Скачать PuTTY: Русская версия
Русскоязычная сборка PuTTY 0.73-RU-17 от 21 декабря 2019:
| Обычная версия: | putty-0.73-ru-17.zip |
| Портативная версия: | putty-0.73-ru-17-portable.zip |
| PuTTY: | putty.exe |
| PuTTY Portable: | putty_portable.exe |
| PSCP: | pscp.exe |
| PSFTP: | psftp.exe |
| Plink: | plink.exe |
| Pageant: | pageant.exe |
| PuTTYgen: | puttygen.exe |
| Исходный код: | putty-0.73-ru-17-src.zip |
| Контрольные суммы: | sha256sums |
Стабильный релиз PuTTY 0.76 от 17 июля 2021. Скачать официальную версию Telnet/SSH клиента:
64-разрядная версия:
| Инсталлятор: | putty-64bit-0.76-installer.msi | (цифровая подпись) |
| Архив Zip: | putty.zip | (цифровая подпись) |
| PuTTY: | putty.exe | (цифровая подпись) |
| PSCP: | pscp.exe | (цифровая подпись) |
| PSFTP: | psftp.exe | (цифровая подпись) |
| Plink: | plink.exe | (цифровая подпись) |
| Pageant: | pageant.exe | (цифровая подпись) |
| PuTTYgen: | puttygen.exe | (цифровая подпись) |
| PuTTYtel: | puttytel.exe | (цифровая подпись) |
| Контрольные суммы: | md5sums | (цифровая подпись) |
| sha1sums | (цифровая подпись) | |
| sha256sums | (цифровая подпись) | |
| sha512sums | (цифровая подпись) |
32-разрядная версия:
| Инсталлятор: | putty-0.76-installer.msi | (цифровая подпись) |
| Архив Zip: | putty.zip | (цифровая подпись) |
| PuTTY: | putty.exe | (цифровая подпись) |
| PSCP: | pscp.exe | (цифровая подпись) |
| PSFTP: | psftp.exe | (цифровая подпись) |
| Plink: | plink.exe | (цифровая подпись) |
| Pageant: | pageant.exe | (цифровая подпись) |
| PuTTYgen: | puttygen.exe | (цифровая подпись) |
| PuTTYtel: | puttytel.exe | (цифровая подпись) |
| Контрольные суммы: | md5sums | (цифровая подпись) |
| sha1sums | (цифровая подпись) | |
| sha256sums | (цифровая подпись) | |
| sha512sums | (цифровая подпись) |
Регулярная тестовая сборка PuTTY собирается каждый день из Git-репозитория.
Нашли ошибку в стабильной версии и ждёте её исправления? Можно рассчитывать, что здесь этот фикс появится намного раньше, чем выйдет следующий релиз. Эта версия для вас, если вам не терпится опробовать все нововведения раньше остальных. С другой стороны, тестовые сборки иногда могут получиться крайне нестабильными.
64-разрядная версия:
| Инсталлятор: | putty-64bit-installer.msi | (цифровая подпись) |
| Архив Zip: | putty.zip | (цифровая подпись) |
| PuTTY: | putty.exe | (цифровая подпись) |
| PSCP: | pscp.exe | (цифровая подпись) |
| PSFTP: | psftp.exe | (цифровая подпись) |
| Plink: | plink.exe | (цифровая подпись) |
| Pageant: | pageant.exe | (цифровая подпись) |
| PuTTYgen: | puttygen.exe | (цифровая подпись) |
| PuTTYtel: | puttytel.exe | (цифровая подпись) |
| Контрольные суммы: | md5sums | (цифровая подпись) |
| sha1sums | (цифровая подпись) | |
| sha256sums | (цифровая подпись) | |
| sha512sums | (цифровая подпись) |
32-разрядная версия:
| Инсталлятор: | putty-installer.msi | (цифровая подпись) |
| Архив Zip: | putty.zip | (цифровая подпись) |
| PuTTY: | putty.exe | (цифровая подпись) |
| PSCP: | pscp.exe | (цифровая подпись) |
| PSFTP: | psftp.exe | (цифровая подпись) |
| Plink: | plink.exe | (цифровая подпись) |
| Pageant: | pageant.exe | (цифровая подпись) |
| PuTTYgen: | puttygen.exe | (цифровая подпись) |
| PuTTYtel: | puttytel.exe | (цифровая подпись) |
| Контрольные суммы: | md5sums | (цифровая подпись) |
| sha1sums | (цифровая подпись) | |
| sha256sums | (цифровая подпись) | |
| sha512sums | (цифровая подпись) |
Доступна официальная версия PuTTY для ARM-устройств под управлением Windows — перейти на страницу загрузки.
PuTTY можно найти в репозиториях практически всех популярных дистрибутивов. Например, для установки PuTTY на Ubuntu, Debian, Linux Mint, ALT Linux, достаточно выполнить команду:
sudo apt-get install putty
PuTTY на OS X можно установить из портов через системы сборки MacPorts и Homebrew — подробнее в статье.
Для удобства предоставлено несколько версий исходного кода, для различных платформ. Фактически, нет существенной разницы между архивами исходников для Unix и Windows; различия находятся главным образом в форматировании (имена файлов, окончания строк, и т.д.).
