Bloatware is so common on PCs these days that each computer review on our sister site Laptop has a section dedicated to the issue. To get rid of unwanted, preinstalled programs, many tech-savvy users do a «clean» Windows re-installation as soon as they buy a new machine.
However, that may not be possible on some recent Lenovo laptops and desktops. Forum discussions on Ars Technica and Y Combinator allege that Lenovo-provided bloatware installs itself even with a clean installation, leading commenters to suspect that the Chinese computer maker has installed some sort of «bootkit» that survives a full wipe-and-reinstall.
MORE: Best and Worst Laptop Brands
Lenovo representatives did not admit or deny the presence of such software when questioned by Tom’s Guide. Instead, they directed us to a Lenovo press statement (opens in new tab) issued July 31 that advised updating the BIOS firmware on certain Lenovo machines to resolve a security vulnerability created by a BIOS utility called Lenovo Service Engine (LSE) — which does indeed sound like what the forum discussions have been about.
This could be another public-relations black mark for the company, which in February was discovered to be pre-installing a browser hijacker called Superfish that would break Web encryption and insert supplemental ads in Web browsers on certain machines.
According to a Lenovo security advisory, (opens in new tab) also issued July 31, Lenovo Service Engine (LSE) boots before the operating system and installs software called OneKey Optimizer (opens in new tab), which, according to Lenovo documentations, «can enhance your PC’s performance by updating firmware, drivers and pre-installed apps.»
Lenovo now recommends that users patch the BIOS to disable LSE, and the company says it stopped preinstalling LSE in May. However, there are sure to be many computers in supply chains, not to mention already sold, that have the software.
Whenever Windows 7 or 8 is installed on a computer Lenovo pre-loaded with LSE, the machine’s BIOS performs a check to see if OneKey Optimizer is present, and if the check fails, that software is re-installed.
Lenovo stated the LSE security flaw was brought to its attention by independent security researcher Roel Schouwenberg, formerly of Kaspersky Lab, who described «possible ways [LSE] could be exploited in the Lenovo Notebook implementation by an attacker, including a buffer overflow attack and an attempted connection to a Lenovo test server.»
Lenovo has released a LSE Windows Disabler Tool, and instructions for using it are below.
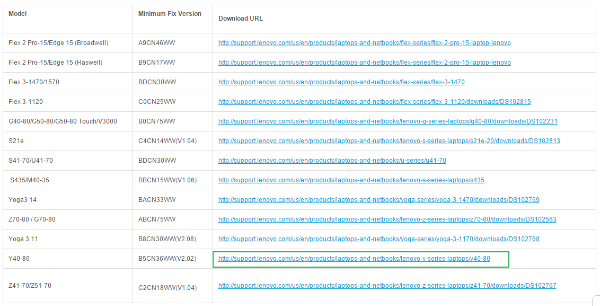
Here’s a list of Lenovo computers sold in North America that have LSE installed:
- Flex 2 Pro-15/Edge 15 (Broadwell)
- Flex 2 Pro-15/Edge 15 (Haswell)
