You can activate Microsoft virtualization-based security (VBS) for supported Windows guest operating systems at the same time you create a virtual machine.
Configuring VBS is a process that involves first activating VBS in the virtual machine then activating VBS in the Windows guest OS.
Prerequisites
See vSphere Virtualization-based Security Best Practices for acceptable CPUs.
Using Intel CPUs for VBS requires vSphere 6.7 or later. Create a virtual machine that uses hardware version 14 or later and one of the following supported guest operating systems:
- Windows 10 (64 bit) or later releases
- Windows Server 2016 (64 bit) or later releases
Using AMD CPUs for VBS requires vSphere 7.0 Update 2 or later. Create a virtual machine that uses hardware version 19 or later and one of the following supported guest operating systems:
- Windows 10 (64 bit), version 1809 or later releases
- Windows Server 2019 (64 bit) or later releases
Ensure that you install the latest patches for Windows 10, version 1809, and Windows Server 2019, before activating VBS.
For more information about activating VBS on virtual machines on AMD platforms, see the VMware KB article at https://kb.vmware.com/s/article/89880.
Procedure
- Connect to vCenter Server by using the vSphere Client.
- Select an object in the inventory that is a valid parent object of a virtual machine, for example, an ESXi host or a cluster.
- Right-click the object, select New Virtual Machine, and follow the prompts to create a virtual machine.
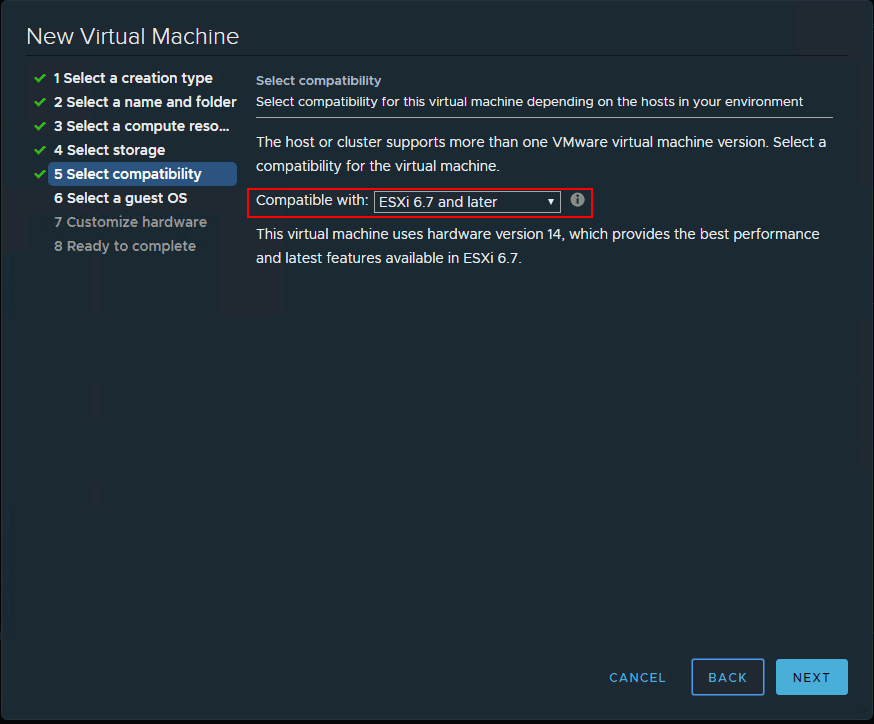
Option Action Select a creation type Create a virtual machine. Select a name and folder Specify a name and target location. Select a compute resource Specify an object for which you have privileges to create virtual machines. Select storage In the VM storage policy, select the storage policy. Select a compatible datastore. Select compatibility Intel CPU: Ensure that ESXi 6.7 and later is selected. AMD CPU: Ensure that ESXi 7.0 U2 and later is selected.
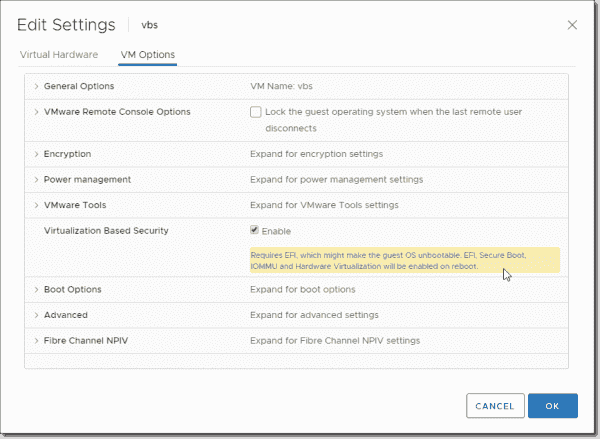
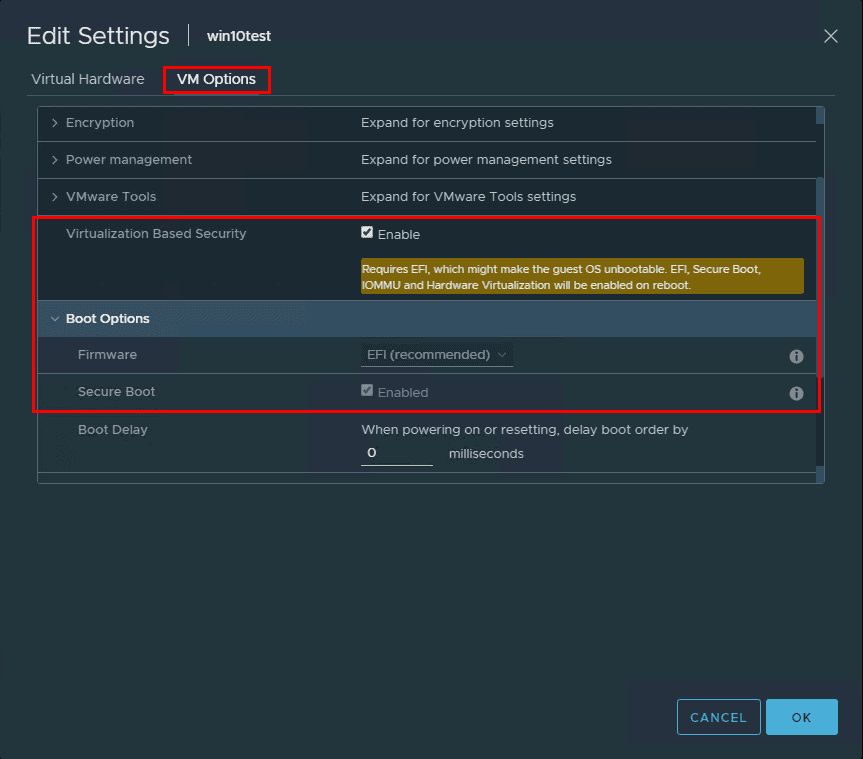
Select a guest OS Select the Windows guest operating system option that best corresponds to operating system release. Select the Enable Windows Virtualization Based Security check box.
