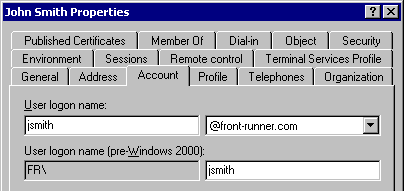
Часть 1
Системы на базе Windows NT завоевали прочные позиции на компьютерном рынке в качестве серверов малого и среднего класса. Однако Windows 2000 компания Microsoft позиционирует и как операционную систему для мощных серверов, предназначенных для решения задач масштаба предприятия.
В настоящее время термин «сервер для корпоративного сектора рынка» относится к системам с четырьмя и более процессорами и объемом оперативной памяти в несколько гигабайт. До недавнего времени на этом рынке доминировали операционные системы семейства UNIX благодаря достигнутому на протяжении 90-х гг. высокому уровню производительности, надежности, управляемости и гарантированной готовности. Чтобы стать реальной альтернативой UNIX на рынке корпоративных серверов, Windows 2000 должна превзойти ее по всем этим показателям.
Длинный список новых возможностей и усовершенствований, которые действительно позволяют считать разработку Windows 2000 значительным шагом вперед, включает и устранение недостатков, не позволивших Windows NT 4.0 выйти на рынок высокопроизводительных систем. В предлагаемой статье я хочу остановиться на возможностях Windows 2000, благодаря которым, по мнению разработчиков Microsoft, она превратиться в действительно масштабируемую операционную систему. Статья будет состоять из двух частей. В первой части я расскажу о новых возможностях Windows 2000 и приемах оптимизации, которые позволяют данной операционной системе более полно использовать большие объемы оперативной памяти. В следующем номере речь идет о многопроцессорных средствах Windows 2000.
Масштабируемость и оперативная память
Серверы масштаба предприятия, как правило, интенсивно используют оперативную память. Обычно они работают с объемами данных, исчисляемых десятками гигабайт, что сопряжено с жесткими требованиями к объему, установленной на сервере физической памяти. Типичный пример такой ситуации — сервер баз данных, обслуживающий многогигабайтную БД предприятия или несколько баз данных масштаба подразделения общим объемом в несколько гигабайт. Другие примеры интенсивного использования памяти крупными серверами — системы планирования ресурсов предприятия (Enterprise Resource Planning, ERP), приложения из сферы научных исследований или финансового анализа, где объем данных также исчисляется многими гигабайтами. Задержка при обращении к устройствам массовой памяти в несколько раз больше, чем при обращении к оперативной памяти; то же касается и пропускной способности. Именно поэтому весьма желательно, чтобы сервер мог хранить в оперативной памяти весь рабочий набор данных или хотя бы значительную его часть.
Рассмотрим гипотетический запрос к базе данных, размер которой составляет 6 Гбайт. Если в распоряжении сервера имеется только 1 Гбайт оперативной памяти, то в процессе выполнения запроса системе управления базой данных придется последовательно считать с диска содержимое всей базы в память сервера. При пропускной способности дисковой подсистемы 10 Мбайт/c запрос займет около 10 мин. Но если на том же сервере имеется 8 Гбайт оперативной памяти, вся база данных целиком поместится в кэш, и никаких обращений к диску не будет вовсе. При пропускной способности физической памяти порядка 1 Гбайт/с на тот же самый запрос уйдет всего несколько секунд. Приведенный пример иллюстрирует разницу между сервером, мощность которого адекватна объему обслуживаемых данных, и сервером, вынужденным полагаться на дисковую подсистему.
Большую часть времени серверные приложения не нуждаются в доступе ко всему рабочему набору данных. Вместо этого приложение хранит часто используемые порции данных в кэше, оставляя прочую информацию на диске. Типичный пример приложения, которое действует подобным образом, — Web-сервер; он хранит в кэше файлы, обращение к которым происходит чаще, чем к другим. При появлении запросов к таким файлам Web-сервер быстро предоставляет их пользователю. Вообще говоря, чем больше файлов Web-сервер может хранить в кэше, тем реже нужно будет обращаться к диску.
Кажется совершенно очевидным, что чем больше памяти установлено на сервере, тем большую нагрузку он сможет выдержать. Однако оказывается, что простое механическое расширение объема оперативной памяти вовсе не обязательно приводит к тому, что приложения масштабируются, т. е. полностью используют преимущества наличия дополнительной памяти. Для эффективного масштабирования необходимо выполнять два требования. Во-первых, операционная система должна уметь использовать всю установленную оперативную память, а во-вторых, она должна обеспечивать приложениям прямой доступ к этой памяти.
Большинство 64-разрядных операционных систем без труда справляются с такими требованиями. Эти ОС в состоянии адресовать всю установленную в системе память, поскольку выполняются на 64-разрядных аппаратных платформах. То же утверждение справедливо и для 64-разрядных приложений. В их распоряжении имеется 264 разряда для адресации, поэтому уже сейчас объем физической памяти, доступный такому приложению, значительно превосходит объемы оперативной памяти вычислительных систем обозримого будущего. Однако 32-разрядные операционные системы явно не соответствуют указанным требованиям. Это вынуждает разработчиков ОС создавать дополнительные механизмы для обслуживания огромных объемов памяти на серверах масштаба предприятия.
 |
| Экран 1. Виртуальное адресное пространство приложения. |
Первый недостаток 32-разрядных ОС состоит в том, что они ориентированы на 32-разрядные компьютеры, в частности аппаратные платформы на базе процессоров Intel x86. Исторически сложилось так, что эти системы поддерживают не более 4 Гбайт физической памяти (для адресации используется 232 байт = 4 Гбайт). Второй недостаток связан с общепринятым в таких системах методом хранения указателя в виде 4-байтового целого, что ограничивает объем виртуальной памяти, доступной приложению, 4 Гбайт. Большинство операционных систем, включая Windows 2000, NT и UNIX, делят виртуальное адресное пространство приложения на две области (см. Рисунок 1). Первая предназначена для нужд самого приложения, а вторую занимают ядро операционной системы, драйверы устройств и кэш файловой системы. Такой симбиоз позволяет ОС и драйверам устройств непосредственно обращаться к адресному пространству приложения, что обеспечивает эффективность обмена данными между приложением и службами операционной системы. Если бы ОС и приложение располагались в отдельных адресных пространствах, каждый системный вызов, включая операции ввода/вывода, сопровождался бы пересылкой данных между областью приложения и областью ОС, что сопряжено со значительными накладными расходами.
В NT 4.0 граница проходит посредине 4-гигабайтного адресного пространства, так что 2 Гбайт отводится приложению, а еще 2 Гбайт остается на нужды операционной системы. Администраторы систем Windows NT Server Enterprise Edition (NTS/E) для платформы x86, Windows 2000 Advanced Server (Windows 2000 AS) и Windows 2000 Datacenter Server (Datacenter) могут изменить пропорцию деления адресного пространства с помощью загрузочного переключателя /3GB. В этом случае под область приложений будет отведено 3 Гбайт, а системе останется 1 Гбайт памяти.
Размер адресного пространства, отведенного приложению, ограничивает максимальный объем данных, которыми оно может манипулировать непосредственно. Например, если на 32-разрядном сервере баз данных установлено 4 Гбайт оперативной памяти и используется схема деления 3:1, то этот сервер потенциально может обслуживать до 3 Гбайт оперативных данных без обращения к дисковой подсистеме. Анализ производительности усложняется, если ОС обслуживает обращение приложения к диску из файлового кэша; в этом случае фактического обмена с диском может не быть вовсе. В результате даже при наличии всего 3 Гбайт собственной виртуальной памяти приложение под управлением NT 4.0 может при некоторых условиях прямо или косвенно иметь доступ почти к 4 Гбайт физической памяти (конечно же, если система располагает таким объемом). Впрочем, вопрос о том, какие именно данные хранятся в кэше за пределами 3 Гбайт адресного пространства приложения, находится вне его компетенции — за это отвечает операционная система. И, наконец, если на сервере выполняется несколько активных приложений, операционная система разделяет физическую память сервера между ними.
Преодоление барьера 4 Гбайт на платформе x86
Архитектура x86 обслуживает не более 4 Гбайт внутренней и внешней физической памяти, в то время как операционная система может поддерживать больше. Чтобы процессоры семейства x86 могли обеспечить использование более 4 Гбайт физической памяти, нужно было внести изменения в их архитектуру. Поскольку разработчики Intel быстро осознали, что четырехгигабайтное ограничение будет препятствовать увеличению доли платформ x86 на рынке систем масштаба предприятия, процессоры x86 были дополнены новыми режимами работы. Так, в процессорах семейства Pentium Pro реализован новый режим расширения физического адреса (Physical Address Extension, PAE), а в процессорах Pentium II впервые использована 36-разрядная технология адресации с расширенной страницей (Page Size Extension, PSE36).
В обычном режиме работы процессоры x86 обеспечивают поддержку двухуровневой страничной архитектуры для преобразования виртуальных адресов (которыми оперируют и операционная система, и приложения) в физические адреса (которые используются запоминающим устройством). Блок управления памятью (Memory Management Unit, MMU) процессора x86 делит виртуальный адрес на три поля, как показано на Рисунке 2. Специальный регистр процессора CR3 указывает на структуру данных каталога страниц, а первое поле виртуального адреса служит индексом к этому каталогу. Блок MMU выбирает соответствующий четырехбайтный адрес из элемента каталога страниц (Page Directory Entry, PDE) по указанному индексу, локализуя таким образом таблицу страниц. Второе поле виртуального адреса задает элемент этой таблицы. Записи таблицы страниц (Page Table Entries, PTE) представляют собой четырехбайтное слово (32 бит). Элемент таблицы страниц определяет 20-разрядный адрес физической страницы, а поскольку в архитектуре x86 размер страницы равен 4096 (212) байт, максимальный адрес, который может быть сформирован таким образом, составляет 220+12 байт, что соответствует 4 Гбайт физической памяти. Последнее поле виртуального адреса задает смещение на странице, на которую указывает запись таблицы страниц.
Технология PSE36 позволяет операционной системе выдать блоку управления памятью команду выполнения одноуровневой трансляции виртуального адреса по указанной точке входа в каталоге страниц (см. Рисунок 3). Операционная система инициирует одноуровневую трансляцию с помощью маркировки записи в каталоге страниц атрибутом «страница расширенного размера» (Page-Size Exten-ded). При этом MMU использует физический адрес, хранящийся в элементе каталога страниц, как окончательный адрес страницы, а не адрес таблицы страниц. Кроме того, в MMU применяются 14-разрядные адреса страницы вместо стандартных 20-разрядных, но в этом режиме система работает с 4-мегабайтными (222 байт), а не 4-килобайтными страницами. В результате этих ухищрений можно получить 36-разрядные физические адреса (14-разрядный адрес страницы плюс 22-разрядный размер страницы), которых вполне достаточно для адресации 64 Гбайт физической памяти.
 |
| Экран 4. Операция записи в память при использовании механизма PSE86. |
Недостатком архитектуры PSE36 является увеличение размера страниц (4 Мбайт вместо стандартных 4 Кбайт): это малоэффективно при обычных операциях. В начале 1998 г. в Intel был разработан специальный драйвер устройства Intel PSE36 Driver, позволяющий приложениям, использующим архитектуру PSE36, адресовать память за пределами 4 Гбайт. Этот драйвер работает только под управлением NTS/E и разрешает использовать более 4 Гбайт памяти только одному приложению, причем только в качестве виртуального диска (RAM-диска). Адресное пространство приложения и операционной системы по-прежнему располагается в пределах 4-гигабайтной области, поэтому, когда приложению необходимо записать данные в память PSE36, оно извещает об этом драйвер PSE36, который копирует данные из буфера приложения в указанную область памяти за пределами 4 Гбайт. Этот процесс представлен на Рисунке 4.
Наличие дополнительной физической памяти, доступной приложению благодаря архитектуре PSE36, обычно приводит к повышению производительности работы приложения, которому иначе пришлось бы обращаться к диску. К сожалению, копирование данных за 4-гигабайтную границу и обратно драйвером PSE36 может пагубно отразиться на общей производительности системы. Именно поэтому разработчики Microsoft не стали продвигать PSE36 и предпочли использовать режим расширенной физической адресации PAE, который обеспечивает поддержку больших объемов физической памяти на платформе x86.
Когда процессор x86 работает в режиме расширенной физической адресации, блок MMU делит виртуальные адреса на четыре поля (см. Рисунок 5). MMU по-прежнему пользуется каталогами и таблицами страниц, но здесь имеется дополнительный уровень — таблица указателей на таблицы каталогов (Page Directory Pointer Table). В режиме PAE возможность адресации большего объема памяти, чем в стандартном режиме трансляции адресов, достигается не только за счет дополнительного уровня, но еще и за счет того, что записи каталогов и таблиц страниц имеют длину 8 (двойное слово), а не 4 байт. В результате внутреннее представление физического адреса имеет длину 24 бит, что позволяет системам x86 поддерживать 224+12 байт (64 Гбайт) памяти. Преимущество технологии расширенной физической адресации PAE перед PSE36 носит принципиальный характер: операционная система может использовать всю имеющуюся оперативную память как память общего назначения, так что операции копирования при обращении за пределы 4 Гбайт больше не нужны.
Поскольку режим PAE является дополнительным (его использовать не обязательно), а метод преобразования виртуальных адресов в физические отличается от принятого в стандартной архитектуре процессоров x86, разработчики операционных систем должны модифицировать код ОС для платформы x86 с учетом особенностей режима PAE. Специалисты Microsoft разработали версию ядра Windows 2000, которая реализует архитектуру PAE для платформы x86 при условии, что система поддерживает режим PAE и имеет более 4 Гбайт физической памяти. В этом случае загрузчик NT (NT Loader, NTLDR) вызывает ядро PAE ntkrnlpa.exe вместо стандартного ядра ntoskrnl.exe (существуют одно- и многопроцессорные версии ядра как для стандартного режима, так и для режима PAE). После загрузки ядра операционные системы Windows 2000 Professional и Windows 2000 Server ограничивают объем памяти, доступной приложениям, 4 Гбайт. В случае Windows 2000 Advanced Server, ядро с поддержкой режима PAE способно адресовать максимум 8 Гбайт памяти; ядро версии Datacenter в состоянии использовать максимум 64 Гбайт физической памяти, если система таким объемом располагает.
Address Windowing Extensions
Когда Windows 2000 находилась в стадии разработки, специалисты Intel создали набор микросхем 450NX, который позволяет процессорам семейства x86 использовать архитектуру расширенной физической адресации PAE для преодоления барьера в 4 Гбайт. Microsoft, в свою очередь, разработала универсальный интерфейс для применения в системах с большим объемом физической памяти. Используя этот интерфейс, который носит название «расширение адресного окна» (Address Windowing Extensions, AWE), приложение может, во-первых, запросить область физической памяти в исключительное пользование и, кроме того, получить доступ к любой части выделенной физической памяти с помощью так называемого адресного окна своего адресного пространства.
Для выделения физической памяти с помощью интерфейса AWE приложение вызывает функцию Allocate-UserPhysicalPages из состава API Win32. Затем приложение обращается к стандартной функции API Win32 VirtualAlloc для создания адресного окна в 4-гигабайтной области адресного пространства приложения. Функция VirtualAlloc устанавливает флаг MEM_PHYSICAL. Для ядра Windows 2000 это означает, что приложение создает адресное окно. После того как физическая память выделена, а окно создано, приложение может отобразить любой фрагмент физической памяти в созданном адресном окне. Например, если приложение создает адресное окно размером 256 Мбайт и выделяет для своих нужд 4 Гбайт физической памяти (при условии, что такой объем памяти в системе реально имеется), с помощью функций Map-UserPhysicalPages и MapUserPhysi-calPagesScatter API Win32 оно может обращаться к любой части физической памяти, отображая ее на 256-мегабайтное адресное окно. Размер окна приложения задает максимальный объем физической памяти, к которому приложение может получить доступ с помощью отображения. Процесс отображения физической памяти в адресное окно AWE показан на Рисунке 6.
 |
| Экран 7. Адресное окно AWE. |
Интерфейс AWE имеется во всех версиях Windows 2000, он активизирован независимо от объема установленной в системе памяти. Тем не менее технология AWE наиболее эффективна для систем с объемом физической памяти не менее 2 Гбайт. Поскольку приложениям отводится лишь 2 или 3 Гбайт собственной виртуальной памяти (в зависимости от того, использовался переключатель /3GB при загрузке ОС или нет), API AWE позволяет приложениям непосредственно манипулировать значительно большим объемом памяти, чем позволяет их адресное пространство. Например, для системы под управлением Windows 2000 AS и объемом оперативной памяти 8 Гбайт сервер базы данных может с помощью AWE реализовать почти 8-гигабайтный кэш под данные БД, доступные через адресные окна интерфейса AWE.
Помимо предоставления приложениям прямого доступа к огромному объему физической памяти, механизм AWE обладает еще двумя важными преимуществами. Прежде всего, это единообразная поддержка на всех 32- и 64-разрядных платформах; кроме того, с памятью, выделенной с помощью AWE, могут работать практически все стандартные вызовы API Win32.
Работа с памятью в среде SMP
Помимо усовершенствований ядра операционной системы, которые позволили приложениям пользоваться огромными объемами физической памяти, разработчики Windows 2000 внесли дополнительные изменения в алгоритмы работы с оперативной памятью, чтобы повысить производительность многопроцессорных систем на базе Windows 2000. Еще в NT 4.0 было введено понятие резервного списка (Lookaside List) — пула буферов фиксированного размера в области памяти ядра, которые ядро Windows 2000 и драйверы устройств создают и используют в качестве кэша для решения тех или иных задач.
Когда какое-либо приложение выполняет запрос к файловой системе, например чтение из файла, подсистема диспетчера ввода/вывода (I/O Manager) должна выделить буфер для хранения структуры данных запроса (I/O Request Packet, IRP). Диспетчер ввода/вывода передает буфер драйверу файловой системы, обслуживающему чтение файла, к которому обратилось приложение. Когда драйвер файловой системы завершает обслуживание операции чтения, диспетчер ввода/вывода должен освободить буфер данных IRP. Без использования резервных списков диспетчер ввода/вывода вынужден часто выделять и освобождать буферы IRP. Именно для повышения производительности диспетчера ввода/вывода Windows 2000 предназначен резервный список. Вместо того чтобы возвращать буфер IRP в общий пул памяти, диспетчер ввода/вывода хранит его в резервной области IRP. Теперь при необходимости выделить буфер для обслуживания запроса ввода/вывода диспетчер будет проверять состояние резерва. Если в списке есть хотя бы один свободный буфер, диспетчеру ввода/вывода нет нужды обращаться к диспетчеру буферов ядра системы. Ядро отслеживает, как часто драйверы устройств или подсистема ядра обращаются к освободившимся буферам в пуле резерва, и в соответствии с частотой таких обращений оптимизирует размер резерва. Чем чаще происходят обращения, тем больше максимально допустимое число резервных буферов. Когда размер пула резерва достигает текущего максимума, ядро возвращает буферы резерва в общий пул памяти.
Разработчики Windows 2000 внесли изменения в организацию резервного пула для оптимизации производительности системы. В многопроцессорных серверах используется специальный механизм синхронизации кэшируемых данных. Его задача — обеспечить тождественность копий одних и тех же данных в кэше разных процессоров. Необходимость такой синхронизации на многопроцессорных системах ведет к дополнительным «накладным расходам», поскольку алгоритм синхронизации регулярно захватывает многопроцессорную шину данных, тем самым препятствуя работе процессоров. В NT 4.0 все процессоры совместно используют единый резервный пул буферов ввода/вывода; в результате обновление резервных списков ведет к снижению производительности системы из-за необходимости синхронизации. Кроме того, при наличии общего пула процессоры должны блокировать его на время доступа; в NT это делается с помощью механизма блокировок, что также ведет к непроизводительному использованию многопроцессорной шины и замедляет работу процессоров. Во избежание падения производительности Windows 2000 создает для каждого процессора отдельный пул резервных буферов.
В системе существует порядка 10 пулов резервных буферов для каждого процессора. Помимо собственно пула диспетчера ввода/вывода такую же технику организации резервных буферов используют и две другие подсистемы Windows 2000: диспетчер объектов (Object Manager) и диспетчер кэша (Cache Manager). Диспетчер буферов ядра системы также применяет этот метод для оптимизации создания пулов 32-байтных буферов для каждого из процессоров сервера. Когда драйвер устройства или подсистема ядра посылают запрос на выделение буфера размером 32 байт (или меньше), диспетчер буферов ядра старается сначала выполнить запрос с помощью освободившегося буфера из своего резервного списка.
Помимо организации собственного списка резервных буферов для каждого процессора, разработчики Microsoft реализовали несколько других, более тонких методов оптимизации работы подсистемы диспетчера памяти Windows 2000, чтобы повысить масштабируемость памяти в многопроцессорной среде. Например, в Windows 2000 усовершенствован механизм рабочих наборов, который используется для хранения в физической памяти данных, чаще всего запрашиваемых приложением.
Размер пула и размер кэша
В NT 4.0 реализован резидентный пул для неперемещаемой памяти. Здесь драйверы устройств и оперативной системы хранят структуры данных, которые должны постоянно оставаться в физической памяти и не перемещаться на диск. Диспетчер памяти рассчитывает размер резидентного пула на основе нескольких параметров, в том числе в зависимости от того, сколько физической памяти установлено в системе (максимальный размер резидентного пула для NT 4.0 составляет 128 Мбайт). Работа драйвера Microsoft TCP/IP, выделяющего память из резидентного пула для каждого TCP/IP-соединения, напрямую зависит от размера резидентного пула. Таким образом, размер резидентного пула, в частности, ограничивает число одновременных TCP/IP-соединений. В процессе работы Web-сервера предприятия драйверам TCP/IP и другим драйверам может потребоваться объем памяти, превышающий предельный размер резидентного пула. В связи с этим разработчики Microsoft повысили объем максимально выделяемой памяти для резидентного пула в Windows 2000 до 256 Мбайт. При этом используются более компактные структуры данных для обслуживания резидентного пула, что позволяет дополнительно сэкономить память.
И, наконец, в NT 4.0 подсистема диспетчера кэша может использовать максимум 256 Мбайт виртуального адресного пространства, которое выделяет ей диспетчер памяти. В Win-dows 2000 этот предел повышен до 960 Мбайт. Увеличение доступного объема памяти позволяет диспетчеру кэша эффективно обслуживать большее число кэшированных файлов, поскольку ему не придется выполнять дополнительные операции по отображению физической памяти в область виртуальной кэш-памяти. Однако увеличение объема виртуальной памяти, отводимой под кэш, никак не влияет на число операций ввода/вывода, которые выполняет подсистема диспетчера кэша. Довольно широко распространено представление о том, что в операционных системах Windows 2000 и NT 4.0 кэш файловой системы использует физическую память лишь в пределах размера виртуального кэша. Между тем это совершенно неверно. На самом деле диспетчер кэша и в Windows 2000, и в NT 4.0 использует всю имеющуюся физическую память компьютерной системы.
