I’ve OpenSSH 7.6 installed in Windows 7 for testing purposes. SSH client & server work just fine till I tried to access one of my AWS EC2 box from this windows.
It seems like I need to change the permission on the private key file. This can be easily done on unix/linux with chmod command.
What about windows?
private-key.ppm is copied directly from AWS and I guess the permission too.
C:>ssh -V
OpenSSH_7.6p1, LibreSSL 2.5.3
C:>ver
Microsoft Windows [Version 6.1.7601]
C:>
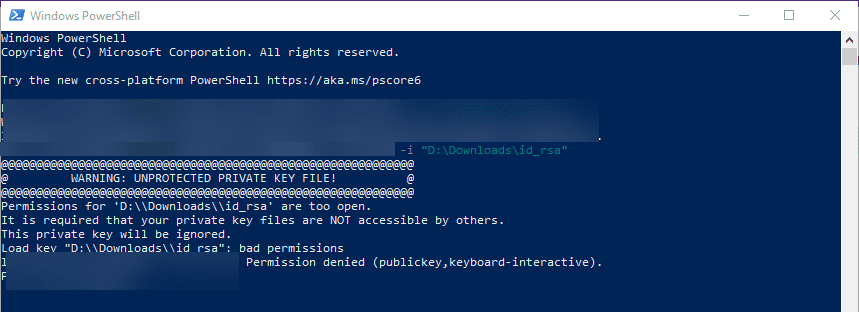
C:>ssh ubuntu@192.168.0.1 -i private-key.ppk
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@ WARNING: UNPROTECTED PRIVATE KEY FILE! @
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
Permissions for 'private-key.ppk' are too open.
It is required that your private key files are NOT accessible by others.
This private key will be ignored.
Load key "private-key.ppk": bad permissions
ubuntu@192.168.0.1: Permission denied (publickey).
C:>
C:>
C:>ssh ubuntu@192.168.0.1 -i private-key.ppm
Warning: Identity file private-key.ppm not accessible: No such file or directory.
ubuntu@192.168.0.1: Permission denied (publickey).
C:>
asked Feb 18, 2018 at 5:10
11
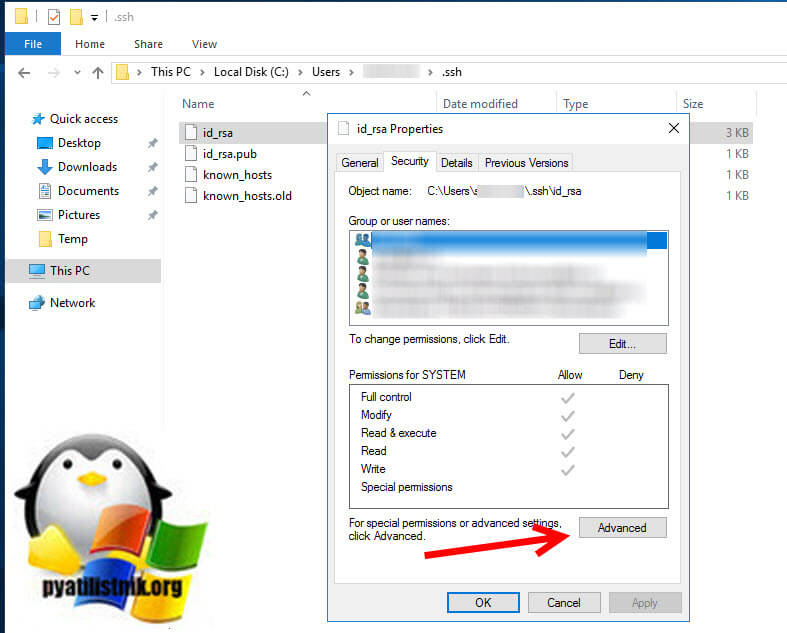
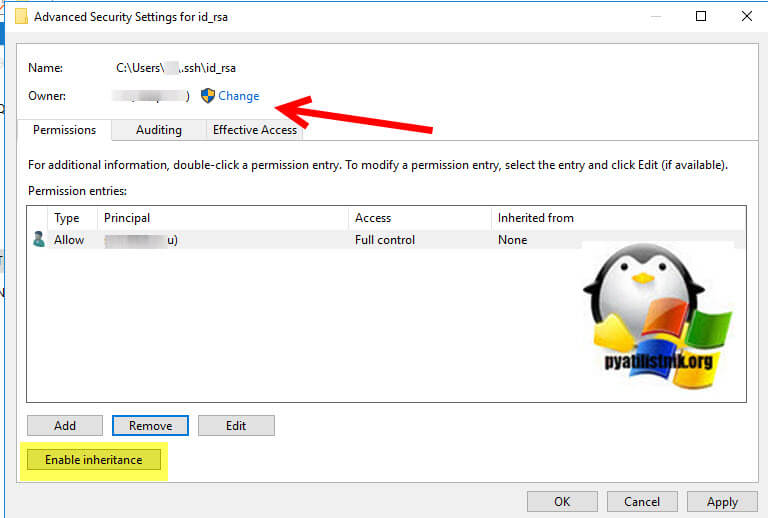
You locate the file in Windows Explorer, right-click on it then select «Properties». Navigate to the «Security» tab and click «Advanced».
