В этой статье мы покажем, как настроить сервер централизованной аутентификации, авторизации и аккаунтинга (RADIUS) на операционной системе Windows Server 2016, а также как настроить Radius-аутентификацию на Cisco устройствах с помощью службы Политики сети и доступа (Network Policy Server).
RADIUS (англ. Remote Authentication in Dial-In User Service) — протокол для реализации аутентификации, авторизации и сбора сведений об использованных ресурсах, разработанный для передачи сведений между центральным севером и различными сетевым оборудованием и клиентами.
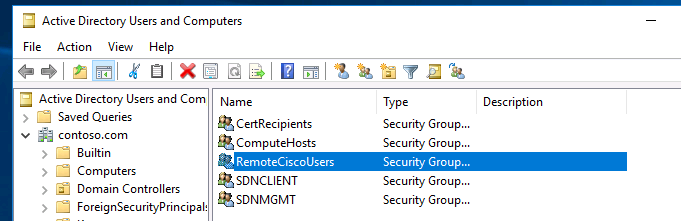
В первую очередь создайте в домене Active Directory группу безопасности AllowRemoteCiscoUsers, в которую нужно добавить пользователей, которым будет разрешена аутентификации на маршрутизаторах и коммутаторах Cisco.
Далее нужно установить на сервере, с помощью которого будет выполнятся аутентификация клиентов и назначаться права доступа, роль RADIUS сервера. Для этого на сервере Windows Server 2016 откройте оснастку Server Manager и вызовите мастер добавления ролей — Add Roles and features.
В открывшемся мастере на шаге выбора ролей отметьте роль Network Policy and Access Services. На шаге выбора служб роли в нашей ситуации достаточно будет выбрать только службу Network Policy Server.
Протокол Remote Authentication Dial In User Service (RADIUS) в Windows Server 2016 включен в состав роли Network Policy Server.
В консоли Server Manager выберите меню Tools и откройте консоль Network Policy Server (nps.msc).
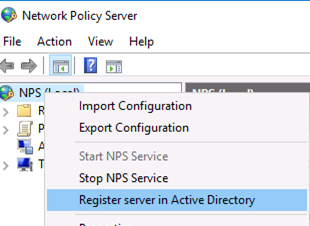
Для полноценного использования NPS-сервера в домене необходимо зарегистрировать его в домене Active Directory. В оснастке на NPS, щелкните ПКМ по вашему NPS узлу и выберите Register server in Active Directory.
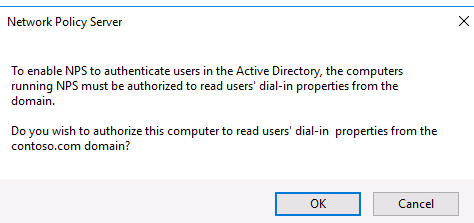
Подтвердите регистрацию сервера в Active Directory:
При этом мы должны предоставите серверу полномочия на чтение свойств учётных записей пользователей, касающихся удалённого доступа. Сервер при этом будет добавлен во встроенную доменную группу RAS and IAS Servers.
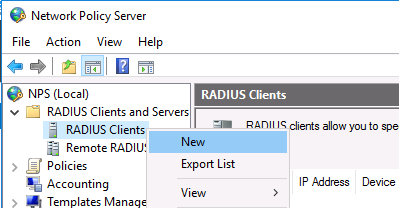
Теперь можно добавить клиента Radius. Для этого в дереве консоли NPS разверните раздел RADIUS Clients and Servers и на элементе RADIUS Clients выберите пункт New.
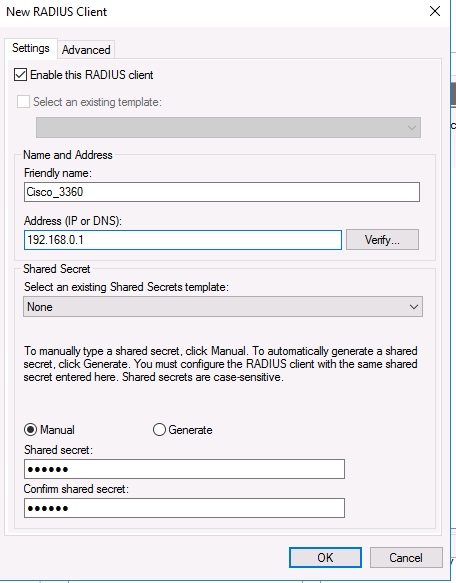
На вкладке Settings заполните поля Friendly name, Client address (можно указать IP адрес или DNS имя подключающегося сетевого устройства) и пароль — Shared Secret + Confirm shared (этот пароль вы будете использовать в настройках коммутатора или маршрутизатора Cisco для установления доверительных отношений с Radius сервером).
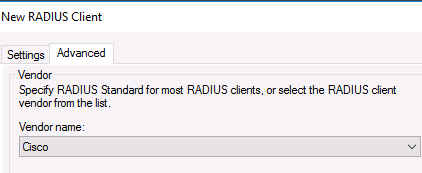
Во вкладке Advanced выберите в поле Vendor name — Cisco.
Теперь нужно создать политики доступа на сервере RADIUS. С помощью политик доступа мы свяжем клиента Radius и доменную группу пользователей.
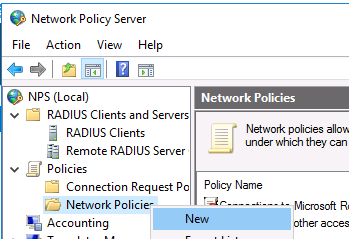
Раскройте ветку Policies —> Network Policies, и выберите пункт меню New:
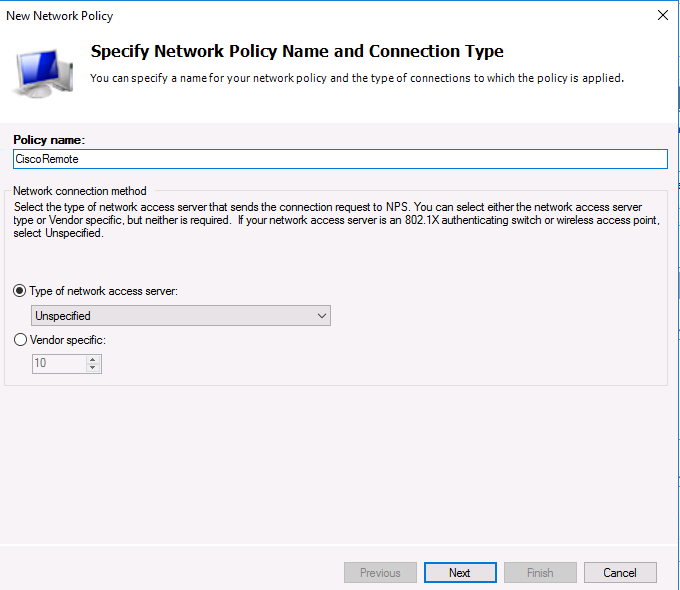
Укажите Имя политики (Policy name). Тип сервера доступа к сети (Type of network access server) оставьте без изменения (Unspecified):
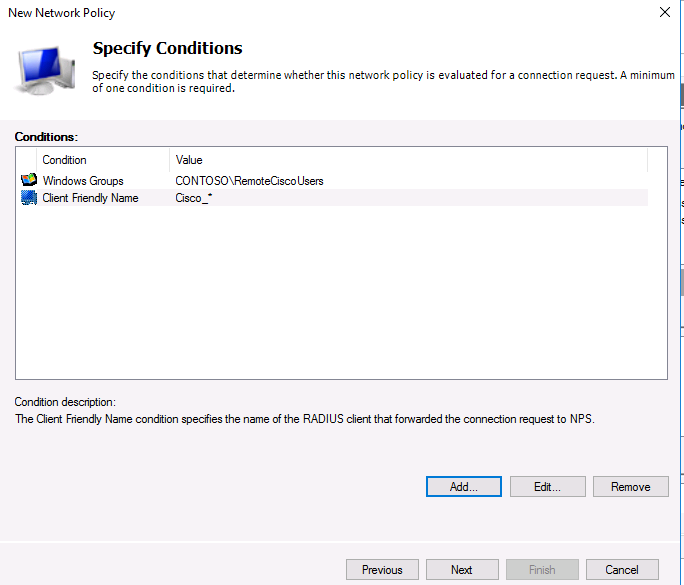
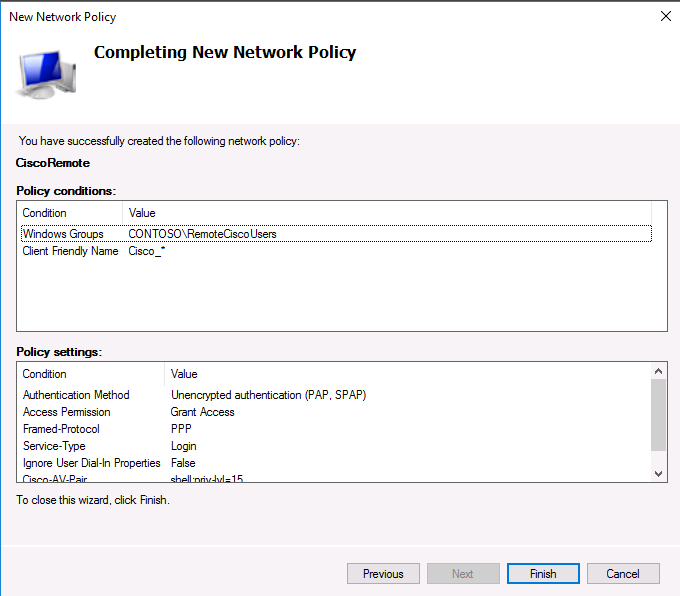
На следующем шаге Specify conditions нам нужно добавить условия, при которых будет применяться данная политика RADIUS. Добавим два условия: вы хотите, что для успешной авторизации пользователь входил в определенную доменную группу безопасности, и устройство, к которому осуществляется доступ, имело определённое имя. С помощью кнопки Add добавим сначала условие, выбрав тип Windows Group (добавьте группу RemoteCiscoUsers) и укажите Client Friendly Name (Cisco_*).
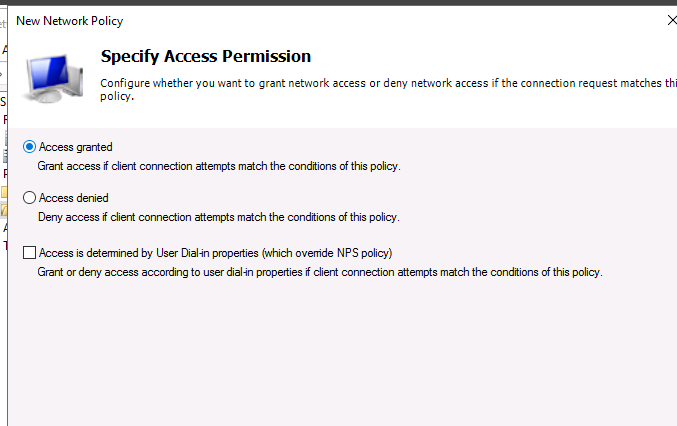
На следующем выберите значение Доступ разрешен (Access Granted).
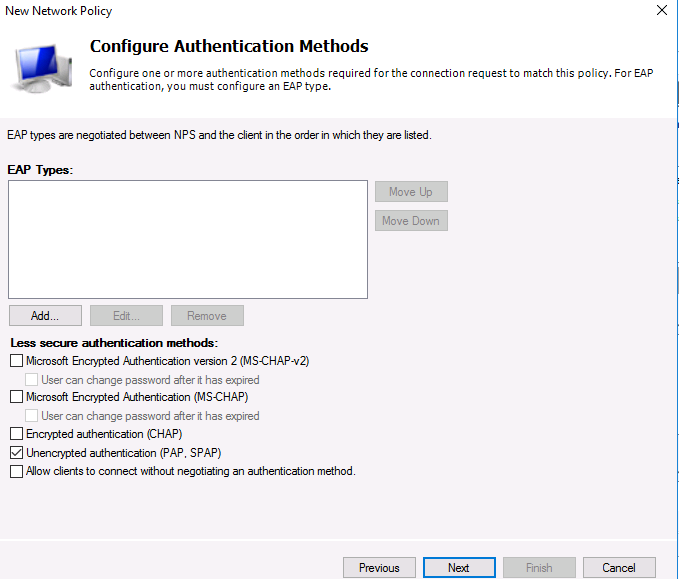
Т.к. наш коммутатор Cisco поддерживает только метод аутентификации Unencrypted authentication (PAP, SPAP), снимите все остальные флажки.
Следующий шаг настройки ограничений (Constraints) мы пропустим.
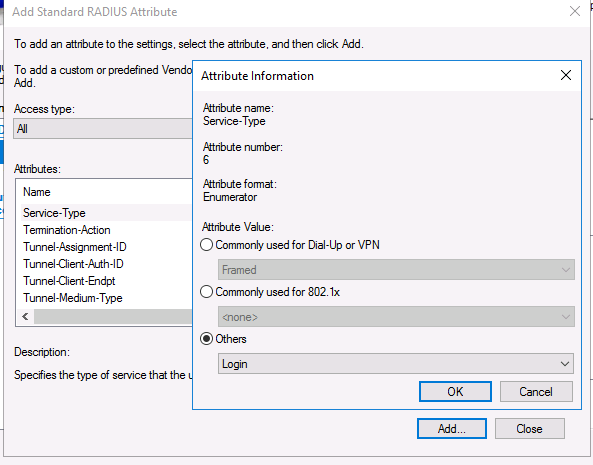
В разделе Configure Settings перейдите секцию RADIUS Attributes -> Standard. Удалите имеющиеся там атрибуты и нажмите кнопку Add.
Выберите Access type -> All, затем Service-Type->Add. Укажите Others=Login.
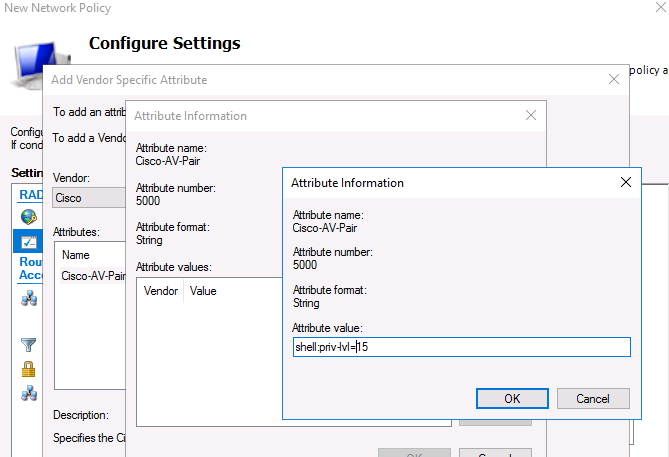
Теперь в секции RADIUS Attributes -> Vendor Specific добавьте новый атрибут. В пункте Vendor, найдите Cisco и нажмите Add. Здесь нужно добавить сведения об атрибуте. Нажмите Add и укажите следующее значение атрибута:
shell: priv-lvl = 15
На последнем экране будут указаны все созданные вами настройки политики NPS. Нажмите Finish:
При создании и планировании политик обратите внимание на то, что имеет значение их порядок. Политики обрабатываются сверху вниз, и все условия очередной политике соблюдены, эта политика применяется к клиенту, а дальнейшая обработка других политик прекращается. То есть с точки зрения безопасности и разрешения конфликтов между политиками правильнее будет располагать политики в порядке возрастания административных полномочий.
После создания политики, можно переходить к настройке маршрутизаторов и коммутаторов Cisco для аутентификации на сервере Radius NPS.
AAA работает таким образом, что, если не получен ответ от сервера, клиент предполагает, что аутентификация не выполнена. Чтобы не потерять доступ к своим сетевым устройствам, которые вы переключаете на авторизацию на Radius сервера, обязательно создайте локальных пользователей на случай если RADIUS сервер станет недоступен по какой-либо причине.
Ниже пример конфигурации для авторизации на Radius (NPS) сервере для коммутатора Cisco Catalyst:
aaa new-model
aaa authentication login default group radius local
aaa authorization exec default group radius if-authenticated
radius-server host 192.168.1.16 key R@diu$pa$$
service password-encryption
На этом минимальная настройка коммутатора закончена и можно испытать новый механизм аутентификации и авторизации в действии.
Наконец «Долгая дорога в дюнах» закончилась, и мы пришли к корпоративному управляемому Wi-fi решению. В начале думали про решение Cisco или Aruba, но к сожалению текущий бюджет никак не располагает к решениям подобного плана. В итоге, в ходе долгих поисков истины и раздумий, решили остановиться на решении Ubnt (отдельно благодарю Александра за нужные советы). Конечно, это не одного поля ягоды с решением Cisco или Aruba, но в текущей ситуации, что есть, то есть.
Как говорил мой командир: «На пожаре и Х… водопровод» (да простят меня за мой русский).
Итак, решение выбрано, задача настроить корпоративный внутренний и гостевой сегменты Wi-fi с авторизацией на Radius сервере.
VPN сервер уже готов, осталось настроить RADIUS, сегодня как раз об этом. На первый взгляд, развернуть и настроить RADIUS сервер, не такая уж сложная задача, но немного загнались с сертификатом, пришлось «поплясать с бубном», ну об этом далее по порядку.
