I finally found the answer (I haven’t noted my source but it was from a search);
While the code works in Windows XP, in Windows 7, you must add this at the beginning:
// using System.Net;
ServicePointManager.Expect100Continue = true;
ServicePointManager.SecurityProtocol = SecurityProtocolType.Tls12;
// Use SecurityProtocolType.Ssl3 if needed for compatibility reasons
And now, it works perfectly.
ADDENDUM
As mentioned by Robin French; if you are getting this problem while configuring PayPal, please note that they won’t support SSL3 starting by December, 3rd 2018. You’ll need to use TLS. Here’s Paypal page about it.
answered May 25, 2010 at 13:18
Simon DugréSimon Dugré
17.5k11 gold badges55 silver badges73 bronze badges
24
The solution to this, in .NET 4.5 is
ServicePointManager.SecurityProtocol = SecurityProtocolType.Tls12;
If you don’t have .NET 4.5 then use
ServicePointManager.SecurityProtocol = (SecurityProtocolType)3072;
answered Feb 22, 2018 at 14:46
4
Make sure the ServicePointManager settings are made before the HttpWebRequest is created, else it will not work.
Works:
ServicePointManager.Expect100Continue = true;
ServicePointManager.SecurityProtocol = SecurityProtocolType.Tls
| SecurityProtocolType.Tls11
| SecurityProtocolType.Tls12
| SecurityProtocolType.Ssl3;
HttpWebRequest request = (HttpWebRequest)WebRequest.Create("https://google.com/api/")
Fails:
HttpWebRequest request = (HttpWebRequest)WebRequest.Create("https://google.com/api/")
ServicePointManager.Expect100Continue = true;
ServicePointManager.SecurityProtocol = SecurityProtocolType.Tls
| SecurityProtocolType.Tls11
| SecurityProtocolType.Tls12
| SecurityProtocolType.Ssl3;
soccer7
3,2213 gold badges28 silver badges49 bronze badges
answered Jun 21, 2018 at 21:39
hogarth45hogarth45
3,2471 gold badge22 silver badges27 bronze badges
8
Note: Several of the highest voted answers here advise setting ServicePointManager.SecurityProtocol, but Microsoft explicitly advises against doing that. Below, I go into the typical cause of this issue and the best practices for resolving it.
One of the biggest causes of this issue is the active .NET Framework version. The .NET framework runtime version affects which security protocols are enabled by default.
- In ASP.NET sites, the framework runtime version is often specified in web.config. (see below)
- In other apps, the runtime version is usually the version for which the project was built, regardless of whether it is running on a machine with a newer .NET version.
There doesn’t seem to be any authoritative documentation on how it specifically works in different versions, but it seems the defaults are determined more or less as follows:
| Framework Version | Default Protocols |
|---|---|
| 4.5 and earlier | SSL 3.0, TLS 1.0 |
| 4.6.x | TLS 1.0, 1.1, 1.2, 1.3 |
| 4.7+ | System (OS) Defaults |
For the older versions, your mileage may vary somewhat based on which .NET runtimes are installed on the system. For example, there could be a situation where you are using a very old framework and TLS 1.0 is not supported, or using 4.6.x and TLS 1.3 is not supported.
Microsoft’s documentation strongly advises using 4.7+ and the system defaults:
We recommend that you:
- Target .NET Framework 4.7 or later versions on your apps. Target .NET Framework 4.7.1 or later versions on your WCF apps.
- Do not specify the TLS version. Configure your code to let the OS decide on the TLS version.
- Perform a thorough code audit to verify you’re not specifying a TLS or SSL version.
For ASP.NET sites: check the targetFramework version in your <httpRuntime> element, as this (when present) determines which runtime is actually used by your site:
<httpRuntime targetFramework="4.5" />
Better:
<httpRuntime targetFramework="4.7" />
answered Oct 2, 2019 at 6:02
JLRisheJLRishe
98k19 gold badges130 silver badges166 bronze badges
5
I had this problem trying to hit https://ct.mob0.com/Styles/Fun.png, which is an image distributed by CloudFlare on its CDN that supports crazy stuff like SPDY and weird redirect SSL certs.
Instead of specifying Ssl3 as in Simons answer I was able to fix it by going down to Tls12 like this:
ServicePointManager.SecurityProtocol = SecurityProtocolType.Tls12;
new WebClient().DownloadData("https://ct.mob0.com/Styles/Fun.png");
InteXX
5,8956 gold badges40 silver badges73 bronze badges
answered Oct 15, 2014 at 17:42
Bryan LegendBryan Legend
6,7221 gold badge59 silver badges60 bronze badges
3
After many long hours with this same issue I found that the ASP.NET account the client service was running under didn’t have access to the certificate. I fixed it by going into the IIS Application Pool that the web app runs under, going into Advanced Settings, and changing the Identity to the LocalSystem account from NetworkService.
A better solution is to get the certificate working with the default NetworkService account but this works for quick functional testing.
answered Dec 4, 2014 at 16:31
Nick GotchNick Gotch
9,11914 gold badges70 silver badges95 bronze badges
3
The error is generic and there are many reasons why the SSL/TLS negotiation may fail. The most common is an invalid or expired server certificate, and you took care of that by providing your own server certificate validation hook, but is not necessarily the only reason. The server may require mutual authentication, it may be configured with a suites of ciphers not supported by your client, it may have a time drift too big for the handshake to succeed and many more reasons.
