups.
show fragment command output enhanced
The output for show fragment command was enhanced to include IP fragment related drops and error counters.
No modified screens
show tech-support command output enhanced
The output for show tech-support command was enhanced to include the bias that is configured for the crypto accelerator. The bias value can be ssl, ipsec, or balanced.
No modified screens
Support to configure cplane keepalive holdtime values
Due to communication delays caused by high CPU usage, the response to the keepalive event fails to reach ASA, resulting in trigerring failover due to card failure. You can now configure the keepalive timeout period and the maximum keepalive counter value to ensure sufficient time and retries are given.
You can now configure the maximum in-negotiation SAs as an absolute value up to 15000 or a maximum value derived from the maximum device capacity; formerly, only a percentage was allowed.
New/Modified commands: crypto ikev2 limit max-in-negotiation-sa value
ASA provides protection against CSRF attacks for WebVPN handlers. If a CSRF attack is detected, a user is notified by warning messages. This feature is enabled by default.
Kerberos server validation for Kerberos Constrained Delegation (KCD).
When configured for KCD, the ASA initiates an AD domain join with the configured server in order to acquire Kerberos keys. These keys are required for the ASA to request service tickets on behalf of clientless SSL VPN users. You can optionally configure the ASA to validate the identity of the server during domain join.
We changed the following screens: Configuration > Remote Access VPN > Clientless SSL VPN Access > Advanced > Microsoft KCD Server
Upgrade the Software
This section provides the upgrade path information and a link to complete your upgrade.
ASA Upgrade Path
To view your current version and model, use one of the following methods:
CLI—Use the show version command.
See the following table for the upgrade path for your version. Some older versions require an intermediate upgrade before you can upgrade to a newer version. Recommended versions are in bold.
 Note |
| Support for configuring the maximum in-negotiation SAs as an absolute value |
| Cross-Site Request Forgery (CSRF) Vulnerabilities Prevention for WebVPN Handlers |
For guidance on security issues on the ASA, and which releases contain fixes for each issue, see the ASA Security Advisories.
ASA 9.14(x) was the final version for the ASA 5525-X, 5545-X, and 5555-X.
ASA 9.12(x) was the final version for the ASA 5512-X, 5515-X, 5585-X, and ASASM.
ASA 9.2(x) was the final version for the ASA 5505.
ASA 9.1(x) was the final version for the ASA 5510, 5520, 5540, 5550, and 5580.
Источник
Adblock
detector
Note
What is the Cisco ASDM?
Cisco ASDM is the Cisco Adaptive Security Device Manager, delivering world-class security management and monitoring through an intuitive, easy to use Web-based management interface.
Cisco ASDM Features and Capabilities
The Cisco ASDM is ideal for small or simple deployments, and it provides the following:
- Setup wizards that help you configure and manage Cisco firewall devices
- Powerful real-time log viewer and monitoring dashboards that provide an at-a-glance view of firewall appliance status and health
- Troubleshooting features and powerful debugging tools such as packet trace and packet capture
Where to download Cisco ASDM?
Now, you may ask the topic of this article, Cisco ASDM Download.
