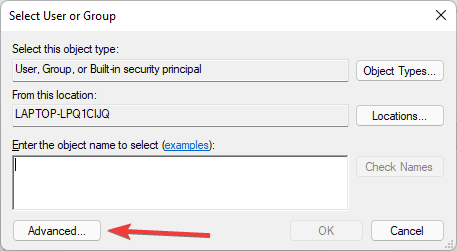
I’ve installed openssh for windows and when I run ssh localhost I get
Bad owner or permissions on C:Usersgary/.ssh/config
I’ve looked at these 2 questions https://superuser.com/questions/348694/bad-owner-or-permissions-error-using-cygwins-ssh-exe and https://serverfault.com/questions/253313/ssh-returns-bad-owner-or-permissions-on-ssh-config but none of the answers work for me. sshd is running as a service as the Local System user. I’ve run chmod 0600 C:Usersgary.sshconfig and chown gary C:Usersgary.sshconfig. I’ve also cleared the ACL by running setfacl -b C:Usersgary.sshconfig and then chmod 0600 C:Usersgary.sshconfig again. I’ve also tried changing the owner to SYSTEM and got the same error.
I’m not sure what else to do, is there anything wrong with my setup? I also have git installed which installed mingw, I deleted ssh and sshd from my git installation so they wouldn’t be on my path.
Other commands I’ve run are
icacls "C:Usersgary.sshconfig" /setowner gary
chown -R gary:1049089 C:Usersgary.ssh
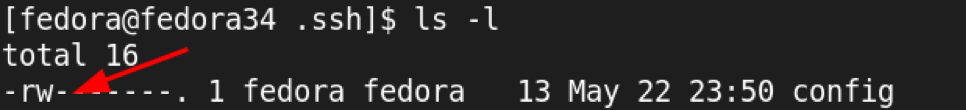
ls -la C:Usersgary.sshconfig shows
-rw-r—r— 1 gary 1049089 229 Jan 3 14:43 ‘C:Usersgary.sshconfig’
it keeps showing this even after changing the owner to SYSTEM, but in the file properties in file explorer it shows SYSTEM as the owner
asked Apr 19, 2018 at 16:53
4
This started popping up immediately after I created another user with Administrator privileges, and that account began inheriting access to my .ssh folder.
You do not need to change your permissions whatsoever.
Just go to .ssh, right-click Properties, Security Tab, Advanced. DISABLE INHERITANCE, then click on the Administrator user (the one that is not you) and Remove them. Apply. Done.
answered Oct 7, 2019 at 18:32
Jason HughesJason Hughes
2,1951 gold badge10 silver badges8 bronze badges
13
Use ssh client from Git instead of Windows inbuilt SSH client. E.g. set VS Code to use C:Program FilesGitusrbinssh.exe instead of C:WindowsSystem32OpenSSHssh.exe.
Steps:
- In VS Code navigated to [File] -> [Preferences] -> [Settings] -> Search remote.ssh.path
- Input C:Program FilesGitusrbinssh.exe
Alternatively:
- Update PATH environment variable to point to Git bin before Windows System32.
- Type «env» in Start bar to edit System (or account) environment variables.
- Select Path and hit edit.
- Add C:Program FilesGitusrbinssh.exe to the list and move it to the top of the list.
Lisa
4,2432 gold badges26 silver badges34 bronze badges
answered May 15, 2018 at 7:57
Gerard CarbóGerard Carbó
1,64716 silver badges16 bronze badges
6
Just got same issue after re-install windows. And easily fixed just by changing the file permissions to
SYSTEM & Administrators - Full Control
[your username] - Modify & as Owner
Note:
- I’m still using Windows 10 built-in SSH client
C:WindowsSystem32OpenSSHssh.exe& not using cygwin at all
Suncatcher
10.2k10 gold badges52 silver badges89 bronze badges
answered May 31, 2018 at 12:53
Fery WFery W
1,34214 silver badges27 bronze badges
5
For those still struggling with this, check this out: https://github.com/PowerShell/openssh-portable/pull/418. This was the case for me. It turns out that your computer should be named differently from your username… 🤷♂️ It will probably be fixed soon in future updates, because fix got into commit.
So again: if your computer name is the same as your username and you still haven’t fixed this issue with permissions dialog, then probably renaming your computer could help.
answered Feb 4, 2020 at 1:41
5
Instead of using the properties box, you can use the one liner:
icacls .ssh /grant:r <yourUserName>:f /inheritance:r
/grant:r username:f -> grant and overwrite permissions, giving full permissions to username
/inheritance:r -> remove inherited permissions
Keep known_hosts writable with
icacls .ssh/known_hosts /grant:rw <username>:f /inheritance:r
R Ben R
3244 silver badges9 bronze badges
answered Jun 10, 2021 at 21:39
LarryHLarryH
1,6282 gold badges12 silver badges14 bronze badges
1
I’m not sure what version of Windows you’re running, but since this is recent I’d guess Windows 10. I recently found out that an OpenSSH client is installed by default as of the April 2018 update. I then found I had two instances of OpenSSH: the one I installed myself and the one Windows gave me. Uninstalling the one I had installed caused the error message you describe.
The solution that worked for me was to remove the user-installed OpenSSH as well as the C:Usersusername.ssh folder, and let Windows 10 OpenSSH create the folder when you run the command the next time. I didn’t have any configuration I was worried about losing, but if you do I’d suggest copying and pasting the contents of the files somewhere and recovering them afterwards.
Hope this helps!
answered Aug 2, 2018 at 1:38
17slim17slim
1,2241 gold badge16 silver badges21 bronze badges
2
Having the exact same issue today, this is how I solved it:
- Go to C:Usersusername.ssh
- Right-click the config file
- Properties -> Security -> Advanced -> Disable Inheritance -> Disable
inheritance -> Remove all inherited permissions from this object ->
Apply -> Yes -> Ok -> Ok
answered Nov 26, 2021 at 9:40
0
Use FixUserFilePermissions.ps1 to fix permissions of client side files — keys and config files of current user.
git clone git@github.com:PowerShell/openssh-portable.git
cd openssh-portable/contrib/win32/openssh
.FixUserFilePermissions.ps1 -Confirm:$false
answered Jul 26, 2019 at 6:25
SlashGordonSlashGordon
6907 silver badges11 bronze badges
2
On windows server this is due to permission problem. Need to remove access to other users for the following folders
.ssh — folder
Right click on this folder -> Select «Give access to» — > Click on «Remove Access»
Right click on this folder -> Select «properties» — > «Securities» — > Click on «Edit Permissions» — Remove other users except the ID you are logged in.
Repeat the same process for the folder under which you have .pem file. (Note: Keep .pem file in a separate folder)
answered Apr 10, 2021 at 5:54
Dave RadaDave Rada
811 silver badge1 bronze badge
1
For anyone, who still has troubles after applying the owner + modify (plus full control for admins): it did not work for me. Then I saw a solution to remove all other users (incl all admins), which did not help either.
This worked for me:
- leave System and Administrators in place, with full control, as suggested above
- leave the user itself in place, as owner, with modify, as suggested above
- however, remove any other user or group. You probably need to go to advanced first, to disable inheritance of rights
after I removed an administrative user who was added by Windows after entering my folder (by passing through the UAC box), it worked for me again.