The best solution is to use the SChannel troubleshooting tools set. SChannel is the SSPI provider responsible for SSL and TLS and your client will use it for the handshake. Take a look at TLS/SSL Tools and Settings.
Also see How to enable Schannel event logging.
answered May 18, 2010 at 18:14
Remus RusanuRemus Rusanu
285k40 gold badges429 silver badges564 bronze badges
3
The approach with setting
ServicePointManager.SecurityProtocol = SecurityProtocolType.Tls12
Seems to be okay, because Tls1.2 is latest version of secure protocol. But I decided to look deeper and answer do we really need to hardcode it.
Specs: Windows Server 2012R2 x64.
From the internet there is told that .NetFramework 4.6+ must use Tls1.2 by default. But when I updated my project to 4.6 nothing happened.
I have found some info that tells I need manually do some changes to enable Tls1.2 by default
https://support.microsoft.com/en-in/help/3140245/update-to-enable-tls-1-1-and-tls-1-2-as-default-secure-protocols-in-wi
But proposed windows update doesnt work for R2 version
But what helped me is adding 2 values to registry. You can use next PS script so they will be added automatically
Set-ItemProperty -Path 'HKLM:SOFTWAREWow6432NodeMicrosoft.NetFrameworkv4.0.30319' -Name 'SchUseStrongCrypto' -Value '1' -Type DWord
Set-ItemProperty -Path 'HKLM:SOFTWAREMicrosoft.NetFrameworkv4.0.30319' -Name 'SchUseStrongCrypto' -Value '1' -Type DWord
That is kind of what I was looking for. But still I cant answer on question why NetFramework 4.6+ doesn’t set this …Protocol value automatically?
answered Oct 28, 2019 at 20:58
simply goodsimply good
9211 gold badge12 silver badges25 bronze badges
5
Another possible cause of the The request was aborted: Could not create SSL/TLS secure channel error is a mismatch between your client PC’s configured cipher_suites values, and the values that the server is configured as being willing and able to accept. In this case, when your client sends the list of cipher_suites values that it is able to accept in its initial SSL handshaking/negotiation «Client Hello» message, the server sees that none of the provided values are acceptable, and may return an «Alert» response instead of proceeding to the «Server Hello» step of the SSL handshake.
To investigate this possibility, you can download Microsoft Message Analyzer, and use it to run a trace on the SSL negotiation that occurs when you try and fail to establish an HTTPS connection to the server (in your C# app).
If you are able to make a successful HTTPS connection from another environment (e.g. the Windows XP machine that you mentioned — or possibly by hitting the HTTPS URL in a non-Microsoft browser that doesn’t use the OS’s cipher suite settings, such as Chrome or Firefox), run another Message Analyzer trace in that environment to capture what happens when the SSL negotiation succeeds.
Hopefully, you’ll see some difference between the two Client Hello messages that will allow you to pinpoint exactly what about the failing SSL negotiation is causing it to fail. Then you should be able to make configuration changes to Windows that will allow it to succeed. IISCrypto is a great tool to use for this (even for client PCs, despite the «IIS» name).
The following two Windows registry keys govern the cipher_suites values that your PC will use:
- HKLMSOFTWAREPoliciesMicrosoftCryptographyConfigurationSSL0010002
- HKLMSYSTEMCurrentControlSetControlCryptographyConfigurationLocalSSL0010002
Here’s a full writeup of how I investigated and solved an instance of this variety of the Could not create SSL/TLS secure channel problem: http://blog.jonschneider.com/2016/08/fix-ssl-handshaking-error-in-windows.html
answered Aug 31, 2016 at 4:33
Jon SchneiderJon Schneider
24.9k21 gold badges144 silver badges167 bronze badges
3
Something the original answer didn’t have. I added some more code to make it bullet proof.
ServicePointManager.Expect100Continue = true;
ServicePointManager.DefaultConnectionLimit = 9999;
ServicePointManager.SecurityProtocol = SecurityProtocolType.Tls | SecurityProtocolType.Tls11 | SecurityProtocolType.Tls12 | SecurityProtocolType.Ssl3;
answered Jun 1, 2016 at 15:05
SpoiledTechie.comSpoiledTechie.com
10.4k20 gold badges77 silver badges99 bronze badges
5
The top-voted answer will probably be enough for most people. However, in some circumstances, you could continue getting a «Could not create SSL/TLS secure channel» error even after forcing TLS 1.2. If so, you may want to consult this helpful article for additional troubleshooting steps. To summarize: independent of the TLS/SSL version issue, the client and server must agree on a «cipher suite.» During the «handshake» phase of the SSL connection, the client will list its supported cipher-suites for the server to check against its own list. But on some Windows machines, certain common cipher-suites may have been disabled (seemingly due to well-intentioned attempts to limit attack surface), decreasing the possibility of the client & server agreeing on a cipher suite. If they cannot agree, then you may see «fatal alert code 40» in the event viewer and «Could not create SSL/TLS secure channel» in your .NET program.
The aforementioned article explains how to list all of a machine’s potentially-supported cipher suites and enable additional cipher suites through the Windows Registry. To help check which cipher suites are enabled on the client, try visiting this diagnostic page in MSIE. (Using System.Net tracing may give more definitive results.) To check which cipher suites are supported by the server, try this online tool (assuming that the server is Internet-accessible). It should go without saying that Registry edits must be done with caution, especially where networking is involved. (Is your machine a remote-hosted VM? If you were to break networking, would the VM be accessible at all?)