Масштабируемость многопроцессорных систем
Новые средства операционной системы Windows 2000, которые позволяют ядру и приложениям использовать большие объемы физической памяти, чем это было доступно NT 4.0, расширяют сферу применения данной ОС до систем корпоративного класса и задач масштаба предприятия. Более того, оптимизация вопросов совместного использования памяти несколькими процессорами позволяет более эффективно применять Windows 2000 в многопроцессорных системах, что также будет способствовать ее продвижению на рынок операционных систем для серверов корпоративного класса. В следующей статье я продолжу рассказ о масштабируемости Windows 2000 и остановлюсь на тех характеристиках новой операционной системы и методах оптимизации производительности, которые помогут ядру Windows 2000 и приложениям более эффективно работать на многопроцессорных системах.
МАРК РУСИНОВИЧ — доктор философии и редактор Windows 2000 Magazine. С ним можно связаться по электронной почте по адресу: mark@sysinternals.com, или через Web-узел http://www.sysinternals.com
| Professional | Server | Advanced Server | Datacenter |
| 4 Гбайт | 4 Гбайт | 8 Гбайт | 32 Гбайт |
«Windows NT 5.0» redirects here. For the code name of this operating system, see List of Microsoft codenames.
| Version of the Windows NT operating system | |
 |
|

Screenshot of Windows 2000 Professional with SP4, showing the Start menu and the Getting Started with Windows window. |
|
| Developer | Microsoft |
|---|---|
| OS family | Microsoft Windows |
| Working state | No longer supported |
| Source model |
|
| Released to manufacturing |
December 15, 1999; 23 years ago[2] |
| General availability |
February 17, 2000; 22 years ago[3] |
| Final release | Service Pack 4 with Update Rollup (5.0.2195) / September 13, 2005; 17 years ago[4] |
| Marketing target | Business and Server |
| Update method | Windows Update |
| Platforms | IA-32 (including PC-98) (Alpha, MIPS, PowerPC in alpha, beta, and release candidate versions) |
| Kernel type | Hybrid (Windows NT kernel) |
| Userland | Windows API, NTVDM, OS/2 1.x, SFU |
| Default user interface |
Windows shell (Graphical) |
| License | Proprietary commercial software |
| Preceded by | Windows NT 4.0 (1996) |
| Succeeded by | Windows XP (2001, client) Windows Server 2003 (2003, servers) |
| Official website | microsoft.com/windows2000/ at the Wayback Machine (archived December 3, 2000) |
| Support status | |
| Mainstream support ended on June 30, 2005 Extended support ended on July 13, 2010[5] |
Windows 2000 is a major release of the Windows NT operating system developed by Microsoft and oriented towards businesses. It was the direct successor to Windows NT 4.0, and was released to manufacturing on December 15, 1999,[2] and was officially released to retail on February 17, 2000 and September 26, 2000 for Windows 2000 Datacenter Server. It was Microsoft’s business operating system until the introduction of Windows XP Professional in 2001.
Windows 2000 introduced NTFS 3.0,[6] Encrypting File System,[7] as well as basic and dynamic disk storage.[8] Support for people with disabilities was improved over Windows NT 4.0 with a number of new assistive technologies,[9] and Microsoft increased support for different languages[10] and locale information.[11] The Windows 2000 Server family has additional features, most notably the introduction of Active Directory,[12] which in the years following became a widely used directory service in business environments.
Four editions of Windows 2000 were released: Professional, Server, Advanced Server, and Datacenter Server;[13] the latter was both released to manufacturing and launched months after the other editions.[14] While each edition of Windows 2000 was targeted at a different market, they shared a core set of features, including many system utilities such as the Microsoft Management Console and standard system administration applications.
Microsoft marketed Windows 2000 as the most secure Windows version ever at the time;[15] however, it became the target of a number of high-profile virus attacks such as Code Red[16] and Nimda.[17] For ten years after its release, it continued to receive patches for security vulnerabilities nearly every month until reaching the end of support on July 13, 2010, the same day which support ended for Windows XP SP2.[5]
Windows 2000 and Windows 2000 Server were succeeded by Windows XP and Windows Server 2003, released in 2001 and 2003, respectively.
Windows 2000 is the final version of Windows that supports PC-98, i486 and SGI Visual Workstation 320 and 540, as well as Alpha, MIPS and PowerPC in alpha, beta, and release candidate versions. Its successor, Windows XP, only supports x86 and Itanium processors.
History[edit]
|
|
This section is missing information about features (other than the boot screen and sounds) introduced during the development. Please expand the section to include this information. Further details may exist on the talk page. (May 2021) |
Windows 2000, originally named NT 5.0, is a continuation of the Microsoft Windows NT family of operating systems, replacing Windows NT 4.0. Chairman and CEO Bill Gates was originally «pretty confident» NT 5.0 would ship in the first half of 1998,[18] revealing that the first set of beta builds had been shipped in early 1997; these builds were identical to Windows NT 4.0. The first official beta was released in September 1997, followed by Beta 2 in August 1998.[19][20] On October 27, 1998, Microsoft announced that the name of the final version of the operating system would be Windows 2000, a name which referred to its projected release date.[21] Windows 2000 Beta 3 was released in May 1999.[19] NT 5.0 Beta 1 was similar to NT 4.0, including a very similarly themed logo. NT 5.0 Beta 2 introduced a new ‘mini’ boot screen, and removed the ‘dark space’ theme in the logo. The NT 5.0 betas had very long startup and shutdown sounds, though these were changed in the early Windows 2000 beta, but during Beta 3, a new piano-made startup and shutdown sounds were made, composed by Steven Ray Allen.[22] It was featured in the final version as well as in Windows Me. The new login prompt from the final version made its first appearance in Beta 3 build 1946 (the first build of Beta 3). The new, updated icons (for My Computer, Recycle Bin etc.) first appeared in Beta 3 build 1964. The Windows 2000 boot screen in the final version first appeared in Beta 3 build 1983. Windows 2000 did not have an actual codename because, according to Dave Thompson of Windows NT team, «Jim Allchin didn’t like codenames».[23]
Windows 2000 Service Pack 1 was codenamed «Asteroid»[24] and Windows 2000 64-bit was codenamed «Janus.»[25][26] During development, there was a build for the Alpha which was abandoned in the final stages of development (between RC1 and RC2[27]) after Compaq announced they had dropped support for Windows NT on Alpha. From here, Microsoft issued three release candidates between July and November 1999, and finally released the operating system to partners on December 12, 1999, followed by manufacturing three days later on December 15.[28] The public could buy the full version of Windows 2000 on February 17, 2000. Three days before this event, which Microsoft advertised as «a standard in reliability,» a leaked memo from Microsoft reported on by Mary Jo Foley revealed that Windows 2000 had «over 63,000 potential known defects.»[29] After Foley’s article was published, she claimed that Microsoft blacklisted her for a considerable time.[30] However, Abraham Silberschatz et al. claim in their computer science textbook that «Windows 2000 was the most reliable, stable operating system Microsoft had ever shipped to that point. Much of this reliability came from maturity in the source code, extensive stress testing of the system, and automatic detection of many serious errors in drivers.»[31] InformationWeek summarized the release «our tests show the successor to NT 4.0 is everything we hoped it would be. Of course, it isn’t perfect either.»[32] Wired News later described the results of the February launch as «lackluster.»[33] Novell criticized Microsoft’s Active Directory, the new directory service architecture, as less scalable or reliable than its own Novell Directory Services (NDS) alternative.[34]
Windows 2000 is the last public release of Windows for PC-98, I486 and SGI Visual Workstation 320 and 540 as Windows XP runs solely on IA-32 only. Windows 2000 was initially planned to replace both Windows 98 and Windows NT 4.0. However, this would be changed later, as an updated version of Windows 98 called Windows 98 Second Edition was released in 1999.
On or shortly before February 12, 2004, «portions of the Microsoft Windows 2000 and Windows NT 4.0 source code were illegally made available on the Internet.»[35] The source of the leak was later traced to Mainsoft, a Windows Interface Source Environment partner.[36] Microsoft issued the following statement:
«Microsoft source code is both copyrighted and protected as a trade secret. As such, it is illegal to post it, make it available to others, download it or use it.»
Despite the warnings, the archive containing the leaked code spread widely on the file-sharing networks. On February 16, 2004, an exploit «allegedly discovered by an individual studying the leaked source code»[35] for certain versions of Microsoft Internet Explorer was reported. On April 15, 2015, GitHub took down a repository containing a copy of the Windows NT 4.0 source code that originated from the leak.[37]
Microsoft planned to release a 64-bit version of Windows 2000, which would run on 64-bit Intel Itanium microprocessors, in 2000.[38][39] However, the first officially released 64-bit version of Windows was Windows XP 64-Bit Edition, released alongside the 32-bit editions of Windows XP on October 25, 2001,[40] followed by the server versions Windows Datacenter Server Limited Edition and later Windows Advanced Server Limited Edition, which were based on the pre-release Windows Server 2003 (then known as Windows .NET Server) codebase.[41][42] These editions were released in 2002, were shortly available through the OEM channel and then were superseded by the final versions of Server 2003.[42]
New and updated features[edit]
Windows 2000 introduced many of the new features of Windows 98 and 98 SE into the NT line,[43] such as the Windows Desktop Update,[43] Internet Explorer 5 (Internet Explorer 6, which followed in 2001, is also available for Windows 2000),[43] Outlook Express, NetMeeting, FAT32 support,[44] Windows Driver Model,[45] Internet Connection Sharing,[43] Windows Media Player, WebDAV support[46] etc. Certain new features are common across all editions of Windows 2000, among them NTFS 3.0,[6] the Microsoft Management Console (MMC),[47] UDF support, the Encrypting File System (EFS),[48] Logical Disk Manager,[49] Image Color Management 2.0,[50] support for PostScript 3-based printers,[50] OpenType (.OTF) and Type 1 PostScript (.PFB) font support[50] (including a new font—Palatino Linotype—to showcase some OpenType features[51]), the Data protection API (DPAPI),[52] an LDAP/Active Directory-enabled Address Book,[53] usability enhancements and multi-language and locale support. Windows 2000 also introduced USB device class drivers for USB printers, Mass storage class devices,[54] and improved FireWire SBP-2 support for printers and scanners, along with a Safe removal applet for storage devices.[55] Windows 2000 SP4 added native USB 2.0 support. Windows 2000 is also the first Windows version to support hibernation at the operating system level (OS-controlled ACPI S4 sleep state) unlike Windows 98 which required special drivers from the hardware manufacturer or driver developer.[56]
A new capability designed to protect critical system files called Windows File Protection was introduced. This protects critical Windows system files by preventing programs other than Microsoft’s operating system update mechanisms such as the Package Installer, Windows Installer and other update components from modifying them.[57] The System File Checker utility provides users the ability to perform a manual scan of the integrity of all protected system files, and optionally repair them, either by restoring from a cache stored in a separate «DLLCACHE» directory, or from the original install media.
Microsoft recognized that a serious error (a Blue Screen of Death or stop error) could cause problems for servers that needed to be constantly running and so provided a system setting that would allow the server to automatically reboot when a stop error occurred.[58] Also included is an option to dump any of the first 64 KB of memory to disk (the smallest amount of memory that is useful for debugging purposes, also known as a minidump), a dump of only the kernel’s memory, or a dump of the entire contents of memory to disk, as well as write that this event happened to the Windows 2000 event log.[58] In order to improve performance on servers running Windows 2000, Microsoft gave administrators the choice of optimizing the operating system’s memory and processor usage patterns for background services or for applications.[59] Windows 2000 also introduced core system administration and management features as the Windows Installer,[60] Windows Management Instrumentation[61] and Event Tracing for Windows (ETW)[62] into the operating system.
Plug and Play and hardware support improvements[edit]
The most notable improvement from Windows NT 4.0 is the addition of Plug and Play with full ACPI and Windows Driver Model support. Similar to Windows 9x, Windows 2000 supports automatic recognition of installed hardware, hardware resource allocation, loading of appropriate drivers, PnP APIs and device notification events. The addition of the kernel PnP Manager along with the Power Manager are two significant subsystems added in Windows 2000.
Windows 2000 introduced version 3 print drivers (user mode printer drivers)[63] based on Unidrv, which made it easier for printer manufacturers to write device drivers for printers.[64] Generic support for 5-button mice is also included as standard [65] and installing IntelliPoint allows reassigning the programmable buttons. Windows 98 lacked generic support.[66] Driver Verifier was introduced to stress test and catch device driver bugs.[67]
Shell[edit]
Windows 2000 introduces layered windows that allow for transparency, translucency and various transition effects like shadows, gradient fills and alpha-blended GUI elements to top-level windows.[68] Menus support a new Fade transition effect.
Improvements in Windows Explorer: «Web-style» folders, media preview and customizable toolbars
The Start menu in Windows 2000 introduces personalized menus, expandable special folders and the ability to launch multiple programs without closing the menu by holding down the SHIFT key. A Re-sort button forces the entire Start Menu to be sorted by name. The Taskbar introduces support for balloon notifications which can also be used by application developers. Windows 2000 Explorer introduces customizable Windows Explorer toolbars, auto-complete in Windows Explorer address bar and Run box, advanced file type association features, displaying comments in shortcuts as tooltips, extensible columns in Details view (IColumnProvider interface), icon overlays, integrated search pane in Windows Explorer, sort by name function for menus, and Places bar in common dialogs for Open and Save.
Windows Explorer has been enhanced in several ways in Windows 2000. It is the first Windows NT release to include Active Desktop, first introduced as a part of Internet Explorer 4.0 (specifically Windows Desktop Update), and only pre-installed in Windows 98 by that time.[69] It allowed users to customize the way folders look and behave by using HTML templates, having the file extension HTT. This feature was abused by computer viruses that employed malicious scripts, Java applets, or ActiveX controls in folder template files as their infection vector. Two such viruses are VBS/Roor-C[70] and VBS.Redlof.a.[71]
The «Web-style» folders view, with the left Explorer pane displaying details for the object currently selected, is turned on by default in Windows 2000. For certain file types, such as pictures and media files, the preview is also displayed in the left pane.[72] Until the dedicated interactive preview pane appeared in Windows Vista, Windows 2000 had been the only Windows release to feature an interactive media player as the previewer for sound and video files, enabled by default. However, such a previewer can be enabled in previous versions of Windows with the Windows Desktop Update installed through the use of folder customization templates.[73] The default file tooltip displays file title, author, subject and comments;[74] this metadata may be read from a special NTFS stream, if the file is on an NTFS volume, or from an OLE structured storage stream, if the file is a structured storage document. All Microsoft Office documents since Office 4.0[75] make use of structured storage, so their metadata is displayable in the Windows 2000 Explorer default tooltip. File shortcuts can also store comments which are displayed as a tooltip when the mouse hovers over the shortcut. The shell introduces extensibility support through metadata handlers, icon overlay handlers and column handlers in Explorer Details view.[76]
The right pane of Windows 2000 Explorer, which usually just lists files and folders, can also be customized. For example, the contents of the system folders aren’t displayed by default, instead showing in the right pane a warning to the user that modifying the contents of the system folders could harm their computer. It’s possible to define additional Explorer panes by using DIV elements in folder template files.[69] This degree of customizability is new to Windows 2000; neither Windows 98 nor the Desktop Update could provide it.[77] The new DHTML-based search pane is integrated into Windows 2000 Explorer, unlike the separate search dialog found in all previous Explorer versions. The Indexing Service has also been integrated into the operating system and the search pane built into Explorer allows searching files indexed by its database.[78]
NTFS 3.0[edit]
Main article: NTFS
Microsoft released the version 3.0 of NTFS[6] (sometimes incorrectly called «NTFS 5» in relation to the kernel version number) as part of Windows 2000; this introduced disk quotas (provided by QuotaAdvisor), file-system-level encryption, sparse files and reparse points. Sparse files allow for the efficient storage of data sets that are very large yet contain many areas that only have zeros.[79] Reparse points allow the object manager to reset a file namespace lookup and let file system drivers implement changed functionality in a transparent manner.[80] Reparse points are used to implement volume mount points, junctions, Hierarchical Storage Management, Native Structured Storage and Single Instance Storage.[80] Volume mount points and directory junctions allow for a file to be transparently referred from one file or directory location to another.
Windows 2000 also introduces a Distributed Link Tracking service to ensure file shortcuts remain working even if the target is moved or renamed. The target object’s unique identifier is stored in the shortcut file on NTFS 3.0 and Windows can use the Distributed Link Tracking service for tracking the targets of shortcuts, so that the shortcut file may be silently updated if the target moves, even to another hard drive.[81]
Encrypting File System[edit]
The Encrypting File System (EFS) introduced strong file system-level encryption to Windows. It allows any folder or drive on an NTFS volume to be encrypted transparently by the user.[48] EFS works together with the EFS service, Microsoft’s CryptoAPI and the EFS File System Runtime Library (FSRTL).[82] To date, its encryption has not been compromised.[citation needed]
EFS works by encrypting a file with a bulk symmetric key (also known as the File Encryption Key, or FEK), which is used because it takes less time to encrypt and decrypt large amounts of data than if an asymmetric key cipher were used.[82] The symmetric key used to encrypt the file is then encrypted with a public key associated with the user who encrypted the file, and this encrypted data is stored in the header of the encrypted file. To decrypt the file, the file system uses the private key of the user to decrypt the symmetric key stored in the file header. It then uses the symmetric key to decrypt the file. Because this is done at the file system level, it is transparent to the user.[83]
For a user losing access to their key, support for recovery agents that can decrypt files is built into EFS. A Recovery Agent is a user who is authorized by a public key recovery certificate to decrypt files belonging to other users using a special private key. By default, local administrators are recovery agents however they can be customized using Group Policy.
Basic and dynamic disk storage[edit]
Windows 2000 introduced the Logical Disk Manager and the diskpart command line tool for dynamic storage.[8] All versions of Windows 2000 support three types of dynamic disk volumes (along with basic disks): simple volumes, spanned volumes and striped volumes:
- Simple volume, a volume with disk space from one disk.
- Spanned volumes, where up to 32 disks show up as one, increasing it in size but not enhancing performance. When one disk fails, the array is destroyed. Some data may be recoverable. This corresponds to JBOD and not to RAID-1.
- Striped volumes, also known as RAID-0, store all their data across several disks in stripes. This allows better performance because disk reads and writes are balanced across multiple disks. Like spanned volumes, when one disk in the array fails, the entire array is destroyed (some data may be recoverable).
In addition to these disk volumes, Windows 2000 Server, Windows 2000 Advanced Server, and Windows 2000 Datacenter Server support mirrored volumes and striped volumes with parity:
- Mirrored volumes, also known as RAID-1, store identical copies of their data on 2 or more identical disks (mirrored). This allows for fault tolerance; in the event one disk fails, the other disk(s) can keep the server operational until the server can be shut down for replacement of the failed disk.
- Striped volumes with parity, also known as RAID-5, functions similar to striped volumes/RAID-0, except «parity data» is written out across each of the disks in addition to the data. This allows the data to be «rebuilt» in the event a disk in the array needs replacement.
Accessibility[edit]
With Windows 2000, Microsoft introduced the Windows 9x accessibility features for people with visual and auditory impairments and other disabilities into the NT-line of operating systems.[9] These included:
- StickyKeys: makes modifier keys (
ALT,CTRLandSHIFT) become «sticky»: a user can press the modifier key, and then release it before pressing the combination key. (Activated by pressing Shift five times quickly.) - FilterKeys: a group of keyboard-related features for people with typing issues, including:
- Slow Keys: Ignore any keystroke not held down for a certain period.
- Bounce Keys: Ignore repeated keystrokes pressed in quick succession.
- Repeat Keys: lets users slow down the rate at which keys are repeated via the keyboard’s key-repeat feature.
- Toggle Keys: when turned on, Windows will play a sound when the
CAPS LOCK,NUM LOCKorSCROLL LOCKkey is pressed. - SoundSentry: designed to help users with auditory impairments, Windows 2000 shows a visual effect when a sound is played through the sound system.
- MouseKeys: lets users move the cursor around the screen via the numeric keypad.
- SerialKeys: lets Windows 2000 support speech augmentation devices.
- High contrast theme: to assist users with visual impairments.
- Microsoft Magnifier: a screen magnifier that enlarges a part of the screen the cursor is over.[84]
Additionally, Windows 2000 introduced the following new accessibility features:
- On-screen keyboard: displays a virtual keyboard on the screen and allows users to press its keys using a mouse or a joystick.[85]
- Microsoft Narrator: introduced in Windows 2000, this is a screen reader that utilizes the Speech API 4, which would later be updated to Speech API 5 in Windows XP
- Utility Manager: an application designed to start, stop, and manage when accessibility features start. This was eventually replaced by the Ease of Access Center in Windows Vista.
- Accessibility Wizard: a control panel applet that helps users set up their computer for people with disabilities.
Languages and locales[edit]
Windows 2000 introduced the Multilingual User Interface (MUI).[10] Besides English, Windows 2000 incorporates support for Arabic, Armenian, Baltic, Central European, Cyrillic, Georgian, Greek, Hebrew, Indic, Japanese, Korean, simplified Chinese, Thai, traditional Chinese, Turkic, Vietnamese and Western European languages.[86] It also has support for many different locales.[11]
Games[edit]
Windows 2000 included version 7.0 of the DirectX API, commonly used by game developers on Windows 98.[87] The last version of DirectX that was released for Windows 2000 was DirectX 9.0c (Shader Model 3.0), which shipped with Windows XP Service Pack 2. Microsoft published quarterly updates to DirectX 9.0c through the February 2010 release after which support was dropped in the June 2010 SDK. These updates contain bug fixes to the core runtime and some additional libraries such as D3DX, XAudio 2, XInput and Managed DirectX components. The majority of games written for versions of DirectX 9.0c (up to the February 2010 release) can therefore run on Windows 2000.
Windows 2000 included the same games as Windows NT 4.0 did: FreeCell, Minesweeper, Pinball, and Solitaire.[88]
System utilities[edit]
Windows 2000’s Computer Management console can perform many system tasks. This image shows a disk defragmentation in progress.
