The latest Npcap release is version 1.72.
Npcap 1.72
Installer and debug symbols available at https://npcap.com/
-
Fixed an issue where promiscuous mode or other hardware packet filters are ignored after a second
handle is opened on the same adapter, including handles opened in the process of listing adapters
withpcap_findalldevs(). Fixes #647. -
Fixed an issue with validation of parameters to
PacketGetNetInfoEx(). TheNEntriesparameter
was not being checked for values less than or equal to 0. Fixes #625.
Npcap 1.71
Installer, debug symbols, and SDK available from https://npcap.org/#download
-
Increase strictness in checking for and restoring adapter parameters modified during capture:
hardware packet filter and lookahead will only be modified if the original value can be
determined. This fixes issues with connectivity on certain adapter types (WWAN and some WiFi
adapters) after a capture is closed. -
Modify NDIS binding parameters so that Npcap will bind both above and below a NIC teaming or
network bridge IM driver. This may improve capture options in related situations, like #115. -
Updated build configurations to enable DEP and ASLR for npcap.sys, which were missing from the
original configs inherited from WinPcap. Additionally, enabled Control Flow Guard for Packet.dll
and all helper EXEs. -
Fix a BSoD issue on Windows 8.1 due to registering a service without a name. Fixes #565.
-
Fix an issue with admin-only mode where high-integrity processes (UAC not enforced) could not open
or list adapters. Fixes #606. -
Restored an undocumented data member of the struct
ADAPTERthat is not used internally. Directly
accessing members of theADAPTERstruct fromPacket32.his highly discouraged, since the
API inPacket32.his not intended for use apart from libpcap. Closes #609. -
Extensive refactoring of driver code for performance and maintainability.
Npcap 1.70
Installer, debug symbols, and SDK available from https://npcap.org/#download
-
Major overhaul of Packet.dll to improve performance of
PacketGetAdapterNames(), used by
pcap_findalldevs(), andPacketOpenAdapter(), used in all libpcap functions that return a
pcap_t. Reduced calls toGetAdaptersAddresses(), properly caching results for short periods.
Errors from lower functions are correctly propagated, making diagnosis of failures easier. Fixes
#168, #61, and #586. -
PacketGetNetType()now always sets the LinkSpeed field to 0. Many adapters did not support the OID
that was being used to get the link speed, and libpcap (Npcap’s published API) does not pass this
information through, so there should be no impact on the majority of software. Software that needs
link speed may usepcap_oid_get_request()orGetAdaptersAddresses()to get the information. -
The undocumented
char PacketLibraryVersion[]export has been removed. ThePacketGetVersion()
function is the documented way to get the runtime version of the Packet.dll library. -
Packet injection operations (
pcap_inject(),PacketSendPacket(),pcap_sendqueue_transmit(),
andPacketSendPackets()) now properly pend the related Write IRP until the NBLs have
been returned by NDIS. This may make packet injection more efficient. -
Packet injection operations are no longer limited to one at a time. Multiple threads can issue
multiple send operations concurrently on the same capture handle without issue, unless system
resource limits result in allocation failures. Additionally, WinPcap’s limit of 256 concurrent
sends on each adapter has been removed. Each Write call is still synchronous, however. -
Loopback packet capture and injection now uses fewer WFP filters and callbacks, avoids duplicate
packet processing, uses inspection rather than blocking filters, and persists callout driver
objects while still removing callout filters when captures are not using them. These and other
improvements increase loopback capture efficiency and reduce interference with other network
components. -
Npcap is only supported on Windows 7 SP1 and later, and requires KB4474419 to support SHA-2
signature validation. The installer will now check these specific requirements, rather than
attempting an installation that will fail anyway. -
Added timeouts to subprocess executions in the installer to prevent a hung installation.
-
Fixed a minor issue with Npcap OEM’s silent installer: Npcap 1.55 and later ought to avoid
reinstalling the same version if the existing installation options match the requested options,
but/winpcap_mode=nowould never match. -
Packet sendqueue operations (
pcap_sendqueue_transmit(),PacketSendPackets())
with time synchronization (syncparameter) have been improved to use timed waits when
possible, only falling back to busy wait for inter-packet delays of less than 50
microseconds. Time difference calculations have been revised to avoid integer overflows
and loss of precision. Fixes #580. -
Packet sendqueue operations now more strictly check timestamp order. If an out-of-order
timestamp is encountered, the packet will not be transmitted.PacketSendPackets()will
set the last error value toERROR_INVALID_TIME. Since packets may be
reported slightly out-of-timestamp-order on multiprocessor machines due to
processing delays, only timestamps that are more than 1ms earlier than the
preceding timestamp will generate the error. -
Npcap is now built with the Win11 SDK and WDK (10.0.22000). We look forward to
implementing support for the exciting new features of NDIS and WFP. -
Improve capture handle state transitions within the Npcap driver. State mismatches led
to issues like #584, where the wrong error code was
reported when the adapter was detached and reattached. -
Fix an issue where raw WiFi capture handles (
/dot11_supportinstall option) would not
reattach after a network disconnect and reconnect. Normal handles got this ability in
Npcap 1.60, but raw WiFi frame captures (monitor mode) did not take advantage of it.
Fixes #591. -
Npcap now avoids setting hardware packet filters (
OID_GEN_CURRENT_PACKET_FILTER,
PacketSetHwFilter()) that the miniport does not declare support for. This may improve
compatibility with WWAN (e.g. 3G and LTE) and VPN connections. -
Npcap now tracks the original lookahead value (
OID_GEN_CURRENT_LOOKAHEAD,
PacketSetMaxLookahead()) before requesting the max value from the miniport, and restores it once
the capture handle is closed. The practice of setting the lookahead to max value was inherited
from WinPcap, and may be changed in the future subject to performance testing.
Npcap 1.60
Installer and debug symbols available from https://npcap.org/#download
-
Npcap can now tolerate network disconnections or NDIS stack
modifications that previously resulted in programs like Wireshark
stopping with the error «PacketReceivePacket error: The device has
been removed. (1617)». This error may still be returned, but user
programs can consider it a transient error. If the network is
reconnected, capture can resume on the same handle. Fixes
#506. -
Improved validation for IRP parameters, resolving potential BSoD
crashes that could be triggered by software interacting directly
with the driver’s device interface. These bugs still affect the last
releases of WinPcap. Thanks to Ilja Van Sprundel from IOActive for
reporting them. -
Fix an issue with NX pool compatibility that caused Npcap 1.50 and
1.55 to fail to run on some Windows 7 systems. Fixes
#536. -
Fix how the installer handles
/option=enforced, which was broken
in Npcap 1.55. Fixes #556. -
Concurrently released the Npcap SDK Version 1.12, which fixes native
ARM compilation by including the ARM64 wpcap.lib, among other
changes. The SDK now has its own change log at
https://github.com/nmap/npcap/blob/master/SDK_CHANGELOG.md. -
Further driver source code hardening to catch more bugs
before they manifest in worse ways. This includes adding more SAL
annotations for code analysis, extra assertions, etc. -
The
/prior_driverinstaller option now selects the Npcap 1.30
driver, since Microsoft’s cross-certificate expired 30 minutes
before we signed Version 1.31. See
#536. -
Simplified the code base by removing a bunch of unused or
unneccessary code. This includes «kernel dump mode» (MODE_DUMP)
which was inherited from WinPcap 3.1 even though it had already been
deactivated there in 2005. Also removed legacy WinPcap code which allowed
their (long discontinued) «Pro» version DLL to install the driver
itself. This is not allowed by modern operating systems. We were
able to remove a bunch of code from NPFInstall.exe too. Updated the
INF file to prevent npf_wifi service from being configured, since it
was never actually used. -
Fix an issue causing
pcap_setmode()/PacketSetMode()with a value
ofMODE_CAPTto fail.MODE_CAPTis the default for new handles,
so this only affects software that usesMODE_STATand then
switches toMODE_CAPT, or software that expects a call to
pcap_setmode(MODE_CAPT)on a handle already inMODE_CAPTto
succeed. Fixes #558. -
When installing Npcap in WinPcap API-Compatible mode (the default),
the Npcap installer will perform the uninstallation of WinPcap
directly instead of running the WinPcap uninstaller. This prevents
the WinPcap uninstaller from rebooting the system and allows us to
clean up partial or broken installations. -
Further deprecate the «Legacy loopback support» option: The
npcapwatchdog scheduled task will not check for the existence of the
Npcap Loopback Adapter. -
Added the
PnpLockDowndirective to the npcap.sys INF file for
additional Windows file protection of the driver binary. -
Replaced a feature of NPFInstall.exe and the SimpleSC.dll NSIS
plugin with Powershell commands to improve installer size and
compatibility. May fix #226. -
While you won’t see it in the code itself, we dramatically improved
our automated build and testing proceses. We now run automated
native-arch builds and testing of multiple programs (particularly
the SDK Examples) on all 3 architectures (x86, x64, and ARM). All
tests are run with the debug build of the driver (assertions on) and
Driver Verifier with at least standard settings, and only when that
passes is the release build run through the same tests, also with
Driver Verifier. The tests are also run in x86 emulation on x64 and
ARM.