In my company’s case, we enabled several additional «ECDHE_ECDSA» suites via Registry edit, to fix an immediate problem and guard against future problems. But if you cannot (or will not) edit the Registry, then numerous workarounds (not necessarily pretty) come to mind. For example: your .NET program could delegate its SSL traffic to a separate Python program (which may itself work, for the same reason that Chrome requests may succeed where MSIE requests fail on an affected machine).
answered Jun 1, 2019 at 6:16
APWAPW
3544 silver badges6 bronze badges
1
This one is working for me in MVC webclient
public string DownloadSite(string RefinedLink)
{
try
{
Uri address = new Uri(RefinedLink);
ServicePointManager.ServerCertificateValidationCallback = delegate { return true; };
ServicePointManager.SecurityProtocol = SecurityProtocolType.Ssl3;
System.Net.ServicePointManager.SecurityProtocol = SecurityProtocolType.Tls11 | SecurityProtocolType.Tls12;
using (WebClient webClient = new WebClient())
{
var stream = webClient.OpenRead(address);
using (StreamReader sr = new StreamReader(stream))
{
var page = sr.ReadToEnd();
return page;
}
}
}
catch (Exception e)
{
log.Error("DownloadSite - error Lin = " + RefinedLink, e);
return null;
}
}
soccer7
3,2213 gold badges28 silver badges49 bronze badges
answered Oct 4, 2017 at 7:14
Arun Prasad E SArun Prasad E S
9,1338 gold badges73 silver badges84 bronze badges
3
«The request was aborted: Could not create SSL/TLS secure channel» exception can occur if the server is returning an HTTP 401 Unauthorized response to the HTTP request.
You can determine if this is happening by turning on trace-level System.Net logging for your client application, as described in this answer.
Once that logging configuration is in place, run the application and reproduce the error, then look in the logging output for a line like this:
System.Net Information: 0 : [9840] Connection#62912200 - Received status line: Version=1.1, StatusCode=401, StatusDescription=Unauthorized.
In my situation, I was failing to set a particular cookie that the server was expecting, leading to the server responding to the request with the 401 error, which in turn led to the «Could not create SSL/TLS secure channel» exception.
answered Aug 19, 2014 at 19:55
Jon SchneiderJon Schneider
24.9k21 gold badges144 silver badges167 bronze badges
1
Another possibility is improper certificate importation on the box. Make sure to select encircled check box. Initially I didn’t do it, so code was either timing out or throwing same exception as private key could not be located.
answered Jul 11, 2012 at 22:27
SherlockSherlock
1,0128 silver badges18 bronze badges
1
I had this problem because my web.config had:
<httpRuntime targetFramework="4.5.2" />
and not:
<httpRuntime targetFramework="4.6.1" />
answered Aug 15, 2017 at 10:47
Terje SolemTerje Solem
7661 gold badge9 silver badges25 bronze badges
1
Doing this helped me:
System.Net.ServicePointManager.SecurityProtocol = SecurityProtocolType.Tls12;
answered Jan 26, 2021 at 22:39
Merlyn007Merlyn007
4091 gold badge7 silver badges21 bronze badges
0
Finally found solution for me.
Try this adding below line before calling https url (for .Net framework 4.5):
ServicePointManager.SecurityProtocol = SecurityProtocolType.Tls12;
Luis Teijon
4,6737 gold badges35 silver badges56 bronze badges
answered Jun 16, 2021 at 5:24
0
As you can tell there are plenty of reasons this might happen. Thought I would add the cause I encountered …
If you set the value of WebRequest.Timeout to 0, this is the exception that is thrown. Below is the code I had… (Except instead of a hard-coded 0 for the timeout value, I had a parameter which was inadvertently set to 0).
WebRequest webRequest = WebRequest.Create(@"https://myservice/path");
webRequest.ContentType = "text/html";
webRequest.Method = "POST";
string body = "...";
byte[] bytes = Encoding.ASCII.GetBytes(body);
webRequest.ContentLength = bytes.Length;
var os = webRequest.GetRequestStream();
os.Write(bytes, 0, bytes.Length);
os.Close();
webRequest.Timeout = 0; //setting the timeout to 0 causes the request to fail
WebResponse webResponse = webRequest.GetResponse(); //Exception thrown here ...
answered Apr 25, 2014 at 20:50
TCCTCC
2,5061 gold badge23 silver badges35 bronze badges
1
The root of this exception in my case was that at some point in code the following was being called:
ServicePointManager.SecurityProtocol = SecurityProtocolType.Ssl3;
This is really bad. Not only is it instructing .NET to use an insecure protocol, but this impacts every new WebClient (and similar) request made afterward within your appdomain. (Note that incoming web requests are unaffected in your ASP.NET app, but new WebClient requests, such as to talk to an external web service, are).
In my case, it was not actually needed, so I could just delete the statement and all my other web requests started working fine again. Based on my reading elsewhere, I learned a few things:
- This is a global setting in your appdomain, and if you have concurrent activity, you can’t reliably set it to one value, do your action, and then set it back. Another action may take place during that small window and be impacted.
- The correct setting is to leave it default. This allows .NET to continue to use whatever is the most secure default value as time goes on and you upgrade frameworks. Setting it to TLS12 (which is the most secure as of this writing) will work now but in 5 years may start causing mysterious problems.