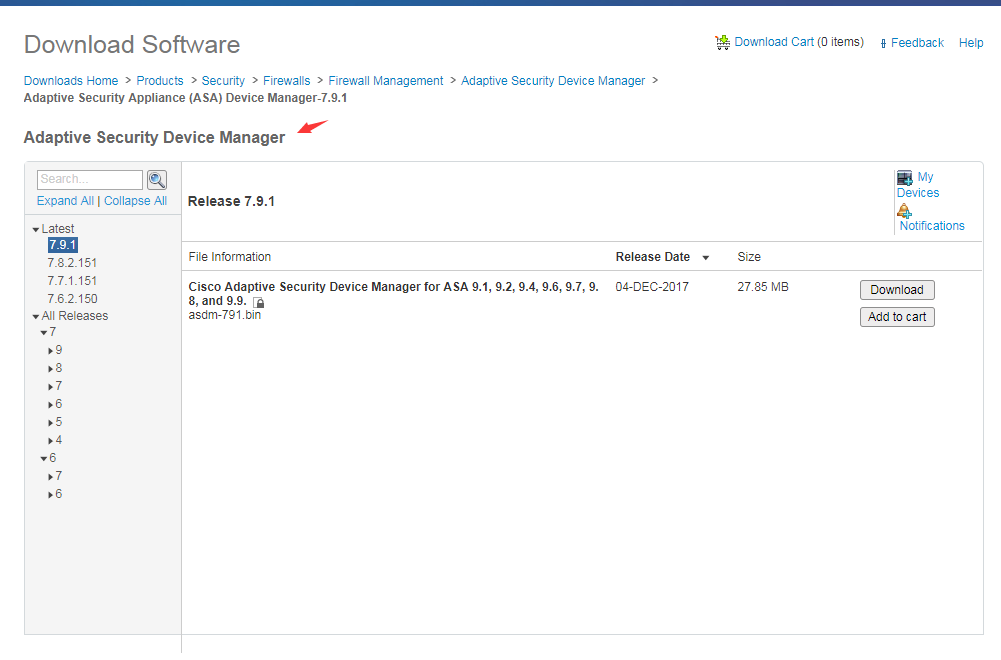
Cisco provides the download site.
https://software.cisco.com/download/release.html?mdfid=279513399&softwareid=280775064&release=7.9.1&relind=AVAILABLE&rellifecycle=&reltype=latest
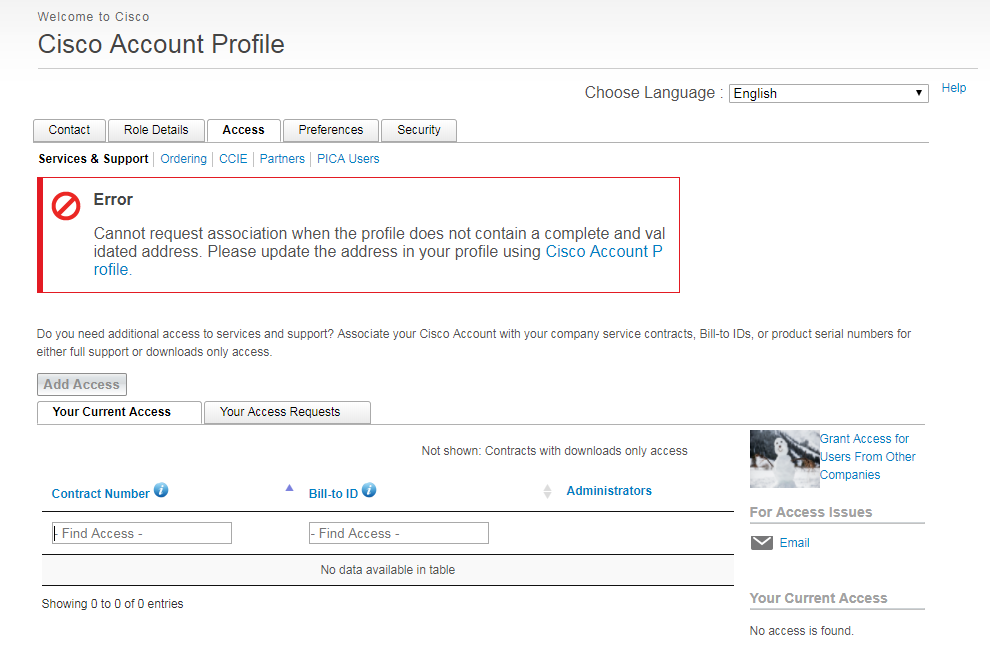
However, to need these services and support, please associate your Cisco Account with your company service contracts, Bill-to IDs, or product serial numbers for either full support or downloads only access.
If you only have a Cisco account, but you don’t have type any access information, you may have these problems:
In short, to download Cisco ASDM, you must have effective access, and buy Cisco devices through formal suppliers.
Was this article helpful?
23 out 48 found this helpful
Platform Features
ASAv for the Public Cloud
We introduced the ASAv for the following Public Cloud offerings:
-
Oracle Cloud Infrastrucure (OCI)
-
Google Cloud Platform (GCP)
No modified screens.
