In today’s topic, we will learn how to install and configure Windows Server Update Services.
Before that we will understand about the WSUS first.
What is WSUS?
Windows Server Update Services allows network administrators to specify the Microsoft updates that should be installed,
create separate groups of computers for different sets of updates, and get reports on the compliance levels of the computers and the updates that must be installed.
To install the WSUS in Windows Server 2016 follow the below steps:
Go to Server Manager – click Manage and click Add roles and Features as shown in below window.
In before you begin window, click Next to continue.
Select required installation type and click Next to move on.
Select server from the server pool to install this role and click Next to continue.
Select Windows Server update services role and select Include management tools and click Add feature to continue.
Click Next on Features window.
Click Next on Windows Server update services window and click Next to continue.
Select the required role services to continue and click Next.
Create on folder on your local server to download the updates or else you can give the remote path to avoid disk space
issues in WSUS server and provide the path in the below window and click Next to continue.
Cross verify the installation selections and proceed further and click Install to continue.
Click Close to finish the installation of WSUS role on Windows server 2016.
Now we need to configure the WSUS, post installing the role you will see yellow escalation mark on the flag in Server
manager. Click that and launch Post-Installation tasks.
It will take some time finish post installation tasks.
Post successfully completing you can see the below in server manager task flag.
To configure go to WSUS and click next to continue.
On improvement program, select the required option and click Next to continue.
Select Synchronize update from Microsoft update and click Next to continue.
Click Next to proceed further
Click on start connecting to proceed further to save and download upstream server and proxy server information. Your
upstream server and proxy server settings and synchronize information about available updates.
Select Download updates only in these languages and select English and click Next to continue.
Select the required products Windows 7, Windows 10, Windows Server 2008 r2 and Windows Server 2012 r2 and click Next
to continue.
Choose classifications and click Next to continue.
Select Synchronize automatically and click Next to continue.
Check begin initial synchronization and click Next.
Click Finish to complete the configuration.
This concludes the installation and configuration of WSUS on Windows Server 2016.
Post completing the installation open the WSUS console and it looks like below.
Thank you for reading and Happy Learning.
С помощью сервера обновлений Windows Server Update Services (WSUS) вы можете развернуть собственную централизованную систему обновления продуктов Microsoft (операционных систем Widows, Office, SQL Server, Exchange и т.д.) на компьютерах и серверах в локальной сети компании. В этой статье мы рассмотрим, как установить и настроить сервер обновлений WSUS в Windows Server 2019/2016/2012R2.
Содержание:
- Установка роли WSUS в Windows Server
- Начальная настройка сервера обновлений WSUS в Windows Server
- Установка консоли администрирования WSUS в Windows 10/11
- Оптимизация производительности WSUS
Как работает WSUS?
Сервер WSUS реализован в виде отдельной роли Windows Server. В общих словах сервис WSUS можно описать так:
- После установки сервер WSUS по расписанию синхронизируется с серверами обновлений Microsoft Update в Интернете и скачивает новые обновления для выбранных продуктов;
- Администратор WSUS выбирает, какие обновления нужно установить на рабочие станции и сервера компании и одобряет их установку;
- Клиенты WSUS в локальной сети скачивают и устанавливают обновления с вашего сервера обновлений согласно настроенным политикам.
Установка роли WSUS в Windows Server
Начиная с Windows Server 2008, сервис WSUS выделен в отдельную роль, которую можно установить через консоль управления сервером или с помощью PowerShell.
Если вы развертываете новый сервер WSUS, рекомендуется сразу устанавливать его на последнем релизе Windows Server 2022 (возможна установка на Windows Serve Core).
Чтобы установить WSUS, откройте консоль Server Manager и отметьте роль Windows Server Update Services (система автоматически выберет и предложит установить необходимые компоненты веб сервера IIS).
В следующем окне нужно выбрать, какие компоненты WSUS нужно установить. Обязательно отметьте опцию WSUS Services. Две следующие опции зависят от того, какую базу данных вы планируете использовать для WSUS.
Настройки сервера, метаданные обновлений, информация о клиентах WSUS хранятся в базе данных SQL Server. В качестве базы данных WSUS вы можете использовать:
- Windows Internal Database (WID) – встроенную базу данных Windows, опция WID Connectivity (это рекомендуемый и работоспособный вариант даже для больших инфраструктур);
- Отдельную базу Microsoft SQL Server, развернутую на локальном или удаленном сервере. Вы можете использовать редакции MS SQL Enterprise, Standard (требуют лицензирования) или бесплатную Express редакцию. Это опция SQL Server Connectivity.
Внутреннюю базу Windows (Windows Internal Database) рекомендуется использовать, если:
- У вас отсутствуют лицензии MS SQL Server;
- Вы не планируется использовать балансировку нагрузки на WSUS (NLB WSUS);
- При развертывании дочернего сервера WSUS (например, в филиалах). В этом случае на вторичных серверах рекомендуется использовать встроенную базу WSUS.
В бесплатной SQL Server Express Edition максимальный размер БД ограничен 10 Гб. Ограничение Windows Internal Database – 524 Гб. Например, в моей инфраструктуре размер базы данных WSUS на 3000 клиентов составил около 7Гб.
При установке роли WSUS и MS SQL Server на разных серверах есть ряд ограничений:
- SQL сервер с БД WSUS не может быть контроллером домена Active Directory;
- Сервер WSUS нельзя разворачивать на хосте с ролью Remote Desktop Services.
База WID по умолчанию называется SUSDB.mdf и хранится в каталоге windir%widdata. Эта база поддерживает только Windows аутентификацию (но не SQL). Инстанс внутренней (WID) базы данных для WSUS называется server_nameMicrosoft##WID.
Базу WID можно администрировать через SQL Server Management Studio (SSMS), если указать в строке подключения
\.pipeMICROSOFT##WIDtsqlquery
.
Если вы хотите хранить файлы обновлений локально на сервере WSUS, включите опцию Store updates in the following locations и укажите путь к каталогу. Это может быть папка на локальном диске (рекомендуется использовать отдельный физический или логический том), или сетевой каталог (UNC путь). Обновления скачиваются в указанный каталог только после их одобрения администратором WSUS.
Размер базы данных WSUS сильно зависит от количества продуктов и версий ОС Windows, которое вы планируете обновлять. В большой организации размер файлов обновлений на WSUS сервере может достигать сотни Гб.
Если у вас недостаточно места на дисках для хранения файлов обновлений, отключите эту опцию. В этом случае клиенты WSUS будут получать одобренный файлы обновлений из Интернета (вполне рабочий вариант для небольших сетей).
Также вы можете установить сервер WSUS с внутренней базой данный WID с помощью PowerShell командлета Install-WindowsFeature:
Install-WindowsFeature -Name UpdateServices, UpdateServices-WidDB, UpdateServices-Services, UpdateServices-RSAT, UpdateServices-API, UpdateServices-UI –IncludeManagementTools
Начальная настройка сервера обновлений WSUS в Windows Server
После окончания установки роли WSUS вам нужно выполнить его первоначальную настройку. Откройте Server Manager и выберите Post-Deployment Configuration -> Launch Post-Installation tasks.
Для управления WSUS из командной строки можно использовать консольную утилиту
WsusUtil.exe
. Например, чтобы указать путь к каталогу с файлами обновлений WSUS, выполните:
CD "C:Program FilesUpdate ServicesTools"
WsusUtil.exe PostInstall CONTENT_DIR=E:WSUS
Или, например, вы можете перенастроить ваш WSUS на внешнюю базу данных SQL Server:
wsusutil.exe postinstall SQL_INSTANCE_NAME="SQLSRV1SQLINSTANCEWSUS" CONTENT_DIR=E:WSUS_Content
Затем откройте консоль Windows Server Update Services. Запустится мастер первоначальной настройки сервера обновлений WSUS.
Укажите, будет ли сервер WSUS скачивать обновления с сайта Microsoft Update напрямую (Synchronize from Microsoft Update) или он должен получать их с вышестоящего WSUS сервера (Synchronize from another Windows Update Services server). Дочерние WSUS сервера обычно развертываются на удаленных площадках с большим количеством клиентов (300+) для снижения нагрузки на WAN канал.
Если в вашей сети используется прокси-сервер для доступа в Интернет, далее нужно указать адрес и порт прокси сервера, и логин/пароль для аутентификации.
Проверьте подключение к вышестоящему серверу обновлений (или Windows Update). Нажмите кнопку Start Connecting.
Выберите языки продуктов, для которых WSUS будет получать обновления. Мы укажем English и Russian (список языков может быть в дальнейшем изменен из консоли WSUS).
Затем выберите продукты, для которых WSUS должен скачивать обновления. Выберите только те продукты Microsoft, которые используются в Вашей корпоративной сети. Например, если вы уверены, что в вашей сети не осталось компьютеров с Windows 7 или Windows 8, не выбирайте эти опции.
Обязательно включите в классификации следующие общие разделы:
- Developer Tools, Runtimes, and Redistributable — для обновления библиотек Visual C++ Runtime
- Windows Dictionary Updates в категории Windows
- Windows Server Manager – Windows Server Update Services (WSUS) Dynamic Installer
На странице Classification Page, нужно указать типы обновлений, которые будут распространяться через WSUS. Рекомендуется обязательно указать: Critical Updates, Definition Updates, Security Packs, Service Packs, Update Rollups, Updates.
Обновления редакций (билдов) Windows 10 (21H2, 20H2, 1909 и т.д.) в консоли WSUS входят в класс Upgrades.
Настройте расписание синхронизации обновлений. В большинстве случаев рекомендуется использовать автоматическую ежедневную синхронизацию сервера WSUS с серверами обновлений Microsoft Update. Рекомендуется выполнять синхронизацию в ночные часы, чтобы не загружать канал Интернет в рабочее время.
Первоначальная синхронизация сервера WSUS с вышестоящим сервером обновлений может занять несколько дней (в зависимости от количества продуктов, которое вы выбрали ранее).
После окончания работы мастера запустится консоль WSUS.
Консоль WSUS состоит из нескольких разделов:
- Updates – обновления, доступные на сервере WSUS (здесь можно управлять одобрением обновлений и назначать их для установки)
- Computers – здесь можно создать группы клиентов WSUS (компьютеры и серверы)
- Downstream Servers – позволяет настроить, будете ли вы получать из обновления Windows Update или вышестоящего сервера WSUS
- Syncronizations –расписание синхронизации обновлений
- Reports – отчёты WSUS
- Options – настройка сервера WSUS
Клиенты теперь могут получать обновления, подключившись к WSUS серверу по порту 8530 (в Windows Server 2003 и 2008 по умолчанию использоваться 80 порт). Проверьте, что этот порт открыт на сервере обновлений:
Test-NetConnection -ComputerName wsussrv1 -Port 8530
Можно использовать защищенное SSL подключение по порту 8531. Для этого нужно привязать сертификат в IIS.
Если порт закрыт, создайте соответствующее правило в Windows Defender Firewall.
Установка консоли администрирования WSUS в Windows 10/11
Для администрирования сервера обновления WSUS используется консоль Windows Server Update Services (
wsus.msc
). Вы можете управлять серверов WSUS как с помощью локальной консоли, так и по сети с удаленного компьютера.
Консоль администрирования WSUS для десктопных компьютеров с Windows 10 или 11 входит в состав RSAT. Для установки компонента Rsat.WSUS.Tool, выполните следующую PowerShell команду:
Add-WindowsCapability -Online -Name Rsat.WSUS.Tools~~~~0.0.1.0
Если вы хотите установить консоль WSUS в Windows Server, выполните команду:
Install-WindowsFeature -Name UpdateServices-Ui
При установке WSUS в Windows Server создаются две дополнительные локальные группы. Вы можете использовать их для предоставления доступа пользователям к консоли управления WSUS.
- WSUS Administrators
- WSUS Reporters
Для просмотра отчетов по установленным обновлениям и клиентам на WSUS нужно установить:
- Microsoft System CLR Types для SQL Server 2012 (SQLSysClrTypes.msi);
- Microsoft Report Viewer 2012 Runtime (ReportViewer.msi).
Если компоненты не установлен, при формировании любого отчета WSUS появится ошибка:
The Microsoft Report Viewer 2012 Redistributable is required for this feature. Please close the console before installing this package.
Оптимизация производительности WSUS
В этом разделе опишем несколько советов, касающихся оптимизации производительности сервера обновлений WSUS в реальных условиях.
- Для нормальной работы WSUS на сервере обновлений нужно должно быть свободным минимум 4 Гб RAM и 2CPU;
- При большом количестве клиентов WSUS (более 1500) вы можете столкнутся с существенным снижением производительность пула IIS WsusPoll, который раздает обновления клиентам. Может появляться ошибка 0x80244022 на клиентах, или при запуске консоль WSUS падать с ошибкой Error: Unexpected Error + Event ID 7053 в Event Viewer (The WSUS administration console has encountered an unexpected error. This may be a transient error; try restarting the administration console. If this error persists).
Для решения проблемы нужно добавить RAM на сервер и оптимизировать настройки пула IIS в соответствии с рекомендациями в статье. Воспользуетесь такими командами:
Import-Module WebAdministration
Set-ItemProperty -Path IIS:AppPoolsWsusPool -Name queueLength -Value 2500
Set-ItemProperty -Path IIS:AppPoolsWsusPool -Name cpu.resetInterval -Value "00.00:15:00"
Set-ItemProperty -Path IIS:AppPoolsWsusPool -Name recycling.periodicRestart.privateMemory -Value 0
Set-ItemProperty -Path IIS:AppPoolsWsusPool -Name failure.loadBalancerCapabilities -Value "TcpLevel" - Включите автоматическое одобрения для обновлений антивируса Microsoft В противном случае WSUS станет существенно тормозить и потреблять всю доступную оперативную память.
Антивирусные проверки могут негативно влиять на производительность WSUS. Во встроенном Microsoft Defender антивирусе в Windows Server рекомендуется исключить следующие папки из области проверки:
- WSUSWSUSContent;
- %windir%widdata;
- SoftwareDistributionDownload.
[1] часть — Установка роли WSUS на Windows Server 2016
[2] часть — Конфигурирование WSUS
[3] часть — Настройка WSUS
[4] часть — Траблшутинг WSUS
В этой статье мы рассмотрим установку роли WSUS.
В нашем примере мы будем использовать два системных диска, системный и второй для хранения скаченный обновлений WSUS.
Добавляем роль Windows Server Update Services и соглашаемся с предложенным списком ролей.
В разделе Features добавляем .Net Framework 3.5
Если количество клиентов и обновлений не большое, тогда нет необходимости в использовании сторонней базы данных.
Задаем путь, где будут хранится скаченные обновления. В нашем случае это E:WSUSUpdates
Подтверждаем роли для IIS
При необходимости задаем путь для установки .Net Framework 3.5
Задаем путь
Ожидаем окончания установки роли.
Запуск конфигурирования после установки
Если вы закрыли предыдущее окно, запускаем Post-deployment Configuration в консоли Server Manager
Конфигурирование завершено
На этом установка роли WSUS завершена, можно приступать к настройке.
| title | description | ms.topic | ms.assetid | ms.author | author | manager | ms.date |
|---|---|---|---|---|---|---|---|
|
Step 2 — Configure WSUS |
Windows Server Update Services (WSUS) topic — Configure WSUS is step two in a four-step process for deploying WSUS. |
article |
d4adc568-1f23-49f3-9a54-12a7bec5f27c |
jgerend |
JasonGerend |
mtillman |
9/18/2020 |
Applies to: Windows Server 2022, Windows Server 2019, Windows Server 2016, Windows Server 2012 R2, Windows Server 2012
After you install the Windows Server Update Services (WSUS) server role on your server, you need to properly configure it. You also need to configure your client computers to receive their updates from the WSUS server.
This article walks you through the following procedures:
| Task | Description |
|---|---|
| 2.1. Configure network connections | Configure your firewall and proxy settings to allow the server to make the connections that it needs. |
| 2.2. Configure WSUS by using the WSUS Configuration Wizard | Use the WSUS Configuration Wizard to perform the base WSUS configuration. |
| 2.3. Secure WSUS with the Secure Sockets Layer protocol | Configure the Secure Sockets Layer (SSL) protocol to help protect WSUS. |
| 2.4. Configure WSUS computer groups | Create computer groups in the WSUS Administration Console to manage updates in your organization. |
| 2.5. Configure client computers to establish SSL connections with the WSUS server | Set up the client computers to establish secure connections to the WSUS server. |
| 2.6. Configure client computers to receive updates from the WSUS server | Set up the client computers to receive their updates from the WSUS server. |
2.1. Configure network connections
Before you start the configuration process, be sure that you know the answers to the following questions:
-
Is the server’s firewall configured to allow clients to access the server?
-
Can this computer connect to the upstream server (such as the server that’s designated to download updates from Microsoft Update)?
-
Do you have the name of the proxy server and the user credentials for the proxy server, if you need them?
You can then start configuring the following WSUS network settings:
-
Updates: Specify the way this server will get updates (from Microsoft Update or from another WSUS server).
-
Proxy: If you identified that WSUS needs to use a proxy server to have internet access, you need to configure proxy settings in the WSUS server.
-
Firewall: If you identified that WSUS is behind a corporate firewall, you’ll have to take additional steps at the edge device to allow WSUS traffic.
[!IMPORTANT]
If you only have one WSUS server, it must have internet access, because it needs to download updates from Microsoft. If you have multiple WSUS servers, only one server needs internet access. The others only need network access to the internet-connected WSUS server. Your client computers don’t need internet access; they only need network access to a WSUS server.
[!TIP]
If your network is «air gapped»—if it does not have access to the internet at all—you can still use WSUS to provide updates to client computers on the network. This approach requires two WSUS servers. One WSUS server with internet access collects the updates from Microsoft. A second WSUS server on the protected network serves the updates to the client computers. Updates are exported from the first server onto removable media, carried across the air gap, and imported onto the second server. This is an advanced configuration that’s beyond the scope of this article.
2.1.1. Configure your firewall to allow your first WSUS server to connect to Microsoft domains on the internet
If a corporate firewall is between WSUS and the internet, you might have to configure that firewall to ensure that WSUS can get updates. To get updates from Microsoft Update, the WSUS server uses ports 80 and 443 for the HTTP and HTTPS protocols. Although most corporate firewalls allow this type of traffic, some companies restrict internet access from the servers because of security policies. If your company restricts access, you’ll need to configure your firewall to allow your WSUS server to access Microsoft domains.
Your first WSUS server must have outbound access to ports 80 and 443 on the following domains:
-
http://windowsupdate.microsoft.com
-
http://*.windowsupdate.microsoft.com
-
https://*.windowsupdate.microsoft.com
-
http://*.update.microsoft.com
-
https://*.update.microsoft.com
-
http://*.windowsupdate.com
-
http://download.windowsupdate.com
-
https://download.microsoft.com
-
http://*.download.windowsupdate.com
-
http://wustat.windows.com
-
http://ntservicepack.microsoft.com
-
http://go.microsoft.com
-
http://dl.delivery.mp.microsoft.com
-
https://dl.delivery.mp.microsoft.com
-
http://*.delivery.mp.microsoft.com
-
https://*.delivery.mp.microsoft.com
[!IMPORTANT]
You must configure your firewall to allow the first WSUS server to access any URL within these domains. The IP addresses associated with these domains are constantly changing, so don’t try to use IP address ranges instead.
For a scenario in which WSUS is failing to get updates because of firewall configurations, see article 885819 in the Microsoft Knowledge Base.
2.1.2. Configure the firewall to allow your other WSUS servers to connect to the first server
If you have multiple WSUS servers, you should configure the other WSUS servers to access the first («topmost») server. Your other WSUS servers will receive all their update information from the topmost server. This configuration allows you to manage your entire network by using the WSUS Administration Console on the topmost server.
Your other WSUS servers must have outbound access to the topmost server through two ports. By default, these are ports 8530 and 8531. You can change these ports, as described later in this article.
[!NOTE]
If the network connection between the WSUS servers is slow or expensive, you can configure one or more of the other WSUS servers to receive update payloads directly from Microsoft. In this case, only a small amount of data will be sent from those WSUS servers to the topmost server. For this configuration to work, the other WSUS servers must have access to the same internet domains as the topmost server.
[!NOTE]
If you have a large organization, you can use chains of connected WSUS servers, rather than having all your other WSUS servers connect directly to the topmost server. For example, you can have a second WSUS server that connects to the topmost server, and then have other WSUS servers connect to the second WSUS server.
2.1.3. Configure your WSUS servers to use a proxy server, if needed
If the corporate network uses proxy servers, the proxy servers must support HTTP and HTTPS protocols. They also must use basic authentication or Windows authentication. You can meet these requirements by using one of the following configurations:
-
A single proxy server that supports two protocol channels. In this case, set one channel to use HTTP and the other channel to use HTTPS.
[!NOTE]
You can set up one proxy server that handles both protocols for WSUS during the installation of WSUS server software. -
Two proxy servers, each of which supports a single protocol. In this case, one proxy server is configured to use HTTP, and the other proxy server is configured to use HTTPS.
To set up WSUS to use two proxy servers
-
Log on to the computer that will be the WSUS server by using an account that’s a member of the Local Administrators group.
-
Install the WSUS server role. During the WSUS Configuration Wizard, don’t specify a proxy server.
-
Open a command prompt (Cmd.exe) as an administrator:
- Go to Start.
- In Start Search, type Command prompt.
- At the top of the start menu, right-click Command prompt, and then select Run as administrator.
- If the User Account Control dialog box appears, enter the appropriate credentials (if requested), confirm that the action that it displays is what you want, and then select Continue.
-
In the command prompt window, go to the C:Program FilesUpdate ServicesTools folder. Enter the following command:
wsusutil ConfigureSSLproxy [<proxy_server proxy_port>] -enableIn that command:
-
proxy_server is the name of the proxy server that supports HTTPS.
-
proxy_port is the port number of the proxy server.
-
-
Close the command prompt window.
To add a proxy server to the WSUS configuration
-
Open the WSUS Administration Console.
-
On the left pane, expand the server name, and then select Options.
-
On the Options pane, select Update Source and Update Server, and then select the Proxy Server tab.
-
Select the Use a proxy server when synchronizing checkbox.