- If you really need to set a value, you should consider doing it in a separate specialized application or appdomain and find a way to talk between it and your main pool. Because it’s a single global value, trying to manage it within a busy app pool will only lead to trouble. This answer: https://stackoverflow.com/a/26754917/7656 provides a possible solution by way of a custom proxy. (Note I have not personally implemented it.)
answered Sep 16, 2016 at 23:54
1
In my case, the service account running the application did not have permission to access the private key. Once I gave this permission, the error went away
- mmc
- certificates
- Expand to personal
- select cert
- right click
- All tasks
- Manage private keys
- Add the service account user
answered Nov 13, 2017 at 21:24
Dinesh RajanDinesh Rajan
2,29822 silver badges17 bronze badges
1
If you are running your code from Visual Studio, try running Visual Studio as administrator. Fixed the issue for me.
answered Feb 27, 2018 at 16:59
handleshandles
7,60116 gold badges61 silver badges85 bronze badges
1
System.Net.WebException: The request was aborted: Could not create
SSL/TLS secure channel.
In our case, we where using a software vendor so we didn’t have access to modify the .NET code. Apparently .NET 4 won’t use TLS v 1.2 unless there is a change.
The fix for us was adding the SchUseStrongCrypto key to the registry. You can copy/paste the below code into a text file with the .reg extension and execute it. It served as our «patch» to the problem.
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINESOFTWAREWow6432NodeMicrosoft.NETFrameworkv4.0.30319]
"SchUseStrongCrypto"=dword:00000001
[HKEY_LOCAL_MACHINESOFTWAREMicrosoft.NETFrameworkv4.0.30319]
"SchUseStrongCrypto"=dword:00000001
answered Jul 26, 2018 at 14:35
capdragoncapdragon
14.3k24 gold badges102 silver badges152 bronze badges
3
I have struggled with this problem all day.
When I created a new project with .NET 4.5 I finally got it to work.
But if I downgraded to 4.0 I got the same problem again, and it was irreversable for that project (even when i tried to upgrade to 4.5 again).
Strange no other error message but «The request was aborted: Could not create SSL/TLS secure channel.» came up for this error
answered Dec 2, 2015 at 16:08
aghostaghost
1922 silver badges8 bronze badges
2
In case that the client is a windows machine, a possible reason could be that the tls or ssl protocol required by the service is not activated.
This can be set in:
Control Panel -> Network and Internet -> Internet Options -> Advanced
Scroll settings down to «Security» and choose between
- Use SSL 2.0
- Use SSL 3.0
- Use TLS 1.0
- Use TLS 1.1
- Use TLS 1.2
answered May 10, 2017 at 7:05
cnomcnom
2,8714 gold badges27 silver badges59 bronze badges
4
none of this answer not working for me , the google chrome and postman work and handshake the server but ie and .net not working. in google chrome in security tab > connection show that encrypted and authenticated using ECDHE_RSA with P-256 and AES_256_GCM cipher suite to handshake with the server.
i install IIS Crypto and in cipher suites list on windows server 2012 R2 ican’t find ECDHE_RSA with P-256 and AES_256_GCM cipher suite. then i update windows to the last version but the problem not solve. finally after searches i understood that windows server 2012 R2 not support GSM correctly and update my server to windows server 2016 and my problem solved.
answered May 31, 2020 at 5:46
I was having this same issue and found this answer worked properly for me. The key is 3072. This link provides the details on the ‘3072’ fix.
ServicePointManager.SecurityProtocol = (SecurityProtocolType)3072;
XmlReader r = XmlReader.Create(url);
SyndicationFeed albums = SyndicationFeed.Load(r);
In my case two feeds required the fix:
https://www.fbi.gov/feeds/fbi-in-the-news/atom.xml
https://www.wired.com/feed/category/gear/latest/rss
Stephen Rauch♦
46.7k31 gold badges109 silver badges131 bronze badges
answered May 27, 2018 at 14:02
joeydoodjoeydood
511 silver badge4 bronze badges
1
None of the answers worked for me.
This is what worked:
Instead of initializing my X509Certifiacte2 like this:
var certificate = new X509Certificate2(bytes, pass);
I did it like this:
var certificate = new X509Certificate2(bytes, pass, X509KeyStorageFlags.MachineKeySet | X509KeyStorageFlags.PersistKeySet | X509KeyStorageFlags.Exportable);
Notice the X509KeyStorageFlags.Exportable !!
I didn’t change the rest of the code (the WebRequest itself):
// I'm not even sure the first two lines are necessary:
ServicePointManager.Expect100Continue = true;
ServicePointManager.SecurityProtocol = SecurityProtocolType.Tls12;
request = (HttpWebRequest)WebRequest.Create(string.Format("https://{0}.sii.cl/cvc_cgi/dte/of_solicita_folios", server));
request.Method = "GET";
request.Referer = string.Format("https://hercules.sii.cl/cgi_AUT2000/autInicio.cgi?referencia=https://{0}.sii.cl/cvc_cgi/dte/of_solicita_folios", servidor);
request.UserAgent = "Mozilla/4.0";
request.ClientCertificates.Add(certificate);
request.CookieContainer = new CookieContainer();
using (HttpWebResponse response = (HttpWebResponse)request.GetResponse())
{
// etc...