ASAv support for Autoscale
The ASAv now supports Autoscale for the following Public Could offerings:
-
Amazon Web Services (AWS)
-
Miscrosoft Azure
Autoscaling increases or decreases the number of ASAv application instances based
on capacity requirements.
No modified screens.
ASAv for Microsoft Azure support for Accelerated Networking (SR-IOV).
The ASAv on the Microsoft Azure Public Cloud now supports Azure’s Accelerated
Networking (AN), which enables single root I/O virtualization (SR-IOV) to a VM,
greatly improving its networking performance.
No modified screens.
Firewall Features
Changes to PAT address allocation in clustering. The PAT pool
flat option is now enabled by default and it is not
configurable.
The way PAT addresses are distributed to the members of a cluster is changed.
Previously, addresses were distributed to the members of the cluster, so your PAT
pool would need a minimum of one address per cluster member. Now, the master
instead divides each PAT pool address into equal-sized port blocks and distributes
them across cluster members. Each member has port blocks for the same PAT
addresses. Thus, you can reduce the size of the PAT pool, even to as few as one IP
address, depending on the amount of connections you typically need to PAT. Port
blocks are allocated in 512-port blocks from the 1024-65535 range. You can
optionally included the reserved ports, 1-1023, in this block allocation when you
configure PAT pool rules. For example, in a 4-node cluster, each node gets 32
blocks with which it will be able to handle 16384 connections per PAT pool IP
address compared to a single node handling all 65535 connections per PAT pool IP
address.
As part of this change, PAT pools for all systems, whether standalone or
operating in a cluster, now use a flat port range of 1023 — 65535. Previously, you
could optionally use a flat range by including the flat
keyword in a PAT pool rule. The flat keyword is no
longer supported: the PAT pool is now always flat. The
include-reserve keyword, which was previously a
sub-keyword to flat , is now an independent keyword
within the PAT pool configuration. With this option, you can include the 1 — 1023
port range within the PAT pool.
Note that if you configure port block allocation (the
block-allocation PAT pool option), your block
allocation size is used rather than the default 512-port block. In addition, you
cannot configure extended PAT for a PAT pool for systems in a cluster.
New/Modified screens: NAT PAT Pool configuration.
XDMCP inspection disabled by default in new installations.
Previously, XDMCP inspection was enabled by default for all traffic. Now, on new
installations, which includes new systems and reimaged systems, XDMCP is off by
default. If you need this inspection, please enable it. Note that on upgrades,
your current settings for XDMCP inspection are retained, even if you simply had it
enabled by way of the default inspection settings.
High Availability and Scalability Features
Disable failover delay
When you use bridge groups or IPv6 DAD, when a failover occurs the new active
unit waits up to 3000 ms for the standby unit to finish networking tasks and
transition to the standby state. Then the active unit can start passing traffic.
To avoid this delay, you can disable the waiting time, and the active unit will
start passing traffic before the standby unit transitions.
New/Modified screens:
Routing Features
Multicast IGMP interface state limit raised from 500 to 5000
The multicast IGMP state limit per interface was raised from 500 to 5000.
New/Modified commands: igmp limit
No ASDM support.
Also in 9.12(4).
Interface Features
ASDM support for unique MAC address generation for single context mode
You can now enable unique MAC address generation for VLAN subinterfaces in single
context mode in ASDM. Normally, subinterfaces share the same MAC address with the
main interface. Because IPv6 link-local addresses are generated based on the MAC
address, this feature allows for unique IPv6 link-local addresses. CLI support was
added in ASA 9.8(3), 9.8(4), and 9.9(2) and later.
New/Modified screen:
DDNS support for the web update method
You can now configure an interface to use DDNS with the web update method.
New/Modified screens:
Certificate Features
Modifications to Match Certificate commands to support static CRL Distribution
Point URL
The static CDP URL configuration commands allowed CDPs to be mapped uniquely to
each certificate in a chain that is being validated. However, only one such
mapping was supported for each certificate. This modification allows statically
configured CDPs to be mapped to a chain of certificates for authentication.
