Contents
Introduction
This document provides information about an error message in the Cisco Adaptive Security Device Manager (ASDM).
This video posted to the Cisco Support Community demonstrates how to troubleshoot a few of the common ASDM access issues:
Prerequisites
Requirements
There are no specific requirements for this document.
Components Used
The information in this document is based on Cisco ASDM 5.0 and later.
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command.
Conventions
Refer to Cisco Technical Tips Conventions for more information on document conventions.
Problem: You are Authorized to Access Only Home and Monitoring Views
If you click the Configuration tab in the ASDM, you might recieve this error message: «you are authorized to access only Home and Monitoring Views«.
Solution
The error occurs due to the user privilege. Go to the PIX/ASA CLI prompt, and create the new user and password with full privilege 15 as shown here:
ASA(config)#username cisco password cisco123 priv 15
The full privilege level allows you to log into the ASDM.
Problem: Your Firewall Image has a Version Number Null which is not Supported by ASDM
When you try to run the ASDM interface, the Your Firewall image has a version number null which is not support by ASDM error may be received.
The same error on the FWSM appears as:
Your FWSM image has a version number unknown which is not supported by ASDM
This error is caused by one of these reasons:
-
No ASDM image in the flash
-
No aaa related configuration for ASDM access through http
-
Incompatible Java version
Solution 1
Verify whether or not the compatible ASDM image exists in the flash, and then specify the location of the image:
ASA(config)#show asdm image
ASA(config)#asdm image flash:asdm-XXX.bin
Solution 2
Enter the aaa command for ASDM access through http:
ASA(config)#aaa authentication http console <server-tag> LOCAL
Solution 3
Verify whether or not the Java version is compatible. Then upgrade/downgrade the Java version accordingly and install the JRE.
Solution 4
If you attempt to access the ASDM over a VPN connection, make sure the management-access <ASDM access Interface name> command is configured on the ASA. For example, if the ASDM is accessed using the inside interface, then use the management-access Inside command.
Problem: Using a 64-bit Java Version on Windows causes ASDM Launcher to Fail and the Launcher does not Run
When you use a 64-bit Java version on Windows, it causes the ASDM Launcher to fail and the launcher does not run.
Solution
This issue is documented in Cisco bug ID CSCtb86774 (registered customers only) .
The workaround is to run the ASDM using the web browser.
Problem: %ASA-7-725014: SSL lib error. Function: SSL3_GET_CLIENT_HELLO Reason: no shared cipher
This log displays when you try to load ASDM (which fails to load):
%ASA-7-725014: SSL lib error. Function: SSL3_GET_CLIENT_HELLO Reason: no shared cipher
Solution
In order to resolve this issue, use an alternate or additional encryption alogorithm and use the ssl encryption command:
ASA(config)# ssl encryption rc4-sha1
ASA(config)# ssl encryption rc4-md5
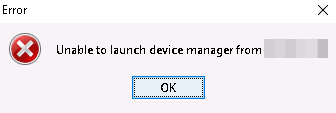
Problem: Unable to Launch Device Manager from ip-address/hostname
This error message displays when you access the ASDM:
Solution
In order to resolve this issue, check if a compatible ASDM image is on the flash or not:
ASA#show asdm image
Problem: When ‘http 0 0 outside’ is configured, the ‘Could not start admin’ Error Message is Displayed
This problem is caused by Cisco bug ID CSCsm39805 (registered customers only) . As a result, ASDM cannot be launched.
Solution
In order to resolve this issue, access the ASA through the CLI, and assign the http server to listen on a different port.
Example 1:
ASA(config)#no http server enable ASA(config)#http server enable 444
Example 2:
ASA(config)#no http server enable 8923 ASA(config)#http server enable 8924
Problem: Exception in thread «SGZ Loader: launchSgzApplet» java.lang.NumberFormatException: For input string: «1 year 0»
This problem is caused by Cisco bug ID CSCsr89144 (registered customers only) in ASA running for more than one year with ASDM 6.0.3 or 6.1. As a result, ASDM cannot be launched.
Solution
This error can be resolved by reloading the ASA.