}
In fact I’m not even sure that the first two lines are necessary…
answered Apr 30, 2019 at 17:58
sportssports
7,67312 gold badges69 silver badges128 bronze badges
2
Another possibility is that the code being executed doesn’t have the required permissions.
In my case, I got this error when using Visual Studio debugger to test a call to a web service. Visual Studio wasn’t running as Administrator, which caused this exception.
answered Oct 30, 2019 at 10:11
OfirDOfirD
7,9673 gold badges43 silver badges78 bronze badges
This fixed for me, add Network Service to permissions.
Right click on the certificate > All Tasks > Manage Private Keys… > Add… > Add «Network Service».
answered Apr 6, 2018 at 6:27
jayasurya_jjayasurya_j
1,4191 gold badge13 silver badges22 bronze badges
1
- Remove From My Forums
-
Question
-
User945338570 posted
Hi ,
I am getting error saying «The request was aborted: Could not create SSL/TLS secure channel» while consuming a third party API in my code. The code works fine when runs on Windows10 or Windows Server 2016 r2 but giving above error on Wndows7 and Windows
Server 2012 R2.WebRequest Code:
var postData = "grant_type=password";
postData += "&xyz=" + ConfigurationManager.AppSettings["scope"] + "";
postData += "&xxx=" + ConfigurationManager.AppSettings["username"] + "";
postData += "&abc=" + ConfigurationManager.AppSettings["password"] + "";
string username = ConfigurationManager.AppSettings["authusername"];
string password = ConfigurationManager.AppSettings["authpassword"];
String encoded = System.Convert.ToBase64String(System.Text.Encoding.GetEncoding("ISO-8859-1").GetBytes(username + ":" + password));
HttpWebRequest request = (HttpWebRequest)WebRequest.Create(apiurl); request.Method = "POST"; byte[] byteArray = Encoding.UTF8.GetBytes(postData); request.ContentLength = byteArray.Length; request.ContentType = @"application/x-www-form-urlencoded"; request.Headers.Add("Authorization", "Basic " + encoded); request.ProtocolVersion = HttpVersion.Version10; using (Stream dataStream = request.GetRequestStream()) { dataStream.Write(byteArray, 0, byteArray.Length); } try { if (detailedLogPrint > 1) strLog += string.Format("{0:hh:mm:ss:fff tt}", DateTime.Now) + $"tAPI execution startingrn"; using (HttpWebResponse response = (HttpWebResponse)request.GetResponse()) { long length = response.ContentLength; using (var reader = new StreamReader(response.GetResponseStream())) { result = reader.ReadToEnd(); finalResult = "Success"; if (detailedLogPrint > 1) { strLog += string.Format("{0:hh:mm:ss:fff tt}", DateTime.Now) + $"tAPI response received : {result}rn"; } } } } catch (WebException ex) { finalResult = "Fail"; using (var stream = ex.Response.GetResponseStream()) using (var reader = new StreamReader(stream)) { string strAPIResponse = reader.ReadToEnd(); strLog += string.Format("{0:hh:mm:ss:fff tt}", DateTime.Now) + $"tWebException : {strAPIResponse}rn"; } } catch (Exception ex) { finalResult = "Fail"; strLog += string.Format("{0:hh:mm:ss:fff tt}", DateTime.Now) + $"tException : {ex.Message}rn"; }Here is my Web.Config Settings:
<?xml version="1.0"?> <!-- For more information on how to configure your ASP.NET application, please visit http://go.microsoft.com/fwlink/?LinkId=301879 --> <configuration> <connectionStrings> <add name="IDGDB" connectionString="Data Source=localhost;initial catalog=mydatabase;user id=sa;password=1234;" providerName="System.Data.SqlClient"/> </connectionStrings> <appSettings> <add key="LogPath" value="C://ReverseAPILogs"/> <add key="PrintDetailedLogs" value="2"/> <add key="oAuthAPIURL" value="https://thirdpartysite.com/oauth/token"/> <add key="authusername" value="bf41ac5b-xxx-xxxx"/> <add key="authpassword" value="********"/> <add key="scope" value="CustomerServicing"/> <add key="username" value="********"/> <add key="password" value="********0"/> <add key="onboardingAPIURL" value="https://thirdpartysite.com/xxx/agenton/v1"/> <add key="X-IBM-Client-Id" value="*********"/> <add key="X-IBM-Client-Secret" value="**************"/> <add key="sourceSystem" value="AMS"/> <add key="sourceOfLead" value="W2R"/> <add key="soaAppId" value="MREC"/> </appSettings> <!