Npcap 1.55
Installer and debug symbols available from https://npcap.org/#download . Npcap SDK 1.11 was released concurrently, with only minor changes to const-ness of some function parameters in Packet32.h and additional documentation on installer options.
-
Npcap installer can now recognize NetCfg status codes indicating that a
reboot is required (0x0004a020,NETCFG_S_REBOOT), and will prompt the user
to reboot. In silent mode, the installer will return code 3010 (0x0bc2,
ERROR_SUCCESS_REBOOT_REQUIRED) to indicate this result. Fixes #224. -
Npcap installer’s silent mode now offers better control over when to remove
and reinstall an existing Npcap installation. Documentation has been updated
for the new installation options/require_version,/require_features, and
/forceand will be published with the new Npcap SDK 1.11. Fixes #523. -
Fixed an installation failure (0xe0000247) on Windows 8.1/Server 2012 R2 and
earlier systems which have not updated root certificates. The root certificates
are now installed to the Roots trust store. Fixes #233. -
Fixed an issue since Npcap 1.30 where broadcast and subnet masks for adapters
returned bypcap_findalldevs()were in host byte order, displaying values
like «0.240.255.255». Fixes #525. -
Libpcap 1.10.1 has been updated to include some recent changes to the libpcap-1.10
release branch which extend support to adapters with the NdisMediumIP media type,
including Wireguard Wintun virtual adapters. Fixes #173. -
Added specific bad-value checks for issues originating in other drivers which
may be incorrectly attributed to Npcap. These checks, in combination with
additionalconstqualifiers, should serve as assurance that Npcap is not
modifying traffic during capture and cannot be responsible for such crashes. -
Powershell commands launched by the installer are now run with the
-NoProfileoption. Fixes #529. -
Npcap SDK minor change to add const qualifiers to parameters to several Packet.dll functions.
-
Npcap installer now uses Unicode internally. This may result in mixed-encoding install.log files.
Npcap 1.50
Installer and debug symbols available from https://npcap.org/#download
-
Fixed #513 which prevented Npcap 1.40 from installing.
-
All PowerShell scripts installed or used during installation are now digitally signed.
-
Npcap can now be installed on Windows 10 for ARM64 devices. Both ARM64 and
x86 DLLs will be installed, allowing existing x86 applications such as Nmap
or Wireshark to run without modification. -
Npcap SDK 1.10 release coincides with this release, providing updated
documentation and libs for ARM64. -
Npcap code now passes Microsoft’s Static Driver Verifier for NDIS drivers and
Visual Studio’s Code Analysis «AllRules» ruleset. A couple of minor and
extremely-improbable bugs were fixed in addition to general code cleanup and annotation. -
On Windows 8 and 8.1, the Npcap driver has been updated to NDIS 6.30,
supporting network stack improvements like RSC and QoS. Windows 10 still uses
NDIS 6.50 and Windows 7 uses NDIS 6.20. -
Npcap is no longer distributed with SHA-1 digital signatures. Windows 7 and
Server 2008 R2 will require KB4474419 in order to install Npcap. All other
platforms support SHA-2 digital signatures by default. -
Streamlined loopback packet injection to avoid using Winsock Kernel (WSK)
sockets. This removes a significant amount of complexity and overhead. -
Due to Microsoft’s deprecation of cross-signed root certificates for kernel-mode code signing,
Npcap 1.40 may not install correctly on Windows versions prior to Windows 10.
Our testing did not show any issues, but users who experience installation
failures may use the/prior_driver=yesinstallation option to install the
Npcap 1.31 driver instead, which has no such issues. -
The «npcapwatchdog» scheduled task, which ensures the Npcap driver service is
configured to start at boot, is now installed with a description when
possible (Windows 7 does not support creating scheduled tasks via PowerShell).
Fixes #498. -
Fix an issue where installation under Citrix Remote Access or other
situations would fail with the message «Installer runtime error 255 at
76539962, Could not load SimpleSC.dll». Fixes #226. -
Ensure driver signature can be validated on systems without Internet access
by installing the entire certificate chain, including the chain for the
timestamp counter-signature. This should address #233. -
Fix an issue with comparing adapter names retrieved from the Registry. This
prevented Npcap 1.31 from being used for SendToRx and other less-used
features. Fixes #311. -
Npcap driver no longer excludes adapters based on media type, which may allow
capture on some devices that were previously unavailable.
Npcap 1.40
RELEASE RETRACTED Due to #513, we have retracted Npcap 1.40 and have released Npcap 1.50 to address this issue.
Npcap 1.31
Installer and debug symbols available from https://npcap.org/#download
-
Fix a bug with the non-default legacy loopback capture support that caused
all requests to open a capture handle to open the loopback capture instead.
It is recommended to not select «Legacy loopback support» at installation
unless you know your application relies on it. Fixes #302. -
For Windows 10 and Server 2016 and later, restore the ability to capture
traffic on VMware VMnet interfaces such as the host-only and NAT virtual
networks. This will be restored for other supported Windows versions in a
later release. Fixes #304.
Npcap 1.30
Installer and debug symbols available at https://npcap.org/#download
-
Restore raw WiFi frame capture support, which had been broken in a few ways
since Npcap 0.9983. Additional improvements enablePacketSetMonitorMode()
for non-admin-privileged processes, allowing Wireshark to correctly enable
monitor mode via checkbox without requiring WlanHelper.exe. -
Fixed WlanHelper.exe to correctly set modes and channels for adapters, if run
with Administrator privileges. Fixes #122. -
Improved speed of
pcap_findalldevs()by using fewer calls to
GetAdaptersAddresses()and avoiding direct Registry inspection. The new
method may result in more adapters being available for capture than
previously reported. See #169. -
Updated Packet.dll to use modern
HeapAlloc()allocation, faster than the
legacyGlobalAlloc()inherited from WinPcap. -
Improve error reporting from
PacketGetAdapterNames()and related functions.
Npcap 1.20
Installer, SDK and debug symbols available from https://npcap.org/#download
-
Upgrade wpcap.dll to libpcap 1.10. This change enables software to use
pcap_set_tstamp_type()to set the packet capture time source and precision
per capture handle. The currently-supported types (see
pcap-tstamp) are:PCAP_TSTAMP_HOST_HIPREC_UNSYNCED— default, maps toTIMESTAMPMODE_SINGLE_SYNCHRONIZATIONPCAP_TSTAMP_HOST_LOWPREC— maps toTIMESTAMPMODE_QUERYSYSTEMTIMEPCAP_TSTAMP_HOST_HIPREC— maps toTIMESTAMPMODE_QUERYSYSTEMTIME_PRECISE
-
Fix an issue preventing
WlanHelper.exefrom changing WiFi parameters for
adapters which caused the error message «makeOIDRequest::My_PacketOpenAdapter
error». Fixes #122 and several other reports
of the same issue. -
Fixed an issue that prevented NDIS protocol drivers from reducing the
hardware packet filter, even if the removed bits/filters were only set by
that protocol driver initially. This may fix #106. -
Fixed an issue with
pcap_sendqueue_transmit()that caused it to busy-wait
in an attempt to synchronize packet sends with pcap timestamps, even when the
program did not request synchronization. Fixes #113. -
The installer will now safely remove and replace broken installations due to
#268. -
Upgraded installer to NSIS 3, which improves compatibility with modern Windows versions.
-
Added application manifests to several installer tools and removed Windows
Vista from the manifests of others, improving compatibility.
Npcap is packet capture library for Windows operating system. Npcap is created and developed as a Nmap project. Npcap is based on WinPcap project which is currently not actively developed. The most important feature of Npcap is support for Windows 10 operating systems where WinPcap only supports up to Windows 7.
Npcap Features
Npcap provides a lot of powerful features according to WinPcap. Here are some of them.
- `NDIS 6 support` will make the Npcap work with newer Windows operating systems like Windows 10, Windows Server 2016, etc.
- `Extra Security` will only provide packet capture to the Administrator level users. If a non-Admin user tries to package capture he should pass UAC (User Account Control).
- `Loopback Packet Capture` makes Npcap capture loopback interface packet capture which is generally used for different services to communicate on the local host.
- `Loopback Packet Injection` makes Npcap inject packets to the loopback interfaces.
- `Libpcap` API support is very useful where popular applications like Wireshark, tcpdump can use Npcap easily like a native application.