Problem: ASDM Cannot be loaded. Click Ok to exit ASDM. Unexpected end of file from server.
This problem occurs when a user tries to connect to the ASA using ASDM.
Solution
Reload the ASA.
Problem: Error — ASDM is unable to read the configuration file
This problem is caused by Cisco bug ID CSCsx39786 (registered customers only) in ASA running with ASA 7.2.4 and ASDM 5.2.4. As a result, ASDM cannot be launched.
Solution
Downgrade to Java 6 Update 7.
Problem: Unable to Reset the VPN Tunnel using ASDM
The user is unable to reset the VPN Tunnel using ASDM.
Solution
Select Monitoring > VPN > VPN statistics > VPN session and choose active tunnel and log off in order to reset the tunnel.
Problem: Unable to load the DLL «C:Program FilesJavajre6binclientjvm.dll»
Not able to start ASDM because of the Java version mismatch.
Solution
In order to avoid this error, perform these steps:
-
Downgrade the Java version to Version 6, Update 7.
-
Edit the adsm-launcher config file and modify the Java path to the folder that contained the jvm.dll.
Problem: Unable to view access list hit count entry on ASDM
The Hit Counter of ASDM does not display a value, including zero (0).
Solution
ASDM always sends a request for all ACLs in one HTTP server request string to the FWSM. The FWSM device is unable to handle the super long request to its HTTPS server from the ASDM, runs out of buffer space, and finally drops the request. When you have too many access lists, the request from ASDM to the FWSM becomes too long for the FWSM to process. As a result, it does not get the correct response. This is an expected behavior with the functionality of ASDM and the FWSM. Bugs CSCta01974 (registered customers only) and CSCsz14320 (registered customers only) have been filed to address this behavior with no known workaround. A temporary workaround is to use the CLI to monitor the ACL hits.
There are several other bugs filed to address this issue which are superseded by another bug, CSCsl15055 (registered customers only) . This bug shows that the issue is fixed in 6.1(1.54). For the FWSM, the fixed ASDM version is 6.2.1F. The issue has been fixed by tweaking how the ASDM queries the FWSM for the ACL information. Instead of sending one big, long request string that contains all the access list information, the ASDM now splits them into multiple meaningful requests and sends to the FWSM for processing.
Note: The access list hit count entry on the FWSM is supported from version 4.0 onwards.
Problem: Unable to access ASDM when SSL encryption level is set to AES256-SHA1
User is unable to access ASDM when SSL encryption level is set to AES256-SHA1 on the PC.
Solution
This issue occurs when the command ssl encryption rc4-sha1 aes128-sha1 aes256-sha1 3des-sha1 is used which sets encryption level to AES256-SHA1. The issue can be resolved by either removing this command or by installing the JCE version of Java so that the PC becomes AES 256 compatible.
Problem: ASA network objects get deleted when using ASDM version 6.4.5
While editing an existing network object using ASDM version 6.4.5, the object disappears from the list of all objects when you click OK.
Solution
Downgrade to ASDM version 6.2.4 in order to resolve this issue.
Problem: Error — ASDM cannot be loaded. Unconnected sockets not implemented.
The user receives the ASDM cannot be loaded. Unconnected sockets not implemented. error message when accessing the ASDM.
Solution
This error message is the result of an incompatibility between the ASDM version and Java version, and is logged in Cisco bug ID CSCsv12681 (registered customers only) .
In order to resolve this issue, try one of these methods:
-
Upgrade the ASDM to version 6.2 or later.
-
Specify the Java version as Java 6 Update 7.
Problem: Performance issues when ASDM configuration size exceeds 512 kb on Windows
Performance issues seen on ASDM when the configuration exceeds 512 kb on a Windows machine.
Solution
ASDM supports a maximum configuration size of 512 kb. If you exceed this amount, you may experience performance issues. For example, when you load the configuration, the status dialog shows the percentage of the configuration that is complete. However, with large configurations, it stops incrementing and appears to suspend operation, even though ASDM might still be processing the configuration. If this situation occurs, we recommend that you consider increasing the ASDM system heap memory.
In order to increase the ASDM heap memory size, modify the launcher shortcut.