Если вы хотите внести свой вклад в разработку PuTTY, мы настоятельно рекомендуем начать с исходного кода Development Snapshot.
Исходный код PuTTY для Windows:
Для получения дополнительной информации о компиляции PuTTY из исходников, читайте файл README.
Исходный код PuTTY для Linux:
Для сборки исходников release-версии, распакуйте архив, перейдите в директорию unix, и выполните команду:
make -f Makefile.gtk
Для сборки snapshot-исходников достаточно запустить стандартные:
./configure && make
Для дополнительной информации читайте файл README.
Доступ к Git
Если вы хотите следить за развитием PuTTY вплоть до минуты, или посмотреть журнал изменений для каждого файла в базе исходников, вы можете получить доступ напрямую к git репозиторию PuTTY.
Версию исходников master (последнее состояние, с самыми свежими изменениями) можно получить используя команду:
git clone https://git.tartarus.org/simon/putty.git
Также по адресу https://git.tartarus.org/?p=simon/putty.git доступен WWW браузер по репозиторию Git.
Юридическое предупреждение:
Использование PuTTY, PSCP, PSFTP и Plink может оказаться незаконным в тех странах или организациях, где шифрование полностью или частично запрещено. Полагаем, что на данном этапе развития законодательной базы в сфере IT в России и русскоязычных странах, использование применяемых протоколов шифрования не противоречит законам, но мы не юристы, и поэтому, если у вас есть сомнения, вы должны обратиться за юридической помощью прежде, чем загрузить что-либо с этого сайта.
Использование отдельного Telnet-клиента PuTTYtel не ограничено законами о криптографии, так как данные в нём не шифруются.
PuTTY is a popular SSH, Telnet, and SFTP client for Windows. It is typically used for remote access to server computers over a network using the SSH protocol. This is the download page.
For more information on PuTTY, see the PuTTY page. For information on SSH (Secure Shell), see here. For information on Telnet, see here. For information on SFTP secure file transfers, see here.
Download PuTTY installation package for Windows
Master download site
Simon Tatham publishes new PuTTY versions on his personal home page.
Installation and setup instructions
-
Installation instructions for Windows
-
Setting up public key authentication using PuTTYgen
Verifying release signatures
The releases are signed with GPG, using the PuTTY release key.
To verify the signatures, you need the gpg tool. On Debian-based Linux, it can be installed with aptitude install gnupg. On Red Hat 7, it can be installed with yum install gnupg2.
To import the signature key into GPG, use:
gpg --import putty-release-2015.ascTo check the signature of a file, use:
gpg --verify <signaturefile> <datafile>For example:
gpg --verify putty-64bit-0.69-installer.msi.gpg putty-64bit-0.69-installer.msiPackage contents: putty.exe, puttygen.exe, psftp.exe, pscp.exe, pagent.exe
The installation package includes putty.exe, puttygen.exe, psftp.exe, pscp.exe, and pagent.exe.
putty.exe is the main executable for the terminal client. It can also be used standalone, without the installation package, by simply copying the executable to a USB stick and running it on a new machine. This way, the user can carry the executable with them. However, this should not be assumed to provide great security — malware on the machine where it is used can still compromise the software (cf. CIA hacking tool bothanspy) and viruses may get installed on the USB stick whenever it is inserted in a new machine.
puttygen.exe is can be used for generating SSH keys on Windows. See the separate puttygen page on how to create and set up SSH keys with it.
psftp.exe is an SFTP file transfer client. It only works on the command line, and does not support graphically dragging and dropping files between systems. See Tectia SSH if you’d like that functionality.
pscp.exe is a command line SCP client.
pagent.exe is an SSH agent for PuTTY. Keys are first created with puttygen.exe and can then be loaded into pagent for automating logins and for implementing single sign-on.
Alternatives
For other SSH clients and comparison, see the SSH clients page. Several more modern alternatives are available.
Server for Windows or other platforms
You don’t need to worry about a server if you are going to connect to a school or work server. However, if you are planning to use PuTTY to log into your own systems, then you may need to install and enable a server.
Most Linux and Unix systems come with OpenSSH preinstalled. On some distributions, you may need to install the server. On Debian-derived systems, the following will install the server:
sudo aptitude install openssh-serverOn Red Hat systems, the following will install the server:
sudo yum install openssh-serverDepending on the system, you may also need to start the server if you don’t want to reboot. The following should work on most systems:
sudo service sshd restartFor Windows, the Tectia SSH is a popular choice and comes with commercial support services. It also runs on IBM z/OS mainframes. Unix/Linux are available with support for business-critical applications.
SSH key management needs attention
SSH is often used with public key authentication to implement automation and single sign-on.
Public key authentication uses a new kind of access credential, the SSH key, for authentication. It is much more secure than traditional password authentication, especially compared to hard-coded passwords in scripts, but the keys need proper management.
Most organizations with more than a hundred servers have large numbers of SSH keys. Usually, these keys have not been properly managed and audited. An SSH risk assessment is recommended. Organizations should consider deploying key management software to establish proper provisioning, termination, and monitoring for key-based access.
Risks of unmanaged SSH keys include uncontrolled attack spread across the server infrstructure, including to disaster recovery data centers and backup systems.