Для начала необходимо запросить сертификат с Центра сертификации, центр сертификации у нас уже есть, поэтому его установку в этом посте я пропущу.
MMC-Файл-Добавить или удалить оснастку-Добавляем Сертификаты-Учетной записи компьютера-Локальным компьютером.
Находим наш центр сертификации
Запрашиваем сертификат (*.p12), сохраняем его на диск, далее устанавливаем его в Личные сертификаты на будущий радиус сервер
Далее добавляем роль самого RADIUS сервера
Далее запускаем Сервер политики сети
Добавляем в раздел RADIUS-клиенты свои Wi-fi точки доступа или сервер управления точками доступа если он поддерживает эту возможность (в этом случае он будет выполнять роль RADIUS клиента)
Общий секрет, указываем тот, который в последствии укажем на Wi-fi точке (IP адрес точки в той подсети, где она находится).
Переходим к политике запросов на подключение
Вот тут, если нажать на:защищенные EAP(PEAP)-Изменить, мы должны видеть свой сертификат, если он был правильно запрошен и установлен.
Далее настраиваем Сетевые политики
На первый взгляд настройка RADIUS сервера на этом закончена, но это еще не все.
На эту тему есть четкие рекомендации, про которые я совсем забыл (спасибо Александру, что он напомнил):
https://technet.microsoft.com/en-us/library/cc754198.aspx?f=255&MSPPError=-2147217396
если сервер не включен в группу RAS and IAS, то его надо туда добавить:
https://msdn.microsoft.com/en-us/library/cc754878(v=ws.11).aspx
На всякий случай проверяем, что все так, как должно быть, открываем на сервере локальную политику (gpedit.msc)
И проверяем следующий пункт
Далее на точке или точках Wi-fi указываем авторизацию WPA Enterprise.
Здесь же хотел поблагодарить Романа, за подробные разъяснения по неясным моментам по серверу управлению Wi-fi и настройкам непосредственно Wi-fi.
И получаем далее авторизуем с доменными учетными данными, пользователей подключаемых к корпоративному Wi-fi.
Почитать по теме можно здесь:
How to Configure Windows 2012 NPS for Radius Authentication with Ubiquiti Unifi
или здесь:
https://habrahabr.ru/post/142070/
Всем хорошей работы!!!
06.12.2016 —
Posted by |
ms windows server 2016
Sorry, the comment form is closed at this time.
RADIUS (Remote Authentication in Dial-In User Service) is a network protocol for the implementation of authentication, authorization, and collecting information about the resources used. It is designed to transfer information between the central platform and network clients/devices. Your remote access (RADIUS) server can communicate with a central server/service (for example, Active Directory domain controller) to authenticate remote dial-in clients and authorize them to access some network services or resources. Thanks to this, you can use a single centralized authentication system in your domain.
In this article, we’ll show how to configure the centralized RADIUS server based on Windows Server 2022, 2019, or 2016 OSs, and how to configure RADIUS authentication on Cisco devices using the Network Policy Server (NPS) service. In this example, the RADIUS will use the AD to authenticate remote users and authorize them to access Cisco and Mikrotik switches/routers (act as RADIUS clients) command-line interface.
Installing Radius Server (NPS) Role on Windows Server 2022/2019/2016
At first, create a new security group in the Active Directory domain (for example, RemoteCiscoUsers) in which you will need to add all users that will be allowed to authenticate on Cisco routers and switches (How to add AD user to group with PowerShell?).
Starting with Windows Server 2008 R2, the RADIUS server functionality was implemented with the Network Policy Services (NPS) role. With the NPS role, you can authenticate remote clients against Active Directory using the Radius protocol.
So, you need to install the RADIUS server role on your Windows Server 2022/2019/2016. Open the Server Manager console and run the Add Roles and Features wizard. The Remote Authentication Dial-In User Service (RADIUS) protocol in Windows Server is a part of the Network Policy Server role. In the wizard that appears, select the Network Policy and Access Services role in the role selection step.
Note. Also, you can install NPS role and management tools from an elevated PowerShell console:
Install-WindowsFeature NPAS –IncludeManagementTools
Check if the NPAS role is installed on your Windows Server host:
Get-WindowsFeature -Name NPAS
After the role installation is completed, open the Network Policy Server (nps.msc) in the Tools menu.
To use the NPS server in the domain, you must register it in the Active Directory. In the NPS snap-in, right-click on a root and select Register server in Active Directory.
Confirm the registration of the server in Active Directory.
Also, you can register your NPS server in Active Directory with a command:
netsh ras add registeredserver
In this case, the server will be given the authority to read the properties of Active Directory user accounts to authenticate users. The server will be added to the built-in domain group RAS and IAS Servers.
Now you can add the Radius client. Radius client is the device from which your server will receive authentication requests. In this example, it could be a Cisco router, switch, Wi-Fi access point, etc.
To add the new Radius client, expand the RADIUS Clients and Servers section in the NPS console tree and select New on the RADIUS Clients item.
On the Settings tab, fill the fields Friendly name, client Address (you can specify IP address or DNS name), and Shared Secret + Confirm shared password (you will use this password in the configuration of the Cisco switch/router).
Note. The shared secret password is rarely used in huge corporate networks due to the problems with the distribution of shared keys. Instead of shared passwords, it is recommended to use certificates. If you have a corporate Certification Authority deployed to implement PKI infrastructure, you can request and import a *.p12 certificate for the Radius/NPS server. Just add the certificate to the personal certification store of the Local Machine.
In the Advanced tab, select Vendor name – Cisco.
You can use the PowerShell command instead of the NPS GUI to add a new RADIUS client. In this case, you can use the New-NpsRadiusClient PowerShell cmdlet:
New-NpsRadiusClient –Address "192.168.31.1" –Name "cisco2960" –SharedSecret "Zb+kp^JUy]vePb-h.Q*d=weya2AY?hn+npRRp[/J7d"
Configuring NPS Policies on the RADIUS Server
NPS policies allow you to authenticate remote users and grant them access permissions configured in the NPS role. Using NPS access policies, you can make a link to the RADIUS client records and the domain security group that determines the level of access to CISCO devices.
There are two types of policies on a RADIUS server:
- Connection request policies — these policies define a set of conditions that determines which RADIUS servers should authenticate and authorize connection requests received from RADIUS clients;