-
In the Proxy server name text box, enter the name of the proxy server.
-
In the Proxy port number text box, enter the port number of the proxy server. The default port number is 80.
-
If the proxy server requires that you use a specific user account, select the Use user credentials to connect to the proxy server checkbox. Enter the required user name, domain, and password into the corresponding text boxes.
-
If the proxy server supports basic authentication, select the Allow basic authentication (password is sent in cleartext) checkbox.
-
Select OK.
To remove a proxy server from the WSUS configuration
-
Clear the Use a proxy server when synchronizing checkbox.
-
Select OK.
2.1.4. Configure your firewall to allow client computers to access a WSUS server
Your client computers will all connect to one of your WSUS servers. The client computer must have outbound access to two ports on the WSUS server. By default, these are ports 8530 and 8531.
2.2. Configure WSUS by using the WSUS Configuration Wizard
This procedure assumes that you’re using the WSUS Configuration Wizard, which appears the first time you start the WSUS Management Console. Later in this topic, you’ll learn how to perform these configurations by using the Options page.
To configure WSUS
-
On the left pane of Server Manager, select Dashboard > Tools > Windows Server Update Services.
[!NOTE]
If the Complete WSUS Installation dialog box appears, select Run. In the Complete WSUS Installation dialog box, select Close when the installation successfully finishes. -
The WSUS Configuration Wizard opens. On the Before you Begin page, review the information, and then select Next.
-
Read the instructions on the Join the Microsoft Update Improvement Program page. Keep the default selection if you want to participate in the program, or clear the checkbox if you don’t. Then select Next.
-
On the Choose Upstream Server page, select one of the two options: Synchronize the updates with Microsoft Update or Synchronize from another Windows Server Update Services server.
If you choose to synchronize from another WSUS server:
-
Specify the server name and the port on which this server will communicate with the upstream server.
-
To use SSL, select the Use SSL when synchronizing update information checkbox. The servers will use port 443 for synchronization. (Make sure that this server and the upstream server support SSL.)
-
If this is a replica server, select the This is a replica of the upstream server checkbox.
-
-
After you select the options for your deployment, select Next.
-
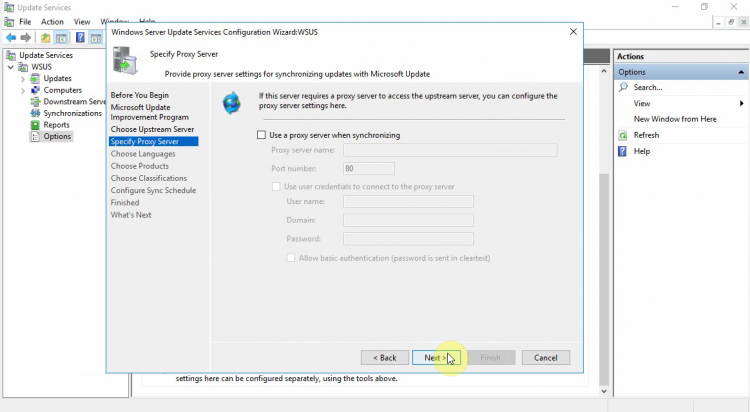
On the Specify Proxy Server page, select the Use a proxy server when synchronizing checkbox. Then enter the proxy server name and port number (port 80 by default) in the corresponding boxes.
[!IMPORTANT]
You must complete this step if you identified that WSUS needs a proxy server to have internet access. -
If you want to connect to the proxy server by using specific user credentials, select the Use user credentials to connect to the proxy server checkbox. Then enter the user name, domain, and password of the user in the corresponding boxes.
If you want to enable basic authentication for the user who is connecting to the proxy server, select the Allow basic authentication (password is sent in cleartext) checkbox.
-
Select Next.
-
On the Connect to Upstream Server page, select start Connecting.
-
When WSUS connects to the server, select Next.
-
On the Choose Languages page, you have the option to select the languages from which WSUS will receive updates: all languages or a subset of languages. Selecting a subset of languages will save disk space, but it’s important to choose all the languages that all the clients of this WSUS server need.
If you choose to get updates only for specific languages, select Download updates only in these languages, and then select the languages for which you want updates. Otherwise, leave the default selection.
[!WARNING]
If you select the option Download updates only in these languages, and this server has a downstream WSUS server connected to it, this option will force the downstream server to also use only the selected languages. -
After you select the language options for your deployment, select Next.
-
The Choose Products page allows you to specify the products for which you want updates. Select product categories, such as Windows, or specific products, such as Windows Server 2012. Selecting a product category selects all the products in that category.
-
After you select the product options for your deployment, select Next.
-
On the Choose Classifications page, select the update classifications that you want to get. Choose all the classifications or a subset of them, and then select Next.
-
The Set Sync Schedule page enables you to select whether to perform synchronization manually or automatically.
-
If you select Synchronize manually, you must start the synchronization process from the WSUS Administration Console.
-
If you select Synchronize automatically, the WSUS server will synchronize at set intervals.
Set the time for First synchronization, and then specify the number of synchronizations per day that you want this server to perform. For example, if you specify four synchronizations per day, starting at 3:00 AM, synchronizations will occur at 3:00 AM, 9:00 AM, 3:00 PM, and 9:00 PM.
-
-
After you select the synchronization options for your deployment, select Next.
-
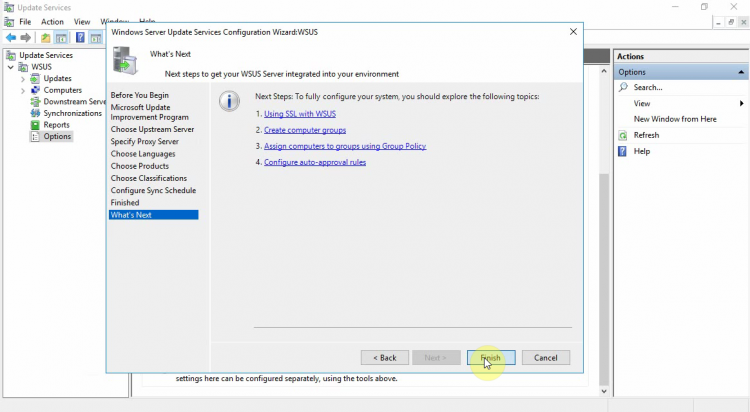
On the Finished page, you have the option to start the synchronization now by selecting the Begin initial synchronization checkbox.
If you don’t select this option, you need to use the WSUS Management Console to perform the initial synchronization. Select Next if you want to read more about additional settings, or select Finish to conclude this wizard and finish the initial WSUS setup.
-
After you select Finish, the WSUS Administration Console appears. You’ll use this console to manage your WSUS network, as described later on.
2.3. Secure WSUS with the Secure Sockets Layer protocol
You should use the SSL protocol to help secure your WSUS network. WSUS can use SSL to authenticate connections and to encrypt and protect update information.
[!WARNING]
Securing WSUS by using the SSL protocol is important for the security of your network. If your WSUS server does not properly use SSL to secure its connections, an attacker might be able to modify crucial update information as it’s sent from one WSUS server to another, or from the WSUS server to the client computers. This will allow the attacker to install malicious software on client computers.
[!IMPORTANT]
Clients and downstream servers that are configured to use Transport Layer Security (TLS) or HTTPS must also be configured to use a fully qualified domain name (FQDN) for their upstream WSUS server.
2.3.1. Enable SSL/HTTPS on the WSUS server’s IIS service to use SSL/HTTPS
To begin the process, you must enable SSL support on the WSUS server’s IIS service. This effort involves creating an SSL certificate for the server.
The steps that are required to get an SSL certificate for the server are beyond the scope of this article and will depend on your network configuration. For more information and for instructions about how to install certificates and set up this environment, we suggest the following articles:
-
Suite B PKI step-by-step guide
-
Implementing and administering certificate templates
-
Active Directory Certificate Services upgrade and migration guide
-
Configure certificate autoenrollment
2.3.2. Configure the WSUS server’s IIS web server to use SSL for some connections
WSUS requires two ports for connections to other WSUS servers and to client computers. One port uses SSL/HTTPS to send update metadata (crucial information about the updates). By default, this is port 8531. A second port uses HTTP to send update payloads. By default, this is port 8530.
[!IMPORTANT]
You can’t configure the entire WSUS website to require SSL. WSUS is designed to encrypt update metadata only. This is the same way that Windows Update distributes updates.To guard against an attacker tampering with the update payloads, all update payloads are signed through a specific set of trusted signing certificates. In addition, a cryptographic hash is computed for each update payload. The hash is sent to the client computer over the secure HTTPS metadata connection, along with the other metadata for the update. When an update is downloaded, the client software verifies the payload’s digital signature and hash. If the update has been changed, it’s not installed.
You should require SSL only for these IIS virtual roots:
-
SimpleAuthWebService
-
DSSAuthWebService
-
ServerSyncWebService
-
APIremoting30
-
ClientWebService
You should not require SSL for these virtual roots:
-
Content
-
Inventory
-
ReportingWebService
-
SelfUpdate
The certificate of the certification authority (CA) must be imported into each WSUS server’s Trusted Root CA store for the local computer, or the Trusted Root CA store for WSUS if it exists.
For more information about how to use SSL certificates in IIS, see Require Secure Sockets Layer (IIS 7).
[!IMPORTANT]
You must use the certificate store for the local computer. You can’t use a user’s certificate store.
Normally, you should configure IIS to use port 8531 for HTTPS connections and port 8530 for HTTP connections. If you change these ports, you must use two adjacent port numbers. The port number used for HTTP connections must be exactly 1 less than the port number used for HTTPS connections.
You must reinitialize ClientServicingProxy if the server name, SSL configuration, or port number has changed.
2.3.3. Configure WSUS to use the SSL signing certificate for its client connections
-
Log on to the WSUS server by using an account that’s a member of the WSUS Administrators group or the Local Administrators group.
-
Go to Start, type CMD, right-click Command prompt, and then select Run as administrator.
-
Go to the %ProgramFiles%Update ServicesTools folder.
-
In the command prompt window, enter the following command:
wsusutil configuressl _certificateName_In that command, certificateName is the DNS name of the WSUS server.
2.3.4. Secure the SQL Server connection, if needed
If you use WSUS with a remote SQL Server database, the connection between the WSUS server and the database server is not secured through SSL. This creates a potential attack vector. To help protect this connection, consider the following recommendations:
-
Move the WSUS database to the WSUS server.
-
Move the remote database server and the WSUS server to a private network.
-
Deploy Internet Protocol security (IPsec) to help secure network traffic. For more information about IPsec, see Creating and using IPsec policies.
2.3.5. Create a code-signing certificate for local publishing, if needed
In addition to distributing updates that Microsoft provides, WSUS supports local publishing. Local publishing allows you to create and distribute updates that you design yourself, with your own payloads and behaviors.
Enabling and configuring local publishing is beyond the scope of this article. For full details, see Local publishing.
[!IMPORTANT]
Local publishing is a complicated process and is often not needed. Before you decide to enable local publishing, you should carefully review the documentation and consider whether and how you’ll use this functionality.
2.4. Configure WSUS computer groups
Computer groups are an important part of using WSUS effectively. Computer groups permit you to test and target updates to specific computers. There are two default computer groups: All Computers and Unassigned Computers. By default, when each client computer first contacts the WSUS server, the server adds that client computer to both of these groups.
You can create as many custom computer groups as you need to manage updates in your organization. As a best practice, create at least one computer group to test updates before you deploy them to other computers in your organization.
2.4.1. Choose an approach for assigning client computers to computer groups
There are two approaches to assigning client computers to computer groups. The right approach for your organization will depend on how you typically manage your client computers.
-
Server-side targeting: This is the default approach. In this approach, you assign client computers to computer groups by using the WSUS Administration Console.
This approach gives you the flexibility to quickly move client computers from one group to another as circumstances change. But it means that new client computers must manually be moved from the Unassigned Computers group to the appropriate computer group.
-
Client-side targeting: In this approach, you assign each client computer to computer groups by using policy settings set on the client computer itself.
This approach makes it easier to assign new client computers to the appropriate groups. You do so as part of configuring the client computer to receive updates from the WSUS server. But it means that client computers can’t be assigned to computer groups, or moved from one computer group to another, through the WSUS Administration Console. Instead, the client computers’ policies must be modified.
2.4.2. Enable client-side targeting, if appropriate
[!IMPORTANT]
Skip this step if you’ll use server-side targeting.
-
In the WSUS Administration Console, under Update Services, expand the WSUS server, and then select options.
-
On the General tab on the Options pane, select Use Group Policy or registry settings on computers.
2.4.3. Create the desired computer groups
[!NOTE]
You must create computer groups by using the WSUS Administration Console, whether you use server-side targeting or client-side targeting to add client computers to the computer groups.
-
In the WSUS Administration Console, under Update Services, expand the WSUS server, expand Computers, right-click All computers, and then select Add Computer Group.
-
In the Add Computer Group dialog, for Name, specify the name of the new group. Then select Add.
2.5. Configure client computers to establish SSL connections with the WSUS server
Assuming that you’ve configured the WSUS server to help protect the client computers’ connections by using SSL, you must configure the client computers to trust those SSL connections.
The WSUS server’s SSL certificate must be imported into the client computers’ Trusted Root CA store, or into the client computers’ Automatic Update Service Trusted Root CA store if it exists.
[!IMPORTANT]
You must use the certificate store for the local computer. You can’t use a user’s certificate store.
The client computers must trust the certificate that you bind to the WSUS server. Depending on the type of certificate that’s used, you might have to set up a service to enable the client computers to trust the certificate that’s bound to the WSUS server.
If you’re using local publishing, you should also configure the client computers to trust the WSUS server’s code-signing certificate. For instructions, see Local publishing.
2.6. Configure client computers to receive updates from the WSUS server
By default, your client computers receive updates from Windows Update. They must be configured to receive updates from the WSUS server instead.
[!IMPORTANT]
This article presents one set of steps for configuring client computers by using Group Policy. These steps are appropriate in many situations. But many other options are available for configuring update behavior on client computers, including using mobile device management. These options are documented in Manage additional Windows Update settings.
2.6.1. Choose the correct set of policies to edit
If you’ve set up Active Directory in your network, you can configure one or multiple computers simultaneously by including them in a Group Policy Object (GPO), and then configuring that GPO with WSUS settings.
We recommend that you create a new GPO that contains only WSUS settings. Link this WSUS GPO to an Active Directory container that’s appropriate for your environment.
In a simple environment, you might link a single WSUS GPO to the domain. In a more complex environment, you might link multiple WSUS GPOs to several organizational units (OUs). Linking GPOs to OUs will enable you to apply WSUS policy settings to different types of computers.
If you don’t use Active Directory in your network, you’ll configure each computer by using the Local Group Policy Editor.
2.6.2. Edit policies to configure the client computers
[!NOTE]
These instructions assume that you’re using the most recent versions of the policy editing tools. On older versions of the tools, the policies might be arranged differently.
-
Open the appropriate policy object:
- If you’re using Active Directory, open the Group Policy Management Console, browse to the GPO on which you want to configure WSUS, and select Edit. Then expand Computer Configuration and expand Policies.
- If you’re not using Active Directory, open the Local Group Policy Editor. The local computer policy appears. Expand Computer Configuration.
-
In the object that you expanded in the previous step, expand Administrative Templates, expand Windows components, expand Windows Update, and select Manage end user experience.
-
On the details pane, double-click Configure Automatic Updates. The Configure Automatic Updates policy opens.
-
Select Enabled, and then select the desired option under the Configure automatic updating setting to manage how Automatic Updates will download and install approved updates.
We recommend using the Auto download and schedule the install setting. It ensures that the updates you approve in WSUS will be downloaded and installed in a timely fashion, without the need for user intervention.
-
If desired, edit other parts of the policy, as documented in Manage additional Windows Update settings.
[!NOTE]
The Install updates from other Microsoft products checkbox has no effect on client computers receiving updates from WSUS. The client computers will receive all updates approved for them on the WSUS server. -
Select OK to close the Configure Automatic Updates policy.
-
Back in the Windows Update node of the tree, select Manage updates offered from Windows Server Update Service.
-
On the Manage updates offered from Windows Server Update Service details pane, double-click Specify intranet Microsoft update service location. The Specify intranet Microsoft update service location policy opens.
-
Select Enabled, and then enter the URL of the WSUS server in both the Set the intranet update service for detecting updates and Set the intranet statistics server text boxes.
[!WARNING]
Make sure to include the correct port in the URL. Assuming that you configured the server to use SSL as recommended, you should specify the port that’s configured for HTTPS. For example, if you chose to use port 8531 for HTTPS, and the server’s domain name is wsus.contoso.com, you should enter https://wsus.contoso.com:8531 in both text boxes. -
Select OK to close the Specify intranet Microsoft update service location policy.
Configure client-side targeting, if appropriate
If you’ve chosen to use client-side targeting, you should now specify the appropriate computer group for the client computers you’re configuring.
[!NOTE]
These steps assume that you’ve just completed the steps for editing policies to configure the client computers.
-
On the Manage updates offered from Windows Server Update Service details pane, double-click Enable client-side targeting. The Enable client-side targeting policy opens.
-
Select Enabled, and then enter the name of the WSUS computer group to which you want to add the client computers in the Target group name for this computer box.
If you’re running a current version of WSUS, you can add the client computers to multiple computer groups by entering the group names, separated by semicolons. For example, you can enter Accounting;Executive to add the client computers to both the Accounting and Executive computer groups.
-
Select OK to close the Enable client-side targeting policy.
2.6.3. Let the client computer connect to the WSUS server
Client computers will not appear in the WSUS Administration Console until they connect to the WSUS server for the first time.
-
Wait for the policy changes to take effect on the client computer.
If you used an Active Directory-based GPO to configure the client computers, it will take some time for the Group Policy Update mechanism to deliver the changes to a client computer. If you want to speed this up, you can open a command prompt window with elevated privileges and then enter the command gpupdate /force.
If you used the Local Group Policy Editor to configure an individual client computer, the changes take effect immediately.
-
Restart the client computer. This step makes sure that the Windows Update software on the computer detects the policy changes.
-
Let the client computer scan for updates. This scan normally takes some time.
You can speed up the process by using one of these options:
- On Windows 10 or 11, use the Settings app’s Windows Update page to manually check for updates.
- On versions of Windows before Windows 10, use the Windows Update icon in Control Panel to manually check for updates.
- On versions of Windows before Windows 10, open a command prompt window with elevated privileges and enter the command wuauclt /detectnow.
2.6.4 Verify the client computer’s successful connection to the WSUS server
If you’ve performed all the previous steps successfully, you’ll see the following results:
-
The client computer successfully scans for updates. (It might or might not find any applicable updates to download and install.)
-
Within about 20 minutes, the client computer appears in the list of computers displayed in the WSUS Administration Console, based on the type of targeting:
-
If you’re using server-side targeting, the client computer appears in the All Computers and Unassigned Computers computer groups.
-
If you’re using client-side targeting, the client computer appears in the All Computers computer group and in the computer group that you selected while configuring the client computer.
-
2.6.5. Set up the client computer’s server-side targeting, if appropriate
If you’re using server-side targeting, you should now add the new client computer to the appropriate computer groups.
-
In the WSUS Administration Console, find the new client computer. It should appear in the All Computers and Unassigned Computers computer groups in the WSUS server’s list of computers.
-
Right-click the client computer and select Change membership.
-
In the dialog, select the appropriate computer groups, and then select OK.
Intune is a great tool to deploy Windows Updates in all endpoints.
Probably when you have mobile devices that are out of the Company.
If you want to read more for Intune you can find interesting articles by Damien Van Robaeys in http://www.systanddeploy.com/
But there are lot companies that it hasn’t the budget to use Intune or for any other reason that maybe has.
In this case we can use WSUS (Windows Server Update Services) which can deploy the Windows Updates from one location in all endpoints.
So let’ start to explain
Before install WSUS
Before start the installation of WSUS you must decide how you will Plan the WSUS Deployment.
It’s recommended to read the article from Microsoft Docs Plan your WSUS Deployment
WSUS use the port 443 and https protocol.
If you don’t want to allow Internet Access in the WSUS Server you must allow the following URL in your firewall
- http://windowsupdate.microsoft.com
- http://*.windowsupdate.microsoft.com
- https://*.windowsupdate.microsoft.com
- http://*.update.microsoft.com
- https://*.update.microsoft.com
- http://*.windowsupdate.com
- http://download.windowsupdate.com
- https://download.microsoft.com
- http://*.download.windowsupdate.com
- http://wustat.windows.com
- http://ntservicepack.microsoft.com
- http://go.microsoft.com
- http://dl.delivery.mp.microsoft.com
- https://dl.delivery.mp.microsoft.com
How to install WSUS
The installation of WSUS Role it’s easy without complexity
So let’s start
- Open Server Manager
- Click Manage — Add Roles & Features
- Click Next