Organizations should also be aware of security risks related to SSH port forwarding. It is a technology that has many good uses, but it can also enable unfettered access across firewalls. Employees and attackers can leave tunnels back into the internal network from the public Internet. This particularly affects organizations using cloud computing services.
Using telnet is not recommended
In addition to SSH, the PuTTY can be used as a telnet client. Telnet is insecure. Its use is not recommended.
The main problem with telnet is that it transmits all passwords and any transmitted data in the clear. Anyone with access to any computer on the same network can steal user names and passwords that are transmitted. Such password sniffing attacks were very common on the Internet already in the 1990s.
Telnet sessions can also be hijacked in the network. Attackers can inject their own commands into telnet sessions. Protection from such attacks was the main reason why Tatu Ylonen developed SSH as a replacement for telnet in the first place. Use of telnet has not been recommended for 20 years.
SFTP file transfer support
File transfer support is implemented as a separate program, PSFTP. It is available only as a command-line tool. There is no graphical user interface for file transfers.
SCP file transfers are supported via the PSCP program. This is also command-line only.
Modern implementations, such as Tectia SSH, have integrated file transfers in the terminal client.
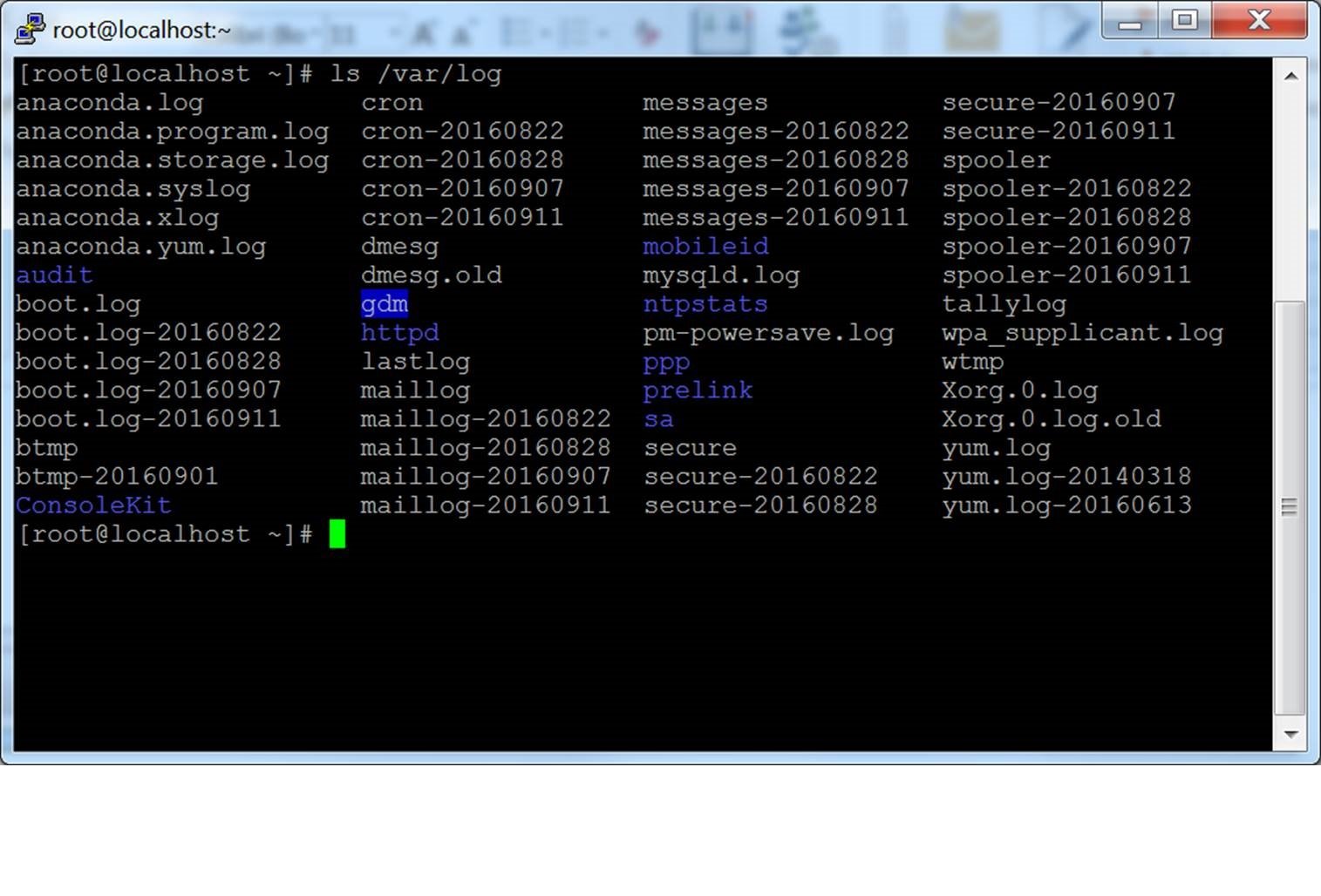
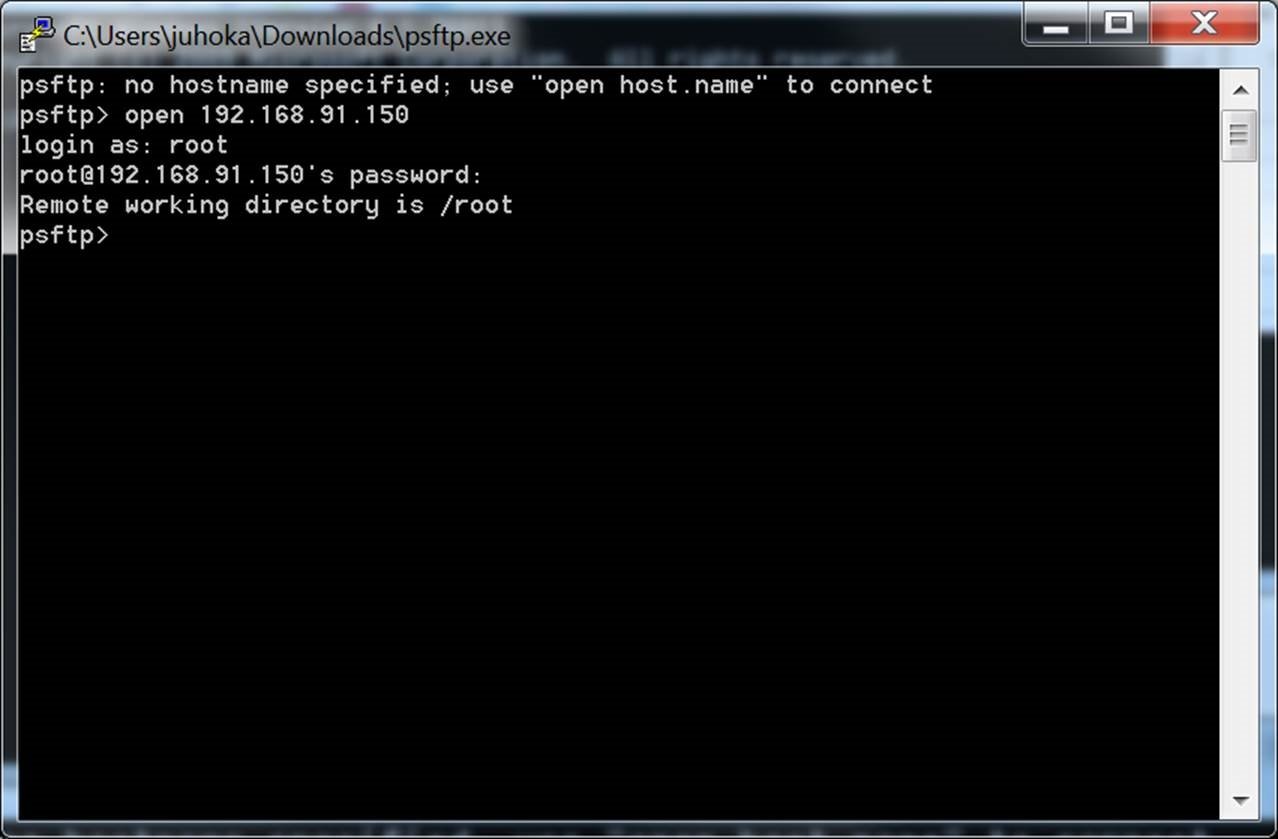
Screenshots
PuTTY terminal window
PSFTP command line Use
Bitvise SSH Client: Free SSH file transfer, terminal and tunneling
Our SSH client supports all desktop and server versions of Windows, 32-bit and 64-bit, from Windows XP SP3 and Windows Server 2003, up to the most recent – Windows 11 and Windows Server 2022.
Our client is free for use of all types, including in organizations. To begin, simply download it here.
Our SSH and SFTP client for Windows incorporates:
-
One of the most advanced graphical SFTP clients.
-
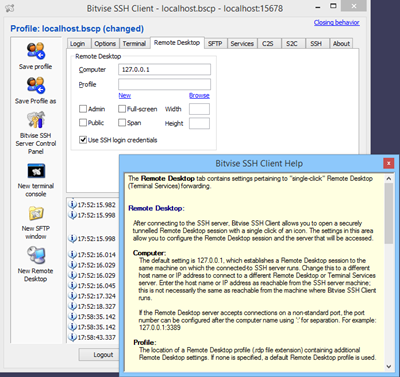
Single-click Remote Desktop forwarding.
-
State-of-the-art terminal emulation with support for the bvterm, xterm, and vt100 protocols.
-
Support for corporation-wide single sign-on using SSPI (GSSAPI) Kerberos 5 and NTLM user authentication, as well as Kerberos 5 host authentication.
-
Support for ECDSA, RSA and DSA public key authentication with comprehensive user keypair management.
-
Encryption and security: Provides state-of-the-art encryption and security suitable as part of a standards-compliant solution meeting the requirements of PCI, HIPAA, or FIPS 140-2 validation.
-
SSH jump proxy: Connect to a final destination SSH or SFTP server by connecting through an SSH jump server. In the graphical SSH Client, this is configured in Proxy settings, on the Login tab.