- Network policies — a set of conditions and settings that allow you to specify who is authorized to connect to your network and a list of assigned access permissions. These policies are processed sequentially from the top to down;
In our case, we will use only the NPS Network policies. Expand the Policies > Network Policies branch and select New:
Specify the Policy name, the type of network access server should remain unchanged (Unspecified).
In the next step Specify conditions, you need to add the conditions under which this RADIUS policy will be applied. Let’s add two conditions — the authorized user must be a member of a specific domain security group, and the device you want to access has a certain name. Use the Add option to create a new condition by selecting the Windows Group type (add the RemoteCiscoUsers group) and specifying the Client Friendly Name (Cisco_*).
Note. The Client Friendly Name field may differ from the DNS name of your device. We will need it in the further steps to identify a specific network device when creating a Remote Access Policy. Using this name, you can specify, for example, a mask by which several different RADIUS clients will be processed by a single access policy.
On the next screen, select Access Granted.
Our Cisco switch supports only the Unencrypted authentication method (PAP, SPAP), so that’s why we’ll uncheck all other options.
Skip the next configuration Constraints step.
In the Configure Settings section, go to the RADIUS Attributes > Standard section. Delete the existing attributes there and click the Add button.
Select Access type > All, then Service-Type > Add. Specify Others = Login.
Now add a new attribute in the RADIUS Attributes > Vendor Specific section. Under Vendor, select Cisco, and click Add. Here you need to add information about the attribute. Click Add and specify the following value:
shell: priv-lvl = 15
This value means that the user authorized by this policy will be granted a maximum (15) administrative access permission on the Cisco device.
The last screen displays all selected NPS policy settings. Click Finish.
Hint. You can back up the current NPS server configuration to the XML file using the command:
Export-NpsConfiguration -Path c:psbackup_nps.xml
If you need to restore the NPS configuration from a previously created backup file, run:
Import-NpsConfiguration -Path c:psbackup_nps.xml
When creating and planning RADIUS policies, pay attention to what matters in their order. Policies are processed from the top to down, and when it turns out that all the conditions in the next policy are met, their further processing is terminated. You can change the priorities of policies in the NPS console using the Processing Order value.
To enable the user account to be used for Radius authentication, open the Active Directory Users and Computers snap-in (dsa.msc), find the user, open its properties, go to the Dial-In tab and select the Control access through NPS Network Policy option in the Network Access Permission section.
Also, you can check the current option value using PowerShell:
Get-ADUser richard.doe -Properties msNPAllowDialin -Server dc1.theitbros.com
If the above command did not return any result (empty), this means that the default value “Control access through NPS Network Policy” is used.
If you want to reset this user attribute to the default state, use the command:
Set-ADUser richard.doe -Clear msNPAllowDialin -Server dc1.theitbros.com
Or you can reset this attribute for all users in the specific Active Directory OU using the LDAP filter:
Get-ADUser -SearchBase "ou=Users,ou=Paris,dc=theitbros,dc=com" -LDAPFilter "(msNPAllowDialin=*)" | % {Set-ADUser $_ -Clear msNPAllowDialin}
Configuring RADIUS Setting on Cisco Devices
After creating the policy, you can proceed to configure your Cisco routers or switches for authentication on the newly installed Radius NPS server.
Because we use domain accounts for authorization, the user credentials must be transmitted over the network in an encrypted form. To do this, disable the telnet protocol on the switch and enable SSHv2 on Cisco using the following commands in configuration mode:
configure terminal crypto key generate rsa modulus 1024 ip ssh version 2
AAA works in such a way: if the response from the server is not received, the client assumes unsuccessful authentication. Be sure to create a local user in case the RADIUS server is unavailable for some reason.
You can create a local user with the following command:
username cisco_local password $UPerrP@ssw0rd
To make the use of SSH mandatory and disable remote access using Telnet, execute the following commands:
line vty 5 15 transport input ssh
Below is an example of the configuration for authorizing a Radius server for the Cisco Catalyst Switch:
aaa new-model aaa authentication login default group radius local aaa authorization exec default group radius if-authenticated radius-server host 192.168.1.16 key Sfs34e#sf #Specify your RADIUS server IP address and key for encryption (the shared secret that we specified on the RADIUS server) service password-encryption # Enable password encryption
If you have several Radius servers, add them to the group:
aaa group server radius radius_srv_group server 192.168.1.16 server 192.168.101.16
This completes the minimum switch configuration and you can try to check Radius authentication on your Cisco device.
How to Configure RADIUS Authentication on Microtik (RouterOS) Devices?
In this part, we will show you how to configure RADIUS authentication for VPN user connections via a Mikrotik router (RouterOS based).
Open the Network Policy Server console (nps.msc) and create a new Radius client.
Select New RADIUS Client and configure the following settings:
- Enable this RADIUS Client;
- Friendly Name — enter the name of your Mikrotik router here;
- Address — specific the IP address of the Mikrotik router;
- Specify your Preshared secret key.
Create a new Network Policy with the following settings:
- User Groups — specify the name of the domain user group that is allowed to authenticate on your Mikrotik router;
- Authentication Type — MS-CHAPv2;
- Tunnel Type — Point-to-Point Tunneling Protocol (PPTP);
- Access Permissions — Access granted;
- In the Configure Authentication Methods window, leave only MS-CHAPv2 and allow users to change expired passwords (User can change password after it has expired option);
- Multilink and Bandwidth Allocation Protocol (BAP) – Do not allow Multilink connections;
- In the Standard section, remove Service-Type – Framed and leave only Framed-Protocol PPP;
- Encryptions — leave only the Strongest encryption (MPP 128-bit) method.
Once you have created a new policy, open the Network Policy Server settings.
Leave only the following UDP ports for the RADIUS server communications:
- Authentication — 1812;
- Accounting — 1813.
Check if these UDP ports are open in Microsoft Defender Firewall Rules. If not, open them manually.