Customize hardware Customize the hardware, for example, by changing disk size or CPU. Ready to complete Review the information and click Finish.
Results
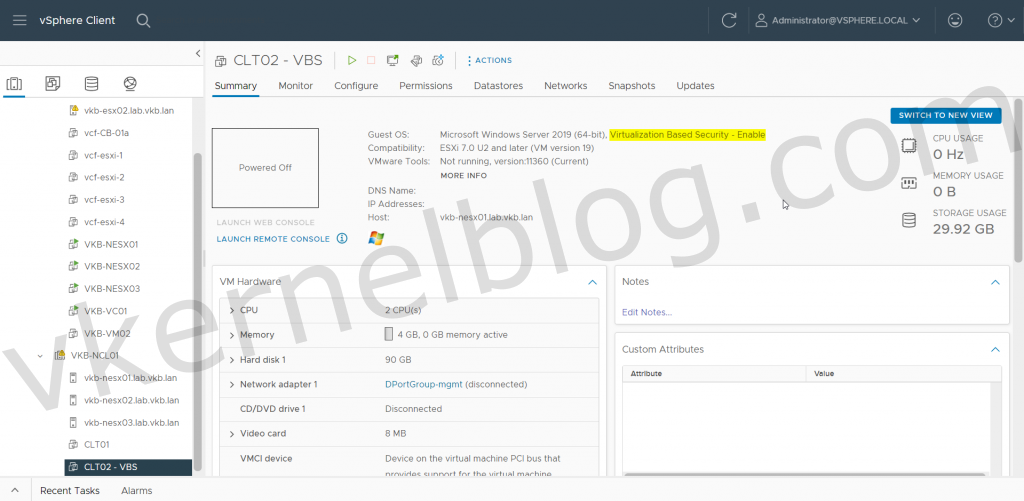
The Virtual Machine Details tile under the Summary tab displays «Virtualization Based Security — Enable».
What to do next
See Activate Virtualization-based Security on the Guest Operating System.
You can enable Microsoft virtualization-based security (VBS) for supported Windows guest operating systems.
You enable VBS from within the Windows Guest OS. Windows configures and enforces VBS through a Group Policy Object (GPO). The GPO gives you the ability to turn off and on the various services, such as Secure Boot, Device Guard, and Credential Guard, that VBS offers. Certain Windows versions also require you to perform the additional step of enabling the Hyper-V platform.
See Microsoft’s documentation about deploying Device Guard to enable virtualization-based security for details.
Prerequisites
- Ensure that virtualization-based security has been enabled on the virtual machine.
Procedure
- In Microsoft Windows, edit the group policy to turn on VBS and choose other VBS-related security options.
- (Optional) For Microsoft Windows versions less than Redstone 4, in the Windows Features control panel, enable the Hyper-V platform.
- Reboot the guest operating system.
With version 6.7, VMware added support for the Windows 10 virtualization-based security (VBS) feature to the vSphere suite. Microsoft’s VBS is also available for Windows Server 2016 operating systems (OSes).
Contents
- What is Virtualization-based Security (VBS)?
- What are the restrictions on VBS-enabled VMs?
- What are the vSphere requirements for VBS?
- How do you enable VBS?
- Final words
- Author
- Recent Posts
Vladan Seget is an independent consultant, professional blogger, vExpert 2009-2021, VCAP-DCA/DCD and MCSA. He has been working for over 20 years as a system engineer.
What is Virtualization-based Security (VBS)?
VBS uses hardware and software virtualization features to enhance Windows system security by creating an isolated, hypervisor-restricted, specialized subsystem.
Basically, Microsoft is using a Windows role (or component) called the Hyper-V role, which boots the OS. This hypervisor allows Microsoft to isolate some sensitive information in places that would normally be accessible to the OS. Here we can think of cached credentials and such things.
Most modern systems have a Trusted Platform Module (TPM) 2.0 device built into the hardware. However, someone had to do it in software. And this is the goal. To give you an idea, here is a screenshot from a VMware blog post.
Microsoft VBS
As you can see, the Windows 10 virtual machine (VM) has a hypervisor role active and has the credentials stored elsewhere.
What are the restrictions on VBS-enabled VMs?
VBS is only usable on Windows 10 and Windows Server 2016, and vSphere features exist that are not compatible with VBS:
- VMware Fault Tolerance (FT)
- vSphere PCI passthrough
- vSphere hot add for CPU or memory
What are the vSphere requirements for VBS?
As mentioned above, VBS is only available as of vSphere 6.7. The requirements for working with VBS are:
- A VM with virtual hardware 14
- Hardware virtualization and an input/output memory management unit (IOMMU) exposed to the VM
- Secure boot enabled
- EFI firmware
- 64-bit CPU
- Intel VT-d or AMD-Vi ARM64 system memory management units (SMMUs)
- TPM 2.0
How do you enable VBS?
In the VMware vSphere client, first connect to vSphere and select the VM for which you want to enable VBS.
- Shut down the VM and tick the Enable box next to Virtualization Based Security under VM Options.
Enabling VBS
Note: The VM has to be booting EFI (not BIOS) to satisfy the requirements. If you are creating new Windows 10 or Windows 2016 VMs, you should make sure you are selecting UEFI firmware before installing. After installing the system, it is pretty difficult to switch.
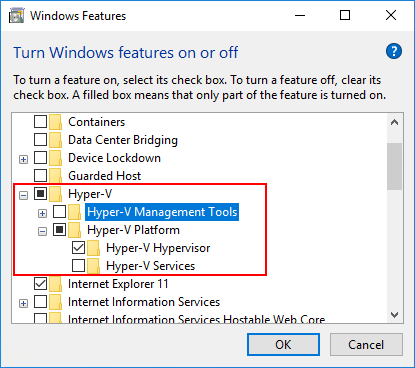
And once the VM is up and running, we’ll need to activate the Hyper-V role. You can do this through a simple command appwiz.cpl, which automatically brings up the window where we select Add/Remove Turn Windows features on and off. Once there, we can look for the Hyper-V section and check the box Hyper-V Hypervisor.
Enabling the Hyper V Hypervisor
If you want to add a Hyper-V role on Windows Server 2016, you’ll use the Add roles and features wizard within your Server Manager.
Once you’re done, it’ll ask you to reboot the system.
Let’s continue after the VM comes up.