Administrative and Troubleshooting Features
Manual import of node secret file from the RSA Authentication Manager for SDI AAA
server groups.
You can import the node secret file that you export from the RSA Authentication
Manager for use with SDI AAA server groups.
We added the following screen: .
show fragment command output enhanced
The output for show fragment command was enhanced to include
IP fragment related drops and error counters.
No modified screens
show tech-support command output enhanced
The output for show tech-support command was enhanced to
include the bias that is configured for the crypto accelerator. The bias value can
be ssl, ipsec, or balanced.
No modified screens
Monitoring Features
Support to configure cplane keepalive holdtime values
Due to communication delays caused by high CPU usage, the response to the
keepalive event fails to reach ASA, resulting in trigerring failover due to card
failure. You can now configure the keepalive timeout period and the maximum
keepalive counter value to ensure sufficient time and retries are given.
We added the following screen: .
VPN Features
value
You can now configure the maximum in-negotiation SAs as an absolute value up to
15000 or a maximum value derived from the maximum device capacity; formerly, only
a percentage was allowed.
New/Modified commands: crypto ikev2 limit max-in-negotiation-sa
value
No ASDM support.
Also in 9.12(4).
Handlers
ASA provides protection against CSRF attacks for WebVPN handlers. If a CSRF
attack is detected, a user is notified by warning messages. This feature is
enabled by default.
Kerberos server validation for Kerberos Constrained Delegation (KCD).
When configured for KCD, the ASA initiates an AD domain join with the configured
server in order to acquire Kerberos keys. These keys are required for the ASA to
request service tickets on behalf of clientless SSL VPN users. You can optionally
configure the ASA to validate the identity of the server during domain join.
We changed the following screens:
Активный участник
Зарегистрирован: 09.11.2012
Пользователь #: 143,414
Сообщения: 537
Источник
Release Notes for Cisco ASDM, 7.6(x)
Available Languages
Download Options
Release Notes for Cisco ASDM, 7.6(x)
First Published: March 21, 2016
Last Updated: October 24, 2016
Release Notes for Cisco ASDM, 7.6(x)
This document contains release information for Cisco ASDM Version 7.6(x) for the Cisco ASA series.
Important Notes
Potential Traffic Outage (9.6(2.1) through 9.6(3))—Due to bug CSCvd78303, the ASA may stop passing traffic after 213 days of uptime. The effect on each network will be different, but it could range from an issue of limited connectivity to something more extensive like an outage. You must upgrade to a new version without this bug, when available. In the meantime, you can reboot the ASA to gain another 213 days of uptime. Other workarounds may be available. See Field Notice FN-64291 for affected versions and more information.
The ASAv 9.5.2(200) features, including Microsoft Azure support, are not available in 9.6(1). They are available in 9.6(2).
ASDM 7.6(2) supports AnyConnect Client profiles in multiple context mode. This feature requires AnyConnect Version 4.2.00748 or 4.3.03013 and later.
(ASA 9.6.2) Upgrade impact when using multiple-mode configuration—When upgrading from 9.5.2 to 9.6.1 and then subsequently to 9.6.2, any existing RAVPN for multiple-mode configuration will stop working. Post upgrade to the 9.6.2 image, a reconfiguration to give each context a storage space and to get new AnyConnect images in all of the contexts is required.
(ASA 9.6(2)) Upgrade impact when using SSH public key authentication—Due to updates to SSH authentication, additional configuration is required to enable SSH public key authentication; as a result, existing SSH configurations using public key authentication no longer work after upgrading. Public key authentication is the default for the ASAv on Amazon Web Services (AWS), so AWS users will see this issue. To avoid loss of SSH connectivity, you can update your configuration before you upgrade. Or you can use ASDM after you upgrade (if you enabled ASDM access) to fix the configuration.
Sample original configuration for a username «admin»:
To use the ssh authentication command, before you upgrade, enter the following commands:
We recommend setting a password for the username as opposed to keeping the nopassword keyword, if present. The nopassword keyword means that any password can be entered, not that no password can be entered. Prior to 9.6(2), the aaa command was not required for SSH public key authentication, so the nopassword keyword was not triggered. Now that the aaa command is required, it automatically also allows regular password authentication for a username if the password (or nopassword ) keyword is present.