Now you need to configure the connection settings for Windows Server RADIUS in the Mikrotik configuration (we assume that PPP VPN Server is already configured on RouterOS to connect users).
Check in the PPTP server settings that only mschap2 is allowed to use for authentication.
Now we need to configure the connection to Radius NPS server. Select New Radius Server and specify the following options:
- Service: ppp;
- Address: IP address of the RADIUS server;
- Secret: preshared key that you specified in the network policy settings;
- Src/ Address: Mikrotik IP address from which traffic will be sent to NPS;
- Authentication Port: 1812;
- Accounting Port: 1813.
Add appropriate access rules to Mikrotik Firewall.
Then go to Secrets > PPP Authentication and Accounting and enable the Use Radius option.
It remains to configure a PPTP VPN connection to your Mikrotik VPN on users’ computers. To authenticate to Mikrotik, users can use their Active Directory accounts (accounts must be added to the AD group that you have specified when creating the Miktotik Network Policy on NPS).
How to Check the NPS/RADIUS Logs on Windows?
To enable NPS Server Radius Authentication logging, you need to enable the Network Policy Server audit policy. You can enable this policy via the local Group Policy Editor or with the following commands:
auditpol /get /subcategory:"Network Policy Server" auditpol /set /subcategory:"Network Policy Server" /success:enable /failure:enable
Now you can open the Event Viewer console (eventvwr.msc), go to the Windows Logs > Security, and filter the event by the Event ID 6272.
Network Policy Server granted access to a user.
If you need to find all NPS authorizations events for the specific user (Richard.Doe in this example), use the next PowerShell script:
$Query = @"
<QueryList>
<Query Id="0" Path="Security">
<Select Path="Security">
*[EventData[Data[@Name='SubjectUserName'] and (Data=theitbrosrichard.doe')]] and
*[System[(EventID='6272')]]
</Select>
</Query>
</QueryList>
"@
$events = Get-WinEvent -FilterXML $Query
$ipaddr = @{ label="IP"; Expression={$_.properties[9].value} }
$events | select $ipaddr | group "IP" | format-table Count, Name -autosize
- About
- Latest Posts
I enjoy technology and developing websites. Since 2012 I’m running a few of my own websites, and share useful content on gadgets, PC administration and website promotion.
Looking for instructions to configure Radius server on Windows server 2016? This article will guide you in detail on how to do that. Scroll down to read!
Since Radius Server was born, it has brought much more convenience to Windows users. Most of us don’t see what this tool looks like, but we use its applications almost every day.
In today’s article, we will tell you more about this tool, then walk you through the instructions on how to configure Radius server on Windows Server 2016 in detail. Let’s kick right in!
Radius Server And Its Features
In the first part, let’s get to know what this tool is and its main features!
Radius Server Windows
RADIUS is an abbreviation for Remote Authentication in Dial-In User Service. It is known as a protocol used for authenticating and collecting data from the connected resources. RADIUS works by sending information from the headquarters to network devices and vice versa. Users can therefore access the central service to authorize the dial-in devices or services remotely.
Main Features Of Radius Server
There are many positive features about the Radius server. Let’s check one by one:
- Wireless Authentication: The version IEEE 802.11 authentication offers access control to wireless routers, access points, hotspots in EAP/WPA-Enterprise/WPA2-Enterprise modes.
- Multiple authentication backends: The Radius server also supports multiple authentications. It may authenticate against local windows groups, Windows domains, LDAP directories.
- Advanced Radius proxy: The incoming and outgoing forwarded packets are applied for Radius requests.
- Built-in account management: This means using the Radius server, you can modify, add, delete users’ accounts within the database.
- Radius server provides dynamic authorization extensions
- It offers third-party billing system integration as the ClearBox Server may be integrated with SQL-based systems of billing to support the RADIUS server authentication process.
- The protocol offers multiple accounting consumer
- Users can enjoy the cloud integration service by using this protocol
In this part, we are going to focus on how to set up a RAdius server on the Windows Servers 2016 operating system. In addition, users can find here instructions for verification of this program on Cisco devices. Let’s take a closer look!
Setting Up The Radius Server (NPS) Role
To prepare for installing Radius server roles, users are suggested to make a new group of security in the AD domain named RemoteSiscoUsers. After that, add all the users who are going to be involved in Cisco router authentication.
Creating a security group
The point is that from Windows version 2008 R2, the Radius server sets up with the Network Policy Services (NPS) function. This feature helps users authorize faraway clients against AD with the help of the Radius component.
Now, we will guide you on how to setup the radius server function on the Windows Server 2016 operating system. First, open the Service Manager function before launching the Add Roles and Features wizard. You will see a screen open on your desktop; choose the Network Policy and Access Services option.
The thing is you also can use the order statement to install the NPS role by using PowerShell: Install-WindowsFeature NPAS -IncludeManagementTools
After the installation process is accomplished, log in to the Network Policy Server (nps.msc) located in the bar “Tools”.
Choosing Network Policy Server option
The next step is registering your server within the Active Directory. Under the NPS option, click on the right mouse of the root before selecting the Register server within the Active Directory option.
Selecting the Register server in the Active Directory option
Then, users should confirm this process of registration
Confirmation process
Another way of registering the NPS server inside the Active directory is using the order statement: netsh ras add registered server. Hence, the server will join in the built-in group of domains. And it will be given the authority to read the features of Active Directory user accounts.
The server is added in the domain group IAS and RAS Servers
Next, you can put in the Radius client. In this case, your client can be an address for wi-fi accessing, a router, or a switch.
Adding a new Radius client
A setting screen will appear, and it requires users to fill in the necessary information. Users should pay attention to the passwords that were applied in the configuration in the previous stage for the Cisco router.
Filling in the necessary information
Head to the Advanced menu on the right of setting one, choose the Vendor name as Cisco.