- Keep the default settings and click Next.

- If you don’t have add other Server in Server Manager just leave the default and click Next. Unless select the local Server and click Next.

- Check the Windows Server Update Services and at the same time click Add Features.

- Click Next

- Once again Next without Add any Feature

- Click once again Next. It’s just steps that proceed to finish the installation of WSUS.

- Don’t change anything for the Role Services of the Web Server and click Next.

- Windows Server Update Services Wizard. Just click Next

- We don’t need the option Sql Server Connectivity.

- You must select if you want to store the Windows Updates local in your Server or not

- Let’s explain the difference here.
- If you store the Windows Updates local the endpoints will download quicker the Windows Updates from the WSUS
- If you will not store the Windows Updates in your Server you save disk space but need more time the endpoints to download the Windows Updates from the WSUS.
- If you decide to store the Windows Updates it’s recommended to create a separate partition.
- Take your decision and click Next. In my Scenario i choose to store the Windows Updates and gave the path.

- Click Install and wait until finish.

How to configure WSUS
After finish the installation of the WSUS then you must configure the WSUS Server using Configuration Wizard.
This is one time configuration wizard that you must do before start using WSUS.
- Open the Server Manager
- Click in the Flag
- Click Launch-Post Installation Task

If you skip it by mistake then you can launch it from WSUS Server Console
- From the Server Manager click Tools — Windows Server Update Services

- Expand the Server Name. In my scenario is WSUS
- Select Options.
- From the right side click WSUS Server Configuration Wizard

- In the first step click Next.

- Click Next again

- Keep the default option Synchronize from Microsoft Updates.

- Specify proxy information if you have got one. Unless click Next without change anything.
- Click Start Connecting to Connect in Upstream Server.

- Specify the Language for your Windows Updates.

- Specify the products that you want to update. I select Windows Server 2012 , Windows Server 20016 and 2019.

- Specify the type of the Windows updates to download.

- Configure when you want to synchronize the WSUS with the Windows Updates.

- Check the Begin initial synchronization.Click Next

- Click Finish.
- You can see the Synchronization Status from the Console
Until finish the synchronization let’s go to create the Group Policies to deploy the Windows updates in the Endpoints that you would like.
How to configure Group Policy for WSUS
The last step after finish the Installation and Configuration of WSUS is to create a Group Policy for the WSUS.
In the Group Policy configure from which Server will request the Windows Updates the Endpoint.
- Create a new Group Policy
- Go in Computer Configuration > Policies > Administrative Templates > Windows Components > Windows Update.
- Edit the Configure Automatic Updates with any of the options that match in your environment. In this scenario i select 3 — Automatic download and notify for install and 0-Every Day

- Edit the Specify intranet Microsoft update service location. You must enter the URL of the intranet server which is in type of http:<fqdn>:8350

- Now Apply the GPO in every Organization Unit which include the Endpoints that will be receive Windows Updates from WSUS
- Once apply the GPO in the Endpoints you will be ask how can identify that the GPO apply and it’s sure that the Endpoint will retrieve Windows Updates from WSUS?
- One way is to open Server Manager — — Local Server
- Verify that in the Windows Updates says Download Windows updates only using managed updating service

- The other way is to open the registry
- Go in HKLMSOFTWAREPoliciesMicrosoftWindowsWindowsUpdate.