- In the VM, open gpedit.msc and browse to:
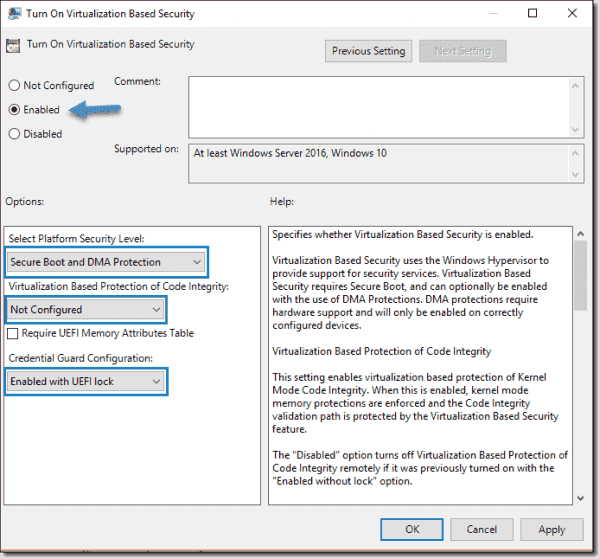
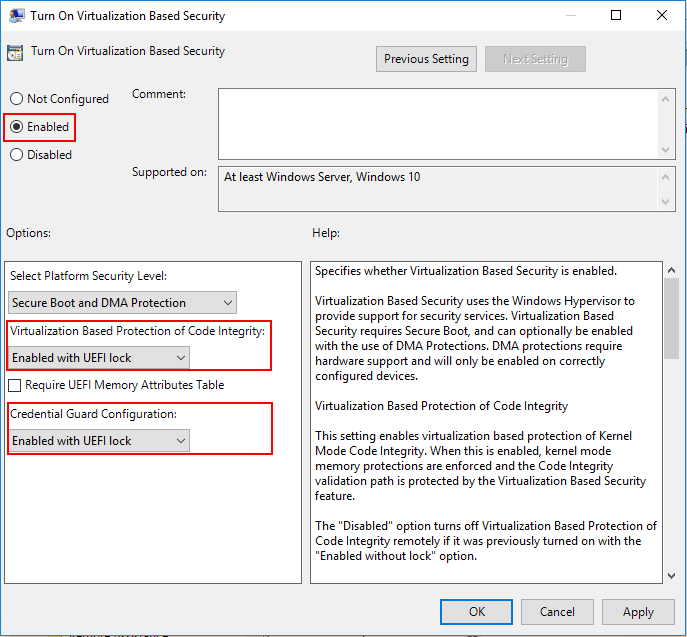
Computer Configuration > Administrative Templates > System > Device Guard > Turn On Virtualization Based Security. Set it to Enable and configure the options as follows:
- Select Platform Security Level: Secure Boot and DMA Protection
- Virtualization Based Protection of Code Integrity: Enabled with UEFI lock
- Credential Guard Configuration: Enabled with UEFI lock
If you want to be able to turn off Windows Defender Credential Guard remotely, choose Enabled without lock.
Credential Guard configuration
If you want to activate VBS for multiple systems, you can do this via Group Policy in your domain.
Final words
I think there will be further expansion of VBS in Windows Server 2019. It is a great feature that helps protect Windows against malware and all kinds of attacks where credentials are involved.
Subscribe to 4sysops newsletter!
VMware vSphere 6.7 has brought this feature in collaboration with Microsoft. It is great to see that these two giants now work hand in hand on features that improve security.

One of the many areas of VMware vSphere 6.7 that has seen fantastic improvements has been in the realm of security. VMware has shown they are diligently committed to continuing to strive for excellence when it comes to tomorrow’s security needs in the enterprise datacenter. There are really big security features with vSphere 6.7 – notably including – TPM 2.0 support for ESXi, Virtual TPM 2.0 for VMs, support for Microsoft Virtualization Based Security, and multiple syslog targets. One of the really cool security features that I have been anxious to try out is the support for Microsoft Virtualization Based Security. What is Microsoft Virtualization Based Security and what are its security benefits? How do we go about enabling Windows 10 Virtualization Based Security with vSphere 6.7 in a virtual machine?
What is Microsoft Virtualization Based Security?
Microsoft Virtualization Based Security or VBS by its definition from Microsoft uses hardware virtualization features to create and isolate a secure region of memory from the normal operating system. In essence, Microsoft is using its hypervisor, Hyper-V, to boot the operating system. Additionally this underlying hypervisor allows Microsoft to be able to protect certain extremely sensitive pieces of information that would normally reside in the operating system itself, such as cached credentials, but instead, with Virtualization Based Security enabled, Microsoft is using the hypervisor as a restricted memory space where sensitive information such as credentials can be stored instead of the operating system itself.
However, as probably stood out in the description above, Virtualization Based Security uses “hardware virtualization features…” to implement this new security layer. If you are running a virtual machine, we are not exposing the hardware virtualization features. However, that is where VMware vSphere 6.7 comes into play here and really shines. With VMware vSphere 6.7, VMware has worked very closely with Microsoft to virtualize these “hardware” features that VBS expects to be present, so that in a virtual machine, these features can be turned on without issue. The ESXi hypervisor presents these features to the underlying guest operating system such as Windows 10 so VBS can successfully run. How cool is that?!
The VBS features are able to run because VMware has enabled the following features in ESXi 6.7 to be presented to the guest operating system in the virtual machine:

- Nested virtualization
- IOMMU
- EFI firmware
- Secure Boot
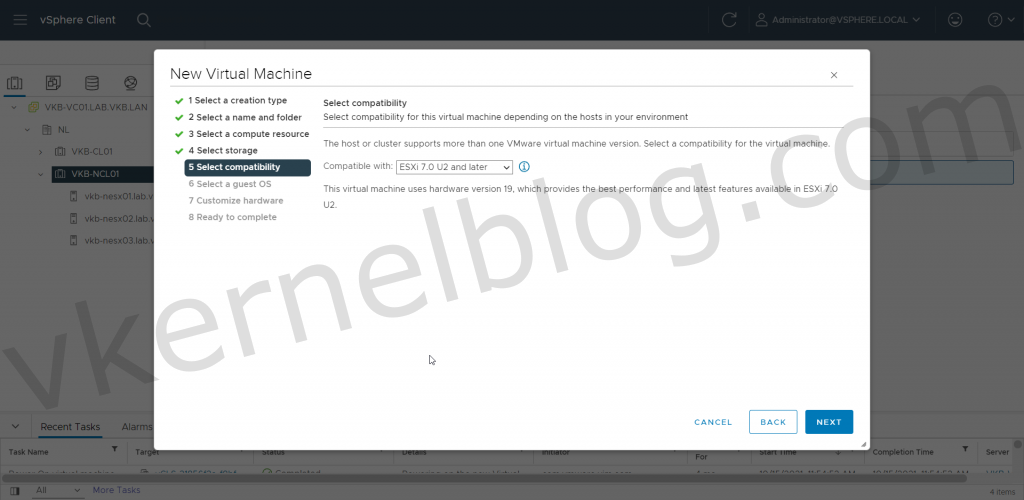
Below, I am creating a Windows 10 Pro virtual machine in a nested ESXi 6.7 vSphere environment. Here I am choosing the ESXi 6.7 and later compatibility level (which I believe is a requirement, however, will update the post if I find otherwise).
After creating the new Windows 10 VM and installing Windows, I powered off the virtual machine (powering off is required to enable the feature) and configured the VM for Virtualization Based Security. This is accomplished with a single checkbox! Right click a virtual machine choose Edit Settings >> VM Options. You will see the Virtualization Based Security option. Click the checkbox to Enable. Note the message that is displayed when the checkbox is enabled.