-- For a description of web.config changes see http://go.microsoft.com/fwlink/?LinkId=235367. The following attributes can be set on the <httpRuntime> tag. <system.Web> <httpRuntime targetFramework="4.7" /> </system.Web> --> <system.web> <compilation debug="true" targetFramework="4.5"/> <httpRuntime targetFramework="4.5"/> </system.web> <system.webServer> <handlers> <remove name="ExtensionlessUrlHandler-Integrated-4.0"/> <remove name="OPTIONSVerbHandler"/> <remove name="TRACEVerbHandler"/> <add name="ExtensionlessUrlHandler-Integrated-4.0" path="*." verb="*" type="System.Web.Handlers.TransferRequestHandler" preCondition="integratedMode,runtimeVersionv4.0"/> </handlers> </system.webServer> <runtime> <assemblyBinding xmlns="urn:schemas-microsoft-com:asm.v1"> <dependentAssembly> <assemblyIdentity name="System.Web.Helpers" publicKeyToken="31bf3856ad364e35"/> <bindingRedirect oldVersion="1.0.0.0-3.0.0.0" newVersion="3.0.0.0"/> </dependentAssembly> <dependentAssembly> <assemblyIdentity name="System.Web.Mvc" publicKeyToken="31bf3856ad364e35"/> <bindingRedirect oldVersion="1.0.0.0-5.2.3.0" newVersion="5.2.3.0"/> </dependentAssembly> <dependentAssembly> <assemblyIdentity name="System.Web.WebPages" publicKeyToken="31bf3856ad364e35"/> <bindingRedirect oldVersion="1.0.0.0-3.0.0.0" newVersion="3.0.0.0"/> </dependentAssembly> </assemblyBinding> </runtime> <system.codedom> <compilers> <compiler language="c#;cs;csharp" extension=".cs" type="Microsoft.CodeDom.Providers.DotNetCompilerPlatform.CSharpCodeProvider, Microsoft.CodeDom.Providers.DotNetCompilerPlatform, Version=1.0.0.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35" warningLevel="4" compilerOptions="/langversion:6 /nowarn:1659;1699;1701"/> <compiler language="vb;vbs;visualbasic;vbscript" extension=".vb" type="Microsoft.CodeDom.Providers.DotNetCompilerPlatform.VBCodeProvider, Microsoft.CodeDom.Providers.DotNetCompilerPlatform, Version=1.0.0.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35" warningLevel="4" compilerOptions="/langversion:14 /nowarn:41008 /define:_MYTYPE="Web" /optionInfer+"/> </compilers> </system.codedom> </configuration>Please help!
Ситуация:
С недавних пор наши приложения на .net 4.5 в функционал которых, кроме прочего, входит загрузка страниц с сайтов. Перестали работать на серверах Windows Werver 2008 R2 и Windows Server 2012 R2
Ошибка
Не удалось создать защищенный канал ssl/tls
или она же на английском
The request was aborted: Could not create SSL/TLS secure channel
Причем эти же приложения работали нормально на машинах разработчиков на Windows 10.
Разбор ситуации. Что не помогло
Сразу скажу — много форумов читали, много советов перепробовали — нам
не помогли такие действия:
игры с настройкой протокола в приложении
ServicePointManager.ServerCertificateValidationCallback += new RemoteCertificateValidationCallback(AlwaysGoodCertificate);
ServicePointManager.Expect100Continue = true;
ServicePointManager.DefaultConnectionLimit = 9999;
ServicePointManager.SecurityProtocol = SecurityProtocolType.Tls12;
игры с переходом на более свежий фреймворк:
пробовали и .NET 4.6.1 и .NET 4.7.2
Но попробуйте, может у вас другой случай (я думаю, в случае другой конфигурации машины — могут помочь)
Вот советы, которые нам не помогли
Disable SSL fallback and use only TLS for outbound connections in .NET? (Poodle mitigation)
https://stackoverflow.com/questions/26389899/disable-ssl-fallback-and-use-only-tls-for-outbound-connections-in-net-poodle
How to specify SSL protocol to use for WebClient class
https://stackoverflow.com/questions/30491716/how-to-specify-ssl-protocol-to-use-for-webclient-class
.Net WebClient: Could not create SSL/TLS secure channel
https://www.aspsnippets.com/Articles/Net-WebClient-Could-not-create-SSLTLS-secure-channel.aspx
Запрос был прерван: Не удалось создать защищенный канал SSL/TLS
https://answer-id.com/ru/74496884
Запрос был прерван: не удалось создать безопасный канал SSL / TLS
https://qastack.ru/programming/2859790/the-request-was-aborted-could-not-create-ssl-tls-secure-channel
Не удалось создать защищенный канал SSL/TLS только на сервере Windows Server 2012
https://coderoad.ru/59975964/%D0%9D%D0%B5-%D1%83%D0%B4%D0%B0%D0%BB%D0%BE%D1%81%D1%8C-%D1%81%D0%BE%D0%B7%D0%B4%D0%B0%D1%82%D1%8C-%D0%B7%D0%B0%D1%89%D0%B8%D1%89%D0%B5%D0%BD%D0%BD%D1%8B%D0%B9-%D0%BA%D0%B0%D0%BD%D0%B0%D0%BB-SSL-TLS-%D1%82%D0%BE%D0%BB%D1%8C%D0%BA%D0%BE-%D0%BD%D0%B0-%D1%81%D0%B5%D1%80%D0%B2%D0%B5%D1%80%D0%B5-Windows-Server
How to enable TLS 1.2 on the site servers and remote site systems
https://docs.microsoft.com/en-us/mem/configmgr/core/plan-design/security/enable-tls-1-2-server
How to enable TLS 1.2 on clients
https://docs.microsoft.com/en-us/mem/configmgr/core/plan-design/security/enable-tls-1-2-client
Разбор ситуации 2: Варианты решения
Продолжили наши разбирательства, и, думаем, нашли причину ошибки и
2 возможных варианта решения:
Наиболее вероятная причина ошибки
Старые операционки не поддерживают новые наборы шифрования протокола TLS 1.2
Суть наших умозаключений
похоже, что проблема в наборах шифрования (Cipher Suites)
попытался их внимательнее поразбирать с помощью статьи
https://docs.microsoft.com/en-us/answers/questions/227738/windows-server-2012-r2-tls-12-cipher-suites.html
не помогло.