How to configure WSUS Computer Groups
Probably you will have Server , Workstations and different OS in your environment.
To target the Updates for the different OS and type of Endpoints you can create the Computer Groups.
The hierarchy depends from your infrastructure.
I will show you only how can create the Computer Group and add the Endpoints in the Group
- Right click in All Computers and select Add Computer Group

- Type the name of the Computer Group. Click Add

- Now right click on Updates and select New update View

- Tick the Updates are for a specific product
- Click in any produc.

- Select only the product that you prefer. For this scenario i select Windows 10

- Type the name of the View and click OK
- Now click on the new Update View
- Change the Filter to Unapproved

- Select the Windows Updates that you want to deploy in your Windows 10 Endpoints (in my example)
- As you can see i use the search to find the Update for the specific version of Windows 10
- Right click select Approve

- Select the Computer Group and select Approve for Install.

That’s it! Now base on which Computer has in Group and the Group Policy Settings will be install the Windows Updates.
As you can see it’s very easy when you separate with the Groups the types of your Endpoints because you can target the specific Windows Updates for the specific group of Endpoints very quickly.
How to Automatic Approval Updates
It’s not the recommended option for all the Windows Updates but only for the Security Updates.
We must keep every time all our Servers with the latest Security Updates to avoid any security hole in our systems.
It’s not easy to keep the process manual when you have hundred of Servers to maintain.
For this reason i will show you how can approve automatic all the Security Updates for your Windows OS
- Open the WSUS
- Click in the Options
- From the right side Select Automatic Approvals

- Click in the New Rule

- Tick the first 2 Options

- Now click in Any Classification

- Select only the Security Updates. Click OK

- Select any Product

- Select only the product that you want to automatic approve the Security Updates. For the scenario i select Windows Server 2016.Click OK

- Click in all computers

- Select the Computer Group which include the specific Servers or Workstations with the appropriate Windows OS. Click OK

- If you have already download the Windows Updates then you must click in Run Rule to approve all the Security Updates.
- You don’t need to click in Run Rule for the next updates that will download or if you don’t have start to download any Windows update yet.

- Now you can easily create a new Update View which will include only the Security Updates to verify that all has been approved

Remember that until now we have only Automatic Approve all the Security updates.
If you want to proceed with automatic installation of the Security Updates you must change your Group Policy settings.
Read the paragraph How to configure Group Policy for WSUS to understand which settings must be change in Group Policy
To be honest it’s not very easy process because must be dedicate specific time to find and approve the Windows Updates for every Category.
But remember that this will happened only once and create an automate procedure while you have centralize your Windows Updates and know exactly which Endpoints are out of Date and must be Updated.
Have a nice weekend !!
Be Safe

Windows Server Update Services or WSUS is a Microsoft product that allows us to centrally manage patches for Microsoft operating systems and other Microsoft products. With Windows Server 2016, the process is basically the same as previous server operating systems to install and configure the product and generally get up and running with WSUS managing our patches in a particular environment. Let’s look at how to install and configure Windows Server 2016 WSUS.
Installing the Windows Server Update Services role is very straightforward and is basically what we would expect with installing any role or feature. This is done through Server Manager. The process is fairly next, next, finish in nature.
Here we select a role based installation.

Select our server.
Choose Windows Server Update Services all the way at the bottom of the Server Roles.
We will get prompted for additional features that need to be installed.
Next, Next finish process underway…
Finally, we get to the Role Services and should see WID Connectivity and WSUS Services.
Here we select a file path to use for storing updates.
We will have Web Server Role services installed with WSUS.
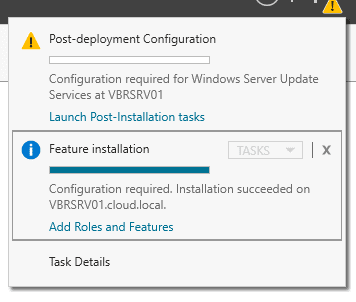
After the role service is installed, we will see a exclamation bang in the upper right hand corner of our Server Manager. It will show Post-deployment Configuration that will need to be done. Click this and it will finish things out.
WSUS Specific Configuration
Now we begin the WSUS configuration itself where we actually setup our configuration for the WSUS server portion.
Since I don’t have another WSUS server I am wanting to synchronize from, I choose to Synchronize from Microsoft Update which pulls directly from Microsoft.
Choose your connectivity options here. If you use a proxy, you need to configure it.
Now, click the Start Connecting button. This process will take a long time depending on your connection.
Click Next.
Choose your language here.
On our Choose Products screen we actually choose operating systems and products we want to pull down and store updates for.
Next, we choose our Classifications where we can set the types of updates for the selected operating systems. This includes choices on Critical updates, drivers, feature packs, security updates, etc.
Next is our Sync Schedule where we configure when we want a synchronization with our upstream source server to happen. We can also set the number of synchronizations per day.
On the Finished screen, we can choose to Begin initial synchronization which will start pulling down the updates that meet the criteria.
The basic summary screen tells us what we might want to think about doing next including setting up SSL, creating computer groups, etc.
That concludes the basic Windows Server 2016 Install and Configure of WSUS.
Reporting Services
If you try and click on any data in the WSUS screen such as updates needed, etc, you will quickly find several errors or warning pop up about SQL Server 2012 CLR Types and Report Viewer 2012 binaries.
After installing the CLR types, I was able to run the Report Viewer 2012 Runtime.
Thoughts
In this basic tutorial on how to install and configure Windows Server 2016 WSUS, it is easy to see that the process is fairly straightforward to get the role installed and configured. Also, installing the needed report components allows us to view reports from the WSUS console on the server itself. In our next WSUS post, we will take a deeper dive into interacting with WSUS, troubleshooting, and other configuration.
Windows Server Update Services (WSUS) can use a lot of resources, so why not use Windows Server Core and make the most of the resources you have. In this post I’ll go through the initial steps on how to deploy and configure a WSUS server using command line and PowerShell. Important note: If you need the to boot Windows Server 2016 ISO from a USB flash drive, use Rufus.
Installing Windows Server 2016 Core
Boot the server from the Windows Server 2016 media and on the Select the Operating System you want to install screen, select the option Windows Server 2016 Standard or Datacenter edition. The other options with Desktop Experience in brackets are the options for the other server editions with a GUI also installed. Important Note: You can no longer add and remove the GUI (Desktop Experience) with Windows Server 2016 as you could with Windows Server 2012 & 2012 R2. This is due to numerous problems with keeping the installation and removal process consistent with updates. With Windows Server 2016, the only way to add or remove the GUI is to re-install and select one of the server editions with the Desktop Experience option.
Initial Configuration
Once the install process has completed, you will be prompted with a command line window, and asked to set the Administrator password.
- Set the local Administrator password.
- Type sconfig to get the Server Configuration menu. It’s pretty straight forward.
- You’ll need to configure at least the Network Settings — IP address, subnet mask, gateway, and DNS.
- You may want to enable Remote Desktop.
- Add the server to the domain — you’ll be asked if you’d like to change the computer name, and prompted to restart the server.
- After the restart, log in as a user with administrator privileges to the server.
Tip: The sconfig menu is also present in the GUI version of Windows Server 2016, making initial configuration of new servers easier.
Additional Storage Configuration
You may want to configure additional locally attached disks or iSCSI/MPIO storage. Creating new volumes that are locally attached can be done via the diskpart command line tool. Below are the commands to create a new, NTFS formatted volume, with the drive letter of E: and the name “WSUS Content”, from a second disk in the server using the diskpart tool. First, run diskpart from the command line, then use the following commands:
|
|
iSCSI storage can be configured using the same GUI tools you would use in the GUI version of Windows Server. The MPIO feature must be installed before the tool is available. You can do this via PowerShell:
|
|
When MPIO is installed you can load the MPIO utility using mpiocpl. For the iSCSI utility you can use iscsicpl. iSCSI is installed as part of the base Windows Server 2016 feature set.
Install Windows Server Update Services (WSUS)
If you’ve just logged on to the server, type PowerShell into the command line window before running any of the commands below.
- First we need to install the WSUS feature:
|
|
Now we need to run some post install tasks.
- We’ll create a directory for the WSUS content on the E: drive.
- To configure WSUS to use the directory you just created and the Windows Internal Database (WID is based on SQL Express), run the following command:
|
|
- Alternatively you might want to use an external SQL server for the WSUS database, if so run the following command instead:
|
|
WSUS is now running and able to be configured further. This is possible with PowerShell, but not as straightforward as the installation above. For this next section I’ll be chickening out and using the GUI using the WSUS MMC on a Windows 10 admin PC. To obtain the WSUS MMC download and install the following:
- Remote Server Administration tools (RSAT) for Windows 10
- Microsoft Report Viewer 2012 Runtime redistributable
- Microsoft System CLR Types for Microsoft SQL Server 2012: x64 version, x86 version
In case the links to Microsoft System CLR Types fail in future, here is the main download page link. This page links to components from the Microsoft SQL Server 2012 Feature Pack, you need to go to the Install Instructions section and download the specific component you need.
Configuring Windows Server Update Services
Once you have downloaded and installed all the software listed above on your admin PC, you can continue with the configuration.
- Open the Windows Service Update Services Microsoft Management Console (WSUS MMC).
- You should see a Before You Begin wizard. Click Next.
- Join the Microsoft Update Improvement Program if you wish.
- Choose Upstream server, as this is the first WSUS server you’ll choose Synchronize from Microsoft Update.
- Specify the Proxy Server settings if needed.
- Click Start Connecting. This may take a while.
- Select the applicable languages for your environment.
- Select the applicable Products. I recommend selecting all products as we’ll only be downloading updates that we actually need.
- Select the Classifications. I recommend selecting all except Drivers and Driver Sets. Drivers in WSUS increase the size of the database immensely.
- Configure the Sync Schedule. I recommend leaving this on manual until setup and synchronisation has been completed.
- Check the Begin initial synchronization box. This may also take a while.
- Click Finish.
Once the initial configuration is complete, now we can start to configure WSUS for every day operation.
- In the WSUS MMC go to the Options node.
- Setup a Synchronization Schedule. I recommend once or twice a day, out of regular hours. Click OK.
- Go to Automatic Approvals.
- There’s a built-in rule to automatically approve Critical and Security updates, meaning that they will be downloaded and distributed via WSUS without any admin interaction. I recommend enabling this, but don’t run the rule.
- You may also want to add a rule for Definition Updates from Exchange, Office, and Windows Defender if applicable to you. Click OK.
- Now go to Computers.
- Set the option here to Use Group Policy or registry settings on computers and click OK.
- Go to E-Mail notifications and enable them if you want status reports and Emails about the new updates that have been synchronised. Click OK.
- In the WSUS MMC, go to the Computers node.
- Create the computer groups that you require here. I recommend a ‘pilot’ group and a ‘regular’ group both for client devices and servers.
Configuring Group Policy
To enable your clients to get updates from WSUS using the settings above, you’ll need to configure the group policy for them.
- Open the Group Policy Management MMC and go to the Group Policy Objects node.
- Right click on the node and select New to create a new GPO for WSUS. Give it a name and click OK.
- Right click on the new GPO and click Edit to open it.
- Navigate to Computer Configuration/Policies/Administrative Templates/Windows Components/Windows Update
- Go to the setting Specify intranet Microsoft update service location.
- Set it to
http://wsusserver.contoso.com:8530in both text boxes. - Go to Enable client-side targeting and enter the name of a group that you created in WSUS.
- For multiple groups, repeat steps 2 — 7 for each group.
- You can use Active Directory Security Groups to control which client devices get which GPO and therefore go into the desired WSUS group.
There lots of other settings in GPO to configure Windows Update that I recommend taking a look, specifically Configure Automatic Updates which controls when client devices install updates.
Managing Updates
After some time (approximately 24 hours) your client devices should have contacted the WSUS server and be in the correct group. Now you need to approve the updates required for your environment.
- On the overview of your WSUS server, click on Updates needed by computers.
- Change the drop down menu Approval to Unapproved and wait for the list to refresh.
- Right-click on the Title bar and enable the Supersedence column.
- Click on the very tiny Supersedence column to sort the updates by Supersedence.
- Approve the top critical, security and any other updates you want to be installed on your client devices.
- Once the client devices have downloaded, installed, and reported back to the WSUS server, you will have a better idea if any more updates are required.
Maintenance and Troubleshooting
Keeping WSUS running over time requires some maintenance. I created a custom PowerShell script that runs every day to perform the maintenance on the database. More specifically it declines and deletes old updates, and old computers. It can also e-mail a notification with information about it’s clean up run. My script is available on the Microsoft TechNet Gallery, the PowerShell Gallery and I’ve also posted about it here. You can also clean up the WSUS database manually using the Server Cleanup Wizard found in Options. Here are the PowerShell commands to do this:
|
|
You may sometimes encounter an error when trying to connect to the WSUS server using the MMC. Error: Unexpected Error, and appears as Event ID 7053 in Event Viewer.
I’ve known this error to occur frequently. To combat it we must reconfigure some IIS AppPool settings relating to WSUS, but as this is a Windows Server Core installation the regular IIS configuration tool isn’t available. Luckily, we can do this using PowerShell: Log on to the WSUS server with an administrative account and run PowerShell from the command line, then type the following commands:
|
|
Finally, you can also try the following command, if needed:
|
|
If you’d like to contact me, please leave a comment, send me a tweet or DM, or you can join my Discord server.
-Mike
In this article, we are going to learn the ‘Complete Guide to Install and Configure WSUS Server 2016 (Windows Server Update Services)’. Windows Server Update Services (WSUS), formerly known as Software Update Services, is a computer program and network service developed by Microsoft Corporation that enables administrators to distribute Microsoft-issued updates and hotfixes for Microsoft products in a corporate environment.
Before proceeding with installation and configuration, make sure your machine meets the following requirements:
- The static IP address configured.
- Turned off the Windows firewall.
- The latest security updates from Microsoft are installed.
- The Internet connection is working.
Complete Guide to Install and Configure WSUS Server 2016 (Windows Server Update Services)
Follow the below Steps To Install and Configure WSUS Server 2016 (Windows Server Update Services):
Step 1. Open Server Manager.
Step 2. Click Add Role and Features.
Step 3. Read the important requirements and try to meet them (this includes a strong password for the administrator account, stable IP configuration, and installation of the latest security updates). Click next to continue.
Step 4. Choose Role-based or Feature-based installation and click Next.
Step 5. Select a server from the server pool, and click next.
Role-based or Feature-based installation
Step 6. Select the destination server for Windows Server Update Services from the server pool and click Next.
Windows Server Update Services
Step 7: Click Add Features
Step 8: Click Next
Step 9: Click Next
Step 10: Select WID Connectivity & WSUS Services then Click on Next.
WSUS Role Services
Step 11: On the Content location selection page, type a valid location to store the updates. For example, you can create a folder named WSUS at the root of Private Drive D for this purpose and type WSUS as a valid location.
WSUS Store Update Path
Step 12: The Web Server Role (IIS) page opens. Review the information, and then click Next.
Step 13: In select the role services to install for Web Server (IIS), retain the defaults, and then click Next.
Select the role services to install for Web Server (IIS)
Step 14: Click Install and the installation will begin which can take 10 – 15 minutes to complete.
Install Role
Step 15: Now you can see the WSUS installation process is completed.
Installation Completed
Also Read – Step by Step Configure WDS Server (Windows Deployment Services) On Windows Server 2016
Configuring WSUS Server:
Once the WSUS installation is complete, in the summary window on the Installation progress page, click Launch Post-Installation tasks. The text changes, requesting: Please wait while your server is configured. When the task has finished, the text changes to Configuration successfully completed. Click Close.
Post-Installation tasks
Step 1: Open your server manager dashboard, Click Tools -> Windows Server Update Services
Step 2: Click Next
Configuring WSUS Server
Step 3: Click Next
Click Next
Step 4: Select Synchronize From Microsoft Update or another server & click on Next.
Synchronize From Microsoft Update
Step 5: If you have a proxy server in your network, configure the proxy settings otherwise click Next
proxy server
Step 6: Click Start Connecting to connect to the upstream server of Microsoft
Start Connecting to connect to the upstream server of Microsoft
Step 7: Select language and click Next.
Select language
Step 8: Select the product you need to download updates for. Click Next.
Select the product
Step 9: Select the type of updates and click Next
Select the type of updates
Step 10: Select Synchronize manually and click Next. You can also set up an automatic schedule for synchronization.
automatic schedule for synchronization
Step 11: Click Next.
Click Next
Step 12: Click Finish.
Click Finish
As you can see above we have successfully Configure WSUS Server 2016. open update service and click on synchronizing.
WSUS Server 2016
WSUS Update Snapshot:-
WSUS Update
Also Read – Tips For Troubleshooting WSUS Client That Are Not Reporting To The WSUS Server
That’s all, In this article, we have explained the Complete Guide to Install and Configure WSUS Server 2016 (Windows Server Update Services). I hope you enjoy this article. If you like this article, then just share it. If you have any questions about this article, please comment.
Now that you know what is the role of WSUS in an infrastructure and which features can offer, you are ready to implement it.
Before you start designing and installing WSUS on Windows Server 2016, you should take a look at the minimum requirements that your infrastructure needs to meet.
Install Windows Server Update Services (WSUS)
After you open Server Manager, click Manage and then Add Roles and Features.
In the Before You Begin section, click Next to continue.
In the Installation Type section, select Role-based or feature-based installation and click Next to continue.
In the Server Selection section, select Select a server from the server pool, and then the server to install the role. Click Next to continue.
Under Server Roles, select Windows Server Update Services. In the window that appears, click the Add Features button while you have ticked Include management tools, and then click Next to continue.
In the Features section, you do not have to choose anything, click Next to continue.
In the WSUS section, click Next to continue.
In the Role Services subsection, select the WID Connectivity and WSUS Services options and click Next to continue. WID (Windows Internal Database) means that an internal database will be created on the machine. This is the proposed regulation for the majority of cases of small and medium-sized enterprises. For larger installations using SQL Server, enable the SQL Server Connectivity option.
In the Content sub-section, enable the Store update option in the following location option, and then type the location (local or network) to store the system updates. Make sure you have enough GB of free disk space to report. Click Next to continue.
In the Web Server Role (IIS) section, click Next to continue.
In the Role Services subsection, all necessary services are already pre-defined. Click Next to continue.
In the Confirmation section, take a look at the features to be installed and click the Install button to start the process.
Then, in the Results section, you will see the progress of the installation. You can leave the window open or close it, the installation will be completed regardless of your choice.
At this point, WSUS is installed on Windows Server 2016. However, this was the first step. You will need now to complete the WSUS configuration wizard to enable WSUS.
You can use the Windows Server Update Services (WSUS) update server to deploy Microsoft product updates (Windows, Office, SQL Server, Exchange, etc.) to computers and servers in the company’s local network. In this article, we’ll walk you through how to install and configure the WSUS update server on Windows Server 2022/2019/2016, or 2012 R2.
Contents:
- How to Install WSUS Role on Windows Server 2016/2016/2012R2?
- Initial WSUS Configuration on Windows Server
- How to Install WSUS Management Console on Windows 10 and 11?
- Optimizing WSUS Performance
How does WSUS work?
The WSUS server is implemented as a separate Windows Server role. In general terms, the WSUS service can be described as follows:
- After installation, the WSUS server is scheduled to synchronize with Microsoft Update servers on the Internet and download new updates for selected products;
- The WSUS administrator selects which updates to install on company workstations and servers and approves their installation;
- WSUS clients (computers) on the local network download and install updates from your update server according to configured update policies.
How to Install WSUS Role on Windows Server 2016/2016/2012R2?
Starting with Windows Server 2008, WSUS is a separate role that can be installed through the Server Management console or using PowerShell.
If you are deploying a new WSUS server, we recommend that you install it on the latest release of Windows Server 2022 (installation on Windows Server Core is possible).
To install WSUS, open the Server Manager console and check the Windows Server Update Services role (the system will automatically select and offer to install the necessary IIS web server components).
In the next window, choose which WSUS role services you want to install. Be sure to check the WSUS Services option. The next two options depend on which SQL database you plan to use for WSUS.
Server settings, update metadata, and WSUS client information are stored in a SQL Server database. As a WSUS database you can use:
- Windows Internal Database (WID) – built-in Windows database (WID Connectivity option). This is the recommended and workable option even for large infrastructures;
- A separate Microsoft SQL Server database is deployed on a local or remote server. You can use MS SQL Enterprise, Standard (licensing required), or the free Express edition. This is the SQL Server Connectivity option.
The Windows Internal Database) is recommended if:
- You don’t have unused MS SQL Server licenses;
- You are not planning to use WSUS load balancing (NLB WSUS)
- When deploying a downstream (child) WSUS server (for example, in branch offices). In this case, it is recommended to use the built-in WSUS database on secondary servers.
In the free SQL Server Express Edition, the maximum database size is limited to 10 GB. The Windows Internal Database is limited to 524 GB. For example, in my infrastructure, the size of the WSUS database for 3000 clients was about 7GB.
If you install the WSUS role and the MS SQL database on different servers, there are some limitations:
- SQL Server with WSUS database cannot be an Active Directory domain controller;
- The WSUS server cannot be deployed on a host with the Remote Desktop Services role.
The default WID database is called SUSDB.mdf and is stored in the folder %windir%widdata. This database supports only Windows authentication (not SQL). The internal (WID) database instance for WSUS is called server_nameMicrosoft##WID.
The WSUS WID database can be administered through SQL Server Management Studio (SSMS) if you specify the following connection string: \.pipeMICROSOFT##WIDtsqlquery.
If you do not have enough disk space to store update files, disable this option. In this case, WSUS clients will receive approved update files from the Internet (a viable option for small networks).
If you want to store update files locally on the WSUS server, enable the option Store updates in the following locations and specify the directory path. This can be a folder on a local disk (a separate physical or logical volume is recommended), or a network location (UNC path). Updates are downloaded to the specified directory only after they have been approved by the WSUS administrator.
The size of the WSUS database is highly dependent on the number of Microsoft products and the Windows versions you plan to update. In a large organization, the size of update files on a WSUS server can reach hundreds of GB.
If you do not have enough disk space to store update files, disable this option. In this case, WSUS clients will receive approved update files from the Internet (a viable option for small networks).
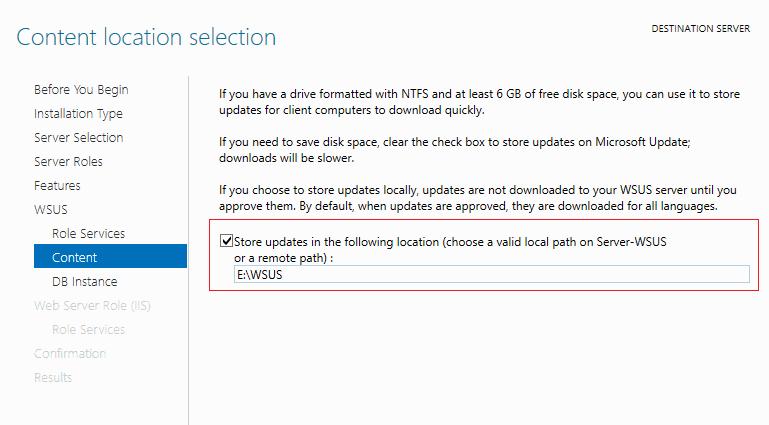
You can also install a WSUS server with an internal database (WID) using the following PowerShell command:
Install-WindowsFeature -Name UpdateServices, UpdateServices-WidDB, UpdateServices-Services, UpdateServices-RSAT, UpdateServices-API, UpdateServices-UI -IncludeManagementTools
Initial WSUS Configuration on Windows Server
After you finish installing the WSUS role, you need to complete its initial configuration. Open Server Manager and select Post-Deployment Configuration -> Launch Post-Installation tasks.
You can use the WsusUtil.exe console tool to manage WSUS from the command prompt. For example, to change the path to the WSUS update files directory, run:
CD "C:Program FilesUpdate ServicesTools"
WsusUtil.exe PostInstall CONTENT_DIR=D:WSUS
Or, for example, you can switch your WSUS to an external SQL Server database:
wsusutil.exe postinstall SQL_INSTANCE_NAME="MUN-SQL1WSUSDB" CONTENT_DIR=D:WSUS_Content
Then open the Windows Server Update Services console. The WSUS Update Server Initial Configuration Wizard starts.
Specify whether the WSUS server will download updates from the Microsoft Update site directly (Synchronize from Microsoft Update) or if it should receive them from an upstream WSUS server (Synchronize from another Windows Update Services server). Downstream WSUS servers are usually deployed at remote sites with a large number of clients (300+) to reduce the load on the WAN link.
On Windows 10 and 11, you can use Delivery Optimization to reduce the bandwidth usage of update traffic on your communication channels.
If your access the Internet through a proxy server, you need to specify the address and port of the proxy server, as well as authentication credentials.
Next, check the connection to the upstream update server (or Windows Update). Click Start Connecting.
Then you need to select the product languages for which WSUS will download updates. We select English (the list of the languages can further be changed from the WSUS console).
Then specify the list of products for which the WSUS should download updates. Select only those Microsoft products that are used in your environment. For example, if you are sure that there are no Windows 7 or Windows 8 computers left on your network, don’t select these options. This will significantly save space on the WSUS server drive.
Be sure to include the following general sections in the WSUS classification:
- Developer Tools, Runtimes, and Redistributable — used to update Visual C++ Runtime libraries;
- Windows Dictionary Updates in the Windows category;
- Windows Server Manager – Windows Server Update Services (WSUS) Dynamic Installer.
On the Classification Page, you need to specify the types of updates to be deployed via WSUS. It is recommended to select: Critical Updates, Definition Updates, Security Packs, Service Packs, Update Rollups, and Updates.
The Windows 10 build upgrades (21H2, 20H2, 1909, etc.) in the WSUS console are included in the Upgrades class.
Configure your update synchronization schedule. It is recommended to use the automatic daily synchronization of the WSUS server with Microsoft Update servers. The WSUS synchronization should be performed at night, in order not to impact the Internet channel during business hours.
The initial synchronization of the WSUS server with the upstream update server may take up to several days, depending on the number of products you chose earlier and your ISP.
After the wizard is done, the WSUS console will start.
There are several sections in the WSUS console tree:
- Updates – available updates on the WSUS server (here you can manage the update approvals and assign them for installation);
- Computers – here you can manage WSUS client groups (computers, servers, test, and production groups, etc.);
- Downstream Servers – allows you to configure whether you receive from Windows Update or an upstream WSUS server;
- Synchronizations – update synchronization schedule;
- Reports –different WSUS reports;
- Options –WSUS configuration settings.
Clients can now receive updates by connecting to the WSUS server on port 8530 (in Windows Server 2003 and 2008, port 80 is used by default). Check that this port is open on the WSUShost:
Test-NetConnection -ComputerName yourwsushost1 -Port 8530
You can use a secure SSL connection on port 8531. To do this, you need to bind a certificate to the WSUS Administration website in IIS.
If the port is closed, create an allow rule in Windows Defender Firewall.
How to Install WSUS Management Console on Windows 10 and 11?
You use the Windows Server Update Services console (wsus.msc) to manage WSUS. You can manage WSUS hosts either using the local console or over the network from a remote computer.
The WSUS Administration Console for Windows 10 or 11 is installed from the Remote Server Administration Tools (RSAT). To install the Rsat.WSUS.Tool component, run the following PowerShell command:
Add-WindowsCapability -Online -Name Rsat.WSUS.Tools~~~~0.0.1.0
If you want to install the WSUS console on Windows Server, use the command:
Install-WindowsFeature -Name UpdateServices-Ui
When you install WSUS on Windows Server, two additional local groups are created. You can use them to grant users access to the WSUS management console.
- WSUS Administrators
- WSUS Reporters
To view reports about updates and clients on WSUS, you must install:
- Microsoft System CLR Types for SQL Server 2012 (SQLSysClrTypes.msi);
- Microsoft Report Viewer 2012 Runtime (ReportViewer.msi).
To view different update reports in the WSUS console, you must install the optional Microsoft Report Viewer 2008 SP1 Redistributable (or higher) components on your server.
If these components are not installed, then when generating any WSUS report, an error will appear:
The Microsoft Report Viewer 2012 Redistributable is required for this feature. Please close the console before installing this package.
Optimizing WSUS Performance
This section describes a few tips for optimizing the performance of the WSUS Update Server in a real-world environment.
- For WSUS to work properly, the update host must have at least 4 GB of RAM and 2CPU free;
- With a large number of WSUS clients (more than 1500), you may experience significant performance degradation of the IIS WsusPoll pool that distributes updates to clients. Error 0x80244022 may appear on clients, or when starting the WSUS console, it may crash with an error Error: Unexpected Error + Event ID 7053 in the Event Viewer (
The WSUS administration console has encountered an unexpected error. This may be a transient error; try restarting the administration console. If this error persists).To resolve this issue, you need to add more RAM to your WSUS host and optimize your IIS pool settings as recommended in the article. Use these PowerShell commands:
Import-Module WebAdministration
Set-ItemProperty -Path IIS:AppPoolsWsusPool -Name queueLength -Value 2500
Set-ItemProperty -Path IIS:AppPoolsWsusPool -Name cpu.resetInterval -Value "00.00:15:00"
Set-ItemProperty -Path IIS:AppPoolsWsusPool -Name recycling.periodicRestart.privateMemory -Value 0
Set-ItemProperty -Path IIS:AppPoolsWsusPool -Name failure.loadBalancerCapabilities -Value "TcpLevel" - Enable automatic approval for Microsoft antivirus signature/definition updates. Otherwise, WSUS can slow down significantly and consume all available RAM.
Antivirus checks can negatively impact WSUS performance. In the built-in Microsoft Defender Antivirus in Windows Server, it is recommended to exclude the following folders from the Real-time protection scope:
- WSUSWSUSContent;
- %windir%widdata;
- SoftwareDistributionDownload.
Stay tuned!