Requires EFI, which might make the guest OS unbootable. EFI, Secure Boot, IOMMU and Hardware Virtualization will be enabled on reboot.
Now, after booting the Windows 10 Pro 1803 VM back up, let’s go through the steps to enable Virtualization Based Security. The next two steps can be done in either order, however, I like to enable the group policy setting first for VBS and then enable Hyper-V in Windows 10 so that after the feature is enabled, the one reboot is all that needs to take place. In my testing, these appear to be able to be done in either order.
To navigate to the Group Policy setting that needs to be enabled, open up the local group policy editor by typing gpedit.msc in a run menu. Navigate to Computer Configuration >> Administrative Templates >> System > Device Guard >> Turn On Virtualization Based Security. Set the policy to Enabled. We will also set the following settings:
- Select Platform Security level: Secure Boot and DMA Protection
- Virtualization Based Protection of Code Integrity: Enabled with UEFI lock
- Credential Guard Configuration: Enabled with UEFI lock
If you want to be able to enable or disable this setting remotely choose the Enabled without UEFI lock option.
Now that we have the option turned on in vSphere 6.7 and the group policy entry set for the Windows 10 Pro 1803 virtual machine, we enable the Hyper-V hypervisor in Windows. An easy way to get to the Turn Windows features on or off is the appwiz.cpl command. Choose the Hyper-V checkbox then select only the Hyper-V Platform and Hyper-V Hypervisor options. You can enable the Hyper-V Management Tools if you want, however, they are not needed for VBS.
After enabling the Hyper-V feature, you will be asked to restart Windows.
Verifying Virtualization Based Security Is Enabled in Windows 10
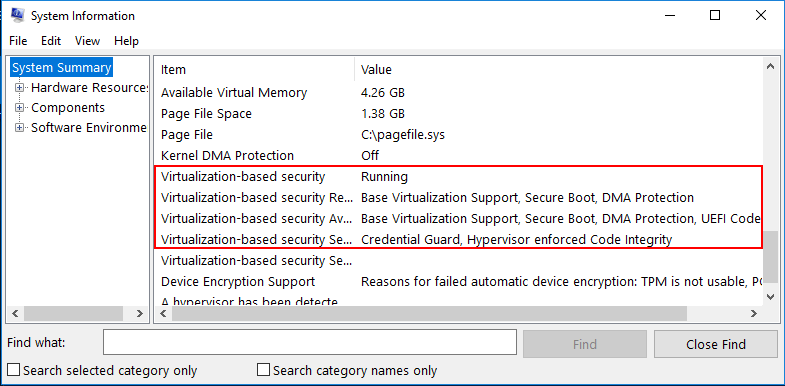
To verify that Virtualization Based Security is enabled in our Windows 10 Pro 1803 workstation, we can use the msinfo32.exe command. Simply type it at a run or search menu and we will take a look at the entries presented. Notice under the System Summary node, if you scroll down, you will see the entries highlighted below. Notably, we want to see the following:
- Virtualization-based security is Running
- Virtualization-based security services configured – Credential Guard, Hypervisor enforced Code Integrity
Takeaways
Enabling Windows 10 Virtualization Based Security with vSphere 6.7 is a great way to make sure that running Windows 10 or Windows Server 2016 virtual machines are even further protected with secure memory areas being restricted. This makes attacks such as “pass the hash” exponentially more difficult to exploit. VMware has made turning this feature on extremely easy with vSphere 6.7. Literally a single checkbox enables all the needed hardware emulated features to allow Windows 10/Server 2016 to be able to setup in VBS mode using Hyper-V in a nested configuration within vSphere 6.7. Check out these and other great security enhancements with vSphere 6.7. A great resource is the VMware security blog with Mike Foley. Check that out here: https://blogs.vmware.com/vsphere/2018/04/introducing-vsphere-6-7-security.html
Virtualization Based Security (VBS) is a Microsoft Windows feature that was introduced in Windows 10, Windows Server 2016 and higher. Microsoft VBS uses hardware virtualization features to create and isolate a secure region of memory from the normal operating system. For example, Windows can use this isolated memory space to store credentials (Credential Guard) to mitigate the pass the hash vulnerability.
Virtualization Based Security effectively reduces the Windows attack surface, so even if a malicious actor gains access to the OS kernel, the protected content can prevent code execution and the access of secrets, such as system credentials
The communication between the Windows OS and the credentials that are stored in an isolated memory space, will be done over RPC calls.
Requirements
VM Hardware Requirements
- VM hardware 14 or higher.
- Guest OS that supports Virtualized based Security that exists of the following VM hardware settings.
- IOMMU
- Hardware virtualization
- EUFI boot firmware
- Secureboot
- vTPM (Optionally)
The following will also be needed when using vTPM:
vCenter Requirements
- Enterprise plus license (for the native key provider)
- ESXI Cluster
- Key Provider (Native or 3th party)
Configure VMware Native Key Provider
Let me start by saying vTPM is not required to have to implement Microsoft VBS with Credential Guard. Credential Guard will work, but it will be less secure.
The only way to assign a Trusted Platform module device to a VM, is by having a configured key provider in vCenter (Native or 3th party). The key provider need to be maintained, so it will be an additional dependency in the infrastructure.
In the previous versions of vSphere, you could only configure external key providers like HyTrust to enable those security features. Guess what? VMware has finally released a native key provider called vSphere Native Key Provider.
Click here for more information about Key Providers.
We will use the vSphere Native Key Provider in this example.
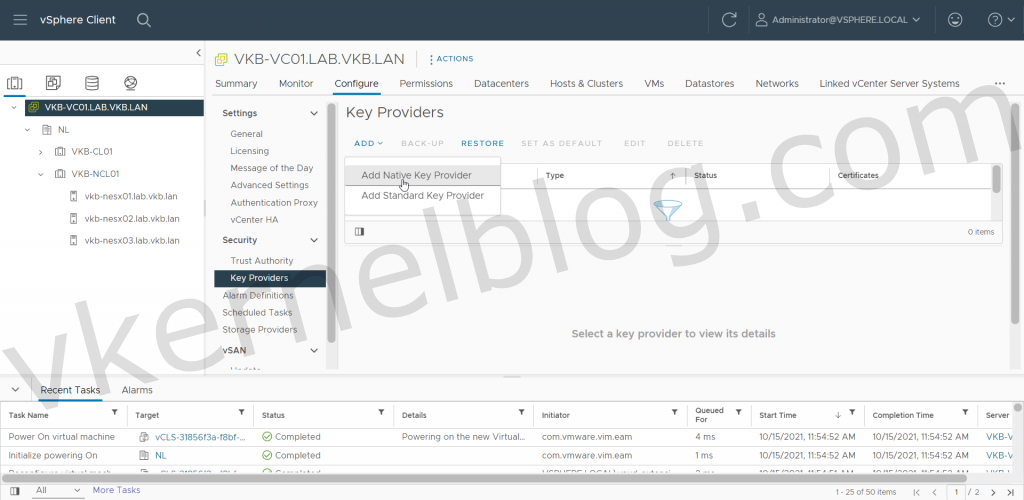
1. Login to the vCenter web GUI, click on the vCenter object, click on Configure and select Key Providers.
2. Click on the ADD button and select ADD NATIVE KEY PROVIDERS to open the wizard.
3. Enter a name for the vSphere Native Key Provider and if needed enable the Use Key Provider only with TPM protected ESXI hosts if needed. In my lab, I disabled this option, because i’m using nested ESXI hosts.