- Flex 3-1470/1570
- Flex 3-1120
- G40-80/G50-80/G50-80 Touch/V3000
- S21e
- S41-70/U41-70
- S435/M40-35
- Yoga3 14
- Z70-80 / G70-80
- Yoga 3 11
- Y40-80
- Z41-70/Z51-70
How to Remove Lenovo Service Engine
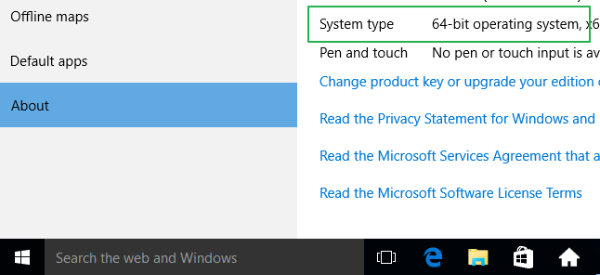
1. You’ll need to know if your computer is a 32-bit or 64-bit version of Windows, so click on the Start button.
2. Select Settings.
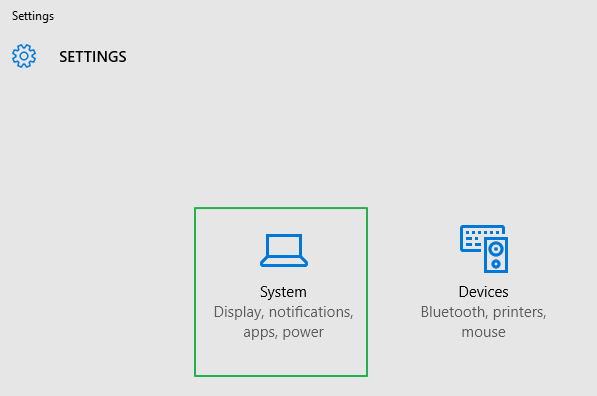
3. Click System.
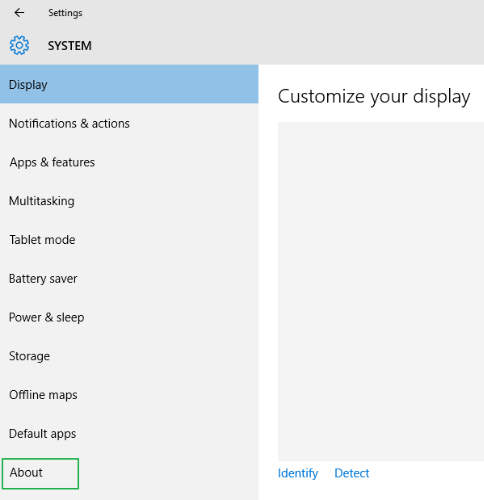
4. Select About from the left rail.
5. Note what the screen says for System Type.
6. Browse to the Lenovo Security Advisory (opens in new tab), where you’ll select the link for your specific Lenovo machine.
7. Click the «Date» button to bring the most recent update to the top of the page.
8. Scroll down until you find the item for «Lenovo LSE Windows Disabler Tool» and click the download icon next to the version that matches your version of Windows.
9. Open the program once it downloads. It will remove the LSE software.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
Henry is a managing editor at Tom’s Guide covering streaming media, laptops and all things Apple, reviewing devices and services for the past seven years. Prior to joining Tom’s Guide, he reviewed software and hardware for TechRadar Pro, and interviewed artists for Patek Philippe International Magazine. He’s also covered the wild world of professional wrestling for Cageside Seats, interviewing athletes and other industry veterans.
Bloatware is so common on PCs these days that each computer review on our sister site Laptop has a section dedicated to the issue. To get rid of unwanted, preinstalled programs, many tech-savvy users do a «clean» Windows re-installation as soon as they buy a new machine.
However, that may not be possible on some recent Lenovo laptops and desktops. Forum discussions on Ars Technica and Y Combinator allege that Lenovo-provided bloatware installs itself even with a clean installation, leading commenters to suspect that the Chinese computer maker has installed some sort of «bootkit» that survives a full wipe-and-reinstall.
MORE: Best and Worst Laptop Brands
Lenovo representatives did not admit or deny the presence of such software when questioned by Tom’s Guide. Instead, they directed us to a Lenovo press statement (opens in new tab) issued July 31 that advised updating the BIOS firmware on certain Lenovo machines to resolve a security vulnerability created by a BIOS utility called Lenovo Service Engine (LSE) — which does indeed sound like what the forum discussions have been about.
This could be another public-relations black mark for the company, which in February was discovered to be pre-installing a browser hijacker called Superfish that would break Web encryption and insert supplemental ads in Web browsers on certain machines.
According to a Lenovo security advisory, (opens in new tab) also issued July 31, Lenovo Service Engine (LSE) boots before the operating system and installs software called OneKey Optimizer (opens in new tab), which, according to Lenovo documentations, «can enhance your PC’s performance by updating firmware, drivers and pre-installed apps.»
Lenovo now recommends that users patch the BIOS to disable LSE, and the company says it stopped preinstalling LSE in May. However, there are sure to be many computers in supply chains, not to mention already sold, that have the software.
Whenever Windows 7 or 8 is installed on a computer Lenovo pre-loaded with LSE, the machine’s BIOS performs a check to see if OneKey Optimizer is present, and if the check fails, that software is re-installed.
Lenovo stated the LSE security flaw was brought to its attention by independent security researcher Roel Schouwenberg, formerly of Kaspersky Lab, who described «possible ways [LSE] could be exploited in the Lenovo Notebook implementation by an attacker, including a buffer overflow attack and an attempted connection to a Lenovo test server.»
Lenovo has released a LSE Windows Disabler Tool, and instructions for using it are below.
Here’s a list of Lenovo computers sold in North America that have LSE installed:
- Flex 2 Pro-15/Edge 15 (Broadwell)
- Flex 2 Pro-15/Edge 15 (Haswell)
- Flex 3-1470/1570
- Flex 3-1120
- G40-80/G50-80/G50-80 Touch/V3000
- S21e
- S41-70/U41-70
- S435/M40-35
- Yoga3 14
- Z70-80 / G70-80
- Yoga 3 11
- Y40-80
- Z41-70/Z51-70
How to Remove Lenovo Service Engine
1. You’ll need to know if your computer is a 32-bit or 64-bit version of Windows, so click on the Start button.
2. Select Settings.
3. Click System.
4. Select About from the left rail.
5. Note what the screen says for System Type.
6. Browse to the Lenovo Security Advisory (opens in new tab), where you’ll select the link for your specific Lenovo machine.