Windows 2000 introduced the Microsoft Management Console (MMC), which is used to create, save, and open administrative tools.[47] Each of these is called a console, and most allow an administrator to administer other Windows 2000 computers from one centralised computer. Each console can contain one or many specific administrative tools, called snap-ins.[47] These can be either standalone (with one function), or an extension (adding functions to an existing snap-in). In order to provide the ability to control what snap-ins can be seen in a console, the MMC allows consoles to be created in author mode or user mode.[47] Author mode allows snap-ins to be added, new windows to be created, all portions of the console tree to be displayed and consoles to be saved. User mode allows consoles to be distributed with restrictions applied. User mode consoles can grant full access to the user for any change, or they can grant limited access, preventing users from adding snapins to the console though they can view multiple windows in a console. Alternatively users can be granted limited access, preventing them from adding to the console and stopping them from viewing multiple windows in a single console.[89]
The main tools that come with Windows 2000 can be found in the Computer Management console (in Administrative Tools in the Control Panel).[90] This contains the Event Viewer—a means of seeing events and the Windows equivalent of a log file,[91] a system information utility, a backup utility, Task Scheduler and management consoles to view open shared folders and shared folder sessions, configure and manage COM+ applications, configure Group Policy,[92] manage all the local users and user groups, and a device manager.[93] It contains Disk Management and Removable Storage snap-ins,[94] a disk defragmenter as well as a performance diagnostic console, which displays graphs of system performance and configures data logs and alerts. It also contains a service configuration console, which allows users to view all installed services and to stop and start them, as well as configure what those services should do when the computer starts. CHKDSK has significant performance improvements.[95]
Windows 2000 comes with two utilities to edit the Windows registry, REGEDIT.EXE and REGEDT32.EXE.[96] REGEDIT has been directly ported from Windows 98, and therefore does not support editing registry permissions.[96] REGEDT32 has the older multiple document interface (MDI) and can edit registry permissions in the same manner that Windows NT’s REGEDT32 program could. REGEDIT has a left-side tree view of the Windows registry, lists all loaded hives and represents the three components of a value (its name, type, and data) as separate columns of a table. REGEDT32 has a left-side tree view, but each hive has its own window, so the tree displays only keys and it represents values as a list of strings. REGEDIT supports right-clicking of entries in a tree view to adjust properties and other settings. REGEDT32 requires all actions to be performed from the top menu bar. Windows XP is the first system to integrate these two programs into a single utility, adopting the REGEDIT behavior with the additional NT features.[96]
The System File Checker (SFC) also comes with Windows 2000. It is a command line utility that scans system files and verifies whether they were signed by Microsoft and works in conjunction with the Windows File Protection mechanism. It can also repopulate and repair all the files in the Dllcache folder.[97]
Recovery Console[edit]
The Recovery Console is usually used to recover unbootable systems.
The Recovery Console is run from outside the installed copy of Windows to perform maintenance tasks that can neither be run from within it nor feasibly be run from another computer or copy of Windows 2000.[98] It is usually used to recover the system from problems that cause booting to fail, which would render other tools useless, like Safe Mode or Last Known Good Configuration, or chkdsk. It includes commands like fixmbr, which are not present in MS-DOS.
It has a simple command-line interface, used to check and repair the hard drive(s), repair boot information (including NTLDR), replace corrupted system files with fresh copies from the CD, or enable/disable services and drivers for the next boot.
The console can be accessed in either of the two ways:
- Booting from the Windows 2000 CD, and choosing to start the Recovery Console from the CD itself instead of continuing with setup. The Recovery Console is accessible as long as the installation CD is available.
- Preinstalling the Recovery Console on the hard disk as a startup option in
Boot.ini, via WinNT32.exe, with the /cmdcons switch.[99] In this case, it can only be started as long as NTLDR can boot from the system partition.
Windows Scripting Host 2.0[edit]
Windows 2000 introduced Windows Script Host 2.0 which included an expanded object model and support for logon and logoff scripts.
Networking[edit]
- Starting with Windows 2000, the Server Message Block (SMB) protocol directly interfaces with TCP/IP. In Windows NT 4.0, SMB requires the NetBIOS over TCP/IP (NBT) protocol to work on a TCP/IP network.
- Windows 2000 introduces a client-side DNS caching service. When the Windows DNS resolver receives a query response, the DNS resource record is added to a cache. When it queries the same resource record name again and it is found in the cache, then the resolver does not query the DNS server. This speeds up DNS query time and reduces network traffic.
Server family features[edit]
The Windows 2000 Server family consists of Windows 2000 Server, Windows 2000 Advanced Server, Windows 2000 Small Business Server, and Windows 2000 Datacenter Server.
All editions of Windows 2000 Server have the following services and features built in:
- Routing and Remote Access Service (RRAS) support, facilitating dial-up and VPN connections using IPsec, L2TP or L2TP/IPsec, support for RADIUS authentication in Internet Authentication Service, network connection sharing, Network Address Translation, unicast and multicast routing schemes.
- Remote access security features: Remote Access Policies for setup, verify Caller ID (IP address for VPNs), callback and Remote access account lockout[100]
- Autodial by location feature using the Remote Access Auto Connection Manager service
- Extensible Authentication Protocol support in IAS (EAP-MD5 and EAP-TLS) later upgraded to PEAPv0/EAP-MSCHAPv2 and PEAP-EAP-TLS in Windows 2000 SP4
- DNS server, including support for Dynamic DNS. Active Directory relies heavily on DNS.
- IPsec support and TCP/IP filtering
- Smart card support
- Microsoft Connection Manager Administration Kit (CMAK) and Connection Point Services
- Support for distributed file systems (DFS)
- Hierarchical Storage Management support including remote storage,[101] a service that runs with NTFS and automatically transfers files that are not used for some time to less expensive storage media
- Fault tolerant volumes, namely Mirrored and RAID-5
- Group Policy (part of Active Directory)
- IntelliMirror, a collection of technologies for fine-grained management of Windows 2000 Professional clients that duplicates users’ data, applications, files, and settings in a centralized location on the network. IntelliMirror employs technologies such as Group Policy, Windows Installer, Roaming profiles, Folder Redirection, Offline Files (also known as Client Side Caching or CSC), File Replication Service (FRS), Remote Installation Services (RIS) to address desktop management scenarios such as user data management, user settings management, software installation and maintenance.
- COM+, Microsoft Transaction Server and Distributed Transaction Coordinator
- MSMQ 2.0
- TAPI 3.0
- Integrated Windows Authentication (including Kerberos, Secure channel and SPNEGO (Negotiate) SSP packages for Security Support Provider Interface (SSPI)).
- MS-CHAP v2 protocol
- Public Key Infrastructure (PKI) and Enterprise Certificate Authority support
- Terminal Services and support for the Remote Desktop Protocol (RDP)
- Internet Information Services (IIS) 5.0 and Windows Media Services 4.1
- Network quality of service features[102]
- A new Windows Time service which is an implementation of Simple Network Time Protocol (SNTP) as detailed in IETF RFC 1769. The Windows Time service synchronizes the date and time of computers in a domain[103] running on Windows 2000 Server or later. Windows 2000 Professional includes an SNTP client.
The Server editions include more features and components, including the Microsoft Distributed File System (DFS), Active Directory support and fault-tolerant storage.
Distributed File System[edit]
The Distributed File System (DFS) allows shares in multiple different locations to be logically grouped under one folder, or DFS root. When users try to access a network share off the DFS root, the user is really looking at a DFS link and the DFS server transparently redirects them to the correct file server and share. A DFS root can only exist on a Windows 2000 version that is part of the server family, and only one DFS root can exist on that server.
There can be two ways of implementing a DFS namespace on Windows 2000: either through a standalone DFS root or a domain-based DFS root. Standalone DFS allows for only DFS roots on the local computer, and thus does not use Active Directory. Domain-based DFS roots exist within Active Directory and can have their information distributed to other domain controllers within the domain – this provides fault tolerance to DFS. DFS roots that exist on a domain must be hosted on a domain controller or on a domain member server. The file and root information is replicated via the Microsoft File Replication Service (FRS).[104]
Active Directory[edit]
A new way of organizing Windows network domains, or groups of resources, called Active Directory, is introduced with Windows 2000 to replace Windows NT’s earlier domain model. Active Directory’s hierarchical nature allowed administrators a built-in way to manage user and computer policies and user accounts, and to automatically deploy programs and updates with a greater degree of scalability and centralization than provided in previous Windows versions. User information stored in Active Directory also provided a convenient phone book-like function to end users. Active Directory domains can vary from small installations with a few hundred objects, to large installations with millions. Active Directory can organise and link groups of domains into a contiguous domain name space to form trees. Groups of trees outside of the same namespace can be linked together to form forests.
Active Directory services could always be installed on a Windows 2000 Server Standard, Advanced, or Datacenter computer, and cannot be installed on a Windows 2000 Professional computer. However, Windows 2000 Professional is the first client operating system able to exploit Active Directory’s new features. As part of an organization’s migration, Windows NT clients continued to function until all clients were upgraded to Windows 2000 Professional, at which point the Active Directory domain could be switched to native mode and maximum functionality achieved.
Active Directory requires a DNS server that supports SRV resource records, or that an organization’s existing DNS infrastructure be upgraded to support this. There should be one or more domain controllers to hold the Active Directory database and provide Active Directory directory services.
Volume fault tolerance[edit]
Along with support for simple, spanned and striped volumes, the Windows 2000 Server family also supports fault-tolerant volume types. The types supported are mirrored volumes and RAID-5 volumes:
- Mirrored volumes: the volume contains several disks, and when data is written to one it is also written to the other disks. This means that if one disk fails, the data can be totally recovered from the other disk. Mirrored volumes are also known as RAID-1.
- RAID-5 volumes: a RAID-5 volume consists of multiple disks, and it uses block-level striping with parity data distributed across all member disks. Should a disk fail in the array, the parity blocks from the surviving disks are combined mathematically with the data blocks from the surviving disks to reconstruct the data on the failed drive «on-the-fly.»
Deployment[edit]
| Minimum | Recommended | |
|---|---|---|
| IA-32 PCs | ||
| CPU | Pentium 133 MHz | Pentium II 300 MHz |
| Memory | 32 MB (128 MB for Windows 2000 Server) | 128 MB (256 MB for Windows 2000 Server) |
| Free space | 1 GB (2 GB for Windows 2000 Server) | 5 GB |
| Graphics hardware | 800×600 VGA or better monitor | 1024×768 VGA or better monitor |
| Input device(s) | Keyboard and/or mouse |
Windows 2000 can be deployed to a site via various methods. It can be installed onto servers via traditional media (such as CD) or via distribution folders that reside on a shared folder. Installations can be attended or unattended. During a manual installation, the administrator must specify configuration options. Unattended installations are scripted via an answer file, or a predefined script in the form of an INI file that has all the options filled in. An answer file can be created manually or using the graphical Setup manager. The Winnt.exe or Winnt32.exe program then uses that answer file to automate the installation. Unattended installations can be performed via a bootable CD, using Microsoft Systems Management Server (SMS), via the System Preparation Tool (Sysprep), via the Winnt32.exe program using the /syspart switch or via Remote Installation Services (RIS). The ability to slipstream a service pack into the original operating system setup files is also introduced in Windows 2000.[105]
The Sysprep method is started on a standardized reference computer – though the hardware need not be similar – and it copies the required installation files from the reference computer to the target computers. The hard drive does not need to be in the target computer and may be swapped out to it at any time, with the hardware configured later. The Winnt.exe program must also be passed a /unattend switch that points to a valid answer file and a /s file that points to one or more valid installation sources.
Sysprep allows the duplication of a disk image on an existing Windows 2000 Server installation to multiple servers. This means that all applications and system configuration settings will be copied across to the new installations, and thus, the reference and target computers must have the same HALs, ACPI support, and mass storage devices – though Windows 2000 automatically detects «plug and play» devices. The primary reason for using Sysprep is to quickly deploy Windows 2000 to a site that has multiple computers with standard hardware. (If a system had different HALs, mass storage devices or ACPI support, then multiple images would need to be maintained.)
Systems Management Server can be used to upgrade multiple computers to Windows 2000. These must be running Windows NT 3.51, Windows NT 4.0, Windows 98 or Windows 95 OSR2.x along with the SMS client agent that can receive software installation operations. Using SMS allows installations over a wide area and provides centralised control over upgrades to systems.
Remote Installation Services (RIS) are a means to automatically install Windows 2000 Professional (and not Windows 2000 Server) to a local computer over a network from a central server. Images do not have to support specific hardware configurations and the security settings can be configured after the computer reboots as the service generates a new unique security ID (SID) for the machine. This is required so that local accounts are given the right identifier and do not clash with other Windows 2000 Professional computers on a network.[106]
RIS requires that client computers are able to boot over the network via either a network interface card that has a Pre-Boot Execution Environment (PXE) boot ROM installed or that the client computer has a network card installed that is supported by the remote boot disk generator. The remote computer must also meet the Net PC specification. The server that RIS runs on must be Windows 2000 Server and it must be able to access a network DNS Service, a DHCP service and the Active Directory services.[107]
Editions[edit]
Microsoft released various editions of Windows 2000 for different markets and business needs: Professional, Server, Advanced Server and Datacenter Server. Each was packaged separately.
Windows 2000 Professional was designed as the desktop operating system for businesses and power users. It is the client version of Windows 2000. It offers greater security and stability than many of the previous Windows desktop operating systems. It supports up to two processors, and can address up to 4 GB of RAM. The system requirements are a Pentium processor (or equivalent) of 133 MHz or greater, at least 32 MB of RAM, 650 MB of hard drive space, and a CD-ROM drive (recommended: Pentium II, 128 MB of RAM, 2 GB of hard drive space, and CD-ROM drive).[108] However, despite the official minimum processor requirements, it is still possible to install Windows 2000 on 4th-generation x86 CPUs such as the 80486.
Screenshot of Windows 2000 Server with Configure Your Server component.
Windows 2000 Server shares the same user interface with Windows 2000 Professional, but contains additional components for the computer to perform server roles and run infrastructure and application software. A significant new component introduced in the server versions is Active Directory, which is an enterprise-wide directory service based on LDAP (Lightweight Directory Access Protocol). Additionally, Microsoft integrated Kerberos network authentication, replacing the often-criticised NTLM (NT LAN Manager) authentication system used in previous versions. This also provided a purely transitive-trust relationship between Windows 2000 Server domains in a forest (a collection of one or more Windows 2000 domains that share a common schema, configuration, and global catalog, being linked with two-way transitive trusts). Furthermore, Windows 2000 introduced a Domain Name Server which allows dynamic registration of IP addresses. Windows 2000 Server supports up to 4 processors and 4 GB of RAM, with a minimum requirement of 128 MB of RAM and 1 GB hard disk space, however requirements may be higher depending on installed components.[108]
Windows 2000 Advanced Server is a variant of Windows 2000 Server operating system designed for medium-to-large businesses. It offers the ability to create clusters of servers, support for up to 8 CPUs, a main memory amount of up to 8 GB on Physical Address Extension (PAE) systems and the ability to do 8-way SMP. It supports TCP/IP load balancing and builds on Microsoft Cluster Server (MSCS) in Windows NT Enterprise Server 4.0, adding enhanced functionality for two-node clusters.[109] System requirements are similar to those of Windows 2000 Server,[108] however they may need to be higher to scale to larger infrastructure.
Screenshot of Windows 2000 Datacenter Server, asking the user to complete setup by configuring Cluster and Remote Installation service in the Configure Your Server component.
Windows 2000 Datacenter Server is a variant of Windows 2000 Server designed for large businesses that move large quantities of confidential or sensitive data frequently via a central server.[110] Like Advanced Server, it supports clustering, failover and load balancing. Its minimum system requirements are similar to those of Advanced Server,[108] but it was designed to be capable of handing advanced, fault-tolerant and scalable hardware—for instance computers with up to 32 CPUs and 32 GBs RAM, with rigorous system testing and qualification, hardware partitioning, coordinated maintenance and change control. Windows 2000 Datacenter Server was released to manufacturing on August 11, 2000[111] and launched on September 26, 2000.[112] This edition was based on Windows 2000 with Service Pack 1[110] and was not available at retail.[113]
Service packs[edit]
| Service pack | Release date |
|---|---|
| Service Pack 1 (SP1) | August 15, 2000 |
| Service Pack 2 (SP2) | May 16, 2001 |
| Service Pack 3 (SP3) | August 29, 2002 |
| Service Pack 4 (SP4) | June 26, 2003 |
| SP4 Update Rollup | September 13, 2005 |
Windows 2000 has received four full service packs and one rollup update package following SP4, which is the last service pack. Microsoft phased out all development of its Java Virtual Machine (JVM) from Windows 2000 in SP3. Internet Explorer 5.01 has also been upgraded to the corresponding service pack level.
Service Pack 4 with Update Rollup was released on September 13, 2005, nearly four years following the release of Windows XP and sixteen months prior to the release of Windows Vista.
Microsoft had originally intended to release a fifth service pack for Windows 2000, but Microsoft cancelled this project early in its development, and instead released Update Rollup 1 for SP4, a collection of all the security-related hotfixes and some other significant issues.[114] The Update Rollup does not include all non-security related hotfixes and is not subjected to the same extensive regression testing as a full service pack. Microsoft states that this update will meet customers’ needs better than a whole new service pack, and will still help Windows 2000 customers secure their PCs, reduce support costs, and support existing computer hardware.[115]
Upgradeability[edit]
Several Windows 2000 components are upgradable to latest versions, which include new versions introduced in later versions of Windows, and other major Microsoft applications are available. These latest versions for Windows 2000 include:
- ActiveSync 4.5
- DirectX 9.0c (5 February 2010 Redistributable)
- Internet Explorer 6 SP1 and Outlook Express 6 SP1
- Microsoft Agent 2.0
- Microsoft Data Access Components 2.81
- Microsoft NetMeeting 3.01 and Microsoft Office 2003 on Windows 2000 SP3 and SP4 (and Microsoft Office XP on Windows 2000 versions below SP3.)
- MSN Messenger 7.0 (Windows Messenger)
- MSXML 6.0 SP2
- .NET Framework 2.0 SP2
- Tweak UI 1.33
- Visual C++ 2008
- Visual Studio 2005
- Windows Desktop Search 2.66
- Windows Script Host 5.7
- Windows Installer 3.1
- Windows Media Format Runtime and Windows Media Player 9 Series (including Windows Media Encoder 7.1 and the Windows Media 8 Encoding Utility)
Security[edit]
During the Windows 2000 period, the nature of attacks on Windows servers changed: more attacks came from remote sources via the Internet. This has led to an overwhelming number of malicious programs exploiting the IIS services – specifically a notorious buffer overflow tendency.[116] This tendency is not operating-system-version specific, but rather configuration-specific: it depends on the services that are enabled.[116] Following this, a common complaint is that «by default, Windows 2000 installations contain numerous potential security problems. Many unneeded services are installed and enabled, and there is no active local security policy.»[117] In addition to insecure defaults, according to the SANS Institute, the most common flaws discovered are remotely exploitable buffer overflow vulnerabilities.[118] Other criticized flaws include the use of vulnerable encryption techniques.[119]
Code Red and Code Red II were famous (and much discussed) worms that exploited vulnerabilities of the Windows Indexing Service of Windows 2000’s Internet Information Services (IIS).[16] In August 2003, security researchers estimated that two major worms called Sobig and Blaster infected more than half a million Microsoft Windows computers.[120] The 2005 Zotob worm was blamed for security compromises on Windows 2000 machines at ABC, CNN, the New York Times Company, and the United States Department of Homeland Security.[121]
On September 8, 2009, Microsoft skipped patching two of the five security flaws that were addressed in the monthly security update, saying that patching one of the critical security flaws was «infeasible.»[122] According to Microsoft Security Bulletin MS09-048: «The architecture to properly support TCP/IP protection does not exist on Microsoft Windows 2000 systems, making it infeasible to build the fix for Microsoft Windows 2000 Service Pack 4 to eliminate the vulnerability. To do so would require re-architecting a very significant amount of the Microsoft Windows 2000 Service Pack 4 operating system, there would be no assurance that applications designed to run on Microsoft Windows 2000 Service Pack 4 would continue to operate on the updated system.» No patches for this flaw were released for the newer Windows XP (32-bit) and Windows XP Professional x64 Edition either, despite both also being affected;[123] Microsoft suggested turning on Windows Firewall in those versions.[124]
Support lifecycle[edit]
Windows 2000 and Windows 2000 Server were superseded by newer Microsoft operating systems: Windows 2000 Server products by Windows Server 2003, and Windows 2000 Professional by Windows XP Professional.
The Windows 2000 family of operating systems moved from mainstream support to the extended support phase on June 30, 2005. Microsoft says that this marks the progression of Windows 2000 through the Windows lifecycle policy. Under mainstream support, Microsoft freely provides design changes if any, service packs and non-security related updates in addition to security updates, whereas in extended support, service packs are not provided and non-security updates require contacting the support personnel by e-mail or phone. Under the extended support phase, Microsoft continued to provide critical security updates every month for all components of Windows 2000 (including Internet Explorer 5.0 SP4) and paid per-incident support for technical issues. Because of Windows 2000’s age, updated versions of components such as Windows Media Player 11 and Internet Explorer 7 have not been released for it. In the case of Internet Explorer, Microsoft said in 2005 that, «some of the security work in IE 7 relies on operating system functionality in XP SP2 that is non-trivial to port back to Windows 2000.»[125]
While users of Windows 2000 Professional and Server were eligible to purchase the upgrade license for Windows Vista Business or Windows Server 2008, neither of these operating systems can directly perform an upgrade installation from Windows 2000; a clean installation must be performed instead or a two-step upgrade through XP/2003. Microsoft has dropped the upgrade path from Windows 2000 (and earlier) to Windows 7. Users of Windows 2000 must buy a full Windows 7 license.
Although Windows 2000 is the last NT-based version of Microsoft Windows which does not include product activation, Microsoft has introduced Windows Genuine Advantage for certain downloads and non-critical updates from the Download Center for Windows 2000.
Windows 2000 reached the end of its lifecycle on July 13, 2010 (alongside Service Pack 2 of Windows XP). It will not receive new security updates and new security-related hotfixes after this date.[5][126] In Japan, over 130,000 servers and 500,000 PCs in local governments were affected; many local governments said that they will not update as they do not have funds to cover a replacement.[127]
As of 2011, Windows Update still supports the Windows 2000 updates available on Patch Tuesday in July 2010, e.g., if older optional Windows 2000 features are enabled later. Microsoft Office products under Windows 2000 have their own product lifecycles. While Internet Explorer 6 for Windows XP did receive security patches up until it lost support, this is not the case for IE6 under Windows 2000. The Windows Malicious Software Removal Tool installed monthly by Windows Update for XP and later versions can be still downloaded manually for Windows 2000.[128]
Microsoft in 2020 announced that it would disable the Windows Update service for SHA-1 endpoints and since Windows 2000 did not get an update for SHA-2, Windows Update Services are no longer available on the OS as of late July 2020.[129] However, as of April 2021, the old updates for Windows 2000 are still available on the Microsoft Update Catalog.[130]
Total cost of ownership[edit]
In October 2002, Microsoft commissioned IDC to determine the total cost of ownership (TCO) for enterprise applications on Windows 2000 versus the TCO of the same applications on Linux. IDC’s report is based on telephone interviews of IT executives and managers of 104 North American companies in which they determined what they were using for a specific workload for file, print, security and networking services.
IDC determined that the four areas where Windows 2000 had a better TCO than Linux – over a period of five years for an average organization of 100 employees – were file, print, network infrastructure and security infrastructure. They determined, however, that Linux had a better TCO than Windows 2000 for web serving. The report also found that the greatest cost was not in the procurement of software and hardware, but in staffing costs and downtime. While the report applied a 40% productivity factor during IT infrastructure downtime, recognizing that employees are not entirely unproductive, it did not consider the impact of downtime on the profitability of the business. The report stated that Linux servers had less unplanned downtime than Windows 2000 servers. It found that most Linux servers ran less workload per server than Windows 2000 servers and also that none of the businesses interviewed used 4-way SMP Linux computers. The report also did not take into account specific application servers – servers that need low maintenance and are provided by a specific vendor. The report did emphasize that TCO was only one factor in considering whether to use a particular IT platform, and also noted that as management and server software improved and became better packaged the overall picture shown could change.[131]
See also[edit]
- Architecture of Windows NT
- BlueKeep (security vulnerability)
- Comparison of operating systems
- DEC Multia, one of the DEC Alpha computers capable of running Windows 2000 beta
- Microsoft Servers, Microsoft’s network server software brand
- Windows Neptune, a cancelled consumer edition based on Windows 2000
References[edit]
- ^ «Microsoft Shared Source Initiative Overview». Microsoft. March 2003. Archived from the original on April 2, 2003. Retrieved February 17, 2017.