Note: Use Key Provider only with TPM protected ESXI hosts will only enable the vSphere Key Provider on hosts that that physcially has a TPM 2.0 chip.
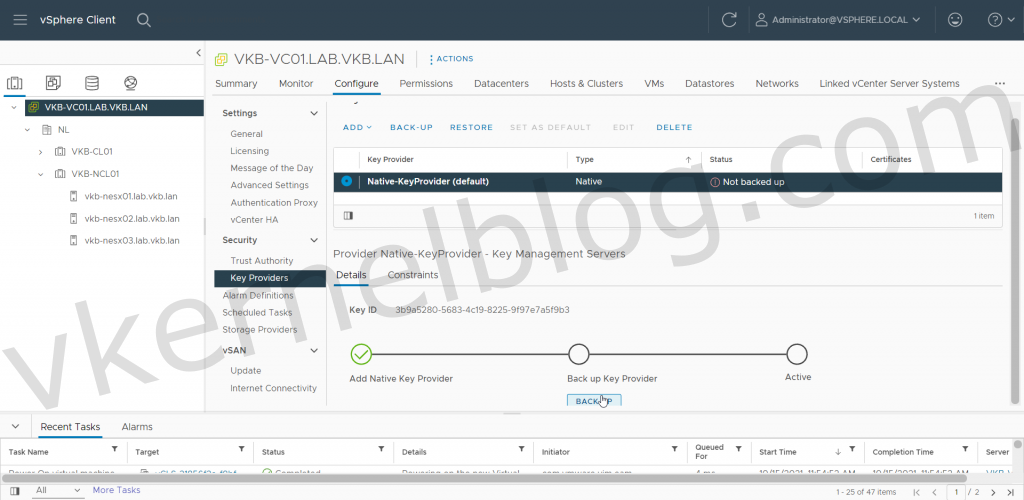
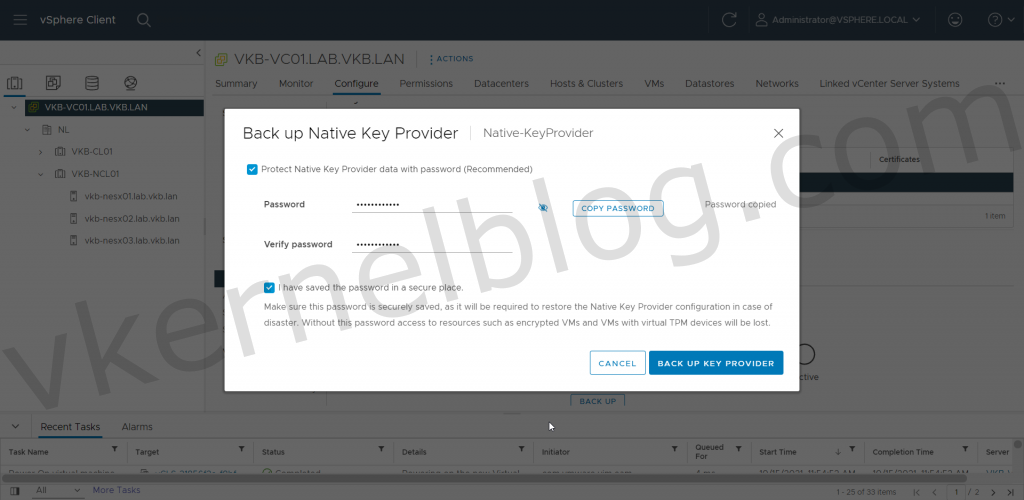
4. Create a backup of the vSphere Native Key Provider.
Microsoft VBS
Configure VBS in an existing Windows VM
Note: You should only enable the Virtualized Based Security option when the Windows Guest OS has been installed with an EUFI firmware. Converting from BIOS to EUFI could be a hard time in Windows.
- Select the Windows VM and click on edit settings.
- Click on the VM Options tab.
- Enable the Virtualized Based Security option.
- Click on Save to commit the changes.
Configure VBS in a new Windows VM
1. Create a new Windows VM (Windows 10, Windows 2016 or higher).
2. Select the latest compatibility mode to get the latest VM Hardware version.
3. Select a compatible Windows Guest OS Family that supports Microsoft Virtualized Based Security.
Have you noticed the guest OS output in the VM summary? This only means that the VM hardware has been optimized for the use of VBS. VBS still needs to be enabled inside the Guest OS.
Configure VBS in Guest OS
The virtual machine CLT02 has been configured with the required VM hardware components and is now ready to be configured for VBS in the Guest OS. Let’s have a look at the current System Information > System Summary on the CLT02 VM without VBS enabled in the Guest OS:
Next step is to enable the Microsoft VBS within the Guest OS with the security options you would like to have configured. More information can be found on the official Microsoft website.
- Open the local group policy with gpedit.msc and browse to Computer Configuration > Administrative Templates > System > Device Guard.
- Enable the setting: Turn On Virtualization Based Security.
- Configure the VBS options: (Configure the options according your needs.)
| Option | Value | Info |
| Select Platform Security Level | Secure Boot and DMA protection | Among the commands that follow, you can choose settings for Secure Boot and Secure Boot with DMA. In most situations, we recommend that you choose Secure Boot. This option provides Secure Boot with as much protection as is supported by a given computer’s hardware. A computer with input/output memory management units (IOMMUs) will have Secure Boot with DMA protection. A computer without IOMMUs will simply have Secure Boot enabled. |
| Virtualization Based Protection Of Code Integrity | Enabled with EUFI Lock | This setting enables virtualization based protection of Kernel Mode Code Integrity. When this is enabled, kernel mode memory protections are enforced and the Code Integrity validation path is protected by the Virtualization Based Security feature.
The “Enabled with UEFI lock” option ensures that Virtualization Based Protection of Code Integrity cannot be disabled remotely. In order to disable the feature, you must set the Group Policy to “Disabled” as well as remove the security functionality from each computer, with a physically present user, in order to clear configuration persisted in UEFI |
| Require EUFI Memory Attributes Table | Checked | The “Require UEFI Memory Attributes Table” option will only enable Virtualization Based Protection of Code Integrity on devices with UEFI firmware support for the Memory Attributes Table. Devices without the UEFI Memory Attributes Table may have firmware that is incompatible with Virtualization Based Protection of Code Integrity which in some cases can lead to crashes or data loss or incompatibility with certain plug-in cards. If not setting this option the targeted devices should be tested to ensure compatibility. |
| Credential Guard Configuration | Enabled with EUFI Lock | This setting lets users turn on Credential Guard with virtualization-based security to help protect credentials.