Complete these steps:
-
Right-click the shortcut for the ASDM-IDM Launcher, and choose Properties.
-
Click the Shortcut tab.
-
In the Target field, change the argument prefixed with -Xmx in order to specify your desired heap size. For example, change it to -Xmx768m for 768 MB or -Xmx1g for 1 GB. For more information about this parameter, refer to the Xmx topic in this Oracle document
.
Note: This solution applies only to Windows PCs.
Problem: Error received when accessing the IPS functionality tab in ASDM 6.2
After the upgrade to Java 1.6.0_18, ASDM 6.2 generates this error:
Your current Java memory heap size is less than 512 MB. You must increase the Java memory heap size before accessing IPS functionality
Solution
In order to resolve this issue, you need to increase the memory specification to 512 MB:
-
Use the ASDM launcher on Windows:
For ASDM versions lesser then/equal to 6.2 — Right-click the ASDM launcher icon on the desktop and change the target string value from -Xmx256m to -Xmx512m.
For ASDM versions greater than 6.2 — Go to file C:Program FilesCisco SystemsASDMasdm-launcher.config and update string -Xmx256m to -Xmx512m.
-
Use the Run ASDM option on Windows/Linux:
When the Run ASDM option is selected, you will receive an option to download the asdm.jnlp file or bring up the ASDM using Java webstart. After you download the asdm.jnlp file, edit it in order to change the «max-heap-size» value from 256m to 512m. Then, bring up the asdm.jnlp file with Java webstart in order to bring up ASDM.
Refer to Cisco bug ID CSCtf21045 (registered customers only) for more information.
Related Information
- Cisco Adaptive Security Device Manager Product Support
- Cisco ASA 5500 Series Adaptive Security Appliances Product Support
- Technical Support & Documentation — Cisco Systems

Main
Оценка: 98.13% — 8 Голосов
Общая
Проблема с подключением к Cisco ASA через Java апплет ASDM.
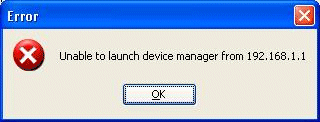
При попытке подключения к Cisco ASA через ASDM появляется ошибка Unable to launch Device Manager.
Чтобы исправить открываем файл java.security находящийся в каталоге C:Program Files (x86)Javajre1.8.0_291libsecurity, находим строку jdk.tls.disabledAlgorithms и удаляем из нее значение TLSv1.
- Просмотров: 3848
|
|
Страница 1 из 1 | [ Сообщений: 7 ] |
Unable to launch device manager
| Автор | Сообщение |
|---|---|
|
Зарегистрирован: 11 мар 2013, 07:25 |
Добрый день! asa 5505 выдает ошибку Unable to launch device manager при попытке подключится через ASDM конфиг: Код: ciscoasa# sh run dhcpd auto_config outside версия явы 6u7 |
| 11 мар 2013, 07:32 |
|
|
aliotru Зарегистрирован: 01 янв 1970, 03:00 |
К такой штуке мне удалось подключиться только с 6 явой. Если не удается запустить через установленный ASDM, то через браузер можно установить новый, который будет использовать только 6 яву |
| 11 мар 2013, 08:05 |
|
|
termitorennet Зарегистрирован: 11 мар 2013, 07:25 |
так он и через браузер не заходит и еше на саму циску пинги не доходят и с циски на клиент (комп) |
| 11 мар 2013, 08:32 |
|
|
aliotru Зарегистрирован: 01 янв 1970, 03:00 |
А комп точно получает IP?? |
| 11 мар 2013, 09:26 |
|
|
termitorennet Зарегистрирован: 11 мар 2013, 07:25 |
комп получает по дцхп |
| 11 мар 2013, 10:21 |
|
|
Cadet Зарегистрирован: 14 мар 2012, 15:48 |
только explorer у меня дает подключить |
| 11 мар 2013, 20:38 |
|
|
babaluba Зарегистрирован: 05 янв 2014, 15:22 |
Надо посмотреть свойство ярлыка запуска ASMD, поменять путь на 6 яву.Вместо WindowsSystem32javaw.exe — Program Files (x86)Javajre6binjavaw.exe». |
| 05 янв 2014, 15:27 |
|
| Показать сообщения за: Поле сортировки |
|
|
Страница 1 из 1 | [ Сообщений: 7 ] |
You have a Cisco ASDM launcher and your launcher does not start anymore with JRE 7, JRE 8, JRE 9, JRE 10, JRE 11, JRE 12+. You get the error:
Probably this issue came from an Java Update.