Change the owner to you, disable inheritance and delete all permissions. Then grant yourself «Full control» and save the permissions. Now SSH won’t complain about file permission too open anymore.
It should end up looking like this:
MSC
5571 gold badge5 silver badges13 bronze badges
answered Feb 18, 2018 at 8:57
iBugiBug
9,6777 gold badges37 silver badges66 bronze badges
22
Keys must only be accessible to the user they’re intended for and no other account, service, or group.
- GUI:
[File] Properties → Security → Advanced- Owner: The key’s user
- Permission Entries: Remove all except for the key’s user
- Set key’s user to Full Control
Cmd:::# Set Key File Variable: Set Key="%UserProfile%.sshid_rsa" ::# Remove Inheritance: Icacls %Key% /c /t /Inheritance:d ::# Set Ownership to Owner: :: # Key's within %UserProfile%: Icacls %Key% /c /t /Grant %UserName%:F :: # Key's outside of %UserProfile%: TakeOwn /F %Key% Icacls %Key% /c /t /Grant:r %UserName%:F ::# Remove All Users, except for Owner: Icacls %Key% /c /t /Remove:g "Authenticated Users" BUILTINAdministrators BUILTIN Everyone System Users ::# Verify: Icacls %Key% ::# Remove Variable: set "Key="PowerShell:# Set Key File Variable: New-Variable -Name Key -Value "$env:UserProfile.sshid_rsa" # Remove Inheritance: Icacls $Key /c /t /Inheritance:d # Set Ownership to Owner: # Key's within $env:UserProfile: Icacls $Key /c /t /Grant ${env:UserName}:F # Key's outside of $env:UserProfile: TakeOwn /F $Key Icacls $Key /c /t /Grant:r ${env:UserName}:F # Remove All Users, except for Owner: Icacls $Key /c /t /Remove:g Administrator "Authenticated Users" BUILTINAdministrators BUILTIN Everyone System Users # Verify: Icacls $Key # Remove Variable: Remove-Variable -Name Key
answered Jun 8, 2018 at 15:34
24
In addition to the answer provided by ibug. Since i was using the ubuntu system inside windows to to run the ssh command. It still was not working. So i did
sudo ssh ...
and then it worked
answered Sep 8, 2018 at 13:27
Parv SharmaParv Sharma
7035 silver badges5 bronze badges
9
I had a similar issue but I was at work and don’t have the ability to change file permissions on my work computer. What you need to do is install WSL then copy the your key to the hidden ssh directory in WSL:
cp <path to your key> ~/.ssh/<name of your key>
Now you should be able to modify the permissions normally.
sudo chmod 600 ~/.ssh/<your key's name>
Then ssh using WSL:
ssh -i ~/.ssh/<name of your key> <username>@<ip address>
Giacomo1968
51.6k18 gold badges161 silver badges205 bronze badges
answered Sep 6, 2019 at 18:17
JKauffmanJKauffman
5614 silver badges2 bronze badges
5
You just need to do at least four things:
- Disable inheritance
- Convert inherited permissions to explicit permissions
- Remove Users group
- You will end up with no Users can access private files, this should be enough to add id_rsa.