- `WinPcap` compatibility is another useful compatibility feature for Npcap.
Npcap Versions
Npcap is an open source project and provided free for most cases. But as an open source project, it needs some support for costs. So Npcap provides as 2 versions for open source and commercial use
- Opensource Npcap source code can be downloaded, compiled and used for internal use.
- Npcap OEM Commercial license is provided with enterprise features like silent installer and commercial support. With Npcap OEM commercial license npcap can be redistributed with different products and libraries.
Npcap can be downloaded from the following URL. The latest version of the Npcap is 0.996 .
https://nmap.org/npcap/dist/npcap-0.996.exe
Install Npcap
Windows 10 operating systems provide SmartScreen as a security measure. We can bypass SmartScreen check by clicking Run in the following window.
As Npcap requires access to the system functions the installation requires Administrative privileges with the following screen in order to start the installation. We will simply click Yes.
If there is an already install Npcap version it will be uninstalled automatically with the following screen.
In the following screen, we will accept the License Agreement of Npcap by clicking I Agree
The most important part of the Npcap installation is the following screen where we will set and provide installation options.
- `Support loopback traffic` will provide support for Loopback adapter packet capture and injection which will create a Npcap Loopback Adapter.
- `Restrict Npcap driver’s access to Administrators only` will secure access to npcap packet capture to Administrative users
- `Support raw 802.11 traffic for wireless adapters` will add wireless traffic capture support with IEEE 802.11 protocols
- `Install Npcap in WinPcap API-compatible Mode` will set fully WinPcap compatibility.
The installation will take a little time to complete.
When the Npcap installation is completed successfully we will see the following screen.
Print Npcap Service Status
Npcap is installed as a driver with a service. In order to capture packets, the Npcap service should be working. The service is named as npcap and we can print or display service status from the command line with sc command. We will open an MS-DOS or PowerShell with Administrator privileges like below.
Windows CMD.exe or Command Shell Tutorial with Examples
> sc query npcap
We can see that the npcap service status is currently running.
Start Npcap Service
We can also start Npcap service with the sc command like below. This operation also requires Administrative privileges.
> sc start npcap
Stop Npcap Service
We can stop Npcap service with the sc command like below. This operation also requires Administrative privileges.
> sc stop npcap
nmap / npcap
Goto Github
PK
View Code? Open in Web Editor
NEW
145.0
474.0
12.06 MB
Nmap Project’s Windows packet capture and transmission library
Home Page: https://npcap.com
License: Other
C++ 36.27%
C 59.80%
Makefile 0.47%
Batchfile 1.72%
HTML 0.05%
PowerShell 1.68%
packet-capture
windows
npcap’s Introduction
Npcap is a packet capture and injection library for
Windows by the Nmap Project. It is a complete update to
the unmaintained WinPcap project with improved
speed, reliability, and security.
Documentation
The complete documentation for Npcap is available in the Npcap
Guide on npcap.com. There you
will find information about
installation,
reporting
bugs,
developing software with
Npcap, and Npcap
internals.
Downloads
The latest installer, Software Development Kit (SDK), source, and debug symbols
can be downloaded from https://npcap.com/#download
Bug report
Please report any bugs or issues about Npcap at: Npcap issues on
GitHub. In your report, please provide
your
DiagReport
output, user software version (e.g. Nmap, Wireshark), reproduce steps and other
information you think necessary. Refer to the Npcap Guide section on reporting
bugs for more
complete directions.
License
The Npcap License allows
end users to download, install, and use Npcap from our site for free on up to 5
systems (including commercial usage). Software providers (open source or
otherwise) which want to use Npcap functionality are welcome to point their
users to npcap.com for those users to download and install.
We fund the Npcap project by selling Npcap OEM. This
special version of Npcap includes enterprise features such as the silent
installer and commercial support as well as special license rights.
Contact
[email protected](Nmap development list, for technical issues and discussion)[email protected](Sales address for commercial/licensing issues)- Npcap Issues Tracker
npcap’s People
npcap’s Issues
npcap stops EtherNet/IP responses
Hello
I am using Wireshark with npcap on Windows 7 to develop an EtherNet/IP client application. Setup is as follows: My development PC -> VPN into the office -> EtherNet/IP Device connected to network. I have been using Npcap 0.99-r8 and Npcap 0.99-r7 — the issue is the same.
Test scenario:
- Start test application, send any EtherNet/IP request packet (e.g. List Identity, using UDP unicast)
=> Response is successfully received - Start WireShark witn NPcap driver, select appropriate NdisWan Adapter.
- Send any EtherNet/IP request packet (e.g. List Identity, using UDP unicast)
=> Request packet can be seen in Wireshark, but no response.
=> Subsequent request packets can be seen in Wireshark, but no response. - Stop logging or Exit WireShark
- Send any EtherNet/IP request packet (e.g. List Identity, using UDP unicast)
=> Response is successfully received
I use my own EtherNet/IP client software or the free Molex EtherNet/IP tool, which is great for showing this issue. Download: https://www.molex.com/mx_upload/superfamily/iccc/EtherNet_IPTool.html
Usage: Start tool, stay on first tab (List Identity), Message Type ‘Unicast’, enter IP address of target device, press ‘Send List Identity Request on UDP’. If successful, ‘Station’ (device) will show up in the frame to the right, otherwise not.
Thanks.
Npcap0.9983 — windows 10 insider GSOD
Last several versions of Windows 10 Insider 20H1 have been causing GSOD with kernel access violations.
When I try to start wireshark and it gets the interfaces will GSOD.
minidump.txt
DiagReport-20191011-111305.txt
Npcap Bug Report
I installed npcap with Nmap; however, it doesn’t seem to be working for either Wireshark or Nmap. In Nmap I get a failed to open lo0 and in Wireshark there are no interfaces. In Nmap I simply tried to scan my ip with the default settings. In Wireshark I only opened the program. I would expect the scan to return some kind of results and for Wireshark to find my adapters. My e-mail is [email protected]. I look forward to any help you may be able to provide.
DiagReport-20191013-220531.txt
Npcap 0.992 — Duplicate packets
I’m seeing a similar problem seen in the closed issue nmap/nmap#1055.
Basically I’m seeing duplicated outbound packets in Wireshark with Npcap. I do not see the issue when using WinPcap. The person who posted issue nmap/nmap#1055 said that toggling the Npcap driver on the network adapter would temporarily fix the issue, however, this does not seem to work for me. When viewing in Wireshark, the timestamps of the duplicated packets are a few nanoseconds apart. The receiving end does not see the duplicate packets, so it’s not actually transmitting them. I’ve seen the issue on multiple machines and Npcap versions, but my current setup is:
Npcap 0.992
Windows 10 1809
Wireshark 3.0.1
Npcap: handle NDIS status notifications
Npcap does not currently do anything with NDIS status notifications, which NDIS documentation states are a more efficient means of obtaining information than issuing OID requests. Furthermore, OID requests may be returned without an answer, with the answer coming later in a status notification.
Mishandling of status notifications is implicated in connectivity problems on Win7: See nmap/nmap#1998 (comment)
Add tcpdump to Npcap installer
The main Windows tcpdump port is currently windump.exe by the WinPcap folks. But like winpcap, it hasn’t been updated in years and isn’t really maintained. It also doesn’t work with our Npcap because it relies on a too-old libpcap. But the changes to make current tcpdump work on Windows with Npcap are minor (we’ve done it in initial testing) and a lot of us still love tcpdump (even though it doesn’t hold a candle to the amazing Wireshark feature-wise).
So the thought is that we should probably make a tcpdump.exe that uses Npcap (submitting any needed changes upstream for hopeful incorporation) and then we could include that as an optional (install by default) checkbox component. It would be useful both to everyone who appreciates tcpdump for Windows, and also handy as a quick check that an Npcap install is working. The tcpdump builds we have been making are less than 1mb, so fairly immaterial space wise. And of course people can choose not to include it in the install by unchecking or using command line installer option if desired.
Npcap: use granular ACL to control access to capture/injection
Currently (Npcap 0.9984), Npcap can only control access to capture and inject at the device level, where the device is the special name and handle that the Npcap driver creates on the system, through which Packet.dll requests handles based on network interface name/GUID. In order to increase security, Npcap offers «Admin-only mode,» which uses SDDL for Device Objects to restrict access to users with Builtin Admin privilege. This requires UAC elevation and applies to all Npcap functions on all interfaces. It is not possible to grant access to individual users or groups.
Instead of relying on device-level access control, Npcap could check the calling user’s security identifier against a fully-featured ACL within the IRP_MJ_CREATE handler. This could enable us to do very specific access control like «Members of the Npcap Read domain group can do packet capture on these interfaces, but not packet injection.»
Challenges:
- Where and how should the ACL be stored? Probably the Registry, but need specifics and format.