The “Enabled with UEFI lock” option ensures that Virtualization Based Protection of Code Integrity cannot be disabled remotely. In order to disable the feature, you must set the Group Policy to “Disabled” as well as remove the security functionality from each computer, with a physically present user, in order to clear configuration persisted in UEFI |
| Secure Launch Configuration | Enabled | This setting sets the configuration of Secure Launch to secure the boot chain. |
4. Reboot the server to activate the VBS functionalities.
Verify with Device Guard and Credential Guard hardware readiness tool
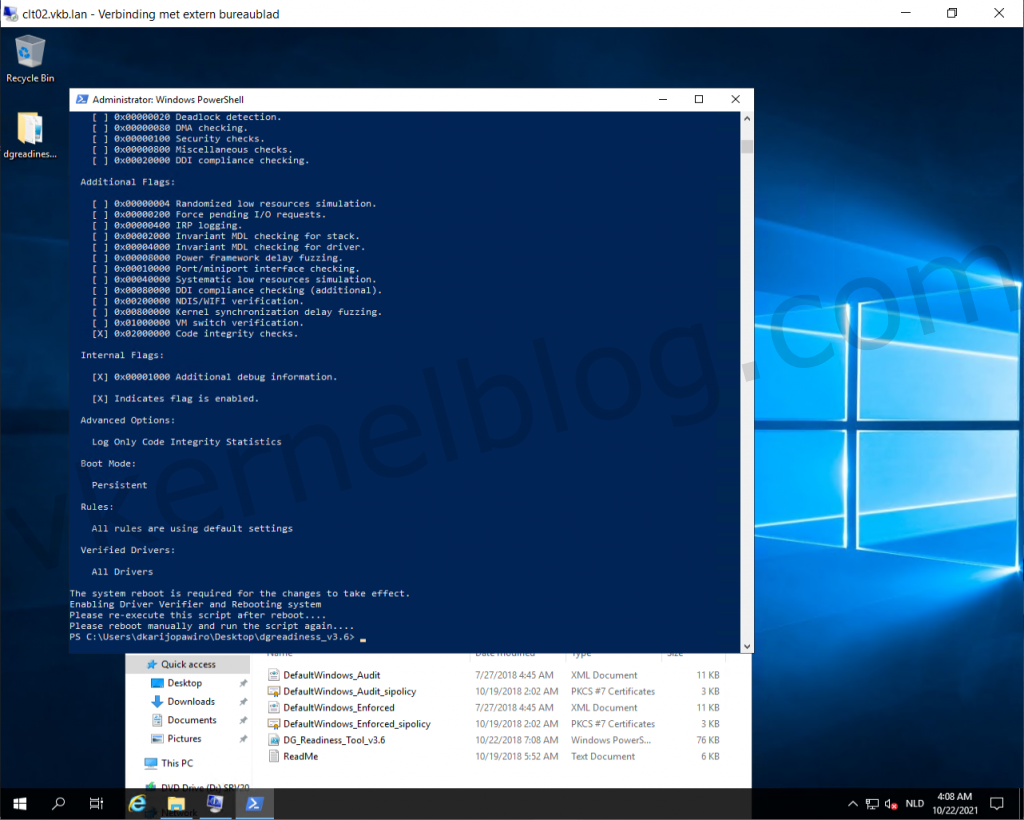
Microsoft released a PowerShell script to verify the readiness of VBS with those security options on your Windows system. You can also enable and disable VBS security options with it. The script can be downloaded from here.
- Download the Device Guard and Credential Guard hardware readiness tool powershell script.
- Run the following command to verify if this device is Device Guard and Credential Guard capable.
.DG_Readiness_Tool_v3.6.ps1 -Capable
Note: Running the script for the first time requires a reboot, because of the Driver verifier that needs to be enabled.
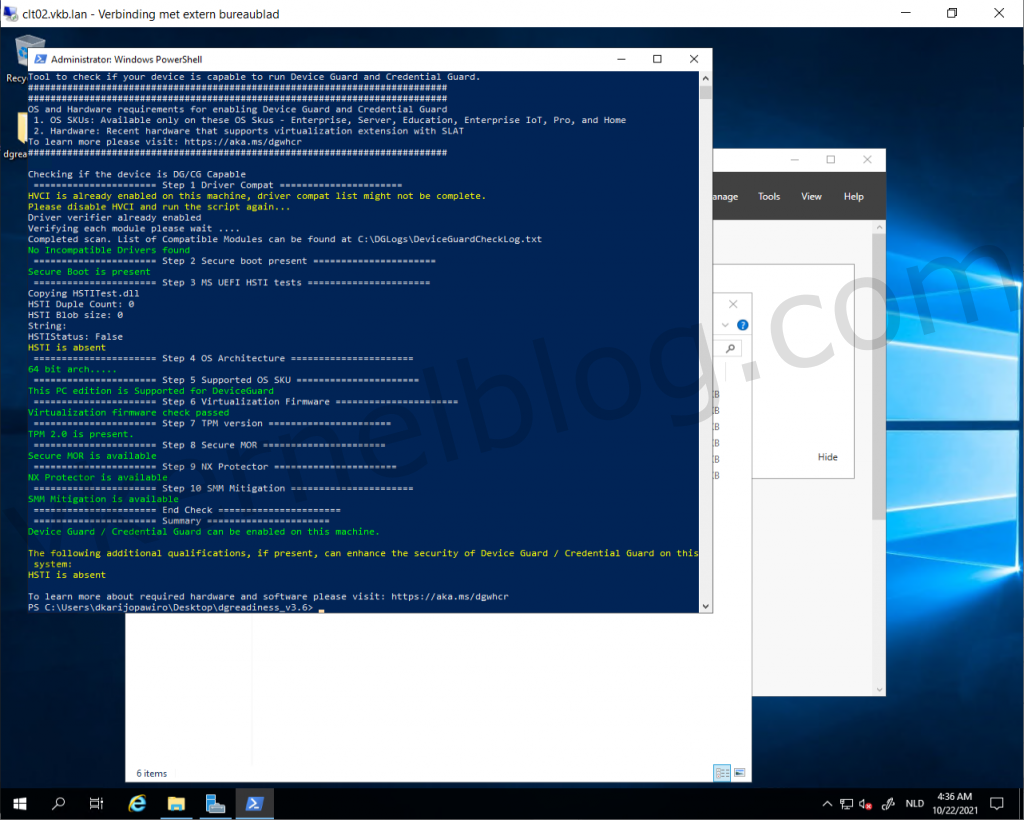
3. Re-run the script again and this time you would see something like this.
HVCI and Credential Guard is enabled, the only thing that is absent is TPM.
4. Power off the Windows VM and add a Trusted Platform Module (vTPM).
Note: if you cannot see Trusted Platform Module under Other devices you probably don’t have a configured Key Provider in vCenter.
5. Power on the Windows VM and perform the same powershell command.
We now have VBS running with Credential Guard on our Windows 2019 test VM.