Hope this helps for anyone who encounters this specific issue 
answered May 17, 2019 at 11:44
benzhibenzhi
1161 silver badge5 bronze badges
0
If User is in Administrative group just keep configuration in
c:programdatasshssh_config instead %USERPROFILE%.sshconfig, will work
answered Sep 7, 2019 at 8:32
1
after disabling inheritance, make sure you add your current user, else u cannot edit the file
answered Aug 30, 2021 at 5:15
1
For me it was fixed by running chmod 0644 config under ~/.ssh/. Earlier it was set to 755 which was causing «Bad owner or permissions on /home/home/.ssh/config»
answered Feb 7, 2020 at 11:27
1
I tried all the solutions above, and sadly still can’t fix this issue. I’m pretty sure the permission of my ssh config is correct, this has been verified by the Explore GUI and the Get-Acl commands.
Then I finally find a way to solve it:
delete the entire .ssh folder and then open powershell and type ssh localhost. It will create a new .ssh folder for you, then you can apply the above permission tweaks(for me I only did one thing: disable inheritance).
So if other solutions doesn’t work for you, maybe you can try this. Hope it’s helpful.
PS: don’t forget to backup your old .ssh folder before deleting it.
answered Feb 27, 2020 at 3:47
ZiengZieng
4431 gold badge7 silver badges17 bronze badges
I was having this problem, and no amount of changing permissions or disabling inheritance on the config file would fix it. It turned out that it did not like my computer name and user name being the same, so I re-named my computer, allowed open ssh to re-create the config file, and the permissions are now correct. That was probably a bad idea to begin with, tbh.
answered May 9, 2020 at 7:07
KR-SOKR-SO
111 bronze badge
1
I deleted C:Usersuser/.ssh/config and reran my stuff, then it worked.
However, if you have something valuable there, make a backup first, just in case!
answered Apr 7, 2021 at 18:00
FusseldiebFusseldieb
1,3042 gold badges18 silver badges44 bronze badges
After a domain change over, I started having this same problem. Went through all of the suggestions listed and nothing worked, including both chmod and chown solutions.
I ended up fixing the problem by copying the folder, pasting it, deleting the original, and then renaming it back to .ssh.
answered Jul 27, 2021 at 16:01
The problem seems from the files are owned/has-permission for more than one user.
1- Go to your ./ssh folder and for both config & id_rsa files. From the properties -> Security -> Advanced:
2- Make sure that the user that you are logged in with IS the only user there.
answered Sep 19, 2019 at 13:09
ßastianßastian
1,7743 gold badges12 silver badges22 bronze badges
No group change or whatever,the first answer is right.Change to git ssh.exe
How?
- uninstall win10’s openssh in Settings
- add path of git’s ssh.exe to your
Path
answered Oct 13, 2019 at 15:24
jojo_007jojo_007
1151 silver badge5 bronze badges
For me it was fixed by running chmod 0644 config under ~/.ssh/ when running WSL.
answered Jan 30, 2020 at 11:43
- Rename the config file to something like config2
- Open this file with notepad
- Save As config (original name)
This worked for me.
Ayman Arif
1,2662 gold badges15 silver badges35 bronze badges
answered Aug 16, 2020 at 8:31
I guess it was caused by the wrong path expression.
Bad owner or permissions on C:Usersgary/.ssh/config
The /.ssh should be .ssh. So I try to use git bash (the terminal tool when install git in Windows system) to run ssh command. It really works. But I don’t really know if it is caused by the reason I guessed.
answered Oct 15, 2020 at 12:05
nilknownilknow
2993 silver badges6 bronze badges
Hi guys after a troubleshoot for a day I found that this «m.. f..» config file should not stand in the .ssh/ path.
For VSCODE just set the config in ‘C:ProgrmaDatasshssh_config’ path as proposed in the second choice of the palette command, and forget .shh path for this configuration.
That worked fine for me.
Nota: there was also a known_host file also created here with strange VM names inside, I deleted also this file. and that helps
answered Feb 16, 2022 at 6:08
For me, re-editing the permission settings in Windows is too complicated. Regenerating another configuration in vscode does not work either.
I set a custom config file path to solve this problem.
[«Remote SSH: Config file»]
The absolute file path to a custom SSH config file.
note: search this option by @ext:ms-vscode-remote.remote-ssh,ms-vscode-remote.remote-ssh-edit config file
answered Aug 3, 2022 at 10:04
Lately, I have been working a lot with SSH and Windows 10, for one transitioning away from WMI for certain things, hopefully, a blog post coming on that front soon. Setting up SSH on Windows 10 is fairly simple to do, but it is one of those processes that can be wrought with missteps and misinformation from various places. As a case in point, you may receive permissions issues on a private key connecting to Windows 10. Why is this? Let’s take a look at bad owner or permissions on SSH config Windows 10 and see what this relates to.
Public key authentication with Windows 10
First of all, if you see this error mentioned in the title of the blog post, it means you are most likely attempting to configure public key authentication to access your OpenSSH installed and configured in Windows 10. Why do you want to configure public key authentication?
First of all, if you want to know how to configure Windows 10 SSH, take a look at my blog post here:
- OpenSSH Server Windows 10 Install with Public Key authentication
Also, learn about OpenSSH in general here:

- OpenSSH
Public key authentication is noted as a more secure way to authenticate to an OpenSSH server. Why is this? With public-key authentication, you have two parts of a cryptographic key that grants access. It includes both a private key and a public key. The SSH server possesses the public key of the key pair, while you as the user possess the private key. In addition to passing the physical private key file, you can also secure the private key with a password.
So, it is easy to understand how this type of authentication is much more secure. As far as the cryptographic key is concerned, an attacker can’t simply brute force the server to guess a weak, guessable, or cracked password to gain access. They have to have possession of the key and know the password if the private key is secured with one.
SSH clients have also come a long way in recognizing when there may be bad ideas in play when it comes to private key files. If the permissions contain other security permissions on the private key file other than the user that should possess those permissions, the key can be more easily compromised.
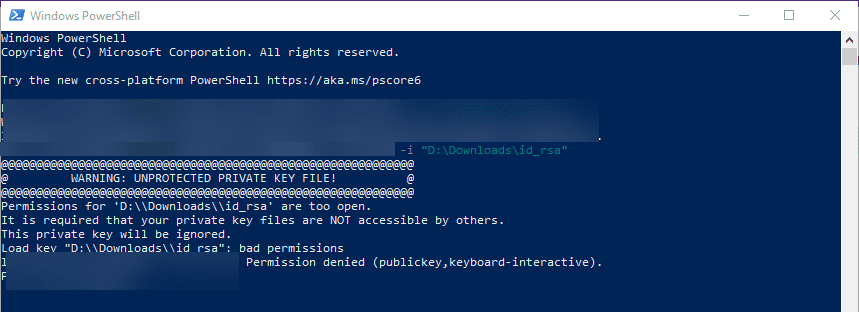
Many SSH clients check for the permissions configured on the SSH private key and if these are too permissive, it will not be allowed for use to make the SSH connection. Note the following error seen when trying to SSH into a remote Windows 10 machine with wide-open permissions on the private key file:
The error above states the issue: Permissions for the key file are too open. It is required that your private key files are NOT accessible by others. This private key will be ignored.
To get past the Bad Owner or Permissions on SSH Config Windows 10 error, you need to configure three things:
- Permissions on the authorized_keys file
- Permissions on your private key file
- sshd_config file changes
Part of the process to properly configure your Windows 10 SSH session for public-key authentication is ensuring the permissions are set correctly, both on the authorized_keys file (holds public key) and the private key file that holds the private key side of your key pair. Let’s take a look at both.
When you enable OpenSSH on your Windows 10 machine, you need to create the .ssh directory in the user profile of the user you will be logging in with. This is the location OpenSSH looks to find the authorized public keys, and by extension, the paired private keys that are allowed to access the machine.