Choosing the name of the vendor
You can apply the PowerShell instead of using NPS GUI for the adding function, apply the New-NpsRadiusClient PowerShell cmdlet. New-NpsRadiusClient –Address “192.168.31.1” –Name “cisco2960” –SharedSecret “Zb+kp^JUy]vePb-h.Q*d=weya2AY?hn+npRRp[/J7d”.
Setting Up NPS Policies On The Radius Server
Using NPS policies will help users verify their faraway guests and give permission to access to utilize the NPS role. Also, by applying these policies, users can have a connection to Radius clients’ records, as well as a group of domain security. Policies on the Radius server is grouped into two categories:
- Connection request policies: These include the conditions that allow Radius servers to verify connection requests from its clients.
- Network policies: These policies include settings and conditions that accept you to authorize the network that can link to your server. These are implemented from the beginning to the bottom one by one.
In our situation, we will apply the policies of NPS Network. Here are the details on how to do it. Follow the route Policies > Network Policies option and choose New:
Choosing the new option
Next, select the name of the Policy, and make sure the sort of network server remains unchanged.
Verifying the Policy name
After that, put in the conditions of Radius that you want to apply. Here you have two conditions:
- Authorized user ought to be a part of a group of a domain security
- The wanted access device must have a name.
Here, you can use adding functions to make new conditions by choosing the type of Windows Group and authorizing the Client Friendly Name. Pay attention to the fact that this name is different from the name of the DNS of your device, as it will be used in the upcoming time to identify specific network equipment.
Specifying conditions
Another screen will pop up on your desktop; choose the option Access Granted!
Choosing the access granted option
Then, select the fourth option, let other options be not chosen.
Selecting the fourth option
Now, leave the next step and head into the configure setting board. Follow the route RADIUS Attributes > Standard section. Remove the existing attributes before choosing the adding button. Then, selecting Access type > All, then Service-Type > Add. Specify Others = Login.
Setting up the attributes information
To put in a new attribute to the Radius Attributes, users have to choose the Vendor-Specific section. Add Cisco below the Vendor. And the value, choose the following: shell: priv-lvl = 15. This value stands for your Cisco device will allow a maximum of 15 administrative accesses from authorized users.
Adding the value of attributes
A screening board will appear with all the chosen NPS policy settings.
The accomplished setting
In case users want to back up the current configuration of the NPS server to the XML file, follow the order statement: Export-NpsConfiguration -Path c:psbackup_nps.xml. If they want to restore NPS configuration from a previous backup, they can use the coding line: Import-NpsConfiguration -Path c:psbackup_nps.xml
The factors that impact the order of Radius policies are quite important.
The policies will be implemented from the beginning to the bottom. If all the conditions in the following policy are met, it will lead to the termination of the upcoming processes. To avoid this scenario, users can use the Processing Order value to make the priorities of policy changed.
The list of policy
To activate the account, you will have to open the Active Directory Users and Computers console (dsa.msc). Next, find the users before heading to its properties and choose functions like in the below photo:
Verifying Radius Setting On Cisco Devices
Following the setup Radius server, verifying the Radius setting on Cisco devices is the next step. Because the domain accounts are applied for the process of authorization, the credentials must be changed into encrypted forms. All you have to do here is disabling the telnet component on the switch before activating SSHv2 on Cisco applying the order statement:
- configure terminal
- crypto key generate rsa modulus 1024
- ip ssh version 2
– So the process will work in the way that in case the response of the server might not be received, the client device will summarize the authentication was unsuccessful. Therefore, you should make a local user: username cisco_local password [email protected]
– Next, to make SSH mandatory to use as well as disable faraway access, you should use Telnet and implement the following code lines:
line vty 5 15
transport input ssh
– You can have a look at a configuration process example of a Radius server utilized for Cisco Catalyst Switch:
aaa new-model
aaa authentication login default group radius local
aaa authorization exec default group radius if-authenticated
radius-server host 192.168.1.16 key Sfs34e#sf
#Specify your RADIUS server IP address and key for encryption (the shared secret that we specified on the RADIUS server)
service password-encryption
# Enable password encryption
If you have several Radius servers, add them to the group:
aaa group server radius radius_srv_group
server 192.168.1.16
server 192.168.101.16
The Bottom Line!
After a long time using, we prefer the Radius server because users can use a single centralized authentication system in their domain. Besides, there are many benefits that users can get.
Via this article, we hope you have known how to configure Radius server on Windows Server 2016 operating system. Although the process looks a bit complicated, it is possible to implement. If there are any related questions, don’t hesitate to send us a message. Good luck!
Post Views:
4,487
Использование для WiFi авторизации доменных учетных записей является очень удобным решением для любой организации где есть контроллер домена. Это удобно в случае если у вас несколько офисов т.к. можно подключаться под личным логином и паролем к wifi в любом офисе и безопасно в случае увольнения сотрудника т.к. его доменный профиль удаляется или блокируется.
Для настройки WiFi авторизации через доменный профиль необходимо будет выполнить следующие настройки:
- Настройка сервера политики сети NPS в Windows 2012
- Настройка RADIUS-клиента на Mikrotik.
Научиться настраивать MikroTik с нуля или систематизировать уже имеющиеся знания можно на углубленном курсе по администрированию MikroTik. Автор курса, сертифицированный тренер MikroTik Дмитрий Скоромнов, лично проверяет лабораторные работы и контролирует прогресс каждого своего студента. В три раза больше информации, чем в вендорской программе MTCNA, более 20 часов практики и доступ навсегда.
Настройка сервера политики сети NPS в Windows 2012.
Открываем «Диспетчер сервера» и приступаем к установке роли «Сервер политики сети» через «Мастер добавления ролей и компонентов». Подробно рассматривать процедуру установки не буду, здесь нет никаких сложностей. У меня на сервере эта роль уже установлена (см. скриншот).

