Since I’m very new to SSL certificates, and the creation and usage of them I figured maybe StackOverflow members can help me out.
I’m from Holland, the common way of online payments is by implementing iDEAL. An online payment protocol supported by the major banks. I have to implement a ‘professional’ version. This includes creating a RSA private key. Based on that key I have to create a certificate and upload it to the webserver.
I’m on a Windows machine and completely confused what to do. I took a look at the OpenSSL website, because the manual forwarded me to that website to get a SSL Toolkit.
The manual provides two commands which have to be executed in order to create a RSA key and a certificate.
The commands are:
openssl genrsa -des3 –out priv.pem -passout pass:myPassword 1024
and
openssl req -x509 -new -key priv.pem -passin pass:myPassword -days 3650 -out cert.cer
Is there a way I can do this by a utility on a windows machine? I’ve downloaded PuTTy KeyGenerator. But I’m not sure what to do, I’ve created a key (SSH-2 RSA, whatever that is..) but how do I create a certificate with that key?
I’ve seen lately many requests in our forums, and I personally received some, about how to generate and manage SSL certificates on Windows machines. It seems one of those topics that is always hot, especially these days with all the services available over public internet connections, and all the scary stories about security breaches.
Whatever “web” service you are willing to execute and publish over the internet, an SSL certificate can protect you as a provider, and your users connecting to it. It’s extremely important to deploy properly configured SSL certificates, yet many don’t do this. Why? Maybe because only Microsoft IIS (Internet Information Services) has an easy wizard to accomplish these tasks. But if you follow this quick tutorial, SSL certificate will be easy to install on any Windows machine, with our without IIS. If you are using or planning to use Veeam software solutions, you can use SSL certificates, for example, to protect the access for example to Enterprise Manager or Cloud Connect.
Several software products have the possibility to generate and use a self-signed certificate. This is a quick and easy method to complete deployments and to test them, but gives no security to users, since they cannot verify the certificate, and thus the authenticity of the service provider.
When a user connects to one of these services, this is the result when a self-signed certificate is used:
In order to properly protect the service and give its users guaranteed security, you should use a proper and generally recognized certificate, issued by one of the Certification Authorities recognized by internet browsers and operating systems.
Step 1: Create the Certificate Signing Request (CSR)
In a public key infrastructure (PKI), a certificate signing request (CSR or certification request) is the text created by the “applicant” (the Service Provider running the service in our case) to a Certificate Authority, that in return sends back a Signed Certificate. It’s like sending out an order, that is then processed following the instructions in it, and the ordered goods are finally delivered.
When creating the CSR, the applicant also generates a key pair and keeps the private key secret. The CSR contains information about the applicant, like the company information and the service DNS, which are signed using the applicant’s private key. The CSR also contains the public key chosen by the applicant.
The first operation you should do is to decide the public “fully qualified domain name” the service will listen to; this will be the DNS name users will contact to use the service; just like opening a website. This name should match the one used in DNS and the one used in the CSR.
To obtain a real certificate, a real domain name must be used. So, in this tutorial, I used my blog’s domain virtualtothecore.com, and the FQDN is:
cc.virtualtothecore.com
In order to generate the CSR, on the Windows Server, you need first to create with a text editor a .inf file. This file (it can be called request.inf) should contain a text like this example:
;----------------- request.inf -----------------
[Version]
Signature="$Windows NT$"
[NewRequest]
Subject = "CN= cc.virtualtothecore.com, OU=IT, O=Skunkworks, L=Milan, S=Lombardy, C=IT"; replace attributes in this line
KeySpec = 1
KeyLength = 2048
; Can be 2048, 4096, 8192, or 16384.
; Larger key sizes are more secure, but have
; a greater impact on performance.
Exportable = TRUE
FriendlyName = "cc"
MachineKeySet = TRUE
SMIME = False
PrivateKeyArchive = FALSE
UserProtected = FALSE
UseExistingKeySet = FALSE
ProviderName = "Microsoft RSA SChannel Cryptographic Provider"
ProviderType = 12
RequestType = PKCS10
KeyUsage = 0xa0
[EnhancedKeyUsageExtension]
OID=1.3.6.1.5.5.7.3.1 ; this is for Server Authentication
[RequestAttributes]
; SAN="dns=FQDN_you_require&dns=other_FQDN_you_require"
The parts in red are to be changed with the specific values of your service, and some informations about your company. Skunkworks, by the way, is the name I gave to my home lab.