7. Click the «Date» button to bring the most recent update to the top of the page.
8. Scroll down until you find the item for «Lenovo LSE Windows Disabler Tool» and click the download icon next to the version that matches your version of Windows.
9. Open the program once it downloads. It will remove the LSE software.
Get instant access to breaking news, the hottest reviews, great deals and helpful tips.
Henry is a managing editor at Tom’s Guide covering streaming media, laptops and all things Apple, reviewing devices and services for the past seven years. Prior to joining Tom’s Guide, he reviewed software and hardware for TechRadar Pro, and interviewed artists for Patek Philippe International Magazine. He’s also covered the wild world of professional wrestling for Cageside Seats, interviewing athletes and other industry veterans.
На этой странице вы можете бесплатно скачать Драйвер для Lenovo G70-80 LSE Windows Disabler Tool v.1.0.0.9
Категория:Notebooks
Производитель:Lenovo
Оборудование:Lenovo G70-80
Тип программы:Software
Название:LSE Windows Disabler Tool
Версия:1.0.0.9
Размер файла:144.79Kb
Рейтинг:5/5
Дата выхода:30 Jul 2015
Система:Windows 10, Windows 10 64-bit, Windows 8.1, Windows 8.1 64-bit, Windows 8, Windows 8 64-bit, Windows 7, Windows 7 64-bit
Status:Free
Загрузок:17
Описание:LSE Windows Disabler Tool driver for Lenovo G70-80
LSE Windows Disabler Tool — Laptops
Правовая информация:Все програмное обеспечение, размещённое на Driver.ru является бесплатным. Все названия и торговые марки принадлежат их владельцам.
Внимание:Некоторые программы получены из непроверенных источников. Мы не гарантируем их совместимость и работоспособность. Всегда проверяйте загруженные файлы с помощью антивирусных программ. Мы не несём никакой ответственности за возможные потери, возникшие в результате установки загруженных программ. Загрузка файла с Driver.ru обозначает вашу информированность об этом и согласие с данными условиями.
Похожие файлы:
Название:Intel VGA Driver
Система:Windows 10 64-bit
Название:Touchpad Driver (Elan, Synaptics)
Система:Windows 10 64-bit
Название:Nvidia VGA Driver
Версия:Nvidia_VGA_22.21.13.8264.A
Система:Windows 10 64-bit
Название:Intel Rapid Storage Technology Driver
Версия:14.5.2.1088_PV
Система:Windows 10 64-bit
Название:Bluetooth Driver (Intel, Atheros, Realtek)
Система:Windows 10 64-bit
Описание:Bluetooth Driver (Intel, Atheros, Realtek) for Lenovo G70-80
Bluetooth Driver (Intel, Atheros, Realtek) Versions: Intel3160_19.41.0.1, NFA335_10.0.1.7, NFA345_10.0.0.242, RTL8723_1.3.887.3
Скачать Lenovo G70-80 Bluetooth Драйвер (Intel, Atheros, Realtek)
Название:Intel Chipset Driver
Система:Windows 10 64-bit
Название:Intel Management Engine Interface Driver
Система:Windows 10 64-bit
Название:Audio Driver
Версия:8.66.27.55
Система:Windows 10 64-bit
Название:WLAN Driver (Intel, Atheros, Realtek)
Версия:Intel3160&3165&8260_19.0.0.9_RTL
Система:Windows 10 64-bit
Название:Camera Driver (Sonix, Realtek)
Система:Windows 10 64-bit
Analysis Lenovo has sold laptops bundled with unremovable software that features a bonus exploitable security vulnerability.
If the crapware is deleted, or the hard drive wiped and Windows reinstalled from scratch, the laptop’s firmware will quietly and automatically reinstall Lenovo’s software on the next boot-up.
Built into the firmware on the laptops’ motherboard is a piece of code called the Lenovo Service Engine (LSE). If Windows is installed, the LSE is executed before the Microsoft operating system is launched.
The LSE makes sure C:Windowssystem32autochk.exe is Lenovo’s variant of the autochk.exe file; if Microsoft’s official version is there, it is moved out of the way and replaced. The executable is run during startup, and is supposed to check the computer’s file system to make sure it’s free of any corruption.
Lenovo’s variant of this system file ensures LenovoUpdate.exe and LenovoCheck.exe are present in the operating system’s system32 directory, and if not, it will copy the executables into that directory during boot up. So if you uninstall or delete these programs, the LSE in the firmware will bring them back during the next power-on or reboot.
LenovoCheck and LenovoUpdate are executed on startup with full administrator access. Automatically, and rather rudely, they connect to the internet to download and install drivers, a system «optimizer», and whatever else Lenovo wants on your computer. Lenovo’s software also phones home to the Chinese giant details of the running system.