- ^ a b «Microsoft Releases Windows 2000 to Manufacturing». News Center. Microsoft. December 15, 1999. Archived from the original on June 4, 2019. Retrieved February 14, 2017.
- ^ «Gates Ushers in Next Generation of PC Computing With Launch of Windows 2000». News Center. Microsoft. February 17, 2000. Archived from the original on October 3, 2019. Retrieved February 17, 2018.
- ^ «Update Rollup 1 for Windows 2000 SP4 and known issues». Microsoft. Archived from the original on March 2, 2017. Retrieved February 17, 2017.
- ^ a b c «Microsoft Product Lifecycle for Windows 2000 family». Support. Microsoft. Archived from the original on April 7, 2013. Retrieved February 17, 2017.
- ^ a b c «New Capabilities and Features of the NTFS 3.0 File System». Microsoft Support. Microsoft. Archived from the original on October 24, 2007. Retrieved February 14, 2017.
- ^ «Implementing the Encrypting File System in Windows 2000». TechNet. Microsoft. March 24, 2009. Archived from the original on August 26, 2017. Retrieved February 14, 2017.
- ^ a b «Disk Management». TechNet. Microsoft. Archived from the original on December 22, 2016. Retrieved February 14, 2017.
- ^ a b «Windows 2000 Professional Accessibility Features». Microsoft. Archived from the original on December 17, 2003. Retrieved February 14, 2017.
- ^ a b «Frequently Asked Questions: Windows Server 2003, Windows XP, and Windows 2000 MUI». MSDN. Microsoft. Archived from the original on February 18, 2017. Retrieved February 17, 2017.
- ^ a b «Windows 2000 — List of Locale IDs and Language Groups». Global Development and Computing Portal. Microsoft. Archived from the original on February 3, 2003. Retrieved February 14, 2017.
- ^ «Windows 2000 Server Family». TechNet. Microsoft. Archived from the original on December 22, 2016. Retrieved February 17, 2017.
- ^ «Microsoft Renames Windows NT 5.0 Product Line to Windows 2000; Signals Evolution of Windows NT Technology Into Mainstream». News Center. Microsoft. October 27, 1998. Archived from the original on January 12, 2009. Retrieved February 14, 2017.
- ^ «Microsoft Announces Final Packaging for Windows 2000». News Center. Microsoft. August 17, 1999. Archived from the original on May 8, 2014. Retrieved February 14, 2017.
- ^ «Microsoft and CyberSafe Extend Windows 2000 Security Across the Enterprise». News Center. Microsoft. January 17, 2000. Archived from the original on February 18, 2017. Retrieved February 17, 2017.
- ^ a b «‘Code Red’ Worm Exploiting Buffer Overflow in IIS Indexing Service DLL». CERT Coordination Center. Software Engineering Institute. July 19, 2001. Archived from the original on August 17, 2016. Retrieved May 17, 2019.
- ^ Swartz, Jon (September 25, 2001). «Nimba called most serious Net attack on business». USA Today. Gannett Company. Archived from the original on February 17, 2017. Retrieved February 17, 2017.
- ^ Veitch, Martin (March 20, 1997). «NT 5.0 to ship in first half 1998 — Gates». ZDNet.
- ^ a b Thurrott, Paul (December 15, 1999). «Road to Gold: A Look at the Development of Windows 2000». Supersite for Windows. Penton. Archived from the original on August 21, 2017. Retrieved April 17, 2019.
- ^ . HPCWire. June 6, 1997 https://www.hpcwire.com/1997/06/06/bill-gates-speaks-about-1998-release-of-nt-5-0/.
- ^ Trott, Bob (October 27, 1998). «It’s official: NT 5.0 becomes Windows 2000». InfoWorld. Archived from the original on March 2, 2005. Retrieved April 22, 2006.
- ^ Fran Board (April 27, 2022). «Ta-da! It’s Windows!». 20k.org (Podcast). Twenty Thousand Hertz. Retrieved December 7, 2022.
- ^ Thurrott, Paul (August 8, 2013). «SuperSite Flashback: NT’s First Decade». Supersite for Windows. Penton. Archived from the original on August 1, 2017. Retrieved August 10, 2013.
- ^ «Windows 2000 service pack nearing release». Zdnetasia.com. January 27, 2000. Archived from the original on May 29, 2012. Retrieved November 13, 2011.
- ^ Thurrott, Paul (July 27, 1999). «64-bit Windows 2000 on track for mid-2000». Windows IT Pro. Archived from the original on May 29, 2012.
- ^ «Windows 2000 to Launch at Comdex, 64-Bit Janus in the Wings». Findarticles.com. August 26, 1999. Archived from the original on July 18, 2010. Retrieved November 13, 2011.
- ^ «RC1 was the build 2072 from June 1999 (and last public Alpha/2000 build), the last known internal build was 2128 and the «Gold» release of Windows 2000 was build 2195″. Alphant.com. Archived from the original on November 30, 2011.
- ^ «Windows 2000 history». ActiveWin. Archived from the original on May 20, 2006. Retrieved April 22, 2006.
- ^ Foley, Mary Jo (February 14, 2000). «Bugfest! Win2000 has 63,000 ‘defects’«. ZDNet. Archived from the original on January 13, 2007. Retrieved July 29, 2014.
- ^ McLaws, Robert (September 20, 2006). «Mary Jo Foley: The Exit Interview». WindowsNow. Archived from the original on January 13, 2015. Retrieved July 26, 2014.
- ^ John Wiley & Sons (2010). Operating System Concepts with Java, 8th Edition, page 901.
- ^ «Special Report — Windows 2000 Review: Say Hello to Win2000». InformationWeek. November 6, 2003. Archived from the original on December 8, 2015. Retrieved April 17, 2019.
- ^ Heilemann, John. «The Truth, The Whole Truth, and Nothing But The Truth». Wired. Archived from the original on July 24, 2008. Retrieved April 17, 2019.
- ^ «NDS eDirectory vs. Microsoft Active Directory?». Novell. November 17, 1999. Archived from the original on February 11, 2005. Retrieved April 22, 2006.
NDS eDirectory is a cross-platform directory solution that works on NT 4.0, Windows 2000 when available, Solaris and NetWare 5. Active Directory will only support the Windows 2000 environment. In addition, eDirectory users can be assured they are using the most trusted, reliable and mature directory service to manage and control their e-business relationships – not a 1.0 release.
- ^ a b «Statement from Microsoft Regarding Illegal Posting of Windows 2000 Source Code». Microsoft. February 20, 2004. Archived from the original on August 5, 2011. Retrieved January 11, 2007.
- ^ «Mainsoft Eyed as Windows Source Code Leak». internetnews.co. February 13, 2004. Archived from the original on March 9, 2021. Retrieved July 3, 2009.
- ^ Van der Saar, Ernesto (April 15, 2015). «Microsoft Takes Pirated Windows NT 4.0 Source Code Offline». TorrentFreak. Archived from the original on November 8, 2020. Retrieved March 28, 2021.
- ^ «Microsoft and Intel Announce Preview Release of 64-Bit Windows for Intel Itanium Processor» (Press release). Microsoft. July 12, 2000. Archived from the original on October 24, 2007. Retrieved October 4, 2007.
- ^ «64-Bit Windows Overview». Microsoft. October 7, 1999. Archived from the original on March 1, 2000. Retrieved July 23, 2014.
- ^ «Microsoft Unveils Plans for 64-Bit Windows Platform — Stories». News.microsoft.com. May 23, 2001. Archived from the original on October 31, 2019. Retrieved February 15, 2020.
- ^ Bekker, Scott (March 5, 2002). «Datacenter Server Limited Edition Released». Redmond Magazine. Archived from the original on August 12, 2014. Retrieved July 23, 2014.
Although Microsoft has pushed back the schedule for Windows .NET Server, the company is going ahead with the release of a limited edition of Windows Datacenter Server based on Windows .NET Server beta code.
- ^ a b «Introducing Windows Advanced Server, Limited Edition». Microsoft. Archived from the original on October 22, 2002. Retrieved January 12, 2013.
- ^ a b c d «Introducing Windows 2000 Professional». Microsoft.com. Archived from the original on March 20, 2007. Retrieved November 13, 2011.
- ^ Description of the FAT32 File System Archived May 8, 2008, at the Wayback Machine,
- ^ «Windows Driver Model (WDM)». Microsoft.com. April 15, 2002. Archived from the original on December 22, 2010. Retrieved November 13, 2011.
- ^ «Overview of Web Folders in Internet Explorer 5». Support.microsoft.com. March 29, 2007. Archived from the original on January 5, 2012. Retrieved November 13, 2011.
- ^ a b c d «Microsoft Management Console – Overview». Technet.microsoft.com. Archived from the original on November 22, 2011. Retrieved November 13, 2011.
- ^ a b «Implementing the Encrypting File System in Windows 2000». Microsoft.com. Archived from the original on July 23, 2008. Retrieved November 13, 2011.
- ^ «Disk Management». Microsoft.com. Archived from the original on January 12, 2009. Retrieved November 13, 2011.
- ^ a b c «Windows 2000 To Include New On-Screen And Printed Scalable Color Solution». Findarticles.com. September 6, 1999. Archived from the original on February 23, 2006. Retrieved November 13, 2011.
- ^ «MSDN Blogs». msdn.com. Microsoft. Archived from the original on August 9, 2014. Retrieved August 8, 2014.
- ^ «How to troubleshoot the Data Protection API (DPAPI)». Support.microsoft.com. December 3, 2007. Archived from the original on October 5, 2011. Retrieved November 13, 2011.
- ^ «How to Configure the Address Book to Query Users Contained in Active Directory». Support.microsoft.com. January 24, 2007. Archived from the original on October 20, 2011. Retrieved November 13, 2011.
- ^ «USB FAQ: Introductory level». Microsoft.com. August 25, 2008. Archived from the original on December 25, 2010. Retrieved November 13, 2011.
- ^ «IEEE 1394 and the Windows platform». Msdn.microsoft.com. December 14, 2001. Archived from the original on November 8, 2011. Retrieved November 13, 2011.
- ^ «Windows and Power Management». Microsoft.com. January 1, 2002. Archived from the original on July 13, 2004. Retrieved November 13, 2011.
- ^ «Microsoft KB article 222193: Description of the Windows File Protection Feature». Archived from the original on August 21, 2006. Retrieved September 17, 2006.
- ^ a b «How to configure system failure and recovery options in Windows». Support.microsoft.com. May 23, 2006. Archived from the original on November 16, 2011. Retrieved November 13, 2011.
- ^ «Analyzing processor activity: Windows 2000 Professional Resource Kit». Microsoft.com. Archived from the original on April 17, 2008. Retrieved November 13, 2011.
- ^ «Using Windows Installer in Windows 2000 beta 3». Entmag.com. October 7, 2011. Archived from the original on January 14, 2009. Retrieved November 13, 2011.
- ^ «Programming with Windows Management Instrumentation». Informit.com. October 4, 2000. Archived from the original on January 3, 2013. Retrieved November 13, 2011.
- ^ «Event Tracing for Windows (ETW): MSDN». Msdn.microsoft.com. Archived from the original on December 2, 2011. Retrieved November 13, 2011.
- ^ «Choosing User Mode or Kernel Mode». Msdn.microsoft.com. Archived from the original on October 6, 2012. Retrieved November 13, 2011.
- ^ «Microsoft Universal Printer Driver — Windows drivers». docs.microsoft.com. Archived from the original on November 11, 2020. Retrieved September 13, 2020.
- ^ «Keyboard and mouse HID client drivers». microsoft.com. Microsoft. Archived from the original on March 14, 2013. Retrieved July 4, 2013.
- ^ «Fourth and Fifth Mouse Buttons Not Recognized by Windows». microsoft.com. Microsoft. Archived from the original on November 26, 2012. Retrieved July 4, 2013.
- ^ Driver Verifier at MSDN Archived April 24, 2012, at the Wayback Machine. Microsoft.
- ^ «Layered Windows: MSDN». Msdn.microsoft.com. Archived from the original on November 26, 2011. Retrieved November 13, 2011.
- ^ a b Esposito, Dino (June 2000). «More Windows 2000 UI Goodies: Extending Explorer Views by Customizing Hypertext Template Files». MSDN Magazine. Archived from the original on August 24, 2007. Retrieved August 26, 2007.
- ^ Sophos, VBS/Roor-C threat analysis Archived November 30, 2007, at the Wayback Machine. Retrieved August 26, 2007.
- ^ «Virus.VBS.Redlof.a». Viruslist.com. January 15, 2004. Archived from the original on October 28, 2007. Retrieved August 26, 2007.
- ^ «Managing Files, Folders, and Search Methods: Microsoft TechNet». Microsoft.com. Archived from the original on January 12, 2009. Retrieved November 13, 2011.
- ^ «How to Enable Preview for Multimedia Files». Microsoft. January 31, 2000. Archived from the original on November 17, 2012. Retrieved March 29, 2012.
- ^ «Windows 2000 Registry: Latest Features and APIs Provide the Power to Customize and Extend Your Apps». MSDN Magazine. November 2000. Archived from the original on April 15, 2003. Retrieved August 26, 2007.
- ^ Kindel, Charlie (August 27, 1993). «OLE Property Sets Exposed». MSDN Magazine. Retrieved August 26, 2007. [dead link]
- ^ «Windows 2000 UI Innovations: MSDN Magazine». Msdn.microsoft.com. Archived from the original on June 5, 2009. Retrieved November 13, 2011.
- ^ «Figure 1 Windows Shell Extensions». MSDN Magazine. June 2000. Archived from the original on August 31, 2004. Retrieved August 26, 2007.
- ^ «What is Indexing Service?: MSDN». Msdn.microsoft.com. Archived from the original on January 1, 2011. Retrieved November 13, 2011.
- ^ «Sparse Files Use Quota Equal to Total Allocated Length». Support.microsoft.com. February 26, 2007. Archived from the original on November 16, 2012. Retrieved November 13, 2011.
- ^ a b «Improved NTFS File System». Microsoft.com. Archived from the original on April 16, 2008. Retrieved November 13, 2011.
- ^ «Distributed Link Tracking and Object Identifiers (Windows)». TechNet. Microsoft. October 16, 2012. Archived from the original on October 23, 2012. Retrieved November 27, 2012.
- ^ a b «How Encrypting File System Works». Technet2.microsoft.com. July 19, 2011. Archived from the original on May 22, 2007. Retrieved November 13, 2011.
- ^ «Encrypting File System Archived January 12, 2009, at the Wayback Machine.» Microsoft.
- ^ «A review of Microsoft Magnifier and Narrator». Archived from the original on October 23, 2007.
- ^ «Accessibility Technology & Tools | Microsoft Accessibility». Accessibility. Archived from the original on September 6, 2009.
- ^ «List of languages supported in Windows 2000, Windows XP, and Windows Server 2003». Support. Microsoft. Archived from the original on March 2, 2017. Retrieved February 17, 2017.
- ^ Ask the Windows 2000 Dev Team Archived March 11, 2007, at the Wayback Machine
- ^ Ford, Jerry Lee, Jr (2000). Upgrading to Microsoft Windows 2000 Professional: A Migration Guide for Windows 98 and Windows NT Users. iUniverse.com. Lincoln, NE: iUniverse. p. 90. ISBN 0595148042. Archived from the original on April 2, 2021. Retrieved January 8, 2013.
- ^ Microsoft Press (2000). MCSE 70–210, Microsoft Windows 2000 Professional, pages 58–63.
- ^ «Managing Microsoft Windows 2000 Workstations and Servers». Technet.microsoft.com. Archived from the original on November 27, 2011. Retrieved November 13, 2011.
- ^ «Event Logging and Viewing». Technet.microsoft.com. Archived from the original on November 27, 2011. Retrieved November 13, 2011.
- ^ «Step-by-Step Guide to Understanding the Group Policy Feature Set». Technet.microsoft.com. Archived from the original on November 20, 2011. Retrieved November 13, 2011.
- ^ «Description of Device Manager in Windows 2000 and Windows XP». Support.microsoft.com. May 7, 2007. Archived from the original on October 23, 2011. Retrieved November 13, 2011.
- ^ «Windows 2000: Removable Storage and Backup». Microsoft.com. Archived from the original on April 17, 2008. Retrieved November 13, 2011.
- ^ «Windows 2000 Chkdsk Management». Microsoft. Archived from the original on November 4, 2012. Retrieved November 13, 2011.
- ^ a b c «Differences between Regedit.exe and Regedt32.exe». Support.microsoft.com. January 19, 2007. Archived from the original on November 20, 2011. Retrieved November 13, 2011.
- ^ «Microsoft KB article 222471: Description of the Windows 2000 System File Checker (Sfc.exe)». Archived from the original on September 1, 2006. Retrieved September 17, 2006.
- ^ «Description of the Windows 2000 Recovery Console». Support.microsoft.com. February 26, 2007. Archived from the original on November 4, 2011. Retrieved November 13, 2011.
- ^ «How to install the Windows Recovery Console». Support.microsoft.com. October 26, 2007. Archived from the original on November 16, 2011. Retrieved November 13, 2011.
- ^ «Elements of Secure Remote Access». Technet.microsoft.com. Archived from the original on December 18, 2011. Retrieved November 13, 2011.
- ^ «How to use Remote Storage in Windows 2000 Server». Support.microsoft.com. October 30, 2006. Archived from the original on January 10, 2012. Retrieved November 13, 2011.
- ^ «An Overview of Windows 2000 Quality of Service». Technet.microsoft.com. Archived from the original on December 3, 2011. Retrieved November 13, 2011.
- ^ «Basic Operation of the Windows Time Service». Support.microsoft.com. October 26, 2007. Archived from the original on November 2, 2011. Retrieved November 13, 2011.
- ^ «Microsoft KB article 812487: Overview of DFS in Windows 2000». Archived from the original on February 14, 2007. Retrieved September 17, 2006.
- ^ «Make deployment easier in Windows 2000». Microsoft.com. Archived from the original on June 15, 2007. Retrieved November 13, 2011.
- ^ Mark Minasi. Installing Windows 2000 on Workstations with Remote Installation Services.
- ^ Microsoft Press (2000). MCSE 70–210, Microsoft Windows 2000 Professional, pages 543–551.
- ^ a b c d «System requirements for Microsoft Windows 2000 operating systems». Archived from the original on April 16, 2008. Retrieved May 23, 2008.
- ^ Microsoft. Windows 2000 Resource Kit, Chap. 1, «Introducing Windows 2000 Deployment Planning.»
- ^ a b «The Datacenter Program and Windows 2000 Datacenter Server Product». Support.microsoft.com. February 28, 2007. Archived from the original on November 3, 2011. Retrieved November 13, 2011.
- ^ «Microsoft Ships Windows 2000 Datacenter Server to Program Partners». Microsoft.com. August 11, 2000. Archived from the original on March 24, 2014. Retrieved January 9, 2013.
- ^ «Microsoft Windows Datacenter Program — All Systems Go». Microsoft.com. Archived from the original on March 24, 2014. Retrieved January 9, 2013.
- ^ «Microsoft Announces Datacenter Program for Windows 2000». Microsoft.com. February 15, 2000. Archived from the original on March 24, 2014. Retrieved January 9, 2013.
- ^ Naraine, Ryan (November 26, 2004). «Microsoft Scraps Plans for Windows 2000 SP5». Archived from the original on August 26, 2011. Retrieved May 30, 2009.
- ^ «Windows 2000 Update Rollup 1 for Service Pack 4». Microsoft. Archived from the original on January 13, 2006. Retrieved September 27, 2006.
- ^ a b «Worms Wreak Havoc». ECommerce-Guide. August 19, 2003. Archived from the original on March 1, 2005. Retrieved May 17, 2019.
- ^ «Articles — Network Security Resources — GovernmentSecurity.org». Network Security Resources.[permanent dead link]
- ^ «SANS Institute». Archived from the original on September 19, 2006. Retrieved September 17, 2006.
- ^ McCullagh, Declan (May 16, 2000). «Critics Blast MS Security». Wired News. Archived from the original on July 24, 2008. Retrieved February 25, 2010.
- ^ «SoBig worm not slowing down yet». CNN Money. Time Warner. August 21, 2003. Archived from the original on May 17, 2019. Retrieved May 17, 2019.
- ^ Poulsen, Kevin (April 12, 2006). «Border Security System Left Open». Wired. Condé Nast. Archived from the original on February 17, 2017. Retrieved February 17, 2017.
- ^ Techworld Archived April 26, 2014, at the Wayback Machine, September 9, 2009, «Microsoft: Windows 2000 too old to update»
- ^ «microsoft.com». Microsoft. Archived from the original on August 4, 2011. Retrieved November 13, 2011.
- ^ Keizer, Gregg (September 14, 2009). «Microsoft: No TCP/IP patches for you, XP». Computerworld. Archived from the original on May 17, 2019. Retrieved May 17, 2019.
- ^ Marson, Ingrid (June 3, 2005). «Windows 2000 users to miss out on IE 7». CNET. CBS Interactive. Archived from the original on May 17, 2019. Retrieved May 17, 2019.
- ^ «Windows 2000 Transitions to Extended Support June 30, 2005». Microsoft. June 28, 2005. Archived from the original on June 30, 2005. Retrieved February 17, 2017.
- ^ «Windows 2000 still in use locally». The Japan Times. The Japan Times, Ltd. August 20, 2010. Archived from the original on September 10, 2016. Retrieved February 17, 2017.
- ^ «Malicious Software Removal Tool». n (KB890830). Microsoft. 2011. Archived from the original on June 21, 2012. Retrieved July 24, 2011.
- ^ «Windows Update SHA-1 based endpoints discontinued for older Windows devices». support.microsoft.com. Retrieved April 6, 2021.
- ^ «Microsoft Update Catalog». www.catalog.update.microsoft.com. Retrieved April 6, 2021.
- ^ «Windows 2000 Versus Linux in Enterprise Computing Archived April 10, 2008, at the Wayback Machine,» IDC.
Further reading[edit]
- Bolosky, William J.; Corbin, Scott; Goebel, David; & Douceur, John R. «Single Instance Storage in Windows 2000.» Microsoft Research & Balder Technology Group, Inc. (white paper).
- Bozman, Jean; Gillen, Al; Kolodgy, Charles; Kusnetzky, Dan; Perry, Randy; & Shiang, David (October 2002). «Windows 2000 Versus Linux in Enterprise Computing: An assessment of business value for selected workloads.» IDC, sponsored by Microsoft Corporation. White paper.
- Finnel, Lynn (2000). MCSE Exam 70–215, Microsoft Windows 2000 Server. Microsoft Press. ISBN 1-57231-903-8.
- Microsoft. Running Nonnative Applications in Windows 2000 Professional[permanent dead link]. Windows 2000 Resource Kit. Retrieved May 4, 2005.
- Microsoft. «Active Directory Data Storage.» Retrieved May 9, 2005.