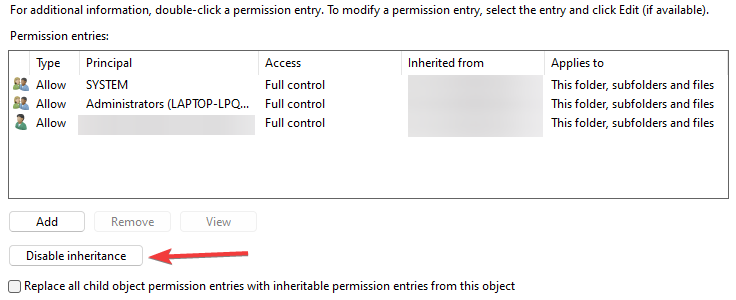
By default, when you create the directory and the authorized_keys file, it will have too many permissions assigned. As you can see, it will have the local Administrators group added to the file. Click Advanced.
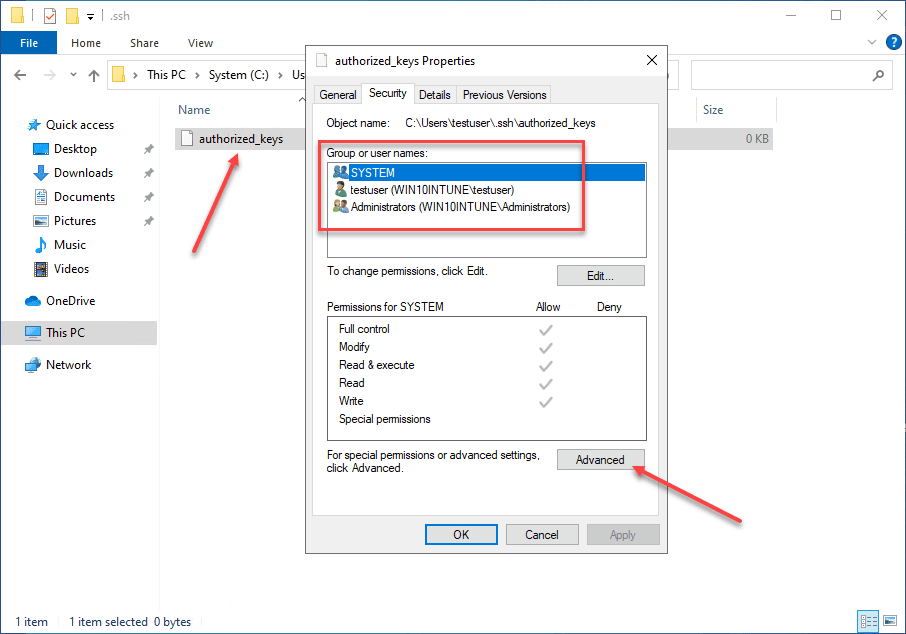
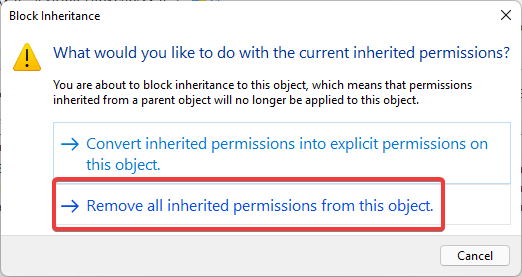
Here, we need to disable inheritance. This breaks inheritance on the folder and allows you to set explicit permissions.
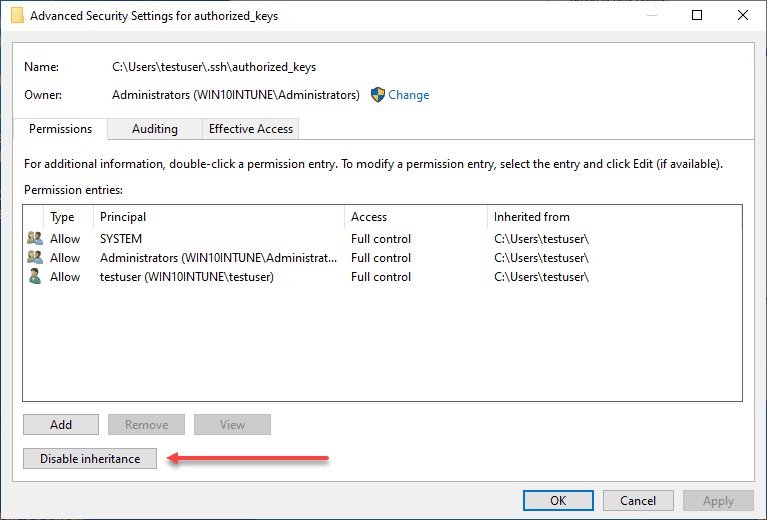
Choose the option Convert inherited permissions into explicit permissions on this object.
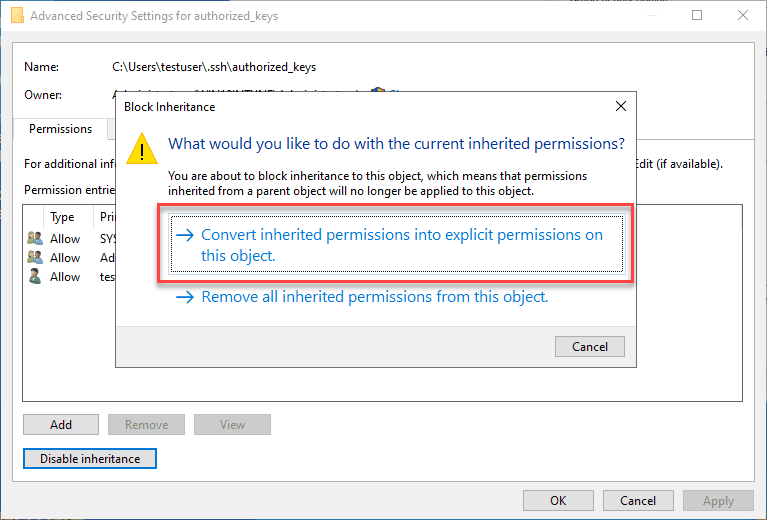
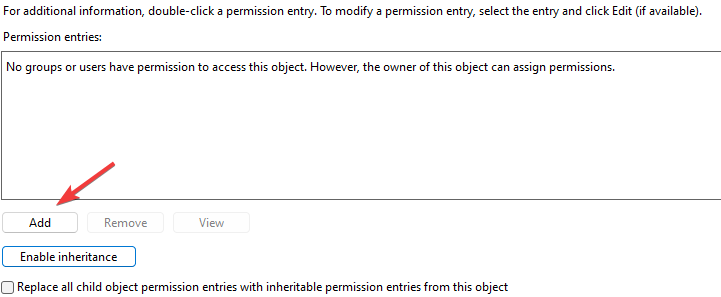
Adjust your permissions so that you only have SYSTEM and your username displayed as having permissions on the authorized_keys file.