Pass the Hash tests
On a machine without VBS
In my home lab, I have a Windows 2019 VM with VBS not enabled. Let’s see perform the Pass The Hash method on this VM. I’m using the Mimikatz tool for this demo. Once a user logged into Windows, the credentials will be saved in the Local Security Authority in memory. With Mimikatz, we can exploit this and retrieve NTLM hashes. With these hashes, we can decrypt the hash to retrieve the password in plain text, and we can also create an authentication token to execute tasks on other servers for example.
- Let’s start with logging in with a testuser that has local administrator rights on a member server.
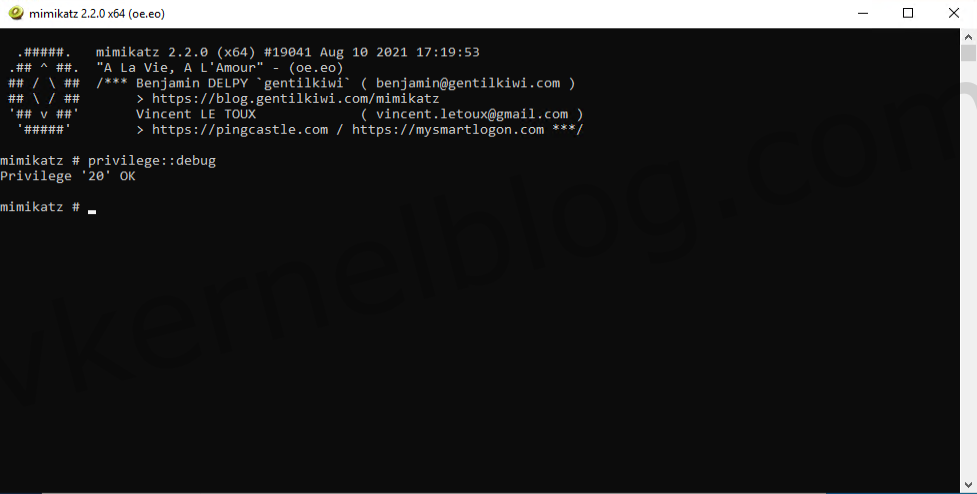
2. Start Mimikatz and perform the following command to get debug rights (this or Local System rights is required for many Mimikatz commands).
privilege::debug
3. Let’s perform the following command to lists all available provider credentials. This usually shows recently logged on user and computer credentials.
sekurlsa::logonpasswords
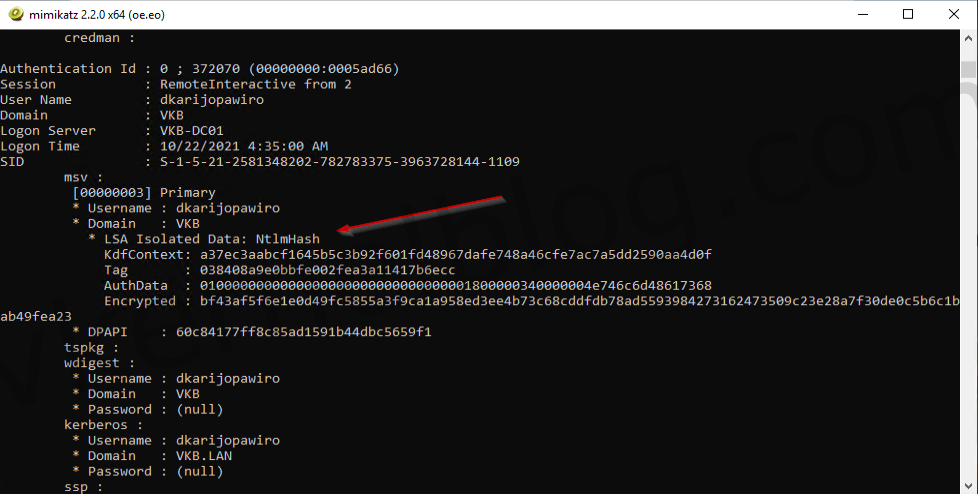
We now have the NTLM hash of the user that has domain admin privileges.
Decrypt the hash
We can easily decrypt the hash to retrieve the password in plain text on hashes.com.
Create a authentication token with the hash.
We can also use the hash to create an authentication token to log on the domain controller for example. This can be done with Mimikatz as well.
- use the following command to create an authentication token:
sekurlsa::pth /user:domainuser /domain:vkb.lan /ntlm:hash
The authentication token has been created and a new CMD window opened. When verifying the active user with whoami, I can still see that the active user is named testuser.
2. Let’s switch over to powershell by entering the word powershell.
3. Perform the following command to start a powershell session to the domain controller with a domain admin user by using the authentication token:
Enter-PSSession -ComputerName domaincontroller.fqdn
We now have a powershell session to the domain controller with a domain admin user. This shows to you all, how easy the Pass The Hash method is.
On a machine with VBS
Microsoft VBS should mitigate the Pass The Hash hack by storing the credentials in an isolated memory space. Let’s perform the same steps on CLT02 that has VBS enabled.
- Open Mimikatz and get the debug privileges.
- Retrieve the logon passwords.
We are now unable to see the NTLM hash in Mimikatz, because the credentials are stored in an isolated memory space.
VMware vSphere 6.7 offers the ability to enable virtualization-based security (VBS) for virtual machines. Let’s find out what kind of protection this setting provides, what’s needed to get it going and how to configure a virtual Domain Controller to use it.
Virtualization-based Security (VBS) uses virtualization features to create and isolate a secure region of memory from the normal Operating System. Windows Server can use this «virtual secure mode» to host a number of security solutions, providing them with greatly increased protection from vulnerabilities in the operating system, and preventing the use of malicious exploits which attempt to defeat protections.
Benefits of using Virtualization-based Security
Virtualization-based Security (VBS) uses the Windows hypervisor to create this virtual secure mode, and to enforce restrictions which protect vital system and Operating System resources, or to protect security assets such as authenticated user credentials.
With the increased protections offered by Virtualization-based Security, even if malware gains access to the Operating System’s kernel, the possible exploits can be greatly limited and contained because the hypervisor can prevent the malware from executing code or accessing platform secrets.
For Active Directory Domain Controllers, specifically, Virtualization-based Security offers:
Secure Boot
The Secure Boot feature in Windows Server 2016, and up, is designed to protect the virtual machine from malicious boot loaders. In traditional Basic Input/Output System (BIOS)-based systems, a rootkit may replace the Windows boot loader, remaining invisible and undetectable on the Domain Controller.
With Secure Boot, a virtual machine no longer boots with BIOS, but with Unified Extensible Firmware Interface (UEFI). UEFI checks the signature of the boot loader before launching, detecting any malware impersonating, replacing or tampering with the Windows boot loader.
Direct Memory Access (DMA) Protection
Direct Memory Access (DMA) attacks try to grab the memory of a running Operating System to gain access to BitLocker keys and other information from the memory. In vSphere, you can take advantage of an Input/Output Memory Management Unit (IOMMU) to connect a DMA-capable I/O bus to the main memory.