- Minasi, Mark (1999). Installing Windows 2000 of Mastering Windows 2000 Server. Sybex. Chapter 3 – Installing Windows 2000 On Workstations with Remote Installation Services.
- Russinovich, Mark (October 1997). «Inside NT’s Object Manager.» Windows IT Pro.
- Russinovich, Mark (2002). «Inside Win2K NTFS, Part 1.» Windows IT Pro (formerly Windows 2000 Magazine).
- Saville, John (January 9, 2000). «What is Native Structure Storage?.» Windows IT Pro (formerly Windows 2000 Magazine).
- Siyan, Kanajit S. (2000). «Windows 2000 Professional Reference.» New Riders. ISBN 0-7357-0952-1.
- Solomon, David; & Russinovich, Mark E. (2000). Inside Microsoft Windows 2000 (Third Edition). Microsoft Press. ISBN 0-7356-1021-5.
- Tanenbaum, Andrew S. (2001), Modern Operating Systems (2nd Edition), Prentice-Hall
- Trott, Bob (October 27, 1998). «It’s official: NT 5.0 becomes Windows 2000.» InfoWorld.
- Wallace, Rick (2000). MCSE Exam 70–210, Microsoft Windows 2000 Professional. Microsoft Press. ISBN 1-57231-901-1.
External links[edit]
- Windows 2000 End-of-Life
- Windows 2000 Service Pack 4
- Windows 2000 Update Rollup 1 Version 2
«Windows NT 5.0» redirects here. For the code name of this operating system, see List of Microsoft codenames.
| Version of the Windows NT operating system | |
 |
|

Screenshot of Windows 2000 Professional with SP4, showing the Start menu and the Getting Started with Windows window. |
|
| Developer | Microsoft |
|---|---|
| OS family | Microsoft Windows |
| Working state | No longer supported |
| Source model |
|
| Released to manufacturing |
December 15, 1999; 23 years ago[2] |
| General availability |
February 17, 2000; 22 years ago[3] |
| Final release | Service Pack 4 with Update Rollup (5.0.2195) / September 13, 2005; 17 years ago[4] |
| Marketing target | Business and Server |
| Update method | Windows Update |
| Platforms | IA-32 (including PC-98) (Alpha, MIPS, PowerPC in alpha, beta, and release candidate versions) |
| Kernel type | Hybrid (Windows NT kernel) |
| Userland | Windows API, NTVDM, OS/2 1.x, SFU |
| Default user interface |
Windows shell (Graphical) |
| License | Proprietary commercial software |
| Preceded by | Windows NT 4.0 (1996) |
| Succeeded by | Windows XP (2001, client) Windows Server 2003 (2003, servers) |
| Official website | microsoft.com/windows2000/ at the Wayback Machine (archived December 3, 2000) |
| Support status | |
| Mainstream support ended on June 30, 2005 Extended support ended on July 13, 2010[5] |
Windows 2000 is a major release of the Windows NT operating system developed by Microsoft and oriented towards businesses. It was the direct successor to Windows NT 4.0, and was released to manufacturing on December 15, 1999,[2] and was officially released to retail on February 17, 2000 and September 26, 2000 for Windows 2000 Datacenter Server. It was Microsoft’s business operating system until the introduction of Windows XP Professional in 2001.
Windows 2000 introduced NTFS 3.0,[6] Encrypting File System,[7] as well as basic and dynamic disk storage.[8] Support for people with disabilities was improved over Windows NT 4.0 with a number of new assistive technologies,[9] and Microsoft increased support for different languages[10] and locale information.[11] The Windows 2000 Server family has additional features, most notably the introduction of Active Directory,[12] which in the years following became a widely used directory service in business environments.
Four editions of Windows 2000 were released: Professional, Server, Advanced Server, and Datacenter Server;[13] the latter was both released to manufacturing and launched months after the other editions.[14] While each edition of Windows 2000 was targeted at a different market, they shared a core set of features, including many system utilities such as the Microsoft Management Console and standard system administration applications.
Microsoft marketed Windows 2000 as the most secure Windows version ever at the time;[15] however, it became the target of a number of high-profile virus attacks such as Code Red[16] and Nimda.[17] For ten years after its release, it continued to receive patches for security vulnerabilities nearly every month until reaching the end of support on July 13, 2010, the same day which support ended for Windows XP SP2.[5]
Windows 2000 and Windows 2000 Server were succeeded by Windows XP and Windows Server 2003, released in 2001 and 2003, respectively.
Windows 2000 is the final version of Windows that supports PC-98, i486 and SGI Visual Workstation 320 and 540, as well as Alpha, MIPS and PowerPC in alpha, beta, and release candidate versions. Its successor, Windows XP, only supports x86 and Itanium processors.
History[edit]
|
|
This section is missing information about features (other than the boot screen and sounds) introduced during the development. Please expand the section to include this information. Further details may exist on the talk page. (May 2021) |
Windows 2000, originally named NT 5.0, is a continuation of the Microsoft Windows NT family of operating systems, replacing Windows NT 4.0. Chairman and CEO Bill Gates was originally «pretty confident» NT 5.0 would ship in the first half of 1998,[18] revealing that the first set of beta builds had been shipped in early 1997; these builds were identical to Windows NT 4.0. The first official beta was released in September 1997, followed by Beta 2 in August 1998.[19][20] On October 27, 1998, Microsoft announced that the name of the final version of the operating system would be Windows 2000, a name which referred to its projected release date.[21] Windows 2000 Beta 3 was released in May 1999.[19] NT 5.0 Beta 1 was similar to NT 4.0, including a very similarly themed logo. NT 5.0 Beta 2 introduced a new ‘mini’ boot screen, and removed the ‘dark space’ theme in the logo. The NT 5.0 betas had very long startup and shutdown sounds, though these were changed in the early Windows 2000 beta, but during Beta 3, a new piano-made startup and shutdown sounds were made, composed by Steven Ray Allen.[22] It was featured in the final version as well as in Windows Me. The new login prompt from the final version made its first appearance in Beta 3 build 1946 (the first build of Beta 3). The new, updated icons (for My Computer, Recycle Bin etc.) first appeared in Beta 3 build 1964. The Windows 2000 boot screen in the final version first appeared in Beta 3 build 1983. Windows 2000 did not have an actual codename because, according to Dave Thompson of Windows NT team, «Jim Allchin didn’t like codenames».[23]
Windows 2000 Service Pack 1 was codenamed «Asteroid»[24] and Windows 2000 64-bit was codenamed «Janus.»[25][26] During development, there was a build for the Alpha which was abandoned in the final stages of development (between RC1 and RC2[27]) after Compaq announced they had dropped support for Windows NT on Alpha. From here, Microsoft issued three release candidates between July and November 1999, and finally released the operating system to partners on December 12, 1999, followed by manufacturing three days later on December 15.[28] The public could buy the full version of Windows 2000 on February 17, 2000. Three days before this event, which Microsoft advertised as «a standard in reliability,» a leaked memo from Microsoft reported on by Mary Jo Foley revealed that Windows 2000 had «over 63,000 potential known defects.»[29] After Foley’s article was published, she claimed that Microsoft blacklisted her for a considerable time.[30] However, Abraham Silberschatz et al. claim in their computer science textbook that «Windows 2000 was the most reliable, stable operating system Microsoft had ever shipped to that point. Much of this reliability came from maturity in the source code, extensive stress testing of the system, and automatic detection of many serious errors in drivers.»[31] InformationWeek summarized the release «our tests show the successor to NT 4.0 is everything we hoped it would be. Of course, it isn’t perfect either.»[32] Wired News later described the results of the February launch as «lackluster.»[33] Novell criticized Microsoft’s Active Directory, the new directory service architecture, as less scalable or reliable than its own Novell Directory Services (NDS) alternative.[34]
Windows 2000 is the last public release of Windows for PC-98, I486 and SGI Visual Workstation 320 and 540 as Windows XP runs solely on IA-32 only. Windows 2000 was initially planned to replace both Windows 98 and Windows NT 4.0. However, this would be changed later, as an updated version of Windows 98 called Windows 98 Second Edition was released in 1999.
On or shortly before February 12, 2004, «portions of the Microsoft Windows 2000 and Windows NT 4.0 source code were illegally made available on the Internet.»[35] The source of the leak was later traced to Mainsoft, a Windows Interface Source Environment partner.[36] Microsoft issued the following statement:
«Microsoft source code is both copyrighted and protected as a trade secret. As such, it is illegal to post it, make it available to others, download it or use it.»
Despite the warnings, the archive containing the leaked code spread widely on the file-sharing networks. On February 16, 2004, an exploit «allegedly discovered by an individual studying the leaked source code»[35] for certain versions of Microsoft Internet Explorer was reported. On April 15, 2015, GitHub took down a repository containing a copy of the Windows NT 4.0 source code that originated from the leak.[37]
Microsoft planned to release a 64-bit version of Windows 2000, which would run on 64-bit Intel Itanium microprocessors, in 2000.[38][39] However, the first officially released 64-bit version of Windows was Windows XP 64-Bit Edition, released alongside the 32-bit editions of Windows XP on October 25, 2001,[40] followed by the server versions Windows Datacenter Server Limited Edition and later Windows Advanced Server Limited Edition, which were based on the pre-release Windows Server 2003 (then known as Windows .NET Server) codebase.[41][42] These editions were released in 2002, were shortly available through the OEM channel and then were superseded by the final versions of Server 2003.[42]
New and updated features[edit]
Windows 2000 introduced many of the new features of Windows 98 and 98 SE into the NT line,[43] such as the Windows Desktop Update,[43] Internet Explorer 5 (Internet Explorer 6, which followed in 2001, is also available for Windows 2000),[43] Outlook Express, NetMeeting, FAT32 support,[44] Windows Driver Model,[45] Internet Connection Sharing,[43] Windows Media Player, WebDAV support[46] etc. Certain new features are common across all editions of Windows 2000, among them NTFS 3.0,[6] the Microsoft Management Console (MMC),[47] UDF support, the Encrypting File System (EFS),[48] Logical Disk Manager,[49] Image Color Management 2.0,[50] support for PostScript 3-based printers,[50] OpenType (.OTF) and Type 1 PostScript (.PFB) font support[50] (including a new font—Palatino Linotype—to showcase some OpenType features[51]), the Data protection API (DPAPI),[52] an LDAP/Active Directory-enabled Address Book,[53] usability enhancements and multi-language and locale support. Windows 2000 also introduced USB device class drivers for USB printers, Mass storage class devices,[54] and improved FireWire SBP-2 support for printers and scanners, along with a Safe removal applet for storage devices.[55] Windows 2000 SP4 added native USB 2.0 support. Windows 2000 is also the first Windows version to support hibernation at the operating system level (OS-controlled ACPI S4 sleep state) unlike Windows 98 which required special drivers from the hardware manufacturer or driver developer.[56]
A new capability designed to protect critical system files called Windows File Protection was introduced. This protects critical Windows system files by preventing programs other than Microsoft’s operating system update mechanisms such as the Package Installer, Windows Installer and other update components from modifying them.[57] The System File Checker utility provides users the ability to perform a manual scan of the integrity of all protected system files, and optionally repair them, either by restoring from a cache stored in a separate «DLLCACHE» directory, or from the original install media.
Microsoft recognized that a serious error (a Blue Screen of Death or stop error) could cause problems for servers that needed to be constantly running and so provided a system setting that would allow the server to automatically reboot when a stop error occurred.[58] Also included is an option to dump any of the first 64 KB of memory to disk (the smallest amount of memory that is useful for debugging purposes, also known as a minidump), a dump of only the kernel’s memory, or a dump of the entire contents of memory to disk, as well as write that this event happened to the Windows 2000 event log.[58] In order to improve performance on servers running Windows 2000, Microsoft gave administrators the choice of optimizing the operating system’s memory and processor usage patterns for background services or for applications.[59] Windows 2000 also introduced core system administration and management features as the Windows Installer,[60] Windows Management Instrumentation[61] and Event Tracing for Windows (ETW)[62] into the operating system.
Plug and Play and hardware support improvements[edit]
The most notable improvement from Windows NT 4.0 is the addition of Plug and Play with full ACPI and Windows Driver Model support. Similar to Windows 9x, Windows 2000 supports automatic recognition of installed hardware, hardware resource allocation, loading of appropriate drivers, PnP APIs and device notification events. The addition of the kernel PnP Manager along with the Power Manager are two significant subsystems added in Windows 2000.
Windows 2000 introduced version 3 print drivers (user mode printer drivers)[63] based on Unidrv, which made it easier for printer manufacturers to write device drivers for printers.[64] Generic support for 5-button mice is also included as standard [65] and installing IntelliPoint allows reassigning the programmable buttons. Windows 98 lacked generic support.[66] Driver Verifier was introduced to stress test and catch device driver bugs.[67]
Shell[edit]
Windows 2000 introduces layered windows that allow for transparency, translucency and various transition effects like shadows, gradient fills and alpha-blended GUI elements to top-level windows.[68] Menus support a new Fade transition effect.
Improvements in Windows Explorer: «Web-style» folders, media preview and customizable toolbars
The Start menu in Windows 2000 introduces personalized menus, expandable special folders and the ability to launch multiple programs without closing the menu by holding down the SHIFT key. A Re-sort button forces the entire Start Menu to be sorted by name. The Taskbar introduces support for balloon notifications which can also be used by application developers. Windows 2000 Explorer introduces customizable Windows Explorer toolbars, auto-complete in Windows Explorer address bar and Run box, advanced file type association features, displaying comments in shortcuts as tooltips, extensible columns in Details view (IColumnProvider interface), icon overlays, integrated search pane in Windows Explorer, sort by name function for menus, and Places bar in common dialogs for Open and Save.
Windows Explorer has been enhanced in several ways in Windows 2000. It is the first Windows NT release to include Active Desktop, first introduced as a part of Internet Explorer 4.0 (specifically Windows Desktop Update), and only pre-installed in Windows 98 by that time.[69] It allowed users to customize the way folders look and behave by using HTML templates, having the file extension HTT. This feature was abused by computer viruses that employed malicious scripts, Java applets, or ActiveX controls in folder template files as their infection vector. Two such viruses are VBS/Roor-C[70] and VBS.Redlof.a.[71]
The «Web-style» folders view, with the left Explorer pane displaying details for the object currently selected, is turned on by default in Windows 2000. For certain file types, such as pictures and media files, the preview is also displayed in the left pane.[72] Until the dedicated interactive preview pane appeared in Windows Vista, Windows 2000 had been the only Windows release to feature an interactive media player as the previewer for sound and video files, enabled by default. However, such a previewer can be enabled in previous versions of Windows with the Windows Desktop Update installed through the use of folder customization templates.[73] The default file tooltip displays file title, author, subject and comments;[74] this metadata may be read from a special NTFS stream, if the file is on an NTFS volume, or from an OLE structured storage stream, if the file is a structured storage document. All Microsoft Office documents since Office 4.0[75] make use of structured storage, so their metadata is displayable in the Windows 2000 Explorer default tooltip. File shortcuts can also store comments which are displayed as a tooltip when the mouse hovers over the shortcut. The shell introduces extensibility support through metadata handlers, icon overlay handlers and column handlers in Explorer Details view.[76]
The right pane of Windows 2000 Explorer, which usually just lists files and folders, can also be customized. For example, the contents of the system folders aren’t displayed by default, instead showing in the right pane a warning to the user that modifying the contents of the system folders could harm their computer. It’s possible to define additional Explorer panes by using DIV elements in folder template files.[69] This degree of customizability is new to Windows 2000; neither Windows 98 nor the Desktop Update could provide it.[77] The new DHTML-based search pane is integrated into Windows 2000 Explorer, unlike the separate search dialog found in all previous Explorer versions. The Indexing Service has also been integrated into the operating system and the search pane built into Explorer allows searching files indexed by its database.[78]
NTFS 3.0[edit]
Main article: NTFS
Microsoft released the version 3.0 of NTFS[6] (sometimes incorrectly called «NTFS 5» in relation to the kernel version number) as part of Windows 2000; this introduced disk quotas (provided by QuotaAdvisor), file-system-level encryption, sparse files and reparse points. Sparse files allow for the efficient storage of data sets that are very large yet contain many areas that only have zeros.[79] Reparse points allow the object manager to reset a file namespace lookup and let file system drivers implement changed functionality in a transparent manner.[80] Reparse points are used to implement volume mount points, junctions, Hierarchical Storage Management, Native Structured Storage and Single Instance Storage.[80] Volume mount points and directory junctions allow for a file to be transparently referred from one file or directory location to another.
Windows 2000 also introduces a Distributed Link Tracking service to ensure file shortcuts remain working even if the target is moved or renamed. The target object’s unique identifier is stored in the shortcut file on NTFS 3.0 and Windows can use the Distributed Link Tracking service for tracking the targets of shortcuts, so that the shortcut file may be silently updated if the target moves, even to another hard drive.[81]
Encrypting File System[edit]
The Encrypting File System (EFS) introduced strong file system-level encryption to Windows. It allows any folder or drive on an NTFS volume to be encrypted transparently by the user.[48] EFS works together with the EFS service, Microsoft’s CryptoAPI and the EFS File System Runtime Library (FSRTL).[82] To date, its encryption has not been compromised.[citation needed]
EFS works by encrypting a file with a bulk symmetric key (also known as the File Encryption Key, or FEK), which is used because it takes less time to encrypt and decrypt large amounts of data than if an asymmetric key cipher were used.[82] The symmetric key used to encrypt the file is then encrypted with a public key associated with the user who encrypted the file, and this encrypted data is stored in the header of the encrypted file. To decrypt the file, the file system uses the private key of the user to decrypt the symmetric key stored in the file header. It then uses the symmetric key to decrypt the file. Because this is done at the file system level, it is transparent to the user.[83]
For a user losing access to their key, support for recovery agents that can decrypt files is built into EFS. A Recovery Agent is a user who is authorized by a public key recovery certificate to decrypt files belonging to other users using a special private key. By default, local administrators are recovery agents however they can be customized using Group Policy.
Basic and dynamic disk storage[edit]
Windows 2000 introduced the Logical Disk Manager and the diskpart command line tool for dynamic storage.[8] All versions of Windows 2000 support three types of dynamic disk volumes (along with basic disks): simple volumes, spanned volumes and striped volumes:
- Simple volume, a volume with disk space from one disk.
- Spanned volumes, where up to 32 disks show up as one, increasing it in size but not enhancing performance. When one disk fails, the array is destroyed. Some data may be recoverable. This corresponds to JBOD and not to RAID-1.
- Striped volumes, also known as RAID-0, store all their data across several disks in stripes. This allows better performance because disk reads and writes are balanced across multiple disks. Like spanned volumes, when one disk in the array fails, the entire array is destroyed (some data may be recoverable).
In addition to these disk volumes, Windows 2000 Server, Windows 2000 Advanced Server, and Windows 2000 Datacenter Server support mirrored volumes and striped volumes with parity:
- Mirrored volumes, also known as RAID-1, store identical copies of their data on 2 or more identical disks (mirrored). This allows for fault tolerance; in the event one disk fails, the other disk(s) can keep the server operational until the server can be shut down for replacement of the failed disk.
- Striped volumes with parity, also known as RAID-5, functions similar to striped volumes/RAID-0, except «parity data» is written out across each of the disks in addition to the data. This allows the data to be «rebuilt» in the event a disk in the array needs replacement.
Accessibility[edit]
With Windows 2000, Microsoft introduced the Windows 9x accessibility features for people with visual and auditory impairments and other disabilities into the NT-line of operating systems.[9] These included:
- StickyKeys: makes modifier keys (
ALT,CTRLandSHIFT) become «sticky»: a user can press the modifier key, and then release it before pressing the combination key. (Activated by pressing Shift five times quickly.) - FilterKeys: a group of keyboard-related features for people with typing issues, including:
- Slow Keys: Ignore any keystroke not held down for a certain period.
- Bounce Keys: Ignore repeated keystrokes pressed in quick succession.
- Repeat Keys: lets users slow down the rate at which keys are repeated via the keyboard’s key-repeat feature.
- Toggle Keys: when turned on, Windows will play a sound when the
CAPS LOCK,NUM LOCKorSCROLL LOCKkey is pressed. - SoundSentry: designed to help users with auditory impairments, Windows 2000 shows a visual effect when a sound is played through the sound system.
- MouseKeys: lets users move the cursor around the screen via the numeric keypad.
- SerialKeys: lets Windows 2000 support speech augmentation devices.
- High contrast theme: to assist users with visual impairments.
- Microsoft Magnifier: a screen magnifier that enlarges a part of the screen the cursor is over.[84]
Additionally, Windows 2000 introduced the following new accessibility features:
- On-screen keyboard: displays a virtual keyboard on the screen and allows users to press its keys using a mouse or a joystick.[85]
- Microsoft Narrator: introduced in Windows 2000, this is a screen reader that utilizes the Speech API 4, which would later be updated to Speech API 5 in Windows XP
- Utility Manager: an application designed to start, stop, and manage when accessibility features start. This was eventually replaced by the Ease of Access Center in Windows Vista.
- Accessibility Wizard: a control panel applet that helps users set up their computer for people with disabilities.
Languages and locales[edit]
Windows 2000 introduced the Multilingual User Interface (MUI).[10] Besides English, Windows 2000 incorporates support for Arabic, Armenian, Baltic, Central European, Cyrillic, Georgian, Greek, Hebrew, Indic, Japanese, Korean, simplified Chinese, Thai, traditional Chinese, Turkic, Vietnamese and Western European languages.[86] It also has support for many different locales.[11]
Games[edit]
Windows 2000 included version 7.0 of the DirectX API, commonly used by game developers on Windows 98.[87] The last version of DirectX that was released for Windows 2000 was DirectX 9.0c (Shader Model 3.0), which shipped with Windows XP Service Pack 2. Microsoft published quarterly updates to DirectX 9.0c through the February 2010 release after which support was dropped in the June 2010 SDK. These updates contain bug fixes to the core runtime and some additional libraries such as D3DX, XAudio 2, XInput and Managed DirectX components. The majority of games written for versions of DirectX 9.0c (up to the February 2010 release) can therefore run on Windows 2000.
Windows 2000 included the same games as Windows NT 4.0 did: FreeCell, Minesweeper, Pinball, and Solitaire.[88]
System utilities[edit]
Windows 2000’s Computer Management console can perform many system tasks. This image shows a disk defragmentation in progress.