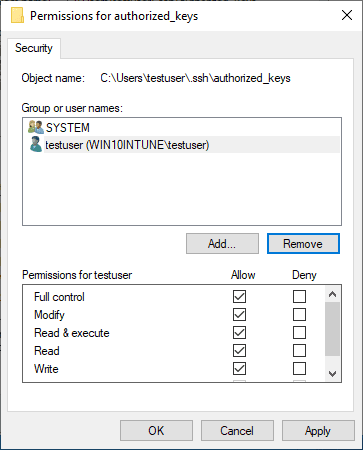
Permissions on your private key file
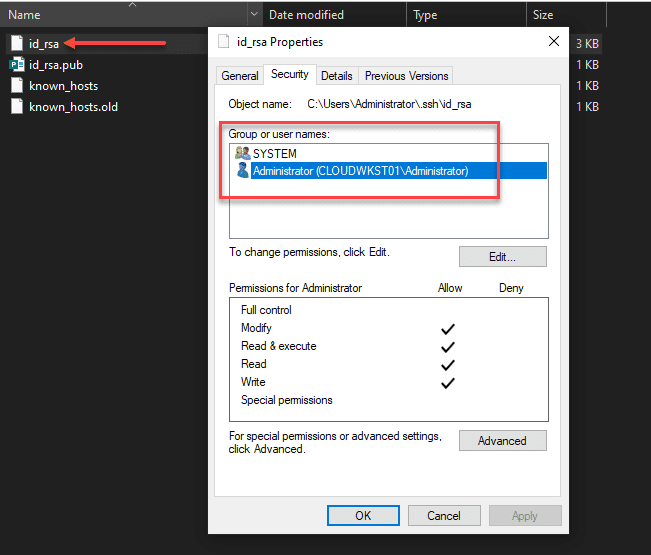
Now, on your private key, you need to ensure the same thing is set. The user that you are logged in with and SYSTEM are the only permissions that need to be enumerated on the private key file.
sshd_config file changes
Now that we have the permissions set correctly on the authorized_keys file and the private key, we need to make sure the sshd_config file is configured correctly. We need to make three changes for this to work correctly:
Below, I have uncommented the PubeyAuthentication yes stanza. Then, we have commented out the PasswordAuthentication yes and Match Group administrators configuration.
PubkeyAuthentication yes
#PasswordAuthentication yes
#Match Group administrators
# AuthorizedKeysFile __PROGRAMDATA__/ssh/administrators_authorized_keysBe sure to restart your OpenSSH SSH Server service on your Windows 10 machine after making these changes to the sshd_config file. Once the changes are in place, you should be able to connect to the machine via SSH.
Wrapping Up
Connecting to Windows 10 via SSH is a great way to make secure connections to Windows 10 when public-key authentication is used. It can also be a great way to use solutions like Ansible to connect to your Windows 10 boxes remotely.
This article helps to solve a Bad owner or permissions on .ssh/config issue occurring on a Windows 10 machine when using a terminal emulator like cmder.
Using cmder on a Windows 10 development machine, I noticed issues after I recently added a new user account to the system. It caused permission issues due to the way inheritance of ownership was being handled.
Resolve ‘Bad Owner or Permission on .ssh/config’ issues on Windows 10
To resolve, I did the following to fix up the permission issues that cause a `Bad owner or permissions on C:\Users\Peter/.ssh/config` from occurring each time I tried to connect to a remote host within cmder:
Fixing the ‘Bad owner or permissions on .ssh/config’ Issue
Follow these steps in the Windows 10 GUI to resolve the permission issues:
- Locate your .ssh folder. It is usually located in C:Users e.g. C:UsersPeter.
- Go to this location with Windows Explorer.
- Right click the .ssh folder and click ‘Properties’.
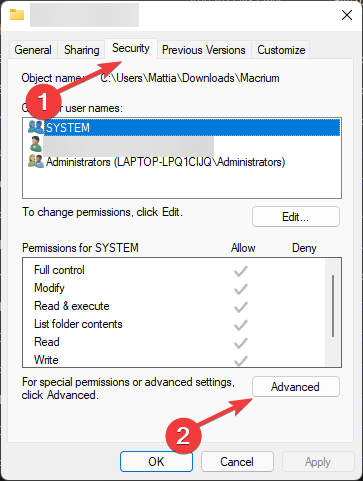
- Find and click the ‘Security’ tab.
- Then click ‘Advanced’.
- Click ‘Disable Inheritance’, click OK.
- A warning popup will appear. Click ‘Remove all inherited permissions from this object’.
Disable Inherited permissions on Windows 10 for a folder.
- Click ‘OK’ to close the ‘Advanced Security Settings for .ssh’ window.
- You will notice that all users will be removed. Let’s add the owner back. On the same window, click the ‘Edit’ button.
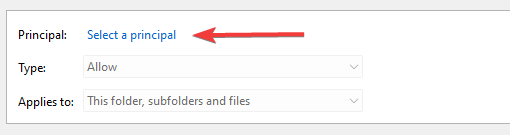
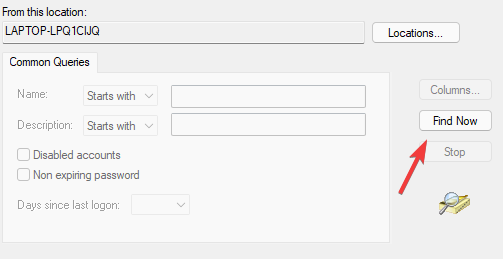
- Next, click ‘Add’ to bring up the Select Users or Groups window.
- Click ‘Advanced’, then click the ‘Find Now’ button. A list of user results should appear.
- Select your user account. In my case, I selected user ‘Peter’.
- Then click OK (approximately three times) to close all windows.
Once all that is done, close and open the cmder app again and attempt to connect to a remote SSH host. Hopefully your set up is fixed and the ‘Bad owner or permissions on .ssh/config’ error prompt is gone.
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and
privacy statement. We’ll occasionally send you account related emails.
Already on GitHub?
Sign in
to your account
Closed
vdonchev opened this issue
May 2, 2018
· 19 comments
Comments
Since yesterday’s windows update (1810), I got this error when trying to connect to any of my servers through ssh:
λ ssh myserver
Bad owner or permissions on C:\Users\MY_USER/.ssh/config
I am using cmder 1.3.4 (i have also tried with 1.3.5).
Ok, here’s the solution that worked for me:
Right click on file:
Properties -> Security -> Advanced -> Disable Inheritance -> Remove all inherited permissions from this object
naseefnaseer, nucklehead, livevasiliy, joshuaPurushothaman, and LyricPants66133 reacted with laugh emoji
jpotma, alexdb88, kuhung, neculaionutni, makampf, fider, RobertYim, AnubisYe, adifahmi, Pippinrao, and 21 more reacted with confused emoji
naseefnaseer, jazz7381, techiall, AugustoEscanor, timgh101, livevasiliy, wbmrcb, S-Ammar, joshuaPurushothaman, and kamisoft-fr reacted with heart emoji
naseefnaseer, ooxif, and nwlab reacted with eyes emoji
I fail to see how that is Cmder’s fault?
It’s working ok with gitbash for example. I have this problem with cmder only.
Ok, here’s the solution that worked for me:
Right click on file:
Properties->Security->Advanced->Disable Inheritance->Remove all inherited permissions from this object
Thanks for your solution. It indeed solved my problem but raise another problem that I can’t write config file now. How can I solve this problem?
Ok, here’s the solution that worked for me:
Right click on file:
Properties->Security->Advanced->Disable Inheritance->Remove all inherited permissions from this objectThanks for your solution. It indeed solved my problem but raise another problem that I can’t write
configfile now. How can I solve this problem?
你可以添加一个用户权限
Thanks, eveyone!I have solved, but setting a content in my vs codes solves the issue !
tatiany-jimirobo, Lilac-Lee, tomhht, vadviktor, Heladitooo, kevinsulatra, aafanasyev, and a-sidorova reacted with heart emoji
rizerzero, cristianireyes, jingyao97, tomhht, vadviktor, Heladitooo, kevinsulatra, and aafanasyev reacted with rocket emoji
Ok, here’s the solution that worked for me:
Right click on file:
Properties->Security->Advanced->Disable Inheritance->Remove all inherited permissions from this object
Thanks. It works for me.
Remember to leave permissions for yourself (Full control was fine)
Ok, here’s the solution that worked for me:
Right click on file:
Properties->Security->Advanced->Disable Inheritance->Remove all inherited permissions from this object
this works for me,thanks
Thanks, eveyone!I have solved, but setting a content in my vs codes solves the issue !