- Identify the error
- What is the root cause?
- How to fix it?
- Modify the existing JRE for your Cisco ASDM
- Prepare a dedicated JRE only for Cisco ASDM (hard way, but more secure)
1. Identify the error
To identify which error you have, you need to open the java console
If you find something similar to this error (exception), your java security configuration is the issue of this error:
Local Launcher Version = 1.5.55
Local Launcher Version Display = 1.5(55)
OK button clicked
Trying for ASDM Version file; url = https://111.111.111.111/admin/
javax.net.ssl.SSLHandshakeException: Received fatal alert: handshake_failure
at sun.security.ssl.Alerts.getSSLException(Unknown Source)
at sun.security.ssl.Alerts.getSSLException(Unknown Source)
at sun.security.ssl.SSLSocketImpl.recvAlert(Unknown Source)
at sun.security.ssl.SSLSocketImpl.readRecord(Unknown Source)
at sun.security.ssl.SSLSocketImpl.performInitialHandshake(Unknown Source)
at sun.security.ssl.SSLSocketImpl.startHandshake(Unknown Source)
at sun.security.ssl.SSLSocketImpl.startHandshake(Unknown Source)
at sun.net.www.protocol.https.HttpsClient.afterConnect(Unknown Source)
at sun.net.www.protocol.https.AbstractDelegateHttpsURLConnection.connect(Unknown Source)
at sun.net.www.protocol.https.HttpsURLConnectionImpl.connect(Unknown Source)
at com.cisco.launcher.y.a(Unknown Source)
at com.cisco.launcher.y.if(Unknown Source)
at com.cisco.launcher.r.a(Unknown Source)
at com.cisco.launcher.s.do(Unknown Source)
at com.cisco.launcher.s.null(Unknown Source)
at com.cisco.launcher.s.new(Unknown Source)
at com.cisco.launcher.s.access$000(Unknown Source)
at com.cisco.launcher.s$2.a(Unknown Source)
at com.cisco.launcher.g$2.run(Unknown Source)
at java.lang.Thread.run(Unknown Source)
Trying for IDM. url=https://111.111.111.111/idm/idm.jnlp/
javax.net.ssl.SSLHandshakeException: Received fatal alert: handshake_failure
at sun.security.ssl.Alerts.getSSLException(Unknown Source)
at sun.security.ssl.Alerts.getSSLException(Unknown Source)
at sun.security.ssl.SSLSocketImpl.recvAlert(Unknown Source)
at sun.security.ssl.SSLSocketImpl.readRecord(Unknown Source)
at sun.security.ssl.SSLSocketImpl.performInitialHandshake(Unknown Source)
at sun.security.ssl.SSLSocketImpl.startHandshake(Unknown Source)
at sun.security.ssl.SSLSocketImpl.startHandshake(Unknown Source)
at sun.net.www.protocol.https.HttpsClient.afterConnect(Unknown Source)
at sun.net.www.protocol.https.AbstractDelegateHttpsURLConnection.connect(Unknown Source)
at sun.net.www.protocol.http.HttpURLConnection.getInputStream0(Unknown Source)
at sun.net.www.protocol.http.HttpURLConnection.getInputStream(Unknown Source)
at sun.net.www.protocol.https.HttpsURLConnectionImpl.getInputStream(Unknown Source)
at com.cisco.launcher.w.a(Unknown Source)
at com.cisco.launcher.s.for(Unknown Source)
at com.cisco.launcher.s.new(Unknown Source)
at com.cisco.launcher.s.access$000(Unknown Source)
at com.cisco.launcher.s$2.a(Unknown Source)
at com.cisco.launcher.g$2.run(Unknown Source)
at java.lang.Thread.run(Unknown Source)
2. What is the root cause?
Oracle has disabled any well known unsafe and unsecure cipher and algorithm. You can re-enable this again, but sadly you have to enable it fully for the complete installation of Java. This means you have to enable unsecure protocols for any java application. Typically it is no issue, but could be in some security relevant environments.