Windows 2000 introduced the Microsoft Management Console (MMC), which is used to create, save, and open administrative tools.[47] Each of these is called a console, and most allow an administrator to administer other Windows 2000 computers from one centralised computer. Each console can contain one or many specific administrative tools, called snap-ins.[47] These can be either standalone (with one function), or an extension (adding functions to an existing snap-in). In order to provide the ability to control what snap-ins can be seen in a console, the MMC allows consoles to be created in author mode or user mode.[47] Author mode allows snap-ins to be added, new windows to be created, all portions of the console tree to be displayed and consoles to be saved. User mode allows consoles to be distributed with restrictions applied. User mode consoles can grant full access to the user for any change, or they can grant limited access, preventing users from adding snapins to the console though they can view multiple windows in a console. Alternatively users can be granted limited access, preventing them from adding to the console and stopping them from viewing multiple windows in a single console.[89]
The main tools that come with Windows 2000 can be found in the Computer Management console (in Administrative Tools in the Control Panel).[90] This contains the Event Viewer—a means of seeing events and the Windows equivalent of a log file,[91] a system information utility, a backup utility, Task Scheduler and management consoles to view open shared folders and shared folder sessions, configure and manage COM+ applications, configure Group Policy,[92] manage all the local users and user groups, and a device manager.[93] It contains Disk Management and Removable Storage snap-ins,[94] a disk defragmenter as well as a performance diagnostic console, which displays graphs of system performance and configures data logs and alerts. It also contains a service configuration console, which allows users to view all installed services and to stop and start them, as well as configure what those services should do when the computer starts. CHKDSK has significant performance improvements.[95]
Windows 2000 comes with two utilities to edit the Windows registry, REGEDIT.EXE and REGEDT32.EXE.[96] REGEDIT has been directly ported from Windows 98, and therefore does not support editing registry permissions.[96] REGEDT32 has the older multiple document interface (MDI) and can edit registry permissions in the same manner that Windows NT’s REGEDT32 program could. REGEDIT has a left-side tree view of the Windows registry, lists all loaded hives and represents the three components of a value (its name, type, and data) as separate columns of a table. REGEDT32 has a left-side tree view, but each hive has its own window, so the tree displays only keys and it represents values as a list of strings. REGEDIT supports right-clicking of entries in a tree view to adjust properties and other settings. REGEDT32 requires all actions to be performed from the top menu bar. Windows XP is the first system to integrate these two programs into a single utility, adopting the REGEDIT behavior with the additional NT features.[96]
The System File Checker (SFC) also comes with Windows 2000. It is a command line utility that scans system files and verifies whether they were signed by Microsoft and works in conjunction with the Windows File Protection mechanism. It can also repopulate and repair all the files in the Dllcache folder.[97]
Recovery Console[edit]
The Recovery Console is usually used to recover unbootable systems.
The Recovery Console is run from outside the installed copy of Windows to perform maintenance tasks that can neither be run from within it nor feasibly be run from another computer or copy of Windows 2000.[98] It is usually used to recover the system from problems that cause booting to fail, which would render other tools useless, like Safe Mode or Last Known Good Configuration, or chkdsk. It includes commands like fixmbr, which are not present in MS-DOS.
It has a simple command-line interface, used to check and repair the hard drive(s), repair boot information (including NTLDR), replace corrupted system files with fresh copies from the CD, or enable/disable services and drivers for the next boot.
The console can be accessed in either of the two ways:
- Booting from the Windows 2000 CD, and choosing to start the Recovery Console from the CD itself instead of continuing with setup. The Recovery Console is accessible as long as the installation CD is available.
- Preinstalling the Recovery Console on the hard disk as a startup option in
Boot.ini, via WinNT32.exe, with the /cmdcons switch.[99] In this case, it can only be started as long as NTLDR can boot from the system partition.
Windows Scripting Host 2.0[edit]
Windows 2000 introduced Windows Script Host 2.0 which included an expanded object model and support for logon and logoff scripts.
Networking[edit]
- Starting with Windows 2000, the Server Message Block (SMB) protocol directly interfaces with TCP/IP. In Windows NT 4.0, SMB requires the NetBIOS over TCP/IP (NBT) protocol to work on a TCP/IP network.
- Windows 2000 introduces a client-side DNS caching service. When the Windows DNS resolver receives a query response, the DNS resource record is added to a cache. When it queries the same resource record name again and it is found in the cache, then the resolver does not query the DNS server. This speeds up DNS query time and reduces network traffic.
Server family features[edit]
The Windows 2000 Server family consists of Windows 2000 Server, Windows 2000 Advanced Server, Windows 2000 Small Business Server, and Windows 2000 Datacenter Server.
All editions of Windows 2000 Server have the following services and features built in:
- Routing and Remote Access Service (RRAS) support, facilitating dial-up and VPN connections using IPsec, L2TP or L2TP/IPsec, support for RADIUS authentication in Internet Authentication Service, network connection sharing, Network Address Translation, unicast and multicast routing schemes.
- Remote access security features: Remote Access Policies for setup, verify Caller ID (IP address for VPNs), callback and Remote access account lockout[100]
- Autodial by location feature using the Remote Access Auto Connection Manager service
- Extensible Authentication Protocol support in IAS (EAP-MD5 and EAP-TLS) later upgraded to PEAPv0/EAP-MSCHAPv2 and PEAP-EAP-TLS in Windows 2000 SP4
- DNS server, including support for Dynamic DNS. Active Directory relies heavily on DNS.
- IPsec support and TCP/IP filtering
- Smart card support
- Microsoft Connection Manager Administration Kit (CMAK) and Connection Point Services
- Support for distributed file systems (DFS)
- Hierarchical Storage Management support including remote storage,[101] a service that runs with NTFS and automatically transfers files that are not used for some time to less expensive storage media
- Fault tolerant volumes, namely Mirrored and RAID-5
- Group Policy (part of Active Directory)
- IntelliMirror, a collection of technologies for fine-grained management of Windows 2000 Professional clients that duplicates users’ data, applications, files, and settings in a centralized location on the network. IntelliMirror employs technologies such as Group Policy, Windows Installer, Roaming profiles, Folder Redirection, Offline Files (also known as Client Side Caching or CSC), File Replication Service (FRS), Remote Installation Services (RIS) to address desktop management scenarios such as user data management, user settings management, software installation and maintenance.
- COM+, Microsoft Transaction Server and Distributed Transaction Coordinator
- MSMQ 2.0
- TAPI 3.0
- Integrated Windows Authentication (including Kerberos, Secure channel and SPNEGO (Negotiate) SSP packages for Security Support Provider Interface (SSPI)).
- MS-CHAP v2 protocol
- Public Key Infrastructure (PKI) and Enterprise Certificate Authority support
- Terminal Services and support for the Remote Desktop Protocol (RDP)
- Internet Information Services (IIS) 5.0 and Windows Media Services 4.1
- Network quality of service features[102]
- A new Windows Time service which is an implementation of Simple Network Time Protocol (SNTP) as detailed in IETF RFC 1769. The Windows Time service synchronizes the date and time of computers in a domain[103] running on Windows 2000 Server or later. Windows 2000 Professional includes an SNTP client.
The Server editions include more features and components, including the Microsoft Distributed File System (DFS), Active Directory support and fault-tolerant storage.
Distributed File System[edit]
The Distributed File System (DFS) allows shares in multiple different locations to be logically grouped under one folder, or DFS root. When users try to access a network share off the DFS root, the user is really looking at a DFS link and the DFS server transparently redirects them to the correct file server and share. A DFS root can only exist on a Windows 2000 version that is part of the server family, and only one DFS root can exist on that server.
There can be two ways of implementing a DFS namespace on Windows 2000: either through a standalone DFS root or a domain-based DFS root. Standalone DFS allows for only DFS roots on the local computer, and thus does not use Active Directory. Domain-based DFS roots exist within Active Directory and can have their information distributed to other domain controllers within the domain – this provides fault tolerance to DFS. DFS roots that exist on a domain must be hosted on a domain controller or on a domain member server. The file and root information is replicated via the Microsoft File Replication Service (FRS).[104]
Active Directory[edit]
A new way of organizing Windows network domains, or groups of resources, called Active Directory, is introduced with Windows 2000 to replace Windows NT’s earlier domain model. Active Directory’s hierarchical nature allowed administrators a built-in way to manage user and computer policies and user accounts, and to automatically deploy programs and updates with a greater degree of scalability and centralization than provided in previous Windows versions. User information stored in Active Directory also provided a convenient phone book-like function to end users. Active Directory domains can vary from small installations with a few hundred objects, to large installations with millions. Active Directory can organise and link groups of domains into a contiguous domain name space to form trees. Groups of trees outside of the same namespace can be linked together to form forests.
Active Directory services could always be installed on a Windows 2000 Server Standard, Advanced, or Datacenter computer, and cannot be installed on a Windows 2000 Professional computer. However, Windows 2000 Professional is the first client operating system able to exploit Active Directory’s new features. As part of an organization’s migration, Windows NT clients continued to function until all clients were upgraded to Windows 2000 Professional, at which point the Active Directory domain could be switched to native mode and maximum functionality achieved.
Active Directory requires a DNS server that supports SRV resource records, or that an organization’s existing DNS infrastructure be upgraded to support this. There should be one or more domain controllers to hold the Active Directory database and provide Active Directory directory services.
Volume fault tolerance[edit]
Along with support for simple, spanned and striped volumes, the Windows 2000 Server family also supports fault-tolerant volume types. The types supported are mirrored volumes and RAID-5 volumes:
- Mirrored volumes: the volume contains several disks, and when data is written to one it is also written to the other disks. This means that if one disk fails, the data can be totally recovered from the other disk. Mirrored volumes are also known as RAID-1.
- RAID-5 volumes: a RAID-5 volume consists of multiple disks, and it uses block-level striping with parity data distributed across all member disks. Should a disk fail in the array, the parity blocks from the surviving disks are combined mathematically with the data blocks from the surviving disks to reconstruct the data on the failed drive «on-the-fly.»
Deployment[edit]
| Minimum | Recommended | |
|---|---|---|
| IA-32 PCs | ||
| CPU | Pentium 133 MHz | Pentium II 300 MHz |
| Memory | 32 MB (128 MB for Windows 2000 Server) | 128 MB (256 MB for Windows 2000 Server) |
| Free space | 1 GB (2 GB for Windows 2000 Server) | 5 GB |
| Graphics hardware | 800×600 VGA or better monitor | 1024×768 VGA or better monitor |
| Input device(s) | Keyboard and/or mouse |
Windows 2000 can be deployed to a site via various methods. It can be installed onto servers via traditional media (such as CD) or via distribution folders that reside on a shared folder. Installations can be attended or unattended. During a manual installation, the administrator must specify configuration options. Unattended installations are scripted via an answer file, or a predefined script in the form of an INI file that has all the options filled in. An answer file can be created manually or using the graphical Setup manager. The Winnt.exe or Winnt32.exe program then uses that answer file to automate the installation. Unattended installations can be performed via a bootable CD, using Microsoft Systems Management Server (SMS), via the System Preparation Tool (Sysprep), via the Winnt32.exe program using the /syspart switch or via Remote Installation Services (RIS). The ability to slipstream a service pack into the original operating system setup files is also introduced in Windows 2000.[105]
The Sysprep method is started on a standardized reference computer – though the hardware need not be similar – and it copies the required installation files from the reference computer to the target computers. The hard drive does not need to be in the target computer and may be swapped out to it at any time, with the hardware configured later. The Winnt.exe program must also be passed a /unattend switch that points to a valid answer file and a /s file that points to one or more valid installation sources.
Sysprep allows the duplication of a disk image on an existing Windows 2000 Server installation to multiple servers. This means that all applications and system configuration settings will be copied across to the new installations, and thus, the reference and target computers must have the same HALs, ACPI support, and mass storage devices – though Windows 2000 automatically detects «plug and play» devices. The primary reason for using Sysprep is to quickly deploy Windows 2000 to a site that has multiple computers with standard hardware. (If a system had different HALs, mass storage devices or ACPI support, then multiple images would need to be maintained.)
Systems Management Server can be used to upgrade multiple computers to Windows 2000. These must be running Windows NT 3.51, Windows NT 4.0, Windows 98 or Windows 95 OSR2.x along with the SMS client agent that can receive software installation operations. Using SMS allows installations over a wide area and provides centralised control over upgrades to systems.
Remote Installation Services (RIS) are a means to automatically install Windows 2000 Professional (and not Windows 2000 Server) to a local computer over a network from a central server. Images do not have to support specific hardware configurations and the security settings can be configured after the computer reboots as the service generates a new unique security ID (SID) for the machine. This is required so that local accounts are given the right identifier and do not clash with other Windows 2000 Professional computers on a network.[106]
RIS requires that client computers are able to boot over the network via either a network interface card that has a Pre-Boot Execution Environment (PXE) boot ROM installed or that the client computer has a network card installed that is supported by the remote boot disk generator. The remote computer must also meet the Net PC specification. The server that RIS runs on must be Windows 2000 Server and it must be able to access a network DNS Service, a DHCP service and the Active Directory services.[107]
Editions[edit]
Microsoft released various editions of Windows 2000 for different markets and business needs: Professional, Server, Advanced Server and Datacenter Server. Each was packaged separately.
Windows 2000 Professional was designed as the desktop operating system for businesses and power users. It is the client version of Windows 2000. It offers greater security and stability than many of the previous Windows desktop operating systems. It supports up to two processors, and can address up to 4 GB of RAM. The system requirements are a Pentium processor (or equivalent) of 133 MHz or greater, at least 32 MB of RAM, 650 MB of hard drive space, and a CD-ROM drive (recommended: Pentium II, 128 MB of RAM, 2 GB of hard drive space, and CD-ROM drive).[108] However, despite the official minimum processor requirements, it is still possible to install Windows 2000 on 4th-generation x86 CPUs such as the 80486.
Screenshot of Windows 2000 Server with Configure Your Server component.
Windows 2000 Server shares the same user interface with Windows 2000 Professional, but contains additional components for the computer to perform server roles and run infrastructure and application software. A significant new component introduced in the server versions is Active Directory, which is an enterprise-wide directory service based on LDAP (Lightweight Directory Access Protocol). Additionally, Microsoft integrated Kerberos network authentication, replacing the often-criticised NTLM (NT LAN Manager) authentication system used in previous versions. This also provided a purely transitive-trust relationship between Windows 2000 Server domains in a forest (a collection of one or more Windows 2000 domains that share a common schema, configuration, and global catalog, being linked with two-way transitive trusts). Furthermore, Windows 2000 introduced a Domain Name Server which allows dynamic registration of IP addresses. Windows 2000 Server supports up to 4 processors and 4 GB of RAM, with a minimum requirement of 128 MB of RAM and 1 GB hard disk space, however requirements may be higher depending on installed components.[108]
Windows 2000 Advanced Server is a variant of Windows 2000 Server operating system designed for medium-to-large businesses. It offers the ability to create clusters of servers, support for up to 8 CPUs, a main memory amount of up to 8 GB on Physical Address Extension (PAE) systems and the ability to do 8-way SMP. It supports TCP/IP load balancing and builds on Microsoft Cluster Server (MSCS) in Windows NT Enterprise Server 4.0, adding enhanced functionality for two-node clusters.[109] System requirements are similar to those of Windows 2000 Server,[108] however they may need to be higher to scale to larger infrastructure.
Screenshot of Windows 2000 Datacenter Server, asking the user to complete setup by configuring Cluster and Remote Installation service in the Configure Your Server component.
Windows 2000 Datacenter Server is a variant of Windows 2000 Server designed for large businesses that move large quantities of confidential or sensitive data frequently via a central server.[110] Like Advanced Server, it supports clustering, failover and load balancing. Its minimum system requirements are similar to those of Advanced Server,[108] but it was designed to be capable of handing advanced, fault-tolerant and scalable hardware—for instance computers with up to 32 CPUs and 32 GBs RAM, with rigorous system testing and qualification, hardware partitioning, coordinated maintenance and change control. Windows 2000 Datacenter Server was released to manufacturing on August 11, 2000[111] and launched on September 26, 2000.[112] This edition was based on Windows 2000 with Service Pack 1[110] and was not available at retail.[113]
Service packs[edit]
| Service pack | Release date |
|---|---|
| Service Pack 1 (SP1) | August 15, 2000 |
| Service Pack 2 (SP2) | May 16, 2001 |
| Service Pack 3 (SP3) | August 29, 2002 |
| Service Pack 4 (SP4) | June 26, 2003 |
| SP4 Update Rollup | September 13, 2005 |
Windows 2000 has received four full service packs and one rollup update package following SP4, which is the last service pack. Microsoft phased out all development of its Java Virtual Machine (JVM) from Windows 2000 in SP3. Internet Explorer 5.01 has also been upgraded to the corresponding service pack level.
Service Pack 4 with Update Rollup was released on September 13, 2005, nearly four years following the release of Windows XP and sixteen months prior to the release of Windows Vista.
Microsoft had originally intended to release a fifth service pack for Windows 2000, but Microsoft cancelled this project early in its development, and instead released Update Rollup 1 for SP4, a collection of all the security-related hotfixes and some other significant issues.[114] The Update Rollup does not include all non-security related hotfixes and is not subjected to the same extensive regression testing as a full service pack. Microsoft states that this update will meet customers’ needs better than a whole new service pack, and will still help Windows 2000 customers secure their PCs, reduce support costs, and support existing computer hardware.[115]
Upgradeability[edit]
Several Windows 2000 components are upgradable to latest versions, which include new versions introduced in later versions of Windows, and other major Microsoft applications are available. These latest versions for Windows 2000 include:
- ActiveSync 4.5
- DirectX 9.0c (5 February 2010 Redistributable)
- Internet Explorer 6 SP1 and Outlook Express 6 SP1
- Microsoft Agent 2.0
- Microsoft Data Access Components 2.81
- Microsoft NetMeeting 3.01 and Microsoft Office 2003 on Windows 2000 SP3 and SP4 (and Microsoft Office XP on Windows 2000 versions below SP3.)
- MSN Messenger 7.0 (Windows Messenger)
- MSXML 6.0 SP2
- .NET Framework 2.0 SP2
- Tweak UI 1.33
- Visual C++ 2008
- Visual Studio 2005
- Windows Desktop Search 2.66
- Windows Script Host 5.7
- Windows Installer 3.1
- Windows Media Format Runtime and Windows Media Player 9 Series (including Windows Media Encoder 7.1 and the Windows Media 8 Encoding Utility)
Security[edit]
During the Windows 2000 period, the nature of attacks on Windows servers changed: more attacks came from remote sources via the Internet. This has led to an overwhelming number of malicious programs exploiting the IIS services – specifically a notorious buffer overflow tendency.[116] This tendency is not operating-system-version specific, but rather configuration-specific: it depends on the services that are enabled.[116] Following this, a common complaint is that «by default, Windows 2000 installations contain numerous potential security problems. Many unneeded services are installed and enabled, and there is no active local security policy.»[117] In addition to insecure defaults, according to the SANS Institute, the most common flaws discovered are remotely exploitable buffer overflow vulnerabilities.[118] Other criticized flaws include the use of vulnerable encryption techniques.[119]
Code Red and Code Red II were famous (and much discussed) worms that exploited vulnerabilities of the Windows Indexing Service of Windows 2000’s Internet Information Services (IIS).[16] In August 2003, security researchers estimated that two major worms called Sobig and Blaster infected more than half a million Microsoft Windows computers.[120] The 2005 Zotob worm was blamed for security compromises on Windows 2000 machines at ABC, CNN, the New York Times Company, and the United States Department of Homeland Security.[121]
On September 8, 2009, Microsoft skipped patching two of the five security flaws that were addressed in the monthly security update, saying that patching one of the critical security flaws was «infeasible.»[122] According to Microsoft Security Bulletin MS09-048: «The architecture to properly support TCP/IP protection does not exist on Microsoft Windows 2000 systems, making it infeasible to build the fix for Microsoft Windows 2000 Service Pack 4 to eliminate the vulnerability. To do so would require re-architecting a very significant amount of the Microsoft Windows 2000 Service Pack 4 operating system, there would be no assurance that applications designed to run on Microsoft Windows 2000 Service Pack 4 would continue to operate on the updated system.» No patches for this flaw were released for the newer Windows XP (32-bit) and Windows XP Professional x64 Edition either, despite both also being affected;[123] Microsoft suggested turning on Windows Firewall in those versions.[124]
Support lifecycle[edit]
Windows 2000 and Windows 2000 Server were superseded by newer Microsoft operating systems: Windows 2000 Server products by Windows Server 2003, and Windows 2000 Professional by Windows XP Professional.
The Windows 2000 family of operating systems moved from mainstream support to the extended support phase on June 30, 2005. Microsoft says that this marks the progression of Windows 2000 through the Windows lifecycle policy. Under mainstream support, Microsoft freely provides design changes if any, service packs and non-security related updates in addition to security updates, whereas in extended support, service packs are not provided and non-security updates require contacting the support personnel by e-mail or phone. Under the extended support phase, Microsoft continued to provide critical security updates every month for all components of Windows 2000 (including Internet Explorer 5.0 SP4) and paid per-incident support for technical issues. Because of Windows 2000’s age, updated versions of components such as Windows Media Player 11 and Internet Explorer 7 have not been released for it. In the case of Internet Explorer, Microsoft said in 2005 that, «some of the security work in IE 7 relies on operating system functionality in XP SP2 that is non-trivial to port back to Windows 2000.»[125]
While users of Windows 2000 Professional and Server were eligible to purchase the upgrade license for Windows Vista Business or Windows Server 2008, neither of these operating systems can directly perform an upgrade installation from Windows 2000; a clean installation must be performed instead or a two-step upgrade through XP/2003. Microsoft has dropped the upgrade path from Windows 2000 (and earlier) to Windows 7. Users of Windows 2000 must buy a full Windows 7 license.
Although Windows 2000 is the last NT-based version of Microsoft Windows which does not include product activation, Microsoft has introduced Windows Genuine Advantage for certain downloads and non-critical updates from the Download Center for Windows 2000.
Windows 2000 reached the end of its lifecycle on July 13, 2010 (alongside Service Pack 2 of Windows XP). It will not receive new security updates and new security-related hotfixes after this date.[5][126] In Japan, over 130,000 servers and 500,000 PCs in local governments were affected; many local governments said that they will not update as they do not have funds to cover a replacement.[127]
As of 2011, Windows Update still supports the Windows 2000 updates available on Patch Tuesday in July 2010, e.g., if older optional Windows 2000 features are enabled later. Microsoft Office products under Windows 2000 have their own product lifecycles. While Internet Explorer 6 for Windows XP did receive security patches up until it lost support, this is not the case for IE6 under Windows 2000. The Windows Malicious Software Removal Tool installed monthly by Windows Update for XP and later versions can be still downloaded manually for Windows 2000.[128]
Microsoft in 2020 announced that it would disable the Windows Update service for SHA-1 endpoints and since Windows 2000 did not get an update for SHA-2, Windows Update Services are no longer available on the OS as of late July 2020.[129] However, as of April 2021, the old updates for Windows 2000 are still available on the Microsoft Update Catalog.[130]
Total cost of ownership[edit]
In October 2002, Microsoft commissioned IDC to determine the total cost of ownership (TCO) for enterprise applications on Windows 2000 versus the TCO of the same applications on Linux. IDC’s report is based on telephone interviews of IT executives and managers of 104 North American companies in which they determined what they were using for a specific workload for file, print, security and networking services.