After you upgrade, the username command no longer requires the password or nopassword keyword; you can require that a user cannot enter a password. Therefore, to force public key authentication only, re-enter the username command:
Upgrade impact when upgrading the ASA on the Firepower 9300— Due to license entitlement naming changes on the back-end, when you upgrade to ASA 9.6(1)/FXOS 1.1.4, the startup configuration may not parse correctly upon the initial reload; configuration that corresponds to add-on entitlements is rejected.
For a standalone ASA, after the unit reloads with the new version, wait until all the entitlements are processed and are in an «Authorized» state ( Monitoring > Properties > Smart License), and simply reload again ( Tools > System Reload) without saving the configuration. After the reload, the startup configuration will be parsed correctly.
For a failover pair if you have any add-on entitlements, follow the upgrade procedure in the FXOS release notes, but reset failover after you reload each unit ( Monitoring > Properties > Failover > Status, Monitoring > Failover > System, or Monitoring > Failover > Failover Group, and then click Reset Failover ).
For a cluster, follow the upgrade procedure in the FXOS release notes; no additional action is required.
ASA 5508-X and 5516-X upgrade issue when upgrading to 9.5(x) or later—Before you upgrade to ASA Version 9.5(x) or later, if you never enabled jumbo frame reservation then you must check the maximum memory footprint. Due to a manufacturing defect, an incorrect software memory limit might have been applied. If you upgrade to 9.5(x) or later before performing the below fix, then your device will crash on bootup; in this case, you must downgrade to 9.4 using ROMMON (Load an Image for the ASA 5500-X Series Using ROMMON), perform the below procedure, and then upgrade again.
Enter the following command to check for the failure condition:
If a value less than 456,384,512 is returned for “Max memory footprint,” then the failure condition is present, and you must complete the remaining steps before you upgrade. If the memory shown is 456,384,512 or greater, then you can skip the rest of this procedure and upgrade as normal.
Enter global configuration mode:
Temporarily enable jumbo frame reservation:
Do not reload the ASA.
Save the configuration:
Disable jumbo frame reservation:
Note
Do not reload the ASA.
Save the configuration again:
You can now upgrade to Version 9.5(x) or later.
The RSA toolkit version used in ASA 9.x is different from what was used in ASA 8.4, which causes differences in PKI behavior between these two versions.
For example, ASAs running 9.x software allow you to import certificates with an Organizational Name Value (OU) field length of 73 characters. ASAs running 8.4 software allow you to import certificates with an OU field name of 60 characters. Because of this difference, certificates that can be imported in ASA 9.x will fail to be imported to ASA 8.4. If you try to import an ASA 9.x certificate to an ASA running version 8.4, you will likely receive the error, «ERROR: Import PKCS12 operation failed.
System Requirements
This section lists the system requirements to run this release.
ASDM Java Requirements
You can install ASDM using Oracle JRE 8.0. OpenJRE is not supported.
Note
Источник
Adblock
detector
Table 1. ASA and ASA FirePOWER: ASDM Operating System and Browser Requirements
3 Replies
-
Did you upload it to the ASA? You should be able to pull up the ASA’s IP in a browser and get a link. Download the .msi and install it.
1 found this helpful
thumb_up
thumb_down
-
Craig (Cisco), I’m not sure if this is a rhetorical question or not… seems fishy coming from you
That said, here goes:
- Make sure ASDM image has been uploaded to the ASA you’re needing to connect to.
- Enable HTTP on the ASA you are wanting to connect to
- Browse to the ASA’s IP address
- Download ASDM installer from the Firewall (after authenticating)
Works just fine:
Was this post helpful?
thumb_up
thumb_down
-
If the image is uploaded to the ASA device, open a web browser and goto:
http://IP-OF-ASA/admin Opens a new window
You should get a page that has a link to download the installer.
Was this post helpful?
thumb_up
thumb_down