-
Obfuscated SSH with an optional keyword. When supported and enabled in both the client and server, obfuscation makes it more difficult for an observer to detect that the protocol being used is SSH. (Protocol; OpenSSH patches)
-
Powerful SSH port forwarding capabilities, including dynamic forwarding through integrated SOCKS and HTTP CONNECT proxy.
-
Powerful command-line parameters which make the SSH client highly customizable and suitable for use in specific situations and controlled environments.
-
SFTP drive mapping: Access files on an SFTP server as if they were local, from any Windows application.
-
An FTP-to-SFTP bridge allowing you to connect to an SFTP server using legacy FTP applications.
-
An advanced, scriptable command-line SFTP client, sftpc.
-
A scriptable command-line remote execution client, sexec, and a command-line terminal console client, stermc.
-
A scriptable command-line tunneling client, stnlc, with support for static port forwarding rules, dynamic SOCKS-based tunneling, and FTP-to-SFTP bridge.
-
Our .NET SSH library, FlowSshNet, with example PowerShell scripts showing how to use the SSH library for file transfer and remote program execution from PowerShell.
-
Bitvise SSH Server remote administration features.
Bitvise software does not contain ads, install product bundles or collect user data for sale. We are 100% supported by users who license our software. Thank you!
Graphical SFTP File Transfers
Bitvise SSH Client incorporates one of the most advanced SFTP file transfer clients, supporting:
- automatic resuming, text file awareness, recursive subdirectory transfers;
- powerful, advanced transfer list management;
- verified-integrity resume with servers that support SFTP v6 check-file and check-file-blocks;
- directory mirroring with servers that support SFTP v6 check-file and check-file-blocks;
- high speed — in tens or hundreds of MB/s with Bitvise SSH Server, network and disk speed permitting;
- fast responsiveness to user input even when in the middle of multiple file transfers.
- SFTP drive — access files on an SFTP server as if they were local, from any Windows application.
Bitvise SSH Client also incorporates an advanced, scriptable command-line SFTP client.
Terminal Access — Remote Console
Bitvise SSH Client provides integrated access to the SSH server’s console, either via VT-100 and xterm protocols supported by most SSH servers on any platform, or via the enhanced bvterm protocol supported by Bitvise SSH Server:
- UTF support with VT-100 and xterm, full Unicode support with bvterm;
- full color support with xterm and bvterm;
- support for large screen buffers, all key combinations including Alt-keys and fully-accurate console rendering with bvterm;
- terminal session recording.
Bitvise SSH Client also incorporates a command line terminal emulation client, stermc, as well as a command-line remote execution client (sexec).
Single sign-on
When using Bitvise SSH Client to connect to a GSSAPI-enabled SSH server in the same or a trusted Windows domain, you can let Kerberos 5 (or on older platforms, NTLM) perform the server as well as user authentication for you. No manual host key verification; no management of user passwords and public keys. Just tell the SSH client which server in the domain to connect to, and if that server is Bitvise SSH Server or another server with compatible support for GSSAPI, the two programs will authenticate and establish a secure connection automatically.
Port Forwarding
Bitvise SSH Client is a powerful SSH2 port forwarding client with many features, including:
-
Dynamic tunneling via integrated proxy
supporting SOCKS4, SOCKS4A, SOCKS5 and HTTP CONNECT proxy tunneling
protocols. Configure your applications to connect to target hosts
through the SSH Client’s proxy, and no manual tunneling rules need be
configured.How to set up programs for dynamic tunneling: Firefox, IE; with these settings in Bitvise SSH Client.
-
Port forwarding settings can be saved to and loaded from a profile. One can maintain multiple complex tunneling configurations without having to manually enter parameters before each session.
-
Bitvise SSH Client minimizes its presence by displaying only a system tray icon when running in the background. If an error is encountered while the program is minimized, the icon reflects that.
-
Server-side forwarding:
with Bitvise SSH Server and Client, a server and multiple clients can be set up
so that all port forwarding rules are configured centrally at the
server, without requiring any client-side setting updates. The SSH
clients only need to be configured once, and port forwarding rules can
easily be changed when necessary. -
Command-line parameters are supported. Using command-line automation,
a port forwarding session can be started from a link in the Startup
menu without requiring any user interaction whatsoever. Help with the
command-line parameters can be found in the SSH client log area when it
is first started, or by executing ‘BvSsh /?’ from a command prompt. -
After an SSH session is established, any external application can be launched automatically.
-
If an SSH session is interrupted, Bitvise SSH Client can automatically reconnect to the server.
Bitvise SSH Client also incorporates an advanced, scriptable command-line tunneling client.
Highly customizable
Run ‘BvSsh -?’ for a list of command-line parameters providing flexibility to:
-
make Bitvise SSH Client load a profile and connect immediately on startup and exit on disconnect using the -profile, -loginOnStartup and -exitOnLogout
parameters; -
make Bitvise SSH Client hide portions of its user interface (main window, authentication messages, access to SSH features) using the -hide and -menu parameters;
-
run Bitvise SSH Client from removable media and prevent it from making any changes to the Windows registry — and yet use public key authentication and
verify host keys using the -noRegistry, -keypairFile and -hostKeyFile
parameters;
and more.