Matthew Lock
4,6312 gold badges34 silver badges42 bronze badges
answered Feb 16, 2019 at 21:58
4
use below command on your key it works on windows
icacls .private.key /inheritance:r
icacls .private.key /grant:r "%username%":"(R)"
answered Oct 4, 2019 at 13:28
4
This seems to be related to the version of OpenSSH you’re running:
where sshreturns:%WinDir%System32OpenSSHssh.exe %ProgramFiles%Gitusrbinssh.exessh -Vreturns:# %WinDir%System32OpenSSHssh.exe OpenSSH_7.5p1, without OpenSSL # %ProgramFiles%Gitusrbinssh.exe OpenSSH_7.3p1, OpenSSL 1.0.2k 26 Jan 2017
When running ..Gitusrbinssh.exe, it works fine and doesn’t complain about the permissions, but running ..OpenSSHssh.exe comes back with the following, even though key ACLs are Full Access for myself and nothing else:
load key "t:mykeysrich-private.ppk": invalid format
banana@127.0.0.127: Permission denied (publickey).
answered Apr 5, 2018 at 11:53
Rich SRich S
3332 silver badges7 bronze badges
6
You can use icacls in Windows instead of chmod to adjust file permission. To give the current user read permission and remove everything else:
Icacls <file name> /Inheritance:r
Icacls <file name> /Grant:r "%Username%":"(R)"
answered Aug 12, 2019 at 12:39
manjuvmanjuv
1371 silver badge4 bronze badges
4
Here’s the way to do it using Microsoft’s tooling, avoiding the problem from the get-go. But it should also fix the issue, meaning you can follow these instructions with existing keys.
Start PowerShell/Terminal as Administrator and run the following:
Install-Module -Force OpenSSHUtils -Scope AllUsers
# Make sure the service isn't disabled
Get-Service -Name ssh-agent | Set-Service -StartupType Manual
# We need this service as ssh-add depends on it
Start-Service ssh-agent
cat ~.sshexample-key.ecdsa | ssh-add -k -
answered Oct 30, 2020 at 14:31
Louis WaweruLouis Waweru
23.5k37 gold badges129 silver badges196 bronze badges
3
A single line in CMD might do the trick; as described here, adding the key from stdin instead of changing the permissions:
cat /path/to/permission_file | ssh-add -k
To check key has been added:
ssh-add -l
answered Nov 28, 2019 at 14:45
majommajom
1212 bronze badges
This is just a scripted version of @JW0914’s CLI answer, so upvote him first and foremost:
# DO the following in powerhsell if not already done:
# Set-ExecutionPolicy RemoteSigned
# NOTE: edit the path in this command if needed
$sshFiles=Get-ChildItem -Path "$env:userprofile.ssh" -Force
$sshFiles | % {
$key = $_
& icacls $key /c /t /inheritance:d
& icacls $key /c /t /grant "${echo $env:username}":F
& icacls $key /c /t /remove Administrator "Authenticated Users" BUILTINAdministrators BUILTIN Everyone System Users
}
# Verify:
$sshFiles | % {
icacls $_
}
answered Oct 3, 2019 at 21:07
bbarkerbbarker
3163 silver badges9 bronze badges
- Copy the public and private keys to
%userprofile%.ssh - Use the batch script below after finding your keys from the cmd prompt with
where *.pub:Md %Userprofile%.ssh Copy PublicKey %Userprofile%.ssh Copy PrivateKey %Userprofile%.ssh Cd %Userprofile%.ssh Icacls .PublicKey /Inheritance:r Icacls .PrivateKey /Inheritance:r Icacls .PublicKey /Grant:r "%Username%":"(F)" Icacls .PrivateKey /Grant:r "%Username%":"(F)" - Right-click each file → Properties → Security:
Remove everyone except the user, setting the permissions for the user to Read
answered Apr 17, 2020 at 19:34
2
I couldn’t get any of these answers working for me due to permission issues, so I’ll share my solution:
- Go to
%UserProfile%.ssh - Copy and paste
id_rsa, rename it to something else [example] - Open the renamed file [
example] and replace the key with your own private key cdto that directory- Enter your passphrase after issuing:
ssh -i example example@127.0.0.1
answered Feb 24, 2020 at 23:03
7
- Download and unzip
OpenSSH-Win64.zip(or Win32, depending on your system) - Execute
FixUserFilePermissions.ps1in PowerShell with administrator privilege
answered Mar 14, 2020 at 15:15
1
Answer by iBug works fine! You can follow that and get rid of this issue.