3. How to fix it?
Best way would be to upgrade your Firewall to later Software version. Sometimes this is not possible. In this case you have to stick to the outdated Cisco Software, and you have to find a solution locally in Java.
3.1. Modify the existing JRE for your Cisco ASDM
find out your active java version by typing in your command line
java -version
Now go to your JRE version specific folder, which is typically under
Windows: C:Program FilesJavajre
Ubuntu: /usr/lib/jvm/
Find the file
java.security
and open it in your prefered editor (open the editor as administrator or with sudo)
Now find the section which contains this:
jdk.tls.disabledAlgorithms=SSLv3, RC4, DES, MD5withRSA, DH keySize < 1024,
EC keySize < 224, 3DES_EDE_CBC, anon, NULL
and change it to
#jdk.tls.disabledAlgorithms=SSLv3, RC4, DES, MD5withRSA, DH keySize < 1024,
# EC keySize < 224, 3DES_EDE_CBC, anon, NULL
jdk.tls.disabledAlgorithms=SSLv3, RC4, DES, MD5withRSA, DH keySize < 1024,
EC keySize < 224, anon, NULL
restart your ASDM and the issue shall be gone
If the issue still persists connect with your browser to the ASDM (https://<yourFirewall>) in the above example it was
https://111.111.111.111
and open in the Browser the SSL details of your connection
<screenshot>
3.2. Prepare a dedicated JRE only for Cisco ASDM (hard way, but more secure)
In this variant you clone a JRE to a different folder and you only use this JRE for the ASDM. This is the most secure way for all other application, since you limit the bad unsecure protocols to Cisco ASDM only.
To achieve this, copy your existing JRE to a special location, and create a script which sets JAVA_HOME and PATH to run java from this new folder.
<to be written>
After updating Cisco ASA 5505 to software version 9.2(4) and ASDM 7.6(2)150 I found myself unable to manage it using ASDM.

Looking at the application logging I see that it’s failing with the following trace:
javax.net.ssl.SSLHandshakeException: Received fatal alert: handshake_failure at sun.security.ssl.Alerts.getSSLException(Alerts.java:192) at sun.security.ssl.Alerts.getSSLException(Alerts.java:154) at sun.security.ssl.SSLSocketImpl.recvAlert(SSLSocketImpl.java:2023) at sun.security.ssl.SSLSocketImpl.readRecord(SSLSocketImpl.java:1125) at sun.security.ssl.SSLSocketImpl.performInitialHandshake(SSLSocketImpl.java:1375) at sun.security.ssl.SSLSocketImpl.startHandshake(SSLSocketImpl.java:1403) at sun.security.ssl.SSLSocketImpl.startHandshake(SSLSocketImpl.java:1387) at sun.net.www.protocol.https.HttpsClient.afterConnect(HttpsClient.java:559) ...
So, it’s not liking the self signed SSL certificate anymore, fair enough, that’s just been laziness on my part, so lets get a proper cert from the CA.
I try to generate the csr on the ASA:
crypto ca enroll SSL-Trustpoint
My CA did not like the csr as it was SHA-1, and my CA will only issue SHA-256 leafs. This should have been a good hint as to why I wasn’t able to establish a trusted connection later.
I then generate my own csr using OpenSSL and got myself a SHA-256 signature algorithm certificate. The following article was helpful in getting the certificate installed:
http://www.cisco.com/c/en/us/support/docs/security-vpn/public-key-infrastructure-pki/200339-Configure-ASA-SSL-Digital-Certificate-I.html
With the certificate configured I still weren’t able to connect. The error message remained the same. This is strange as the certificate is now trusted and both Chrome and Safari are no longer showing any warnings when accessing the hostname.
I then turned to TLSTool to inspect the connection to the ASA, since the Java application is still claiming it’s unable to establish a secure connection:
* protocol: TLS 1.0 * cipher: RSA_WITH_AES_256_CBC_SHA
That tells us it’s a TLS 1.0 using the RSA_WITH_AES_256_CBC_SHA cipher. After some pondering I figure I should check which ciphers my installed JRE supports.