After the configuration file has been edited, it can be saved in a useful location like a dedicated folder c:certificates. Then, open a command prompt with Administrator rights (right click and select “Run as Administrator”), move into c:certificates and run this command:
certreq -new request.inf certreq.txt
If you open the certreq.txt file with a text editor, its content is like this:
—–BEGIN NEW CERTIFICATE REQUEST—–
MIID9jCCAt4CAQAwdTELMAkGA1UEBhMCSVQxETAPBgNVBAgMCExvbWJhcmR5MQ8w
DQYDVQQHDAZWYXJlc2UxEzARBgNVBAoMClNrdW5rd29ya3MxCzAJBgNVBAsMAklU
MSAwHgYDVQQDDBdjYy52aXJ0dWFsdG90aGVjb3JlLmNvbTCCASIwDQYJKoZIhvcN
AQEBBQADggEPADCCAQoCggEBAJUBkduH0xQfJbnt2ryIjdn5z8euMM4zHyd4CFBd
2eCXAnfaskOc3F9eW9zP1KMk0Z/8K9GfezZDkMcbno5hnIkuwBcLoHJUeiWQDm1a
Dutxvgvo1RO2TEQJes5CBKB7vrEakRCco3Cq26rXEparx1MjdmcOVyk2weF9TJNI
UIFr1Tadw/NWCLqwUw4ZGBsDJL0lftuQe0VmxJciZC1EZQXppsXSanSdaIZECJzH
USu0wA5nZL9pltvO3593Kqr-qYkbocRj+T2hixA7n+Y8Bi5pO6pDOs/UdCQodteb
0qCcLUCXBtQoimEL7uwtAPQ07RfiTX9EIeeIxX0+FHD6T7UCAwEAAaCCATowGgYK
KwYBBAGCNw0CAzEMFgo2LjIuOTIEMC4yMFMGCSqGSIb3DQEJDjFGMEQwDgYDVR0P
AQH/BAQDAgWgMBMGA1UdJQQMMAoGCCsGAQUFBwMBMB0GA1UdDgQWBBTEaoWXriXL
I1DePK17Mxh2s8ryRzBTBgkrBgEEAYI3FRQxRjBEAgEJDBZ2YnIuY2xvdWRjb25u
ZWN0LmxvY2FsDBpDTE9VRENPTk5FQ1RcYWRtaW5pc3RyYXRvcgwLY2VydHJlcS5l
eGUwcgYKKwYBBAGCNw0CAjFkMGICAQEeWgBNAGkAYwByAG8AcwBvAGYAdAAgAFIA
UwBBACAAUwBDAGgAYQBuAG4AZQBsACAAQwByAHkAcAB0AG8AZwByAGEAcABoAGkA
YwAgAFAAcgBvAHYAaQBkAGUAcgMBADANBgkqhkiG9w0BAQUFAAOCAQEAQaUqU2Y9
7wH3JhgiDvn85HEZq+60a4WqgXXHiriIG1FnJwuzdG3k+m185N+smSX/VlIXT9fI
Tak034muIRpqwNJR7fz4gPaLnmNowa3Don1la8TihI47Pezl8h76ig04hFfSOUH7
Z4Atq+2XZ55lj/mRksq2oVZUeEzHCf0V7MSQD6M3Yf/WLJGLZG/kDexwDz2I5W9q
6vu2OwmD0eA2mHW1RjycqBJktyaZ7Hy6BF1T1F3AVyJYpTVMT/IbDAzMYZQ4U1/b
sKD5ZHkY2WhrRkD4D2UQpFShPdlaCYf3OP9F9FbLY4mZ7yKaQxrZWaKqRzKEaEMP
ng8IKtDYJRCVAw==
—–END NEW CERTIFICATE REQUEST—–
This is the generated CSR you will use.
Step 2: Obtain a Signed Certificate
With the Certificate Request correctly created, it’s time to get a signed certificate from a Certificate Authority. There are several online services where you can get a certificate, and some of them also offer free time-limited certificates that are useful to test real SSL connections at no expense.
The involved steps vary depending on the selected Certificate Authority, but they usually involve a validation of the CSR, a check against the registered domain via whois protocol to collect the registrant email address, and a verification procedure sent to this email to validate the authenticity of the request.