Additionally, when the graphical Bitvise SSH Client is running, you can use the command line utility BvSshCtrl to programmatically cause the client to log in, log out, or exit. Run ‘BvSshCtrl’ for help.
Portable use of Bitvise SSH Client
Bitvise SSH Client (Tunnelier) supports command-line parameters that control how it uses the Windows registry (the -noRegistry and -baseRegistry parameters). This can be used when control over registry usage is required.
The latest versions of our SSH Client additionally support storing host key information and client authentication keypairs in an SSH Client profile. This means that you can copy the contents of the SSH Client installation directory to a USB key, insert the USB key into another computer, and run the graphical SSH Client as follows:
BvSsh -noRegistry -profile=U:Profile.bscp
This will tell the Client to not use the Windows registry, and to connect exclusively using the host and keypair information you have saved into Profile.bscp.
For more information about the supported command line parameters, run the graphical SSH Client as follows:
BvSsh -?
Bitvise SSH Client further includes command line clients – sftpc, sexec, stermc, and stnlc – which also support the -noRegistry and -profile parameters. These command line clients are frequently used unattended, but can also be used interactively. For more information, check Using Bitvise SSH Client Unattended.
Command-Line SFTP Client
Bitvise SSH Client incorporates sftpc, an advanced command-line SFTP client which supports:
- queued background transfers so you can continue browsing directories while a file downloads (‘get * -bg’);
- powerful command-line parameters for automated scripted transfers launched from a batch file or an external program;
- verified-integrity resume with servers that support SFTP v6 check-file and check-file-blocks;
- automatic text file conversion when transferring files between platforms (the ‘type’ command);
- wildcards — the * and ? wildcard characters can match more than one file;
- recursive transfers — a simple ‘get * -s’ downloads all files and subdirectories;
- resume support — ‘get file.txt -r’ resumes a previously downloaded file if it already exists;
- high speed — in the tens of MB/s with Bitvise SSH Server, network and disk speed permitting.
Additional information:
-
Usage: after installing Bitvise SSH Client, get this help by executing «sftpc -?»
-
Command list: after installing Bitvise SSH Client, get this help by connecting to a server using sftpc, then execute «help» and «help <command>«
-
The «log» utility can be used with sftpc to store the output of each individual SFTP session in a separate, uniquely named log file for auditing.
-
The «retry» utility can be used with sftpc to automatically repeat transfer attempts after specific types of failures.
Command-Line Remote Execution Client
Bitvise SSH Client incorporates sexec,
a scriptable command-line remote execution client which can be used to
securely execute programs on remote machines from a batch file. The
batch file can perform actions based on the exit code reported from the
remote program, and can capture the remote program’s output for
processing by simple redirection of sexec output.
Another command-line program included with Bitvise SSH Client, stermc,
conveniently opens an SSH terminal emulation session with xterm, VT-100
and bvterm support in the same Command Prompt window it is started
from. If you SSH from computer A to computer B running Bitvise SSH Server, and you also have Bitvise SSH Client installed on computer B, you can use stermc to
conveniently establish an onward SSH terminal session to computer C.
All Bitvise command-line clients support all authentication methods
supported by Bitvise SSH Client, can load settings from a profile configured in the graphical client, work with the same user keypair and host key database as the graphical client, can connect through a SOCKS or HTTP CONNECT proxy, and support a common set of command-line parameters controlling most aspects of establishing an SSH connection.
Command-Line Tunneling Client
Bitvise SSH Client incorporates stnlc, a scriptable command line port forwarding client with support for static port forwarding rules, dynamic SOCKS-based tunneling, FTP-to-SFTP bridge, and SFTP drive mapping.
For more information about using this client, run ‘stnlc -h’.
FTP-to-SFTP Bridge
Bitvise SSH Client incorporates an FTP-to-SFTP bridge which performs translation between the FTP and SFTP protocols, allowing any FTP client application to connect securely to an SFTP server through Bitvise SSH Client. Both active mode and passive mode
FTP data connections are supported, as well as restarted transfers,
directory listings and other features. All FTP clients should be able
to list directories and transfer files across Bitvise SSH Client’s FTP-to-SFTP
bridge, including integrated clients in applications such as
DreamWeaver, GUI clients such as BulletProof FTP, and command line
clients such as the default ftp.exe client accompanying Windows. If an
FTP client you use fails to work with Bitvise SSH Client’s FTP-to-SFTP bridge, let us know.
See Accessing an SFTP Server with an FTP Client for more information about the FTP bridge.
Using with Bitvise SSH Server
When connected to Bitvise SSH Server, our client can do all of the above, as well as the following:
-
bvterm console: When connected to Bitvise SSH Server, our client provides you with the best console available on the Windows platform. Our bvterm protocol supports the full spectrum of a Windows console’s features: colors, Unicode characters, all-key access and large scrollable buffers.
-
Remote server configuration: Using Bitvise SSH Client, all SSH Server settings can be configured remotely without having to use Remote Desktop.