IDC determined that the four areas where Windows 2000 had a better TCO than Linux – over a period of five years for an average organization of 100 employees – were file, print, network infrastructure and security infrastructure. They determined, however, that Linux had a better TCO than Windows 2000 for web serving. The report also found that the greatest cost was not in the procurement of software and hardware, but in staffing costs and downtime. While the report applied a 40% productivity factor during IT infrastructure downtime, recognizing that employees are not entirely unproductive, it did not consider the impact of downtime on the profitability of the business. The report stated that Linux servers had less unplanned downtime than Windows 2000 servers. It found that most Linux servers ran less workload per server than Windows 2000 servers and also that none of the businesses interviewed used 4-way SMP Linux computers. The report also did not take into account specific application servers – servers that need low maintenance and are provided by a specific vendor. The report did emphasize that TCO was only one factor in considering whether to use a particular IT platform, and also noted that as management and server software improved and became better packaged the overall picture shown could change.[131]
See also[edit]
- Architecture of Windows NT
- BlueKeep (security vulnerability)
- Comparison of operating systems
- DEC Multia, one of the DEC Alpha computers capable of running Windows 2000 beta
- Microsoft Servers, Microsoft’s network server software brand
- Windows Neptune, a cancelled consumer edition based on Windows 2000
References[edit]
- ^ «Microsoft Shared Source Initiative Overview». Microsoft. March 2003. Archived from the original on April 2, 2003. Retrieved February 17, 2017.
- ^ a b «Microsoft Releases Windows 2000 to Manufacturing». News Center. Microsoft. December 15, 1999. Archived from the original on June 4, 2019. Retrieved February 14, 2017.
- ^ «Gates Ushers in Next Generation of PC Computing With Launch of Windows 2000». News Center. Microsoft. February 17, 2000. Archived from the original on October 3, 2019. Retrieved February 17, 2018.
- ^ «Update Rollup 1 for Windows 2000 SP4 and known issues». Microsoft. Archived from the original on March 2, 2017. Retrieved February 17, 2017.
- ^ a b c «Microsoft Product Lifecycle for Windows 2000 family». Support. Microsoft. Archived from the original on April 7, 2013. Retrieved February 17, 2017.
- ^ a b c «New Capabilities and Features of the NTFS 3.0 File System». Microsoft Support. Microsoft. Archived from the original on October 24, 2007. Retrieved February 14, 2017.
- ^ «Implementing the Encrypting File System in Windows 2000». TechNet. Microsoft. March 24, 2009. Archived from the original on August 26, 2017. Retrieved February 14, 2017.
- ^ a b «Disk Management». TechNet. Microsoft. Archived from the original on December 22, 2016. Retrieved February 14, 2017.
- ^ a b «Windows 2000 Professional Accessibility Features». Microsoft. Archived from the original on December 17, 2003. Retrieved February 14, 2017.
- ^ a b «Frequently Asked Questions: Windows Server 2003, Windows XP, and Windows 2000 MUI». MSDN. Microsoft. Archived from the original on February 18, 2017. Retrieved February 17, 2017.
- ^ a b «Windows 2000 — List of Locale IDs and Language Groups». Global Development and Computing Portal. Microsoft. Archived from the original on February 3, 2003. Retrieved February 14, 2017.
- ^ «Windows 2000 Server Family». TechNet. Microsoft. Archived from the original on December 22, 2016. Retrieved February 17, 2017.
- ^ «Microsoft Renames Windows NT 5.0 Product Line to Windows 2000; Signals Evolution of Windows NT Technology Into Mainstream». News Center. Microsoft. October 27, 1998. Archived from the original on January 12, 2009. Retrieved February 14, 2017.
- ^ «Microsoft Announces Final Packaging for Windows 2000». News Center. Microsoft. August 17, 1999. Archived from the original on May 8, 2014. Retrieved February 14, 2017.
- ^ «Microsoft and CyberSafe Extend Windows 2000 Security Across the Enterprise». News Center. Microsoft. January 17, 2000. Archived from the original on February 18, 2017. Retrieved February 17, 2017.
- ^ a b «‘Code Red’ Worm Exploiting Buffer Overflow in IIS Indexing Service DLL». CERT Coordination Center. Software Engineering Institute. July 19, 2001. Archived from the original on August 17, 2016. Retrieved May 17, 2019.
- ^ Swartz, Jon (September 25, 2001). «Nimba called most serious Net attack on business». USA Today. Gannett Company. Archived from the original on February 17, 2017. Retrieved February 17, 2017.
- ^ Veitch, Martin (March 20, 1997). «NT 5.0 to ship in first half 1998 — Gates». ZDNet.
- ^ a b Thurrott, Paul (December 15, 1999). «Road to Gold: A Look at the Development of Windows 2000». Supersite for Windows. Penton. Archived from the original on August 21, 2017. Retrieved April 17, 2019.
- ^ . HPCWire. June 6, 1997 https://www.hpcwire.com/1997/06/06/bill-gates-speaks-about-1998-release-of-nt-5-0/.
- ^ Trott, Bob (October 27, 1998). «It’s official: NT 5.0 becomes Windows 2000». InfoWorld. Archived from the original on March 2, 2005. Retrieved April 22, 2006.
- ^ Fran Board (April 27, 2022). «Ta-da! It’s Windows!». 20k.org (Podcast). Twenty Thousand Hertz. Retrieved December 7, 2022.
- ^ Thurrott, Paul (August 8, 2013). «SuperSite Flashback: NT’s First Decade». Supersite for Windows. Penton. Archived from the original on August 1, 2017. Retrieved August 10, 2013.
- ^ «Windows 2000 service pack nearing release». Zdnetasia.com. January 27, 2000. Archived from the original on May 29, 2012. Retrieved November 13, 2011.
- ^ Thurrott, Paul (July 27, 1999). «64-bit Windows 2000 on track for mid-2000». Windows IT Pro. Archived from the original on May 29, 2012.
- ^ «Windows 2000 to Launch at Comdex, 64-Bit Janus in the Wings». Findarticles.com. August 26, 1999. Archived from the original on July 18, 2010. Retrieved November 13, 2011.
- ^ «RC1 was the build 2072 from June 1999 (and last public Alpha/2000 build), the last known internal build was 2128 and the «Gold» release of Windows 2000 was build 2195″. Alphant.com. Archived from the original on November 30, 2011.
- ^ «Windows 2000 history». ActiveWin. Archived from the original on May 20, 2006. Retrieved April 22, 2006.
- ^ Foley, Mary Jo (February 14, 2000). «Bugfest! Win2000 has 63,000 ‘defects’«. ZDNet. Archived from the original on January 13, 2007. Retrieved July 29, 2014.
- ^ McLaws, Robert (September 20, 2006). «Mary Jo Foley: The Exit Interview». WindowsNow. Archived from the original on January 13, 2015. Retrieved July 26, 2014.
- ^ John Wiley & Sons (2010). Operating System Concepts with Java, 8th Edition, page 901.
- ^ «Special Report — Windows 2000 Review: Say Hello to Win2000». InformationWeek. November 6, 2003. Archived from the original on December 8, 2015. Retrieved April 17, 2019.
- ^ Heilemann, John. «The Truth, The Whole Truth, and Nothing But The Truth». Wired. Archived from the original on July 24, 2008. Retrieved April 17, 2019.
- ^ «NDS eDirectory vs. Microsoft Active Directory?». Novell. November 17, 1999. Archived from the original on February 11, 2005. Retrieved April 22, 2006.
NDS eDirectory is a cross-platform directory solution that works on NT 4.0, Windows 2000 when available, Solaris and NetWare 5. Active Directory will only support the Windows 2000 environment. In addition, eDirectory users can be assured they are using the most trusted, reliable and mature directory service to manage and control their e-business relationships – not a 1.0 release.
- ^ a b «Statement from Microsoft Regarding Illegal Posting of Windows 2000 Source Code». Microsoft. February 20, 2004. Archived from the original on August 5, 2011. Retrieved January 11, 2007.
- ^ «Mainsoft Eyed as Windows Source Code Leak». internetnews.co. February 13, 2004. Archived from the original on March 9, 2021. Retrieved July 3, 2009.
- ^ Van der Saar, Ernesto (April 15, 2015). «Microsoft Takes Pirated Windows NT 4.0 Source Code Offline». TorrentFreak. Archived from the original on November 8, 2020. Retrieved March 28, 2021.
- ^ «Microsoft and Intel Announce Preview Release of 64-Bit Windows for Intel Itanium Processor» (Press release). Microsoft. July 12, 2000. Archived from the original on October 24, 2007. Retrieved October 4, 2007.
- ^ «64-Bit Windows Overview». Microsoft. October 7, 1999. Archived from the original on March 1, 2000. Retrieved July 23, 2014.
- ^ «Microsoft Unveils Plans for 64-Bit Windows Platform — Stories». News.microsoft.com. May 23, 2001. Archived from the original on October 31, 2019. Retrieved February 15, 2020.
- ^ Bekker, Scott (March 5, 2002). «Datacenter Server Limited Edition Released». Redmond Magazine. Archived from the original on August 12, 2014. Retrieved July 23, 2014.
Although Microsoft has pushed back the schedule for Windows .NET Server, the company is going ahead with the release of a limited edition of Windows Datacenter Server based on Windows .NET Server beta code.
- ^ a b «Introducing Windows Advanced Server, Limited Edition». Microsoft. Archived from the original on October 22, 2002. Retrieved January 12, 2013.
- ^ a b c d «Introducing Windows 2000 Professional». Microsoft.com. Archived from the original on March 20, 2007. Retrieved November 13, 2011.
- ^ Description of the FAT32 File System Archived May 8, 2008, at the Wayback Machine,
- ^ «Windows Driver Model (WDM)». Microsoft.com. April 15, 2002. Archived from the original on December 22, 2010. Retrieved November 13, 2011.
- ^ «Overview of Web Folders in Internet Explorer 5». Support.microsoft.com. March 29, 2007. Archived from the original on January 5, 2012. Retrieved November 13, 2011.
- ^ a b c d «Microsoft Management Console – Overview». Technet.microsoft.com. Archived from the original on November 22, 2011. Retrieved November 13, 2011.
- ^ a b «Implementing the Encrypting File System in Windows 2000». Microsoft.com. Archived from the original on July 23, 2008. Retrieved November 13, 2011.
- ^ «Disk Management». Microsoft.com. Archived from the original on January 12, 2009. Retrieved November 13, 2011.
- ^ a b c «Windows 2000 To Include New On-Screen And Printed Scalable Color Solution». Findarticles.com. September 6, 1999. Archived from the original on February 23, 2006. Retrieved November 13, 2011.
- ^ «MSDN Blogs». msdn.com. Microsoft. Archived from the original on August 9, 2014. Retrieved August 8, 2014.
- ^ «How to troubleshoot the Data Protection API (DPAPI)». Support.microsoft.com. December 3, 2007. Archived from the original on October 5, 2011. Retrieved November 13, 2011.
- ^ «How to Configure the Address Book to Query Users Contained in Active Directory». Support.microsoft.com. January 24, 2007. Archived from the original on October 20, 2011. Retrieved November 13, 2011.
- ^ «USB FAQ: Introductory level». Microsoft.com. August 25, 2008. Archived from the original on December 25, 2010. Retrieved November 13, 2011.
- ^ «IEEE 1394 and the Windows platform». Msdn.microsoft.com. December 14, 2001. Archived from the original on November 8, 2011. Retrieved November 13, 2011.
- ^ «Windows and Power Management». Microsoft.com. January 1, 2002. Archived from the original on July 13, 2004. Retrieved November 13, 2011.
- ^ «Microsoft KB article 222193: Description of the Windows File Protection Feature». Archived from the original on August 21, 2006. Retrieved September 17, 2006.
- ^ a b «How to configure system failure and recovery options in Windows». Support.microsoft.com. May 23, 2006. Archived from the original on November 16, 2011. Retrieved November 13, 2011.
- ^ «Analyzing processor activity: Windows 2000 Professional Resource Kit». Microsoft.com. Archived from the original on April 17, 2008. Retrieved November 13, 2011.
- ^ «Using Windows Installer in Windows 2000 beta 3». Entmag.com. October 7, 2011. Archived from the original on January 14, 2009. Retrieved November 13, 2011.
- ^ «Programming with Windows Management Instrumentation». Informit.com. October 4, 2000. Archived from the original on January 3, 2013. Retrieved November 13, 2011.
- ^ «Event Tracing for Windows (ETW): MSDN». Msdn.microsoft.com. Archived from the original on December 2, 2011. Retrieved November 13, 2011.
- ^ «Choosing User Mode or Kernel Mode». Msdn.microsoft.com. Archived from the original on October 6, 2012. Retrieved November 13, 2011.
- ^ «Microsoft Universal Printer Driver — Windows drivers». docs.microsoft.com. Archived from the original on November 11, 2020. Retrieved September 13, 2020.
- ^ «Keyboard and mouse HID client drivers». microsoft.com. Microsoft. Archived from the original on March 14, 2013. Retrieved July 4, 2013.
- ^ «Fourth and Fifth Mouse Buttons Not Recognized by Windows». microsoft.com. Microsoft. Archived from the original on November 26, 2012. Retrieved July 4, 2013.
- ^ Driver Verifier at MSDN Archived April 24, 2012, at the Wayback Machine. Microsoft.
- ^ «Layered Windows: MSDN». Msdn.microsoft.com. Archived from the original on November 26, 2011. Retrieved November 13, 2011.
- ^ a b Esposito, Dino (June 2000). «More Windows 2000 UI Goodies: Extending Explorer Views by Customizing Hypertext Template Files». MSDN Magazine. Archived from the original on August 24, 2007. Retrieved August 26, 2007.
- ^ Sophos, VBS/Roor-C threat analysis Archived November 30, 2007, at the Wayback Machine. Retrieved August 26, 2007.
- ^ «Virus.VBS.Redlof.a». Viruslist.com. January 15, 2004. Archived from the original on October 28, 2007. Retrieved August 26, 2007.
- ^ «Managing Files, Folders, and Search Methods: Microsoft TechNet». Microsoft.com. Archived from the original on January 12, 2009. Retrieved November 13, 2011.
- ^ «How to Enable Preview for Multimedia Files». Microsoft. January 31, 2000. Archived from the original on November 17, 2012. Retrieved March 29, 2012.
- ^ «Windows 2000 Registry: Latest Features and APIs Provide the Power to Customize and Extend Your Apps». MSDN Magazine. November 2000. Archived from the original on April 15, 2003. Retrieved August 26, 2007.
- ^ Kindel, Charlie (August 27, 1993). «OLE Property Sets Exposed». MSDN Magazine. Retrieved August 26, 2007. [dead link]
- ^ «Windows 2000 UI Innovations: MSDN Magazine». Msdn.microsoft.com. Archived from the original on June 5, 2009. Retrieved November 13, 2011.
- ^ «Figure 1 Windows Shell Extensions». MSDN Magazine. June 2000. Archived from the original on August 31, 2004. Retrieved August 26, 2007.
- ^ «What is Indexing Service?: MSDN». Msdn.microsoft.com. Archived from the original on January 1, 2011. Retrieved November 13, 2011.
- ^ «Sparse Files Use Quota Equal to Total Allocated Length». Support.microsoft.com. February 26, 2007. Archived from the original on November 16, 2012. Retrieved November 13, 2011.
- ^ a b «Improved NTFS File System». Microsoft.com. Archived from the original on April 16, 2008. Retrieved November 13, 2011.
- ^ «Distributed Link Tracking and Object Identifiers (Windows)». TechNet. Microsoft. October 16, 2012. Archived from the original on October 23, 2012. Retrieved November 27, 2012.
- ^ a b «How Encrypting File System Works». Technet2.microsoft.com. July 19, 2011. Archived from the original on May 22, 2007. Retrieved November 13, 2011.
- ^ «Encrypting File System Archived January 12, 2009, at the Wayback Machine.» Microsoft.
- ^ «A review of Microsoft Magnifier and Narrator». Archived from the original on October 23, 2007.
- ^ «Accessibility Technology & Tools | Microsoft Accessibility». Accessibility. Archived from the original on September 6, 2009.
- ^ «List of languages supported in Windows 2000, Windows XP, and Windows Server 2003». Support. Microsoft. Archived from the original on March 2, 2017. Retrieved February 17, 2017.
- ^ Ask the Windows 2000 Dev Team Archived March 11, 2007, at the Wayback Machine
- ^ Ford, Jerry Lee, Jr (2000). Upgrading to Microsoft Windows 2000 Professional: A Migration Guide for Windows 98 and Windows NT Users. iUniverse.com. Lincoln, NE: iUniverse. p. 90. ISBN 0595148042. Archived from the original on April 2, 2021. Retrieved January 8, 2013.
- ^ Microsoft Press (2000). MCSE 70–210, Microsoft Windows 2000 Professional, pages 58–63.
- ^ «Managing Microsoft Windows 2000 Workstations and Servers». Technet.microsoft.com. Archived from the original on November 27, 2011. Retrieved November 13, 2011.
- ^ «Event Logging and Viewing». Technet.microsoft.com. Archived from the original on November 27, 2011. Retrieved November 13, 2011.
- ^ «Step-by-Step Guide to Understanding the Group Policy Feature Set». Technet.microsoft.com. Archived from the original on November 20, 2011. Retrieved November 13, 2011.
- ^ «Description of Device Manager in Windows 2000 and Windows XP». Support.microsoft.com. May 7, 2007. Archived from the original on October 23, 2011. Retrieved November 13, 2011.
- ^ «Windows 2000: Removable Storage and Backup». Microsoft.com. Archived from the original on April 17, 2008. Retrieved November 13, 2011.
- ^ «Windows 2000 Chkdsk Management». Microsoft. Archived from the original on November 4, 2012. Retrieved November 13, 2011.
- ^ a b c «Differences between Regedit.exe and Regedt32.exe». Support.microsoft.com. January 19, 2007. Archived from the original on November 20, 2011. Retrieved November 13, 2011.
- ^ «Microsoft KB article 222471: Description of the Windows 2000 System File Checker (Sfc.exe)». Archived from the original on September 1, 2006. Retrieved September 17, 2006.
- ^ «Description of the Windows 2000 Recovery Console». Support.microsoft.com. February 26, 2007. Archived from the original on November 4, 2011. Retrieved November 13, 2011.
- ^ «How to install the Windows Recovery Console». Support.microsoft.com. October 26, 2007. Archived from the original on November 16, 2011. Retrieved November 13, 2011.
- ^ «Elements of Secure Remote Access». Technet.microsoft.com. Archived from the original on December 18, 2011. Retrieved November 13, 2011.
- ^ «How to use Remote Storage in Windows 2000 Server». Support.microsoft.com. October 30, 2006. Archived from the original on January 10, 2012. Retrieved November 13, 2011.
- ^ «An Overview of Windows 2000 Quality of Service». Technet.microsoft.com. Archived from the original on December 3, 2011. Retrieved November 13, 2011.
- ^ «Basic Operation of the Windows Time Service». Support.microsoft.com. October 26, 2007. Archived from the original on November 2, 2011. Retrieved November 13, 2011.
- ^ «Microsoft KB article 812487: Overview of DFS in Windows 2000». Archived from the original on February 14, 2007. Retrieved September 17, 2006.
- ^ «Make deployment easier in Windows 2000». Microsoft.com. Archived from the original on June 15, 2007. Retrieved November 13, 2011.
- ^ Mark Minasi. Installing Windows 2000 on Workstations with Remote Installation Services.
- ^ Microsoft Press (2000). MCSE 70–210, Microsoft Windows 2000 Professional, pages 543–551.
- ^ a b c d «System requirements for Microsoft Windows 2000 operating systems». Archived from the original on April 16, 2008. Retrieved May 23, 2008.
- ^ Microsoft. Windows 2000 Resource Kit, Chap. 1, «Introducing Windows 2000 Deployment Planning.»
- ^ a b «The Datacenter Program and Windows 2000 Datacenter Server Product». Support.microsoft.com. February 28, 2007. Archived from the original on November 3, 2011. Retrieved November 13, 2011.
- ^ «Microsoft Ships Windows 2000 Datacenter Server to Program Partners». Microsoft.com. August 11, 2000. Archived from the original on March 24, 2014. Retrieved January 9, 2013.
- ^ «Microsoft Windows Datacenter Program — All Systems Go». Microsoft.com. Archived from the original on March 24, 2014. Retrieved January 9, 2013.
- ^ «Microsoft Announces Datacenter Program for Windows 2000». Microsoft.com. February 15, 2000. Archived from the original on March 24, 2014. Retrieved January 9, 2013.
- ^ Naraine, Ryan (November 26, 2004). «Microsoft Scraps Plans for Windows 2000 SP5». Archived from the original on August 26, 2011. Retrieved May 30, 2009.
- ^ «Windows 2000 Update Rollup 1 for Service Pack 4». Microsoft. Archived from the original on January 13, 2006. Retrieved September 27, 2006.
- ^ a b «Worms Wreak Havoc». ECommerce-Guide. August 19, 2003. Archived from the original on March 1, 2005. Retrieved May 17, 2019.
- ^ «Articles — Network Security Resources — GovernmentSecurity.org». Network Security Resources.[permanent dead link]
- ^ «SANS Institute». Archived from the original on September 19, 2006. Retrieved September 17, 2006.
- ^ McCullagh, Declan (May 16, 2000). «Critics Blast MS Security». Wired News. Archived from the original on July 24, 2008. Retrieved February 25, 2010.
- ^ «SoBig worm not slowing down yet». CNN Money. Time Warner. August 21, 2003. Archived from the original on May 17, 2019. Retrieved May 17, 2019.
- ^ Poulsen, Kevin (April 12, 2006). «Border Security System Left Open». Wired. Condé Nast. Archived from the original on February 17, 2017. Retrieved February 17, 2017.
- ^ Techworld Archived April 26, 2014, at the Wayback Machine, September 9, 2009, «Microsoft: Windows 2000 too old to update»
- ^ «microsoft.com». Microsoft. Archived from the original on August 4, 2011. Retrieved November 13, 2011.
- ^ Keizer, Gregg (September 14, 2009). «Microsoft: No TCP/IP patches for you, XP». Computerworld. Archived from the original on May 17, 2019. Retrieved May 17, 2019.
- ^ Marson, Ingrid (June 3, 2005). «Windows 2000 users to miss out on IE 7». CNET. CBS Interactive. Archived from the original on May 17, 2019. Retrieved May 17, 2019.
- ^ «Windows 2000 Transitions to Extended Support June 30, 2005». Microsoft. June 28, 2005. Archived from the original on June 30, 2005. Retrieved February 17, 2017.
- ^ «Windows 2000 still in use locally». The Japan Times. The Japan Times, Ltd. August 20, 2010. Archived from the original on September 10, 2016. Retrieved February 17, 2017.
- ^ «Malicious Software Removal Tool». n (KB890830). Microsoft. 2011. Archived from the original on June 21, 2012. Retrieved July 24, 2011.
- ^ «Windows Update SHA-1 based endpoints discontinued for older Windows devices». support.microsoft.com. Retrieved April 6, 2021.
- ^ «Microsoft Update Catalog». www.catalog.update.microsoft.com. Retrieved April 6, 2021.
- ^ «Windows 2000 Versus Linux in Enterprise Computing Archived April 10, 2008, at the Wayback Machine,» IDC.
Further reading[edit]
- Bolosky, William J.; Corbin, Scott; Goebel, David; & Douceur, John R. «Single Instance Storage in Windows 2000.» Microsoft Research & Balder Technology Group, Inc. (white paper).
- Bozman, Jean; Gillen, Al; Kolodgy, Charles; Kusnetzky, Dan; Perry, Randy; & Shiang, David (October 2002). «Windows 2000 Versus Linux in Enterprise Computing: An assessment of business value for selected workloads.» IDC, sponsored by Microsoft Corporation. White paper.