- How should system admins update or modify the ACLs? Probably a helper program, but it would be best to use existing Windows APIs and dialogs for identifying principals and editing ACEs.
- Synchronization between Registry and running driver, avoiding race conditions.
NPCAP 0.99-r7 capture filter incorrectly ignores egress traffic when filtering on packet contents
Version Information
OS: Windows 10 Pro, version 1803, build 17134.556
NPCAP: 0.99-r7, tested and confirmed on 0.99-r8 as well
Current Behavior
When capturing traffic with Wireshark (with NPCAP 0.99-r7 installed as a dependency) while utilizing a capture filter that filters based upon packet data, egress traffic sourced from the local machine that should pass through the filter without issue does not pass through the filter. When capturing traffic without a capture filter that filters based upon packet data, egress traffic sourced from the local machine appears without issue.
An example of a capture filter that filters based upon packet data is as follows:
In the compressed file attached to the bottom of this issue are two PCAPs captured on my computer (IP of 192.168.10.50):
- npcap_broken_udp_capture_filter_with_data_filter.pcapng — Hereafter called «broken_udp», this capture utilized the above capture filter
udp[8:2] & 0xf = 1 - npcap_working_udp_capture_filter.pcapng — Hereafter called «working_udp», this capture utilized
udpas a capture filter
Both PCAP files result from captures taken at close to the exact same time. For reference, the first packet in «broken_udp» is the 217th packet in «working_udp» (almost exactly the same arrival time and epoch timestamp, and the rest of the packet is identical.) As you can see, all of the traffic in «broken_udp» is destined to my computer at 192.168.10.50, while «working_udp» has a considerable amount of traffic sourced from 192.168.10.50 that does not show up in «broken_udp».
One example of a packet in «working_udp» that should have been captured in «broken_udp» is packet 219 in «working_udp» (source 192.168.10.50, destination 69.47.158.237). The Message Type field in the STUN header has a value of 0x0001, which should be matched by the udp[8:2] & 0xf = 1 capture filter. However, this packet does not appear in the «broken_udp» PCAP.
These PCAPs demonstrate the current behavior with UDP, but I was able to reproduce the same behavior with a TCP capture filter as well. If you use the capture filter tcp[32:2] & 0xf = 1, only traffic that ingresses the machine will be displayed. Utilizing bit masks is not necessary to reproduce the behavior, either — I attempted to use a capture filter of udp[8:2]==0x0001 and encountered the current behavior as well.
Expected Behavior
Expected behavior is for a capture filter that filters based upon data within the packet itself to capture traffic in both ingress and egress directions.
Additional Troubleshooting
I believe this is an issue with NPCAP 0.99-r7/r8 because this issue did not exist when WinPCAP v4.1.3 was installed on my computer. @vaindil originally encountered this issue when he was running NPCAP 0.99-r7, and we were puzzled over how the same capture filter yielded different results on our different computers. The biggest relevant difference between our machines was that he was using NPCAP, while I was using WinPCAP. When I uninstalled WinPCAP and NPCAP 0.99-r7, I was able to reproduce this issue.
A DiagReport is also included in the compressed file uploaded to the bottom of this issue.
Please let me know if you need any additional information about this issue!
npcap_issue.zip
Add ARM64 Win10 Support to Npcap
We are considering adding Windows 10 ARM64 support to Npcap. With that, we would support all 3 Windows 10 architectures. Windows 10 ARM64 is a new (released in late 2017) system that is used on some more portable laptop/tablet devices like the Samsung Galaxy Book 2. @pmsjt from Microsoft has already done and tested an initial port and submitted it as a pull request here: #18 .
Having ARM64 Npcap should enable Nmap to work on these ARM64 devices too, which would be nice.
We’re wondering how much Nmap/Npcap user interest there is in supporting Windows 10 ARM64? If it is something you want for a specific reason, please comment and describe your use case, including any particular devices you’d want to make sure are supported. Based on the responses, we’ll decide whether to buy some ARM64 hardware and get to work. Thanks!
Npcap rpcapd SERVER support
Hi there,
I gave a try at rpcapd (via WinPCAP on Windows and libpcap master on Linux) and it seemed to fit our usage nicely. It seems broken (it probably worked one time out of ten and when it doesn’t it reports some number of packets but won’t forward them) on Windows 2016 (and probably Windows 10 from some reports I saw) but works fine on Windows 2012.
I quickly looked at different mailing lists & issues trackers hoping the problem was already reported or known and I stumbled on npcap.
WinPCAP seems frozen and I don’t have much hope to make it work out the box without probably having to debug/recompile it (and I’ll probably have issues later since I won’t be able to sign it? I’m not well versed in Windows development, sorry :)).
Installing npcap in WinPCAP compatibility mode will make rpcapd.exe simply quit immediately and there doesn’t seem to be an rpcapd server embedded with npcap.
Do you have any plans to provide rpcapd (which is now available from libpcap with configure --enable-remote) and the corresponding service or do you have any clue why npcap’s compatibility mode seems to make rpcapd.exe from WinPCAP exit?
Thanks!
Regards.
Update Issue / Bug
Just updated to version 3.2 and installed npcap in the process. Had a version running ok with WinPCap. Windows 7 x64. After successful install no adapters listed. Have reinstalled several times as well as cleaned old drivers/files, installed in safe mode, etc. I ran the fixinstall.bat inside the npcap directory and got an error:
The service name is invalid [SC] Open Service FAILED 1060: The specified service does not exist as an installed service see: net helpmsg 2185
Can’t seem to revert to old version. Have tried uninstalling and manually removing drivers.
Investigate skipping the step of adding Insecure.Com EV cert to Windows trust store in some cases
Right now we sign Npcap release installers with our extended validation (EV) codesigning certificate, which we also use to sign the drivers. Since the Insecure.Com (formal Nmap Project company name) is of course not trusted by Windows by default, it pops up a warning asking the user whether to trust it and install the software. Assuming the user asks to do this, we load the certs into the trust store before installing the driver to prevent this scary warning from happening again. One down side we’ve seen is that users with certain monitoring apps create alert when an already-expired cert is loaded into the trust store. It is still legitimate to do so since codesigning certs only need to be used for SIGNING during their validity dates. It’s OK for software to check the signature later. However, we might be able to remove the cert-loading step on Windows 10 since we now use Microsoft attestation-signing. Since we have a valid attestation-signature, users don’t get the driver install warning anyway. Removing this step might also make the software install finish more quickly. We don’t use attestation-signing for Windows 8 and older because those systems don’t support it, so we might want to still keep the trust store load for those.
Npcap not able to capture the out packets of PC Ethernet
I am using the npcap-0.996 version, trying to capture the out packets of the PC of particular adapter.
I opened the pcap session in promiscuous mode with the pcap_open function and reading the packets continuously by pcap_next_ex function. Able to read the incoming packets but not able to read the out packets.
Can Npcap use KeQuerySystemTimePrecise() if running on Windows 8 or later?
Somebody complained about packet time stamps drifting from system time with WinPcap on Windows 10.
WinPcap has, at least on 32-bit Windows, a registry parameter HKLMSystemCurrentControlSetServicesNPFTimestampMode that controls how time stamps are generated:
- 0 (default) -> Timestamps generated through KeQueryPerformanceCounter, less reliable on SMP/HyperThreading machines, precision = some microseconds
- 2 -> Timestamps generated through KeQuerySystemTime, more reliable on SMP/HyperThreading machines, precision = scheduling quantum (10/15 ms)
- 3 -> Timestamps generated through the i386 instruction RDTSC, less reliable on SMP/HyperThreading/SpeedStep machines, precision = some microseconds
There also appears to be a setting of 1, the symbol for which in time_calls.h is TIMESTAMPMODE_SYNCHRONIZATION_ON_CPU_WITH_FIXUP, and a setting of 99, the symbol for which is TIMESTAMPMODE_SYNCHRONIZATION_ON_CPU_NO_FIXUP.
It looks as if, on 64-bit Windows, the RDTSC version isn’t supported.
From a quick look at the Npcap driver, it seems to behave similarly, although the NT GET_TIME() code went from
#ifdef _X86_
if ( TimestampMode == TIMESTAMPMODE_RDTSC )
{
GetTimeRDTSC(dst,data);
}
else
#endif // _X86_
if ( TimestampMode == TIMESTAMPMODE_QUERYSYSTEMTIME )
{
GetTimeQST(dst,data);
}
else
{
GetTimeKQPC(dst,data);
}
in WinPcap to
#ifdef _X86_
if (g_TimestampMode == TIMESTAMPMODE_RDTSC)
{
GetTimeRDTSC(dst, data);
}
else
#endif // _X86_
if (g_TimestampMode == TIMESTAMPMODE_QUERYSYSTEMTIME)
{
GetTimeQST(dst, data);
}
else
{
GetTimeKQPC(dst, data);
}
on Npcap — the mis-indentation of the #endif makes it less clear that modes 0 and 2 are still supported.
