The OpenVPN community project team is proud to release OpenVPN 2.6.0. This is a new stable release with some major new features.
For details see: Changes.rst
The Changes document also contains a section with workarounds for common problems encountered when using OpenVPN with OpenSSL 3.
New features and improvements in 2.6.0 compared to 2.5.8:
- Data Channel Offload (DCO) kernel acceleration support for Windows, Linux, and FreeBSD.
- OpenSSL 3 support.
- Improved handling of tunnel MTU, including support for pushable MTU.
- Outdated cryptographic algorithms disabled by default, but there are options to override if necessary.
- Reworked TLS handshake, making OpenVPN immune to replay-packet state exhaustion attacks.
- Added —peer-fingerprint mode for a more simplistic certificate setup and verification.
- Added Pre-Logon Access Provider support to OpenVPN GUI for Windows.
- Improved protocol negotiation, leading to faster connection setup.
- Included openvpn-gui updated to 11.36.0.0. See CHANGES.rst.
- Updated easy-rsa3 bundled with the installer on Windows.
- Various bug fixes.
Windows 64-bit MSI installer |
GnuPG Signature | OpenVPN-2.6.0-I003-amd64.msi |
Windows ARM64 MSI installer |
GnuPG Signature | OpenVPN-2.6.0-I003-arm64.msi |
Windows 32-bit MSI installer |
GnuPG Signature | OpenVPN-2.6.0-I003-x86.msi |
Source zip |
GnuPG Signature | openvpn-2.6.0.tar.gz |
The OpenVPN community project team is proud to release OpenVPN 2.5.4. This release include a number of fixes and small improvements. One of the fixes is to password prompting on windows console when stderr redirection is in use — this breaks 2.5.x on Win11/ARM, and might also break on Win11/amd64. Windows executable and libraries are now built natively on Windows using MSVC, not cross-compiled on Linux as with earlier 2.5 releases. Windows installers include updated OpenSSL and new OpenVPN GUI. The latter includes several improvements, the most important of which is the ability to import profiles from URLs where available. Installer version I602 fixes loading of pkcs11 files on Windows. Installer version I603 fixes a bug in the version number as seen by Windows (was 2.5..4, not 2.5.4). Installer I604 fixes some small Windows issues.
Source tarball (gzip) |
GnuPG Signature | openvpn-2.5.4.tar.gz |
Source tarball (xz) |
GnuPG Signature | openvpn-2.5.4.tar.xz |
Source zip |
GnuPG Signature | openvpn-2.5.4.zip |
Windows 32-bit MSI installer |
GnuPG Signature | OpenVPN-2.5.4-I604-x86.msi |
Windows 64-bit MSI installer |
GnuPG Signature | OpenVPN-2.5.4-I604-amd64.msi |
Windows ARM64 MSI installer |
GnuPG Signature | OpenVPN-2.5.4-I604-arm64.msi |
Overview of changes since OpenVPN 2.4
Faster connections
Crypto specific changes
- ChaCha20-Poly1305 cipher in the OpenVPN data channel (Requires OpenSSL 1.1.0 or newer)
- Improved TLS 1.3 support when using OpenSSL 1.1.1 or newer
- Client-specific tls-crypt keys (—tls-crypt-v2)
- Improved Data channel cipher negotiation
- Removal of BF-CBC support in default configuration (see below for possible incompatibilities)
Server-side improvements
- HMAC based auth-token support for seamless reconnects to standalone servers or a group of servers.
- Asynchronous (deferred) authentication support for auth-pam plugin
- Asynchronous (deferred) support for client-connect scripts and plugins
Network-related changes
- Support IPv4 configs with /31 netmasks now
- 802.1q VLAN support on TAP servers
- IPv6-only tunnels
- New option —block-ipv6 to reject all IPv6 packets (ICMPv6)
Linux-specific features
- VRF support
- Netlink integration (OpenVPN no longer needs to execute ifconfig/route or ip commands)
Windows-specific features
- Wintun driver support, a faster alternative to tap-windows6
- Setting tun/tap interface MTU
- Setting DHCP search domain
- Allow unicode search string in —cryptoapicert option
- EasyRSA3, a modern take on OpenVPN CA management
- MSI installer
Important notices
BF-CBC cipher is no longer the default
Cipher handling for the data channel cipher has been significantly changed between OpenVPN 2.3/2.4 and v2.5, most notably there are no «default cipher BF-CBC» anymore because it is no longer considered a reasonable default. BF-CBC is still available, but it needs to be explicitly configured now.
For connections between OpenVPN 2.4 and v2.5 clients and servers, both ends will be able to negotiate a better cipher than BF-CBC. By default they will select one of the AES-GCM ciphers, but this can be influenced using the —data-ciphers setting.
Connections between OpenVPN 2.3 and v2.5 that have no —cipher setting in the config (= defaulting to BF-CBC and not being negotiation-capable) must be updated. Unless BF-CBC is included in —data-ciphers or there is a «—cipher BF-CBC» in the OpenVPN 2.5 config, a v2.5 client or server will refuse to talk to a v2.3 server or client, because it has no common data channel cipher and negotiating a cipher is not possible. Generally, we recommend upgrading such setups to OpenVPN 2.4 or v2.5. If upgrading is not possible we recommend adding data-ciphers AES-256-GCM:AES-128-GCM:AES-128-CBC (for v2.5+) or cipher AES-128-CBC (v2.4.x and older) to the configuration of all clients and servers.
If you really need to use an unsupported OpenVPN 2.3 (or even older) release and need to stay on BF-CBC (not recommended), the OpenVPN 2.5 based client will need a config file change to re-enable BF-CBC. But be warned that BF-CBC and other related weak ciphers will be removed in coming OpenVPN major releases.
Connectivity to some VPN service provider may break
Connecting with an OpenVPN 2.5 client to at least one commercial VPN service that
implemented their own cipher negotiation method that always reports back that it is using BF-CBC to the client is broken in v2.5. This has always caused warning about mismatch ciphers. We have been in contact with some service providers and they are looking into it. This is not something the OpenVPN community can fix. If your commercial VPN does not work with a v2.5 client, complain to the VPN service provider.
More details on these new features as well as a list of deprecated features and user-visible changes are available in Changes.rst.
The OpenVPN community project team is proud to release OpenVPN 2.5.3. Besides a number of small improvements and bug fixes, this release fixes a possible security issue with OpenSSL config autoloading on Windows (CVE-2021-3606). Updated OpenVPN GUI is also included in Windows installers.
Source tarball (gzip) |
GnuPG Signature | openvpn-2.5.3.tar.gz |
Source tarball (xz) |
GnuPG Signature | openvpn-2.5.3.tar.xz |
Source zip |
GnuPG Signature | openvpn-2.5.3.zip |
Windows 32-bit MSI installer |
GnuPG Signature | OpenVPN-2.5.3-I601-x86.msi |
Windows 64-bit MSI installer |
GnuPG Signature | OpenVPN-2.5.3-I601-amd64.msi |
Windows ARM64 MSI installer |
GnuPG Signature | OpenVPN-2.5.3-I601-arm64.msi |
Overview of changes since OpenVPN 2.4
Faster connections
- Connections setup is now much faster
Crypto specific changes
- ChaCha20-Poly1305 cipher in the OpenVPN data channel (Requires OpenSSL 1.1.0 or newer)
- Improved TLS 1.3 support when using OpenSSL 1.1.1 or newer
- Client-specific tls-crypt keys (—tls-crypt-v2)
- Improved Data channel cipher negotiation
- Removal of BF-CBC support in default configuration (see below for possible incompatibilities)
Server-side improvements
- HMAC based auth-token support for seamless reconnects to standalone servers or a group of servers.
- Asynchronous (deferred) authentication support for auth-pam plugin
- Asynchronous (deferred) support for client-connect scripts and plugins
Network-related changes
- Support IPv4 configs with /31 netmasks now
- 802.1q VLAN support on TAP servers
- IPv6-only tunnels
- New option —block-ipv6 to reject all IPv6 packets (ICMPv6)
Linux-specific features
- VRF support
- Netlink integration (OpenVPN no longer needs to execute ifconfig/route or ip commands)
Windows-specific features
- Wintun driver support, a faster alternative to tap-windows6
- Setting tun/tap interface MTU
- Setting DHCP search domain
- Allow unicode search string in —cryptoapicert option
- EasyRSA3, a modern take on OpenVPN CA management
- MSI installer
Important notices
BF-CBC cipher is no longer the default
Cipher handling for the data channel cipher has been significantly changed between OpenVPN 2.3/2.4 and v2.5, most notably there are no «default cipher BF-CBC» anymore because it is no longer considered a reasonable default. BF-CBC is still available, but it needs to be explicitly configured now.
For connections between OpenVPN 2.4 and v2.5 clients and servers, both ends will be able to negotiate a better cipher than BF-CBC. By default they will select one of the AES-GCM ciphers, but this can be influenced using the —data-ciphers setting.
Connections between OpenVPN 2.3 and v2.5 that have no —cipher setting in the config (= defaulting to BF-CBC and not being negotiation-capable) must be updated. Unless BF-CBC is included in —data-ciphers or there is a «—cipher BF-CBC» in the OpenVPN 2.5 config, a v2.5 client or server will refuse to talk to a v2.3 server or client, because it has no common data channel cipher and negotiating a cipher is not possible. Generally, we recommend upgrading such setups to OpenVPN 2.4 or v2.5. If upgrading is not possible we recommend adding data-ciphers AES-256-GCM:AES-128-GCM:AES-128-CBC (for v2.5+) or cipher AES-128-CBC (v2.4.x and older) to the configuration of all clients and servers.
If you really need to use an unsupported OpenVPN 2.3 (or even older) release and need to stay on BF-CBC (not recommended), the OpenVPN 2.5 based client will need a config file change to re-enable BF-CBC. But be warned that BF-CBC and other related weak ciphers will be removed in coming OpenVPN major releases.
Connectivity to some VPN service provider may break
Connecting with an OpenVPN 2.5 client to at least one commercial VPN service that
implemented their own cipher negotiation method that always reports back that it is using BF-CBC to the client is broken in v2.5. This has always caused warning about mismatch ciphers. We have been in contact with some service providers and they are looking into it. This is not something the OpenVPN community can fix. If your commercial VPN does not work with a v2.5 client, complain to the VPN service provider.
More details on these new features as well as a list of deprecated features and user-visible changes are available in Changes.rst.
The OpenVPN community project team is proud to release OpenVPN 2.5.2. It fixes two related security vulnerabilities (CVE-2020-15078) which under very specific circumstances allow tricking a server using delayed authentication (plugin or management) into returning a PUSH_REPLY before the AUTH_FAILED message, which can possibly be used to gather information about a VPN setup. In combination with «—auth-gen-token» or a user-specific token auth solution it can be possible to get access to a VPN with an otherwise-invalid account. OpenVPN 2.5.2 also includes other bug fixes and improvements. Updated OpenSSL and OpenVPN GUI are included in Windows installers.
Source tarball (gzip) |
GnuPG Signature | openvpn-2.5.2.tar.gz |
Source tarball (xz) |
GnuPG Signature | openvpn-2.5.2.tar.xz |
Source zip |
GnuPG Signature | openvpn-2.5.2.zip |
Windows 32-bit MSI installer |
GnuPG Signature | OpenVPN-2.5.2-I601-x86.msi |
Windows 64-bit MSI installer |
GnuPG Signature | OpenVPN-2.5.2-I601-amd64.msi |
Overview of changes since OpenVPN 2.4
Faster connections
- Connections setup is now much faster
Crypto specific changes
- ChaCha20-Poly1305 cipher in the OpenVPN data channel (Requires OpenSSL 1.1.0 or newer)
- Improved TLS 1.3 support when using OpenSSL 1.1.1 or newer
- Client-specific tls-crypt keys (—tls-crypt-v2)
- Improved Data channel cipher negotiation
- Removal of BF-CBC support in default configuration (see below for possible incompatibilities)
Server-side improvements
- HMAC based auth-token support for seamless reconnects to standalone servers or a group of servers.
- Asynchronous (deferred) authentication support for auth-pam plugin
- Asynchronous (deferred) support for client-connect scripts and plugins
Network-related changes
- Support IPv4 configs with /31 netmasks now
- 802.1q VLAN support on TAP servers
- IPv6-only tunnels
- New option —block-ipv6 to reject all IPv6 packets (ICMPv6)
Linux-specific features
- VRF support
- Netlink integration (OpenVPN no longer needs to execute ifconfig/route or ip commands)
Windows-specific features
- Wintun driver support, a faster alternative to tap-windows6
- Setting tun/tap interface MTU
- Setting DHCP search domain
- Allow unicode search string in —cryptoapicert option
- EasyRSA3, a modern take on OpenVPN CA management
- MSI installer
Important notices
BF-CBC cipher is no longer the default
Cipher handling for the data channel cipher has been significantly changed between OpenVPN 2.3/2.4 and v2.5, most notably there are no «default cipher BF-CBC» anymore because it is no longer considered a reasonable default. BF-CBC is still available, but it needs to be explicitly configured now.
For connections between OpenVPN 2.4 and v2.5 clients and servers, both ends will be able to negotiate a better cipher than BF-CBC. By default they will select one of the AES-GCM ciphers, but this can be influenced using the —data-ciphers setting.
Connections between OpenVPN 2.3 and v2.5 that have no —cipher setting in the config (= defaulting to BF-CBC and not being negotiation-capable) must be updated. Unless BF-CBC is included in —data-ciphers or there is a «—cipher BF-CBC» in the OpenVPN 2.5 config, a v2.5 client or server will refuse to talk to a v2.3 server or client, because it has no common data channel cipher and negotiating a cipher is not possible. Generally, we recommend upgrading such setups to OpenVPN 2.4 or v2.5. If upgrading is not possible we recommend adding data-ciphers AES-256-GCM:AES-128-GCM:AES-128-CBC (for v2.5+) or cipher AES-128-CBC (v2.4.x and older) to the configuration of all clients and servers.
If you really need to use an unsupported OpenVPN 2.3 (or even older) release and need to stay on BF-CBC (not recommended), the OpenVPN 2.5 based client will need a config file change to re-enable BF-CBC. But be warned that BF-CBC and other related weak ciphers will be removed in coming OpenVPN major releases.
Connectivity to some VPN service provider may break
Connecting with an OpenVPN 2.5 client to at least one commercial VPN service that
implemented their own cipher negotiation method that always reports back that it is using BF-CBC to the client is broken in v2.5. This has always caused warning about mismatch ciphers. We have been in contact with some service providers and they are looking into it. This is not something the OpenVPN community can fix. If your commercial VPN does not work with a v2.5 client, complain to the VPN service provider.
More details on these new features as well as a list of deprecated features and user-visible changes are available in Changes.rst.
The OpenVPN community project team is proud to release OpenVPN 2.5.1. It includes several bug fixes and improvements as well as updated OpenSSL and OpenVPN GUI for Windows.
Source tarball (gzip) |
GnuPG Signature | openvpn-2.5.1.tar.gz |
Source tarball (xz) |
GnuPG Signature | openvpn-2.5.1.tar.xz |
Source zip |
GnuPG Signature | openvpn-2.5.1.zip |
Windows 32-bit MSI installer |
GnuPG Signature | OpenVPN-2.5.1-I601-x86.msi |
Windows 64-bit MSI installer |
GnuPG Signature | OpenVPN-2.5.1-I601-amd64.msi |
Overview of changes since OpenVPN 2.4
Faster connections
- Connections setup is now much faster
Crypto specific changes
- ChaCha20-Poly1305 cipher in the OpenVPN data channel (Requires OpenSSL 1.1.0 or newer)
- Improved TLS 1.3 support when using OpenSSL 1.1.1 or newer
- Client-specific tls-crypt keys (—tls-crypt-v2)
- Improved Data channel cipher negotiation
- Removal of BF-CBC support in default configuration (see below for possible incompatibilities)
Server-side improvements
- HMAC based auth-token support for seamless reconnects to standalone servers or a group of servers.
- Asynchronous (deferred) authentication support for auth-pam plugin
- Asynchronous (deferred) support for client-connect scripts and plugins
Network-related changes
- Support IPv4 configs with /31 netmasks now
- 802.1q VLAN support on TAP servers
- IPv6-only tunnels
- New option —block-ipv6 to reject all IPv6 packets (ICMPv6)
Linux-specific features
- VRF support
- Netlink integration (OpenVPN no longer needs to execute ifconfig/route or ip commands)
Windows-specific features
- Wintun driver support, a faster alternative to tap-windows6
- Setting tun/tap interface MTU
- Setting DHCP search domain
- Allow unicode search string in —cryptoapicert option
- EasyRSA3, a modern take on OpenVPN CA management
- MSI installer
Important notices
BF-CBC cipher is no longer the default
Cipher handling for the data channel cipher has been significantly changed between OpenVPN 2.3/2.4 and v2.5, most notably there are no «default cipher BF-CBC» anymore because it is no longer considered a reasonable default. BF-CBC is still available, but it needs to be explicitly configured now.
For connections between OpenVPN 2.4 and v2.5 clients and servers, both ends will be able to negotiate a better cipher than BF-CBC. By default they will select one of the AES-GCM ciphers, but this can be influenced using the —data-ciphers setting.
Connections between OpenVPN 2.3 and v2.5 that have no —cipher setting in the config (= defaulting to BF-CBC and not being negotiation-capable) must be updated. Unless BF-CBC is included in —data-ciphers or there is a «—cipher BF-CBC» in the OpenVPN 2.5 config, a v2.5 client or server will refuse to talk to a v2.3 server or client, because it has no common data channel cipher and negotiating a cipher is not possible. Generally, we recommend upgrading such setups to OpenVPN 2.4 or v2.5. If upgrading is not possible we recommend adding data-ciphers AES-256-GCM:AES-128-GCM:AES-128-CBC (for v2.5+) or cipher AES-128-CBC (v2.4.x and older) to the configuration of all clients and servers.
If you really need to use an unsupported OpenVPN 2.3 (or even older) release and need to stay on BF-CBC (not recommended), the OpenVPN 2.5 based client will need a config file change to re-enable BF-CBC. But be warned that BF-CBC and other related weak ciphers will be removed in coming OpenVPN major releases.
Connectivity to some VPN service provider may break
Connecting with an OpenVPN 2.5 client to at least one commercial VPN service that
implemented their own cipher negotiation method that always reports back that it is using BF-CBC to the client is broken in v2.5. This has always caused warning about mismatch ciphers. We have been in contact with some service providers and they are looking into it. This is not something the OpenVPN community can fix. If your commercial VPN does not work with a v2.5 client, complain to the VPN service provider.
More details on these new features as well as a list of deprecated features and user-visible changes are available in Changes.rst.
The OpenVPN community project team is proud to release OpenVPN 2.5.0 which is a new major release with many new features.
Source tarball (gzip) |
GnuPG Signature | openvpn-2.5.0.tar.gz |
Source tarball (xz) |
GnuPG Signature | openvpn-2.5.0.tar.xz |
Source zip |
GnuPG Signature | openvpn-2.5.0.zip |
Windows 32-bit MSI installer |
GnuPG Signature | OpenVPN-2.5.0-I601-x86.msi |
Windows 64-bit MSI installer |
GnuPG Signature | OpenVPN-2.5.0-I601-amd64.msi |
Overview of changes since OpenVPN 2.4
Faster connections
- Connections setup is now much faster
Crypto specific changes
- ChaCha20-Poly1305 cipher in the OpenVPN data channel (Requires OpenSSL 1.1.0 or newer)
- Improved TLS 1.3 support when using OpenSSL 1.1.1 or newer
- Client-specific tls-crypt keys (—tls-crypt-v2)
- Improved Data channel cipher negotiation
- Removal of BF-CBC support in default configuration (see below for possible incompatibilities)
Server-side improvements
- HMAC based auth-token support for seamless reconnects to standalone servers or a group of servers.
- Asynchronous (deferred) authentication support for auth-pam plugin
- Asynchronous (deferred) support for client-connect scripts and plugins
Network-related changes
- Support IPv4 configs with /31 netmasks now
- 802.1q VLAN support on TAP servers
- IPv6-only tunnels
- New option —block-ipv6 to reject all IPv6 packets (ICMPv6)
Linux-specific features
- VRF support
- Netlink integration (OpenVPN no longer needs to execute ifconfig/route or ip commands)
Windows-specific features
- Wintun driver support, a faster alternative to tap-windows6
- Setting tun/tap interface MTU
- Setting DHCP search domain
- Allow unicode search string in —cryptoapicert option
- EasyRSA3, a modern take on OpenVPN CA management
- MSI installer
Important notices
BF-CBC cipher is no longer the default
Cipher handling for the data channel cipher has been significantly changed between OpenVPN 2.3/2.4 and v2.5, most notably there are no «default cipher BF-CBC» anymore because it is no longer considered a reasonable default. BF-CBC is still available, but it needs to be explicitly configured now.
For connections between OpenVPN 2.4 and v2.5 clients and servers, both ends will be able to negotiate a better cipher than BF-CBC. By default they will select one of the AES-GCM ciphers, but this can be influenced using the —data-ciphers setting.
Connections between OpenVPN 2.3 and v2.5 that have no —cipher setting in the config (= defaulting to BF-CBC and not being negotiation-capable) must be updated. Unless BF-CBC is included in —data-ciphers or there is a «—cipher BF-CBC» in the OpenVPN 2.5 config, a v2.5 client or server will refuse to talk to a v2.3 server or client, because it has no common data channel cipher and negotiating a cipher is not possible. Generally, we recommend upgrading such setups to OpenVPN 2.4 or v2.5. If upgrading is not possible we recommend adding data-ciphers AES-256-GCM:AES-128-GCM:AES-128-CBC (for v2.5+) or cipher AES-128-CBC (v2.4.x and older) to the configuration of all clients and servers.
If you really need to use an unsupported OpenVPN 2.3 (or even older) release and need to stay on BF-CBC (not recommended), the OpenVPN 2.5 based client will need a config file change to re-enable BF-CBC. But be warned that BF-CBC and other related weak ciphers will be removed in coming OpenVPN major releases.
Connectivity to some VPN service provider may break
Connecting with an OpenVPN 2.5 client to at least one commercial VPN service that
implemented their own cipher negotiation method that always reports back that it is using BF-CBC to the client is broken in v2.5. This has always caused warning about mismatch ciphers. We have been in contact with some service providers and they are looking into it. This is not something the OpenVPN community can fix. If your commercial VPN does not work with a v2.5 client, complain to the VPN service provider.
More details on these new features as well as a list of deprecated features and user-visible changes are available in Changes.rst.
The OpenVPN community project team is proud to release OpenVPN 2.4.11. It fixes two related security vulnerabilities (CVE-2020-15078) which under very specific circumstances allow tricking a server using delayed authentication (plugin or management) into returning a PUSH_REPLY before the AUTH_FAILED message, which can possibly be used to gather information about a VPN setup. This release also includes other bug fixes and improvements. The I602 Windows installers fix a possible security issue with OpenSSL config autoloading on Windows (CVE-2021-3606). Updated OpenSSL and OpenVPN GUI are included in Windows installers.
Source Tarball (gzip) |
GnuPG Signature | openvpn-2.4.11.tar.gz |
Source Tarball (xz) |
GnuPG Signature | openvpn-2.4.11.tar.xz |
Source Zip |
GnuPG Signature | openvpn-2.4.11.zip |
Windows 7/8/8.1/Server 2012r2 installer (NSIS) |
GnuPG Signature | openvpn-install-2.4.11-I602-Win7.exe |
Windows 10/Server 2016/Server 2019 installer (NSIS) |
GnuPG Signature | openvpn-install-2.4.11-I602-Win10.exe |
A summary of the changes is available in Changes.rst, and a full list of changes is available here.
Please note that LibreSSL is not a supported crypto backend. We accept patches and we do test on OpenBSD 6.0 which comes with LibreSSL, but if newer versions of LibreSSL break API compatibility we do not take responsibility to fix that.
Also note that Windows installers have been built with NSIS version that has been patched against several NSIS installer code execution and privilege escalation problems. Based on our testing, though, older Windows versions such as Windows 7 might not benefit from these fixes. We thus strongly encourage you to always move NSIS installers to a non-user-writeable location before running them.
Please note that OpenVPN 2.4 installers will not work on Windows XP. The last OpenVPN version that supports Windows XP is 2.3.18, which is downloadable as 32-bit and 64-bit versions.
If you find a bug in this release, please file a bug report to our Trac bug tracker. In uncertain cases please contact our developers first, either using the openvpn-devel mailinglist or the developer IRC channel (#openvpn-devel at irc.libera.chat). For generic help take a look at our official documentation, wiki, forums, openvpn-users mailing list and user IRC channel (#openvpn at irc.libera.chat).
Important: you will need to use the correct installer for your operating system. The Windows 10 installer works on Windows 10 and Windows Server 2016/2019. The Windows 7 installer will work on Windows 7/8/8.1/Server 2012r2. This is because of Microsoft’s driver signing requirements are different for kernel-mode devices drivers, which in our case affects OpenVPN’s tap driver (tap-windows6).
This is primarily a maintenance release with bugfixes and small improvements. Windows installers include the latest OpenSSL version (1.1.1i) which includes security fixes.
A summary of the changes is available in Changes.rst, and a full list of changes is available here.
Please note that LibreSSL is not a supported crypto backend. We accept patches and we do test on OpenBSD 6.0 which comes with LibreSSL, but if newer versions of LibreSSL break API compatibility we do not take responsibility to fix that.
Also note that Windows installers have been built with NSIS version that has been patched against several NSIS installer code execution and privilege escalation problems. Based on our testing, though, older Windows versions such as Windows 7 might not benefit from these fixes. We thus strongly encourage you to always move NSIS installers to a non-user-writeable location before running them.
Please note that OpenVPN 2.4 installers will not work on Windows XP. The last OpenVPN version that supports Windows XP is 2.3.18, which is downloadable as 32-bit and 64-bit versions.
If you find a bug in this release, please file a bug report to our Trac bug tracker. In uncertain cases please contact our developers first, either using the openvpn-devel mailinglist or the developer IRC channel (#openvpn-devel at irc.libera.chat). For generic help take a look at our official documentation, wiki, forums, openvpn-users mailing list and user IRC channel (#openvpn at irc.libera.chat).
Important: you will need to use the correct installer for your operating system. The Windows 10 installer works on Windows 10 and Windows Server 2016/2019. The Windows 7 installer will work on Windows 7/8/8.1/Server 2012r2. This is because of Microsoft’s driver signing requirements are different for kernel-mode devices drivers, which in our case affects OpenVPN’s tap driver (tap-windows6).
Source Tarball (gzip) |
GnuPG Signature | openvpn-2.4.10.tar.gz |
Source Tarball (xz) |
GnuPG Signature | openvpn-2.4.10.tar.xz |
Source Zip |
GnuPG Signature | openvpn-2.4.10.zip |
Windows 7/8/8.1/Server 2012r2 installer (NSIS) |
GnuPG Signature | openvpn-install-2.4.10-I601-Win7.exe |
Windows 10/Server 2016/Server 2019 installer (NSIS) |
GnuPG Signature | openvpn-install-2.4.10-I601-Win10.exe |
Instructions for verifying the signatures are available here.
This release is also available in our own software repositories for Debian and Ubuntu, Supported architectures are i386 and amd64. For details. look here.
The Windows installers are bundled with OpenVPN-GUI — its source code is available on its project page and as tarballs on our alternative download server.
This is primarily a maintenance release with bugfixes and improvements. This release also fixes a security issue (CVE-2020-11810, trac #1272) which allows disrupting service of a freshly connected client that has not yet not negotiated session keys. The vulnerability cannot be used to inject or steal VPN traffic.
A summary of the changes is available in Changes.rst, and a full list of changes is available here.
Please note that LibreSSL is not a supported crypto backend. We accept patches and we do test on OpenBSD 6.0 which comes with LibreSSL, but if newer versions of LibreSSL break API compatibility we do not take responsibility to fix that.
Also note that Windows installers have been built with NSIS version that has been patched against several NSIS installer code execution and privilege escalation problems. Based on our testing, though, older Windows versions such as Windows 7 might not benefit from these fixes. We thus strongly encourage you to always move NSIS installers to a non-user-writeable location before running them. We are moving to MSI installers in OpenVPN 2.5, but OpenVPN 2.4.x will remain NSIS-only.
Compared to OpenVPN 2.3 this is a major update with a large number of new features, improvements and fixes. Some of the major features are AEAD (GCM) cipher and Elliptic Curve DH key exchange support, improved IPv4/IPv6 dual stack support and more seamless connection migration when client’s IP address changes (Peer-ID). Also, the new —tls-crypt feature can be used to increase users’ connection privacy.
OpenVPN GUI bundled with the Windows installer has a large number of new features compared to the one bundled with OpenVPN 2.3. One of major features is the ability to run OpenVPN GUI without administrator privileges. For full details, see the changelog. The new OpenVPN GUI features are documented here.
Please note that OpenVPN 2.4 installers will not work on Windows XP. The last OpenVPN version that supports Windows XP is 2.3.18, which is downloadable as 32-bit and 64-bit versions.
If you find a bug in this release, please file a bug report to our Trac bug tracker. In uncertain cases please contact our developers first, either using the openvpn-devel mailinglist or the developer IRC channel (#openvpn-devel at irc.libera.chat). For generic help take a look at our official documentation, wiki, forums, openvpn-users mailing list and user IRC channel (#openvpn at irc.libera.chat).
Important: you will need to use the correct installer for your operating system. The Windows 10 installer works on Windows 10 and Windows Server 2016/2019. The Windows 7 installer will work on Windows 7/8/8.1/Server 2012r2. This is because of Microsoft’s driver signing requirements are different for kernel-mode devices drivers, which in our case affects OpenVPN’s tap driver (tap-windows6).
Source Tarball (gzip) |
GnuPG Signature | openvpn-2.4.9.tar.gz |
Source Tarball (xz) |
GnuPG Signature | openvpn-2.4.9.tar.xz |
Source Zip |
GnuPG Signature | openvpn-2.4.9.zip |
Windows 7/8/8.1/Server 2012r2 installer (NSIS) |
GnuPG Signature | openvpn-install-2.4.9-I601-Win7.exe |
Windows 10/Server 2016/Server 2019 installer (NSIS) |
GnuPG Signature | openvpn-install-2.4.9-I601-Win10.exe |
NOTE: the GPG key used to sign the release files has been changed since OpenVPN 2.4.0. Instructions for verifying the signatures, as well as the new GPG public key are available here.
We also provide static URLs pointing to latest releases to ease automation. For a list of files look here.
This release is also available in our own software repositories for Debian and Ubuntu, Supported architectures are i386 and amd64. For details. look here.
You can use EasyRSA 2 or EasyRSA 3 for generating your own certificate authority. The former is bundled with Windows installers. The latter is a more modern alternative for UNIX-like operating systems.
The Windows installers are bundled with OpenVPN-GUI — its source code is available on its project page and as tarballs on our alternative download server.
This is primarily a maintenance release with bugfixes and improvements. The Windows installers (I601) have several improvements compared to the previous release:
- New tap-windows6 driver (9.24.2) which fixes some suspend and resume issues
- Latest OpenVPN-GUI
- Considerable performance boost due to new compiler optimization flags
A summary of the changes is available in Changes.rst, and a full list of changes is available here.
Please note that LibreSSL is not a supported crypto backend. We accept patches and we do test on OpenBSD 6.0 which comes with LibreSSL, but if newer versions of LibreSSL break API compatibility we do not take responsibility to fix that.
Also note that Windows installers have been built with NSIS version that has been patched against several NSIS installer code execution and privilege escalation problems. Based on our testing, though, older Windows versions such as Windows 7 might not benefit from these fixes. We thus strongly encourage you to always move NSIS installers to a non-user-writeable location before running them. We are moving to MSI installers in OpenVPN 2.5, but OpenVPN 2.4.x will remain NSIS-only.
Compared to OpenVPN 2.3 this is a major update with a large number of new features, improvements and fixes. Some of the major features are AEAD (GCM) cipher and Elliptic Curve DH key exchange support, improved IPv4/IPv6 dual stack support and more seamless connection migration when client’s IP address changes (Peer-ID). Also, the new —tls-crypt feature can be used to increase users’ connection privacy.
OpenVPN GUI bundled with the Windows installer has a large number of new features compared to the one bundled with OpenVPN 2.3. One of major features is the ability to run OpenVPN GUI without administrator privileges. For full details, see the changelog. The new OpenVPN GUI features are documented here.
Please note that OpenVPN 2.4 installers will not work on Windows XP. The last OpenVPN version that supports Windows XP is 2.3.18, which is downloadable as 32-bit and 64-bit versions.
If you find a bug in this release, please file a bug report to our Trac bug tracker. In uncertain cases please contact our developers first, either using the openvpn-devel mailinglist or the developer IRC channel (#openvpn-devel at irc.libera.chat). For generic help take a look at our official documentation, wiki, forums, openvpn-users mailing list and user IRC channel (#openvpn at irc.libera.chat).
Important: you will need to use the correct installer for your operating system. The Windows 10 installer works on Windows 10 and Windows Server 2016/2019. The Windows 7 installer will work on Windows 7/8/8.1/Server 2012r2. This is because of Microsoft’s driver signing requirements are different for kernel-mode devices drivers, which in our case affects OpenVPN’s tap driver (tap-windows6).
Source Tarball (gzip) |
GnuPG Signature | openvpn-2.4.8.tar.gz |
Source Tarball (xz) |
GnuPG Signature | openvpn-2.4.8.tar.xz |
Source Zip |
GnuPG Signature | openvpn-2.4.8.zip |
Windows 7/8/8.1/Server 2012r2 installer (NSIS) |
GnuPG Signature | openvpn-install-2.4.8-I602-Win7.exe |
Windows 10/Server 2016/Server 2019 installer (NSIS) |
GnuPG Signature | openvpn-install-2.4.8-I602-Win10.exe |
NOTE: the GPG key used to sign the release files has been changed since OpenVPN 2.4.0. Instructions for verifying the signatures, as well as the new GPG public key are available here.
We also provide static URLs pointing to latest releases to ease automation. For a list of files look here.
This release is also available in our own software repositories for Debian and Ubuntu, Supported architectures are i386 and amd64. For details. look here.
You can use EasyRSA 2 or EasyRSA 3 for generating your own certificate authority. The former is bundled with Windows installers. The latter is a more modern alternative for UNIX-like operating systems.
The Windows installers are bundled with OpenVPN-GUI — its source code is available on its project page and as tarballs on our alternative download server.
This is primarily a maintenance release with bugfixes and improvements. One of the big things is enhanced TLS 1.3 support. A summary of the changes is available in Changes.rst, and a full list of changes is available here.
Please note that LibreSSL is not a supported crypto backend. We accept patches and we do test on OpenBSD 6.0 which comes with LibreSSL, but if newer versions of LibreSSL break API compatibility we do not take responsibility to fix that.
Also note that Windows installers have been built with NSIS version that has been patched against several NSIS installer code execution and privilege escalation problems. Based on our testing, though, older Windows versions such as Windows 7 might not benefit from these fixes. We thus strongly encourage you to always move NSIS installers to a non-user-writeable location before running them. We are moving to MSI installers in OpenVPN 2.5, but OpenVPN 2.4.x will remain NSIS-only.
Compared to OpenVPN 2.3 this is a major update with a large number of new features, improvements and fixes. Some of the major features are AEAD (GCM) cipher and Elliptic Curve DH key exchange support, improved IPv4/IPv6 dual stack support and more seamless connection migration when client’s IP address changes (Peer-ID). Also, the new —tls-crypt feature can be used to increase users’ connection privacy.
OpenVPN GUI bundled with the Windows installer has a large number of new features compared to the one bundled with OpenVPN 2.3. One of major features is the ability to run OpenVPN GUI without administrator privileges. For full details, see the changelog. The new OpenVPN GUI features are documented here.
Please note that OpenVPN 2.4 installers will not work on Windows XP. The last OpenVPN version that supports Windows XP is 2.3.18, which is downloadable as 32-bit and 64-bit versions.
If you find a bug in this release, please file a bug report to our Trac bug tracker. In uncertain cases please contact our developers first, either using the openvpn-devel mailinglist or the developer IRC channel (#openvpn-devel at irc.libera.chat). For generic help take a look at our official documentation, wiki, forums, openvpn-users mailing list and user IRC channel (#openvpn at irc.libera.chat).
Important: you will need to use the correct installer for your operating system. The Windows 10 installer will not work on Windows 7/8/8.1/Server 2012r2. This is because Microsoft’s driver signing requirements and tap-windows6. For the same reason you need to use an older installer with Windows Server 2016. This older installer has a local privilege escalation vulnerability issue which we cannot resolve for Windows Server 2016 until tap-windows6 passes the HLK test suite on that platform. In the meanwhile we recommend Windows Server 2016 users to avoid installing OpenVPN/tap-windows6 driver on hosts where all users can’t be trusted. Users of Windows 7-10 and Server 2012r2 are recommended to update to latest installers as soon as possible.
Source Tarball (gzip) |
GnuPG Signature | openvpn-2.4.7.tar.gz |
Source Tarball (xz) |
GnuPG Signature | openvpn-2.4.7.tar.xz |
Source Zip |
GnuPG Signature | openvpn-2.4.7.zip |
Windows 7/8/8.1/Server 2012r2 installer (NSIS) |
GnuPG Signature | openvpn-install-2.4.7-I607-Win7.exe |
Windows 10 installer (NSIS) |
GnuPG Signature | openvpn-install-2.4.7-I607-Win10.exe |
Windows Server 2016 installer (NSIS) |
GnuPG Signature | openvpn-install-2.4.7-I603.exe |
NOTE: the GPG key used to sign the release files has been changed since OpenVPN 2.4.0. Instructions for verifying the signatures, as well as the new GPG public key are available here.
We also provide static URLs pointing to latest releases to ease automation. For a list of files look here.
This release is also available in our own software repositories for Debian and Ubuntu, Supported architectures are i386 and amd64. For details. look here.
You can use EasyRSA 2 or EasyRSA 3 for generating your own certificate authority. The former is bundled with Windows installers. The latter is a more modern alternative for UNIX-like operating systems.
The Windows installers are bundled with OpenVPN-GUI — its source code is available on its project page and as tarballs on our alternative download server.
This is primarily a maintenance release with minor bugfixes and improvements, and one security relevant fix for the Windows Interactive Service. Windows installer includes updated OpenVPN GUI and OpenSSL. Installer I601 included tap-windows6 driver 9.22.1 which had one security fix and dropped Windows Vista support. However, in installer I602 we had to revert back to tap-windows 9.21.2 due to driver getting reject on freshly installed Windows 10 rev 1607 and later when Secure Boot was enabled. The failure was due to the new, more strict driver signing requirements. The 9.22.1 version of the driver is in the process of getting approved and signed by Microsoft and will be bundled in an upcoming Windows installer.
Please note that LibreSSL is not a supported crypto backend. We accept patches and we do test on OpenBSD 6.0 which comes with LibreSSL, but if newer versions of LibreSSL break API compatibility we do not take responsibility to fix that.
Also note that Windows installers have been built with NSIS version that has been patched against several NSIS installer code execution and privilege escalation problems. Based on our testing, though, older Windows versions such as Windows 7 might not benefit from these fixes. We thus strongly encourage you to always move NSIS installers to a non-user-writeable location before running them. Our long-term plan is to migrate to using MSI installers instead.
Compared to OpenVPN 2.3 this is a major update with a large number of new features, improvements and fixes. Some of the major features are AEAD (GCM) cipher and Elliptic Curve DH key exchange support, improved IPv4/IPv6 dual stack support and more seamless connection migration when client’s IP address changes (Peer-ID). Also, the new —tls-crypt feature can be used to increase users’ connection privacy.
A summary of the changes is available in Changes.rst, and a full list of changes is available here.
OpenVPN GUI bundled with the Windows installer has a large number of new features compared to the one bundled with OpenVPN 2.3. One of major features is the ability to run OpenVPN GUI without administrator privileges. For full details, see the changelog. The new OpenVPN GUI features are documented here.
Please note that OpenVPN 2.4 installers will not work on Windows XP.
If you find a bug in this release, please file a bug report to our Trac bug tracker. In uncertain cases please contact our developers first, either using the openvpn-devel mailinglist or the developha er IRC channel (#openvpn-devel at irc.libera.chat). For generic help take a look at our official documentation, wiki, forums, openvpn-users mailing list and user IRC channel (#openvpn at irc.libera.chat).
Source Tarball (gzip) |
GnuPG Signature | openvpn-2.4.6.tar.gz |
Source Tarball (xz) |
GnuPG Signature | openvpn-2.4.6.tar.xz |
Source Zip |
GnuPG Signature | openvpn-2.4.6.zip |
Windows installer (NSIS) |
GnuPG Signature | openvpn-install-2.4.6-I602.exe |
NOTE: the GPG key used to sign the release files has been changed since OpenVPN 2.4.0. Instructions for verifying the signatures, as well as the new GPG public key are available here.
We also provide static URLs pointing to latest releases to ease automation. For a list of files look here.
This release is also available in our own software repositories for Debian and Ubuntu, Supported architectures are i386 and amd64. For details. look here.
You can use EasyRSA 2 or EasyRSA 3 for generating your own certificate authority. The former is bundled with Windows installers. The latter is a more modern alternative for UNIX-like operating systems.
The Windows installers are bundled with OpenVPN-GUI — its source code is available on its project page and as tarballs on our alternative download server.
You can download Windows developments snapshots (MSI installers) from here (Index of /downloads/snapshots/github-actions/openvpn2/ ). Those are automatically built from commits to OpenVPN master branch and include functionality which will be available in the next release. Development snapshots are less stable than releases, so use at your own risk.
TAP-Windows driver (NDIS 6)
This is an NDIS 6.20/6.30 implementation of the TAP-Windows driver, used by
OpenVPN and other apps. NDIS 6.20 drivers can run on Windows 7 or higher except
on ARM64 desktop systems where, since the platform relies on next-gen power
management in its drivers, NDIS 6.30 is required.
Build
The prerequisites for building are:
- Python 2.7
-
- Microsoft Windows 10 EWDK (Enterprise Windows Driver Kit)
-
- Visual Studio+Windows Driver Kit works too. Make sure to work from a «Command Prompt for Visual Studio» and to call buildtap.py with «—sdk=wdk».
-
- The devcon source code directory (setup/devcon) from Windows-driver-samples (optional)
-
- If you use the repo from upstream remember to include our patch to devcon.vcxproj to ensure that devcon.exe is statically linked.
- Windows code signing certificate
- Git (not strictly required, but useful for running commands using bundled bash shell)
- MakeNSIS (optional)
- Prebuilt tapinstall.exe binaries (optional)
- Visual Studio 2019 and WiX Toolset for MSM packaging (optional)
Make sure you add Python’s install directory (usually c:python27) to the PATH
environment variable.
Tap-windows6 has been successfully build on Windows 10 and Windows Server 2016 using
CMD.exe, Powershell and Git Bash.
View build script options:
$ python buildtap.py
Usage: buildtap.py [options]
Options:
-h, --help show this help message and exit
-s SRC, --src=SRC TAP-Windows top-level directory, default=<CWD>
--ti=TAPINSTALL tapinstall (i.e. devcon) directory (optional)
-d, --debug enable debug build
--hlk build for HLK tests (test sign, no debug)
-c, --clean do an nmake clean before build
-b, --build build TAP-Windows and possibly tapinstall (add -c to
clean before build)
--sdk=SDK SDK to use for building: ewdk or wdk, default=ewdk
--sign sign the driver files
-p, --package generate an NSIS installer from the compiled files
-m, --package-msm generate a MSM installer from the compiled files
--cert=CERT Common name of code signing certificate,
default=openvpn
--certfile=CERTFILE Path to the code signing certificate
--certpw=CERTPW Password for the code signing certificate/key
(optional)
--crosscert=CERT The cross-certificate file to use, default=MSCV-
VSClass3.cer
--timestamp=URL Timestamp URL to use, default=http://timestamp.verisign
.com/scripts/timstamp.dll
--versionoverride=FILE
Path to the version override file
Edit version.m4 and paths.py as necessary then build:
$ python buildtap.py -b
On successful completion, all build products will be placed in the «dist»
directory as well as tap6.tar.gz. The NSIS installer package will be placed to
the build root directory.
Building tapinstall (optional)
The easiest way to build tapinstall is to clone the Microsoft driver samples
and copy the source for devcon.exe into the tap-windows6 tree. Using PowerShell:
$ git clone https://github.com/OpenVPN/Windows-driver-samples.git $ Copy-Item -Recurse Windows-driver-samples/setup/devcon tap-windows6 $ cd tap-windows6 $ python.exe buildtap.py -b --ti=devcon
The build system also supports reuse of pre-built tapinstall.exe executables.
To make sure the buildsystem finds the executables, create the following
directory structure under tap-windows6 directory:
devcon
├── Release
│ └── devcon.exe
├── x64
│ └── Release
│ └── devcon.exe
└── ARM64
└── Release
└── devcon.exe
This structure is equal to what building tapinstall would create. Then call
buildtap.py with «—ti=devcon». Replace «Release» with your build configuration;
for example, when using —Hlk you’d use «Hlk».
Please note that the NSIS packaging (-p) step will fail if you don’t have
tapinstall.exe available. Also don’t use the «-c» flag or the above directories
will get wiped before MakeNSIS is able to find them.
Developer Mode: Installing, Removing and Replacing the Driver
The driver can be installed using a command-line tool, tapinstall.exe, which is
bundled with OpenVPN and tap-windows installers. Note that in some versions of
OpenVPN tapinstall.exe is called devcon.exe. To install, update or remove the
tap-windows NDIS 6 driver follow these steps:
- place tapinstall.exe/devcon.exe to your PATH
- open an Administrator shell
- cd to dist
- cd to amd64, i386, or arm64 depending on your system’s processor architecture.
If you are actively developing the driver (e.g.: Edit, Compile, Debug, Loop…), you may not be signing your driver each time, thus you need to be aware of the following additional items.
Disable Secure Boot:
Unsigned drivers require disabling secure boot.
- Secure Boot: Varies depending on PC Maker and/or the BIOS setting on your test machine.
- https://docs.microsoft.com/en-us/windows-hardware/manufacture/desktop/disabling-secure-boot
- VMWare (one example): https://docs.vmware.com/en/VMware-vSphere/7.0/com.vmware.vsphere.vm_admin.doc/GUID-898217D4-689D-4EB5-866C-888353FE241C.html
- Virtual Box: SecureBoot is not supported on Virtual Box
- Parallels (MacOS) https://kb.parallels.com/en/124242 [With Parallels 15, it is enabled by default, use 0 to disable]
Enable Windows Test Mode:
Test mode is also required.
- Enable Windows Test Mode via BCEDIT
- For details: https://docs.microsoft.com/en-us/windows-hardware/manufacture/desktop/bcdedit-command-line-options
- Specifically,
bcdedit /set testsigning offorbcdedit /set testsigning on - The result should be
Test Modein the bottom right corner of the windows screen.
Driver Installation:
Notes
- The command
tapinstall install OemVista.inf TAP0901installs the driver - Because your driver is not signed, the
tapinstall installstep will pop up the «Big Scary Unsigned Driver Warning», you’ll need to click OK. - As a result, the driver will be copied into the Windows Driver Store
Updating the Driver, and the Windows Driver Store:
At some point, you will build a shinny new driver and need to test it.
- The command
tapinstall remove TAP0901— removes the driver - However, the previously approved driver is still in the Windows Driver Store
- Typing
tapinstall install ...now, only re-installs the old driver that was copied into the driver store.
Key step: The driver needs to be removed from the driver store also.
- Details: https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2008-R2-and-2008/cc730875(v=ws.11)
There is a script to do this, but it only works if you have not changed the text strings in your driver package
- Script Location: https://github.com/mattock/tap-windows-scripts
The manual steps are:
- Step 1 — Obtain a list of Installed drivers via the command:
pnputil -e, this will list all of theoemNUMBER.inffiles that are in the driver store. - Step 2 — Find your driver in that list, it will be some
oem<NUMBER>.inffile - Step 3 — To delete, use
pnputil.exe /d oemNUMBER.inf
Finally use tapinstall install OemVista.inf TAP0901 to install your driver
Important:
If you do not see the Big Scary Unsigned Driver Warning — Windows will use the old (not new) driver.
Troubleshooting:
Examining the SetupAPI log file helps, see C:WindowsINFsetupapi.dev.log.
Build for HLK tests
A test-signed version of tap-windows6 driver should be used for the HLK tests.
The recommended procedure is to use pre-built, cross-signed devcon.exe and use
the WDK-generated key for signing the driver.
First setup the directory with prebuilt devcon as described above.
Then run the build with the —hlk option:
$ python.exe buildtap.py -c -b --ti=devcon-prebuilt --hlk
Release process and signing
Microsoft’s driver signing requirements have tightened considerably over the
last several years. Because of this this buildsystem no longer attempts to sign
files by default. If you want to sign the files at build time use the —sign
option. The «sign» directory contains several Powershell scripts that help
produce release-signed tap-windows6 packages:
- Cross-Sign: cross-sign tap-windows6 driver files and tapinstall.exe
- Create-DriverSubmission: create architecture-specific attestation signing submission cabinet files
- Extract-DriverSubmission: extract attestation-signed zip files
- Sign-File: sign files (e.g. tap-windows6 installer or driver submission cabinet files)
- Sign-tap6.conf.ps1: configuration file for all the scripts above
- Prepare-Msm.ps1: take Win7- and Win10-signed «dist» directories and produce a «dist» directory that MSM packaging can consume
Most of these scripts operate directly on the «dist» directory that
tap-windows6 build system produces. Below it is assumed that building and
signing is done on the same computer.
First produce cross-signed drivers for (Windows 7/8/8.1/Server 2012r2):
$ python.exe buildtap.py -c -b --ti=devcon $ signCross-Sign.ps1 -SourceDir dist -Force
Note that the «-Force» option for Cross-Sign.ps1 is required except in the
unlikely case that you’re appending a signature.
Next produce a driver submission cabinet files for attestation signing:
$ signCreate-DriverSubmission.ps1 $ Get-ChildItem -Path disk1|signSign-File.ps1
Three architecture-specific (i386, amd64, arm64) cabinet files are created.
Submit these to Windows Dev Center for attestation signing. Note that unsigned
cabinet files will be automatically rejected.
When submitting the drivers to Microsoft take care to only request signatures
applicable for each architecture.
At this point move the cross-signed «dist» directory away:
$ Move-Item dist dist.win7
Download the attestation-signed drivers as zip files put them into a temporary
directory (e.g. tap-windows6tempdir). Then run Extract-DriverSubmission.ps1:
$ Get-ChildItem -Path tempdir -Filter "*.zip"|signExtract-DriverSubmission.ps1
This extracts the drivers into the «dist» directory. Move that directory to dist.win10:
$ Move-Item dist dist.win10
After this you can start creating the installers and/or MSM packages.
If you’re creating NSIS packages do:
$ Move-Item dist.win7 dist $ python.exe buildtap.py -p --ti=devcon $ Move-Item dist dist.win7
Followed by:
$ Move-Item dist.win10 dist $ python.exe buildtap.py -p --ti=devcon $ Move-Item dist dist.win10
Finally sign both installers:
$ Get-Item tap-windows*.exe|signSign-File.ps1
On the other hand if you’re creating MSM packages do:
$ signPrepare-Msm.ps1 $ python buildtap.py -m --sdk=wdk $ Get-Item tap-windows*.msm|signSign-File.ps1
For additional instructions and background information please refer to
this article on OpenVPN community wiki.
Overriding setting defined in version.m4
It is possible to override one or more of the settings in version.m4 file with
the —versionoverride <file> option. Any settings given in the override file
have precedence over those in version.m4.
This is useful when building several tap-windows6 drivers with different
component ids for example.
Notes on proxies
It is possible to build tap-windows6 without connectivity to the Internet but
any attempt to timestamp the driver will fail. For this reason configure your
outbound proxy server before starting the build. Note that the command prompt
also needs to be restarted to make use of new proxy settings.
MSM packaging
In order to build the MSM packages build and sign the driver first:
- Build the TAP driver with buildtap.py and «-b» flag.
- EV-sign the drivers
- WHQL/Attestation-sign the drivers
Place the signed drivers in a directory structure under tap-windows6
directory. Each platform directory should contain the EV-signed driver with a
«win10» subdirectory containing WHQL/Attestation signed driver for that
platform:
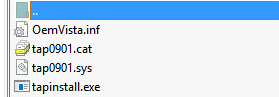
dist
├── amd64
│ ├── win10
│ │ ├── OemVista.inf
│ │ ├── tap0901.cat
│ │ └── tap0901.sys
│ ├── OemVista.inf
│ ├── tap0901.cat
│ └── tap0901.sys
├── arm64
│ ├── win10
│ │ ├── OemVista.inf
│ │ ├── tap0901.cat
│ │ └── tap0901.sys
│ └── (Note: EV-signed driver for arm64 is not used.)
├── include
│ └── tap-windows.h
└── i386
├── win10
│ ├── OemVista.inf
│ ├── tap0901.cat
│ └── tap0901.sys
├── OemVista.inf
├── tap0901.cat
└── tap0901.sys
Building MSM packages requires Visual Studio 2019 (EWDK is not sufficient) and
the WiX Toolset installed. In a Developer Command Prompt for Visual Studio
2019, run:
$ python buildtap.py -m --sdk=wdk
This will compile the installer.dll file with embedded drivers and package it
as a platform-dependent tap-windows-<version>-<platform>.msm files.
As the WiX Toolset does not support the arm64 platform yet, only amd64 and
i386 MSM files are built.
Optional: Consider EV-signing the MSM packages before deploying them. Thou,
MSM signature is ignored when merging MSM into MSI package, users get a choice
to validate the integrity of the downloaded MSM packages manually.
License
See the file COPYING.
-
Anonymizer OpenVPN Network Adapter
Производитель:
TAP-Windows Provider V9
Версия:
9.24.7.601
(12 апр 2022)
Файл *.inf:
oemvista.inf
Windows Vista x64, 7 x64, 8 x64, 8.1 x64, 10 x64
-
Anonymizer OpenVPN Network Adapter
Производитель:
TAP-Windows Provider V9
Версия:
9.24.2.601
(27 сен 2019)
Файл *.inf:
oemvista.inf
Windows Vista x86, 7 x86, 8 x86, 8.1 x86, 10 x86
В каталоге нет драйверов для Anonymizer OpenVPN Network Adapter под Windows.
Скачайте DriverHub для автоматического подбора драйвера.
Драйверы для Anonymizer OpenVPN Network Adapter собраны с официальных сайтов компаний-производителей и других проверенных источников.
Официальные пакеты драйверов помогут исправить ошибки и неполадки в работе Anonymizer OpenVPN Network Adapter (сетевые устройства).
Скачать последние версии драйверов на Anonymizer OpenVPN Network Adapter для компьютеров и ноутбуков на Windows.
OpenVPN users occasionally report tap driver installation issues like Windows 7 OpenVPN TAP driver unsigned.
This can have a great impact when it comes to using VPN software to prevent any third parties online from gathering and using your data.
BEST VPN RECOMMENDATIONS — VETTED BY OUR EXPERTS
There are multiple reasons behind an install failure such as broken driver, invalid or expired driver signature, and conflicting drivers, just to name a few.
No matter the reason behind your problem, we have a quick troubleshooting guide that will allow you to easily install the OpenVPN tap driver. Check out our solutions below.
Does OpenVPN work on Windows 7?
Yes, OpenVPN is compatible with older versions of Windows, including Windows 7.
The VPN client offers dedicated support for the operating system, and the configuration is pretty straightforward.
Moreover, the OpenVPN file and system impact are pretty small, so you should have no reason to worry about it affecting your PC’s performance, even if you use an older device.
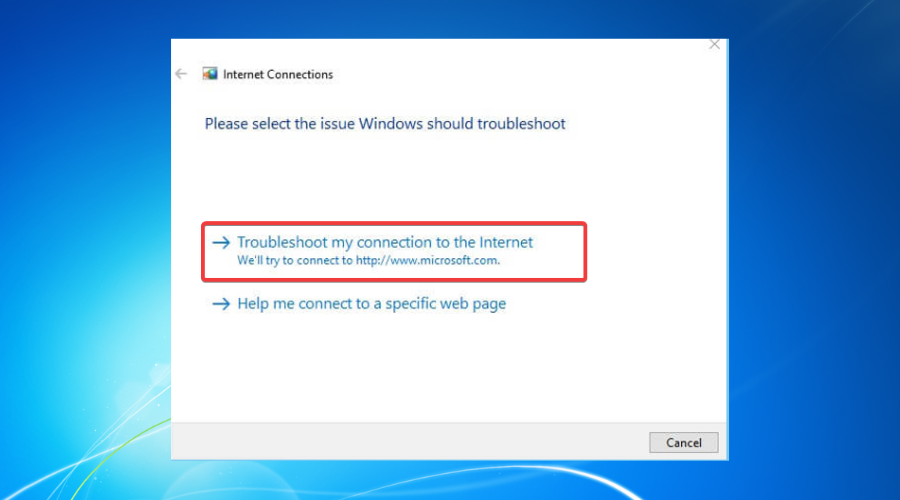
1. Use the Internet Connections Troubleshooter
- Press the Win key.
- Type troubleshoot.
- Select Available Recommended troubleshooting.
- Click the Available troubleshooters’ hyperlink.
- Select Internet Connections and click Run the troubleshooter.
- Select Troubleshoot my connection to the internet.
- Go through the troubleshooting wizard’s steps.
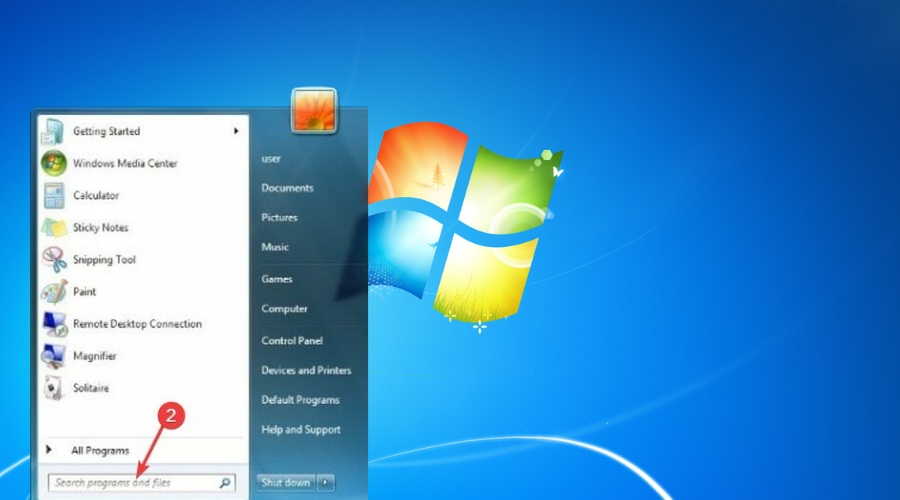
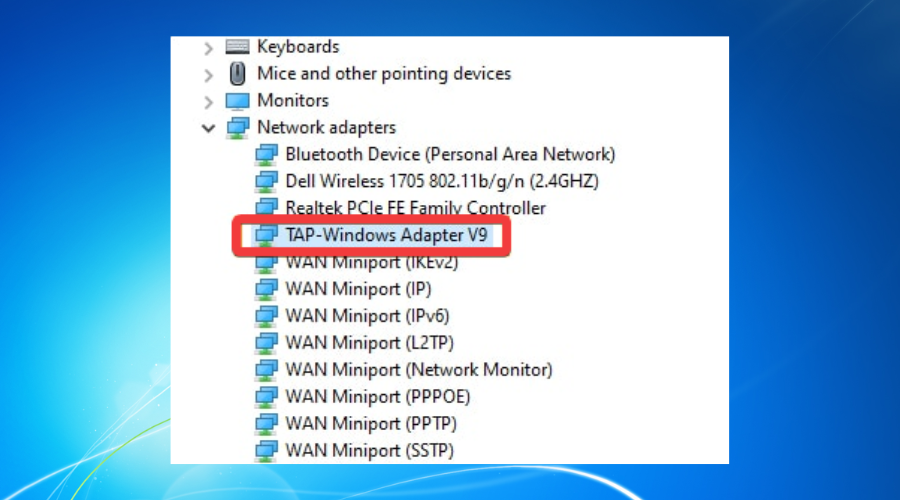
2. Reset the TAP-Windows Adapter Connection
- Press the Start button from your taskbar.
- Type network in the search box.
- Select Network status.
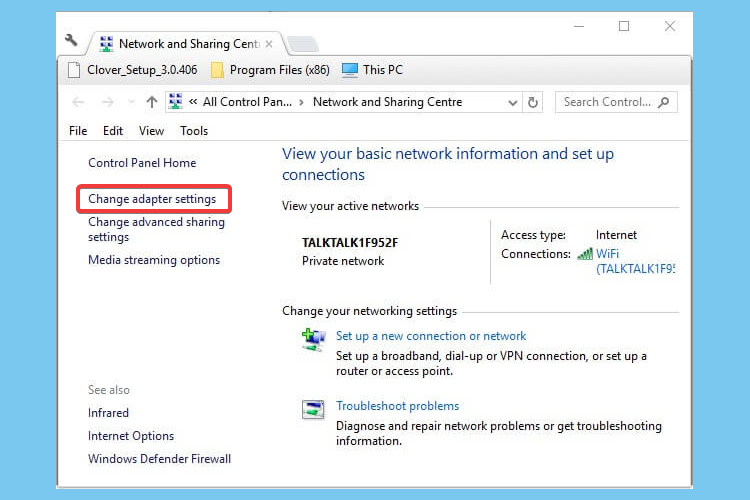
- Click on the Network and Sharing Center button.
- Select the Change adapter settings option.
- Right-click the TAP-Windows Adapter.
- Select Disable.
- Right-click the TAP-Windows Adapter again.
- Select Enable.
- Restart your PC and check if the issue still there.
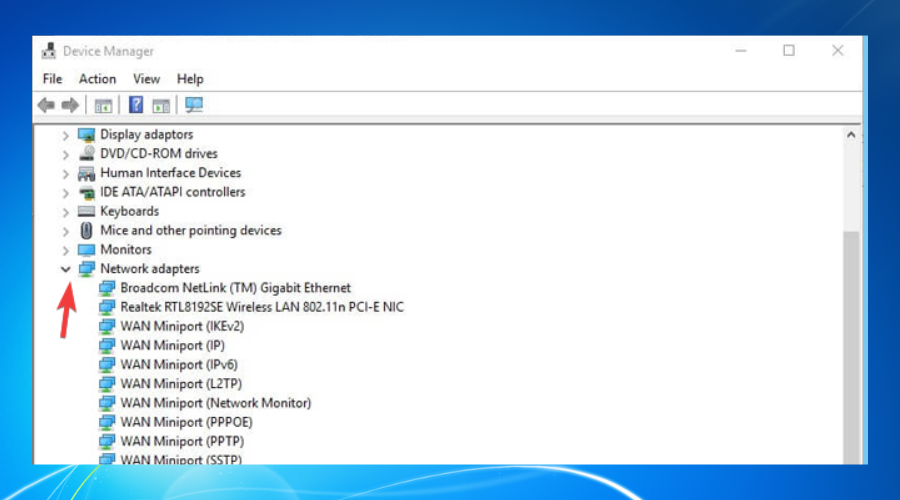
This trick can also help with the All TAP-Windows adapters are currently in use error that many Windows users encounter.
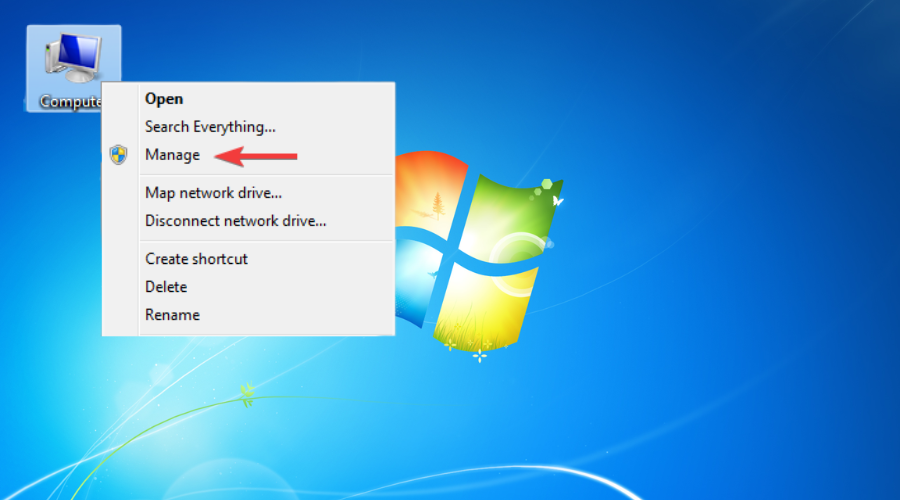
3. Reinstall TAP-Windows Adapter and VPN client
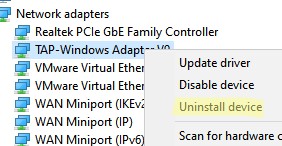
- Right-click on the Computer.
- Choose Manage.
- Expand the Network adapters category.
- Right-click the TAP-Windows Adapter V9.
- Click on Uninstall device.
- Select Uninstall to confirm.
- Press the Windows key + R key combination.
- Type appwiz.cpl and press Enter.
- Select your OpenVPN software.
- Click on the Uninstall button to remove it.
- Restart your PC shortly after uninstalling both services.
- Reinstall your OpenVPN software + TAP adapter driver.
4. Download and install OpenVPN TAP drivers for Windows 7
Windows 7 users report they fixed this issue with the KB4474419 security update that automatically updates your Tap drivers.
- Download the KB4474419 Windows 7 security update.
- Follow the installation prompts and wait for the process to complete.
- Check your OpenVPN Tap drivers.
This update installs SHA-2 code sign support and remediates the Windows that cannot verify the digital signature tap driver error.
Another option is to download an older OpenVPN Tap driver version:
- Uninstall your TAP-Windows Adapter V9 driver from the Device Manager (as presented in the third solution).
- Download OpenVPN Windows 7 signed tap driver (version 2.1.1.)
- Open and run the installer wizard.
Now the signed driver error should be remediated, as users report having issues with the 2.1.2. version. This previous version should work just fine.
If you have any problems manually installing the OpenVPN Tap drivers or want to speed up the process, you can use a dedicated third-party tool such as DriverFix.
5. Change to a more reliable VPN
If you tried all the previous solutions and still get the windows 7 OpenVPN tap driver unsigned issue, you might consider a better VPN alternative.
Private Internet Access, for instance, is a great VPN service that comes with its own TAP driver.
Furthermore, even if it stops working at some point, you can easily reinstall it directly from the VPN client’s configuration screen.

Private Internet Access
Benefit from advanced VPN options and dedicated support for OpenVPN and other protocols!
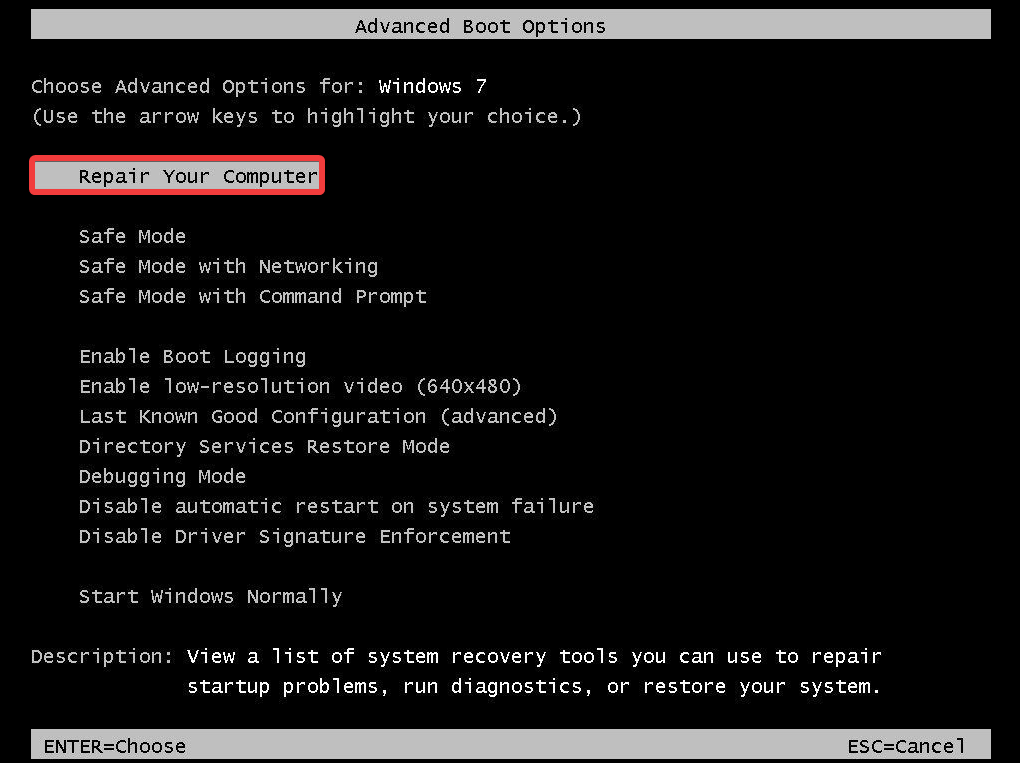
6. Reset Windows 7
- Start the computer.
- Press and hold the F8 key.
- In the Advanced Boot Options menu, choose Repair Your Computer.
- Press Enter.
- Select a keyboard language and click Next.
- If prompted, log in with an administrative account.
- At the System Recovery Options, choose System Restore or Startup Repair (if this is available).
To sum up, if you notice that your OpenVPN tap driver fails to install, there are some steps that you can try from our troubleshooting guide.
However, reinstalling the TAP driver and VPN client will usually fix your issue.
If you need additional help with this VPN service, we have a guide on what to do if OpenVPN is not forwarding traffic.
In case you have an alternative solution we didn’t mention or any questions regarding the ones we listed, feel free to share it with us, in the comments section below
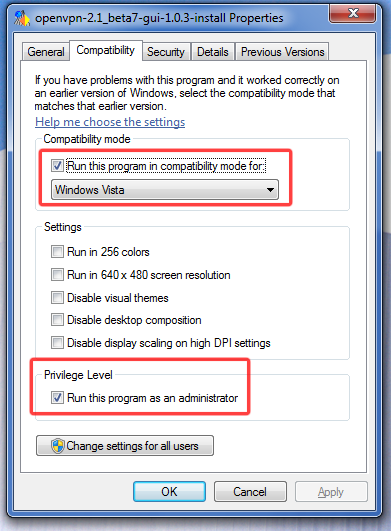
На днях понадобилось мне настроить клиентскую часть OpenVPN на компьютере с установленной Windows 7.
Я предвидел проблемы и потому сразу погуглил на эту тему. Нашел несколько советов, суть которых сводилась к тому, что отличий от установки на Vista мало, и главное из них — в свойствах инсталятора предварительно установить режим совместимости с Vista, а также запуск от имени администратора.
Сразу оговорюсь — в силу своей ленности использую вариант OpenVPN GUI, который мне очень полюбился по практике использования на Windows XP/2003.
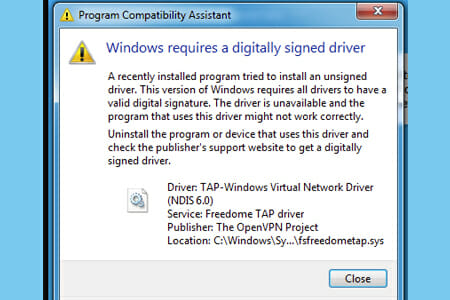
Сделал предлагаемые действия и начал установку. На первый взгляд всё нормально, но не работает :(. Полез разбираться — Windows 7 не может запустить драйвер виртуальной сетевой карты TAP/TUN v8 необходимый для работы OpenVPN
А вот про это Гугль уже молчал. Путем нехитрых логических построений пришел к решению накатать поверх установки OpenVPN GUI оригинальную версию OpenVPN. Потому как поглядев на содержимое инсталятора OpenVPN увидел что там идет более новая версия этого драйвера v9.
Собственно на этом и сказочке конец — после установки OpenVPN поверх OpenVPN GUI все завелось с пол-оборота и радует стабильной работой и по сей день.
Надеюсь этот краткий рассказ сохранит чьи-нибудь нервы 
Ссылки:
OpenVPN GUI: openvpn.se/files/install_packages/openvpn-2.1_beta7-gui-1.0.3-install.exe
OpenVPN: openvpn.net/release/openvpn-2.1_rc15-install.exe
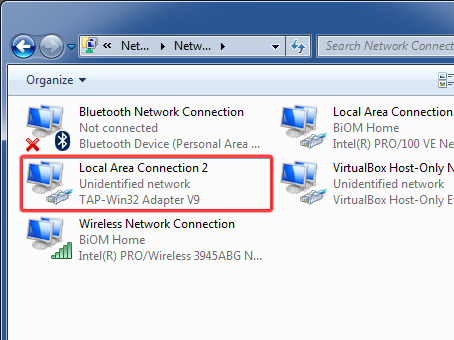
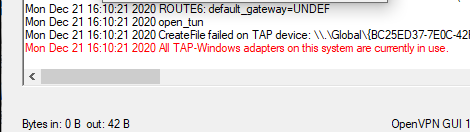
При запуске OpenVPN сервера или подключения из клиента OpenVPN вы можете столкнуться с ошибкой:
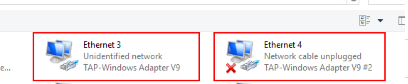
All TAP-Windows adapters on this system are currently in use Exiting due to fatal error
Или
All wintun adapters on this system are currently in use or disabled
Или
No TAP Adapter Available
Вы можете увидеть эту ошибку логе OpenVPN сервера (файл C:Program FilesOpenVPNlogopenvpn.log) или в клиенте OpenVPN GUI/
Это известная ошибка, связанная с тем что в Windows не установлены или некорректно работают виртуальные сетевые адаптеры TAP или wintun.
В OpenVPN 2.5+ вместо сетевых адаптеров TAP можно использовать WinTun от разработчиков WireGuard. По словам разработчиков, wintun драйвер работает быстрее чем классический OpenVPN драйвер TAP. Вы можете выбрать какой сетевой драйвер использовать при установке OpenVPN (TAP-Windows6 или Wintun).
Чтобы исправить эту ошибку нужно выполнить один из следующих шагов (расположены в порядке от самого простого к самому сложному):
- Перезапустить TAP-Windows/WinTun через панель управления.
- Переустановить драйвер TAP-Windows/Wintun;
- Создать новый сетевой адаптер для OpenVPN (или другого VPN клиента)
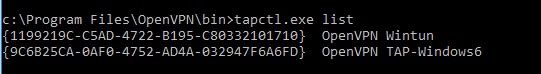
Выведите список всех TAP адаптеров, доступных клиенту OpenVPN:
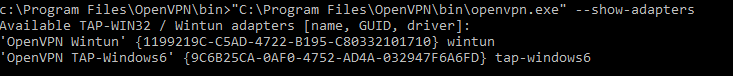
cd "c:Program FilesOpenVPNbin"
“C:Program FilesOpenVPNbinopenvpn.exe” --show-adapters
В нашем случае установлен как Wintun, так и TAP адаптер:
'OpenVPN Wintun' {1199219C-C5AD-4722-B195-C80332101710} wintun
'OpenVPN TAP-Windows6' {9C6B25CA-0AF0-4752-AD4A-032947F6A6FD} tap-windows6
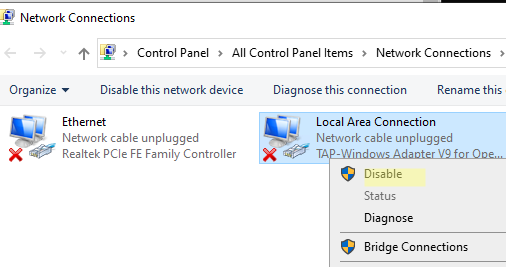
Для устранения ошибки обычно достаточно включить и отключить TAP адаптер в панели управления Windows, перезагрузить компьютер или переустановить клиент OpenVPN.
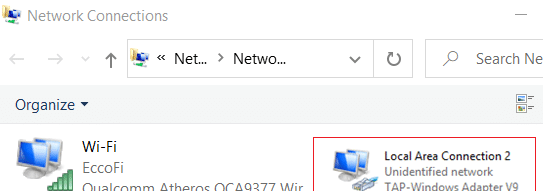
Вы можете включить и отключить сетевой адаптер WinTap из панели управления ncpa.cpl. Щелкните в панели управления по нужному адаптеру (TAP-Windows или Wintun Userspace Tunnel) и выберите Disable. Затем включите его (Enable.)
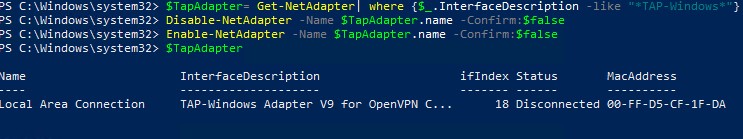
Также вы можете перезапустить все сетевые интерфейсе OpenVPN TAP с помощью PowerShell:
$TapAdapter= Get-NetAdapter| where {$_.InterfaceDescription -like "*TAP-Windows*"}
Disable-NetAdapter -Name $TapAdapter -Confirm:$false
Enable-NetAdapter -Name $TapAdapter -Confirm:$false
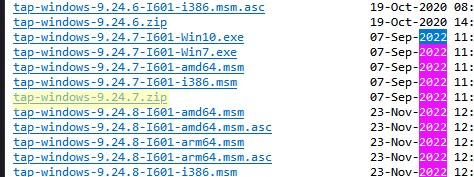
Если предыдущий способ не помог, попробуйте переустановить драйвера для вашего виртуального TAP адаптера вручную
- Скачайте последнюю версию TAP драйвера для Windows здесь (http://build.openvpn.net/downloads/releases/). Например, tap-windows-9.24.7.zip или wintun-amd64-0.8.1.
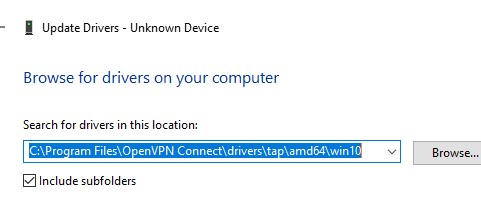
- Распакуйте архив, запустите Device Manager (
devmgmt.msc), щелкните правой кнопкой по сетевому адаптеру TAP-Windows Adapter v9 в секции Network Adapters и выберите Update driver; - Укажите путь к каталогу с драйвером TAP.
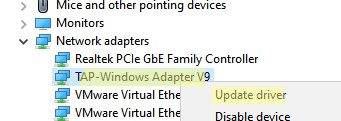
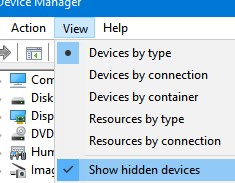
Если вы не видите в панели управления TAP-Windows Adapter V9, откройте консоль Device Manager и включите опцию View-> Show hidden device.
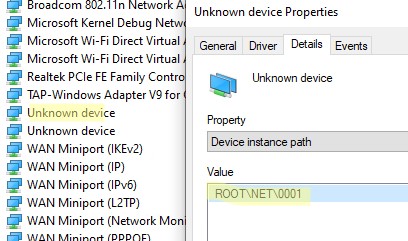
Если в секции Network adapters есть устройства типа unknown device, откройте его свойства, перейдите на вкладку Details и проверьте значение свойства Device instance path.
Если здесь указано ROOTNET000, значит попробуйте выполнить авматотический поиск дрвйвера или вручную укажите путь к INF файлу (например C:Program FilesOpenVPN Connectdriverstapamd64win10OemVista.inf). После этого в панели управления появится ваш TAP адаптер.
В Windows 7 драйвер TAP, подписанный с помощью SHA256, не будет работать корректно, пока вы вручную не установите обновление KB4474419.
В самых редких случаях может помочь полное пересоздание TAP/Wintun адаптера.
Перед установкой нужно удалить существующий сетевой адаптер TAP и его драйвер. Для этого запустите программу C:Program FilesTAP-WindowsUninstall.exe или просто удалите устройство из Device Manager (Uninstall device).
Для установки TAP драйвера используется утилита tapinstall.exe.
Распакуйте архив и запустите установочный файл с правами администратора.
В новых версиях OpenVPN для управления виртуальными сетевыми адаптерами используется утилита c:Program FilesOpenVPNbintapctl.exe.
Вывести список сетевых адаптеров OpenVPN:
tapctl.exe list
Удалить адаптер:
tapctl.exe delete "OpenVPN TAP-Windows6"
Создать новый адаптер TAP:
tapctl.exe create
Создать новый wintun адаптер:
tapctl.exe create --hwid wintun
Обязательно проверьте, что новый сетевой адаптер TAP-Windows Adapter появился в списке сетевых подключения в панели управления Windows (консоль ncpa.cpl).
Также ошибка “ All TAP-Windows adapters on the system are currently in use” может возникнуть, если вы пытаетесь установить несколько OpenVPN подключений с одного компьютера. Для каждого VPN подключения нужно создать свой адаптер.
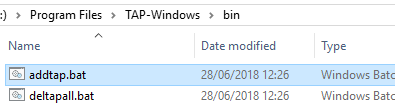
Вы можете создать дополнительный WinTap сетевой адаптер с помощью скрипта (bat файл) %ProgramFiles%TAP-Windowsbinaddtap.bat.
Или с помощью команды (в современных версиях клиента OpenVPN):
c:Program FilesOpenVPNbintapctl.exe.tapctl.exe create
В результате в панели управления появится два (или более) сетевых адаптеров TAP-Windows Adapter V9, и вы сможете одновременно установить несколько одновременных OpenVPN сессий с разными серверами.
Теперь вы можете использовать ваше OpenVPN подключение в Windows и настроить автоматическое подключение к VPN. [/alert]