This was easier said than done, but I found the getEnabledCipherSuites method in the SSLSocket class, which is documented here: https://docs.oracle.com/javase/8/docs/api/javax/net/ssl/SSLSocket.html
I then wrote a small java application to list the enabled cipher suite:
import java.io.IOException;
import javax.net.ssl.SSLServerSocket;
import javax.net.ssl.SSLServerSocketFactory;
public class Test {
public static void main(String[] args) {
SSLServerSocketFactory ssl;
SSLServerSocket sslServerSocket = null;
ssl = (SSLServerSocketFactory) SSLServerSocketFactory.getDefault();
try {
sslServerSocket = (SSLServerSocket) ssl.createServerSocket();
} catch (IOException e) {
// TODO Auto-generated catch block
e.printStackTrace();
}
String[] cipherSuites = sslServerSocket.getEnabledCipherSuites();
for (String suite : cipherSuites) {
System.out.println(suite);
}
}
}
The above code printed the following cipher suites on my machine with Java 8 installed:
$ java Ciphers TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 TLS_RSA_WITH_AES_128_CBC_SHA256 TLS_ECDH_ECDSA_WITH_AES_128_CBC_SHA256 TLS_ECDH_RSA_WITH_AES_128_CBC_SHA256 TLS_DHE_RSA_WITH_AES_128_CBC_SHA256 TLS_DHE_DSS_WITH_AES_128_CBC_SHA256 TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA TLS_RSA_WITH_AES_128_CBC_SHA TLS_ECDH_ECDSA_WITH_AES_128_CBC_SHA TLS_ECDH_RSA_WITH_AES_128_CBC_SHA TLS_DHE_RSA_WITH_AES_128_CBC_SHA TLS_DHE_DSS_WITH_AES_128_CBC_SHA TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256 TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 TLS_RSA_WITH_AES_128_GCM_SHA256 TLS_ECDH_ECDSA_WITH_AES_128_GCM_SHA256 TLS_ECDH_RSA_WITH_AES_128_GCM_SHA256 TLS_DHE_RSA_WITH_AES_128_GCM_SHA256 TLS_DHE_DSS_WITH_AES_128_GCM_SHA256 TLS_ECDHE_ECDSA_WITH_3DES_EDE_CBC_SHA TLS_ECDHE_RSA_WITH_3DES_EDE_CBC_SHA SSL_RSA_WITH_3DES_EDE_CBC_SHA TLS_ECDH_ECDSA_WITH_3DES_EDE_CBC_SHA TLS_ECDH_RSA_WITH_3DES_EDE_CBC_SHA SSL_DHE_RSA_WITH_3DES_EDE_CBC_SHA SSL_DHE_DSS_WITH_3DES_EDE_CBC_SHA TLS_EMPTY_RENEGOTIATION_INFO_SCSV
Hmm, the list does not have any AES_256 ciphers in it? That is strange…
A couple of web searches later I found out that Oracle doesn’t ship with these ciphers and you will have to download and install the Java Cryptography Extension (JCE) Unlimited Strength Jurisdiction Policy Files for your version of Java.