If a mode were supported in which KeQuerySystemTimePrecise() were used, at least on Windows 8 (and its server variant) and later, that would provide a mode that 1) gives high-resolution time stamps and 2) doesn’t drift from the system clock, although it might be more costly than using KeQueryPerformanceCounter(). (And if it’s not more costly, it’s probably the best mode on 64-bit Windows, given that RDTSC isn’t being used.)
Furthermore, given that there’s now a pcap_set_tstamp_type() in libpcap, having the time stamp type be per-pcap_t, rather than system-wide, might be useful. You’d offer a choice between:
PCAP_TSTAMP_HOST— this would useKeQuerySystemTime()prior to Windows 8 andKeQuerySystemTimePrecise()on Windows 8 and later, and would always be available (it’s the default in libpcap);PCAP_TSTAMP_HOST_LOWPREC— this would always useKeQuerySystemTime(), and would be always be available;PCAP_TSTAMP_HOST_HIPREC— this would always useKeQuerySystemTimePrecise(), and would only be available on Windows 8 and later.
If the other time stamp types are useful, we could add new PCAP_TSTAMP_ types for them, and make them available only on Windows (the PCAP_TSTAMP_ADAPTER types are available only on Linux — and they have a number of problems, not the least of which is that they give time as seconds since January 1, 1970, 00:00:00 TAI with at least some adapters; don’t get me started on UN*X time stamps and leap seconds…).
Packet.dll routines should report errors if the service can’t be started or the helper process can’t be run
I was trying to debug a problem where libpcap’s findalldevstest program wasn’t returning any interfaces; the problem is that I needed to copy the helper executable into the run/Debug subdirectory of my libpcap build directory.
If:
NpcapStartHelper()were to return FALSE if the helper needed to be started but couldn’t be started, and TRUE otherwise;PacketOpenAdapterNPF()were to return NULL if NpcapStartHelper()` returned FALSE;PacketAddAdapterIPH()andPacketAddAdapterNPF()were to return FALSE forPacketOpenAdapterNPF()returning NULL and the error being any of theShellExecuteExA()errors that mean «the helper couldn’t be started» rather than meaning «there is no such adapter»;PacketGetAdaptersIPH(),PacketGetAdaptersNPF(), andPacketUpdateAdInfo()were to return FALSE if the correspondingPacketAddAdapterXXX()routine failed with one of those errors;PacketPopulateAdaptersInfoList()were to do the same, and return a success/failure Boolean;
that would, I think, allow this.
This would also allow pcap_activate_npf() to return PCAP_ERROR_PERM_DENIED if a program tries to open an adapter, Npcap is in admin-only mode, and the user says «No» to the UAC prompt — and would also allow any future device-enumerating APIs to do so as well.
Remove duplicate Npcap Loopback Adapters created by earlier Npcap versions
Npcap versions 0.95 through 0.995 had an uninstaller problem where they didn’t always correctly remove the «Npcap Loopback Adapter» that the installer creates. So systems could collect extra versions, since each upgrade during that time would add a new one without deleting any. I found I had 23 and it was bogging down Nmap scan times and Wireshark adapter listing times, mostly because adapter listing is not currently very efficient (see issue nmap/nmap#1551 ). Npcap versions 0.996 and later properly remove the loopback adapter when they uninstall, but they don’t (yet) remove any old duplicate adapters left by 0.95 and 0.995 uninstalls/upgrades. It would be nice to add a feature to the uninstaller to remove ALL old Npcap Loopback Adapters when detected rather than just the latest one. But it’s not quite as easy as expected because the trick is finding the appropriate one by index or GUID. There are several different registries of adapters, and the one with the «Npcap Loopback Adapter» description isn’t the one that NPFInstall currently uses to remove the adapter. So it’s something like: go through all the adapters by description, finding the GUIDs of the ones we want to remove. Then go through all the adapters by index, finding the ones that match one of the guids we want to remove, and remove it.
IN THE MEANTIME, users can manually remove any old loopback adapters by opening device manager (press Windows key and type «device manager»), then expand the «Network adapters» item, then, if there is more than one «Npcap Loopback Adapter», right click on them each and choose «uninstall device». Then reinstall Npcap so you get a proper one recreated. If you only have one «Npcap Loopback Adapter» and you aren’t having any problems with it, then no need to delete anything as you don’t have extras.
Suricata IDS problems (pcap_dump_fopen) with recent Npcap versions
Update: Our suspicion is that this libpcap change may be the cause of the problem. Since libpcap changed the function into a compiler macro, code which uses it will need to be recompiled with latest headers (such as Npcap SDK) in order to continue using it. We may want to talk to Suricata folks about using newer headers for next version. This could also be a good chance for them to update to native Npcap API, if desired.
I haven’t fully investigated this yet, but am hearing reports of people having trouble running the free and open source Suricata IDS with recent versions of Npcap, even when older versions worked. There is an example report here or the error «can not find pcap_dump_open». I am checking whether there are other error messages. The person who reported it to me said that he had enable WinPcap compatability mode (which is apparently requried for Suricata to use Npcap). I installed Suricata 4.1.5 and did not see the WinPcap DLLs in the Suricata directly, but it’s possible they were installed somewhere else. I haven’t tried running it quite yet. We should test with Suricata and/or communicate with the project to ensure solid Npcap support. Ideally, Suricata would support Npcap native mode (it could still support Winpcap too).
Faulty uninstall
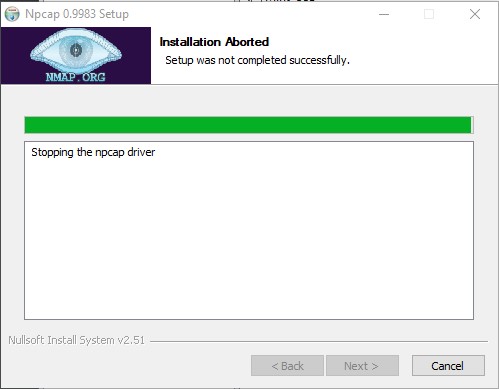
During a recent install of Wireshark on Win10 I selected the «Restrict Npcap driver’s access to Administrators only» option. However, opening Wireshark caused a bunch of repeated UAC prompts to be triggered. I can’t remember the exact next sequence of events, but I eventually tried to reinstall npcap with that box unchecked. I remember the uninstall reporting success, but all attempts to reinstall with the standalone 0.9983 now fail:
I went on an npcap purge and manually deleted every reference to it that I could find: the Program Files folder that still existed, the loopback driver in device manager, all the .dll files for it, several registry keys referencing the drivers, and probably a few other things that I can’t remember. Install still fails at this screen.
I reinstalled Wireshark several times, and each time it detects that the 0.9982 is still installed. I went so far as to look at the source code that Wireshark uses to detect whether it’s already installed and found that it opens up a specific registry key. However, when I try to look that key up in RegEdit it doesn’t even exist. So I have no idea why Wireshark thinks it’s still installed or why the standalone installer just aborts when trying to stop the npcap driver.
Any help would be appreciated.
Npcap installation aborted
Hello there. I tried to install Npcap per warning message I received during Azure ATP sensor installation steps. I removed the WinPcap via Windows control panel, and proceeded to install the Npcap with the following options: loopback_support=no & winpcap_mode=yes.
Unfortunately, the Npcap install process failed and I gathered the logs and screen shot for further review. Any guidance or support/assistance is greatly appreciated. Let me know please. Thank you.
[NPFInstall.log](https://github.com/nmap/nmap/files/3911535/NPFInstall.log)
[install.log](https://github.com/nmap/nmap/files/3911536/install.log)
example with sendpack project not work properly
I use master libpcap and packetdll ,and compile sendpack project ,but the sendpack project funtion pcap_sendpacket works fine howerver I can’t capture packets with wireshark on the same NIC
dnet: Failed to open device eth6 QUITTING!
Hi,
I got error when trying nmap
dnet: Failed to open device eth6 QUITTING!
I tried to reinstall my Npcap but still didnt work
~#nmap -v
Starting Nmap 7.80 ( https://nmap.org ) at 2019-09-20 17:12 SE Asia Standard Time
Read data files from: C:Program Files (x86)Nmap
WARNING: No targets were specified, so 0 hosts scanned.