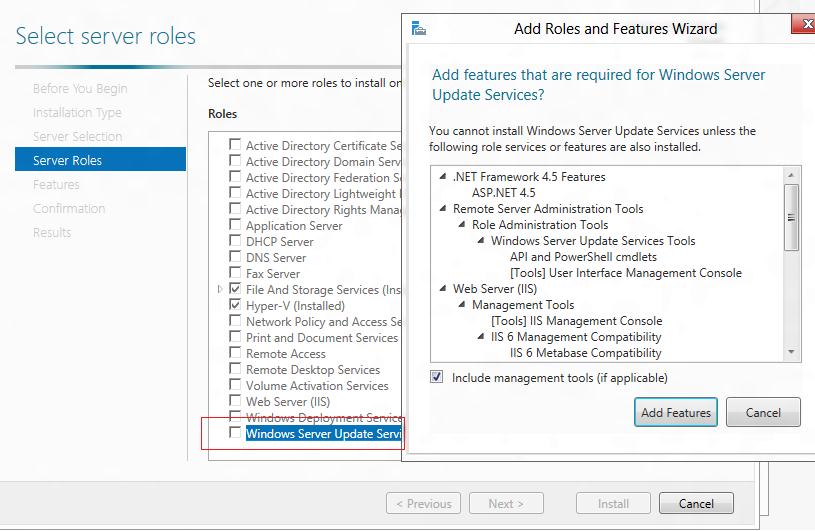
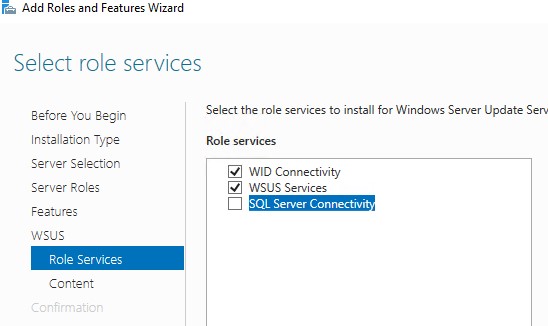
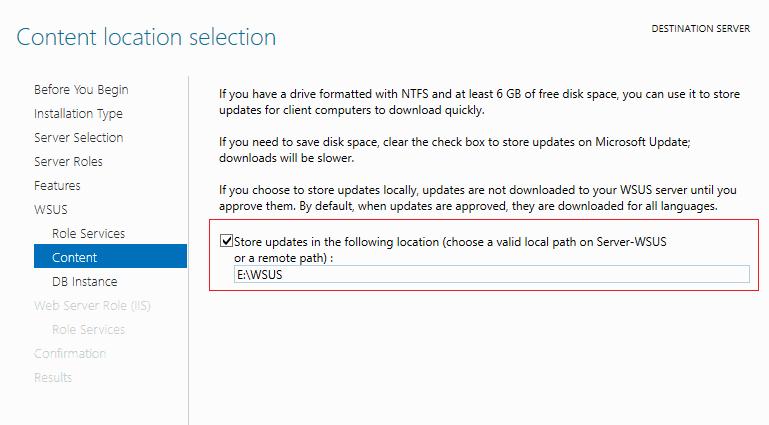
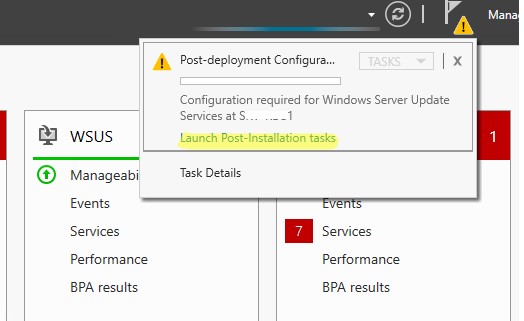
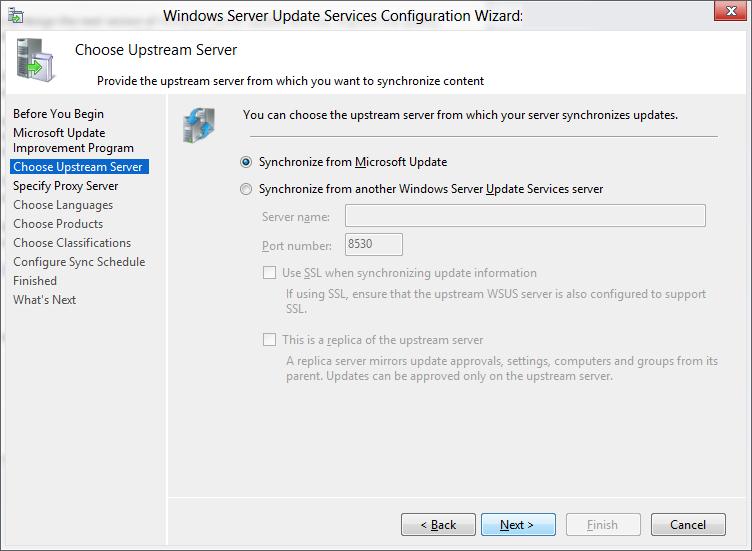
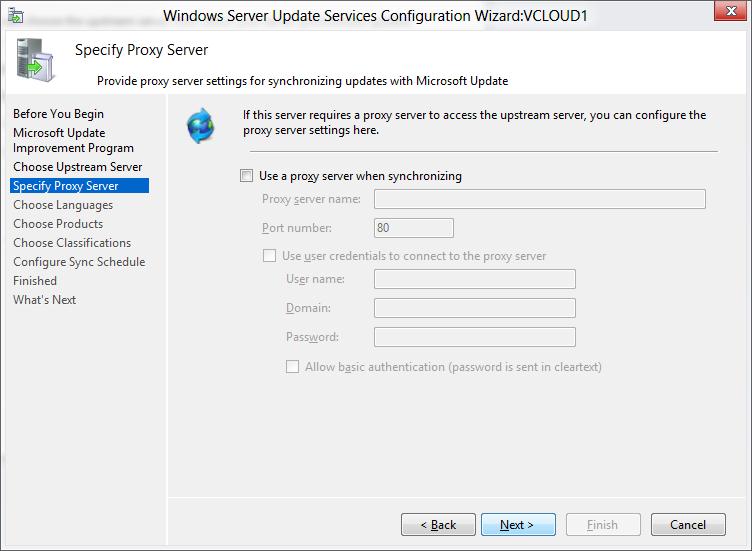
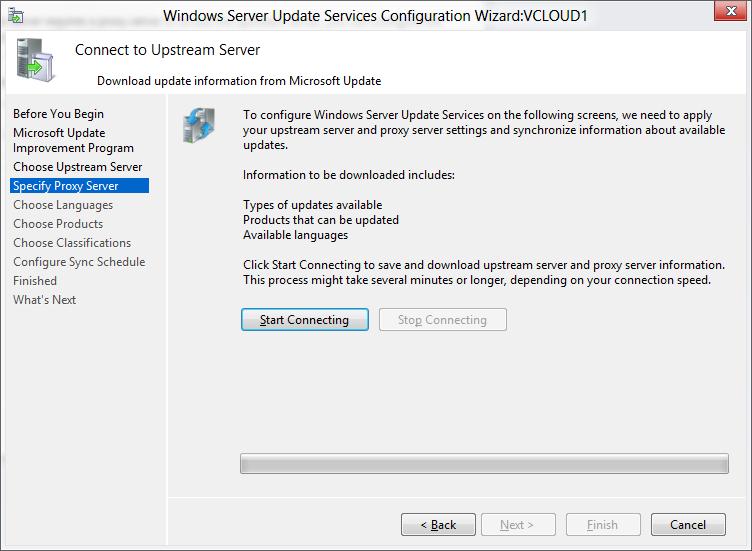
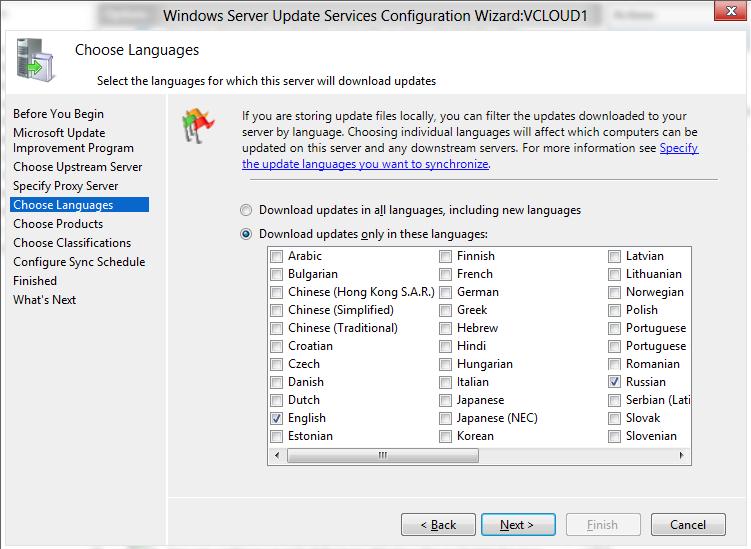
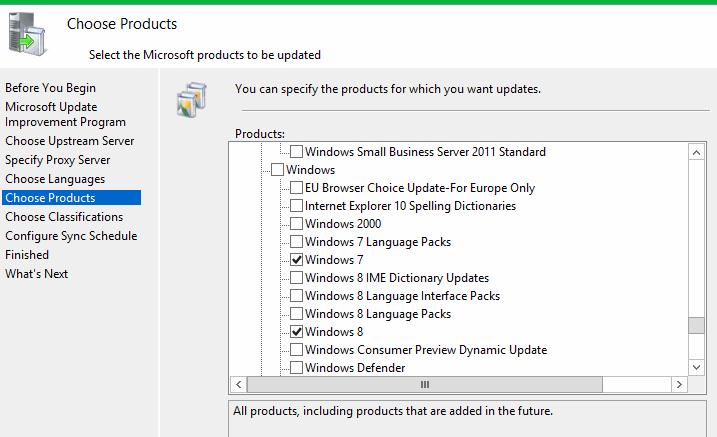
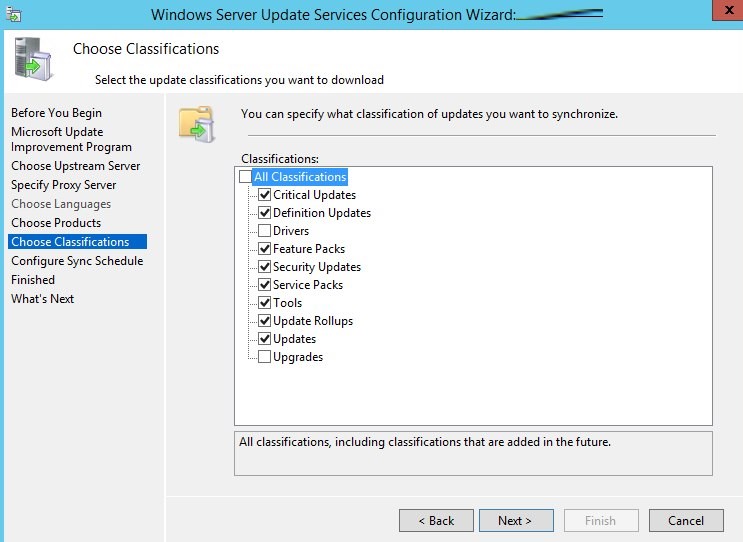
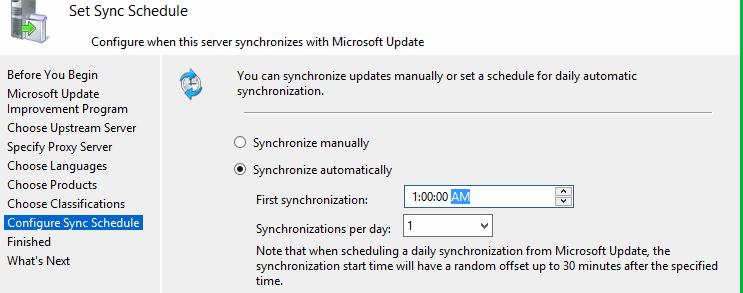
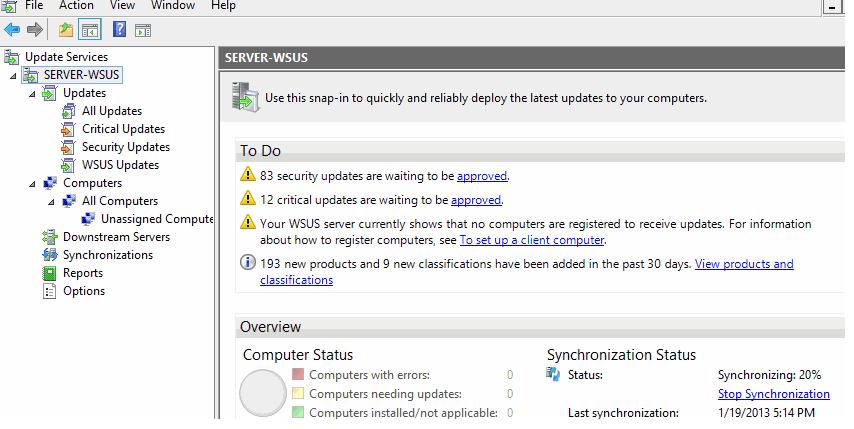
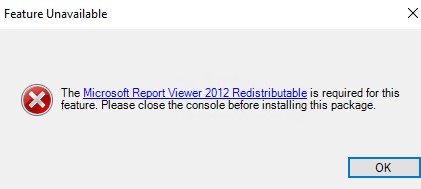
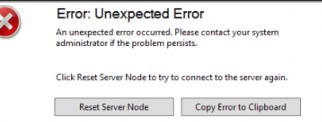 Для решения проблемы нужно добавить RAM на сервер и оптимизировать настройки пула IIS в соответствии с рекомендациями в статье. Воспользуетесь такими командами:
Для решения проблемы нужно добавить RAM на сервер и оптимизировать настройки пула IIS в соответствии с рекомендациями в статье. Воспользуетесь такими командами: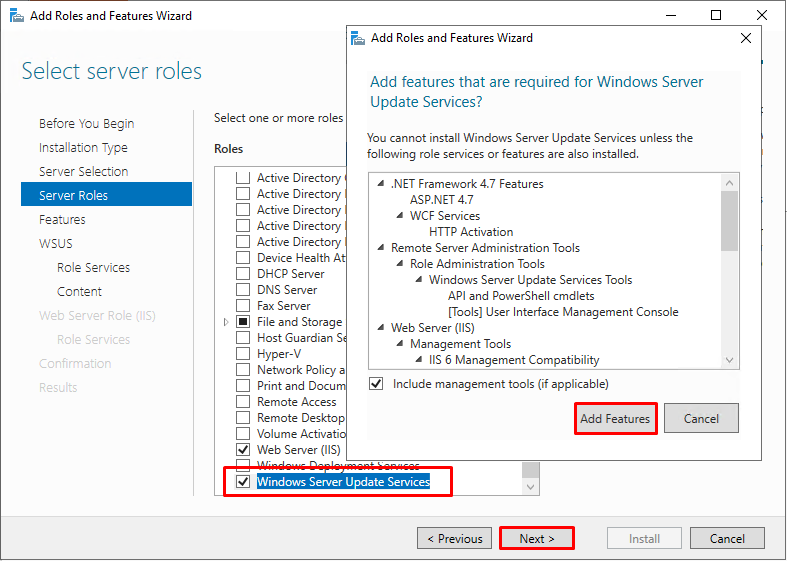
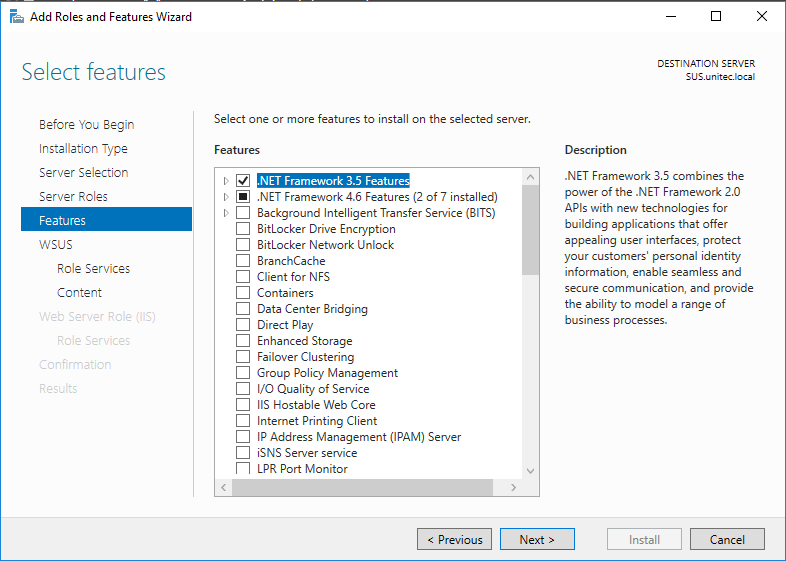
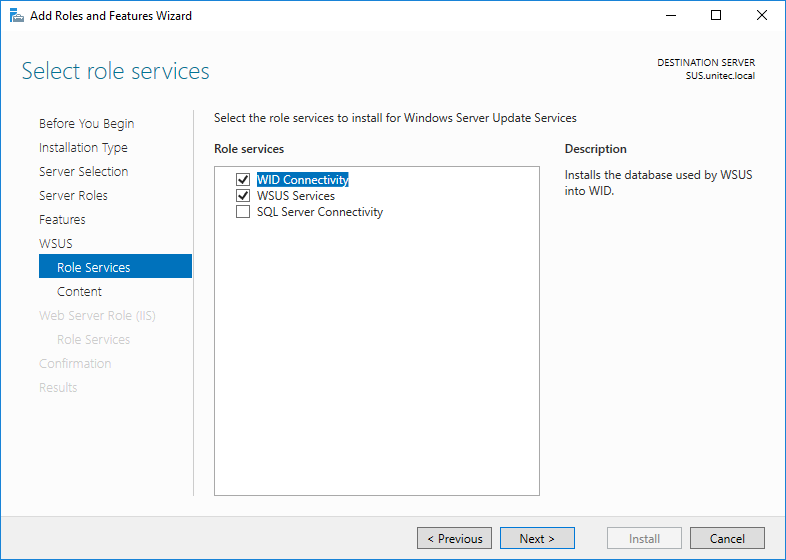
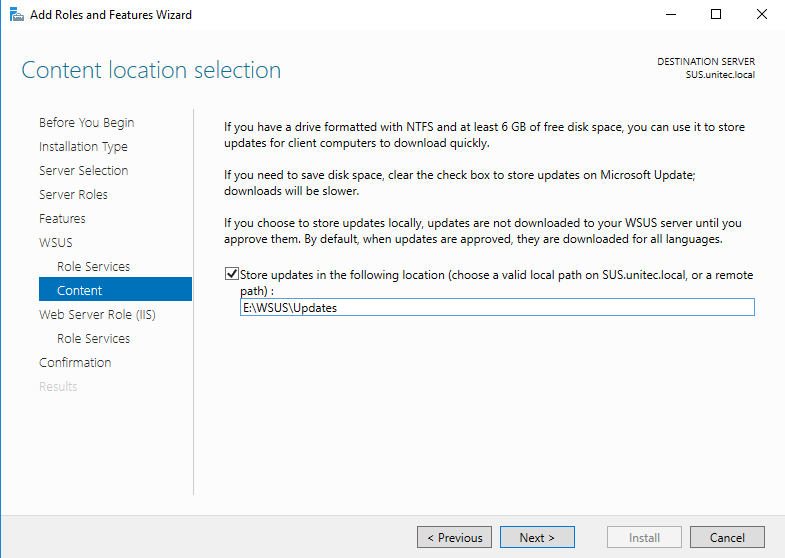
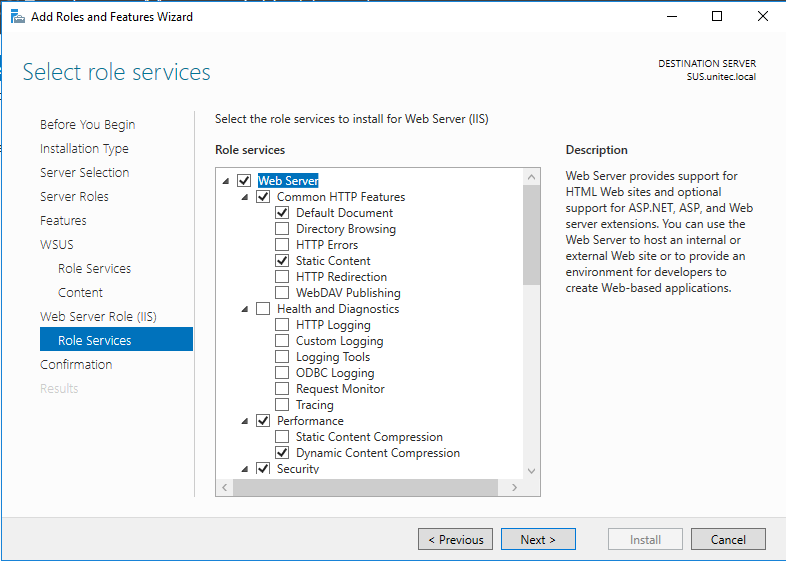
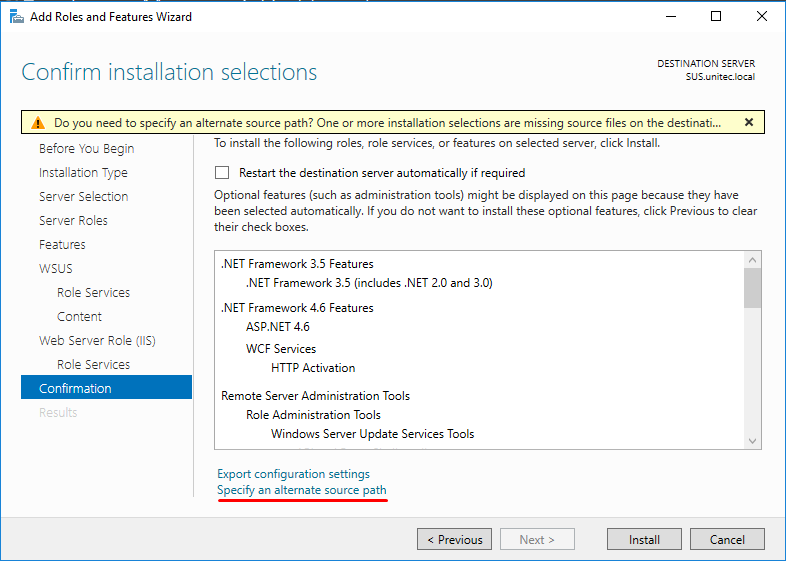
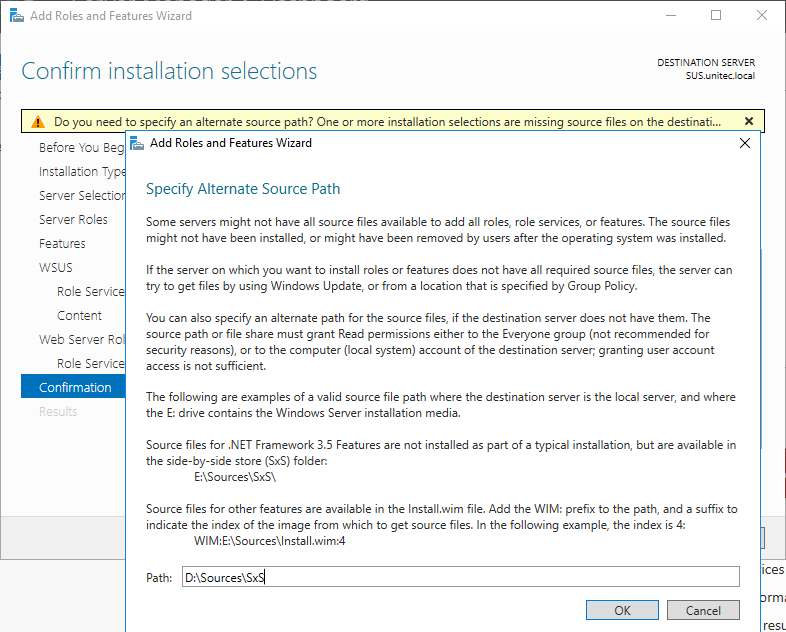
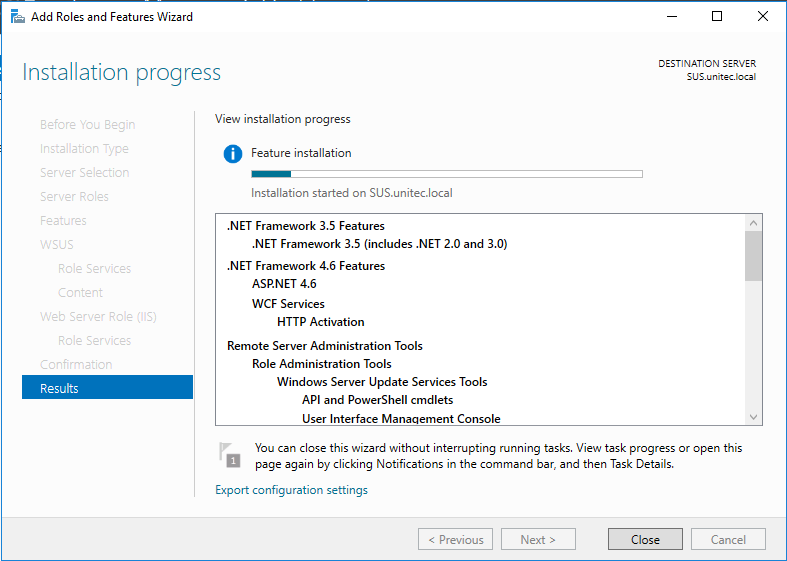