It helps for me!!! Thanks!!! (Прописан путь C:Usersadminsshconfig как на скрине. И все заработало!)
Thanks, eveyone!I have solved, but setting a content in my vs codes solves the issue !
It helps for me!!!!!!!!!!!!!!! Thanks
Ok, here’s the solution that worked for me:
Right click on file:
Properties->Security->Advanced->Disable Inheritance->Remove all inherited permissions from this object
For me helped ONLY setting permissions Like owner — full control (and disabling permissions inheritance, for sure!!) for two more files — ‘config’ file itself and both of my PRIVATE and PUBLIC keys. Only after that Remote-SSH plugin started working as it has to.
It seems that such permissions for VS Code are good enough like 0600 for «.ssh» folder in Linux OS’es.
You can also fix this from the command line. Here are the commands I used:
icacls c:users<username>.sshconfig /inheritance:r
icacls c:users<username>.sshconfig /grant <username>:f
icacls c:users<username>.sshid_rsa /inheritance:r
icacls c:users<username>.sshid_rsa /grant <username>:f
Thanks, eveyone!I have solved, but setting a content in my vs codes solves the issue !
Worked for me, thaks!
Ok, here’s the solution that worked for me:
Right click on file:
Properties->Security->Advanced->Disable Inheritance->Remove all inherited permissions from this object
I had to do this change after I changed the disk where Vagrant is installed.
Ok, here’s the solution that worked for me:
Right click on file:
Properties->Security->Advanced->Disable Inheritance->Remove all inherited permissions from this object
If you followed this without thinking, like I did, it will solve the problem but leave you with no permissions on the file.
I resolved this by opening a PowerShell with Administrator privileges, and then ran the following command on the file:
takeown /F C:Users<user-name>.sshconfig
Where <user-name> is your user name on the system. Then, you can set yourself as the owner and reassign permissions properly through the right-click menu as you normally would.
Hope this helps someone.
Thanks, eveyone!I have solved, but setting a content in my vs codes solves the issue !
best answer!!! thank u
Thanks, eveyone!I have solved, but setting a content in my vs codes solves the issue !
Thank you! This works for me.
by Farhad Pashaei
As a technophile, Farhad has spent the last decade getting hands-on experience with a variety of electronic devices, including smartphones, laptops, accessories, wearables, printers, and so on. When… read more
Published on April 27, 2022
- Changing the permission on the SSH folder can be the quickest fix and does not require any kinds of commands.
- The problem is primarily caused by permission settings, which should be corrected after altering permissions.
- A few commands to solve this issue are available on the internet, some of which may be really helpful.
XINSTALL BY CLICKING THE DOWNLOAD FILE
This software will repair common computer errors, protect you from file loss, malware, hardware failure and optimize your PC for maximum performance. Fix PC issues and remove viruses now in 3 easy steps:
- Download Restoro PC Repair Tool that comes with Patented Technologies (patent available here).
- Click Start Scan to find Windows issues that could be causing PC problems.
- Click Repair All to fix issues affecting your computer’s security and performance
- Restoro has been downloaded by 0 readers this month.
SSH is commonly used by network administrators to control systems, and issues such as Bad owner or permissions on SSH config occur seldom.
Fixing this problem is rather straightforward, but it is one of those processes rife with blunders and misinformation from multiple sources.
But what if someone who did not know how to fix this problem encountered it? Here are some fixes that might help you.
What is SSH used for?
SSH connections have been used to secure a variety of communications and administrative or management duties between a local workstation and a remote host.
Among other things, SSH is used to control routers, server hardware, virtualization platforms, operating systems (OSes), and file transfer programs.
How can I fix bad owner or permissions on SSH config?
1. Change permission
- Open Windows Explorer and locate your .ssh folder. It is usually located in
C:Users - Right-click the .ssh folder and click Properties.
- Find and click the Security tab and then click Advanced.
- Click Disable Inheritance.
- A warning popup will appear. Click Remove all inherited permissions from this object.
- Click OK to close the Advanced Security Settings for .ssh window.
- You will notice that all users will be removed. On the same window, click the Add button.
- Next, click Select a principal to bring up the Select Users or Groups window.
- Click Advanced.
- Click the Find Now button. A list of user results should appear.
- Select your user account.
- Then click OK.
- Fix: This Page Isn’t Eligible to Have a Username [Facebook]
- Why Can’t I Download Netflix on My Laptop & How to Fit It
- How to Fix Trust This Computer Not Showing Up on iPhone & Mac
2. Using commands
- First, type in
chown $USER ~/.ssh/config - After that, type in
chmod 644 ~/.ssh/config
What is the difference between telnet and SSH?
Telecommunications and Networks are abbreviated as Telnet, and it is a networking protocol best known for the UNIX platform.
Telnet is credited as being the first Internet, having been created as a method of remote control for managing mainframe computers from remote terminals when the Internet originally opened in 1969.
While there is no official fix for bad owner or permissions on the SSH config problem, many users have reported that removing inherited permissions has worked for them.
Additionally, there are numerous lines of commands that might fix the issue and are available on the web and in the forums.
The fix for a bad owner or permissions on the SSH config problem can vary in steps depending on the process type.
If you are experiencing ssh_exchange_identification connection closed by host issues, read this article.
Let us know whether you were able to fix the bad owner or permissions on the SSH config in the comments section below.
Newsletter
I’m trying to use ssh.exe in Cygwin (in Windows 7). I copied a config file into c:cygwinhome[USERNAME].ssh. When I run ssh (for example, ssh -vT git@bitbucket.org) I get the following error:
OpenSSH_5.9p1, OpenSSL 0.9.8r 8 Feb 2011
Bad owner or permissions on /home/[USERNAME]/.ssh/config
How do I get ssh to read my configuration file?
asked Oct 20, 2011 at 11:02
Rebecca ScottRebecca Scott
1,3182 gold badges14 silver badges19 bronze badges
1
After doing as above, I always got this:
total 22
drwxrwxr-x+ 1 jl None 0 Sep 9 18:44 .
drwxrwxr-x+ 1 jl None 0 Sep 9 18:44 ..
-rw-rw---- 1 jl None 129 Jul 1 14:30 config
and the error on .ssh/config. So I’ve run chown on the .ssh folder, and chmod again like this:
> chown -R [USERNAME]:users .ssh/
and then:
> chmod -R 600 .ssh/
and finally I got it working:
total 29
drwxrwxr-x+ 1 jl None 0 Sep 9 18:44 .
drwxrwxrwt+ 1 jl None 0 Sep 9 18:44 ..
drw-------+ 1 jl Users 0 Sep 9 18:44 .ssh
Edit(for bash on Windows10)
When you get the error..
Failed to add the host to the list of known hosts (/PATH_TO_HOME/USERNAME/.ssh/known_hosts).
Make sure that known_hosts is writable
$ chmod 755 known_hosts
Note: I believe you only need to set 600 for your private key
Then, try to ssh.
When you get..
Permanently added ‘HOST_IP’ (RSA) to the list of known hosts.
You may replace mode 600
$ chmod 600 known_hosts
P.S.: I think this is a bug on Windows 8.
answered Sep 10, 2013 at 14:03
8
This answer is copied verbatim from https://superuser.com/a/875934/82032. This is the only answer that worked for me after a recent cygwin upgrade.
Don’t forget the ACLs
Nothing worked for me until I stripped the file of ACLs and reset the permissions.