They can be found here for Java 8:
http://www.oracle.com/technetwork/java/javase/downloads/jce8-download-2133166.html
According to the README these should go in the $JAVAHome/lib/security folder, so I naturally chucked them into:
/Library/Java/JavaVirtualMachines/jdk1.8.0_112.jdk/Contents/Home/jre/lib/security
Running my Java application again I now the following ciphers:
$ java Ciphers TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 TLS_RSA_WITH_AES_256_CBC_SHA256 TLS_ECDH_ECDSA_WITH_AES_256_CBC_SHA384 TLS_ECDH_RSA_WITH_AES_256_CBC_SHA384 TLS_DHE_RSA_WITH_AES_256_CBC_SHA256 TLS_DHE_DSS_WITH_AES_256_CBC_SHA256 TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA TLS_RSA_WITH_AES_256_CBC_SHA TLS_ECDH_ECDSA_WITH_AES_256_CBC_SHA TLS_ECDH_RSA_WITH_AES_256_CBC_SHA TLS_DHE_RSA_WITH_AES_256_CBC_SHA TLS_DHE_DSS_WITH_AES_256_CBC_SHA TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 TLS_RSA_WITH_AES_128_CBC_SHA256 TLS_ECDH_ECDSA_WITH_AES_128_CBC_SHA256 TLS_ECDH_RSA_WITH_AES_128_CBC_SHA256 TLS_DHE_RSA_WITH_AES_128_CBC_SHA256 TLS_DHE_DSS_WITH_AES_128_CBC_SHA256 TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA TLS_RSA_WITH_AES_128_CBC_SHA TLS_ECDH_ECDSA_WITH_AES_128_CBC_SHA TLS_ECDH_RSA_WITH_AES_128_CBC_SHA TLS_DHE_RSA_WITH_AES_128_CBC_SHA TLS_DHE_DSS_WITH_AES_128_CBC_SHA TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384 TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256 TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 TLS_RSA_WITH_AES_256_GCM_SHA384 TLS_ECDH_ECDSA_WITH_AES_256_GCM_SHA384 TLS_ECDH_RSA_WITH_AES_256_GCM_SHA384 TLS_DHE_RSA_WITH_AES_256_GCM_SHA384 TLS_DHE_DSS_WITH_AES_256_GCM_SHA384 TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 TLS_RSA_WITH_AES_128_GCM_SHA256 TLS_ECDH_ECDSA_WITH_AES_128_GCM_SHA256 TLS_ECDH_RSA_WITH_AES_128_GCM_SHA256 TLS_DHE_RSA_WITH_AES_128_GCM_SHA256 TLS_DHE_DSS_WITH_AES_128_GCM_SHA256 TLS_ECDHE_ECDSA_WITH_3DES_EDE_CBC_SHA TLS_ECDHE_RSA_WITH_3DES_EDE_CBC_SHA SSL_RSA_WITH_3DES_EDE_CBC_SHA TLS_ECDH_ECDSA_WITH_3DES_EDE_CBC_SHA TLS_ECDH_RSA_WITH_3DES_EDE_CBC_SHA SSL_DHE_RSA_WITH_3DES_EDE_CBC_SHA SSL_DHE_DSS_WITH_3DES_EDE_CBC_SHA TLS_EMPTY_RENEGOTIATION_INFO_SCSV
Progress at last! The required cipher is now listed, but it still doesn’t work. It turns out I got the wrong JavaHome. The ASDM application is using the JavaAppletPlugin.plugin. I found out by looking at how the ASDM application was being launched and it had the following check at the top of the launcher script:
if [ -x "/Library/Internet Plug-Ins/JavaAppletPlugin.plugin/Contents/Home/bin/java" ]; then jrehome="/Library/Internet Plug-Ins/JavaAppletPlugin.plugin/Contents/Home" ...
I then copied the jar files into the lib/security folder:
/Library/Internet Plug-Ins/JavaAppletPlugin.plugin/Contents/Home/lib/security
And finally! ASDM launched successfully!
Since there was a lot of people asking the same questions, but no complete answer anywhere I wrote this up. I hope it helps someone else, I sure would have appreciated finding a similar writeup somewhere.
9 Replies
-
Thanks Rob, just developed this issue recently as well — I should have been able to guess, in the past we had to use those unlimited JCEs for CSOS ordering with our pharmaceutical vendor.
Was this post helpful?
thumb_up
thumb_down
-
Thank you sir. You have done a great service to anyone that has to struggle with this, now or in the future.
I simply won’t update Java unless I absolutely have to because whenever you do it invariably breaks something. It seems Java may have been a good idea that was almost always very poorly implemented.
The only really good program I have ever seen developed in Java is Interactive Broker’s Trader Workstation (TWS). It is perhaps the most extensive, complex and excellent example of what Java could have been and it always works well because they totally ignore the JRE and embed their own JRE with it to prevent any incompatibility problems in advance. Cisco’s ADSM is impressive for what it does and it’s amazing how well it can work when you can get it to run but it is likely 1/500th the size of TWS.