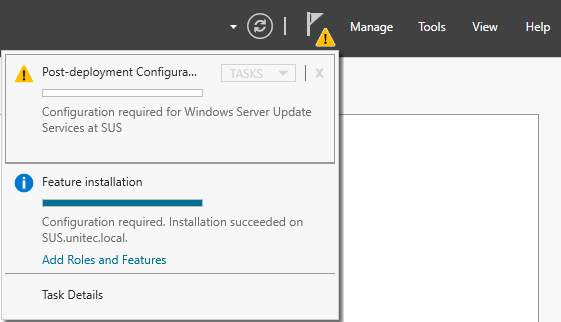
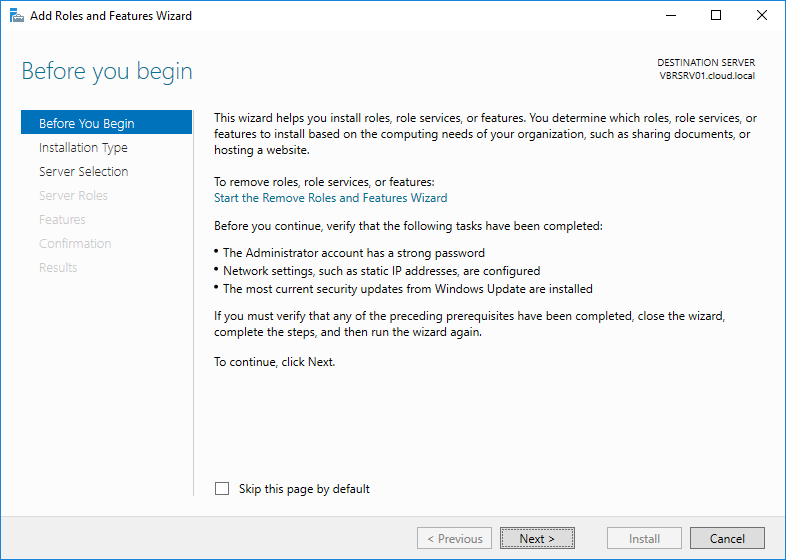
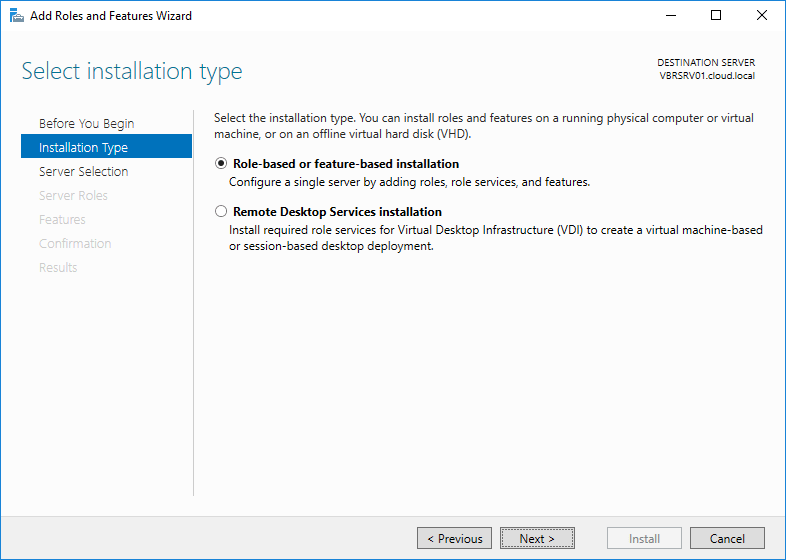
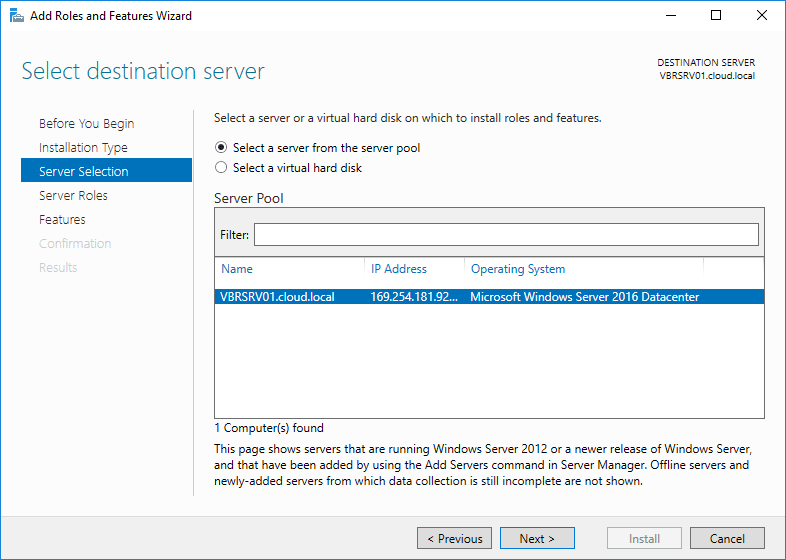
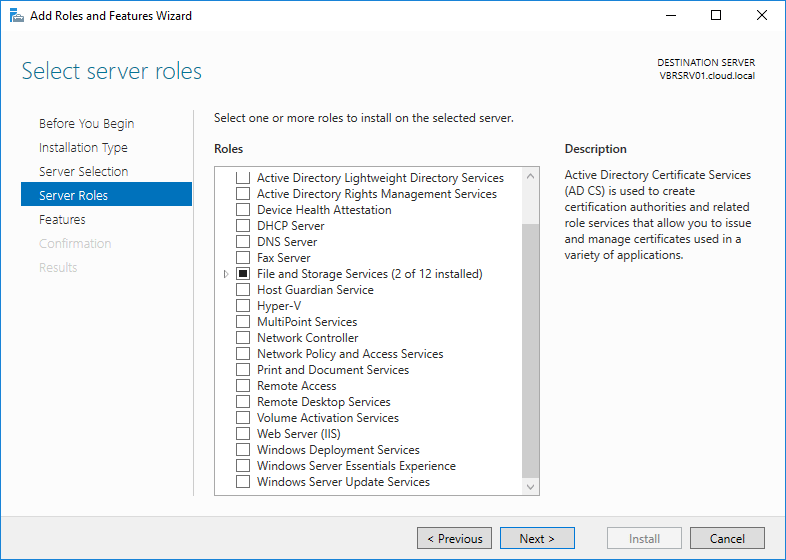
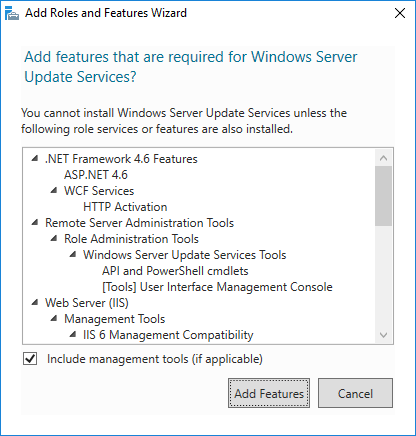
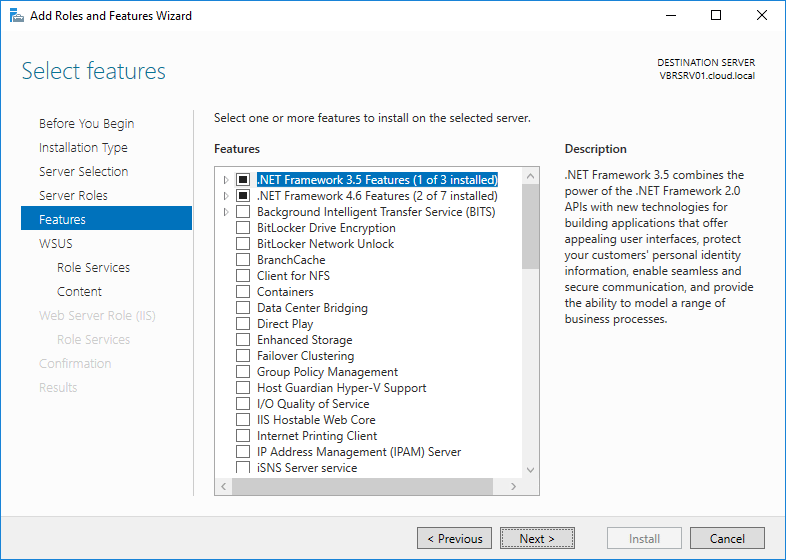
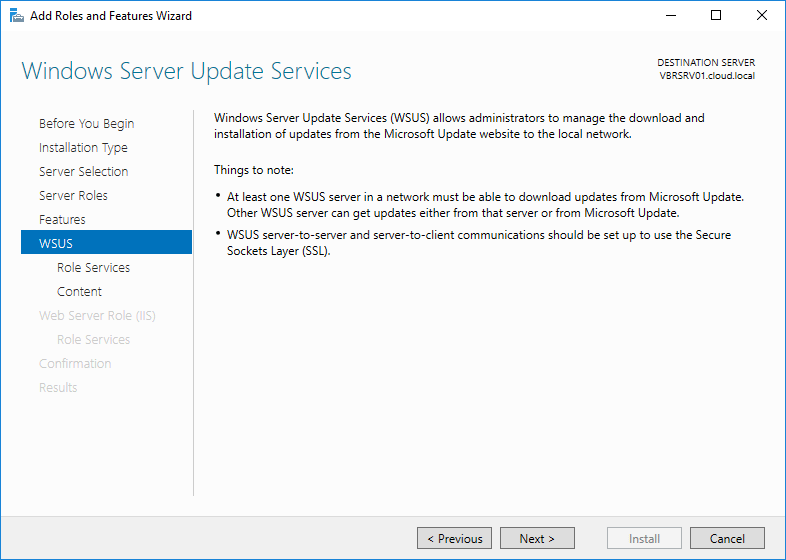
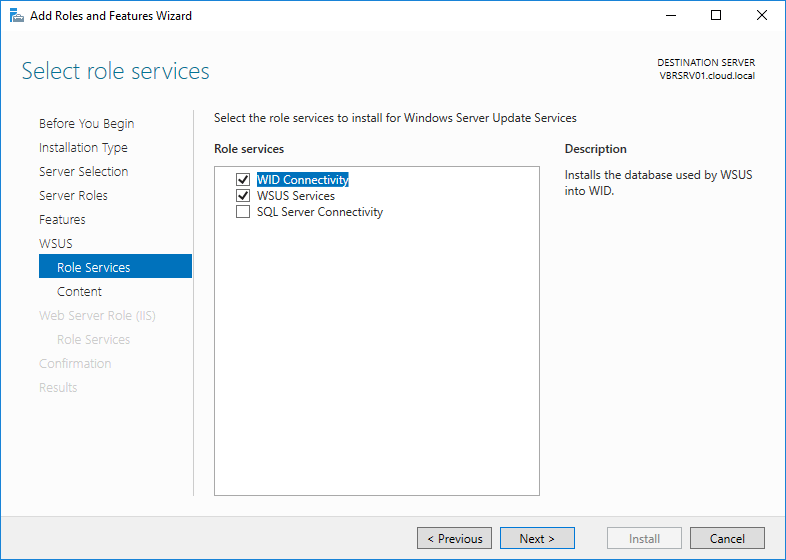
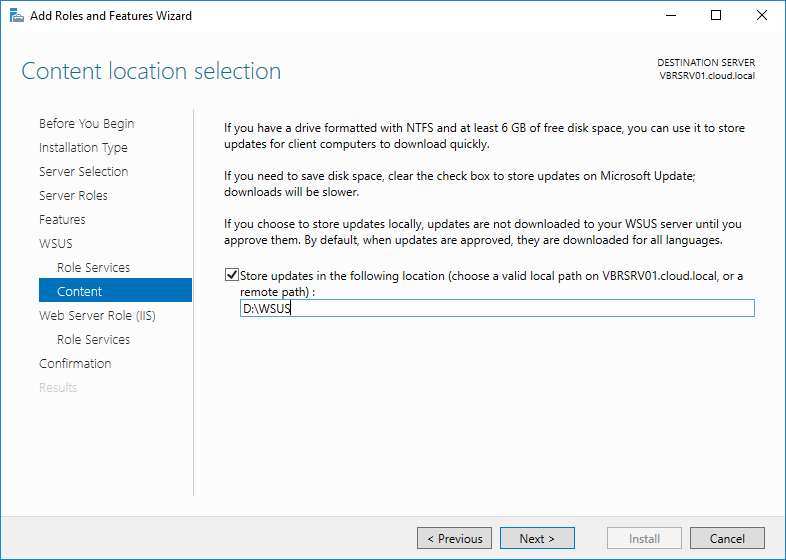
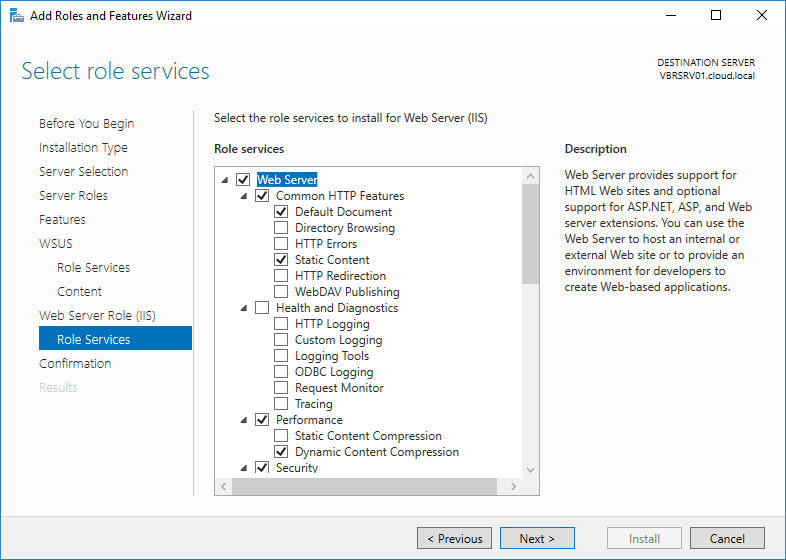
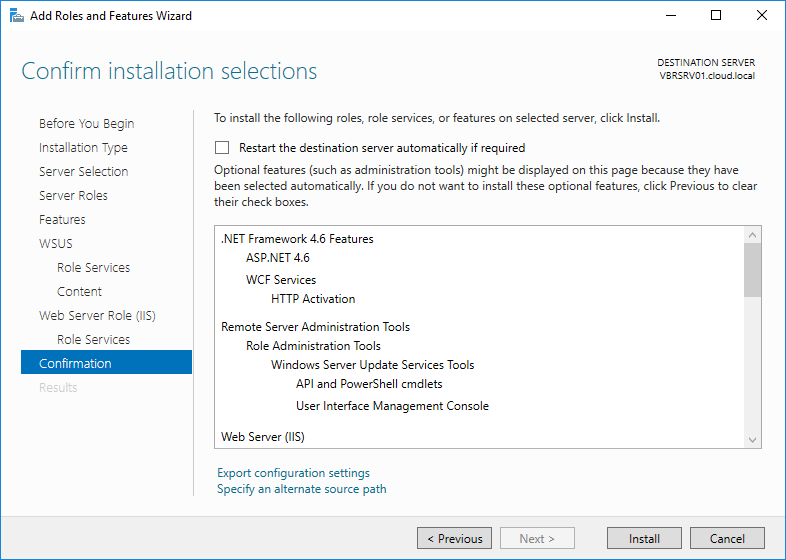
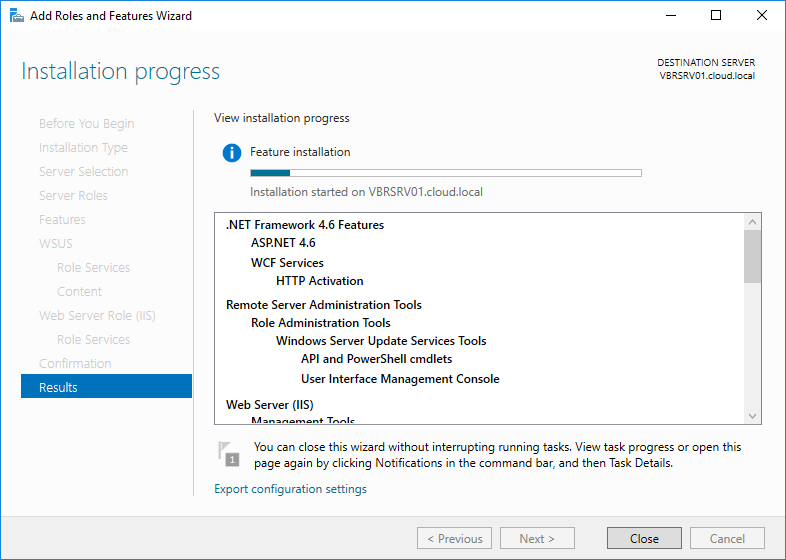
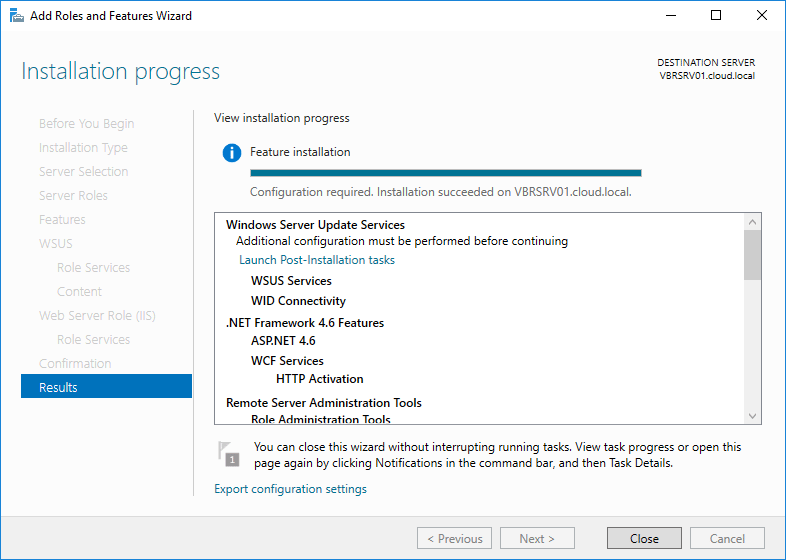
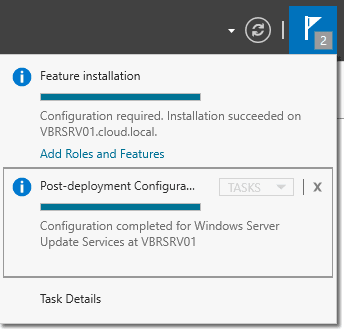
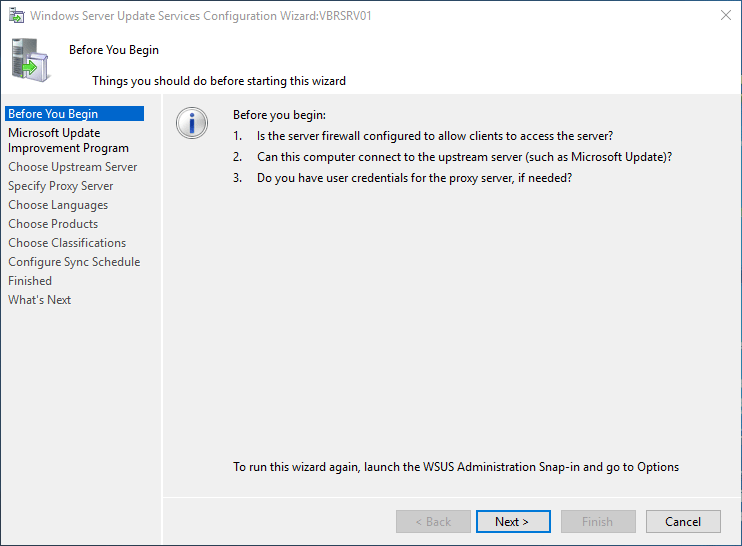
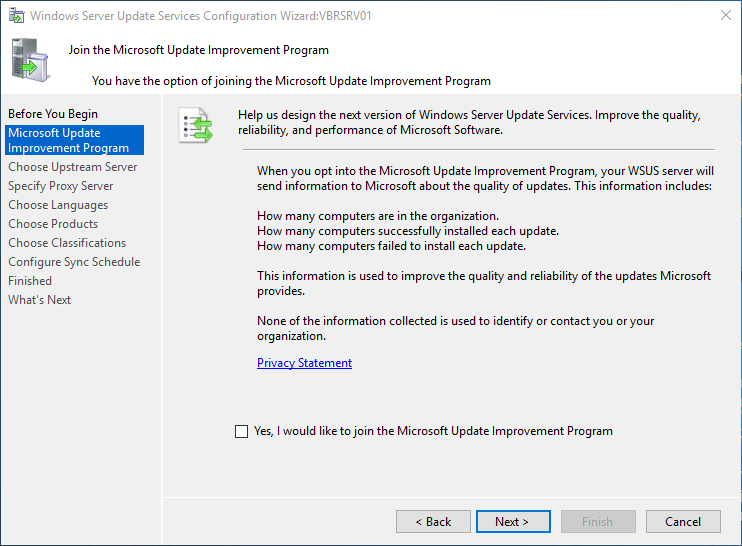
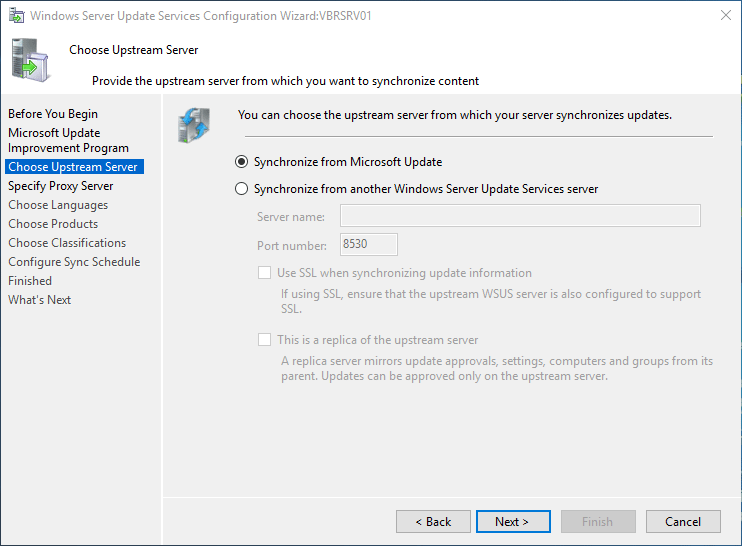
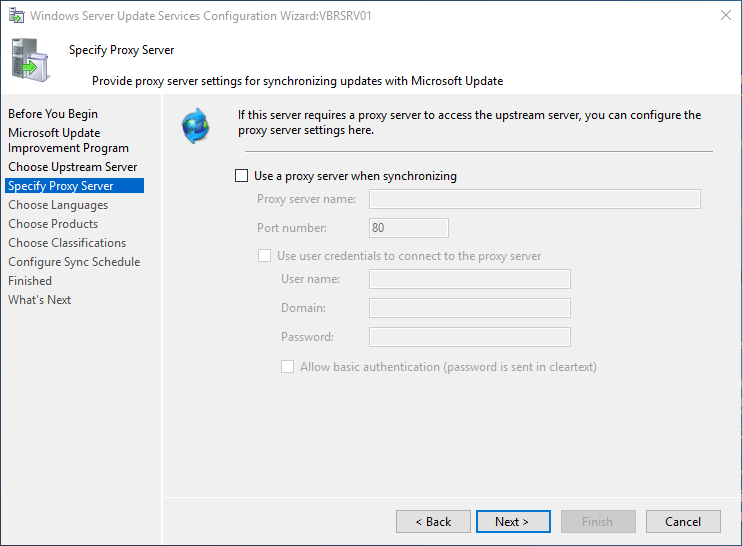
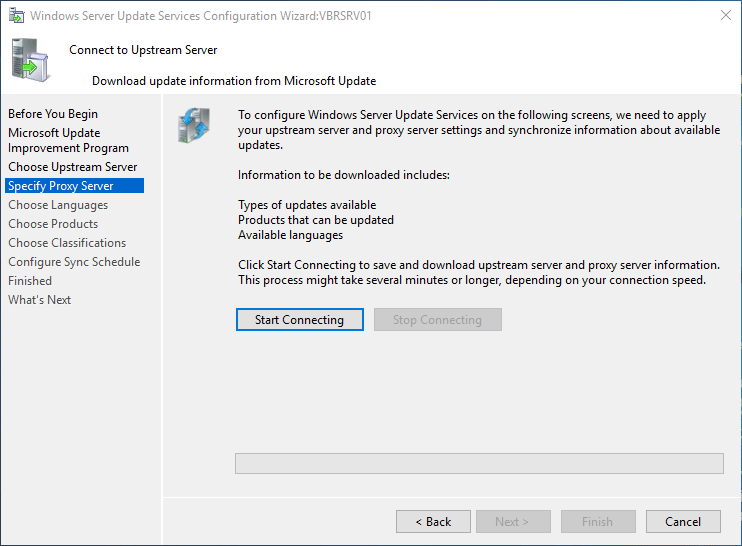
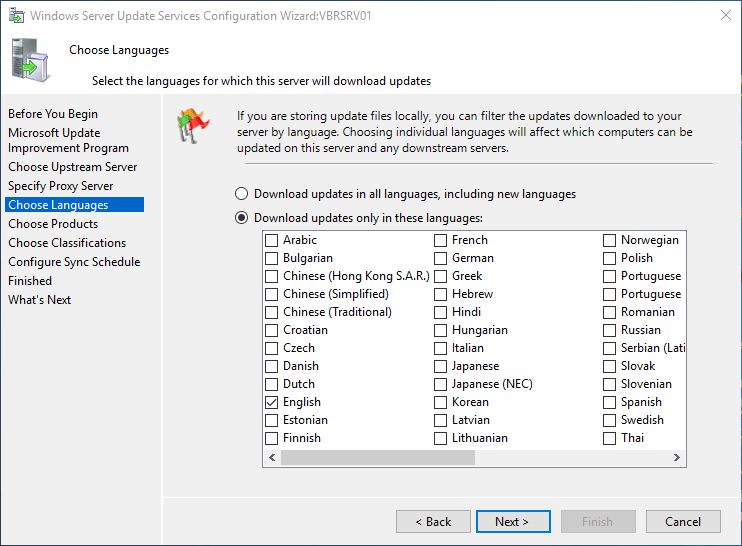
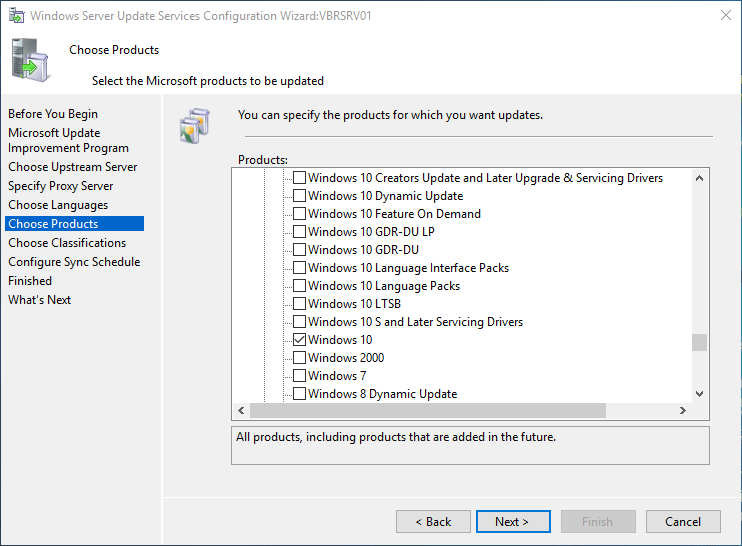
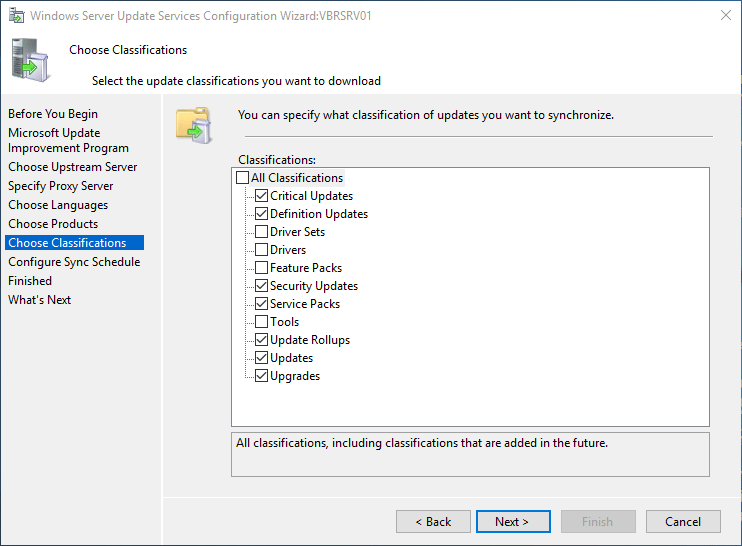
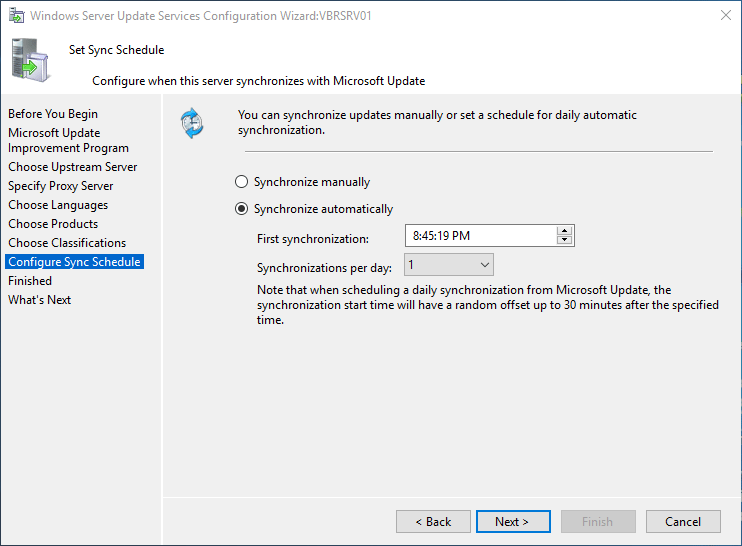