Nmap done: 0 IP addresses (0 hosts up) scanned in 0.22 seconds
Raw packets sent: 0 (0B) | Rcvd: 0 (0B)
~#Npcap version : 0.9983
~#Windows 10 Pro 64 bit
`nmap --iflist
Starting Nmap 7.80 ( https://nmap.org ) at 2019-09-20 17:11 SE Asia Standard Time
************************INTERFACES************************
DEV (SHORT) IP/MASK TYPE UP MTU MAC
eth0 (eth0) fe80::bd3a:9069:1aa7:7d41/64 ethernet up 1500 02:00:4C:4F:xx:xx
eth0 (eth0) 169.254.125.65/16 ethernet up 1500 02:00:4C:4F:xx:xx
eth1 (eth1) fe80::9e1:3379:6e48:eadf/64 ethernet up 1500 0A:00:27:00:xx:xx
eth1 (eth1) 192.168.56.1/24 ethernet up 1500 0A:00:27:00:xx:xx
eth2 (eth2) fe80::2996:ca5c:784c:526c/64 ethernet down 1500 AC:B5:7D:06:xx:xx
eth2 (eth2) 169.254.82.108/16 ethernet down 1500 AC:B5:7D:06:xx:xx
eth3 (eth3) fe80::116a:4787:4dec:44fc/64 ethernet down 1500 1E:B5:7D:06:xx:xx
eth3 (eth3) 169.254.68.252/16 ethernet down 1500 1E:B5:7D:06:xx:xx
eth4 (eth4) fe80::a046:9f43:cdb1:ba6d/64 ethernet down 1500 2E:B5:7D:06:xx:xx
eth4 (eth4) 169.254.186.109/16 ethernet down 1500 2E:B5:7D:06:xx:xx
eth5 (eth5) fe80::f1ef:e8ff:2d49:a0e5/64 ethernet down 1500 5E:B5:7D:06:xx:xx
eth5 (eth5) 169.254.160.229/16 ethernet down 1500 5E:B5:7D:06:xx:xx
eth6 (eth6) fe80::1c3f:c7c1:7b7d:1b97/64 ethernet up 1500 F0:76:1C:37:xx:xx
eth6 (eth6) 192.168.41.117/24 ethernet up 1500 F0:76:1C:37:xx:xx
eth7 (eth7) fe80::1da8:60a7:b42e:211/64 ethernet down 1500 00:FF:66:C0:xx:xx
eth7 (eth7) 169.254.2.17/16 ethernet down 1500 00:FF:66:C0:xx:xx
lo0 (lo0) ::1/128 loopback up -1
lo0 (lo0) 127.0.0.1/8 loopback up -1
DEV WINDEVICE
eth0 <none>
eth0 <none>
eth1 <none>
eth1 <none>
eth2 <none>
eth2 <none>
eth3 <none>
eth3 <none>
eth4 <none>
eth4 <none>
eth5 <none>
eth5 <none>
eth6 <none>
eth6 <none>
eth7 <none>
eth7 <none>
lo0 <none>
lo0 <none>
<none> DeviceNPF_Loopback
**************************ROUTES**************************
DST/MASK DEV METRIC GATEWAY
255.255.255.255/32 eth4 281
255.255.255.255/32 eth0 281
255.255.255.255/32 eth3 281
255.255.255.255/32 eth5 281
255.255.255.255/32 eth2 281
169.254.125.65/32 eth0 281
169.254.255.255/32 eth0 281
255.255.255.255/32 eth1 281
192.168.56.255/32 eth1 281
192.168.56.1/32 eth1 281
192.168.41.117/32 eth6 291
192.168.41.255/32 eth6 291
255.255.255.255/32 eth6 291
255.255.255.255/32 eth7 311
255.255.255.255/32 lo0 331
127.255.255.255/32 lo0 331
127.0.0.1/32 lo0 331
192.168.56.0/24 eth1 281
192.168.41.0/24 eth6 291
169.254.0.0/16 eth0 281
127.0.0.0/8 lo0 331
224.0.0.0/4 eth3 281
224.0.0.0/4 eth4 281
224.0.0.0/4 eth5 281
224.0.0.0/4 eth2 281
224.0.0.0/4 eth1 281
224.0.0.0/4 eth0 281
224.0.0.0/4 eth6 291
224.0.0.0/4 eth7 311
224.0.0.0/4 lo0 331
0.0.0.0/0 eth6 35 192.168.41.1
fe80::2996:ca5c:784c:526c/128 eth2 281
fe80::f1ef:e8ff:2d49:a0e5/128 eth5 281
fe80::bd3a:9069:1aa7:7d41/128 eth0 281
fe80::a046:9f43:cdb1:ba6d/128 eth4 281
fe80::9e1:3379:6e48:eadf/128 eth1 281
fe80::116a:4787:4dec:44fc/128 eth3 281
fe80::1c3f:c7c1:7b7d:1b97/128 eth6 291
fe80::1da8:60a7:b42e:211/128 eth7 311
::1/128 lo0 331
fe80::/64 eth1 281
fe80::/64 eth0 281
fe80::/64 eth4 281
fe80::/64 eth3 281
fe80::/64 eth5 281
fe80::/64 eth2 281
fe80::/64 eth6 291
fe80::/64 eth7 311
ff00::/8 eth4 281
ff00::/8 eth0 281
ff00::/8 eth1 281
ff00::/8 eth2 281
ff00::/8 eth5 281
ff00::/8 eth3 281
ff00::/8 eth6 291
ff00::/8 eth7 311
ff00::/8 lo0 331`
pcap_open() not documented as part of the Npcap API
pcap_open() is one of the WinPcap extensions to the libpcap API. It is currently included in upstream libpcap, but there is no documentation there. We generally document such functions in the Npcap API section of the Npcap Guide, but this one is not documented.
Npcap Bug Report — Can’t Get the LinkSpeed
- Use the WinPCap 4.1.3
I can retrieve the network speed with the following code. - Use the current Npcap «npcap-0.9984.exe»
There are 12 adapters in my win7 system.
But only 1 adapter’s link speed can retrieved.
Following are all the adapters:
1 — DeviceNPF_Loopback, speed = 10000000
2 — DeviceNPF_{ D2F5FDB8 — 026D — 4E3C — 9603 — E0847AF4A334 }, speed = 0
3 — DeviceNPF_{ 35E23E0A — 1D3B — 4BA8 — B1A3 — BFB5D407AFB1 }, speed = 0
4 — DeviceNPF_{ A656415F — 88BE — 4CD1 — 8596 — C736CAFF67AC }, speed = 0
5 — DeviceNPF_{ 23BD7BB6 — 5321 — 441B — 903A — 27418CBC8569 }, speed = 0
6 — DeviceNPF_{ F37FB154 — 95B3 — 4047 — AA98 — F75C3DEC5285 }, speed = 0
7 — DeviceNPF_{ A05D7D3F — 257C — 4D2F — 867A — E821A94B548C }, speed = 0
8 — DeviceNPF_{ 78032B7E — 4968 — 42D3 — 9F37 — 287EA86C0AAA }, speed = 0
9 — DeviceNPF_NdisWanIp, speed = 0
10 — DeviceNPF_{ 4D3329D0 — 7D57 — 4385 — AB76 — 5AA0280929A1 }, speed = 0
11 — DeviceNPF_NdisWanBh, speed = 0
12 — DeviceNPF_NdisWanIpv6, speed = 0
My Code:
LPADAPTER lpAdapter = PacketOpenAdapter(PCHAR AdapterName);
NetType param;
PacketGetNetType(lpAdapter, ¶m);
uint64_t speed = param.LinkSpeed;
Npcap: pcap_findalldevs is very slow
Users are complaining about Wireshark taking a long time to populate the list of adapters, even going so far as to suggest turning off Npcap when using Wireshark for reading pcap files. This shouldn’t take so long.
The most promising idea so far is: Don’t try to open each adapter as it is found (PacketOpenAdapter) in order to determine if it is supported. Packet API docs (unpublished) indicate that PacketGetAdapterNames is supposed to only return supported adapters, but I don’t know if anything relies on that. Need to check libpcap to see, since that’s the primary consumer of that API.
Npcap should perhaps not report a zero RSSI value
It appears that, for some devices, the signal strength is reported as 0 dBm; this probably means that the device doesn’t report the signal strength, not that the signal strength was 1 milliwatt.
See, for example, this ask.wireshark.org question.
NPcap: C:npcap-sdk-0.1Include
Yeah,
Your team has hard-coded the npcap include paths. Please change them to use a relative path.
Npcap buffer sizes are not well-documented
Npcap Guide does not have good documentation of the interaction between the sizes of the kernel buffer, the user buffer, and the number of CPU cores. This information is vital to proper tuning of performance. A brief description follows, which could be used to begin the appropriate documentation:
The Npcap driver stores captured packets in a circular buffer until they are retrieved (pcap_next_ex(), pcap_dispatch(), pcap_loop(), PacketRecievePacket()) by the user program. Each adapter handle (pcap_t or ADAPTER) has its own buffer, the size of which is set via pcap_set_buffer_size(), pcap_setbuff() (deprecated WinPcap extension), or PacketSetBuff(), and which defaults to 1MB. The buffer is split into a number of independent segments according to the number of processors on the system. When a packet is received by the driver, it is put into the buffer segment corresponding to the driver thread’s current processor. If there is not enough room in that segment, the packet is dropped.