Whatever are the differences in the procedures, the final result is a Signed Certificate. It can usually be retrieved in text format or downloaded, and its content is going to be like this:
—–BEGIN CERTIFICATE—–
MIIFLTCCBBWgAwIBAgIQLgiJg4U3yijkhjzA5FK1VjANBgkqhkiG9w0BAQUFADBy
MQswCQYDVQQGEwJHQjEbMBkGA1UECBMSR3JlYXRlciBNYW5jaGVzdGVyMRAwDgYD
VQQHEwdTYWxmb3JkMRowGAYDVQQKExFDT01PRE8gQ0EgTGltaXRlZDEYMBYGA1UE
AxMPRXNzZW50aWFsU1NMIENBMB4XDTE0MDgwNTAwMDAwMFoXDTE0MTEwMzIzNTk1
OVowWDEhMB8GA1UECxMYRG9tYWluIENvbnRyb2wgVmFsaWRhdGVkMREwDwYDVQQL
EwhGcmVlIFNTTDEgMB4GA1UEAxMXY2MudmlydHVhbHRvdGhlY29yZS5jb20wggEi
MA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQCVAZHbh9MUHyW57dq8iI3Z+c/H
rjDOMx8neAhQXdnglwJ32rJDnNxfXlvcz9SjJNGf/CvRn3s2Q5DHG56OYZyJLsAX
C6ByVHolkA5tWg7rcb4L6NUTtkxECXrOQgSge76xGpEQnKNwqtuq1xKWq8dTI3Zn
DlcpNsHhfUyTSFCBa9U2ncPzVgi6sFMOGRgbAyS9JX7bkHtFZsSXImQtRGUF6abF
0mp0nWiGRAicx1ErtMAOZ2S/aZbbzt+fdyqq/qmJG6HEY/k9oYsQO5/mPAYuaTuq
QzrP1HQkKHbXm9KgnC1AlwbUKIphC+7sLQD0NO0X4k1/RCHniMV9PhRw+k+1AgMB
AAGjggHXMIIB0zAfBgNVHSMEGDAWgBTay+qtWwhdzP/jlTOSeVVxjj0+DAdBgNV
HQ4EFgQUxGqFl64lyyNQ3jytezMYdrPK8kcwDgYDVR0PAQH/BAQDAgWgMAwGA1Ud
EwEB/wQCMAAwNAYDVR0lBC0wKwYIKwYBBQUHAwEGCCsGAQUFBwMCBgorBgEEAYI3
CgMDBglghkgBhvhCBAEwTwYDVR0gBEgwRjA6BgsrBgEEAbIxAQICBzArMCkGCCsG
AQUFBwIBFh1odHRwczovL3NlY3VyZS5jb21vZG8uY29tL0NQUzAIBgZngQwBAgEw
OwYDVR0fBDQwMjAwoC6gLIYqaHR0cDovL2NybC5jb21vZG9jYS5jb20vRXNzZW50
aWFsU1NMQ0EuY3JsMG4GCCsGAQUFBwEBBGIwYDA4BggrBgEFBQcwAoYsaHR0cDov
L2NydC5jb21vZG9jYS5jb20vRXNzZW50aWFsU1NMQ0Ffmi5jcnQwJAYIKwYBBQUH
MAGGGGh0dHA6Ly9vY3NwLmNvbW9kb2NhLmNvbTA/BgNVHREEODA2ghdjYy52aXJ0
dWFsdG90aGVjb3JlLmNvbYIbd3d3LmnjLnZpcnR1YWx0b3RoZWNvcmUuY29tMA0G
CSqGSIb3DQEBBQUAA4IBAQCEUHCth5o9h6MYINOnx6GMH3NchYo+BXPtCMsUyf2R
CB/iuteEODUW8Up+UWffF8tFSb9eIuNXyjhzKxqWcSms4qQkvVcH7WI4EZNvczzz
e8WGvbEckoCeGapYS+r5Z6hG865/BX/iiCHFyEB7UwR4xYtMis4XxFNGZLhtOX6D
zmLyVVTYFLyrhrFqOSxjRD25yfKdvG3dKKVBIwnb4xKdNZX/37KSkW15lIz0t2Bx
laMqyZZAOxvKMXRpiAKcReEKQg+TRjdPd0TL9uNOk6YWph/HQX2W7jSlm6HJRvNF
IGNh1H6V2REtiTSnTaFdvbhptJq0oc+N/sRGvvOhKMu/
—–END CERTIFICATE—–
Step 3: Install the Signed Certificate
Back in the Windows server, create an empty text file in c:certificates and call it cert.crt. Open it with a text editor and paste in it the certificate text received from the Certification Authority.
Then, open again a high privileges command prompt, go into the c:certificates directory, and run this command:
certreq –accept cert.crt
Once the command is executed, the certificate is stored in the local Certificate Store of the Windows Operating System.
To manage this and future certificates, you can use the Certificates MMC (Microsoft management console), that gives you graphical access to the Certificate Store. When configuring the console, it only requires you to select “Computer account” and then “local computer”. Imported certificates like the one created in this tutorial is stored under Personal Certificates.
Step 4: A practical use with Veeam Cloud Connect
Let’s see now how this certificate can be used in a real senario. In Veeam Backup & replication, you can protect for example a Cloud Connect deployment. To use the certificate, go into the Cloud Connect Infrastructure node of the Veeam Console, and select “Manage Certificates”. First, you choose “Select certificate from Certificate Store”:
In the following screen, you select to browse the Certificate Store. Here, you expand the “My” tree, and you see the imported certificate. You select it.