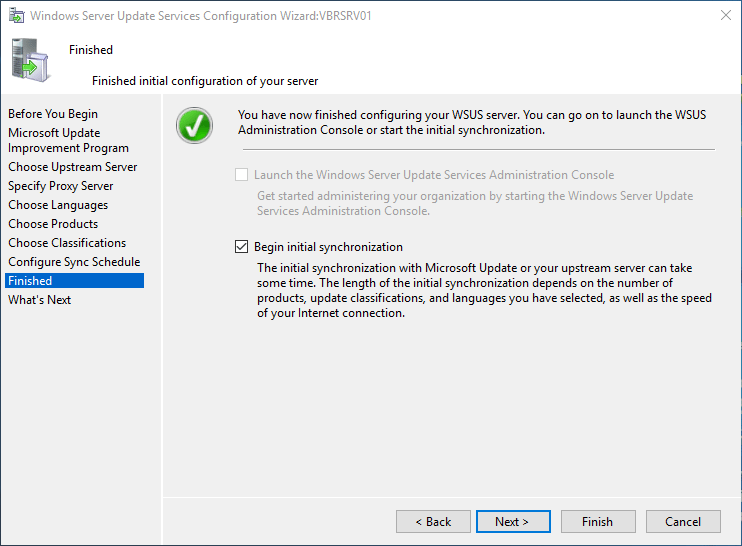
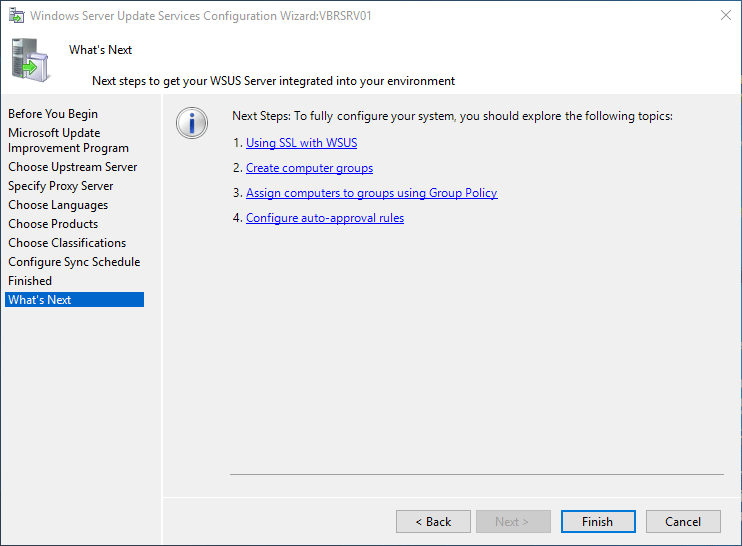
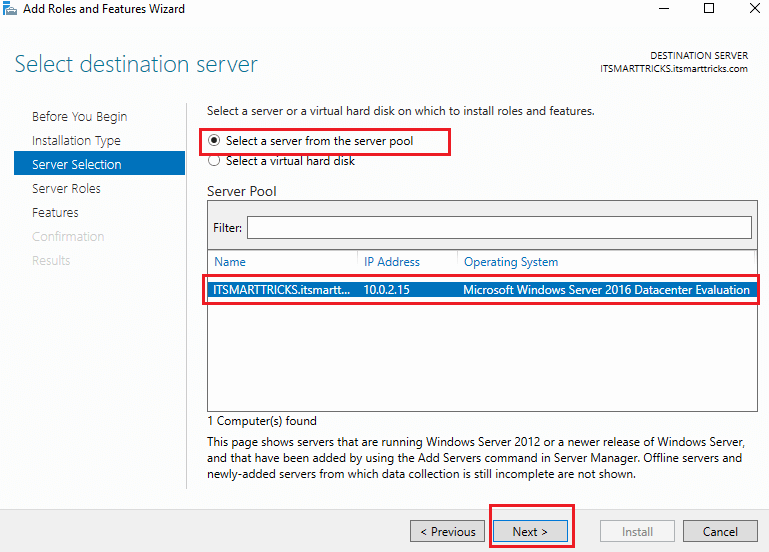
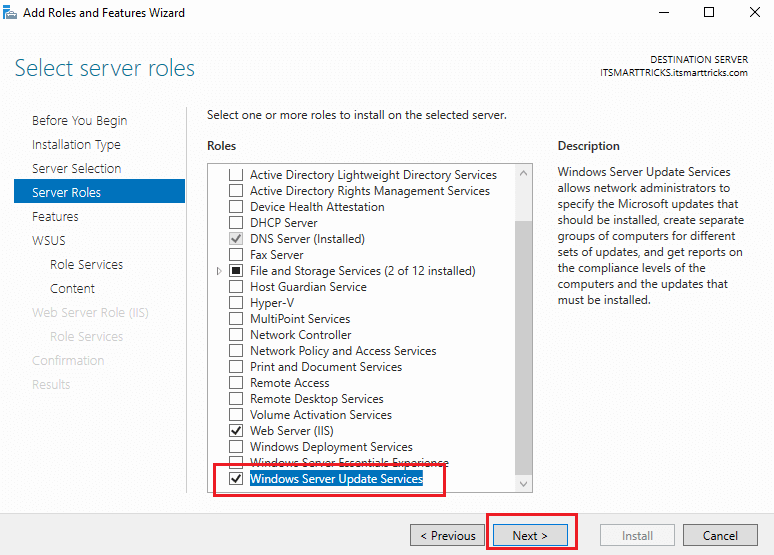
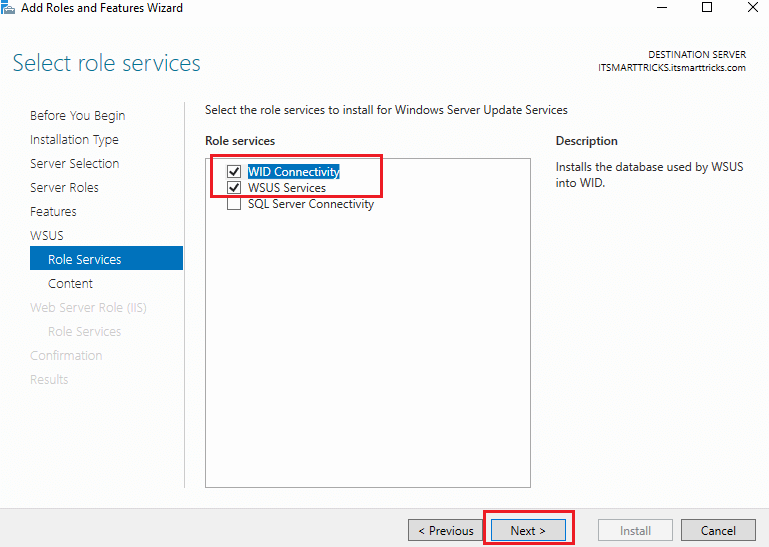
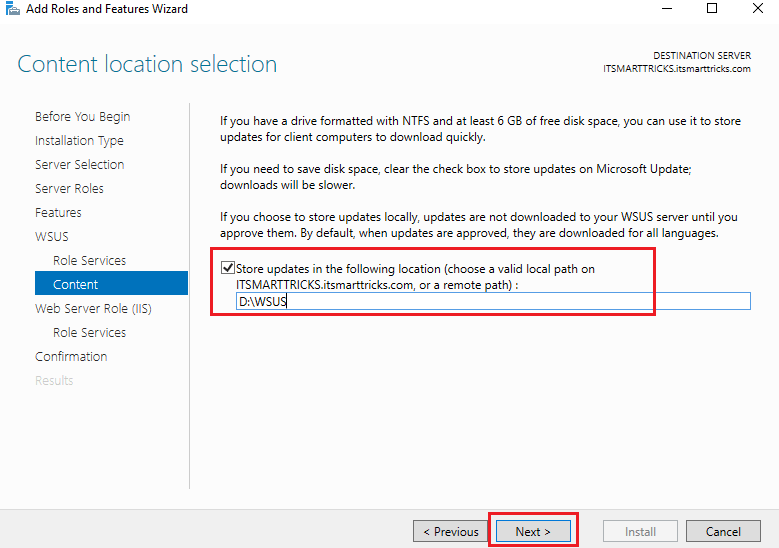
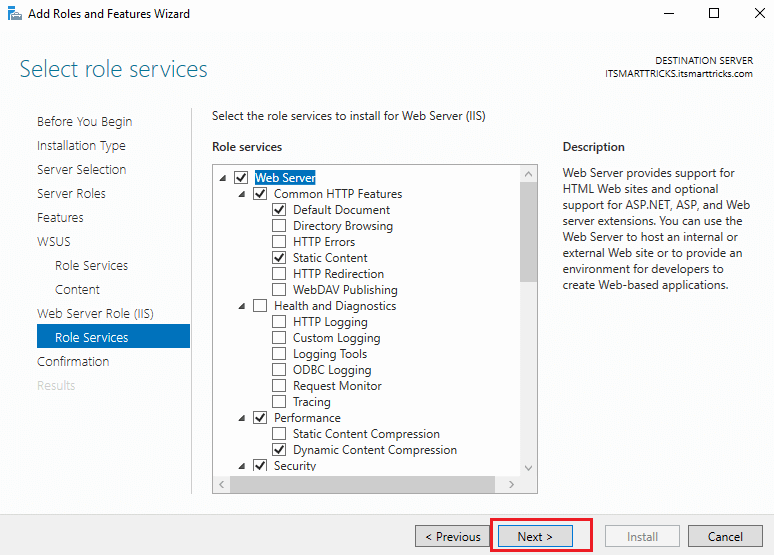
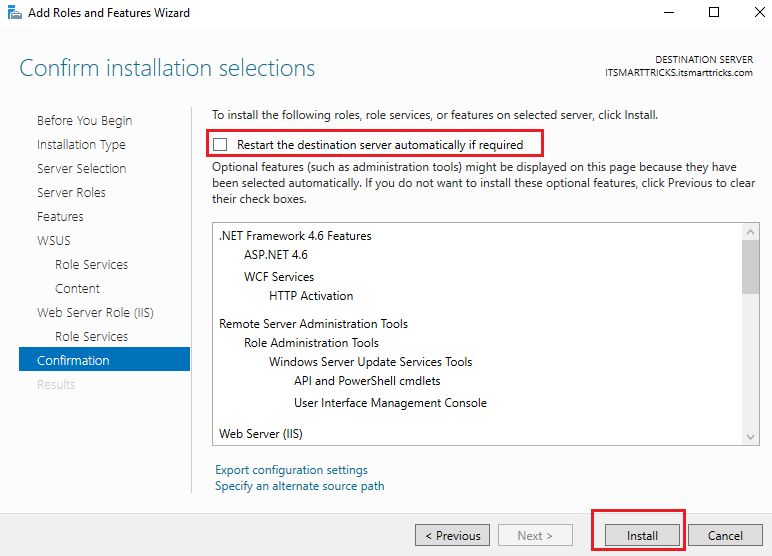
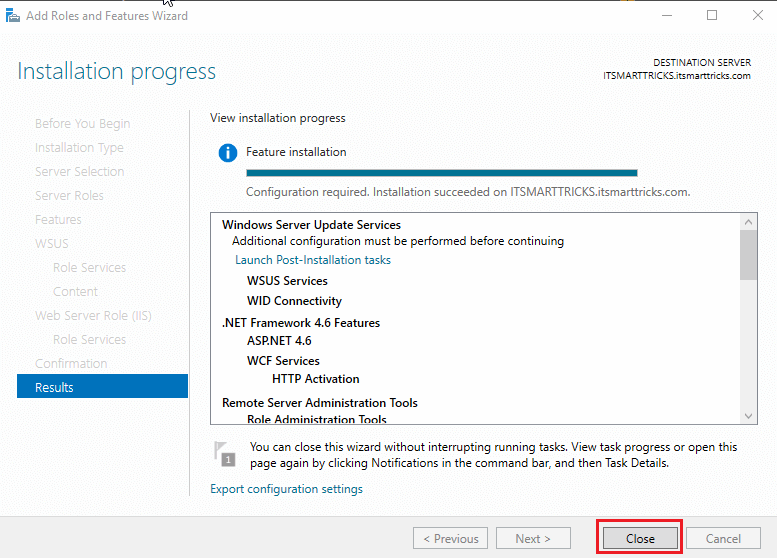
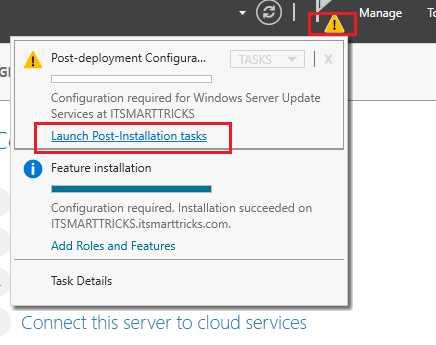
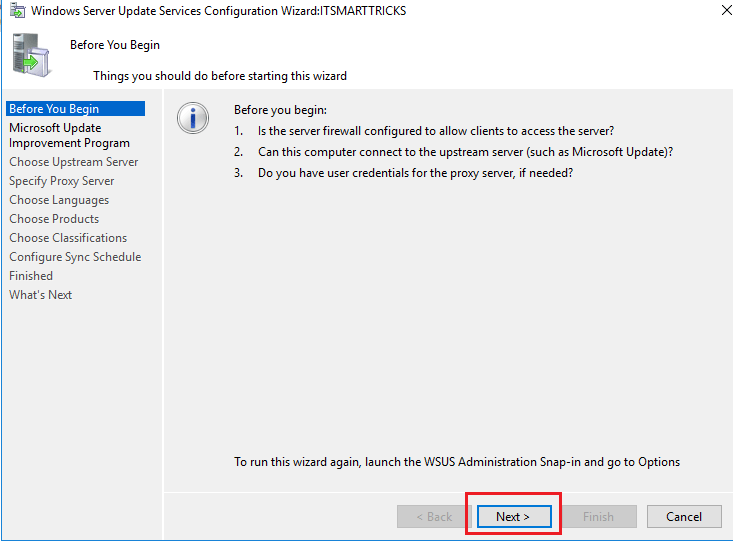
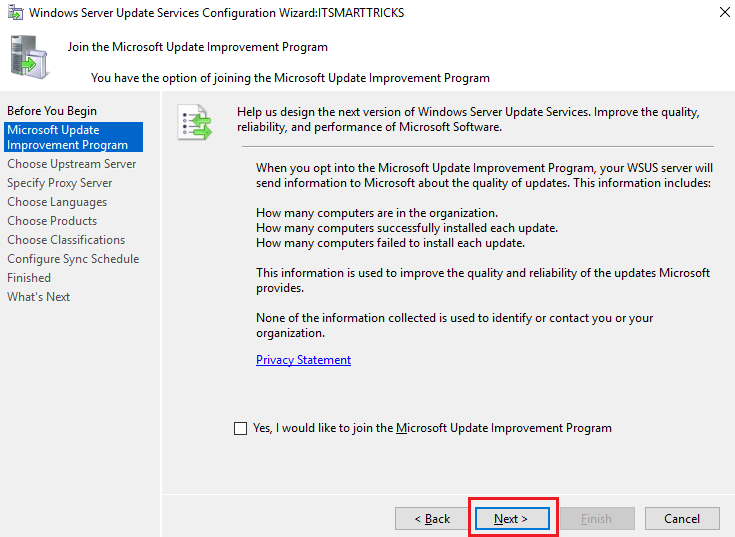
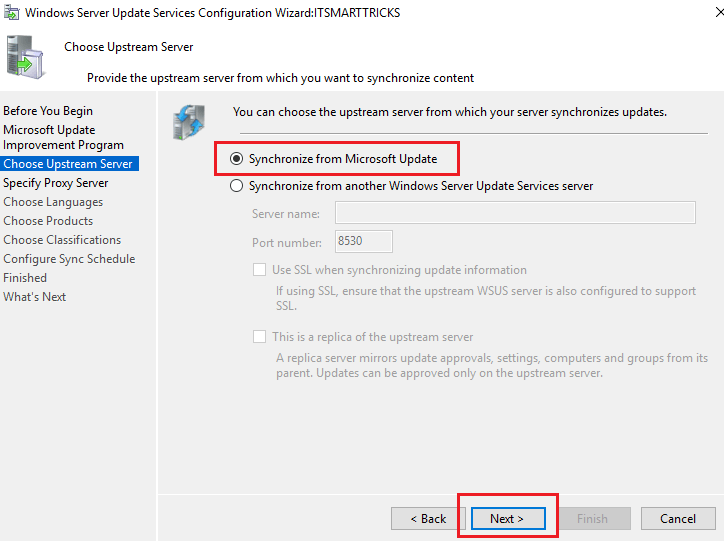
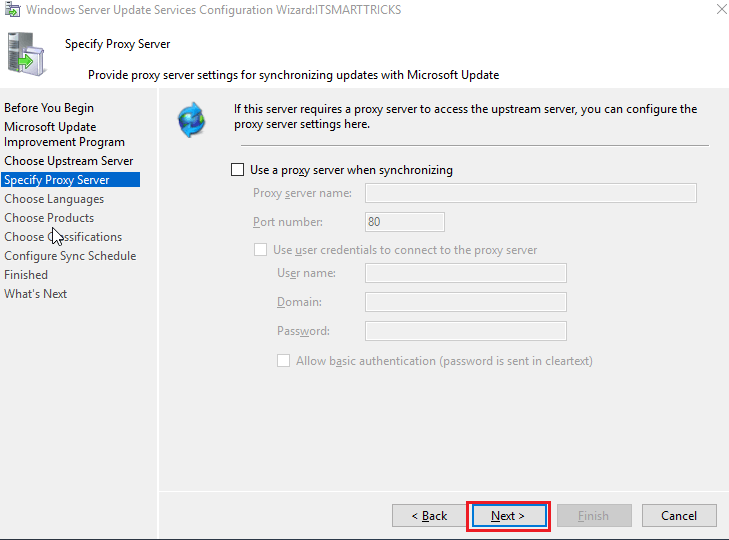
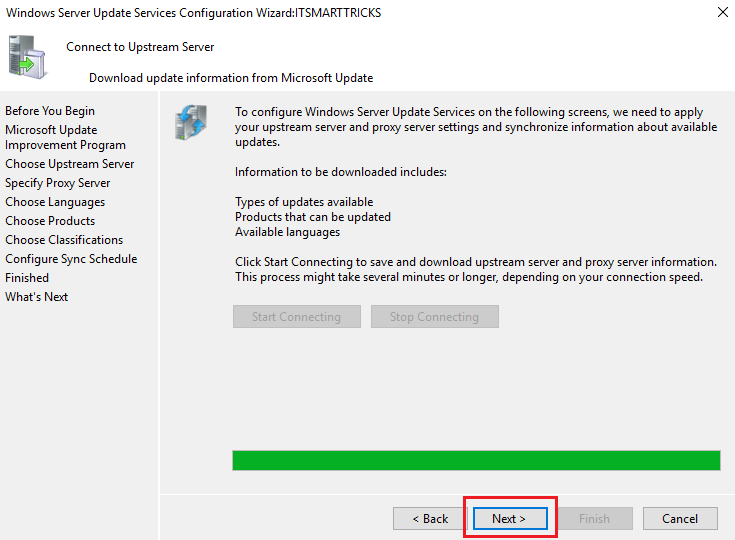
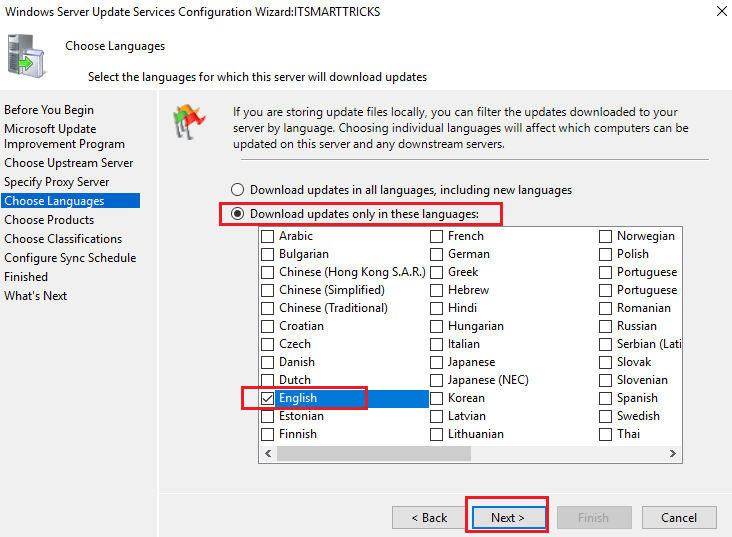
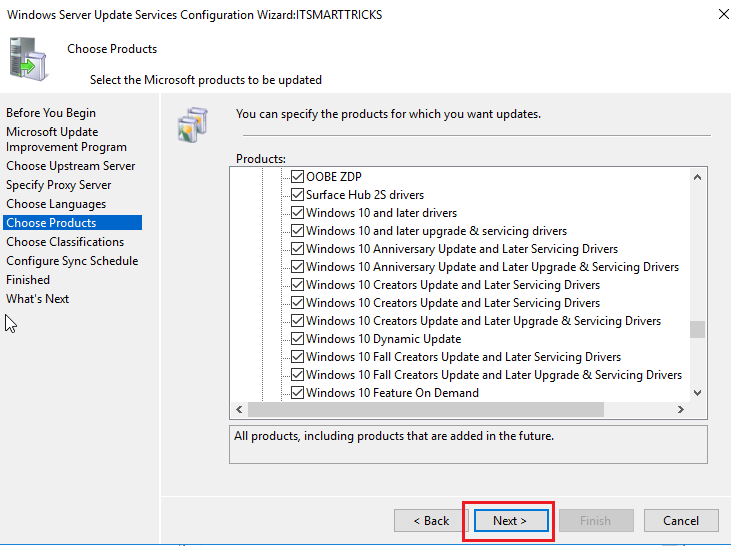
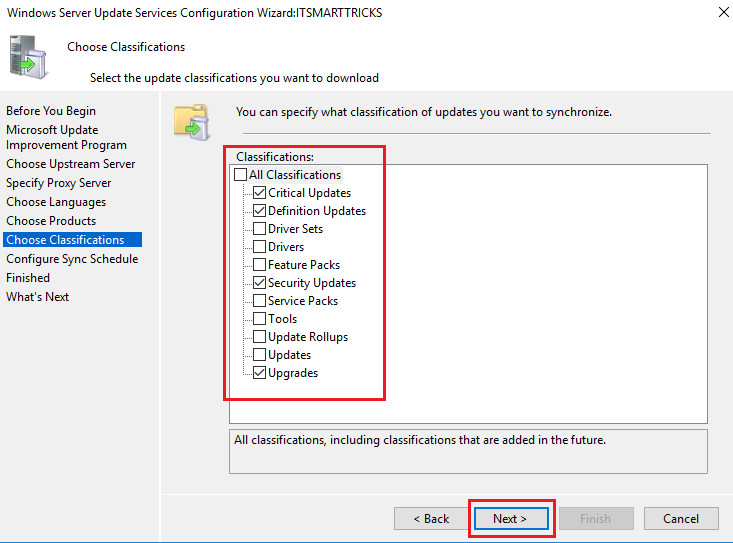
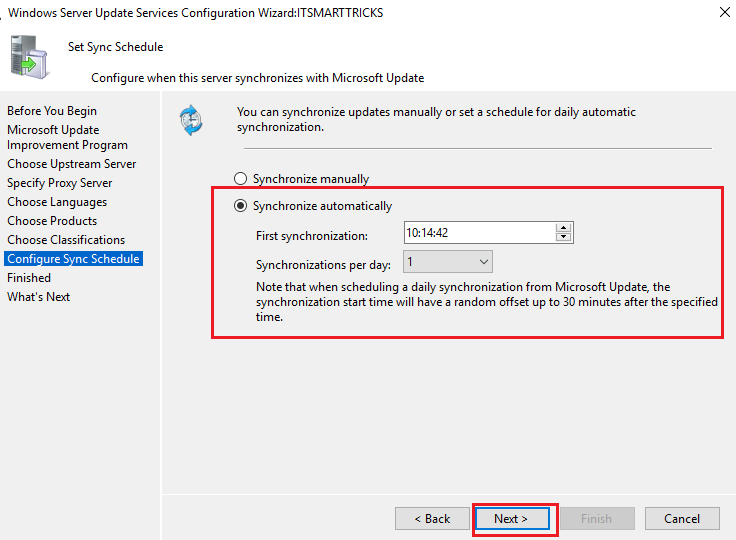
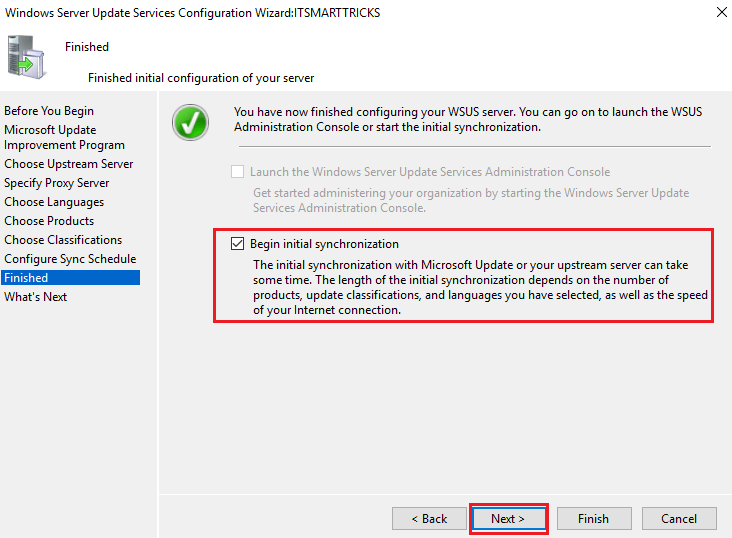
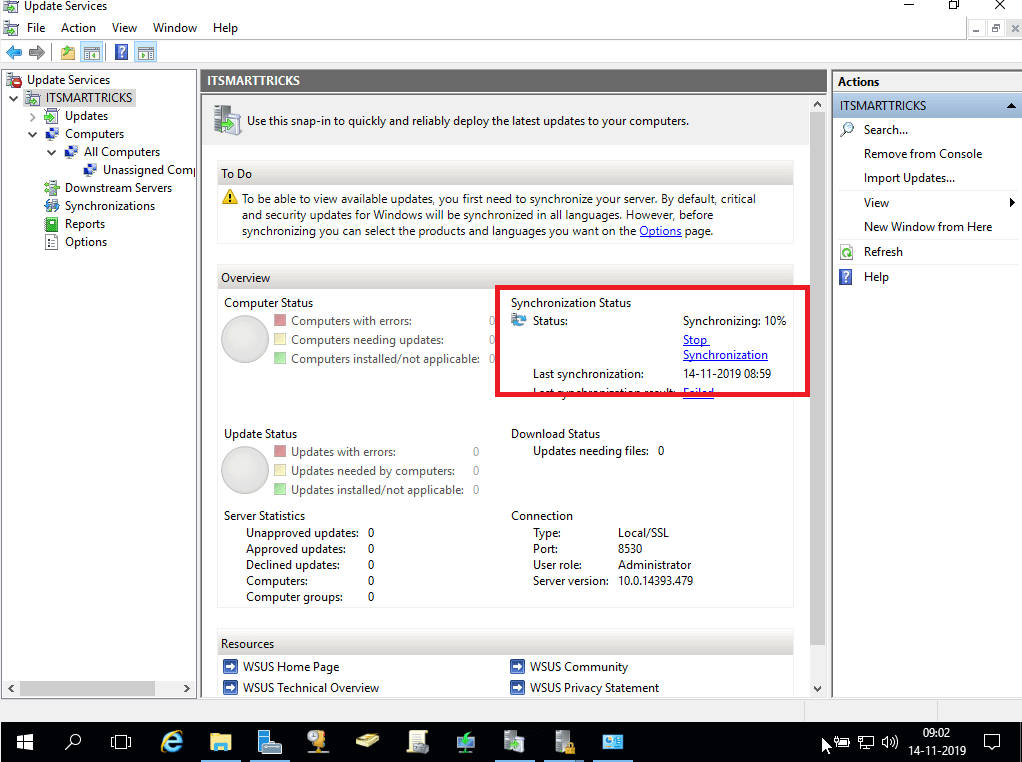
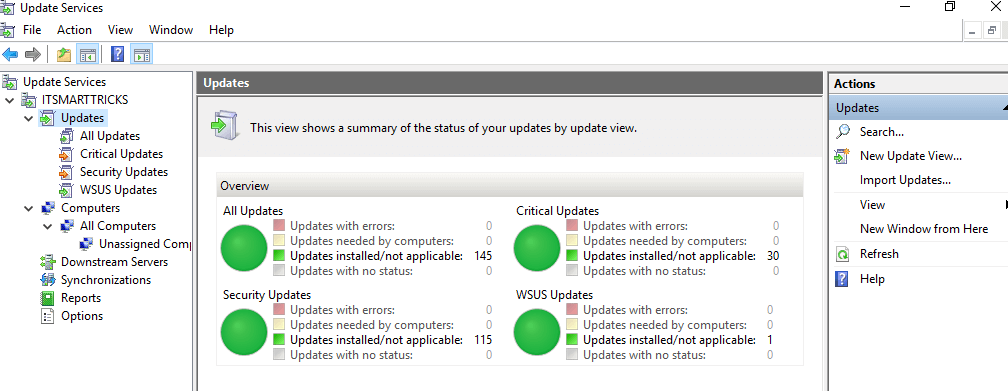
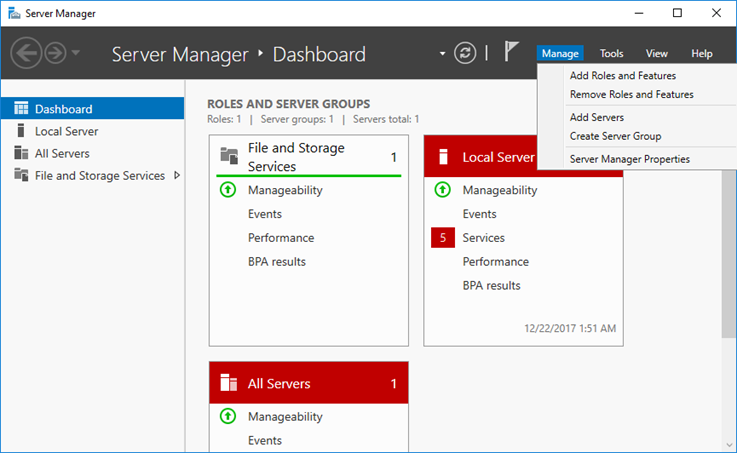