A user program receives packets into a «user buffer» which is passed to PacketRecievePacket(). The driver empties packets from its own buffer segments in the order they were received until it runs out of space in the user buffer or runs out of packets to return. A large user buffer can ensure the kernel buffer is emptied more quickly, preventing packet drops. The libpcap API (wpcap.dll) configures the size of this user buffer via pcap_setuserbuffer(), which defaults to 256KB.
The current behavior of splitting the buffer into number_of_processors segments is flawed, as described in nmap/nmap#1967, but it needs to be documented anyway, since it’s how WinPcap did things, minus the mapping of processor numbers greater than 63 to 63. We can rewrite the documentation if and when we change the behavior.
Fix network disruption during Npcap install on 802.1x authenticated networks
We have received reports from 2 users of 802.1q authenticated networks that their Wifi connection was disrupted during Npcap install until they re-authenticated to rejoin the network or just rebooted their system. We don’t yet know if all 802.1q authenticated networks are similarly disrupted or if it was something specific to these particular networks/systems.
This issue is partially created as a call out for people to report if they are experiencing this issue or not. That will help us decide how to prioritize the issue and figure out what the cases might have in common besides 802.1q. Please let us know what version of Windows you are running too.
Obviously the best fix would be to prevent the network disruption in the first place, but that may be difficult if it is a bug/characteristic of how Windows handles the loading of WFP drivers. In the meantime, we are looking at creating a «/start_driver_now =no» install option that prevents the Npcap driver from loading until the next reboot. That means Npcap functionality won’t be available until then either, but it may be better than risking even temporary network disruption on a running system.
Should there be a guide for people doing development on Npcap?
I’m trying to figure out how to profile a test program (it runs pcap_findalldevs() many times, to try to figure out where the CPU time is going), but apparently this may require 1) .pdb files for wpcap.dll and packet.dll and 2) might also require building the libraries with /PROFILE.
Should there be a guide for people doing development work on Npcap itself, indicating how to set up the development environment? It might belong in the «Npcap internals» documentation.
npcap uninstall fails with wlanhelper in interactive mode
This is just a minor thing — if npcap is reinstalled it de-installs the previous version. This fails if wlanhelper.exe is still running in interactive mode, for obvious reasons. Maybe a check could be added to see if wlanhelper is still running and prompting for a close, just like it does for wireshark.exe?
Wifi adapter interference
On a HP EliteBook 840 G2 , Windows 10, few days after npcap is installed I always have to turn off npcap loopback adapter in order to use wifi to connect to router, it turns off by itself, clicking on turn on wifi manually lasts for half a second and then goes off again. This does not happen imediatelly right after I install npcap but a few days after.
Outbound packets sent but not captured, or duplicated
Problem
When using Wireshark, inbound packets are displayed but outbound packets are not displayed.
Environment
- Windows 8.1.1 x64
- Wireshark 3.0.1 (also tested with 2.x)
- Npcap 0.995
Details
An application is using the WinPcap 4.1.3 SDK to send and receive raw ethernet frames.
With WinPcap 4.1.3 actually installed, this works as expected (all packets are sent and received correctly, and using Wireshark on the interface sending the packets shows both the inbound and outbound packets).
With Npcap 0.995 installed (in WinPcap compatible mode), the packets are sent and received correctly but Wireshark (on the sending interface) only shows the inbound packets, not the outbound packets.
The Wireshark configuration is the same between these two cases; the only change is to uninstall one capture library and install the other.
Possibly of note (but probably unrelated) is that with Npcap installed the network interface shows bindings to NPF and NPCAP, but with WinPcap installed these do not appear. Unticking these causes Wireshark to not capture anything at all.
What Visual Studio version should *libpcap* make the minimum required version?
Currently, I’ve been trying to allow it to work with VS 2013, although I can’t guarantee that I’ve succeeded there.
The npcap README.md says, as of the time I’m filing this issue, that:
The DLLs need to be built using Visual Studio 2013. And the driver needs to be built using Visual Studio 2015 with Windows SDK 10 10586 & Windows Driver Kit 10 10586.
Does «the DLLs» include the libpcap DLL (npcap.dll or whatever it’s called)? If not, what VS version is it built with?
(If it requires VS 2015, including the VS 2015 runtime, or a later version, I can use snprintf() directly, and can use it to make an «generate a malloc()ed formatted string that’s large enough» routine and use that in some places, as long as I kick to the curb some older UN*X versions of snprintf() with non-C99 behavior, which I’m willing to do.)
Unknown error! 800f0203 Npcap LWF driver has failed to be installed.
Hi,
I got the below error when trying to install npcap on a win 2012r2 server.
Unknown error! 800f0203
Npcap LWF driver has failed to be installed.
Failed to create the npcap service for Win7, Win8 and Win10
May I check what is this error code about?
Thanks.
Dan.
Improve Npcap installer options documentation
The Npcap User’s Guide is awesome (IMHO), but it would be great to improve the installer option section. In particular, it would be nice to have a short section on each option which describes in more detail what it does. Right now there is just a one sentence description for each, but many of the options like /admin_only are more complex. Another thing we should cover is Npcap installer return codes, which is especially important for /S users.
Npcap extremely slowing down connectivity at boot WIN10
Hi,
at least in latest Windows 10 version with all patches applied npcap extremely, really extremely slows down connectivity at startup. I would not bother if we were talking about 5 seconds here, but I have to wait like 40-50 seconds on boot to get network connectivity as soon as npcap is installed.
It is not system specific, it is the same on my laptop with wireless as on my desktop with just Ethernet.
Installed :
driver not started at boot time…I don’t want that
and for the rest it makes absolutely no difference if
loopback yes/no,
compatibility mode yes/no,
admin restriction yes/no
it is just always the same, tried on 2 computers as said.
Waiting a minute is too much.
Any ideas here on what that could be or how to investigate? As said I don’t think it makes sense to investigate too deeply for a specific system computer problem
Thanks
Increase stack reservation size of NPFInstall.exe
According to @akontsevoy in nmap/nmap#1910, NPFInstall.exe should increase its stack reservation size. We should investigate this and make any necessary changes.
Error 8007007e while installing npcap
When I try to install Npcap every time i get this error:
In the details there was written
Unknown error! 8007007e
If i need to upload any files then just ask
I cant Uninstall Npcap and when i try to install it it instantly aborts
i just need to uninstall it and reinstall it to use wire shark on my network for school
For which Packet.dll calls can GetLastError() be used if the call fails?
Somebody reported a «failed to set hardware filter to promiscuous mode)» error; that comes from a PacketSetHwFilter() call, which ultimately does a DeviceIoControl() for NDIS adapters.
libpcap currently doesn’t call GetLastError() and report the error code as part of the error if if PacketSetHwFilter() fails. That might provide more useful debugging information.
Npcap: Suspending Windows interrupts network
Reported here: https://seclists.org/nmap-dev/2019/q1/89
On a Windows 10 laptop with VMware Workstation Pro 14.1.6, Npcap is running on the host OS but not on the Windows 10 VM. User suspends the VM, then hibernates the laptop. On wakeup, the VM has no network access until Npcap is uninstalled. Host OS is not affected.
Reported as affecting 0.99-r8 through 0.992.
duplicate sent-out packets seen on local Interface
I have the same problem As: duplicate sent-out packets seen on local Interface nmap/nmap#1055
My OS is windows 10. there are two PC has this problem.
When I uninstall antivirus program in one PC the problem solved.
but another PC has no antivirus program. I don’t know the reason.
NPCAP 0.996 No Network Access/No Valid IP?
I’ve googled this but can’t find anything and what I can find is total greek to me, so I’m posting it here.
I installed this, and rebooted my machine, but it doesn’t seem to be working? It’s listed in my adapters as being enabled, but isn’t in my active networks. It says there’s no network access and when I attempted to troubleshoot, it said there was no valid IP configuration.
I have no idea what any of this means, if it’s normal or how to fix it. Help?
npcap disables RSC (Receive Side Coalescing)
npcap installation causes RSC (Receive Side Coalescing) to be disabled with failure reason «NDISCompatibility». In this case, this is OS software RSC that was introduced in Win10 RS2. I believe that it is enabled by default for devices that do not supports RSC (in HW). Below is the output of «Get-NetAdapterRsc» before and after npcap installation:
PS C:> Get-NetAdapterRsc *
Name IPv4Enabled IPv6Enabled IPv4Operational IPv6Operational IPv4FailureReason IPv6FailureR
State State eason
Wi-Fi True True True True NoFailure NoFailure
PS C:> Get-NetAdapterRsc *
Name IPv4Enabled IPv6Enabled IPv4Operational IPv6Operational IPv4FailureReason IPv6FailureR
State State eason
Wi-Fi True True False False NDISCompatibility NDISCompa…
Npcap failed to install on Windows. 8007005
Support timestamp method selection by capture handle rather than registry key
Operating systems have various timestamp methods available with differing tradeoffs between granularity, accuracy, precision, efficiency, etc.