- Finnel, Lynn (2000). MCSE Exam 70–215, Microsoft Windows 2000 Server. Microsoft Press. ISBN 1-57231-903-8.
- Microsoft. Running Nonnative Applications in Windows 2000 Professional[permanent dead link]. Windows 2000 Resource Kit. Retrieved May 4, 2005.
- Microsoft. «Active Directory Data Storage.» Retrieved May 9, 2005.
- Minasi, Mark (1999). Installing Windows 2000 of Mastering Windows 2000 Server. Sybex. Chapter 3 – Installing Windows 2000 On Workstations with Remote Installation Services.
- Russinovich, Mark (October 1997). «Inside NT’s Object Manager.» Windows IT Pro.
- Russinovich, Mark (2002). «Inside Win2K NTFS, Part 1.» Windows IT Pro (formerly Windows 2000 Magazine).
- Saville, John (January 9, 2000). «What is Native Structure Storage?.» Windows IT Pro (formerly Windows 2000 Magazine).
- Siyan, Kanajit S. (2000). «Windows 2000 Professional Reference.» New Riders. ISBN 0-7357-0952-1.
- Solomon, David; & Russinovich, Mark E. (2000). Inside Microsoft Windows 2000 (Third Edition). Microsoft Press. ISBN 0-7356-1021-5.
- Tanenbaum, Andrew S. (2001), Modern Operating Systems (2nd Edition), Prentice-Hall
- Trott, Bob (October 27, 1998). «It’s official: NT 5.0 becomes Windows 2000.» InfoWorld.
- Wallace, Rick (2000). MCSE Exam 70–210, Microsoft Windows 2000 Professional. Microsoft Press. ISBN 1-57231-901-1.
External links[edit]
- Windows 2000 End-of-Life
- Windows 2000 Service Pack 4
- Windows 2000 Update Rollup 1 Version 2
- Минимальные
- Рекомендуемые
Минимальные системные требования Windows 2000 Professional
- Разрядность: x86 (32-bit)
- ЦП [CPU]: Pentium 133 MHz
- Видеоадаптер [GPU]: Встроенная или дискретная
- Винчестер [HDD]: 1 Gb
- Оперативная память [RAM]: 32 Mb
- Аудиокарта [AUDIO]: Любая
- Контроллер: Клавиатура, Мышь
- Интернет: Может понадобиться для некоторых задач
- DirectX: —
- Разрешение экрана: VGA 640×480
- Дополнительно: DVD/CD привод
Есть поддержка 2 процессоров и оперативки до 4 Gb
Системные требования Windows 2000 Server
- Разрядность: x86 (32-bit)
- ЦП [CPU]: Pentium III, Pentium IV
- Видеоадаптер [GPU]: Любая
- Винчестер [HDD]: 1 Gb
- Оперативная память [RAM]: 128 Mb
- Аудиокарта [AUDIO]: Любая
- Контроллер: Клавиатура, Мышь Microsoft Mouse
- Интернет: Широкополосное соединение
- Дополнительно: DVD/CD привод или USB
Появилась поддержка 4 процессоров.
Чтобы ОС Виндовс 2000 нормально работала вашем персональном компьютере, минимальные характеристики его должны соответствовать примерно следующим условиям: CPU должен иметь 32 (x86) разрядность и тактовую частоту не ниже 133 МГц. «Оперативки» нормальным объемом будет наличие 128 Мб, это даст возможность работать за компьютером. Свободное пространство вашего HDD необходимо хотя-бы 1 Гб.
|
Параметр |
Windows |
Windows |
Windows |
Windows |
|
Максимальное |
2 |
4 |
8 |
32 |
|
Максимальный |
4 |
4 |
8 |
64 |
|
Минимальные |
133 |
133 |
133 |
Н/д |
|
Дополнительные |
Кластеры |
Кластеры |
||
|
Цена, |
319 |
999 |
3999 |
Н/д |
Обе
старшие версии сервера поддерживают
два типа кластеризации (объединения),
которые возможны технологически. Когда
серверы (называемые узлами) объединяются,
каждый из них присоединяется к общему
устройству хранения, и они работают
вместе, как единая система, для обеспечения
уверенной работы важных (критических)
приложений. Если один из узлов выйдет
из строя, то приложение останется
доступным, так как оставшийся узел будет
продолжать обслуживать запросы. Для
Network Load Balancing (NLB) – распределения нагрузки
на сеть, может быть создан кластер,
который будет обслуживать запросы
клиентов, распределяя их среди нескольких
систем, предоставляющих доступ к одному
приложению. Например, у вас может быть
32 сервера, которые снабжены одинаковыми
копиями вашего web-сайта и тогда NLB будет
распределять запросы среди всех этих
серверов, входящих в NLB кластер, увеличивая
производительность, доступность и
надежность.
Windows
2000 Server содержит целый ряд существенных
преимуществ перед Windows NT 4.0. Большинство
из них ориентированы на высокоуровневые
серверы и сети (т. е. сегмент рынка, в
котором по-прежнему превалирует Unix),
однако многие современные промышленные
технологии теперь стали доступными
даже для небольших организаций. Достаточно
лишь вникнуть в новые возможности
(Active Directory, терминальные службы) и оценить
все «за» и «против».
Серверы
MS Windows способны
после запуска и конфигурирования
соответствующих служб или доустановки
соответствующих компонент выполнять
функции не только файловых серверов
или серверов печати, но и серверов RAS
(RRAS – Routing
and Remote Access Server– сервер
удаленного доступа), контроллера домена
(сервера аутентификации), сервера DNS,
WINS, DHCP, IIS
(Internet Information Server -Web сервер),
ISA
сервера (Internet
Security and Acceleration сервер
— межсетевой защитный экран и Proxy
сервер),
SQL
– сервера, терминального сервера, Multi
Protocol Router’а (многопротокольный
маршрутизатор)
и т.д. Каталогизация объектов в сети на
базе серверов Microsoft,
начиная с Windows
2000 обеспечивается
за счет использования Active Directory (AD).
Введение
в концепцию Active Directory
Одним из наиболее
значимых изменений, по сравнению с
Windows NT 4, является включение в Windows 2000
важной новой службы – Active Directory. Active
Directory – это «родная» служба каталогов
для Windows 2000. В NT 4 домен был очень похож
на удаленный остров, с которым можно
было соединиться только используя
механизм доверительных отношений.
Active Directory – полнофункциональная служба
каталогов. Служба каталогов – это
соединение каталога и служб, которые
помогают с этим каталогом работать.
Упрощая, можно сказать, что каталог
хранит информацию, подобно любому
другому каталогу, например, телефонному
справочнику. Каталог может хранить
различную информацию, относящуюся к
пользователям, группам, компьютерам,
принтерам, общим ресурсам и так далее
– будем называть все это объектами.
Каталог хранит также информацию о самом
объекте, или его свойства – будем
называть этоатрибутами. Например,
атрибутами, хранимыми в каталоге о
пользователе, может быть имя его
руководителя, номер телефона, адрес,
имя для входа в систему, пароль, группы,
в которые он входит и многое другое. Для
того, чтобы сделать директорию полезной
для нас, должны существовать службы,
которые будут взаимодействовать с
директорией. Например, можно использовать
директорию, как хранилище информации,
по которой можно аутентифицировать
пользователя, или как место, куда можно
послать запрос для того, чтобы найти
информацию об объекте. Например, можно
запросить директорию показать все
цветные принтеры в офисе в Уфе, номер
телефона Иванова из офиса в Стерлитамаке
или список всех пользовательских учетных
записей, чье имя начинается на «Г». В
Windows 2000 Active Directory отвечает не только за
создание и организацию этих небольших
объектов, но также и за большие объекты,
такие как домены, OU (организационные
единицы) и сайты. Для того, чтобы понять,
что же есть Active Directory на самом деле, нужно
рассмотреть еще несколько связанных с
ней концепций.
Именование
Объектов
Active Directory использует
Lightweight Directory Access Protocol (LDAP) – простой
протокол доступа к каталогам, как главный
протокол доступа. LDAP действует поверх
TCP/IP и определяет способы обращения и
доступа к объектам между клиентом и
сервером Active Directory. В LDAP каждый объект
имеет свое особенное Distinguished Name
(отличительное имя), и это имя отличает
его от других объектов Active Directory, а также
подсказывает нам, где данный объект
расположен. Два главных составных части
отличительного имени – это CN (common name) –
общее имя и DC (domain component) – доменная
составляющая. Общее имя определяет
объект или контейнер, в котором этот
объект находится, в то время как доменный
компонент определяет домен, в котором
объект находится. Например, отличительное
имя может быть следующим:
CN=Dan
DiNicolo, CN=Users, DC=win2000trainer, DC=com
В
этом примере есть пользователь Dan
DiNicolo, который находится внутри контейнера,
называемого Users, в домене win2000trainer, который
является поддоменом .com. Отличительное
имя объекта должно быть уникальным
внутри леса Active Directory.
В
то время как отличительное имя дает нам
полную информацию о расположении
объекта, relative distinguished name (относительное
отличительное имя) определяет объект
внутри его родительского контейнера.
Например, если осуществляется поиск
внутри контейнера Users, относительное
отличительное имя объекта, который
ищется, может быть Dan DiNicolo.
Когда
пользователь входит в домен, расположенный
в Active Directory, у него может быть два типа
имени. Первое из них – традиционное
NetBIOS -имя. В Windows 2000 на него ссылаются как
на downlevel logon name (имя регистрации в ранних
версиях Windows). Этот тип имени существует
для совместимости с ранними версиями
Windows, процесс входа в которые был основан
на использовании имен NetBIOS (такие OS как
NT 4, Windows 9x и так далее). Когда вы используете
downlevel logon name (на вкладке свойств –«имя
входа пользователя пред-Windows 2000») для
входа, пользователь должен ввести имя
пользователя, пароль и выбрать
соответствующий домен, в который он
собирается входить. Второе имя – и это
новинка в Windows 2000 – это возможность
входа в систему с использованием того,
что называется User Principal Name (основное имя
пользователя) или UPN. Основное имя
пользователя имеет следующий формат –
user@domain.com (на вкладке свойств пользователя
это называется – User logon name (имя входа
пользователя)). Если это соглашение
действует, то пользователю не нужно
определять домен, в который он хочет
войти. Фактически, когда для входа в
Windows 2000используется UPN, доменная часть
окна имени для входа в систему закрашена
серым. Пример этих двух типов имен
показан на вкладке свойств учетной
записи пользователя Active Directory:
Различают как
логические, так и физические элементы
Active Directory. Логическая часть Active Directory
включает в себя такие понятия как лес,
деревья, домены и OU. Физическая часть
Active Directory связана с такими понятиями,
как сайты и контроллеры доменов.
Логическая
структура Active Directory
Логическая
структура Active Directory зависит от нужд
вашей организации. Логические элементы
Active Directory это леса, деревья, домены и OU.
Домены
Домен
в Windows 2000 очень напоминает домен в Windows
NT. Для различных намерений и целей, домен
является логической группой пользователей
и компьютеров (объектов), которые связаны
как единица для администрирования и
репликации. Прежде всего домен –это
административная единица. Следовательно,
администратор этого домена может его
администрировать и для этого не нужен
никто другой. Кроме того, все контроллеры
одного домена должны осуществлять
репликацию друг с другом. Мы ссылаемся
на это как на топологию репликации. В
Windows 2000 домены именуются в соответствии
с соглашением об именовании DNS, а не
именовании NetBIOS. Примером имени домена
в Active Directory может быть 2000trainers.com. В Windows
NT имели ограничения по величине, до
которой они могли увеличиваться и этот
размер ограничивался допустимым размером
базы данных SAM (40 Мб или около того).
Поэтому приходилось создавать множества
доменов в компании, в которой действовали
тысячи пользователей и компьютеров.
Теперь же множество доменов не являются
необходимостью в подобном сценарии под
Windows 2000, так как Active Directory может вместить
в себя многие миллионы объектов. Учетные
записи пользователей в Windows 2000 существуют
так же как и в Windows NT. Active Directory также
позволяет вам иметь множество доменов,
формируя структуры, которые называются
деревьями и лесами, о чем я и расскажу
ниже.
Дерево
В
Windows 2000, несколько доменов может все же
потребоваться, особенно в больших
организациях, которые продолжают
требовать надежного контроля над их
средой, их индивидуальностью (как в
случае различных организационных единиц
для ведения бизнеса) и особого
административного контроля. В Active
Directory набор доменов может создаваться
в порядке, напоминающем структуру
дерева. В этом случае «дочерний» домен
наследует свое имя от «родительского»
домена. Например, можно создать отдельные
домены для отделов компании, расположенных
в Европе и Азии. В этом случае, можно
остановиться на структуре, изображенной
ниже:
К
домен в дереве является отдельной и
явно выраженной административной
единицей, так же как и границей для целей
репликации. То есть, если вы создали
учетную запись пользователя в домене
asia.win2000trainer.com, то эта учетная запись,
существующая на контроллере домена,
будет реплицирована на все контроллеры
домена asia.win2000trainer.com. Каждый новый
«дочерний» домен имеет transitive (транзитивные)
двунаправленные доверительные отношения
с «родительским» доменом. Это достигается
автоматически в Active Directory и позволяет
пользователям из одного домена дерева
иметь доступ к ресурсам в другом. Даже
не имея прямых доверительных отношений,
пользователи в Азии могут получать
доступ к ресурсам (для чего у них должны
быть соответствующие разрешения) в
Европе и наоборот, к тому же доверительные
отношения транзитивны (Азия доверяет
своему «родительскому» домену, который
в свою очередь «доверяет» Европе –
таким образом Азия доверяет Европе и
наоборот). Дерево, в общих чертах, можно
определить как набор доменов, которые
связаны отношениями «дочерний»/«родительский»
и поддерживают связанное пространство
имен.
Лес
Лес
– это термин, применяемый для описания
совокупности Active Directory деревьев. Каждое
дерево в лесе имеет собственное отдельное
пространство имен. Например, давайте
предположим, что ваша компания владеет
еще одной более мелкой, называемой Acme
Plumbing. Если я хочу, чтобы Acme Plumbing имел
свое собственное отдельное пространство
имен, я могу достичь этого объединив
деревья и сформировать лес, как показано
ниже:
Д
acmeplunbing.com является частью леса, так же
как и win2000trainer.com, но по-прежнему остается
доменом и может иметь собственное
дерево. Заметьте, что здесь существуют
транзитивные доверительные отношения
между «корневыми» доменами каждого
дерева в лесу – это позволит пользователям
домена acmeplunbing.com получать доступ к
ресурсам в дереве win2000trainer.com и наоборот,
в то же время поддерживает проверку
подлинности в собственном домене.
Заметьте, что первый домен, созданный
в лесу, рассматривается как «корень»
леса. Одна из самых важных особенностей
леса – это то, что каждый отдельный
домен поддерживает общую схему –
определения для различных объектов и
связанных с ними атрибутов, которые
созданы в лесу. Важно осознать, что лес
может быть создан из одного дерева,
которое содержит всего один домен. Это
будет маленький лес, но формально это
будет лес!
OU
– организационные единицы
Организационные
единицы (обычно называемые OU) – это
контейнеры внутри Active Directory которые
создаются для объединения объектов в
целях делегирования административных
прав и применения групповых политик в
домене. OU могут быть созданы для
организации объектов несколькими
путями, в соответствии с их функциями,
местоположением, ресурсами и так далее.
Примером объектов, которые могут быть
объединены в OU могут служить учетные
записи пользователей, компьютеров,
групп и т.д. Диаграмма, приведенная ниже
показывает пример OU, основанной на
местоположении пользователей и ресурсов:

может содержать только объекты из того
домена, в котором они расположены.
Структура OU может широко варьироваться
от компании к компании. Она разрабатывается
с целью облегчить администрирование
ресурсов и применения групповых политик.
В то время как полный административный
контроль может быть дан (делегирован)
пользователю через OU, для больших
организаций становиться возможным
иметь только один домен, в котором каждая
структура будет имеет собственный
контроль только над своей OU.
Физическая
структура
Физическая
структура Active Directory связана с двумя
главными типами объектов – сайтами и
контроллерами доменов.
Сайты
В
отличии от NT 4, в Windows 2000 Active Directory
предусматривает концепцию физического
местоположения внутри структуры. В
Active Directory сайт – это совокупность
подсетей TCP/IP, между которыми существует
высокоскоростное соединение. Хотя
«высокоскоростное» — это относительное
понятие, обычно под этим подразумевается
соединение на скоростях, соответствующих
LAN – соединениям. Вы определяете сайт
в Active Directory для контроля репликации,
аутентификации и местоположения служб.
Как только сайт будет создан, компьютеры
клиентов будут пытаться аутентифицироваться
на контроллере домена, который находится
на данном сайте, вместо того, чтобы
посылать запросы по WAN (глобальной сети).
Сайты также позволяют контролировать,
когда репликация может происходить
между контроллерами доменов. Например,
в NT 4, все BDC получают данные от PDC в
процессе репликации, используя 5-минутный
интервал уведомления об изменениях.
Так как в NT не было предусмотрено простого
пути для контроля репликации между
физическими местоположениями (это можно
сделать, используя специальные скрипты
для регистра), трафик репликации может
перегрузить линии и снизить
производительность сети. Если же вы
определите сайт в Active Directory, вы можете
также определить время и дни, в которые
репликация между сайтами должна
происходить, как часто она должна
происходить, и преимущественные пути
для ее прохождения. Вы должны заметить,
однако, что по умолчанию существует
только один сайт, и пока вы не создадите
другие, репликация будет происходить,
как и раньше, каждый 5-минутный интервал
уведомления об изменениях. Также важно
отметить, что сайты – это другой элемент,
который позволяет большим компаниям
иметь только один домен. Так как не
существует соотношения между логической
и физической структурой Active Directory, вы
можете иметь один домен и сотню сайтов.
Возможность контролировать трафик
репликации – одно из наибольших
преимуществ управляемости Active Directory.
Контроллеры
доменов
Конечно,
не может быть домена без по крайней мере
одного контроллера домена, ведь где-то
же должна храниться база данных Active
Directory. В отличие от Windows NT, где была только
одна копия базы, позволяющая делать
запись (хранящаяся на PDC; копии, хранящиеся
на BDC имели атрибут «только для чтения»),
в Windows 2000 каждый контроллер домена имеет
копию базы данных Active Directory, в которую
можно производить запись. Поэтому все
контроллеры домена в среде Active Directory
достаточно равноправны. Однако, это
усложняет картину, так как теперь каждый
контроллер домена может делать записи
в базу данных. Как и в NT 4, у вас должно
быть как минимум два контроллера в
домене для целей избыточности, а, как
правило, и гораздо больше, в зависимости
от размера организации.
С
контроллера домена в Windows 2000 производится
запуском Installation Wizard (мастер установки
Active Directory) –dcpromo.exe. Этот инструмент
не только позволяет создавать новые
контроллеры домена, но и также новые
домены, деревья и леса. Он позволяет
также понижать контроллер домена до
рядового сервера, если вы того желаете.
Когда вы запускаетеdcpromo.exe,вам
предоставляется выбор, показанный ниже:
После того, как
контроллер домена создан, он хранит
копию базы данных Active Directory (ntds.dit) и
может проводить аутентификацию
пользователей домена. База данных Active
Directory состоит из того, что принято
называть тремя разделами, как показано
на рисунке ниже:

«домен» реплицируется между контроллерами
только внутри одного домена, в то время
как разделы «конфигурация» и «схема»
реплицируются в каждый из доменов,
расположенных в лесу.
Некоторые
из контроллеров домена отличаются от
других специальными ролями, которые
они выполняют. Коротко остановимся на
каждой из этих ролей:
Global
Catalog Server(сервер Глобального Каталога)
– сервер Глобального Каталога – это
контроллер домена, который знает о
каждом единичном объекте, который
существует в Active Directory, в каждом из
доменов. Однако, он сохраняет только
часть атрибутов каждого объекта, которые
считаются наиболее важными. По умолчанию
только один контроллер домена во всем
лесу выполняет эту роль – первый
контроллер домена, созданный в лесу.
Большее число серверов Глобального
Каталога может (и должно) быть создано
в лесу. Когда контроллер домена действует
как сервер Глобального Каталога он
хранит четвертый раздел, как часть базы
данных Active Directory – раздел Глобального
Каталога.
Помимо
роли сервера Глобального Каталога,
контроллеры домена могут выполнять еще
пять специальных ролей, называемых
Operations Masters (основные контроллеры
операций). Они перечислены ниже:
Schema Master(хозяин
схемы) – в лесу только один контроллер
домена может выполнять эту роль. Schema
Master поддерживает схему Active Directory и
поддерживает копию схемы, доступную
для записи. По умолчанию первый контроллер
домена, созданный в корневом домене
леса, выполняет эту роль.
Domain Naming Master
(Хозяин именования доменов) – этот
контроллер домена отслеживает домены,
которые создаются и удаляются из леса,
поддерживая целостность структуры
леса, если какие-либо изменения имеют
место. В лесу существует только один
Domain Naming Master и, по умолчанию, эту роль
выполняет первый контроллер, созданный
в корневом домене леса.
PDC Emulator(хозяин
PDC) – эта роль существует по паре причин,
одна из которых – обратная совместимость
с NT 4 контроллерами. Когда домен повышается
до Windows 2000, первая система, которая
подвергается модернизации – это PDC
(главный контроллер домена), и этот новый
контроллер домена Windows 2000 эмулирует
(имитирует) старый PDC для оставшихся BDC
(резервных контроллеров домена),
работающих под Windows NT. PDC Emulator отслеживает
изменения паролей и выступает «арбитром»
перед тем, как пароль может быть отвергнут
системой. По умолчанию клиенты предыдущих
Windows OS, таких как Windows 9x и NT продолжают
изменять свои пароли на PDC Emulator (до тех
пор, пока на систему не будет установлен
клиент Active Directory). Один контроллер в
каждом домене выполняет роль PDC Emulator,
по умолчанию, это первый контроллер
созданный в домене.
Relative Identifier (RID)
Master(Хозяин RID (relative identificator)) – в NT 4,
PDC отвечает за создание всех SID (security
identificator), то есть отвечает за создание
всех объектов безопасности («пользователь»,
«группа», «компьютер»). В Windows 2000 каждый
контроллер домена может создавать
объекты безопасности. На самом деле SID
состоит из двух частей — SID (который
определяет домен) и RID (который определяет
уникальный объект внутри домена). Для
того, чтобы быть уверенным, что SID
уникален, один контроллер в каждом
домене выполняет роль RID Master, отвечающего
за создание доменного пула RID, и размещения
этих RID на других контроллерах в домене.
Это позволяет быть уверенным, что не
произойдет дублирования объектов SID. В
каждом домене Active Directory действует один
RID Master, по умолчанию, это первый контроллер,
созданный в домене.
Infrastructure Master(Хозяин инфраструктуры) — Infrastructure Master
отслеживает информацию о том, какие
пользователи (из других доменов) являются
членами той или иной группы данного
домена и все изменения, которые имеют
место. Это позволяет быть уверенным в
непротиворечивости участия пользователей
в группах в Active Directory. Каждый домен в
Active Directory имеет одного Infrastructure Master, по
умолчанию, это первый контроллер,
созданный в домене.