Windows version compatibility
Bitvise SSH Client supports the following Windows versions:
- Windows Server 2022
- Windows 11
- Windows Server 2019
- Windows Server 2016
- Windows 10
- Windows Server 2012 R2
- Windows Server 2012
- Windows 8.1
- Windows Server 2008 R2
- Windows Server 2008
- Windows Vista SP1 or SP2
- Windows Server 2003 R2
- Windows Server 2003
- Windows XP SP3
A recent Bitvise SSH Client version should be used on all platforms. The SSH Client is security-sensitive software that communicates across a network. Using a recent version is the only way to receive updates. Therefore, we do not recommend indefinite use of older versions.
Encryption and security features
SSH and SFTP:
-
Key exchange algorithms:
- Curve25519
- ECDH over elliptic curves secp256k1, nistp256, nistp384, nistp521 using SHA-512, SHA-384, or SHA-256
- Diffie Hellman with group exchange using SHA-256
- Diffie Hellman with fixed 4096, 3072, or 2048-bit group parameters using SHA-512 or SHA-256
- Diffie Hellman with 1024-bit group parameters or using SHA-1 (legacy)
- GSSAPI key exchange using Diffie Hellman and Kerberos authentication
-
Signature algorithms:
- Ed25519
- ECDSA over elliptic curves secp256k1, nistp256, nistp384, nistp521 using SHA-512, SHA-384, or SHA-256
- RSA using 4096, 3072, or 2048-bit key sizes with SHA-512 or SHA-256
- RSA using 1024-bit keys or with SHA-1 (legacy)
- DSA using SHA-1 (legacy)
-
Encryption algorithms:
- ChaCha20 with 512-bit keys with Poly1305
- AES with 256, 128-bit keys in GCM mode
- AES with 256, 192, 128-bit keys in CTR mode
- AES with 256, 192, 128-bit keys in CBC mode (legacy)
- 3DES in CTR or CBC mode (legacy)
-
Data integrity protection:
- ChaCha20 with 512-bit keys with Poly1305
- AES with 256, 128-bit keys in GCM mode
- HMAC using SHA-256 or SHA-512, in encrypt-then-MAC mode
- HMAC using SHA-256 or SHA-512 (classic)
- HMAC using SHA-1 (legacy)
-
Server authentication:
- Client verifies server identity using server host key fingerprint or public key
- Automatic synchronization of new host keys to client supported
-
Client authentication:
- Password authentication
- Password change during password authentication
- Public key authentication
- Kerberos single sign-on using GSSAPI
- Two-factor authentication with a time-based one-time password
FIPS 140-2 validation
When FIPS is enabled in Windows, our software uses Windows built-in cryptography, validated by NIST to FIPS 140-2 under certificates
#2937,
#2606,
#2357, and
#1892. On Windows XP and 2003, our software uses the Crypto++ 5.3.0 FIPS DLL, originally validated by NIST under certificate
#819 (historical). When FIPS mode is not enabled, additional non-FIPS algorithms are supported.
Cryptographic implementations and availability
Current Bitvise software versions (9.12 and higher) use the following cryptographic implementations for different algorithms, on different versions of Windows:
| Algorithm | Windows XP, Server 2003 |
Windows Vista to 8.1, Server 2008 to 2012 R2 |
Windows 10, 11, Server 2016 to 2022 |
|---|---|---|---|
| Signature | |||
| RSA | Crypto++ 5.3 | Windows CNG | Windows CNG |
| Ed25519 | n/a | DJB | DJB |
| ECDSA (NIST curves) | Crypto++ 5.3 | Windows CNG | Windows CNG |
| ECDSA/secp256k1 | Crypto++ 5.3 | OpenSSL | Windows CNG |
| 1024-bit DSA | Crypto++ 5.3 | Windows CNG | Windows CNG |
| Non-standard DSA | Crypto++ 5.3 | Crypto++ 5.6 | Crypto++ 5.6 |
| Key exchange | |||
| Classic DH | Crypto++ 5.3 | Windows CNG | Windows CNG |
| Curve25519 | n/a | DJB | DJB |
| ECDH (NIST curves) | Crypto++ 5.3 | Windows CNG | Windows CNG |
| ECDH/secp256k1 | Crypto++ 5.3 | OpenSSL | Windows CNG |
| Encryption | |||
| AES | Crypto++ 5.3 | Windows CNG | Windows CNG |
| ChaCha20 | n/a | OpenSSL | OpenSSL |
| 3DES | Crypto++ 5.3 | Windows CNG | Windows CNG |
| Integrity | |||
| GCM | n/a | Windows CNG | Windows CNG |
| Poly1305 | n/a | OpenSSL | OpenSSL |
| HMAC-SHA2 | Crypto++ 5.3 | Windows CNG | Windows CNG |
| HMAC-SHA1 | Crypto++ 5.3 | Windows CNG | Windows CNG |
This product includes software developed by the OpenSSL Project for use in the OpenSSL Toolkit. (http://www.openssl.org/)
This product includes cryptographic software written by Eric Young (eay@cryptsoft.com).
SSH or Secure Shell is a protocol used for establishing secure encrypted connections over an insecure network such as the internet. Although any application can utilize the SSH protocol to secure its communication, it is mostly used for secure remote logins and secure file transfers. SSH utilizes a public-key methodology to authorize users and their connections.
If you are into the IT industry, you might have required a Secure Shell at some point in your work. Secure Shell a.k.a SSH is a program that lets you log into a remote machine, execute commands, move files, and more. The program is a UNIX-based command protocol that provides authenticated access to a remote computer system.