Npcap has an undocumented legacy method (inherited from Winpcap) for choosing this on a system-wide basis using TimestampMode registry key. It can be set to «0», «2», or «3»:
- 0 is the default and uses KeQueryPerformanceCounter. This provides great precision (some microseconds) but is less reliable on SMP/HyperThreading machines since it doesn’t return monotonic values across multiple CPUs.
- 2 uses KeQuerySystemTime instead, which is more reliable on SMP/HyperThreading machines, with a precision of a scheduling quantum (10/15 milliseconds)
- 3 uses the i386 RDTSC instruction. This is also less reliable on SMP/HyperThreading/SpeedStep machines and has a precision of some microseconds.
The registry location for this key depends on whether you are using Npcap native mode or Winpcap compatible:
- HKLMSystemCurrentControlSetServicesnpcapParametersTimestampMode if using Npcap native API mode (npcap driver)
- HKLMSystemCurrentControlSetServicesnpfParametersTimestampMode if using Winpcap compatible mode (npf driver)
It is probably best to just set both. Also note that even the Winpcap compatible location is a bit different than what Winpcap uses (which is HKLMSystemCurrentControlSetServicesNPFTimestampMode).
We have verified that this feature works with Npcap 0.9983, but we haven’t officially documented it because setting the timestamp mode system-wide is not a great approach. It could cause issues if multiple applications are using Npcap and each wants a different mode.
The better method that we might actually want to officially support uses the per-capture handle timestamp option as described here. That describes the options available on several platforms, but we don’t offer any non-default options through this API on Windows (Npcap). But we might, if we see demand for it. We created this issue both to document the current situation and also so folks can comment if the normal default mechanism doesn’t work well for them. Please also note what you would prefer and why. The more well-supported requests we get, the more we can prioritize this issue. We don’t waste time implementing a feature that nobody seems to want. And, at least for our Nmap Security Scanner, the default timestamp methods seem to be working well enough for us.
Wireshark is not able to see ethernet adapters after changing from WinPCAP to NPCAP on Windows server 2016
Wireshark is not able to see ethernet adapters after changing from WinPCAP to NPCAP on Windows server 2016 for Broadcom Netextreme Virtual Function ethernet adapter.
Attached is the Diagreport. I can reproduce on a fresh empty VM and provide remote access if desired.
C:Program FilesWireshark>dumpcap.exe -D
- DeviceNPF_Loopback (Adapter for loopback traffic capture)
C:Program FilesWireshark>
Network Adapter(s) Info:
Name InterfaceDescription ifIndex Status MacAddress LinkSpeed
Ethernet Broadcom NetXtreme-E Virtual Function 3 Up 00-00-17-02-79-0E 25 Gbps
Caption : [00000002] Broadcom NetXtreme-E Virtual Function
GUID : {CC75C87B-6F35-4560-8556-EA0329DA6CB7}
Index : 2
InterfaceIndex : 3
Manufacturer : Broadcom Corporation
NetConnectionID : Ethernet
PNPDeviceID : PCIVEN_14E4&DEV_16DC&SUBSYS_16D7108E&REV_003&13C0B0C5&1&18
diagreport.txt
Npcap 0.9990: Disrupts loopback connectivity/consumes whole core on WS2016
Greetings,
We have reports from multiple users that Npcap version 0.9990 intermittently disrupts connectivity on the loopback interface (causing connections made on 127.0.0.1 to time out). The issue seems isolated to Windows Server 2016, with isolated reports for WS2019. When it happens, the System process is seen to consume a whole CPU. The problem is resolved when Npcap is downgraded to 0.993 (the version we bundled previously). Has this been a known issue, possibly addressed in 0.9991? The similar issues I’m finding are either Windows 10 or Windows 7.
P.S. This happens despite our software not capturing anything from NPF_Loopback (not even opening a pcap handle on that adapter).
Y2038 problem in Npcap?
Npcap passes packets with a struct bpf_hdr header. The bh_timestamp member is a struct timeval which uses long as the type for tv_usec. This is the same as struct timeval that Windows defines in winsock2.h, and libpcap specifically states that this struct timeval is system-dependent. Packets captured after 19 January 2038 will appear to be captured in 1970. Fixing this issue will require coordination with the-tcpdump-group/libpcap.
npcap 0.992 prevents PPPoE from working
We have many Windows 7 installs and all of them have problems connecting with PPPoE when npcap is installed. I have tried 0.99-r7 and 0.992 version but the symptom is the same. If I uninstall the npcap and install winpcap 4.1.3 the problem disappears.
After installing npcap and trying to make a PPPoE connection an error window pops up with RAS error code 692: ERROR_PORT_OR_DEVICE, A hardware failure has occurred in the port or attached device. The second try shows a different RAS error code 813: ERROR_BROADBAND_ACTIVE, You have attempted to establish a second broadband connection while a previous broadband connection is already established using the same device or port. All other tries give the same error code 813.
Disabling npcap on the ethernet interface under the PPPoE connection doesn’t help. Stopping the npcap service does not help either. Another phenomena is something prevents Windows to be restarted, it stucks on the rebooting screen forever after the RAS error. Even the npcap uninstall stucks at 90% and never finishes after trying to use PPPoE. The uninstall log shows no problem, the last line is «Delete file: C:Program FilesNpcapFixInstall.bat». After restarting the computer the install.log contains more lines after this point. The last line shows «Jump: 76» and the service has removed.
The PPPoE connection should be established by the help of RAS. The computer is connected to a HGW with a 1 Gbps ethernet interface. The broadband connection is created in the Network Sharing Center:
- Set up a new connection
- Connect to the Internet
- Set up a new connection: WAN Miniport (PPPoE)
- Broadband (PPPoE)
- Enter username and password
I tried installing npcap with many different options, but none of them help:
- With or without WinPcap compatibility mode
- With or without Support loopback traffic
Windows Packet Capture
Npcap and WinPcap are Windows versions of the libpcap library. One of them must be installed in order to capture live network traffic on Windows. Npcap supports Windows 7 through Windows 11. WinPcap is for Windows 95 through Windows 8.
The Wireshark installer from 3.0 onwards includes Npcap, where versions before included WinPcap.
Even with the older Wireshark versions, Npcap might work better for you, especially if you run Windows 10.
Npcap has a Yes/No comparison chart — Npcap or WinPcap?
See CaptureSetup/CapturePrivileges for information about using Npcap and WinPcap with Wireshark.
The libpcap file format description can be found at: Development/LibpcapFileFormat
Npcap Versions
Npcap gets regular bug fixes and upgrades on its own release schedule, which means the version bundled with the Wireshark installer may not be the latest.
Please use an updated version when possible.
See the «Add or Remove Programs» list of the «Control Panel» for the installed version.
WinPcap Versions
We strongly recommend that you use Npcap. If you must use WinPcap, use version 4.1.3. Some annoying bugs are fixed in these versions!
See the «Add or Remove Programs» list of the «Control Panel» for the installed version.
Last Stable Release: 4.1.3
The last WinPcap release version was 4.1.3. The 4.1.x versions contain the following improvements:
- Support for Windows XP, Vista, 2008, Windows 7, 2008R2 64 bit, Windows 8 and Server 2012
- Allows remote capture to work with Wireshark
- Based on libpcap 1.0
WinPcap 4.x does not support Windows 3.1, 95, 98, or ME.
Previous Stable Release: 3.1
This version contains substantial bug fixes and extensions above the 3.0 release:
- based on libpcap 0.9.3, with many fixes and extensions above the older version
- dial-up connections (e.g. PPP) can be captured on Windows 2000, Windows XP, and Windows Server 2003, as well as Windows 95, Windows 98, and Windows Me, which were supported by previous releases
- «can’t get a list of interfaces» error fixed
See the change log for WinPcap for a more complete list (although some of those bugs might be bugs in older 3.1 betas rather than in 3.0).
Installation
The Wireshark installer will copy the Npcap installer and call it, so you get installation done «all in one place». This is the same Npcap installer that you can get from Npcap’s download page.
Windows Versions
Npcap supports Windows 7 SP1 through Windows 11. The list of supported Windows versions for WinPcap is available in WinPcap FAQ #14.
Imported from https://wiki.wireshark.org/WinPcap on 2020-08-11 23:27:29 UTC