But there are few things which are needed to be cleared as I faced issues during setting up permissions and it took few minutes for me to figure out the problem!
Following iBug’s answer, you’ll remove all the permissions but how do you set Full Control permission to yourself? that’s where I got stuck at first as I didn’t knew how to do that.
After Disabling Inheritance, you’ll be able to delete all allowed users or groups.
Once Done with that,
Click on Add then click on Set a Principal then enter System and Administrators and your email addredd in the field at bottom then click on check names.
It’ll load the name if user exists.
Then, Click on OK > Type Allow > Basic Permisisons Full Control > Okay
This will setup Full Control permission to SYSTEM, Administrators and Your User.
After that try to ssh using that key. It should be solved now.
I had same issue and I solved that using this method.
If there’s any user or group with that name then it’ll load that.
-Screenshots-
Permission Entries
Select a Principal/ Select User or Groups
answered Feb 8, 2019 at 14:20
2
I’m a Window user, using the Windows’s bash and followed all the steps to set permission using Windows GUI, and it still doesn’t work and it complains:
Permissions 0555 for 'my_ssh.pem' are too open.
It is required that your private key files are NOT accessible by others.
The I added sudo at the front of the ssh command and it just works. Hope this is helpful to others.
answered Nov 26, 2019 at 6:10
3
I had the same problem on Windows 10, and it arouse when I created a second user account on my machine.
Since that new user was also an administrator and It had access to my user folder, I did these steps to limit the access on my .ssh folder and it worked!
- Navigate to your user folder at
C:UsersYOU - Right click on
.ssh/folder to open context menu - Under
Give access to...sub-menu, selectRemove access - Done!
Now try to log back in to your remote computer using ssh!
Hope it helps someone!
answered May 15, 2020 at 23:15
3
Lately, I have been working a lot with SSH and Windows 10, for one transitioning away from WMI for certain things, hopefully, a blog post coming on that front soon. Setting up SSH on Windows 10 is fairly simple to do, but it is one of those processes that can be wrought with missteps and misinformation from various places. As a case in point, you may receive permissions issues on a private key connecting to Windows 10. Why is this? Let’s take a look at bad owner or permissions on SSH config Windows 10 and see what this relates to.
Public key authentication with Windows 10
First of all, if you see this error mentioned in the title of the blog post, it means you are most likely attempting to configure public key authentication to access your OpenSSH installed and configured in Windows 10. Why do you want to configure public key authentication?
First of all, if you want to know how to configure Windows 10 SSH, take a look at my blog post here:
- OpenSSH Server Windows 10 Install with Public Key authentication
Also, learn about OpenSSH in general here:

- OpenSSH
Public key authentication is noted as a more secure way to authenticate to an OpenSSH server. Why is this? With public-key authentication, you have two parts of a cryptographic key that grants access. It includes both a private key and a public key. The SSH server possesses the public key of the key pair, while you as the user possess the private key. In addition to passing the physical private key file, you can also secure the private key with a password.
So, it is easy to understand how this type of authentication is much more secure. As far as the cryptographic key is concerned, an attacker can’t simply brute force the server to guess a weak, guessable, or cracked password to gain access. They have to have possession of the key and know the password if the private key is secured with one.
SSH clients have also come a long way in recognizing when there may be bad ideas in play when it comes to private key files. If the permissions contain other security permissions on the private key file other than the user that should possess those permissions, the key can be more easily compromised.
Many SSH clients check for the permissions configured on the SSH private key and if these are too permissive, it will not be allowed for use to make the SSH connection. Note the following error seen when trying to SSH into a remote Windows 10 machine with wide-open permissions on the private key file:
The error above states the issue: Permissions for the key file are too open. It is required that your private key files are NOT accessible by others. This private key will be ignored.
To get past the Bad Owner or Permissions on SSH Config Windows 10 error, you need to configure three things:
- Permissions on the authorized_keys file
- Permissions on your private key file
- sshd_config file changes
Part of the process to properly configure your Windows 10 SSH session for public-key authentication is ensuring the permissions are set correctly, both on the authorized_keys file (holds public key) and the private key file that holds the private key side of your key pair. Let’s take a look at both.
When you enable OpenSSH on your Windows 10 machine, you need to create the .ssh directory in the user profile of the user you will be logging in with. This is the location OpenSSH looks to find the authorized public keys, and by extension, the paired private keys that are allowed to access the machine.
By default, when you create the directory and the authorized_keys file, it will have too many permissions assigned. As you can see, it will have the local Administrators group added to the file. Click Advanced.
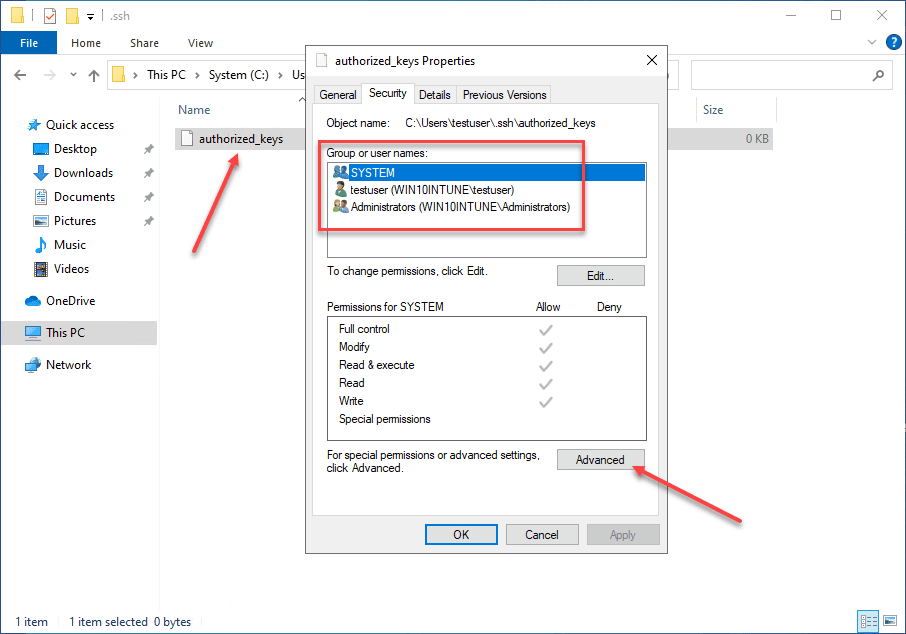
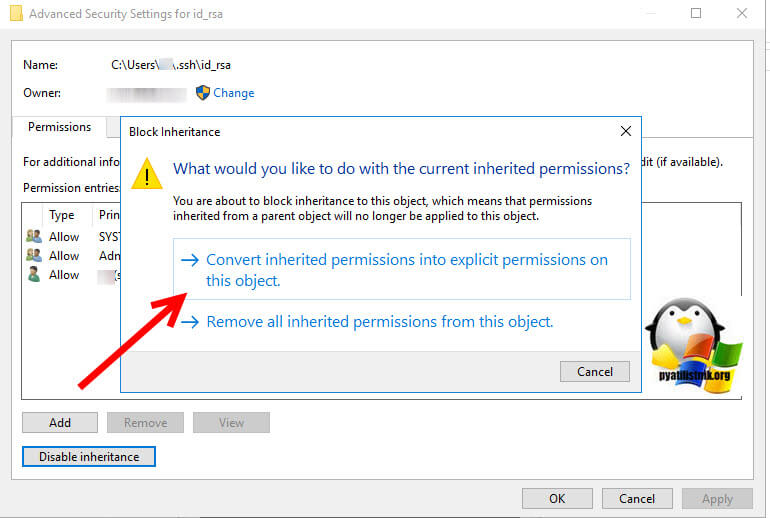
Here, we need to disable inheritance. This breaks inheritance on the folder and allows you to set explicit permissions.
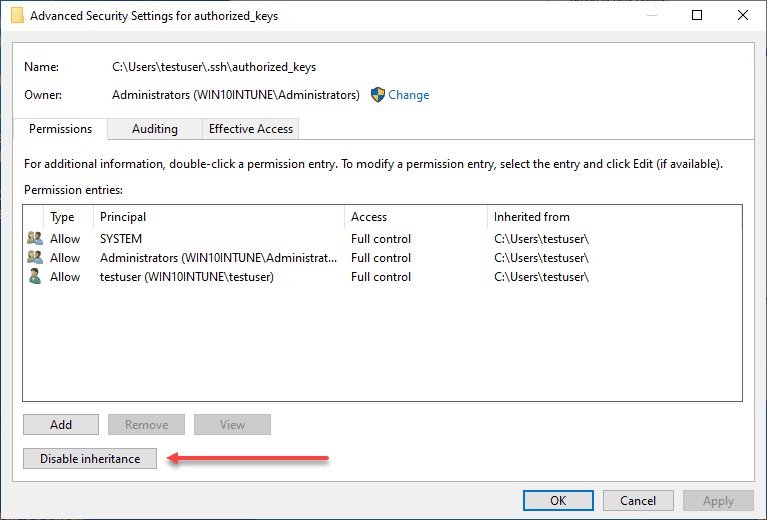
Choose the option Convert inherited permissions into explicit permissions on this object.
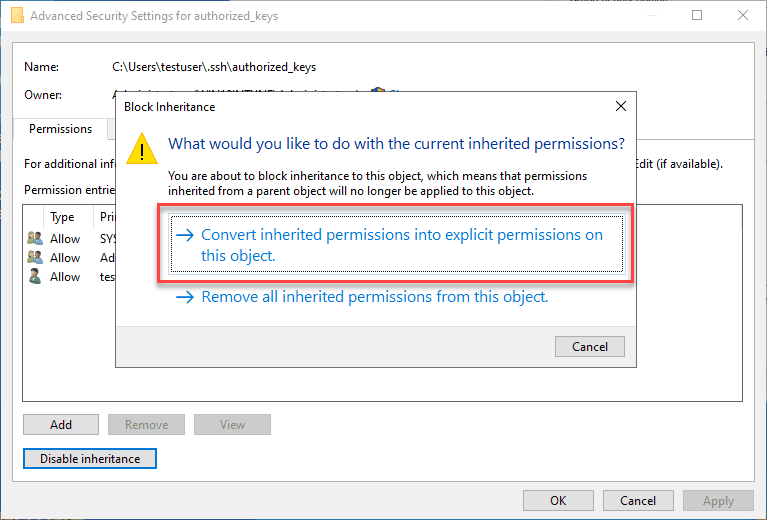
Adjust your permissions so that you only have SYSTEM and your username displayed as having permissions on the authorized_keys file.
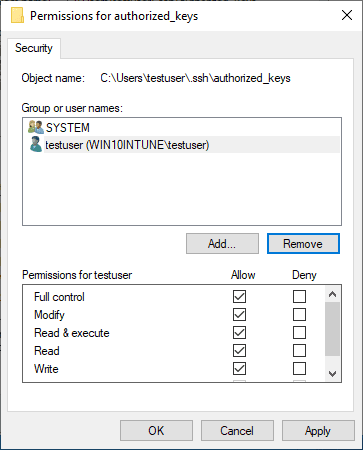
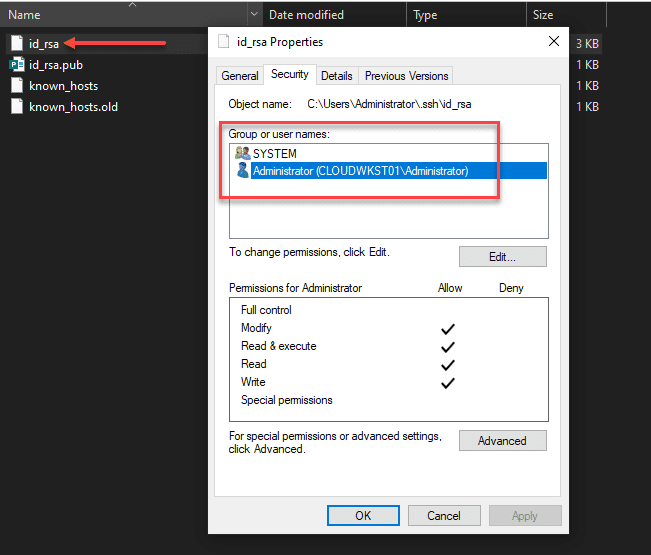
Permissions on your private key file
Now, on your private key, you need to ensure the same thing is set. The user that you are logged in with and SYSTEM are the only permissions that need to be enumerated on the private key file.
sshd_config file changes
Now that we have the permissions set correctly on the authorized_keys file and the private key, we need to make sure the sshd_config file is configured correctly. We need to make three changes for this to work correctly:
Below, I have uncommented the PubeyAuthentication yes stanza. Then, we have commented out the PasswordAuthentication yes and Match Group administrators configuration.
PubkeyAuthentication yes
#PasswordAuthentication yes
#Match Group administrators
# AuthorizedKeysFile __PROGRAMDATA__/ssh/administrators_authorized_keysBe sure to restart your OpenSSH SSH Server service on your Windows 10 machine after making these changes to the sshd_config file. Once the changes are in place, you should be able to connect to the machine via SSH.
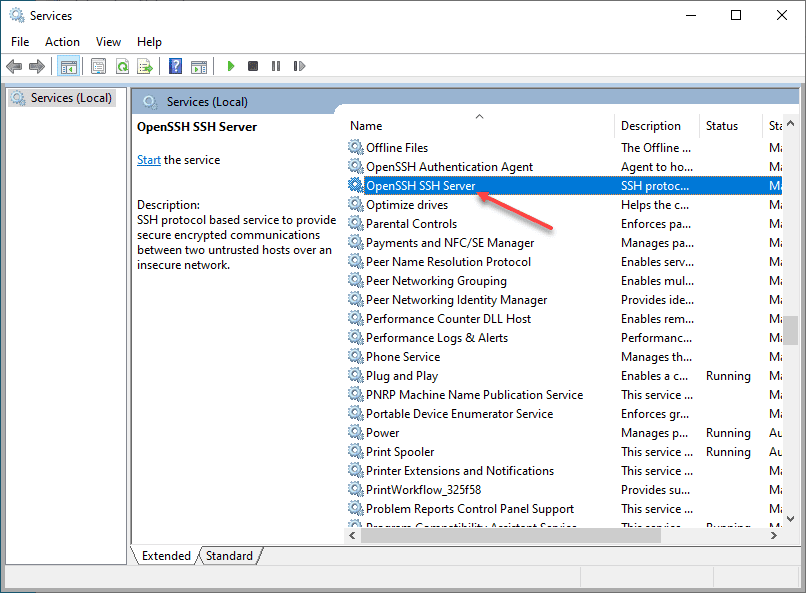
Wrapping Up
Connecting to Windows 10 via SSH is a great way to make secure connections to Windows 10 when public-key authentication is used. It can also be a great way to use solutions like Ansible to connect to your Windows 10 boxes remotely.
Я установил OpenSSH 7.6 в Windows 7 для целей тестирования. Клиент и сервер SSH работают нормально, пока я не попытался получить доступ к одной из своих коробок AWS EC2 из этого окна.
Кажется, мне нужно изменить разрешение на файл закрытого ключа. Это можно легко сделать в Unix / Linux с помощью chmodкоманды.
А как насчет окон?
private-key.ppm скопирован непосредственно из AWS, и я думаю, что разрешение тоже.
C:>ssh -V
OpenSSH_7.6p1, LibreSSL 2.5.3
C:>ver
Microsoft Windows [Version 6.1.7601]
C:>
C:>ssh ubuntu@192.168.0.1 -i private-key.ppk
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@ WARNING: UNPROTECTED PRIVATE KEY FILE! @
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
Permissions for 'private-key.ppk' are too open.
It is required that your private key files are NOT accessible by others.
This private key will be ignored.
Load key "private-key.ppk": bad permissions
ubuntu@192.168.0.1: Permission denied (publickey).
C:>
C:>
C:>ssh ubuntu@192.168.0.1 -i private-key.ppm
Warning: Identity file private-key.ppm not accessible: No such file or directory.
ubuntu@192.168.0.1: Permission denied (publickey).