Продолжили разбирательство
Вот Cipher Suites для разных операционных систем
https://docs.microsoft.com/en-us/windows/win32/secauthn/cipher-suites-in-schannel
по наводкам из статьи установил
IISCrypto
https://www.nartac.com/Products/IISCrypto
Увидел: на локальной машине есть такой набор
TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
он же используется и на веб сайте с которого хотим загружать страницы
это я посмотрел через сайт
https://www.ssllabs.com/ssltest/analyze.html
Вот раздел с наборами шифрования
| Cipher Suites | |
# TLS 1.3 (server has no preference) |
|
TLS_AES_128_GCM_SHA256 (0x1301) ECDH x25519 (eq. 3072 bits RSA) FS |
128 |
TLS_CHACHA20_POLY1305_SHA256 (0x1303) ECDH x25519 (eq. 3072 bits RSA) FS |
256 |
TLS_AES_256_GCM_SHA384 (0x1302) ECDH x25519 (eq. 3072 bits RSA) FS |
256 |
# TLS 1.2 (suites in server-preferred order) |
|
TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (0xc030) ECDH x25519 (eq. 3072 bits RSA) FS |
256 |
TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305_SHA256 (0xcca8) ECDH x25519 (eq. 3072 bits RSA) FS |
256 |
TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 (0xc02f) ECDH x25519 (eq. 3072 bits RSA) FS |
128 |
но, к сожалению, наборы не поддерживается в виндовс сервер 2012
https://docs.microsoft.com/en-us/windows/win32/secauthn/tls-cipher-suites-in-windows-8-1
и тем более в Windows Server 2008
https://docs.microsoft.com/en-us/windows/win32/secauthn/tls-cipher-suites-in-windows-7
а поддерживается только в Windows 10 (Windows Server 2016+)
https://docs.microsoft.com/en-us/windows/win32/secauthn/tls-cipher-suites-in-windows-10-v1607
Поизучали возможность обновления этих пакетов
How to Update Your Windows Server Cipher Suite for Better Security
https://www.howtogeek.com/221080/how-to-update-your-windows-server-cipher-suite-for-better-security/
Но, похоже, тут только возможность упорядочивания их, но новый пакет в ОС добавить вручную нельзя.
Вот более подробный разбор этой темы
Windows Server 2012 R2 TLS 1.2 Cipher Suites
https://docs.microsoft.com/en-us/answers/questions/227738/windows-server-2012-r2-tls-12-cipher-suites.html
вроде бы неудача…
но, в форумах часто проскальзывает что «хром работает, а .NET Framework приложения — нет». Причина в том, что баузер хром использует свои пакеты шифрования а не полагается ОС.
Мы зацепились за эту идею.
В одном из проектов мы использовали компонент — внедренный браузер на Chromium
пакет в Nuget: CefSharp.Winforms, CefSharp.Common.
Попробовали загрузить страницу через этот механизм — работает!
Решения
то есть у вас есть 2 варианта решения
1. переход на свежий Windows Server 2016
2. использование пакета CefSharp но предупреждаю, он увеличивает размер приложения (в нашем случае на 100+ МБ)
Выбор за вами 
Если нужны будут детальные инструкции по CefSharp -напишите в комментах: сделаю отдельную статью.
Материалы по теме
Как узнать версию TLS на сайте
https://ru.wikihow.com/%D1%83%D0%B7%D0%BD%D0%B0%D1%82%D1%8C-%D0%B2%D0%B5%D1%80%D1%81%D0%B8%D1%8E-TLS-%D0%BD%D0%B0-%D1%81%D0%B0%D0%B9%D1%82%D0%B5
Страница для анализа SSL на нужном сайте(домене)
https://www.ssllabs.com/ssltest/analyze.html
How to Update Your Windows Server Cipher Suite for Better Security
https://www.howtogeek.com/221080/how-to-update-your-windows-server-cipher-suite-for-better-security/
Cipher Suites in TLS/SSL (Schannel SSP)
https://docs.microsoft.com/en-us/windows/win32/secauthn/cipher-suites-in-schannel
Demystifying Schannel
https://techcommunity.microsoft.com/t5/core-infrastructure-and-security/demystifying-schannel/ba-p/259233
You are running Invoke-WebRequest and hit with “Could not create SSL/TLS secure channel”, It simply means TLS 1. 2 is not being used.
Windows selects most strong cryptography from the list. How do you know what’s your crypto list?
Display the list of cryptos form this .Net Class variable:
PS E:> [Net.ServicePointManager]::SecurityProtocol
Tls, Tls11, Tls12
My computer shows three cryptos and most strong one is TLS 1.2. If you get the above error message ( “Could not create SSL/TLS secure channel” ), that means the most strong crypto is not supported by the web site you are accessing. (Is Tls12 missing?)
Since this is PowerShell, you can fix it two ways. For temporarily enable TLS 1.2 and make a Invoke-WebRequest,
Run this command before you run Invoke-WebRequest cmdlet. Young only need to set the security protocol to TLS 1.2 only once in the script.
[Net.ServicePointManager]::SecurityProtocol =[Net.SecurityProtocolType]::Tls12
Obviously when you finish running the script, security protocol assignment is lost. It goes back to computer’s default setting.