#remove ACLs
setfacl -b ~/.ssh/config
#reset permissions
chmod 0600 ~/.ssh/config
You can use getfacl to view the current ACL on a file.
getfacl ~/.ssh/config
Before I removed the ACLs (Broken):
# owner: Administrators
# group: None
user::rw-
group::---
group:Authenticated Users:rwx
group:SYSTEM:rwx
mask:rwx
other:---
After: (working)
# file: config
# owner: myusername
# group: None
user::rw-
group::---
other:---
answered Feb 18, 2015 at 16:40
gdw2gdw2
1,2751 gold badge11 silver badges11 bronze badges
3
For unix & OSX
Quite simply:
chown -R $USER:users ~/.ssh/
chmod -R 600 ~/.ssh/
For Windows
If the file is a windows (NTFS) symbolic link, the above won’t work. You need to make it a regular file. I am not sure why.
If you don’t have openssh or cygwin, use chocolatey to install it easily.
choco install cyg-get
Open Cygwin Terminal that was installed with chocolatey and run (note that ssh-keygen creates new keys):
cyg-get install openssh
ssh-keygen
cd ~/.ssh && explorer.exe .
Verify keys are there (or replace them with the keys you want), and then in Cygwin shell:
chown -R $USER:users ~/.ssh/
chmod -R 600 ~/.ssh/
Or for the rare case that you’re using (and generated the keys from) chocolatey’s SSH package:
chown -R $USER:users /cygdrive/c/Users/$USER/.ssh
chmod -R 600 /cygdrive/c/Users/$USER/.ssh
answered Sep 25, 2014 at 13:19
JonathanJonathan
1,61110 gold badges28 silver badges47 bronze badges
1
Check the permissions of the config file using Cygwin’s ls command:
> c:cygwinbinls.exe -la c:cygwinhome[USERNAME].ssh
It will probably be something like this:
total 5
drwxrwxrwt+ 1 Administrators None 0 Oct 20 17:02 .
drwxr-xr-x+ 1 [USERNAME] None 0 Oct 19 08:15 ..
-rw------- 1 Administrators None 57 Oct 20 16:58 config
The config file needs to belong to [USERNAME]. Try this:
> c:cygwinbinchown.exe [USERNAME] c:cygwinhome[USERNAME].sshconfig
ls -la should now show the correct owner. If that still doesn’t work, try resetting the mode (permissions):
> c:cygwinbinchmod.exe 700 c:cygwinhome[USERNAME].sshconfig
answered Oct 20, 2011 at 11:10
Rebecca ScottRebecca Scott
1,3182 gold badges14 silver badges19 bronze badges
0
Important note if your Windows is not in US English: the «users» group’s name is locale-dependant. For example, if your Windows is in Spanish, you’ll have to change the files’ ownership with chown $USER:Usuarios *
answered Jan 11, 2015 at 4:33
RAKKRAKK
3553 silver badges14 bronze badges
None of these (chmod/chown/icacls/setacl/copyacls/explorer>security) worked on my cygwin64/win7/admin, finally this works with cygwin64/ssh -F ~/.ssh/config other solutions are to use older ssh in cygwin32 or ssh in git for windows..
answered Mar 28, 2017 at 7:17
moshmosh
2972 silver badges8 bronze badges
1
For those who uses noacl in path with ~/.ssh dir simple solution is to create native NTFS symbolic link:
cmd# mklink c:home.ssh c:optcygwinhomemisc.ssh
symbolic link created for c:home.ssh <<===>> c:optcygwinhomemisc.ssh
With noacl there is no way to set permissions other then rwxr-xr-x or rw-r--r--. As / hierarchy should be without noacl (or should be with acl) you can create directory here and point to it problematic places for Cygwin’s apps.
answered Aug 14, 2017 at 0:22
gavenkoagavenkoa
1,8345 gold badges29 silver badges38 bronze badges
1
tldr: You may have created the config as adminstrator
Solution
These solutions may be overkill if you ended up mistakenly creating the file as admin, and trying to use the file with local perms.
- Copy the contents of your ssh config
- Delete the file
- Open a new shell (local — non admin)
- Navigate to the path where your config is stored (usually
~/.sshin PowerShell or%userprofile%.sshin cmd) - Run
notepad .config
Simple commands (PowerShell):
$sshPath = '~/.ssh/config'
$content = cat $sshPath
# In case the line above fails, this check will prevent your current config to get deleted
if ($content) {
rm $sshPath
$content | Out-File -en ascii $sshPath
}
answered Sep 19, 2019 at 21:12
When I try to ssh to another box, I get this strange error
$ ssh hostname
Bad owner or permissions on ~/.ssh/config
But I made sure that I own and have rw permissions on the file:
ls -la ~/.ssh/
total 40K
drwx------ 2 robert robert 4.0K Mar 29 11:04 ./
drwx------ 7 robert robert 4.0K Mar 29 11:04 ../
-rw-r--r-- 1 robert robert 2.0K Mar 17 20:47 authorized_keys
-rw-rw-r-- 1 robert robert 31 Mar 29 11:04 config
-rw------- 1 robert robert 1.7K Aug 4 2010 id_rsa
-rw-r--r-- 1 robert robert 406 Aug 4 2010 id_rsa.pub
-rw-r--r-- 1 robert robert 6.1K Mar 29 11:03 known_hosts
asked Mar 29, 2011 at 18:15
RobertRobert
14.5k4 gold badges18 silver badges14 bronze badges
2
I needed to have rw for user only permissions on config. This fixed it.
chmod 600 ~/.ssh/config
As others have noted below, it could be the file owner. (upvote them!)
chown $USER ~/.ssh/config
If your whole folder has invalid permissions here’s a table of possible permissions:
| Path | Permission |
|---|---|
| .ssh directory (code) | 0700 (drwx——) |
private keys (ex: id_rsa) (code) |
0600 (-rw——-) |
config |
0600 (-rw——-) |
public keys (*.pub ex: id_rsa.pub) |
0644 (-rw-r—r—) |
authorized_keys (code) |
0644 (-rw-r—r—) |
known_hosts |
0644 (-rw-r—r—) |
Sources:
- openssh check-perm.c
- openssh readconf.c
- openssh ssh_user_config fix_authorized_keys_perms
answered Mar 29, 2011 at 18:16
RobertRobert
14.5k4 gold badges18 silver badges14 bronze badges
13
These commands should fix the permission problem:
chown $USER ~/.ssh/config
chmod 644 ~/.ssh/config
Prefix with sudo if the files are owned by different user (or you don’t have access to them).
If more files are affected, replace config with *.
In man ssh we can read:
Because of the potential for abuse, this file must have strict permissions: read/write for the user, and not
writable by others. It may be group-writable provided that the group in question contains only the user.
answered Aug 3, 2015 at 11:30
kenorbkenorb
6,2031 gold badge44 silver badges53 bronze badges
4
For me it was an issue with my user account not being the owner of the file
sudo chown myuser ~/.ssh/config
answered May 28, 2015 at 1:07
svnmsvnm
2812 silver badges4 bronze badges
If on Windows Subsystem for Linux (WSL) and you pointed your WSL home directory to your Windows home directory (not recommended!) then chmod has no effect. Before you can chmod the files mentioned in other answers you must add
[automount]
options = "metadata"
to your /etc/wsl.conf then restart WSL (requires build 17093 or later).