To pull this off, the LSE exploits Microsoft’s Windows Platform Binary Table (WPBT) feature. This allows PC manufacturers and corporate IT to inject drivers, programs and other files into the Windows operating system from the motherboard firmware.
The WPBT is stored in the firmware, and tells Windows where in memory it can find an executable called a platform binary to run. Said executable will take care of the job of installing files before the operating system starts.
«During operating system initialization, Windows will read the WPBT to obtain the physical memory location of the platform binary,» Microsoft’s documentation states.
«The binary is required to be a native, user-mode application that is executed by the Windows Session Manager during operating system initialization. Windows will write the flat image to disk, and the Session Manager will launch the process.»
Crucially, the WPBT documentation stresses:
The primary purpose of WPBT is to allow critical software to persist even when the operating system has changed or been reinstalled in a “clean” configuration … Because this feature provides the ability to persistently execute system software in the context of Windows, it becomes critical that WPBT-based solutions are as secure as possible and do not expose Windows users to exploitable conditions.
Oh dear. Secure as possible? Not in this case: security researcher Roel Schouwenberg found and reported a buffer-overflow vulnerability in the LSE that can be exploited to gain administrator-level privileges.
After Lenovo learned of this bug in April, it dawned on the company that its LSE was falling foul of Microsoft’s security guidelines for using the powerful WPBT feature. Two months later, in June, it pulled the whole thing: the LSE software is no longer included in new laptops.
Lenovo has also pulled the LSE from new desktop machines. Incredibly, Lenovo was shipping desktop PCs that feature the LSE in their firmware. These models phone home system data, but do not install any extra software, and do not suffer from the aforementioned privilege-escalation vulnerability. The PC maker’s laptops definitely do, however.
Owners of LSE-afflicted computers urged to update their firmware
A tool quietly released on July 31 will uninstall the engine if it is present in your machine: it is available here for notebooks, and available here for desktops.
On Tuesday this week, Lenovo published a full list of affected desktop and notebook models. Desktop machines built between October 23, 2014 and April 10, 2015, with Windows 8 preinstalled, have the LSE inside them.
Think-branded PCs did not include the LSE, we’re told.
«Lenovo Service Engine (LSE) is a utility in the BIOS that helps users download a program called OneKey Optimizer on certain Lenovo Notebook systems. The utility also sends non-personally identifiable system data to Lenovo servers,» the Chinese goliath explained. «Lenovo, Microsoft and an independent researcher have discovered possible ways this program could be exploited by an attacker, including a buffer overflow attack and an attempted connection to a Lenovo test server.»
The PC biz continued:
LSE uses the Microsoft Windows Platform Binary Table (WPBT) capability. Microsoft has recently released updated security guidelines on how to best implement this feature. Lenovo’s use of LSE was not consistent with these guidelines and Lenovo recommends customers disable this utility by running a disabler program that disables LSE and removes the LSE files from the system.
The LSE functionality has been removed from newly manufactured systems.
Without this climbdown, it would have been virtually impossible for users to remove the rootkit-like engine from the firmware. El Reg hopes other manufacturers aren’t doing the same with the WPBT.
The fallout
Suffice to say, netizens who have discovered this creepy code on their machines are not happy.
«I had this happen to me a few weeks ago, on a new Lenovo laptop, doing a clean install with a new SSD, Windows 8 DVD and Wi-Fi turned off,» a Hacker News user called chuckup said on Tuesday, on noticing Lenovo’s bundleware suddenly appearing on his or her new computer.
«I couldn’t understand how a Lenovo service was installed and running. Delete the file and it reappears on reboot. I’ve never seen anything like this before. Something to think about before buying Lenovo.»
What is worrying is that all of this is pretty much what Microsoft intended. Its WPBT is engineered to allow manufacturers to painlessly inject drivers and programs into the operating system. It’s supposed to be used for things like anti-theft tools, so a system can be disabled via the internet if it’s stolen.
But it also turns rootkit development and installation into a painting-by-the-numbers exercise. Lenovo got caught because its engine had crap security. And it sounds as though Microsoft pressured Lenovo to kill it.
«Richard Stallman is sounding less and less crazy with discoveries like this,» noted another Hacker News poster, referring to the Free Software Foundation supremo who has warned for decades that we’re losing control of our computers.
«To think a manufacturer would essentially rootkit their own machines is testament to how bad things have become.»
This comes on the back of Lenovo’s Superfish scandal, in which the PC maker shipped laptops with adware on them that opened up people to man-in-the-middle eavesdropping. Miscreants could exploit the bundled crapware to snoop on victims’ encrypted connections to websites.
We’ve asked Microsoft to explain the thinking behind its WPBT feature. The Redmond giant was not available for immediate comment. ®