После установки Роли потребуется перезагрузка. Перезагружаем сервер и приступаем к настройке NPS.
Настраиваем подключение RADIUS-клиента.
В Диспетчере серверов открываем /Средства/Сервер политики сети.
Переходим в /NPS/Radius-клиенты и сервер/Radius-клиенты, щелкаем пр. клавишей мыши и выбираем пункт «Новый документ»

Указываем имя (любое понятное для себя), ip-адрес роутера Mikrotik и придумываем общий секрет посложней (можно воспользоваться генератором).

Создаем политики для WiFi авторизации.
На этом шаге настройки воспользуемся мастером настройки 802.1x.
Кликаем лев. клавишей мыши по пункту «NPS(Локально)», затем в правом окне разворачиваем пункт «Стандартная конфигурация».
В пункте сценария настройки выбираем «RADIUS-сервер для беспроводных или кабельных подключений 802.1x» и переходим по ссылке «Настройка 802.1x».

Выбираем пункт «Безопасные беспроводные подключения»

На следующем шаге добавляем RADIUS-клиенты, которые были подключены к RADIUS-серверу ранее.

В качестве метода проверки подлинности выбираем «Microsoft: защищенные EAP (PEAP)».

Выбираем группы пользователей домена, которым будет доступно подключение к WiFi.
В результате получаем следующие результаты политик.
Политика запросов на подключение:

Сетевая политика:
На этом настройка NPS в качестве RADIUS-сервера для WiFi-авторизации завершена. Приступаем к настройке роутера Mikrotik.
Чтобы добавить в Mikrotik подключение к RADIUS-серверу открываем меню RADIUS и жмем плюсик.
- Отмечаем нужную службу «Services» — в случае WiFi авторизации это «wireless».
- Указываем «Adsress» Radius-сервера — это ip-адрес настроенного ранее сервера сетевой политики NPS.
- Заполняем Secret, который был указан при добавлении radius-клиента в NPS.

Все остальные настройки оставляем как есть, если только вы не решили изменить на NPS стандартные порты подключения 1812 и 1813.
Добавляем профиль авторизации: /Wireless/Security profiles. Здесь в Authentication types оставляем только WPA2 EAP.

Указываем в нашем действующем WiFi интерфейсе новый Security profile.

На этом настройка Mikrotik в качестве RADIUS-клиента закончена.
Для диагностики неисправности подключений можно включить Logging для RADIUS: /System/Logging/+. В «Topics» выбираем «radius».

Открываем Log и пробуем подключиться к точке доступа.
Количество успешных и сброшенных подключений можно посмотреть во вкладке Status созданного подключения к radius-серверу.

Научиться настраивать MikroTik с нуля или систематизировать уже имеющиеся знания можно на углубленном курсе по администрированию MikroTik. Автор курса, сертифицированный тренер MikroTik Дмитрий Скоромнов, лично проверяет лабораторные работы и контролирует прогресс каждого своего студента. В три раза больше информации, чем в вендорской программе MTCNA, более 20 часов практики и доступ навсегда.
To setup and install a Cloud RADIUS Server running NPS in AWS running on Windows Server, the easiest and quickest way is to our AWS RADIUS NPS Server solution in the AWS marketplace. Launch the image direct from the marketplace. Perfect solution for providing wireless authentication for your access points (APs).
This AWS RADIUS server solution uses Network Policy Server (NPS) to perform centralized authentication, authorization, and accounting for wireless, authenticating switches, remote access dial-up or virtual private network (VPN) connections. When you use NPS as a RADIUS server, you configure network access servers, such as wireless access points or VPN servers, as RADIUS clients in NPS.
- Authenticate wireless users and control access to your wireless APs based on user, IP, device, AD groups and more
- Unlimited number of RADIUS clients (APs) and remote RADIUS server groups
- Single sign-on solution. Allow users to logon to wireless APs automatically
- Active Directory or local security accounts manager for authentication
- Allow or deny connections to specific wireless networks that you specify by network type and Service Set Identifier (SSID)
- Allow or deny connections based on AD group membership
Cloud RADIUS Server Authentication Solution

Table of Contents
Getting Started with AWS RADIUS Server
Once you have deployed our RADIUS server solution from the AWS marketplace. The first step is to RDP into your new VM:
- Guide on how to RDP into an AWS instance
Next, Once you have logged into the AWS RADIUS server, you are now ready to configure it for wireless authentication with your Active Directory.
Open ‘Network Policy Server’ from the desktop or administrative tools:

The first thing you want to do is register this NPS with your AD active directory.
We do this by right clicking the top of the tree and then clicking ‘Register server in Active Directory’: (This can be your onprem Active Directory or AWS Directory Service).
In this example it is shown as greyed out because the AD have not been added.
If you see the same add to your domain and then come back to this step.

Next we want to create a template for your shared secrets. All of the RADIUS clients that will authenticate with the server will need this shared secret so that they can authenticate.
In the long run it is easier to create a template with this in to save entering it on each RADIUS client we setup.
Expand ‘Template Management’ and right click on ‘Shared Secrets’ and click ‘New’:

Give the template a name and either enter your own shared secret or click the ‘Generate’ radial button and then click ‘Generate’ at the bottom.
Make a note of the share secret, this is needed later.
This will create you one as seen below. If you hover over the yellow warning sign you will see a message telling you that it may be too long for some clients.
If this is the case you can shorten the shared secret to a more appropriate size or create your own. Click ‘OK’ to save:

Next under ‘RADIUS Clients and Servers’ right click ‘RADIUS Clients’ and click ‘New’:

Fill this out with the relevant information, under ‘Address’ enter the IP address of your first RADIUS client.
This will be the address of your first wireless access points. Under ‘Shared Secret’ select the template we created earlier and click ‘OK’:

Repeat this process for any of your wireless access points you want to act as RADIUS clients.
Once you have done this, any you have added will be listed:

Now that all the RADIUS clients are setup we need to setup the access policy, but first you need to make sure you have a certificate in the local computer store.
Add a Trusted Certificate to Network Policy Server (NPS)
A RADIUS server must host a certificate that allows both network clients and APs to validate the server’s identity. There are three options for this certificate:
1.) Acquire a certificate from a trusted Certificate Authority. As long as the CA used is trusted by clients on the network, a certificate can be purchased and uploaded into NPS to accomplish and server identity verification (required by clients). Common examples of trusted CAs include GoDaddy and VeriSign.
2.) Implement a Public Key Infrastructure and generate a certificate (advanced)
A PKI can be used on the network to issue certificates trusted by clients on the network. A strong understanding of PKI is recommended for this option.
3.) Generate a self-signed certificate and turn off client server validation (insecure)
A self-signed certificate can be generated for testing/lab purposes, though clients will not trust a self-signed certificate and will need to have server validation disabled in order to connect.
Create a Self Signed Certificate
If you don’t have a PKI or a certificate from a third party, you can create a self signed certificate using the built-in powershell module.
Open up Powershell.exe as Administrator and run the following command
New-SelfSignedCertificate -DnsName "RADIUS FQDN" -CertStoreLocation "cert:LocalMachineMy"
New-SelfSignedCertificate -DnsName "fs.Test.local"-CertStoreLocation "cert:LocalMachineMy"

Import Self Signed Certificate
Steps below on how to generate a self signed certificate.
Once a certificate has been acquired, these are the instructions on how to import a certificate.
- Right-click the Start button and click Run.
2. Type mmc and hit Enter
3. Hit Ctrl+M (or click File -> Add/Remove Snap-in…)
4. Select Certificates from the Available snap-ins and click Add >
5. Select Computer account and click Next, then Finish.
6. Expand Certificates (Local Computer) -> Personal .
7. Right-click Personal > All Tasks > Import – Select Local Machine, click next and browse to where you’ve saved your certificate.
8. Follow the wizard to import your certificate.
This option is not recommended for production deployment, due to dramatically reduced security.
Setup RADIUS NPS Access Policy
Now lets setup the access policy. With the top of the tree selected, on the right hand side under ‘Standard Configuration’ you need to select ‘RADIUS server for 802.1X Wireless or Wired Connections‘ from the drop down list and then click ‘Configure 802.1X’ below:

Select ‘Secure Wireless Connections’ and give it a suitable name at the bottom and click ‘Next’:

On the next screen you should see a list of RADIUS clients which we setup earlier, so we don’t need to do anything here. Click ‘Next’:

From the drop down list select ‘Microsoft: Protected EAP (PEAP)’ and then click ‘Configure’:

Here you can specify the certificate you would like to use to secure the connection using the drop down menu.
I had already requested a certificate for this purpose which I selected. However you can use the default self-signed one for now. Click ‘OK’ and then click ‘Next’:

At this stage you can specify which domain groups will be given access to the wireless network. Click ‘Add‘ and search for any domain groups you would like to add and then click ‘Next‘:

The next page allows you to configure traffic controls. Here you can setup VLANS and access control lists to control traffic. You will need to refer to your AP manufacturer if they support these options, as this page is optional or you can configure later if you need these settings configured. Press Next to continue

On the last page confirm your settings and click ‘Finish’:

You will now see under the ‘Network Policies’ section that a new policy has been created:

If you double click on this policy you can see the settings that are in force:

Under the ‘Conditions’ tab you can see what conditions are required to connect to the wireless network. In this example anyone who is a member of the DOMAINStaff group will be authorized.
At this stage you can add, edit or remove groups using the buttons below. If we were to add the DOMAINDomain Computers group any machine on the network could authenticate and connect to the wireless network with its machine account:

Going a step further you can create another policy to deny access to the wireless network.
The easiest way to create another policy is to duplicate the first one. Do this by right clicking the first policy and clicking ‘Duplicate Policy’:

Under ‘Overview’ tick the ‘Policy enabled’ box and change the ‘Access Permission’ to ‘Deny access’:

Under the ‘Conditions’ tab click on the current windows group and click ‘Edit’.
Remove the DOMAINStaff group and add the group containing users you don’t want to have access to the wireless network.
Click ‘OK‘ and then click ‘OK’ again:

On the ‘Network Polices’ page right click the newly created deny policy and move it to the top if it isn’t there already so that it has the processing order of ‘1’.
Policies are processed from the top down so the deny policy will be processed first. Denying any user who meets the conditions of the policy even if they are also a member of the group that is listed in the allow policy:

You can at this stage click on the ‘Accounting‘ section and enable this RADIUS server to act as an accounting server too, keeping logs of any connection requests. This is either in the format of a log file or an SQL database.
The next step is to configure the wireless access points to pass authentication requests to our newly configured RADIUS server. The setup and process will differ depending on the brand of access point you are using.
Cisco Meraki RADIUS Authentication
We are going to use Cisco Meraki MR access points in this example.
Once a RADIUS server has been set up with the appropriate requirements to support authentication, the following instructions explain how to configure an SSID to support WPA2-Enterprise, and authenticate against the RADIUS server:
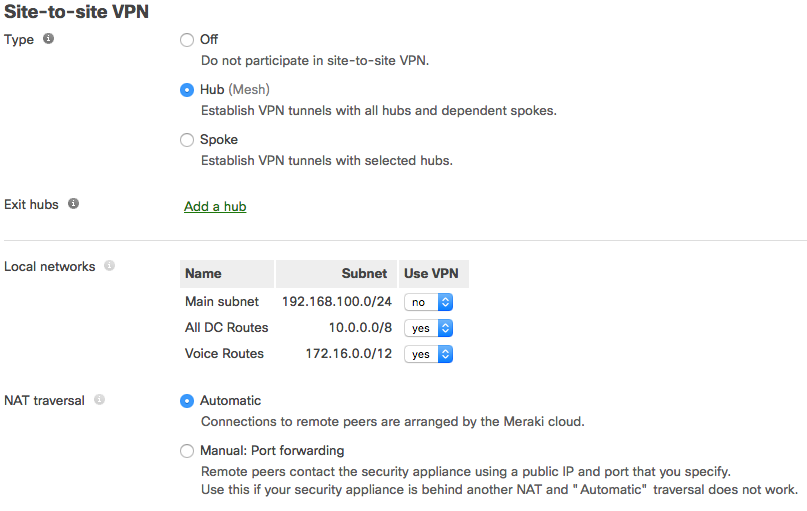
- In Dashboard, navigate to Wireless > Configure > Access control.
- Select your desired SSID from the SSID drop down (or navigate to Wireless > Configure > SSIDs to create a new SSID first).
- For Association requirements choose WPA2-Enterprise with my RADIUS server.
- Under RADIUS servers click Add a server
- Enter the Host (IP address of your RADIUS server, reachable from the access points), Port (UDP port the RADIUS server listens on for Access-requests; 1812 by default) and Secret (RADIUS client shared secret):

6. Click the Save Changes button.
Aside from the RADIUS server requirements outlined above, all authenticating APs will need to be able to contact the IP address and port specified in Dashboard.
Make sure that your APs all have network connectivity to the RADIUS server, and no firewalls are preventing access. Review the AWS firewall ports below
VLAN Tagging Options
Dashboard offers a number of options to tag client traffic from a particular SSID with a specific VLAN tag. Most commonly, the SSID will be associated with a VLAN ID, so all client traffic from that SSID will be sent on that VLAN.
With RADIUS integration, a VLAN ID can be embedded within the RADIUS server’s response. This allows for dynamic VLAN assignment based on the RADIUS server’s configuration.
Please refer to Cisco’s documentation regarding Tagging Client VLANs with RADIUS Attributes for configuration specifics.
Testing RADIUS Server from Meraki Dashboard
Dashboard has a built-in RADIUS test utility, to ensure that all access points (at least those broadcasting the SSID using RADIUS) can contact the RADIUS server:
- Navigate to Wireless > Configure >Access control.
- Ensure that WPA2-Enterprise was already configured based on the instructions in this article.
- Under RADIUS servers, click the Test button for the desired server.
- Enter the credentials of a user account in the Username and Password fields.
- Click Begin test.
- The window will show progress of testing from each access point (AP) in the network, and then present a summary of the results at the end.
APs passed: Access points that were online and able to successfully authenticate using the credentials provided.
APs failed : Access points that were online but unable to authenticate using the credentials provided. Ensure the server is reachable from the APs, the APs are added as clients on the RADIUS server.
APs unreachable: Access points that were not online and thus could not be tested with.
(Optional) Deploy a PEAP Wireless Profile using AD Group Policy
For a seamless user experience, it may be ideal to deploy a PEAP wireless profile to domain computers so users can easily associate with the SSID.
Though optional for user auth, this is strongly recommended for machine authentication.
The following instructions explain how to push a PEAP wireless profile to domain computers using a GPO, on a Domain Controller running Windows Server:
- Open the domain Group Policy Management snap-in.
- Create a new GPO or use an existing GPO.
- Edit the GPO and navigate to Computer Configuration > Policies > Windows Settings > Security Settings > Public Key Policies > Wireless Network (IEEE 801.X) Policies.
- Right Click Wireless Network (IEEE 801.X) Policies and choose Create a New Windows Vista Policy.
- Provide a Vista Policy Name.
- Click Add for Connect to available networks.
- Choose Infrastructure.
- On the Connection tab, provide a Profile Name and enter the SSID of the wireless network for Network Name(s). Click Add.
- Click the Security tab. Configure the following:
- Authentication: WPA2-Enterprise or WPA-Enterprise
- Encryption: AES or TKIP
- Network Authentication Method: Microsoft: Protected EAP (PEAP)
- Authentication mode: Computer Authentication (for machine auth).
- Click Properties.
- For Trusted Root Certification Authorities select the check box next to the appropriate Certificate Authorities and click OK.
- Click OK to close out and click Apply on wireless policy page to save the settings.
- Apply the GPO to the domain or OU containing the domain member computers (refer to Microsoft documentation for details).
Once you’ve deployed the wireless profile to users or manually setup one on a test machine, we can now test connecting.
Testing Wireless Access Profile

Now enter a username and password for a valid domain account that is a member of the group you specified earlier in the allow policy.
Depending on the model of phone you will get more of less detail at this stage. On an Android phone you need to manually specify the certification authority certificate when joining the network that will validate the server certificate we selected earlier during the setup process.
This has to be installed manually first. For testing purposes you can use the drop down list and select ‘Don’t validate’:

On an iOS device initially you will just be asked for a username and password and then asked if you trust the server certificate.
If you have preinstalled the CA certificate beforehand and enabled full trust for it you won’t be asked.
Providing all the details are valid the device will connect to the wireless network as it would with any other:

Single Sign On (SSO) For Windows Devices
For any windows domain joined devices such as tablets or laptops you will have 2 options to connect depending on your setup.
First, If you specified DOMAINDomain Computers earlier in the conditions of the allowed policy the devices will be able to authenticate using their machine accounts.
You can just click the wireless network and it will seamlessly connect authenticating in the background with its machine account. Using group policy or SCCM you can deploy the wireless profile centrally making each Windows device connect automatically without user intervention. However this does require an initial connection to the network (wired or wireless) to receive the GPO or SCCM update.
If you didn’t specify the DOMAINDomain Computers group earlier a user account is required to access the network.
The second option is when a user tries to connect to the wireless network they will be asked for a username and password. If they are already logged in as a domain user they can select the option to connect using the currently logged in user. Providing the user is a member of the correct group the device will connect to the wireless network, authenticating with that users credentials.
Eliminating the need for a pre-shared key gives you much more control over who has access to your wireless network.
Other conditions can be specified under a policy as well as windows groups such as times of the day, IP address ranges, etc. If a user leaves or is compromised there account can be disabled or their password changed to deny them further access to the wireless.
Policies can be tailored to your specific needs giving you’re a lot more flexibility.
AWS RADIUS Server Firewall Ports
The following firewall ports will need to be open for each of your wireless access points (APs) to allow them to access your RADIUS / NPS server in AWS:
RADIUS Authentication and Authorization
UDP: 1812 / 1645
RADIUS Accounting
UDP: 1813 / 1646
To setup AWS firewall rules refer to – AWS Security Groups
You also need to make sure the RADIUS server in AWS can communicate with your AD Active Directory
Radius NPS Server Support / Further Documentation
Check out the following links for further documentation and support for Radius NPS Server:
https://docs.microsoft.com/en-us/windows-server/networking/technologies/nps/nps-top