Was this post helpful?
thumb_up
thumb_down
-
dbeato
This person is a verified professional.
Verify your account
to enable IT peers to see that you are a professional.pure capsaicin
Thanks!! I have only one Cisco 5505 which this will help, although I have not had an issue yet.
Was this post helpful?
thumb_up
thumb_down
-
Why do vendors of security software and management software for security product use Java anyway, that really gets my goat…
Was this post helpful?
thumb_up
thumb_down
-
dbeato
This person is a verified professional.
Verify your account
to enable IT peers to see that you are a professional.pure capsaicin
brianwhelton wrote:
Why do vendors of security software and management software for security product use Java anyway, that really gets my goat…
Specifically Dell and Cisco
Was this post helpful?
thumb_up
thumb_down
-
brianwhelton wrote: Why do vendors of security software and management software for security product use Java anyway, that really gets my goat…
Java was designed to be über secure; but in reality it was implemented very poorly. Both phones on President Trump’s desk in the Oval Office (I really haven’t figured out why he needs two plus two cell phones for Twitter) run Java and the three phones on Admiral Michael S. Rogers desk (Director of the National Security Agency), I really haven’t figured out why he needs three, all run Java.
Was this post helpful?
thumb_up
thumb_down
-
To answer the multitude of phones, you’ll probably find they are either running different crypto (to speak to remote agencies) or are different classifications. But yes, Jave is never implemented corrected and the worst thing with Cisco is that unless you use the exact version of Java, which is normally really old and vulnerable, Cisco software fails.
Was this post helpful?
thumb_up
thumb_down
-
I have had this issue for years using models 5505, 5510, 5512x and 5516x. Here’s what I now use that seems to ignore the version of Java I’m running on the PC. I’m not a code guy, so don’t ask me what all this does, but I started using this file from the web installer of ASDM and I adjust the IPs for individual ASAs.
Copy the text below and paste into a .txt file. Replace any references to the word IPADDRESS with the IP address of your ASA. Then change the file extension to .jnlp. Works like a charm now regardless of Java version. I’m currently able to use this just fine using Java 8 Update 131 and I did not have to do anything to this file after upgrading to this latest version of Java. #JavaBlows
<?xml version=»1.0″ encoding=»utf-8″?>
<jnlp spec=»1.0+» codebase=»https://IPADDRESS/admin/public» Opens a new window; href=»https://IPADDRESS/admin/public/asdm.jnlp»> Opens a new window;
<information>
<title>ASDM on IPADDRESS</title>
<vendor>Cisco Systems, Inc.</vendor>
<homepage href=»http://www.cisco.com/go/asdm»/> Opens a new window;
<description>ASDM on IPADDRESS</description>
<description kind=»short»>ASDM on IPADDRESS</description>
<description kind=»tooltip»>ASDM on IPADDRESS</description>
<icon href=»asdm32.gif»/>
<offline-allowed/>
<shortcut>
<desktop/>
<menu submenu=»Cisco ASDM»/>
</shortcut>
</information><security>
<all-permissions/>
</security><resources>
<j2se version=»1.6+» java-vm-args=»-Xms64m -Xmx512m»/>
<jar href=»dm-launcher.jar» main=»true» download=»eager»/>
<jar href=»lzma.jar» download=»eager»/>
<jar href=»jploader.jar» download=»eager»/>
<jar href=»retroweaver-rt-2.0.jar» download=»eager»/>
<property name=»java.util.Arrays.useLegacyMergeSort» value=»true»/>
<property name=»http.agent» value=»ASDM/»/>
</resources><application-desc main-class=»com.cisco.launcher.Launcher»>
<argument>/webstart</argument>
<argument>IPADDRESS</argument>
</application-desc></jnlp>
Was this post helpful?
thumb_up
thumb_down
-
Mr. Liquid Bread,
The first beer (or 2…or 10) is on me. I no longer have Java induced bouts of depression and Java induced suicidal tendencies. I have deployed your jnlp file everywhere. This should be EVERYWHERE!!!!
You are ‘DA MAN’!!!!!!
Was this post helpful?
thumb_up
thumb_down