The next step of the wizard also shows the Thumbprint of the certificate; this can be sent to customers for additional verifications.
Finished the wizard, the certificate is ready to be used for SSL cyphered connections.
When a user starts a connection to the service, this is the certificate that will be used:
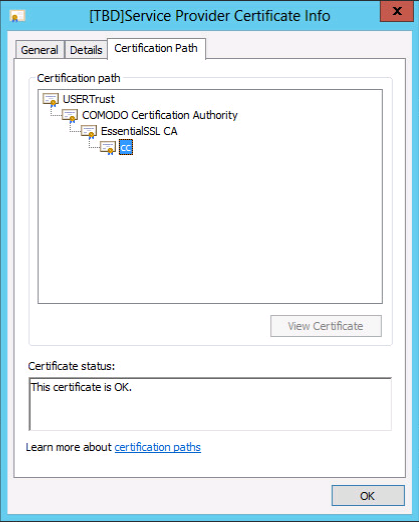
As you can see, and as the user can verify, the certificate is issued to cc.virtualtothecore.com as requested, it’s valid, and the Certification Path is recognized; this means Windows is able to recognize the Certificate Authority that signed the certificate as valid, and accept its certificates.
Create Self-signed SSL certificate on Windows
Now as web application manager we need the SSL certificate in a daily basis to do some testing. Some times you want run Intranet application you need SSL certification as well. So buying a new certificate is costly when you have low IT budget. So you do the same thing to generating self-signed SSL certificate on windows system.There are several way to do that but the easiest way to create the SSL certificate is using OpenSSL. OpenSSL is opensource software so you don’t have any additional cost for that as well. Just you need to do the below steps.
First create a root ca certificate. Then create your individual server certificate. At last you have signed the the in individual server certificate with your root ca certificate. Now you have your own self-signed
What Is Open SSL?
OpenSSL is an open source implementation of the SSL and TLS protocols. It provides an encryption transport layer on top of the normal communications layer. Allowing it to be intertwined with many network applications and services. The default SSL Profile in the Cloud Management Console has a generic Common Name. When associating an SSL profile to a Gateway Cluster? If using the default SSL Profile, your application making API calls may fail to verify the host name. It is connecting to against the certificate presented. In this case, you can generate a new self-signed certificate that represents a common name your application can validate. This topic tells you how to generate self-signed SSL certificate requests using the OpenSSL toolkit to enable HTTPS connections.
OpenSSL is often used to encrypt authentication of mail clients and to secure web based transactions such as credit card payments. Some ports, such as www/apache24 and databases/postgresql91-server. Include a compile option for building with OpenSSL.
OpenSSL is a robust, commercial-grade, and full-featured toolkit for the Transport Layer Security (TLS) & Secure Sockets Layer (SSL) protocols. It is also a general-purpose cryptography library.
OpenSSL is licensed under an Apache-style license. Which basically means that you are free to get and use it for commercial and non-commercial purposes subject to some simple license conditions.
o Create self-signed SSL certificate on Windows system using OpenSSL follow below Steps.
First install the OpenSSL
- To create the self-signed SSL certificate first you have to install the OpenSSL application in your windows system. You can download the application from here.OpenSSL-installtion
Install the software in “C:Program FilesOpenSSL-Win64” location. Then Click Next and finish the installation.
- After completing the installation open the command prompt
Create a temporary directory “demo”
md demo
cd demo
set RANDFILE=c:demo.rnd
set OPENSSL_CONF=C:Program FilesOpenSSL-Win64binopenssl.cfg
- Now lunch the openssl.exe by running the below command
“C:Program FilesOpenSSL-Win64binopenssl.exe”
Use the “” to run the command
- Now you have to create key file for your CA certificate
genrsa -out can.key 2048
- Now create the root CA certificate using the key file
req -new -x509 -days 1826 -key can.key -out canew.crt
It will ask for some details like Country Name, Sate, City, Organization Name FQDN name. FQDN name should be your domain name who have the certificate authority of your domain.
- Now generate public key for your application SSL certificate.
genrsa -out ianew.key 2048
- Now create a CSR with the newly created public key “ianew.key”
req -new -key ianew.key -out ianew.csr
It will ask for some details like Country Name, Sate, City, Organization Name and FQDN name. FQDN name should be your host/computer FQDN name of you web server or application server.
- Now singed the csr certificate with you root CA certificate which you created in step no 2.
x509 -req -days 1826 -in ianew.csr -CA canew.crt -CAkey can.key -set_serial 01 -out ianew.crt
Now your self sign-certificate is ready You have to install the root ca certificate on your client system to avoid the certificate error.
certificate
Now you can deploy the self-signed SSL certificate to your web server hosted in Windows or Linux. This easy way you can create self-signed SSL certificate on Windows by using OpenSSL.