Before mount says:
C: on /mnt/c type drvfs (rw,noatime,uid=1000,gid=1000,case=off)
After mount says:
C: on /mnt/c type drvfs (rw,noatime,uid=1000,gid=1000,metadata,case=off)
answered Aug 22, 2019 at 19:26
Nathan KiddNathan Kidd
2552 silver badges5 bronze badges
1
Don’t forget about the group:
chown $USER:$USER ~/.ssh/config

answered Jan 13, 2020 at 21:10
2
I met this issue on windows 10 with vagrant ssh. And tried all the above methods, but get no luck. Finally I deleted that ssh config file and then it works!
vagrant ssh
Bad owner or permissions on C:\Users\Jeff/.ssh/config
del ...sshconfig
vagrant ssh
Welcome to Ubuntu 14.04.6 LTS (GNU/Linux 3.13.0-170-generic x86_64)
* Documentation: https://help.ubuntu.com/
System information as of Thu Feb 27 02:23:03 UTC 2020
System load: 0.0 Processes: 77
Usage of /: 5.1% of 39.34GB Users logged in: 0
Memory usage: 21% IP address for eth0: 10.0.2.15
Swap usage: 0% IP address for docker0: 172.17.0.1
Graph this data and manage this system at:
https://landscape.canonical.com/
New release '16.04.6 LTS' available.
Run 'do-release-upgrade' to upgrade to it.
vagrant@vagrant-ubuntu-trusty-64:~$
answered Feb 27, 2020 at 4:02
Jeff TianJeff Tian
1211 silver badge6 bronze badges
2
Starting from Windows 10 build 1809, Windows has a native SSH client that is based on the OpenSSH port.
If you try to connect to some host from a Windows command-line prompt (CMD) or PowerShell using the ssh command, you may receive the error as follows:
Bad owner or permissions on
C:\Users\<username>/.ssh/config
This short note shows how to fix the permissions on all the files under the C:\Users\<username>/.ssh folder.
Right-click on the .ssh folder and select “Properties“.
Go to the “Security” tab and click on “Advanced“:
Click on “Disable inheritance“:
Choose the option “Remove all inherited permissions permissions from this object“:
Remove all users and groups except SYSTEM and your user, check the box “Replace all child object permission entries with inheritable permission entries from this object” and click on “OK“:
The correct owners and permissions on the C:\Users\<username>/.ssh folder should look like this:
The “Bad owner or permissions on C:\Users\<username>/.ssh/config” error should be resolved now and you should be able run the ssh command without any issues.
Содержание
- 2 ways to fix bad owner or permissions on SSH config
- What is SSH used for?
- How can I fix bad owner or permissions on SSH config?
- 1. Change permission
- 2. Using commands
- What is the difference between telnet and SSH?
- Fix Bad Owners or Permission on .ssh/config
- Pre-Requisites
- What Causes Bad Owners or Permission Errors?
- How to Fix Bad Owner and Permission Errors
- Conclusion
- About the author
- John Otieno
- Bad Owner or Permissions on SSH Config Windows 10
- Public key authentication with Windows 10
- Bad Owner or Permissions on SSH Config Windows 10
- Permissions on the authorized_keys file
- Permissions on your private key file
- sshd_config file changes
- Wrapping Up
2 ways to fix bad owner or permissions on SSH config
SSH is commonly used by network administrators to control systems, and issues such as Bad owner or permissions on SSH config occur seldom.
Fixing this problem is rather straightforward, but it is one of those processes rife with blunders and misinformation from multiple sources.
But what if someone who did not know how to fix this problem encountered it? Here are some fixes that might help you.
What is SSH used for?
SSH connections have been used to secure a variety of communications and administrative or management duties between a local workstation and a remote host.
Among other things, SSH is used to control routers, server hardware, virtualization platforms, operating systems (OSes), and file transfer programs.
How can I fix bad owner or permissions on SSH config?
1. Change permission
- Open Windows Explorer and locate your .ssh folder. It is usually located in C:Users
- Right-click the .ssh folder and click Properties .
- Find and click the Security tab and then click Advanced.
- Click Disable Inheritance.
- A warning popup will appear. Click Remove all inherited permissions from this object.
- Click OK to close the Advanced Security Settings for .ssh window.
- You will notice that all users will be removed. On the same window, click the Add button.
- Next, click Select a principal to bring up the Select Users or Groups window.
- Click Advanced.
- Click the Find Now button. A list of user results should appear.
- Select your user account.
- Then click OK.
Read more about this topic
2. Using commands
- First, type in
chown $USER
/.ssh/config
After that, type in
chmod 644
What is the difference between telnet and SSH?
Telecommunications and Networks are abbreviated as Telnet, and it is a networking protocol best known for the UNIX platform.
Telnet is credited as being the first Internet, having been created as a method of remote control for managing mainframe computers from remote terminals when the Internet originally opened in 1969.
While there is no official fix for bad owner or permissions on the SSH config problem, many users have reported that removing inherited permissions has worked for them.
Additionally, there are numerous lines of commands that might fix the issue and are available on the web and in the forums.
The fix for a bad owner or permissions on the SSH config problem can vary in steps depending on the process type.
Let us know whether you were able to fix the bad owner or permissions on the SSH config in the comments section below.
Источник
Fix Bad Owners or Permission on .ssh/config
Due to the comfort and control that SSH gives us, we try to implement methods such as Password-less logins using SSH keys and two-factor authentications. However, despite this, we can still encounter errors that might prevent us from using SSH to log in to remote machines.
This quick tutorial will show you how to solve bad ownership or permission on the .ssh/config file.
Pre-Requisites
Before we get started on the guide:
- Ensure you have a private and public key
- Ensure your public key is available in the authorized_keys file of your remote machine.
If you do not have either of the requirements above met, consider the following tutorial where I detail how to generate and copy SSH key-pairs.
What Causes Bad Owners or Permission Errors?
The bad owner or permission error on the .ssh/config file results from incorrect permissions either on the file itself or the .ssh directory.
The files in the .ssh directory should have the read and write permission of the user only; that does not include the group or others.
How to Fix Bad Owner and Permission Errors
To solve this error, all we need to do is set the correct permissions on the .ssh/config file.
If you are not that comfortable with Linux permissions, check out this intuitive tool for using chmod.
To set the correct permissions, use the command:
Once you execute the above command, the file permission should be as follows:
You can also use the chown command to upvote the owner of the file using the command:
Using these two methods, you should have the bad owner or permission error fixed, and you can proceed to log in to your SSH.
Conclusion
That was a short and quick guide on resolving .ssh/config bad owner or permission error. If you are looking for a more in-depth tutorial, check out the following SSH troubleshooting guide.
John Otieno
My name is John and am a fellow geek like you. I am passionate about all things computers from Hardware, Operating systems to Programming. My dream is to share my knowledge with the world and help out fellow geeks. Follow my content by subscribing to LinuxHint mailing list
Источник
Bad Owner or Permissions on SSH Config Windows 10
Lately, I have been working a lot with SSH and Windows 10, for one transitioning away from WMI for certain things, hopefully, a blog post coming on that front soon. Setting up SSH on Windows 10 is fairly simple to do, but it is one of those processes that can be wrought with missteps and misinformation from various places. As a case in point, you may receive permissions issues on a private key connecting to Windows 10. Why is this? Let’s take a look at bad owner or permissions on SSH config Windows 10 and see what this relates to.
Public key authentication with Windows 10
First of all, if you see this error mentioned in the title of the blog post, it means you are most likely attempting to configure public key authentication to access your OpenSSH installed and configured in Windows 10. Why do you want to configure public key authentication?
First of all, if you want to know how to configure Windows 10 SSH, take a look at my blog post here:
Also, learn about OpenSSH in general here:
Public key authentication is noted as a more secure way to authenticate to an OpenSSH server. Why is this? With public-key authentication, you have two parts of a cryptographic key that grants access. It includes both a private key and a public key. The SSH server possesses the public key of the key pair, while you as the user possess the private key. In addition to passing the physical private key file, you can also secure the private key with a password.
So, it is easy to understand how this type of authentication is much more secure. As far as the cryptographic key is concerned, an attacker can’t simply brute force the server to guess a weak, guessable, or cracked password to gain access. They have to have possession of the key and know the password if the private key is secured with one.