SSH uses RSA public-key cryptography and provides secure communications over insecure channels and hence is used widely by the network administrators. Since it strives to create a confidential connection across two machines, the commands are encrypted in many ways. A digital certificate and passwords are used at both ends to ensure a secure connection.
While you can now enable & use OpenSSH on Windows, today in this post, we will check out some free SSH Client software for Windows 11/10 – PuTTY, WinSCP, Bitvise SSH, OpenSSH, SmarTTY and Dameware FreeSSH.
Communication over SSH happens between an SSH Client and an SSH Server. A client can be authenticated using a password or a pair of public and private keys. Once a client is authenticated, a secure tunnel is established between the client and the server. And this tunnel is used to send encrypted data which would have rather been un-encrypted and insecure. SSH has a lot of applications, and it prevents quite a lot of cyber-attacks, such as a man in the middle attacks.
Before the widespread of SSH, protocols like Telnet and FTP were prevalent. But considering the security and privacy offered by this protocol, many of users and developers have moved to SSH. Some of the applications of SSH are Remote Login, Remote Commands, Secure File Transfer, and a lot more. Any application can take advantage of SSH protocol using the port forwarding technique. Understanding this protocol requires deep knowledge of Computer Networks, protocols, and prevalent network models (TCP/IP and OSI).
Knowing the basics, let us now take a look at some free SSH Clients for Windows PC – PuTTY, Bitvise, and SmarTTY.
1] PuTTY
Originally written for Microsoft, this SSH client is now available for many other operating systems, and being very easy to use, PuTTY is one of the most popular SSH clients used by Windows users. It is a portable tool and provides full control over the encryptions and the protocol version. Besides SSH, PuTTY can connect to computers via SCP, rlogin, Telnet, and raw socket connection.
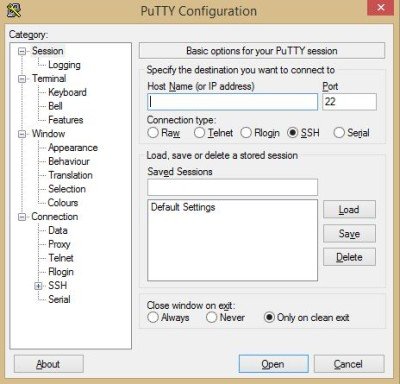
PuTTY is one of the most widely used SSH clients for Windows 11/10/8/7. It is highly customizable and offers great features. It supports connections over both SSH 1 (insecure), SSH 2, and Telnet. To establish a connection using PuTTY, all you need to do is enter the hostname and the port (usually 22), and you are good to go. You can customize all other settings by going to a relevant section of the left menu. Apart from that, you can even customize the look and feel of the PuTTY terminal. You can download it here.
2] WinSCP
Best known for its secure file transfer WinSCP is an open-source free SSH Client for Windows users. Besides SSH, it supports SFTP and SCP protocols to connect to your computer to a remote machine. It comes with an integrated text editor and can also integrate with PuTTY authentication agent. It gives you the option of storing the sessions and comes with all other standard features. The portable version of WinSCP is also available. You can download it here.
3] OpenSSH
Like most of the other SSH Clients, OpenSSH supports all SSH protocol versions and provides secure tunneling capabilities. It encrypts all your traffic and avoids the risks of hijacking. It works as a good alternative to programs like telnet and rlogin. It is included in almost every popular operating system like Linux, OSX, Solaris, and BSD. You can download it here.
4] Dameware FreeSSH
This free SSH Windows Client lets you make SSH connections with a simple protocol. Dameware FreeSSH connects you to the remote machine using SSH2, SSH1, and Telnet protocols and lets you manage multiple sessions from a single console. You can save the sessions easily. You can download it here.
5] Bitvise SSH Client
Bitvise SSH Client is a free SSH client that offers rich GUI experience. The client is easy to set up and install. Apart from SSH, it offers SFTP, which is a secure alternative to conventional file transfer protocol. Apart from SSH Client, Bitvise also offers an SSH Server application for Windows. The client is completely free to download and install, but you may need to purchase a license for the server application.
Although not as simple as PuTTY, Bitvise SSH client comes with a simple layout and well-organized categories. Bitvise connects you to the remote machine via SSH2, provides access and lets you transfer the files. It is equipped with a set of required tools and can fulfill your work needs in a secure environment. Click here to download Bitvise.
Read: Best PuTTy alternative for SSH Clients for Windows.
6] SmarTTY
SmarTTY is considered as one of the best alternatives to PuTTY. It offers a great variety of features such as multiple tabs for one session and inbuilt public key authorization. Another interesting feature in SmarTTY is that it lets you edit your files remotely. The inbuilt editor is very handy and useful. Also, it comes with features such as Automatic CRLF to LF conversion. Click here to download SmarTTY.
If you are connecting your computer to a remote machine, you probably would want to keep all your data safe and secure. Secure Shell Clients can help you with that. All you need to do is to download and install the set up a suitable SSH client software on your Windows computer, run it, and create an encrypted connection with any remote PC. It is always advised to test the connections before you create secure keys and start the file transfer.
You may want to have a look at these Free FTP Client Software too.