If you need to make it permanent, you could add TLS 1.2 in the cryptography list in Registry. Open PowerShell in Administrative mode (Run as Admin), then add these registry entries:
Set strong cryptography on 64 bit .Net Framework (version 4 and above)
Set-ItemProperty -Path 'HKLM:SOFTWAREWow6432NodeMicrosoft.NetFrameworkv4.0.30319' -Name 'SchUseStrongCrypto' -Value '1' -Type DWord
Set strong cryptography on 32 bit .Net Framework (version 4 and above)
Set-ItemProperty -Path 'HKLM:SOFTWAREMicrosoft.NetFrameworkv4.0.30319' -Name 'SchUseStrongCrypto' -Value '1' -Type DWord
You have close all PowerShell Windows and reopen it to take effect the registry settings.
Did that help? leave me a reply.
Published by —Anand—
Being in Silicon Valley for years, I became a IT Infrastructure Geek by experience and surrounded by other Geeks everywhere. I try to help others by the solutions I found on odd occasions.
View all posts by —Anand—
Published
May 31, 2019May 31, 2019
by Vladimir Popescu
Being an artist his entire life while also playing handball at a professional level, Vladimir has also developed a passion for all things computer-related. With an innate fascination… read more
Updated on June 22, 2020
XINSTALL BY CLICKING THE DOWNLOAD FILE
This software will keep your drivers up and running, thus keeping you safe from common computer errors and hardware failure. Check all your drivers now in 3 easy steps:
- Download DriverFix (verified download file).
- Click Start Scan to find all problematic drivers.
- Click Update Drivers to get new versions and avoid system malfunctionings.
- DriverFix has been downloaded by 0 readers this month.
If you encountered the error Windows server could not create SSL/TLS secure channel when trying to show a document in WebView on Office Web App Server, you are not the only one experiencing this issue.
A great number of users have encountered the same issue. Some users encountered the same error when a request is being made to an https endpoint on Cloudflare.
This issue can be extremely frustrating, and it will not allow you to create an SSL/TLS secure channel, so your server setup can not be completed accordingly.
In this article, we will explore some of the best-proven methods to try out. Please follow the methods described in this article carefully in order to avoid causing issues.
Here’s what to do to fix the Windows server could not create SSL/TLS secure channel error
1. Set ServicePoint to TLS 1.2
Some users have reported that setting the ServicePoint to TLS 1.2 solved their issue. Follow these steps to do so:
- Find the global.asax file inside the root of your site.
- Right-click it -> select View code.
- You should be able to find an Application_Start method inside the file mentioned above.
- Add these lines to the code to force TLS 1.2:
namespace YourApplication { public class WebApiApplication : System.Web.HttpApplication { protected void Application_Start() { //**Add these lines** if (ServicePointManager.SecurityProtocol.HasFlag(SecurityProtocolType.Tls12) == false) { ServicePointManager.SecurityProtocol = ServicePointManager.SecurityProtocol | SecurityProtocolType.Tls12; } //**Add these lines** AreaRegistration.RegisterAllAreas(); GlobalConfiguration.Configure(WebApiConfig.Register); FilterConfig.RegisterGlobalFilters(GlobalFilters.Filters); RouteConfig.RegisterRoutes(RouteTable.Routes); BundleConfig.RegisterBundles(BundleTable.Bundles); } } }
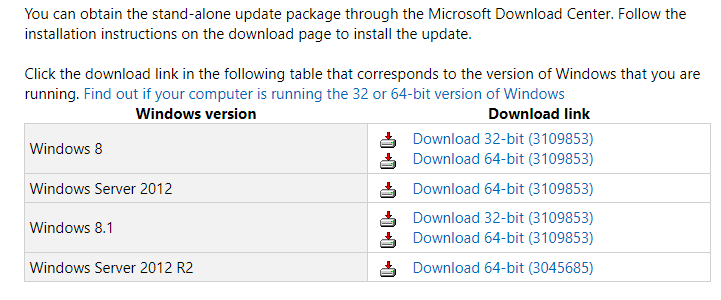
2. Download the Security Advisor update manually
- Visit this official Microsoft webpage.
- Scroll down to the bottom of the page -> download the installer that corresponds to the version of Windows you’re running.
- Install it to your PC and check to see if the issue persists. If it does, please try the next method.
Windows Server 2008 and 2008 R2 end of support coming in July
3. Enable SSL3 and TLS and add TLS 1.1 and TLS 1.2 inside the Registry Editor
To enable SSL3 and TLS follow these steps:
- Access the App Server Instances -> select the server by using the left pane.
- Click on HTTP Server and HTTP Server Listeners inside the left side of your screen.
- Select the required HTTP listener.
- Under the section SSL/TLS settings -> activate the options you require.
To add TLS 1.1 and TLS 1.2:
- Press Win+R keys on your keyboard -> type in Regedit -> press Enter.
- Navigate to the following location:
HKEY_LOCAL_MACHINESOFTWAREMicrosoft.NETFrameworkv4.0.30319.
- Inside the right-side pane -> right click -> create new DWORD registry value.
- Set the name to SchUseStrongCrypto, and set the value to 1.
- Restart IIS (Internet Information Services).
Conclusion
We hope that following the methods mentioned above have helped you fix the error Windows server could not create SSL/TLS secure channel.
We would love to know if this guide helped you. Please feel free to let us know if it did, or if you have any suggestions, by leaving a comment under this article.