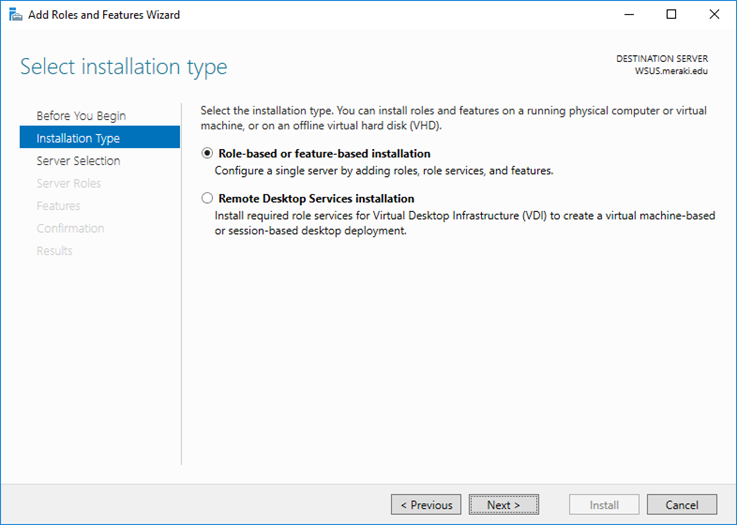

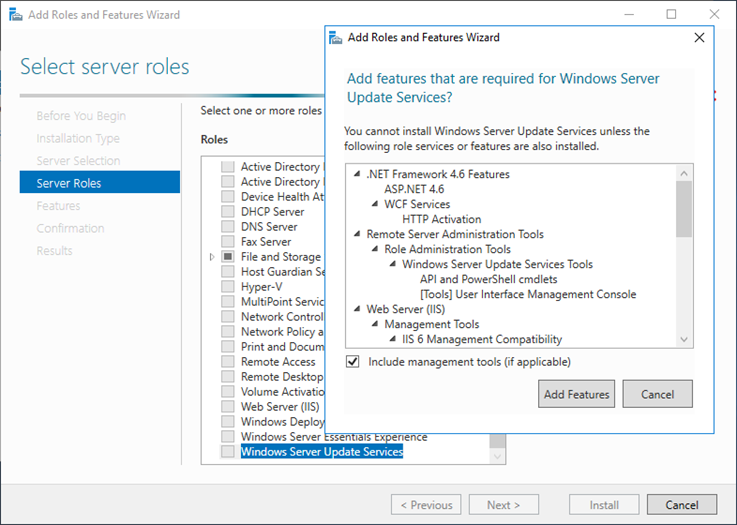
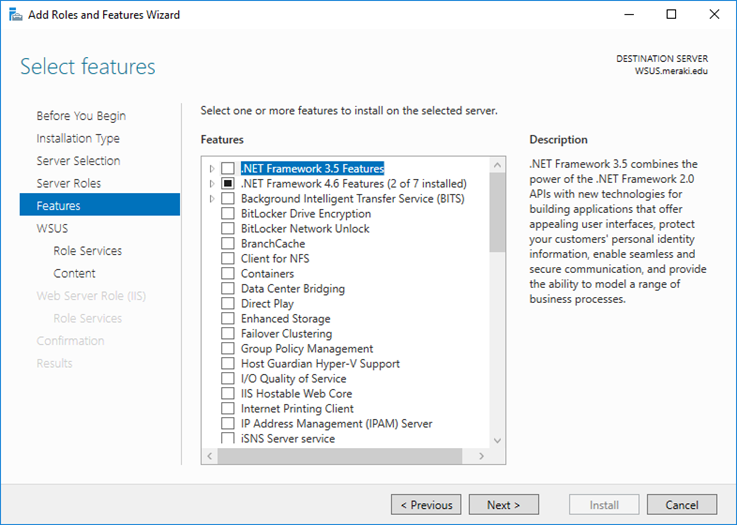

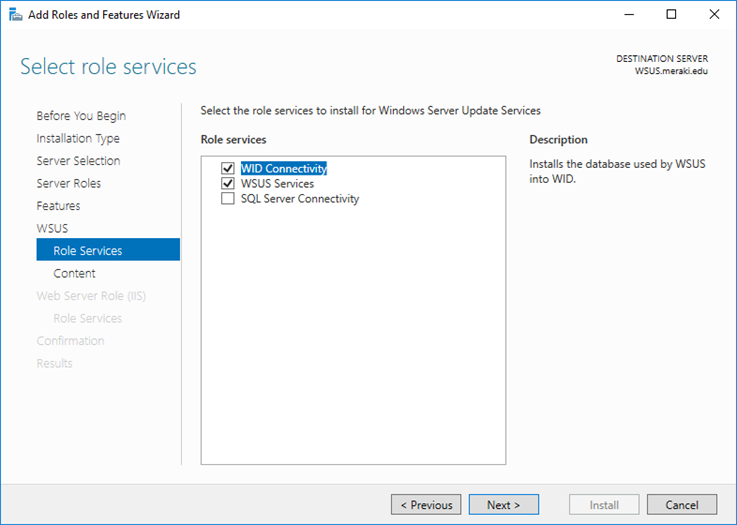



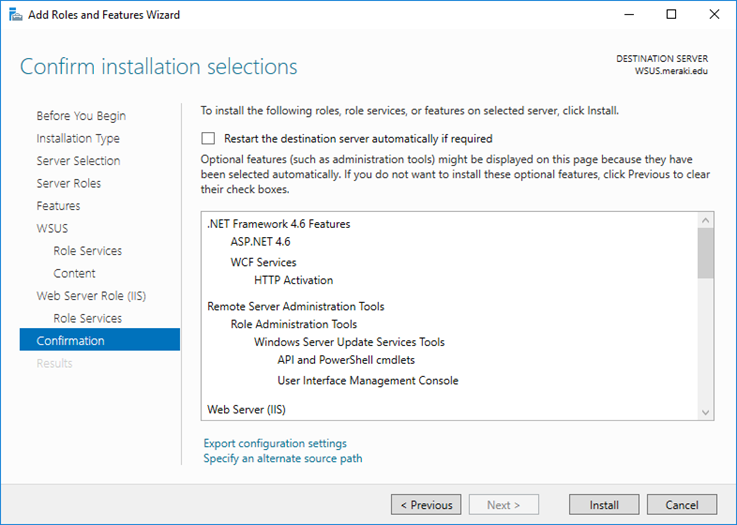
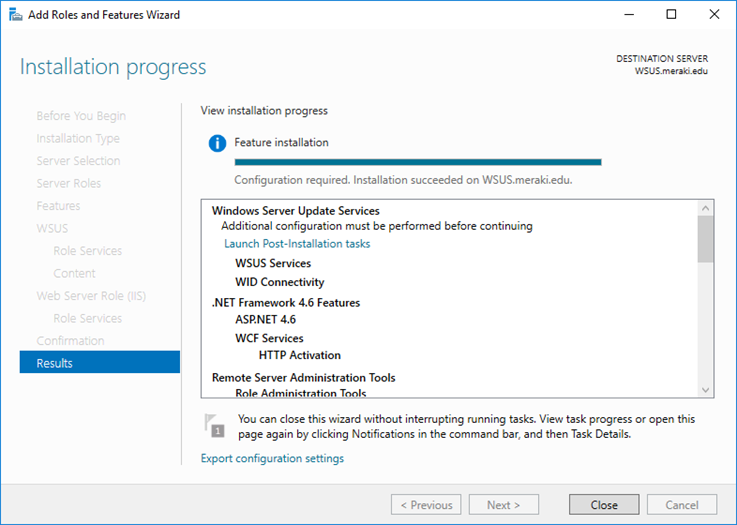
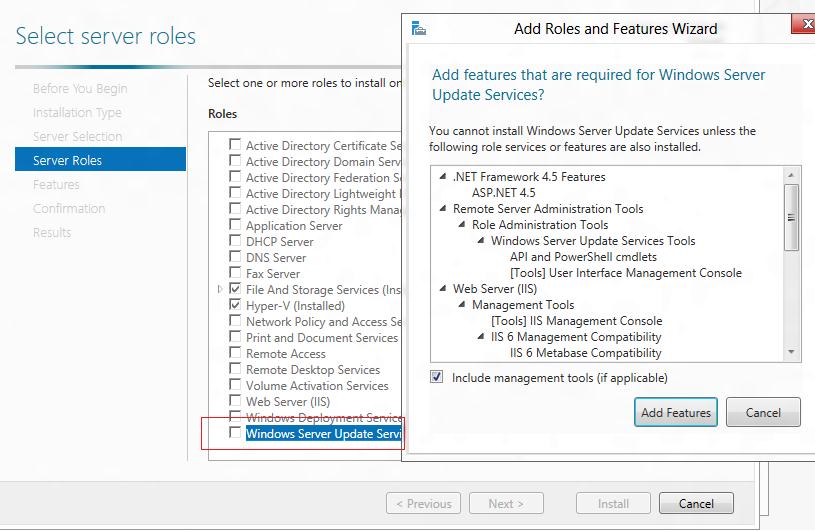
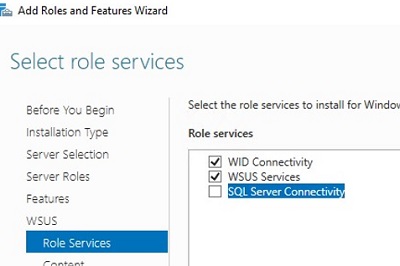
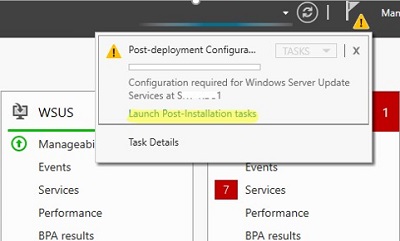
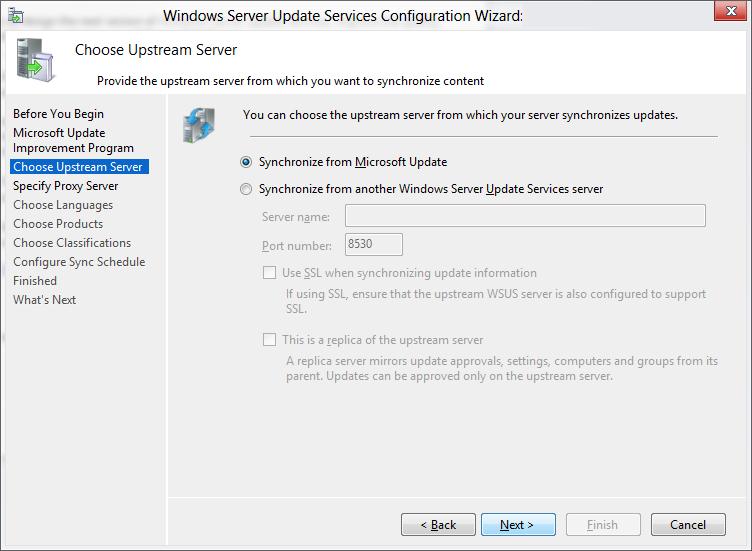
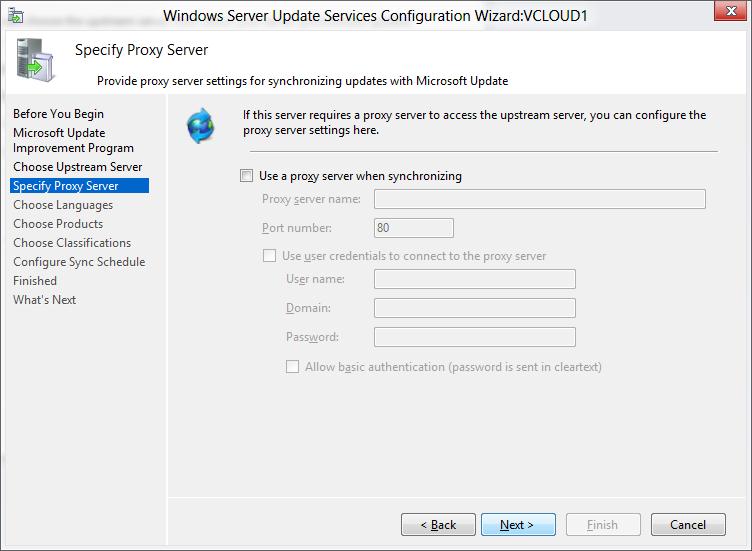
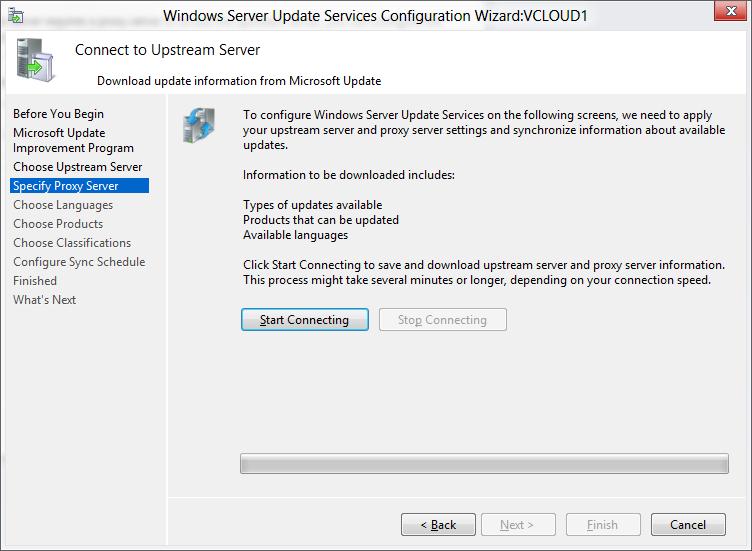
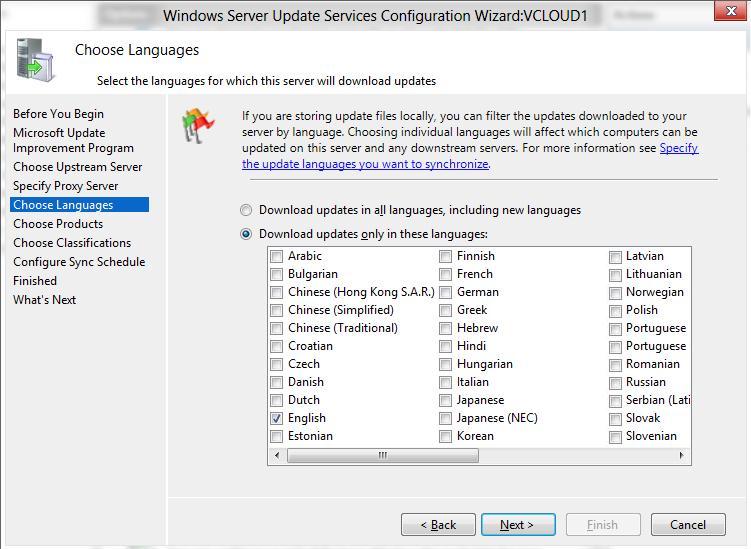
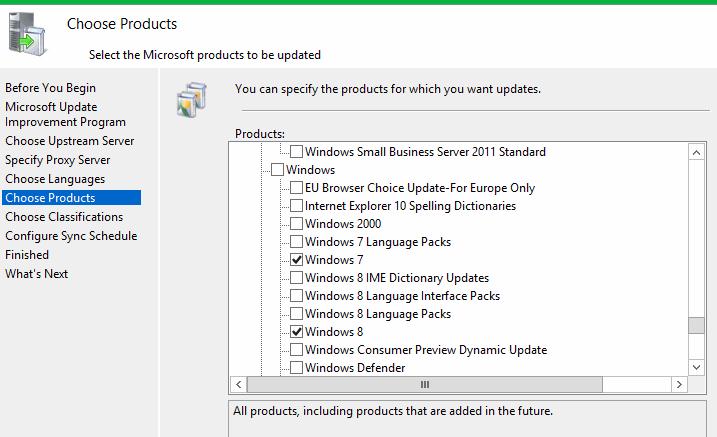
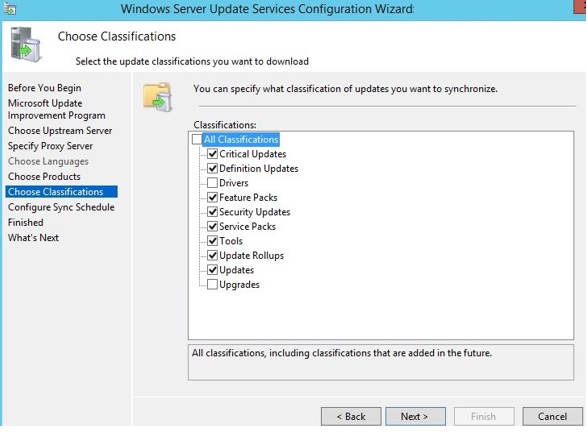
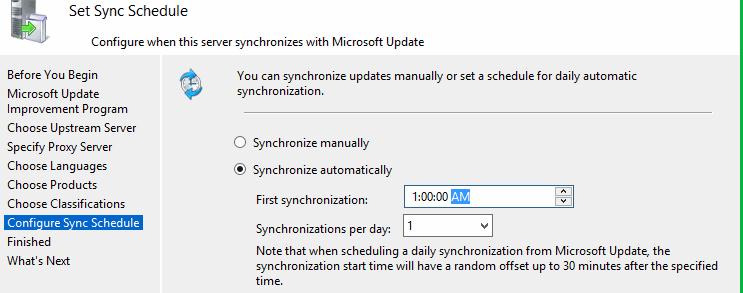
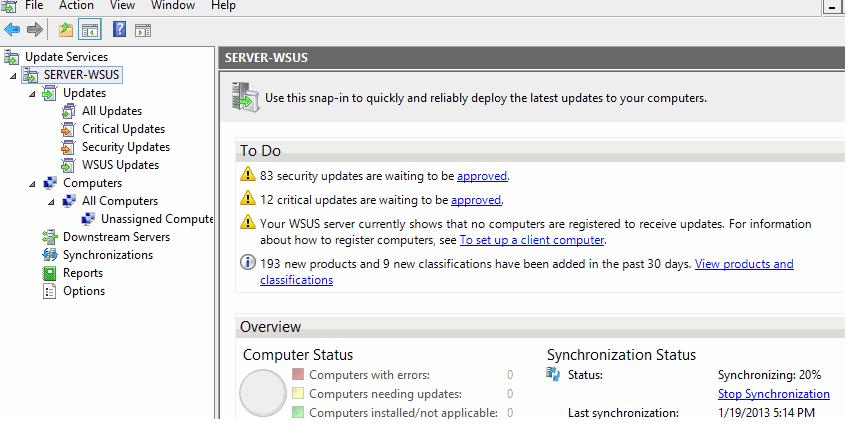
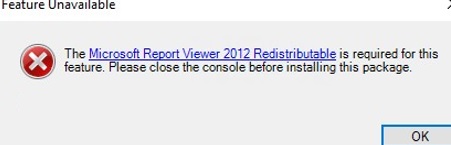
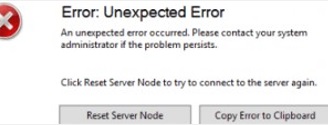 To resolve this issue, you need to add more RAM to your WSUS host and optimize your IIS pool settings as recommended in the article. Use these PowerShell commands:
To resolve this issue, you need to add more RAM to your WSUS host and optimize your IIS pool settings as recommended in the article. Use these PowerShell commands: