The OpenVPN community project team is proud to release OpenVPN 2.6.0. This is a new stable release with some major new features.
For details see: Changes.rst
The Changes document also contains a section with workarounds for common problems encountered when using OpenVPN with OpenSSL 3.
New features and improvements in 2.6.0 compared to 2.5.8:
- Data Channel Offload (DCO) kernel acceleration support for Windows, Linux, and FreeBSD.
- OpenSSL 3 support.
- Improved handling of tunnel MTU, including support for pushable MTU.
- Outdated cryptographic algorithms disabled by default, but there are options to override if necessary.
- Reworked TLS handshake, making OpenVPN immune to replay-packet state exhaustion attacks.
- Added —peer-fingerprint mode for a more simplistic certificate setup and verification.
- Added Pre-Logon Access Provider support to OpenVPN GUI for Windows.
- Improved protocol negotiation, leading to faster connection setup.
- Included openvpn-gui updated to 11.36.0.0. See CHANGES.rst.
- Updated easy-rsa3 bundled with the installer on Windows.
- Various bug fixes.
Windows 64-bit MSI installer |
GnuPG Signature | OpenVPN-2.6.0-I003-amd64.msi |
Windows ARM64 MSI installer |
GnuPG Signature | OpenVPN-2.6.0-I003-arm64.msi |
Windows 32-bit MSI installer |
GnuPG Signature | OpenVPN-2.6.0-I003-x86.msi |
Source zip |
GnuPG Signature | openvpn-2.6.0.tar.gz |
The OpenVPN community project team is proud to release OpenVPN 2.5.4. This release include a number of fixes and small improvements. One of the fixes is to password prompting on windows console when stderr redirection is in use — this breaks 2.5.x on Win11/ARM, and might also break on Win11/amd64. Windows executable and libraries are now built natively on Windows using MSVC, not cross-compiled on Linux as with earlier 2.5 releases. Windows installers include updated OpenSSL and new OpenVPN GUI. The latter includes several improvements, the most important of which is the ability to import profiles from URLs where available. Installer version I602 fixes loading of pkcs11 files on Windows. Installer version I603 fixes a bug in the version number as seen by Windows (was 2.5..4, not 2.5.4). Installer I604 fixes some small Windows issues.
Source tarball (gzip) |
GnuPG Signature | openvpn-2.5.4.tar.gz |
Source tarball (xz) |
GnuPG Signature | openvpn-2.5.4.tar.xz |
Source zip |
GnuPG Signature | openvpn-2.5.4.zip |
Windows 32-bit MSI installer |
GnuPG Signature | OpenVPN-2.5.4-I604-x86.msi |
Windows 64-bit MSI installer |
GnuPG Signature | OpenVPN-2.5.4-I604-amd64.msi |
Windows ARM64 MSI installer |
GnuPG Signature | OpenVPN-2.5.4-I604-arm64.msi |
Overview of changes since OpenVPN 2.4
Faster connections
Crypto specific changes
- ChaCha20-Poly1305 cipher in the OpenVPN data channel (Requires OpenSSL 1.1.0 or newer)
- Improved TLS 1.3 support when using OpenSSL 1.1.1 or newer
- Client-specific tls-crypt keys (—tls-crypt-v2)
- Improved Data channel cipher negotiation
- Removal of BF-CBC support in default configuration (see below for possible incompatibilities)
Server-side improvements
- HMAC based auth-token support for seamless reconnects to standalone servers or a group of servers.
- Asynchronous (deferred) authentication support for auth-pam plugin
- Asynchronous (deferred) support for client-connect scripts and plugins
Network-related changes
- Support IPv4 configs with /31 netmasks now
- 802.1q VLAN support on TAP servers
- IPv6-only tunnels
- New option —block-ipv6 to reject all IPv6 packets (ICMPv6)
Linux-specific features
- VRF support
- Netlink integration (OpenVPN no longer needs to execute ifconfig/route or ip commands)
Windows-specific features
- Wintun driver support, a faster alternative to tap-windows6
- Setting tun/tap interface MTU
- Setting DHCP search domain
- Allow unicode search string in —cryptoapicert option
- EasyRSA3, a modern take on OpenVPN CA management
- MSI installer
Important notices
BF-CBC cipher is no longer the default
Cipher handling for the data channel cipher has been significantly changed between OpenVPN 2.3/2.4 and v2.5, most notably there are no «default cipher BF-CBC» anymore because it is no longer considered a reasonable default. BF-CBC is still available, but it needs to be explicitly configured now.
For connections between OpenVPN 2.4 and v2.5 clients and servers, both ends will be able to negotiate a better cipher than BF-CBC. By default they will select one of the AES-GCM ciphers, but this can be influenced using the —data-ciphers setting.
Connections between OpenVPN 2.3 and v2.5 that have no —cipher setting in the config (= defaulting to BF-CBC and not being negotiation-capable) must be updated. Unless BF-CBC is included in —data-ciphers or there is a «—cipher BF-CBC» in the OpenVPN 2.5 config, a v2.5 client or server will refuse to talk to a v2.3 server or client, because it has no common data channel cipher and negotiating a cipher is not possible. Generally, we recommend upgrading such setups to OpenVPN 2.4 or v2.5. If upgrading is not possible we recommend adding data-ciphers AES-256-GCM:AES-128-GCM:AES-128-CBC (for v2.5+) or cipher AES-128-CBC (v2.4.x and older) to the configuration of all clients and servers.
If you really need to use an unsupported OpenVPN 2.3 (or even older) release and need to stay on BF-CBC (not recommended), the OpenVPN 2.5 based client will need a config file change to re-enable BF-CBC. But be warned that BF-CBC and other related weak ciphers will be removed in coming OpenVPN major releases.
Connectivity to some VPN service provider may break
Connecting with an OpenVPN 2.5 client to at least one commercial VPN service that
implemented their own cipher negotiation method that always reports back that it is using BF-CBC to the client is broken in v2.5. This has always caused warning about mismatch ciphers. We have been in contact with some service providers and they are looking into it. This is not something the OpenVPN community can fix. If your commercial VPN does not work with a v2.5 client, complain to the VPN service provider.
More details on these new features as well as a list of deprecated features and user-visible changes are available in Changes.rst.
The OpenVPN community project team is proud to release OpenVPN 2.5.3. Besides a number of small improvements and bug fixes, this release fixes a possible security issue with OpenSSL config autoloading on Windows (CVE-2021-3606). Updated OpenVPN GUI is also included in Windows installers.
Source tarball (gzip) |
GnuPG Signature | openvpn-2.5.3.tar.gz |
Source tarball (xz) |
GnuPG Signature | openvpn-2.5.3.tar.xz |
Source zip |
GnuPG Signature | openvpn-2.5.3.zip |
Windows 32-bit MSI installer |
GnuPG Signature | OpenVPN-2.5.3-I601-x86.msi |
Windows 64-bit MSI installer |
GnuPG Signature | OpenVPN-2.5.3-I601-amd64.msi |
Windows ARM64 MSI installer |
GnuPG Signature | OpenVPN-2.5.3-I601-arm64.msi |
Overview of changes since OpenVPN 2.4
Faster connections
- Connections setup is now much faster
Crypto specific changes
- ChaCha20-Poly1305 cipher in the OpenVPN data channel (Requires OpenSSL 1.1.0 or newer)
- Improved TLS 1.3 support when using OpenSSL 1.1.1 or newer
- Client-specific tls-crypt keys (—tls-crypt-v2)
- Improved Data channel cipher negotiation
- Removal of BF-CBC support in default configuration (see below for possible incompatibilities)
Server-side improvements
- HMAC based auth-token support for seamless reconnects to standalone servers or a group of servers.
- Asynchronous (deferred) authentication support for auth-pam plugin
- Asynchronous (deferred) support for client-connect scripts and plugins
Network-related changes
- Support IPv4 configs with /31 netmasks now
- 802.1q VLAN support on TAP servers
- IPv6-only tunnels
- New option —block-ipv6 to reject all IPv6 packets (ICMPv6)
Linux-specific features
- VRF support
- Netlink integration (OpenVPN no longer needs to execute ifconfig/route or ip commands)
Windows-specific features
- Wintun driver support, a faster alternative to tap-windows6
- Setting tun/tap interface MTU
- Setting DHCP search domain
- Allow unicode search string in —cryptoapicert option
- EasyRSA3, a modern take on OpenVPN CA management
- MSI installer
Important notices
BF-CBC cipher is no longer the default
Cipher handling for the data channel cipher has been significantly changed between OpenVPN 2.3/2.4 and v2.5, most notably there are no «default cipher BF-CBC» anymore because it is no longer considered a reasonable default. BF-CBC is still available, but it needs to be explicitly configured now.
For connections between OpenVPN 2.4 and v2.5 clients and servers, both ends will be able to negotiate a better cipher than BF-CBC. By default they will select one of the AES-GCM ciphers, but this can be influenced using the —data-ciphers setting.
Connections between OpenVPN 2.3 and v2.5 that have no —cipher setting in the config (= defaulting to BF-CBC and not being negotiation-capable) must be updated. Unless BF-CBC is included in —data-ciphers or there is a «—cipher BF-CBC» in the OpenVPN 2.5 config, a v2.5 client or server will refuse to talk to a v2.3 server or client, because it has no common data channel cipher and negotiating a cipher is not possible. Generally, we recommend upgrading such setups to OpenVPN 2.4 or v2.5. If upgrading is not possible we recommend adding data-ciphers AES-256-GCM:AES-128-GCM:AES-128-CBC (for v2.5+) or cipher AES-128-CBC (v2.4.x and older) to the configuration of all clients and servers.
If you really need to use an unsupported OpenVPN 2.3 (or even older) release and need to stay on BF-CBC (not recommended), the OpenVPN 2.5 based client will need a config file change to re-enable BF-CBC. But be warned that BF-CBC and other related weak ciphers will be removed in coming OpenVPN major releases.
Connectivity to some VPN service provider may break
Connecting with an OpenVPN 2.5 client to at least one commercial VPN service that
implemented their own cipher negotiation method that always reports back that it is using BF-CBC to the client is broken in v2.5. This has always caused warning about mismatch ciphers. We have been in contact with some service providers and they are looking into it. This is not something the OpenVPN community can fix. If your commercial VPN does not work with a v2.5 client, complain to the VPN service provider.
More details on these new features as well as a list of deprecated features and user-visible changes are available in Changes.rst.
The OpenVPN community project team is proud to release OpenVPN 2.5.2. It fixes two related security vulnerabilities (CVE-2020-15078) which under very specific circumstances allow tricking a server using delayed authentication (plugin or management) into returning a PUSH_REPLY before the AUTH_FAILED message, which can possibly be used to gather information about a VPN setup. In combination with «—auth-gen-token» or a user-specific token auth solution it can be possible to get access to a VPN with an otherwise-invalid account. OpenVPN 2.5.2 also includes other bug fixes and improvements. Updated OpenSSL and OpenVPN GUI are included in Windows installers.
Source tarball (gzip) |
GnuPG Signature | openvpn-2.5.2.tar.gz |
Source tarball (xz) |
GnuPG Signature | openvpn-2.5.2.tar.xz |
Source zip |
GnuPG Signature | openvpn-2.5.2.zip |
Windows 32-bit MSI installer |
GnuPG Signature | OpenVPN-2.5.2-I601-x86.msi |
Windows 64-bit MSI installer |
GnuPG Signature | OpenVPN-2.5.2-I601-amd64.msi |
Overview of changes since OpenVPN 2.4
Faster connections
- Connections setup is now much faster
Crypto specific changes
- ChaCha20-Poly1305 cipher in the OpenVPN data channel (Requires OpenSSL 1.1.0 or newer)
- Improved TLS 1.3 support when using OpenSSL 1.1.1 or newer
- Client-specific tls-crypt keys (—tls-crypt-v2)
- Improved Data channel cipher negotiation
- Removal of BF-CBC support in default configuration (see below for possible incompatibilities)
Server-side improvements
- HMAC based auth-token support for seamless reconnects to standalone servers or a group of servers.
- Asynchronous (deferred) authentication support for auth-pam plugin
- Asynchronous (deferred) support for client-connect scripts and plugins
Network-related changes
- Support IPv4 configs with /31 netmasks now
- 802.1q VLAN support on TAP servers
- IPv6-only tunnels
- New option —block-ipv6 to reject all IPv6 packets (ICMPv6)
Linux-specific features
- VRF support
- Netlink integration (OpenVPN no longer needs to execute ifconfig/route or ip commands)
Windows-specific features
- Wintun driver support, a faster alternative to tap-windows6
- Setting tun/tap interface MTU
- Setting DHCP search domain
- Allow unicode search string in —cryptoapicert option
- EasyRSA3, a modern take on OpenVPN CA management
- MSI installer
Important notices
BF-CBC cipher is no longer the default
Cipher handling for the data channel cipher has been significantly changed between OpenVPN 2.3/2.4 and v2.5, most notably there are no «default cipher BF-CBC» anymore because it is no longer considered a reasonable default. BF-CBC is still available, but it needs to be explicitly configured now.
For connections between OpenVPN 2.4 and v2.5 clients and servers, both ends will be able to negotiate a better cipher than BF-CBC. By default they will select one of the AES-GCM ciphers, but this can be influenced using the —data-ciphers setting.
Connections between OpenVPN 2.3 and v2.5 that have no —cipher setting in the config (= defaulting to BF-CBC and not being negotiation-capable) must be updated. Unless BF-CBC is included in —data-ciphers or there is a «—cipher BF-CBC» in the OpenVPN 2.5 config, a v2.5 client or server will refuse to talk to a v2.3 server or client, because it has no common data channel cipher and negotiating a cipher is not possible. Generally, we recommend upgrading such setups to OpenVPN 2.4 or v2.5. If upgrading is not possible we recommend adding data-ciphers AES-256-GCM:AES-128-GCM:AES-128-CBC (for v2.5+) or cipher AES-128-CBC (v2.4.x and older) to the configuration of all clients and servers.
If you really need to use an unsupported OpenVPN 2.3 (or even older) release and need to stay on BF-CBC (not recommended), the OpenVPN 2.5 based client will need a config file change to re-enable BF-CBC. But be warned that BF-CBC and other related weak ciphers will be removed in coming OpenVPN major releases.
Connectivity to some VPN service provider may break
Connecting with an OpenVPN 2.5 client to at least one commercial VPN service that
implemented their own cipher negotiation method that always reports back that it is using BF-CBC to the client is broken in v2.5. This has always caused warning about mismatch ciphers. We have been in contact with some service providers and they are looking into it. This is not something the OpenVPN community can fix. If your commercial VPN does not work with a v2.5 client, complain to the VPN service provider.
More details on these new features as well as a list of deprecated features and user-visible changes are available in Changes.rst.
The OpenVPN community project team is proud to release OpenVPN 2.5.1. It includes several bug fixes and improvements as well as updated OpenSSL and OpenVPN GUI for Windows.
Source tarball (gzip) |
GnuPG Signature | openvpn-2.5.1.tar.gz |
Source tarball (xz) |
GnuPG Signature | openvpn-2.5.1.tar.xz |
Source zip |
GnuPG Signature | openvpn-2.5.1.zip |
Windows 32-bit MSI installer |
GnuPG Signature | OpenVPN-2.5.1-I601-x86.msi |
Windows 64-bit MSI installer |
GnuPG Signature | OpenVPN-2.5.1-I601-amd64.msi |
Overview of changes since OpenVPN 2.4
Faster connections
- Connections setup is now much faster
Crypto specific changes
- ChaCha20-Poly1305 cipher in the OpenVPN data channel (Requires OpenSSL 1.1.0 or newer)
- Improved TLS 1.3 support when using OpenSSL 1.1.1 or newer
- Client-specific tls-crypt keys (—tls-crypt-v2)
- Improved Data channel cipher negotiation
- Removal of BF-CBC support in default configuration (see below for possible incompatibilities)
Server-side improvements
- HMAC based auth-token support for seamless reconnects to standalone servers or a group of servers.
- Asynchronous (deferred) authentication support for auth-pam plugin
- Asynchronous (deferred) support for client-connect scripts and plugins
Network-related changes
- Support IPv4 configs with /31 netmasks now
- 802.1q VLAN support on TAP servers
- IPv6-only tunnels
- New option —block-ipv6 to reject all IPv6 packets (ICMPv6)
Linux-specific features
- VRF support
- Netlink integration (OpenVPN no longer needs to execute ifconfig/route or ip commands)
Windows-specific features
- Wintun driver support, a faster alternative to tap-windows6
- Setting tun/tap interface MTU
- Setting DHCP search domain
- Allow unicode search string in —cryptoapicert option
- EasyRSA3, a modern take on OpenVPN CA management
- MSI installer
Important notices
BF-CBC cipher is no longer the default
Cipher handling for the data channel cipher has been significantly changed between OpenVPN 2.3/2.4 and v2.5, most notably there are no «default cipher BF-CBC» anymore because it is no longer considered a reasonable default. BF-CBC is still available, but it needs to be explicitly configured now.
For connections between OpenVPN 2.4 and v2.5 clients and servers, both ends will be able to negotiate a better cipher than BF-CBC. By default they will select one of the AES-GCM ciphers, but this can be influenced using the —data-ciphers setting.
Connections between OpenVPN 2.3 and v2.5 that have no —cipher setting in the config (= defaulting to BF-CBC and not being negotiation-capable) must be updated. Unless BF-CBC is included in —data-ciphers or there is a «—cipher BF-CBC» in the OpenVPN 2.5 config, a v2.5 client or server will refuse to talk to a v2.3 server or client, because it has no common data channel cipher and negotiating a cipher is not possible. Generally, we recommend upgrading such setups to OpenVPN 2.4 or v2.5. If upgrading is not possible we recommend adding data-ciphers AES-256-GCM:AES-128-GCM:AES-128-CBC (for v2.5+) or cipher AES-128-CBC (v2.4.x and older) to the configuration of all clients and servers.
If you really need to use an unsupported OpenVPN 2.3 (or even older) release and need to stay on BF-CBC (not recommended), the OpenVPN 2.5 based client will need a config file change to re-enable BF-CBC. But be warned that BF-CBC and other related weak ciphers will be removed in coming OpenVPN major releases.
Connectivity to some VPN service provider may break
Connecting with an OpenVPN 2.5 client to at least one commercial VPN service that
implemented their own cipher negotiation method that always reports back that it is using BF-CBC to the client is broken in v2.5. This has always caused warning about mismatch ciphers. We have been in contact with some service providers and they are looking into it. This is not something the OpenVPN community can fix. If your commercial VPN does not work with a v2.5 client, complain to the VPN service provider.
More details on these new features as well as a list of deprecated features and user-visible changes are available in Changes.rst.
The OpenVPN community project team is proud to release OpenVPN 2.5.0 which is a new major release with many new features.
Source tarball (gzip) |
GnuPG Signature | openvpn-2.5.0.tar.gz |
Source tarball (xz) |
GnuPG Signature | openvpn-2.5.0.tar.xz |
Source zip |
GnuPG Signature | openvpn-2.5.0.zip |
Windows 32-bit MSI installer |
GnuPG Signature | OpenVPN-2.5.0-I601-x86.msi |
Windows 64-bit MSI installer |
GnuPG Signature | OpenVPN-2.5.0-I601-amd64.msi |
Overview of changes since OpenVPN 2.4
Faster connections
- Connections setup is now much faster
Crypto specific changes
- ChaCha20-Poly1305 cipher in the OpenVPN data channel (Requires OpenSSL 1.1.0 or newer)
- Improved TLS 1.3 support when using OpenSSL 1.1.1 or newer
- Client-specific tls-crypt keys (—tls-crypt-v2)
- Improved Data channel cipher negotiation
- Removal of BF-CBC support in default configuration (see below for possible incompatibilities)
Server-side improvements
- HMAC based auth-token support for seamless reconnects to standalone servers or a group of servers.
- Asynchronous (deferred) authentication support for auth-pam plugin
- Asynchronous (deferred) support for client-connect scripts and plugins
Network-related changes
- Support IPv4 configs with /31 netmasks now
- 802.1q VLAN support on TAP servers
- IPv6-only tunnels
- New option —block-ipv6 to reject all IPv6 packets (ICMPv6)
Linux-specific features
- VRF support
- Netlink integration (OpenVPN no longer needs to execute ifconfig/route or ip commands)
Windows-specific features
- Wintun driver support, a faster alternative to tap-windows6
- Setting tun/tap interface MTU
- Setting DHCP search domain
- Allow unicode search string in —cryptoapicert option
- EasyRSA3, a modern take on OpenVPN CA management
- MSI installer
Important notices
BF-CBC cipher is no longer the default
Cipher handling for the data channel cipher has been significantly changed between OpenVPN 2.3/2.4 and v2.5, most notably there are no «default cipher BF-CBC» anymore because it is no longer considered a reasonable default. BF-CBC is still available, but it needs to be explicitly configured now.
For connections between OpenVPN 2.4 and v2.5 clients and servers, both ends will be able to negotiate a better cipher than BF-CBC. By default they will select one of the AES-GCM ciphers, but this can be influenced using the —data-ciphers setting.
Connections between OpenVPN 2.3 and v2.5 that have no —cipher setting in the config (= defaulting to BF-CBC and not being negotiation-capable) must be updated. Unless BF-CBC is included in —data-ciphers or there is a «—cipher BF-CBC» in the OpenVPN 2.5 config, a v2.5 client or server will refuse to talk to a v2.3 server or client, because it has no common data channel cipher and negotiating a cipher is not possible. Generally, we recommend upgrading such setups to OpenVPN 2.4 or v2.5. If upgrading is not possible we recommend adding data-ciphers AES-256-GCM:AES-128-GCM:AES-128-CBC (for v2.5+) or cipher AES-128-CBC (v2.4.x and older) to the configuration of all clients and servers.
If you really need to use an unsupported OpenVPN 2.3 (or even older) release and need to stay on BF-CBC (not recommended), the OpenVPN 2.5 based client will need a config file change to re-enable BF-CBC. But be warned that BF-CBC and other related weak ciphers will be removed in coming OpenVPN major releases.
Connectivity to some VPN service provider may break
Connecting with an OpenVPN 2.5 client to at least one commercial VPN service that
implemented their own cipher negotiation method that always reports back that it is using BF-CBC to the client is broken in v2.5. This has always caused warning about mismatch ciphers. We have been in contact with some service providers and they are looking into it. This is not something the OpenVPN community can fix. If your commercial VPN does not work with a v2.5 client, complain to the VPN service provider.
More details on these new features as well as a list of deprecated features and user-visible changes are available in Changes.rst.
The OpenVPN community project team is proud to release OpenVPN 2.4.11. It fixes two related security vulnerabilities (CVE-2020-15078) which under very specific circumstances allow tricking a server using delayed authentication (plugin or management) into returning a PUSH_REPLY before the AUTH_FAILED message, which can possibly be used to gather information about a VPN setup. This release also includes other bug fixes and improvements. The I602 Windows installers fix a possible security issue with OpenSSL config autoloading on Windows (CVE-2021-3606). Updated OpenSSL and OpenVPN GUI are included in Windows installers.
Source Tarball (gzip) |
GnuPG Signature | openvpn-2.4.11.tar.gz |
Source Tarball (xz) |
GnuPG Signature | openvpn-2.4.11.tar.xz |
Source Zip |
GnuPG Signature | openvpn-2.4.11.zip |
Windows 7/8/8.1/Server 2012r2 installer (NSIS) |
GnuPG Signature | openvpn-install-2.4.11-I602-Win7.exe |
Windows 10/Server 2016/Server 2019 installer (NSIS) |
GnuPG Signature | openvpn-install-2.4.11-I602-Win10.exe |
A summary of the changes is available in Changes.rst, and a full list of changes is available here.
Please note that LibreSSL is not a supported crypto backend. We accept patches and we do test on OpenBSD 6.0 which comes with LibreSSL, but if newer versions of LibreSSL break API compatibility we do not take responsibility to fix that.
Also note that Windows installers have been built with NSIS version that has been patched against several NSIS installer code execution and privilege escalation problems. Based on our testing, though, older Windows versions such as Windows 7 might not benefit from these fixes. We thus strongly encourage you to always move NSIS installers to a non-user-writeable location before running them.
Please note that OpenVPN 2.4 installers will not work on Windows XP. The last OpenVPN version that supports Windows XP is 2.3.18, which is downloadable as 32-bit and 64-bit versions.
If you find a bug in this release, please file a bug report to our Trac bug tracker. In uncertain cases please contact our developers first, either using the openvpn-devel mailinglist or the developer IRC channel (#openvpn-devel at irc.libera.chat). For generic help take a look at our official documentation, wiki, forums, openvpn-users mailing list and user IRC channel (#openvpn at irc.libera.chat).
Important: you will need to use the correct installer for your operating system. The Windows 10 installer works on Windows 10 and Windows Server 2016/2019. The Windows 7 installer will work on Windows 7/8/8.1/Server 2012r2. This is because of Microsoft’s driver signing requirements are different for kernel-mode devices drivers, which in our case affects OpenVPN’s tap driver (tap-windows6).
This is primarily a maintenance release with bugfixes and small improvements. Windows installers include the latest OpenSSL version (1.1.1i) which includes security fixes.
A summary of the changes is available in Changes.rst, and a full list of changes is available here.
Please note that LibreSSL is not a supported crypto backend. We accept patches and we do test on OpenBSD 6.0 which comes with LibreSSL, but if newer versions of LibreSSL break API compatibility we do not take responsibility to fix that.
Also note that Windows installers have been built with NSIS version that has been patched against several NSIS installer code execution and privilege escalation problems. Based on our testing, though, older Windows versions such as Windows 7 might not benefit from these fixes. We thus strongly encourage you to always move NSIS installers to a non-user-writeable location before running them.
Please note that OpenVPN 2.4 installers will not work on Windows XP. The last OpenVPN version that supports Windows XP is 2.3.18, which is downloadable as 32-bit and 64-bit versions.
If you find a bug in this release, please file a bug report to our Trac bug tracker. In uncertain cases please contact our developers first, either using the openvpn-devel mailinglist or the developer IRC channel (#openvpn-devel at irc.libera.chat). For generic help take a look at our official documentation, wiki, forums, openvpn-users mailing list and user IRC channel (#openvpn at irc.libera.chat).
Important: you will need to use the correct installer for your operating system. The Windows 10 installer works on Windows 10 and Windows Server 2016/2019. The Windows 7 installer will work on Windows 7/8/8.1/Server 2012r2. This is because of Microsoft’s driver signing requirements are different for kernel-mode devices drivers, which in our case affects OpenVPN’s tap driver (tap-windows6).
Source Tarball (gzip) |
GnuPG Signature | openvpn-2.4.10.tar.gz |
Source Tarball (xz) |
GnuPG Signature | openvpn-2.4.10.tar.xz |
Source Zip |
GnuPG Signature | openvpn-2.4.10.zip |
Windows 7/8/8.1/Server 2012r2 installer (NSIS) |
GnuPG Signature | openvpn-install-2.4.10-I601-Win7.exe |
Windows 10/Server 2016/Server 2019 installer (NSIS) |
GnuPG Signature | openvpn-install-2.4.10-I601-Win10.exe |
Instructions for verifying the signatures are available here.
This release is also available in our own software repositories for Debian and Ubuntu, Supported architectures are i386 and amd64. For details. look here.
The Windows installers are bundled with OpenVPN-GUI — its source code is available on its project page and as tarballs on our alternative download server.
This is primarily a maintenance release with bugfixes and improvements. This release also fixes a security issue (CVE-2020-11810, trac #1272) which allows disrupting service of a freshly connected client that has not yet not negotiated session keys. The vulnerability cannot be used to inject or steal VPN traffic.
A summary of the changes is available in Changes.rst, and a full list of changes is available here.
Please note that LibreSSL is not a supported crypto backend. We accept patches and we do test on OpenBSD 6.0 which comes with LibreSSL, but if newer versions of LibreSSL break API compatibility we do not take responsibility to fix that.
Also note that Windows installers have been built with NSIS version that has been patched against several NSIS installer code execution and privilege escalation problems. Based on our testing, though, older Windows versions such as Windows 7 might not benefit from these fixes. We thus strongly encourage you to always move NSIS installers to a non-user-writeable location before running them. We are moving to MSI installers in OpenVPN 2.5, but OpenVPN 2.4.x will remain NSIS-only.
Compared to OpenVPN 2.3 this is a major update with a large number of new features, improvements and fixes. Some of the major features are AEAD (GCM) cipher and Elliptic Curve DH key exchange support, improved IPv4/IPv6 dual stack support and more seamless connection migration when client’s IP address changes (Peer-ID). Also, the new —tls-crypt feature can be used to increase users’ connection privacy.
OpenVPN GUI bundled with the Windows installer has a large number of new features compared to the one bundled with OpenVPN 2.3. One of major features is the ability to run OpenVPN GUI without administrator privileges. For full details, see the changelog. The new OpenVPN GUI features are documented here.
Please note that OpenVPN 2.4 installers will not work on Windows XP. The last OpenVPN version that supports Windows XP is 2.3.18, which is downloadable as 32-bit and 64-bit versions.
If you find a bug in this release, please file a bug report to our Trac bug tracker. In uncertain cases please contact our developers first, either using the openvpn-devel mailinglist or the developer IRC channel (#openvpn-devel at irc.libera.chat). For generic help take a look at our official documentation, wiki, forums, openvpn-users mailing list and user IRC channel (#openvpn at irc.libera.chat).
Important: you will need to use the correct installer for your operating system. The Windows 10 installer works on Windows 10 and Windows Server 2016/2019. The Windows 7 installer will work on Windows 7/8/8.1/Server 2012r2. This is because of Microsoft’s driver signing requirements are different for kernel-mode devices drivers, which in our case affects OpenVPN’s tap driver (tap-windows6).
Source Tarball (gzip) |
GnuPG Signature | openvpn-2.4.9.tar.gz |
Source Tarball (xz) |
GnuPG Signature | openvpn-2.4.9.tar.xz |
Source Zip |
GnuPG Signature | openvpn-2.4.9.zip |
Windows 7/8/8.1/Server 2012r2 installer (NSIS) |
GnuPG Signature | openvpn-install-2.4.9-I601-Win7.exe |
Windows 10/Server 2016/Server 2019 installer (NSIS) |
GnuPG Signature | openvpn-install-2.4.9-I601-Win10.exe |
NOTE: the GPG key used to sign the release files has been changed since OpenVPN 2.4.0. Instructions for verifying the signatures, as well as the new GPG public key are available here.
We also provide static URLs pointing to latest releases to ease automation. For a list of files look here.
This release is also available in our own software repositories for Debian and Ubuntu, Supported architectures are i386 and amd64. For details. look here.
You can use EasyRSA 2 or EasyRSA 3 for generating your own certificate authority. The former is bundled with Windows installers. The latter is a more modern alternative for UNIX-like operating systems.
The Windows installers are bundled with OpenVPN-GUI — its source code is available on its project page and as tarballs on our alternative download server.
This is primarily a maintenance release with bugfixes and improvements. The Windows installers (I601) have several improvements compared to the previous release:
- New tap-windows6 driver (9.24.2) which fixes some suspend and resume issues
- Latest OpenVPN-GUI
- Considerable performance boost due to new compiler optimization flags
A summary of the changes is available in Changes.rst, and a full list of changes is available here.
Please note that LibreSSL is not a supported crypto backend. We accept patches and we do test on OpenBSD 6.0 which comes with LibreSSL, but if newer versions of LibreSSL break API compatibility we do not take responsibility to fix that.
Also note that Windows installers have been built with NSIS version that has been patched against several NSIS installer code execution and privilege escalation problems. Based on our testing, though, older Windows versions such as Windows 7 might not benefit from these fixes. We thus strongly encourage you to always move NSIS installers to a non-user-writeable location before running them. We are moving to MSI installers in OpenVPN 2.5, but OpenVPN 2.4.x will remain NSIS-only.
Compared to OpenVPN 2.3 this is a major update with a large number of new features, improvements and fixes. Some of the major features are AEAD (GCM) cipher and Elliptic Curve DH key exchange support, improved IPv4/IPv6 dual stack support and more seamless connection migration when client’s IP address changes (Peer-ID). Also, the new —tls-crypt feature can be used to increase users’ connection privacy.
OpenVPN GUI bundled with the Windows installer has a large number of new features compared to the one bundled with OpenVPN 2.3. One of major features is the ability to run OpenVPN GUI without administrator privileges. For full details, see the changelog. The new OpenVPN GUI features are documented here.
Please note that OpenVPN 2.4 installers will not work on Windows XP. The last OpenVPN version that supports Windows XP is 2.3.18, which is downloadable as 32-bit and 64-bit versions.
If you find a bug in this release, please file a bug report to our Trac bug tracker. In uncertain cases please contact our developers first, either using the openvpn-devel mailinglist or the developer IRC channel (#openvpn-devel at irc.libera.chat). For generic help take a look at our official documentation, wiki, forums, openvpn-users mailing list and user IRC channel (#openvpn at irc.libera.chat).
Important: you will need to use the correct installer for your operating system. The Windows 10 installer works on Windows 10 and Windows Server 2016/2019. The Windows 7 installer will work on Windows 7/8/8.1/Server 2012r2. This is because of Microsoft’s driver signing requirements are different for kernel-mode devices drivers, which in our case affects OpenVPN’s tap driver (tap-windows6).
Source Tarball (gzip) |
GnuPG Signature | openvpn-2.4.8.tar.gz |
Source Tarball (xz) |
GnuPG Signature | openvpn-2.4.8.tar.xz |
Source Zip |
GnuPG Signature | openvpn-2.4.8.zip |
Windows 7/8/8.1/Server 2012r2 installer (NSIS) |
GnuPG Signature | openvpn-install-2.4.8-I602-Win7.exe |
Windows 10/Server 2016/Server 2019 installer (NSIS) |
GnuPG Signature | openvpn-install-2.4.8-I602-Win10.exe |
NOTE: the GPG key used to sign the release files has been changed since OpenVPN 2.4.0. Instructions for verifying the signatures, as well as the new GPG public key are available here.
We also provide static URLs pointing to latest releases to ease automation. For a list of files look here.
This release is also available in our own software repositories for Debian and Ubuntu, Supported architectures are i386 and amd64. For details. look here.
You can use EasyRSA 2 or EasyRSA 3 for generating your own certificate authority. The former is bundled with Windows installers. The latter is a more modern alternative for UNIX-like operating systems.
The Windows installers are bundled with OpenVPN-GUI — its source code is available on its project page and as tarballs on our alternative download server.
This is primarily a maintenance release with bugfixes and improvements. One of the big things is enhanced TLS 1.3 support. A summary of the changes is available in Changes.rst, and a full list of changes is available here.
Please note that LibreSSL is not a supported crypto backend. We accept patches and we do test on OpenBSD 6.0 which comes with LibreSSL, but if newer versions of LibreSSL break API compatibility we do not take responsibility to fix that.
Also note that Windows installers have been built with NSIS version that has been patched against several NSIS installer code execution and privilege escalation problems. Based on our testing, though, older Windows versions such as Windows 7 might not benefit from these fixes. We thus strongly encourage you to always move NSIS installers to a non-user-writeable location before running them. We are moving to MSI installers in OpenVPN 2.5, but OpenVPN 2.4.x will remain NSIS-only.
Compared to OpenVPN 2.3 this is a major update with a large number of new features, improvements and fixes. Some of the major features are AEAD (GCM) cipher and Elliptic Curve DH key exchange support, improved IPv4/IPv6 dual stack support and more seamless connection migration when client’s IP address changes (Peer-ID). Also, the new —tls-crypt feature can be used to increase users’ connection privacy.
OpenVPN GUI bundled with the Windows installer has a large number of new features compared to the one bundled with OpenVPN 2.3. One of major features is the ability to run OpenVPN GUI without administrator privileges. For full details, see the changelog. The new OpenVPN GUI features are documented here.
Please note that OpenVPN 2.4 installers will not work on Windows XP. The last OpenVPN version that supports Windows XP is 2.3.18, which is downloadable as 32-bit and 64-bit versions.
If you find a bug in this release, please file a bug report to our Trac bug tracker. In uncertain cases please contact our developers first, either using the openvpn-devel mailinglist or the developer IRC channel (#openvpn-devel at irc.libera.chat). For generic help take a look at our official documentation, wiki, forums, openvpn-users mailing list and user IRC channel (#openvpn at irc.libera.chat).
Important: you will need to use the correct installer for your operating system. The Windows 10 installer will not work on Windows 7/8/8.1/Server 2012r2. This is because Microsoft’s driver signing requirements and tap-windows6. For the same reason you need to use an older installer with Windows Server 2016. This older installer has a local privilege escalation vulnerability issue which we cannot resolve for Windows Server 2016 until tap-windows6 passes the HLK test suite on that platform. In the meanwhile we recommend Windows Server 2016 users to avoid installing OpenVPN/tap-windows6 driver on hosts where all users can’t be trusted. Users of Windows 7-10 and Server 2012r2 are recommended to update to latest installers as soon as possible.
Source Tarball (gzip) |
GnuPG Signature | openvpn-2.4.7.tar.gz |
Source Tarball (xz) |
GnuPG Signature | openvpn-2.4.7.tar.xz |
Source Zip |
GnuPG Signature | openvpn-2.4.7.zip |
Windows 7/8/8.1/Server 2012r2 installer (NSIS) |
GnuPG Signature | openvpn-install-2.4.7-I607-Win7.exe |
Windows 10 installer (NSIS) |
GnuPG Signature | openvpn-install-2.4.7-I607-Win10.exe |
Windows Server 2016 installer (NSIS) |
GnuPG Signature | openvpn-install-2.4.7-I603.exe |
NOTE: the GPG key used to sign the release files has been changed since OpenVPN 2.4.0. Instructions for verifying the signatures, as well as the new GPG public key are available here.
We also provide static URLs pointing to latest releases to ease automation. For a list of files look here.
This release is also available in our own software repositories for Debian and Ubuntu, Supported architectures are i386 and amd64. For details. look here.
You can use EasyRSA 2 or EasyRSA 3 for generating your own certificate authority. The former is bundled with Windows installers. The latter is a more modern alternative for UNIX-like operating systems.
The Windows installers are bundled with OpenVPN-GUI — its source code is available on its project page and as tarballs on our alternative download server.
This is primarily a maintenance release with minor bugfixes and improvements, and one security relevant fix for the Windows Interactive Service. Windows installer includes updated OpenVPN GUI and OpenSSL. Installer I601 included tap-windows6 driver 9.22.1 which had one security fix and dropped Windows Vista support. However, in installer I602 we had to revert back to tap-windows 9.21.2 due to driver getting reject on freshly installed Windows 10 rev 1607 and later when Secure Boot was enabled. The failure was due to the new, more strict driver signing requirements. The 9.22.1 version of the driver is in the process of getting approved and signed by Microsoft and will be bundled in an upcoming Windows installer.
Please note that LibreSSL is not a supported crypto backend. We accept patches and we do test on OpenBSD 6.0 which comes with LibreSSL, but if newer versions of LibreSSL break API compatibility we do not take responsibility to fix that.
Also note that Windows installers have been built with NSIS version that has been patched against several NSIS installer code execution and privilege escalation problems. Based on our testing, though, older Windows versions such as Windows 7 might not benefit from these fixes. We thus strongly encourage you to always move NSIS installers to a non-user-writeable location before running them. Our long-term plan is to migrate to using MSI installers instead.
Compared to OpenVPN 2.3 this is a major update with a large number of new features, improvements and fixes. Some of the major features are AEAD (GCM) cipher and Elliptic Curve DH key exchange support, improved IPv4/IPv6 dual stack support and more seamless connection migration when client’s IP address changes (Peer-ID). Also, the new —tls-crypt feature can be used to increase users’ connection privacy.
A summary of the changes is available in Changes.rst, and a full list of changes is available here.
OpenVPN GUI bundled with the Windows installer has a large number of new features compared to the one bundled with OpenVPN 2.3. One of major features is the ability to run OpenVPN GUI without administrator privileges. For full details, see the changelog. The new OpenVPN GUI features are documented here.
Please note that OpenVPN 2.4 installers will not work on Windows XP.
If you find a bug in this release, please file a bug report to our Trac bug tracker. In uncertain cases please contact our developers first, either using the openvpn-devel mailinglist or the developha er IRC channel (#openvpn-devel at irc.libera.chat). For generic help take a look at our official documentation, wiki, forums, openvpn-users mailing list and user IRC channel (#openvpn at irc.libera.chat).
Source Tarball (gzip) |
GnuPG Signature | openvpn-2.4.6.tar.gz |
Source Tarball (xz) |
GnuPG Signature | openvpn-2.4.6.tar.xz |
Source Zip |
GnuPG Signature | openvpn-2.4.6.zip |
Windows installer (NSIS) |
GnuPG Signature | openvpn-install-2.4.6-I602.exe |
NOTE: the GPG key used to sign the release files has been changed since OpenVPN 2.4.0. Instructions for verifying the signatures, as well as the new GPG public key are available here.
We also provide static URLs pointing to latest releases to ease automation. For a list of files look here.
This release is also available in our own software repositories for Debian and Ubuntu, Supported architectures are i386 and amd64. For details. look here.
You can use EasyRSA 2 or EasyRSA 3 for generating your own certificate authority. The former is bundled with Windows installers. The latter is a more modern alternative for UNIX-like operating systems.
The Windows installers are bundled with OpenVPN-GUI — its source code is available on its project page and as tarballs on our alternative download server.
You can download Windows developments snapshots (MSI installers) from here (Index of /downloads/snapshots/github-actions/openvpn2/ ). Those are automatically built from commits to OpenVPN master branch and include functionality which will be available in the next release. Development snapshots are less stable than releases, so use at your own risk.
- Windows
- MacOS
- Linux
- Android
- iOS
- ChromeOS
Connect to any compatible server
Connect to Access Server, OpenVPN Cloud or any OpenVPN protocol-compatible server or service.
Superior Authentication
Supports 2FA and SAML authentication. Authenticate prior to profile download and connection.
Instant Connection
Easily import connection configuration by just opening a URL.
Frequently asked questions
How do I connect to OpenVPN?
In order to connect to the VPN server or service, you need to obtain a file that contains the specifics needed for the connection. Such a configuration file is called a profile and has an .ovpn file extension.
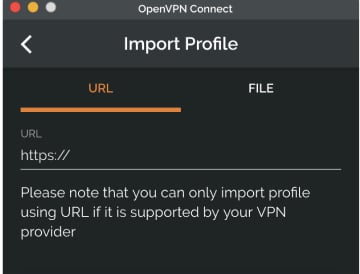
If your business is using Access Server or OpenVPN Cloud and your IT department has provided you a URL, you can directly import the profile by entering the URL.
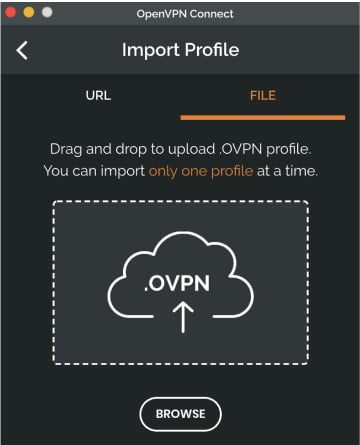
However, if you have received the profile as a file from your IT department or from some other OpenVPN compatible service, you can import the profile by selecting the file.
How do I connect if the OpenVPN client is integrated into my router?
In order to connect to the VPN server or service, you need to obtain a file that contains the specifics needed for the connection. Such a configuration file is called a profile and has an .ovpn file extension.
After receiving the .ovpn file from you IT department, you need to follow instructions specific to the router to extract specific information from the file and use it for configuration. We have made guides for some of the common firmware used in hardware routers and for pfSense:
pfSense
OpenWrt
DD-WRT
OpenVPN
для Windows
OpenVPN — кроссплатформенный инструмент для безопасного туннелирования IP-сетей через единственный UDP или TCP-порт с поддержкой аутентификации сессий и обмена ключами на основе SSL/TLS, шифрования, аутентификации и сжатия пакетов. Поддерживается широкий спектр конфигураций, динамических IP-адресов и NAT, присутствует возможность настраивать удаленный доступ, VPN-соединения типа «точка-точка» и пр.
Основные возможности OpenVPN:
- Поддержка прокси серверов, включая HTTP, SOCKS, NAT и сетевые фильтры.
- Сетевые операции через TCP или UDP транспорт.
- Туннелирования IP-сетей через единственный UDP или TCP-порт с поддержкой аутентификации сессий.
- Эффективное сжатие трафика.
- Поддержка нескольких протоколов шифрования (MD5-HMAC, RSA) и 2048-битного ключа.
- Возможность настраивать удаленный доступ.
- Поддержка динамических IP-адресов и NAT.
- VPN-соединения типа «точка-точка».
ТОП-сегодня раздела «Анонимайзеры, VPN»
Tor Browser 12.0.2
Предоставляет надежную защиту персональной информации и конфиденциальности, которая…
Windscribe 2.5.17
Удобное решение, которое представляет собой набор инструментов, которые работают вместе…
AdGuard VPN 2.0.1
Удобный инструмент для интернет-безопасности и защиты конфиденциальности в Сети,…
Planet VPN 1.4.05.01
Бесплатный VPN с возможностями, функционалом и защищенностью на уровне топовых платных…
DNS Jumper 2.2
DNS Jumper — небольшое бесплатное приложение для быстрого переключения DNS на ПК для повышения уровня безопасности или увеличения скорости работы в Интернете…
Отзывы о программе OpenVPN
Сергей про OpenVPN 2.5.7 [12-07-2022]
OpenVPN-2.5.7-I602-arm64 Win10 очень классная программа, бесплатная и работает на все100%
4 | 6 | Ответить
Валерий про OpenVPN 2.5.6 [24-03-2022]
Хрень, полная ни фига эта прога не меняет ваш регион и ип. Зря качал.
4 | 33 | Ответить
Алексей в ответ Валерий про OpenVPN 2.5.7 [18-01-2023]
Ну если не знать для чего существует данная программа, то хаять конечно же проще.
Свою задачу она выполняет на все 100%
| | Ответить

OpenVPN — это полнофункциональное SSL VPN решение с открытым исходным кодом, которое предоставляет доступ к широкому спектру всевозможных конфигураций, предназначенных для создания виртуальных сетей между компьютерами, получения удалённого доступа к другим ПК, а также защиты передаваемых данных.
Описание OpenVPN:
Эта программа предлагает лёгкую и экономичную альтернативу прочим VPN-сервисам и предназначена, в первую очередь, для малого и среднего бизнеса. Тем не менее, она прекрасно найдет себе применение и при использовании простыми пользователями. Главными особенностями программы можно назвать относительную простоту настройки и использования, высокую стабильность и масштабируемость для огромного количества клиентов.
Программа позволяет создавать зашифрованные каналы двух типов: «Сервер-Клиент» и «Точка-Точка». Первый тип подразумевает подключение к удалённому серверу для работы в сети, а второй — создание прямого виртуального частного туннеля между определёнными машинами. При этом, ОпенВПН позволит установить соединение между компьютерами, находящимися за NAT и сетевым экраном, без необходимости изменения их настроек.
Поддерживаемые методы аутентификации:
- Предустановленный ключ.
- Сертификатная аутентификация.
- При помощи логина и пароля.
Возможно, вас также заинтересует OpenVPN Connect для Android и OpenVPN Connect для iOS.
С нашего сайта вы можете скачать OpenVPN бесплатно, на высокой скорости.
OpenVPN 64 bit is an award-winning and fully-featured SSL VPN solution that can allow everyone from computing novices to large companies to configure the way they are accessing the internet, unlocking powerful services for safer and stealthier browsing experience. Built from the ground up to support latest encryption methods, this app allows you to connect your PC to OpenVPN servers without the fear that anyone will intercept and spy on your data, from where your data requests will be distributed across the rest of the web in a safe and controlled manner.
This downloads the source code. Please download OpenVPN Connect if you need a working OpenVPN GUI client.
By default, the app can distribute your data traffic across many of its servers, making your online location masked and unrecognizable to Internet Service Providers and the rest of the internet in general. In addition to that, It also comes with the large offering of customization tools that can be used for setting up remote access privileges, site-to-site VPNs, enterprise-scale remote access, adaptive load-balancing, advanced Wi-Fi security, failover services, fine-grained user access control, and much more.
The presence of both automated VPN services and advanced tools have made OpenVPN 64bit into #1 secure browsing software of choice for both regular users, organizations of all sizes, and many Fortune 500 companies.
Installation and Use
It comes in a small package that will after installation re-configure the way your computer is accessing the internet. The configuration window of this app is actually very lightweight, and it holds only the most basic of tools for setting the type of your VPN setting (config file, system proxy settings or manual configuration) and a dropdown menu for selecting user interface language (with over 15 available translations).
Originally built for use in enterprise environments, the personal tier of OpenVPN retains the highly advanced technologies and lightweight tools. The core security feature of OpenVPN is based upon OSI layer 2 or 3 secure network extension that is utilizing SSL/TLS protocols. It installs deep into the Windows OS, enabling all the user apps to take advantage of the security features, firewall rules, authentication certificates, and more.
In the real world, ordinary non-business users can encounter various roadblocks that can prevent them from taking full advantage of their home internet connection. This may include ISP data rate throttling, website content region blocking, or even government-imposed firewalls. It allows users to circumvent these issues, offering you stable and secure data stream to their servers, from which you will be re-routed to any major region in the world, and be able to access its “local” content. No matter if you want to simply access region-specific sites and services (such as streaming platforms content offering) or to read censored news outlets, It can allow you to do that in just a few clicks.
Another benefit of an Open VPN is a unified virtual presence. No matter where you physically are, if you are using Open VPN, the rest of the internet will be able to detect you originating from a single region.
Features and Highlights
- Core – With over 50 million downloads, the core technology of Open VPN has proven to be one of the leaders in the field of VPN security.
- Advanced AES encryption – It encrypts all outgoing and incoming internet data with the world’s leading standard for encryption.
- Fortified privacy – Effortlessly protect your personal and online identity by location spoofing your IP address.
- Wireless hot spot protection – Prevent unauthorized access to your data while connecting to public and unsecured Wi-Fi sports.
- Travel protection – Mask your online location no matter where you are.
- Worldwide server connection – Gain access and establish your virtual presence at servers that are in 12 regions around the world.
- Unrestricted access – Access OpenVPN servers from any location in the world.
- 24/7 support – Gain access to support 24/7 via email or live webchat.
- Full Windows compatibility – Available on all modern versions of Windows, ranging from Windows 2003 to Windows 7 (both 32-bit and 64-bit).
Download OpenVPN (64-bit) Latest Version
О программе
Что вы узнаете из обзора:
OpenVPN – бесплатная программа для Windows с полнофункциональной реализацией VPN. Отличается открытым исходным кодом, поддержкой SSL-соединения и продвинутыми настройками для опытных пользователей. С помощью данного софта можно организовать безопасное и конфиденциальное пребывание в Сети.
Поддержка широкого спектра конфигураций, большое число настроек и возможность удалённого доступа являются огромными преимуществами перед другими аналогами, распространяющимися на бесплатной основе.
Поэтому есть смысл скачать OpenVPN на Windows 7, 8, 10, 11, если имеется потребность в расширенном функционале.
Функционал
Программное обеспечение позволяет обеспечивать подключение следующим образом: компьютерный клиент -> прокси-сервер -> интернет. Благодаря данному алгоритму удалось добиться:
- высокой стабильности подключения;
- анонимности в интернете;
- безопасности.
В частности, безопасность активного подключения при условии корректной работы прокси-сервера гарантируется и при использовании общедоступных точек доступа.
Отдельного внимания заслуживают каналы, подразумевающие два вида передачи данных:
- Точка – точка.
- Сервер – клиенты.
За счёт данного механизма обеспечиваются: предельно простое взаимодействие пользователя с софтом, высочайшая защита не только получаемых, но и передаваемый пакетов.
Принцип работы простой – создаются защищённые каналы, через которые осуществляется передача и получение данных, каждый с уникальным шифром, что делает взлом хакерами крайне затруднительным.
Поэтому платная версия пользуется большой популярностью в небольших компаниях и фирмах.
Бесплатная – применяется частными пользователями для обеспечения доступа к заблокированным ресурсам в большей мере, и для защиты в меньшей.
Дополнительно следует отметить наличие возможности объединения нескольких рабочих станций в виртуальную сеть, защищённую встроенными в программное обеспечение средствами.
Задействоваться могут не только персональные компьютеры, находящиеся в офисе и соединённые между собой посредством LAN, но и ПК, находящиеся в других странах – для удалённого доступа.
Если вы хотите оценить функционал, советуем скачать OpenVPN на Windows 7, 8, 10 и только при наличии необходимости приобретать полную версию, так как большинству будет достаточно «базы», доступной без премиум-пакета.
Плюсы и минусы
Время более подробно остановиться на преимуществах и недостатках OpenVPN для Windows 7, 8, 10. Сразу отметим, что плюсов значительно больше и мы упомянули лишь наиболее весомые из них.
Преимущества:
- Осуществление конфиденциального и защищённого обмена информацией внутри созданной сети. Для осуществления передачи приложением используется UDP либо TCP протокол.
- Защита информации обеспечивается за счёт её шифрования. Используется протокол TLS и библиотека OpenSSL. В последних версиях программного обеспечения применяется библиотека PolarSSL, обеспечивающая большую надёжность системы защиты.
- Обеспечение дополнительной защиты за счёт идентификации каждой из сторон, участвующей в обмене информацией. Вмешательство посредника становится невозможным – в том числе, недоступны прослушивание, искажение и передача, удаление данных.
- Безопасный серфинг в интернете. Инструменты браузеров не используются.
- Подмена IP-адреса на выбранный самостоятельно или в автоматическом режиме. Местоположение пользователя и его настоящий IP останутся конфиденциальными.
- Доступ к различным веб-ресурсам, заблокированным ранее.
- Возможность масштабирования системы с подключением к сети сотен, тысяч клиентов при необходимости.
Недостатки:
- необходимость установки клиента;
- платная версия стоит слишком дорого для рядовых пользователей;
- сложности с настройками ПО.
Если вы считаете себя уверенным пользователем ПК, разбираетесь в тонкостях работы VPN – советуем попробовать данный сервис с собственным клиентом. Он позволяет добиться и анонимности в Сети, и повышенной защиты, и имеет место быть в коммерческих проектах. На нашем сайте вы сможете подобрать «под себя» оптимальный VPN на компьютер.
Видео обзор
- Скачайте OpenVPN для Windows по официальной ссылке внизу этого обзора, запустите файл и следуйте инструкции.
- Скачайте файл конфигурации подключения . ovpn, для подключения к серверу ретрансляции. Загрузить OpenVPN Config file можно на — http://www.vpngate.net/en/.
- Выберите VPN-сервер, к которому вы хотите подключиться и кликните на файл *.ovpn, скачайте его. Далее нужно переместить файл *.ovpn в папку config — C:Program FilesOpenVPNconfig.
- Кликните по иконке OpenVPN GUI и выберите запуск от имени администратора.
- Статус подключения будет отображаться на экране.
- После проделанных манипуляций в системе Windows создается виртуальный сетевой адаптер и этот адаптер получит IP-адрес, который начинается с 10.211. Виртуальный адаптер получит адрес шлюза по умолчанию (проверить конфигурацию можно командой ipconfig /all в командной строке). Командой tracert 8.8.8.8 — убедиться, что трафик будет проходить через VPN-сервер.
Системные требования
- Windows 11, 10, 8.1, 8, 7, Vista 32|64-bit (последняя версия)
- Windows XP 32|64-bit (только для версии 2.3.16)
Похожие программы
- ZenMate VPN
- NordVPN
- Windscribe VPN
Скачать OpenVPN
Скачивая OpenVPN на компьютер с ОС Windows 7, 8, 10, можно получить не только доступ к заблокированным ресурсам, но и полноценный многофункциональный комбайн, позволяющий использовать ПО, в том числе, и в коммерческих целях.
Программа позволяет создать сеть для более удобной работы сотрудников внутри офиса и далеко за его пределами – при наличии фрилансеров или работников вне штата, связанных с вами рабочими обязательствами.
Windows 7, 8, 10, 11, Vista
Windows XP 32-bit
Windows XP 64-bit
Windows ARM64 MSI installer

Оцените:

Загрузка…
Скачали: 12 573
OpenVPN — бесплатный программный комплекс для реализации подключений по протоколу VPN к виртуальным частным сетям, создания шифрованных туннелей между сервером и клиентскими компьютерами или подключения типа точка-точка для безопасной передачи данных через Интернет. Пакет OpenVPN на русском языке включает в себя все необходимое для запуска собственного сервера, а так же клиент для подключения к серверам посредством VPN и графический интерфейс OpenVPN GUI.
OpenVPN — это на сегодняшний день один из самых безопасных и скоростных протоколов передачи данных, с открытым исходным кодом. Он необходим для создания безопасного «туннеля» связывающего клиентский и серверный компьютеры, вся информация в котором шифруется с помощью библиотеки OpenSSL, а для передачи используются транспортные протоколы UDP и TCP, на которых базируется Интернет. Структура протокола Опен ВПН позволяет его использовать на компьютерах находящихся за HTTP и SOCKS прокси-серверами, подключённых через NAT и различные сетевые фильтры. Проще говоря, если на вашем компьютере есть подключение к интернету, то практически гарантировано вы сможете подключиться и к VPN-серверу.
Часто OpenVPN применяется для безопасного удалённого подключения к частной сети, например работники могут подключаться к внутренней сети предприятия и использовать находящиеся в ней общие сетевые папки, базы данных, принтеры и т.д. Второй распространённый способ применения — создание шифрованного туннеля между своим компьютером и сервером в интернете для безопасной передачи данных. Это позволяет обойти ограничения на доступ к сайтам налагаемые провайдером, так как все запросы идут в шифрованном виде и он попросту не знает, с какими сайтами и какими данными вы обмениваетесь, кроме того это позволяет сохранить анонимность в Интернете, так как во всех логах будет фигурировать IP-адрес VPN-сервера к которому вы подключены, а не ваш реальный IP.
В большинстве случаев конфиденциальность передаваемых данных обеспечивается 256-битным шифрованием OpenSSL, однако могут использоваться и другие шифры, например, Blowfish, AES, 3DES, CAST-128 или Camellia. Неоднократные аудиты протокола позволили выявить и исправить несколько незначительных ошибок, но при этом конфиденциальность передаваемых данных не находилась под угрозой, поэтому OpenVPN можно назвать одним из самых безопасных протоколов.
Кроме клиента с графическим интерфейсом, необходимого для подключения к северам, в состав установочного пакета входит и OpenVPN сервер с помощью которого можно настроить на компьютерах с операционной системой Windows полноценный OpenVPN Access Server. Обратите внимание, что скачиваемые установочные пакеты OpenVPN на русском языке подходят как для 64-битных, так и для 32-битных операционных систем, но версии для Windows 7 и Windows 10 различаются. Вне зависимости от того, версию для какой операционной системы вы выберите, установочный пакет содержит в себе графический интерфейс OpenVPN GUI, а так же клиент для подключения и сервер OpenVPN.
OpenVPN GUI
Installation Instructions for OpenVPN GUI for Windows
OpenVPN-GUI has been bundled with OpenVPN installers for a long time, so there
is rarely a need to install it separately. Bleeding-edge
versions of OpenVPN-GUI are available in OpenVPN snapshot
installers based on Git master
branch. OpenVPN-GUI gets installed by default in all OpenVPN installers.
Installation using the official OpenVPN installers
- Download an OpenVPN installer
- If you have a previous version of OpenVPN GUI running, shut it down.
Make sure it’s closed by ALL logged on users. - Run the OpenVPN installer
Manual installation of OpenVPN GUI
- First install OpenVPN using an official installer as described above.
- Build your own version of OpenVPN GUI from source. See BUILD.rst
for build instructions. From the build tree copy openvpn-gui.exe,
libopenvpn_plap.dll, openvpn-plap-install.reg and openvpn-plap-uninstall.reg
to OpenVPN’s bin folder.
Default is C:Program FilesOpenVPNbin. You must put it in this folder
because OpenVPN GUI depends on the OpenSSL DLLs installed in this folder by
OpenVPN.
Configuring OpenVPN GUI to start on Windows logon
OpenVPN GUI can be configured to start automatically on logon to Windows from
its setting menu. This is default behavior for all users if OpenVPN GUI was
installed by an OpenVPN 2.4 installer using default installer options.
Adding an OpenVPN configuration file
To launch a VPN connections using OpenVPN GUI you need to add an OpenVPN
configuration file with .ovpn suffix. Any text editor (e.g. notepad.exe) can be
used to create a OpenVPN configuration files. Note that log and log-append
options are ignored as OpenVPN GUI redirects the normal output to a log file
itself. There are sample config files in the sample-config folder. Please
refer to the OpenVPN How To for more
information regarding creating the configuration file.
Once the configuration file is ready, you need to let OpenVPN GUI know about it.
There are three ways to do this:
- Place the file into the system-wide location, usually
C:Program FilesOpenVPNconfig, or any of its immediate
subdirectories. This VPN connection will be visible for all users of the
system. - Place the file into C:UsersusernameOpenVPNconfig, or any of its
immediate subdirectories. The configuration file is only visible for the
user in question. If the user is not a member of the built-in «Administrators»
group or «OpenVPN Administrators» group and tries to launch such a connection,
OpenVPN GUI pops up a UAC, offering to create the latter group (if missing)
and to add the user to it. This will only work if admin-level credentials are
available. - Use the «Import file» function in OpenVPN GUI itself
- See the section on Persistent or Pre-started connections
for how to use OpenVPN GUI to conftrol configurations in
C:Program FilesOpenVPNconfig-auto that are started by the automatic service.
Using OpenVPN GUI
When OpenVPN GUI is started your OpenVPN config folders
(C:UsersusernameOpenVPNconfig and
C:Program FilesOpenVPNconfig) will be scanned for .ovpn files and the
OpenVPN GUI icon will appear in the system tray. Each OpenVPN configuration
file shows up as a separate menu item in the OpenVPN GUI tray, allowing you to
selectively connect to and disconnect to your VPNs. The config dir will be
re-scanned for new config files every time you open the OpenVPN GUI menu by
right-clicking the icon.
When you choose to connect to a site OpenVPN GUI will launch openvpn with
the specified config file. If you use a passphrase protected key you will be
prompted for the passphrase.
If you want OpenVPN GUI to start a connection automatically when it’s started,
you can use the —connect cmd-line option. The extension of the config file
may be optionally included. Example:
openvpn-gui --connect office.ovpn OR openvpn-gui --connect office
Starting version 11.34, any connections active when OpenVPN GUI exits or the user
logs out are automatically reconnected when OpenVPN GUI is restarted.
To get help with OpenVPN GUI please use one of the official OpenVPN support
channels.
Running OpenVPN GUI
Run OpenVPN-GUI as normal user by double clicking on the icon. No
administrative privileges or runas-administrator options are required.
It just works as limited user with the help of Interactive Service which
is enabled by default.
Persistent or Pre-started connections
Starting release 2.5.8 (GUI version 11.30), OpenVPN GUI can
control connections started by the «automatic service»
(OpenVPNService) — also referred to as persistent connections.
OpenVPNService, if running, starts all connection profiles
listed in the config-auto directory in the installation path.
By default, such connections are scanned for, and attempt is
made to attach to their management interfaces if available.
User can then view the status of these connections, and disconnect,
reconnect, detach or re-attach them using the menu items.
It requires that such connections be started with
—management 127.0.0.1 port [pw-file] option in their config file.
pw-file containing a password is optional, but highly recommended.
The password should be a single line of text, preferably shorter than 128
characters of plain ascii.
Further, if —auth-user-pass or any such options requiring
interactive user input are present, the config file must also
contain —management-query-passwords.
This feature may be controlled by changing the Persistent Connections
setting in the General tab of the Settings menu: choose auto
for the default behaviour described above, manual to enumerate
and list such connections but not auto-attach, or disable to not scan
auto-started connection profiles.
Interactively starting connections before logon
Starting release 2.6 (GUI version 11.30), «Start Before Logon»
aka Pre-Logon Access Provider is supported. This feature is not
enabled by default. It may be enabled during installation or
through the General Settings menu of the GUI via the
Start Before Logon check mark.
Only persistent connection profiles described in the previous
section will be listed on the login screen. Ensure that
connections that may be interactively started from login
screen are setup in the config-auto folder, OpenVPNService
is running, and these connections are visible and controllable
from the GUI.
Once those pre-requisites are satisfied, the login screen will
display an icon for Pre-Logon Access Providers, clicking which
will bring up a list of OpenVPN connection profiles available, and
allow connecting or disconnecting them interactively.
Run Connect/Disconnect/Preconnect Scripts
There are three different scripts that OpenVPN GUI can execute to help
with different tasks like mapping network drives.
- Preconnect If a file named «xxx_pre.bat» exist in the config folder
- where xxx is the same as your OpenVPN config file name,
this will be executed BEFORE the OpenVPN tunnel is established. - Connect If a file named «xxx_up.bat» exist in the config folder
- where xxx is the same as your OpenVPN config file name,
this will be executed AFTER the OpenVPN tunnel is established. - Disconnect If a file named «xxx_down.bat» exist in the config folder
- where xxx is the same as your OpenVPN config file name,
this will be executed BEFORE the OpenVPN tunnel is closed.
The outputs of these scripts are redirected to «xxx_pre.log»,
«xxx_up.log» and «xxx_down.log» respectively. These log
files are created in the log_dir and over-written during
each evocation.
Send Commands to a Running Instance of OpenVPN GUI
When an instance of the GUI is running, certain commands may be sent to
it using the command line interface using the following syntax:
openvpn-gui.exe --command *cmd* [*args*]
Currently supported cmds are
- connect
config-name - Connect the configuration named config-name (excluding the
extension .ovpn). If already connected, show the status window. - disconnect
config-name - Disconnect the configuration named config-name if connected.
- reconnect
config-name - Disconnect and then reconnect the configuration named config-name
if connected. - disconnect_all
- Disconnect all active connections.
- silent_connection 0 | 1
- Set the silent connection flag on (1) or off (0)
- exit
- Disconnect all active connections and terminate the GUI process
- rescan
- Rescan the config folders for changes
- import
path - Import the config file pointed to by
path.
If no running instance of the GUI is found, these commands do nothing
except for —command connect config-name which gets interpreted
as —connect config-name
Registry Values affecting the OpenVPN GUI operation
Parameters taken from the global registry values in
HKEY_LOCAL_MACHINESOFTWAREOpenVPN key
- (Default)
- The installation directory of openvpn (e.g., C:Program FilesOpenVPN).
This value must be present. - config_dir
- The global configuration file directory. Defaults to
C:Program FilesOpenVPNconfig - exe_path
- path to openvpn.exe, defaults to C:Program FilesOpenVPNbinopenvpn.exe
- priority
-
the windows priority class for each instantiated OpenVPN process,
can be one of:- IDLE_PRIORITY_CLASS
- BELOW_NORMAL_PRIORITY_CLASS
- NORMAL_PRIORITY_CLASS (default)
- ABOVE_NORMAL_PRIORITY_CLASS
- HIGH_PRIORITY_CLASS
- ovpn_admin_group
- The windows group whose membership allows the user to start any configuration file
in their profile (not just those installed by the administrator in the global
config directory). Default: «OpenVPN Administrators». - disable_save_passwords
- Set to a nonzero value to disable the password save feature.
Default: 0 - auto_config_dir
- If persistent connection support is enabled and the so-called automatic
service (OpenVPNService) is running, any config files in this folder are
scanned and listed in the list of connection profiles.
User Preferences
All other OpenVPN GUI registry values are located below the
HKEY_CURRENT_USERSOFTWAREOpenVPN-GUI key. In a fresh
installation none of these values are present and are not
required for the operation of the program. These keys are only
used for persisting user’s preferences, and the key names
and their values are subject to change.
The user is not expected to edit any of these values directly.
Instead, edit all preferences using the settings menu.
- config_dir
- The user-specific configuration file directory: defaults to
C:UsersusernameOpenVPNconfig.
The GUI parses this directory for configuration files before
parsing the global config_dir. - config_ext
- file extension on configuration files, defaults to ovpn
- connectscript_timeout
- Time in seconds to wait for the connect script to finish. If set to 0
the exitcode of the script is not checked. - disconnectscript_timeout
- Time in seconds to wait for the disconnect script to finish. Must be a
value between 1-99. - preconnectscript_timeout
- Time in seconds to wait for the preconnect script to finish. Must be a
value between 1-99. - log_dir
- log file directory, defaults to C:UsersusernameOpenVPNlog
- log_append
- if set to «0», the log file will be truncated every time you start a
connection. If set to «1», the log will be appended to the log file. - silent_connection
- If set to «1», the status window with the OpenVPN log output will
not be shown while connecting. Warnings such as interactive service
not started or multiple config files with same name are also suppressed. - show_balloon
-
0: Never show any connected balloon
1: Show balloon after initial connection is established
2: Show balloon even after re-connects
- config_menu_view
-
0: Use a hierarchical (nested) display of config menu reflecting the directory sturcture of config files if the number of configs exceed 25, else use a flat display
1: Force flat menu
2: Force nested menu
- disable_popup_messages
- If set to 1 echo messages are ignored
- popup_mute_interval
- Amount of time in hours for which repeated echo messages are not displayed.
Defaults to 24 hours. - management_port_offset
- The management interface port is chosen as this offset plus a connection specific index.
Allowed values: 1 to 61000, defaults to 25340.
All of these registry options are also available as cmd-line options.
Use «openvpn-gui —help» for more info about cmd-line options.
Building OpenVPN GUI from source
See BUILD.rst for build instructions.