SSH clients have also come a long way in recognizing when there may be bad ideas in play when it comes to private key files. If the permissions contain other security permissions on the private key file other than the user that should possess those permissions, the key can be more easily compromised.
Many SSH clients check for the permissions configured on the SSH private key and if these are too permissive, it will not be allowed for use to make the SSH connection. Note the following error seen when trying to SSH into a remote Windows 10 machine with wide-open permissions on the private key file:
The error above states the issue: Permissions for the key file are too open. It is required that your private key files are NOT accessible by others. This private key will be ignored.
Bad Owner or Permissions on SSH Config Windows 10
To get past the Bad Owner or Permissions on SSH Config Windows 10 error, you need to configure three things:
- Permissions on the authorized_keys file
- Permissions on your private key file
- sshd_config file changes
Permissions on the authorized_keys file
Part of the process to properly configure your Windows 10 SSH session for public-key authentication is ensuring the permissions are set correctly, both on the authorized_keys file (holds public key) and the private key file that holds the private key side of your key pair. Let’s take a look at both.
When you enable OpenSSH on your Windows 10 machine, you need to create the .ssh directory in the user profile of the user you will be logging in with. This is the location OpenSSH looks to find the authorized public keys, and by extension, the paired private keys that are allowed to access the machine.
By default, when you create the directory and the authorized_keys file, it will have too many permissions assigned. As you can see, it will have the local Administrators group added to the file. Click Advanced.
Here, we need to disable inheritance. This breaks inheritance on the folder and allows you to set explicit permissions.
Choose the option Convert inherited permissions into explicit permissions on this object.
Adjust your permissions so that you only have SYSTEM and your username displayed as having permissions on the authorized_keys file.
Permissions on your private key file
Now, on your private key, you need to ensure the same thing is set. The user that you are logged in with and SYSTEM are the only permissions that need to be enumerated on the private key file.
sshd_config file changes
Now that we have the permissions set correctly on the authorized_keys file and the private key, we need to make sure the sshd_config file is configured correctly. We need to make three changes for this to work correctly:
Below, I have uncommented the PubeyAuthentication yes stanza. Then, we have commented out the PasswordAuthentication yes and Match Group administrators configuration.
Be sure to restart your OpenSSH SSH Server service on your Windows 10 machine after making these changes to the sshd_config file. Once the changes are in place, you should be able to connect to the machine via SSH.
Wrapping Up
Connecting to Windows 10 via SSH is a great way to make secure connections to Windows 10 when public-key authentication is used. It can also be a great way to use solutions like Ansible to connect to your Windows 10 boxes remotely.
My blog:
https://www.virtualizationhowto.com
_____________________________________________________
Social Media:
https://twitter.com/vspinmaster
Introduction to home lab automation tools I use — 0:00
Hashicorp Packer — what it is and what it does — 1:05
Looking at Packer and a demo of running the command — 1:46
Talking about Packer and how it fully automates operating system installation — 2:20
Introduction to Terraform, what it does, and how you use it — 2:54
Looking at executing Terraform, state files, and configuration — 3:53
Introduction to PowerShell, background, and what it does — 5:08
Introduction to PowerCLI module for PowerShell and how PowerShell is extensible — 5:44
Looking at installing the PowerCLI module — 6:14
Using PowerShell and PowerCLI with Visual Studio Code — 7:04
Introduction to Ansible and configuration management with Playbooks — 7:37
Looking at an inventory file, the Ansible ping command — 8:46
Running an Ansible Playbook to update Linux VMs — 8:56
Wrapping up and thoughts on automation tools in the home lab — 9:20
Building an Ubuntu 22.04 template with Packer:
Automated Windows Server 2022 Packer Build:
Terraform vSphere tutorial — Linux Virtual Machine Clone:
Ansible provisioning VMware VMs:
https://www.virtualizationhowto.com/2021/01/ansible-provisioning-vmware-with-vmware_guest-example/» data-video-title=»Best Home Lab Automation Tools! Packer, Terraform, PowerShell, and Ansible»>
My blog:
https://www.virtualizationhowto.com
Social Media:
https://twitter.com/vspinmaster
Introduction — 0:00
Where storage technology has come over the years — 1:05
Looking at where storage has come in 2022 — 1:45
Elimination of the two-tier storage approach — 2:23
Storage Pool and all devices configured in vSAN storage are capacity and performance — 2:48
Log Structured File system with efficiency improvements — 3:21
Encryption and compression are repositioned and more efficient with vSAN 8 — 3:38
Beginning configuration of the Express Storage Architecture — 4:03
Launching the configure vSAN storage wizard — 4:29
New default is the Express Storage Architecture ESA — 4:41
Services configuration — 4:57
Claiming disks for vSAN ESA — 5:08
I don’t have certified drives but we can still install — 5:23
Enabling Express Storage Architecture with a single disk from each host — 6:00
Creating fault domains — 6:40
Reviewing the configuration — 6:55
vCenter Server tasks kick off in vSphere Client — 7:13
Disks are added to hosts in the vSAN Cluster — 7:34
Looking at disk management — 8:00
Discussing viability of ESA for home labs — 8:33
Concluding thoughts with vSAN Express Storage Architecture and home lab thoughts — 8:53
Configure vSAN Express Storage Architecture ESA:
Upgrade to ESXi 8 in three ways:
VMware vSphere 8 Download links:
https://www.virtualizationhowto.com/2022/10/vmware-vsphere-8-download-links-for-esxi-8-and-vcenter-server-8/» data-video-title=»VMware’s Killer new storage in 2022! Single drive vSAN Express Storage Architecture home lab»>
My blog:
https://www.virtualizationhowto.com
_____________________________________________________
Social Media:
https://twitter.com/vspinmaster
Introduction — 0:00
Going over the typical vCenter Server installation method — 1:05
Relies on vCenter Server or ESXi host — 1:36
Deploy the VCSA appliance from the ISO file — 2:00
Looking at the OVA appliance — 2:14
Describing an error I received deploying the vCenter Server appliance — 2:52
Describing a change needed to successfully deploy a modified OVF template — 3:00
Using the OVFtool to create an OVF tool to deploy vCenter Server — 3:42
Converting the OVA to OVF process — 4:14
The OVF file is successfully created — 4:40
Navigating to the directory where we created the OVF — 4:52
Editing the OVF file — 5:15
Searching for the change we need to make — 5:30
Opening the modified OVF appliance file — 6:35
The wizard kicks off for phase 1 in the deployment of the VCSA appliance — 6:52
EULA — 7:19
Name the VM and storage location — 7:25
VCSA sizing — 7:30
Networking configuration — 7:36
SSO configuration — 8:07
System configuration — 8:17
Domain search path — 8:22
Completing the phase 1 and import begins — 8:36
VCSA booted and navigating manually to the VAMI interface — 9:10
Familiar vCenter Server installer interface from the VAMI interface — 9:33
Clicking Setup box — 9:50
Verifying the network properties — 10:05
Changing time synchronization and SSH access property — 10:15
SSO configuration — 10:25
CEIP options — 11:09
Summary screen — 11:19
Warning about disrupting the process — 11:29
Phase 2 begins — 11:50
VCSA appliance successfully deploys — 11:58
Wrapping up talking about VMware Workstation for home lab — 12:10
Upgrade to ESXi 8.0 in three ways:
VMware vSphere 8 download links:
William Lam’s blog post covering the error for vCenter Server 8 and VMware Workstation:
https://williamlam.com/2022/10/how-to-deploy-the-vcenter-server-appliance-vcsa-8-0-to-vmware-fusion-or-workstation.html» data-video-title=»Install vCenter Server 8 in VMware Workstation! Step-by-step process and error workaround»>
Источник