With IOMMU, memory of Windows Server 2016 installations, and up, is protected from malicious devices that are attempting DMA attacks and faulty devices that are attempting errant memory transfers because a device cannot read or write to memory that has not been explicitly allocated (mapped or re-mapped) for it.
Hypervisor-enforced Code Integrity (HVCI)
Kernel-mode Code Integrity enforces kernel-mode memory protections by protecting the Code Integrity validation path with Virtualization-based Security. All drivers in the virtual machine must be compatible with virtualization-based protection of code integrity; otherwise, the virtual machine fails.
Code Integrity (CI) Policies
Historically, most malware has been unsigned. Simply by deploying code integrity policies, organizations can get immediately protection against unsigned malware. By using Code Integrity policies, an enterprise can also select exactly which binaries can run in both user mode and kernel mode. When completely enforced, it will only load specific applications or software with specific signatures.
Note:
Code Integrity policies are independent of Hypervisor-enforced Code Integrity (HVCI). However, when using CI policies without HVCI, the enforcement will not be as strong as when using CI Policies with HVCI.
Note:
Windows Server 2019 expands on the CI policies feature in Windows Server 2016 by offering built-in CI policies for robust yet quick deployment of Code Integrity.
Other features like Application Guard, Credential Guard and Windows Sandbox, operating in their separate memory spaces are features targeted towards Windows-based devices and are not applicable to Domain Controllers. Well… when you adhere to the rule of thumb not to browse the Internet and install all kinds of software on your Domain Controllers, that is.
Note:
Do not configure Credential Guard on Domain Controllers.
Getting Ready
For Virtualization-based Security (VBS) you’ll need to meet the following requirements:
- At least one ESXi host running VMware vSphere 6.7, or up, managed by vSphere
- At least one virtual machine running hardware version 14 (Compatible only with ESXi 6.7 and later), or up, configured with Virtualization Based Security. and installed with Windows Server 2016, or a later version of Windows Server in this virtualization state.
Note:
The Virtualization Base Security option enables CPU virtualization extensions, IOMMU, EFI firmware and Secure Boot.
Configuring Virtualization-based Security
Configuring Virtualization-based Security consists of three steps:
- Configure the right virtual machine settings on vSphere 6.7
- Configure the right security settings in the virtual Domain Controller
- Install the Hyper-V feature on the virtual Domain Controller
Configure the right virtual machine settings
First, we need to create a virtual Domain Controller that meets the requirements.
ESXi 6.7
When creating a new virtual machine for a Domain Controller, on the 2 Select a name and guest OS page of the New virtual machine wizard, make sure as a Compatibility level you pick ESXi 6.7 virtual machine (or up), resulting in hardware version 14. Pick Microsoft Windows Server 2016 or later (64-bit) as the Gues OS version. Then, make sure you select the option Enable Windows Virtualization Based Security:
vSphere 6.7
In the vSphere Web Client, when creating a new virtual machine, take care of the following settings:
- On the Select compatibility page of the New Virtual Machine wizard, select ESXi 6.7 and later. The accompanying text below this settings will then indicate that This virtual machine uses hardware version 14, which provides the best performance and latest features available in ESXi 6.7.
- On the Select a guest OS page of the New Virtual Machine wizard, specify Microsoft Windows Server 2016 or later (64-bit) as the Guest OS Version and select the option Enable Windows Virtualization Based Security:
Configure the right security settings in the virtual Domain Controller
After installing Windows Server 2016, or up, on the new virtual Domain Controller and configuring it as a Domain Controller for (one of) your Active Directory domain(s), perform the following actions in the virtual machine or on any other domain-joined machine that has the Group Policy Management Console feature installed:
- Sign in with an account that has sufficient permissions in Active Directory to create Group Policy objects and link them to the Domain Controllers Organizational Unit (OU). Typically, a member of the Domain Admins group has these permissions.
- Open the Group Policy Managment console, by either:
- Picking it from the Tools menu in Server Manager.
- Selecting it in the Start Menu from the Windows Administrative Tools folder.
- Clicking the Start button and typing gpmc.msc followed by a press of the Enter button on the keyboard.
- right-clicking the Start button and typing gpmc.msc followed by a click on the OK button.
- The Group Policy Management window appears.
- In the left navigation pane, expand the forest node, then the Domains node, than your domain. Select the Domain Controllers Organizational Unit (OU).
- Right-click Domain Controllers and select the Create a GPO in this domain, and Link it here… menu option.
The New GPO pop-up window appears. - In the New GPO pop-up window, type a name for the Group Policy object.
- Click the OK button.
- In the left navigation pane, expand the Domain Controllers OU and select the newly created Group Policy object.
- Dismiss the Group Policy Management Console pop-up telling you that You have selected a link to a Group Policy Object (GPO). Except for changes to link properties, changes you make here are global to the GPO, and will impact all other locations where this GPO is linked. by clicking the OK button, if it pops up.
- Right-click the Group Policy object and select Edit… from the context menu.
The Group Policy Management Editor window appears. - In the left navigation pane of the Group Policy Management Editor window, expand the Computer Configuration node, then the Policies node, the Administrative Templates node, the System, and finally the Device Guard node.
- In the main pane, double-click the Turn on Virtualization Based Security group policy setting.
The Turn on Virtalization Based Security window appears - In the top part of the Group Policy setting, select the Enabled option.
- At the left Options: pane, select the following options:
- For Virtualization Based Protection of Code Integrity:, select Enabled without lock from the drop-down list. As we are configuring Virtualization-based Security through Group Policy, we’d want Group Policy to be able to remove the settings remotely as well, if need be.
- Enable the Require UEFI Memory Attributes Table option.
- For Secure Launch Configuration:, select Enabled from the drop-down list.
- Click the OK button at the bottom of the Turn on Virtualization Based Security window to save the Group Policy settings and close the Turn on Virtualization Based Security window:
- Close the Group Policy Management Editor window.
- In the left navigation pane of the Group Policy Management window, right-click the Domain Controllers OU. Select Group Policy Update… from the context menu.
The Force Group Policy update window appears. - Click the Yes button to answer the question Are you sure you want to update policy for these computers?
The Remote Group Policy update results window appears. - Click the Close button to close the window.
- Close the Group Policy Management window.
Install the Hyper-V feature on the virtual Domain Controller
If you’ve managed the Group Policy settings from another machine than the virtualized Domain Controller running Windows Server 2016, or up, sign into the Domain Controller with an Active Directory account that has administrative privileges on the Domain Controller.
Run the following lines of Windows PowerShell in an elevated PowerShell window on each Domain Controller that you want enabled with Virtualization-based Security:
Install-WindowsFeature Hyper-V
Restart-Computer
Concluding
Virtualization-based Security offers benefits for virtualized Domain Controllers running Windows Server 2016, and up. It uses nested virtualization, where Microsoft Hyper-V offers the secure memory regions and vSphere offers the virtualization platform as it would do for any virtual machine.
Further reading
Virtualization-based Security (VBS)
Introducing support for Virtualization Based Security in vSphere 6.7
Overview of Device Guard in Windows Server 2016
Enabling Windows 10 Virtualization Based Security with vSphere 6.7