In this tutorial you will be shown how to configure Unifi Controller and Windows Server for RADIUS Wifi access. Why is this useful? Well this allows us to just disable a user account in Active Directory after a termination and the previous employee will no longer have Wifi access. This will prevent Tech Support having to change the Wifi password every time an employee is terminated.
Prerequisites for this tutorial.
- Internal Unifi Controller, I myself am using a UDM-PRO for that function.
- You can use a Cloud Hosted Unifi Controller but you will need to open radius ports on your firewalls wan. Your network firewall should be configured to only allow incoming traffic from your Unifi Hosted Controllers IP address to access the Radius ports.
- Your Unifi equipment should be assigned static IP addresses outside your DHCP Scope. Once done write down the IP addresses alongside their model or unique name.
- Stand up a new physical or virtual server with Windows Server 2019.
- I called my new virtual server HDN-RADIUS. 1vcpu 4GBram 60GB HDD
- Install all updates on new Radius server
- Assign static IP address.
- Join new Radius server to the domain.
- At this point create a Backup or a Virtual Snapshot before moving forward with the tutorial.
- I am a firm believer on keeping ADDC server clean. So do not configure these roles on that server.
Lets get started with installing the required Windows Server Roles!
We will be starting with the newly created Windows Server 2019 and installing the roles we need for radius to work with your Unifi Controller and its Wifi Access Points.
- Open your Windows Server Manager > Click Manage > Click Add Roles and Features.
- Click Next until you reach Server Roles. Enable The following.
- Active Directory Certificate Services
- Network Policy and Access Services
- Remote Access
- Once the items are selected and the prerequisites are approved click Next until you reach AD CS / Roles Services.
- Under Role Services select Certification Authority and click Next.
- Now within Remote Access and Role Services, select DirectAccess and VPN (RAS) and click Next.
- Now click Next all the way through and then Install the Roles and wait until you receive the message that all your roles are installed successfully. Once successful you can close the window.
Lets open up the firewall ports needed.
Here we are going to open up the firewall ports that we need for RADIUS to work with the Unifi Controller.
- From the RADIUS server search for Advanced in the task bar search menu and select Windows Defender Firewall with Advanced Security.
- Locate Inbound Rules > Right Click Inbound Rules > Select New Rule…
- Select Port and click Next.
- Select UDP and provide the Specific Local Ports you want opened which is Port 1812 and then click Next.
- Select Allow the connection and click Next.
- Check mark: Domain, Private and Public. Afterwards click Next.
- Give your Rule a name, I used Radius UDP 1812. Afterwards click Finish.
Lets Configure Active Directory Certificate Services
We are making progress. Here we will be configuring Active Directory Certificate Services, this will be needed for the desktops / laptops that connect to the RADIUS Wifi.
- Open up Window Server Manager. Click on the Flag and then locate Configure Active Directory Certificate Services.
- Under Credentials you will want to specify a Domain Admin Account, then click Next
- Within Role Services check the box for Certification Authority and click Next
- For Setup Type we will want to select the radio button for Enterprise CA, then click Next.
- Within CA Type select the radio button for Root CA and click Next.
- For Private Key we will be providing our own key so we can document it and have it handy. Select the radio button for Create a new private key and then click Next.
- Under Cryptography the defaults can stand as is. Go ahead and click Next.
- Double check your CA Name Settings. They should be similar to mine besides the domain name and server name that I am using of course. Afterwards click Next.
- Under Validity Period you can set your certificate to expire whenever. However my personal preference is 100 years so we do not have to bother with certificate expirations any time soon. Afterwards click Next.
- In Certificate Database section leave these paths the same and click Next.
- Review the Confirmation and select the Configure button.
- Once configured your Results should be Configuration Succeeded. Afterwards click close and we are done with the certification creation.
Lets configure our Network Policy Server
Here we will be configuring the security policies required for our Unifi Controller and Wifi Equipment to communicate with the Radius server and Active Directory / Domain Controller.
- Open Windows Server Manager click Tools > Select Network Policy Server.
- Now that we have Network Policy Server open click on NPS (Local). You should now see the option to change your Standard Configuration from the dropdown select RADIUS server for 802.1X wireless or Wired Connections. Move forward with clicking on Configure 802.1.X.
- Once the Configure 802.1X window is open select the Radio button for Secure Wireless Connections. Then click Next.
- You will be prompted with a screen to add your New RADIUS Client and here you will want to refer back to your list of equipment’s IP Addresses and Device Names.
- Friendly name use your Unifi Equipment’s model or unique name.
- For Address use the assigned static IP address you gave to the equipment.
- Now for Shared Secret, select the radio button for Manual. Type in a strong password and write it down. This password will be used in the Unifi Controller as well. Afterwards click OK.
- You will have to add all your Unifi Devices as clients to the RADIUS server. This will allow Authentication between the server and the Unifi Devices. Once done adding devices click Next.
- For Configure an Authentication Method, click on the dropdown window and select Microsoft: Protected EAP (PEAP) afterwards click Next.
- Under Specify User Groups I am going to add Domain Users to be allowed to access to the RADIUS Authentication. This gives permissions to every domain user to access the Unifi Wireless SSID. You can also create a security group in your AD server and add specific users for access under that group. Once you decide what your preference is click Next.
- All can remain the same under Configure Traffic Controls so continue through and click Next.
- With the following window you can click Finish.
- We are almost done with Network Policy Server. We will now have to register this new RADIUS server with Active Directory. Open Network Policy Server, right click on NPS (Local) and from the menu select Register server in Active Directory. Now we are finished with this section!
Lets create a Group Policy in your AD/DC server
Now this may vary from everyone AD configuration. I always have an OU where my users and computers would reside in and not within the default locations.
- Log into your AD/DC server and open up Group Policy Management. Right click on the OU where your domain users reside in and from the menu select New GPO. Afterwards Name that GPO with an identifiable name. I will be using Radius. then click the OK button.
- Locate and select your new Radius Policy. Under Security Filtering select the Add button and add Domain Users.
- Right click and Edit your new Radius Policy. Drill down this path Computer Configuration > Policies > Windows Settings > Security Settings > Public Key Policies.
- Within Public Key Policies locate Certificate Services Client – Auto-enrollment. Right click the policy and click Properties.
- In the Certificate Services Client – Auto-enrollment Properties window change the Configuration Model to Enabled form the dropdown window. Afterwards check both boxes and click the OK button.
- Drill down this path Computer Configuration > Windows Settings > Security Settings > Public Key Policies. Locate the folder Automatic Certificate Request Settings. Right click it > find New > select Automatic Certificate Requests.
- You will be prompted to start the Wizard, just click Next.
- Select Computer and then click Next.
- Now click Finish. We have now completed the GPO for domain desktop and laptops to properly obtain a security certificate when they connect to the Unifi Wireless SSID.
Configuring your Unifi Controller and Wireless SSID to use Windows RADIUS Server.
We finally made it to the last few steps which are to configure the Unifi Controller and a Wireless SSID to use the Windows RADIUS Server.
- Log into your Unifi Controller. Locate and click the Gear Icon and then click Advanced Features.
- Scroll down and locate RADIUS section. Now click on Add RADIUS Profile.
- To keep it simple I am group to name this RADIUS profile my server name.
- Scroll down until you find RADIUS Settings and select the expand arrow button.
- Here you will add your RADIUS server’s static IP address and the Shared Secret you wrote down when configuring the Unifi Devices in the Network Policy Server. Keep the ports the same for both Authentication Servers and RADIUS Accounting Servers. Once done click Apply Changes button.
- Now we will move forward with configuring a new Wireless SSID. Locate and click on WiFi in the Unifi Controller.
- Locate the Wifi Section and click the Add New WiFi Network button.
- Name your SSID. Select your Internal network from the dropdown and then expand Advanced Tab by clicking the dropdown arrow.
- Scroll down until you find the Security section and expand it by clicking the drop down arrow.
- Here you will first select your security protocol WPA-2 Enterprise. Afterwards under RADIUS Profile, from the dropdown select the profile you recently named and created. Select PMF is Required and finally click the Apply Changes button.
That was exciting! We are finally finished. Your Unifi wireless access points should now be transmitting an SSID. To connect to this SSID you will have to use your domain User Name and Password. Go ahead and give it a shot.
How To Auto Deploy RADIUS WiFi With Group Policy
Windows devices can’t connect to RADIUS 802.1X Wifi
Advanced VPN Configuration: How to configure Windows Server and UDM-PRO UniFi Controller for RADIUS VPN access