C:>
Ответы:
Вы находите файл в проводнике Windows, щелкните его правой кнопкой мыши и выберите «Свойства». Перейдите на вкладку «Безопасность» и нажмите «Дополнительно».
Смените владельца на вас, отключите наследование и удалите все разрешения. Затем предоставьте себе «Полный контроль» и сохраните разрешения. Теперь SSH больше не будет жаловаться на разрешение файла, слишком открытое.
Это должно выглядеть так:
Ключи должны быть доступны только тому пользователю, для которого они предназначены, и никаким другим аккаунтам, сервисам или группам.
- GUI:
- Свойства [Файл] — Безопасность — Дополнительно
- Установите владельца на пользователя ключа
- Удалите всех пользователей, группы и службы, кроме пользователя ключа , в разделе « Записи разрешений».
- Установите для пользователя ключа полный доступ
- Свойства [Файл] — Безопасность — Дополнительно
-
CLI:
:: Set Variable :: set key="C:Pathtokey" :: Remove Inheritance :: cmd /c icacls %key% /c /t /inheritance:d :: Set Ownership to Owner :: cmd /c icacls %key% /c /t /grant %username%:F :: Remove All Users, except for Owner :: cmd /c icacls %key% /c /t /remove Administrator "Authenticated Users" BUILTINAdministrators BUILTIN Everyone System Users :: Verify :: cmd /c icacls %key%
В дополнение к ответу, предоставленному ibug. Так как я использовал систему Ubuntu внутри Windows, чтобы запустить команду SSH. Это все еще не работало. Так я и сделал
sudo ssh ...
и тогда это сработало
У меня была такая же проблема, и, похоже, она связана с версией SSH, которую вы используете.
Если я наберу
where ssh
Я получил…
C:WindowsSystem32OpenSSHssh.exe
C:Program FilesGitusrbinssh.exe
Когда я бегу ssh -Vв обоих местах, я получаю
OpenSSH_7.5p1, without OpenSSL
OpenSSH_7.3p1, OpenSSL 1.0.2k 26 Jan 2017
…соответственно
Итак, когда я запускаю sshиз каталога git / bin, он работает нормально и не жалуется на разрешения, но, запустив ту же командную строку, используя прежнюю установку SSH, он возвращается с этим.
Load key "t:\mykeys\rich-private.ppk": invalid format
banana@127.0.0.127: Permission denied (publickey).
пс. права доступа к файлу — это полный доступ для себя и больше ничего.
Вам нужны только 2 вещи:
1) Отключить наследование
2) Преобразовать унаследованные разрешения в явные разрешения
3) Удалить группу пользователей
4) В итоге пользователи не смогут получить доступ к личным файлам, этого должно быть достаточно для добавления id_rsa.
У меня была похожая проблема, но я был на работе, и у меня нет возможности изменять права доступа к файлам на моем рабочем компьютере. Что вам нужно сделать, это установить WSL и скопировать ключ в скрытый каталог ssh в WSL:
cp <path to your key> ~/.ssh/<name of your key>
Теперь вы сможете нормально изменять разрешения.
sudo chmod 600 ~/.ssh/<your key's name>
Затем SSH с использованием WSL:
ssh -i ~/.ssh/<name of your key> <username>@<ip address>
используйте команду ниже на вашем ключе, она работает на Windows
icacls .private.key /inheritance:r
icacls .private.key /grant:r "%username%":"(R)"
Вы можете использовать icacls в окнах вместо chmod для настройки прав доступа к файлам. Чтобы дать текущему пользователю разрешение на чтение и удалить все остальное,
icacls <file name> /inheritance:r
icacls <file name> /grant:r "%username%":"(R)"
Это всего лишь скриптовая версия ответа CLI @ JW0914, так что в первую очередь оповестите его. Кроме того, это мой первый скрипт PowerShell, поэтому предложения приветствуются.
# DO the following in powerhsell if not already done:
# Set-ExecutionPolicy RemoteSigned
# NOTE: edit the path in this command if needed
$sshFiles=Get-ChildItem -Path C:DevContainerHome.ssh -Force
$sshFiles | % {
$key = $_
& icacls $key /c /t /inheritance:d
& icacls $key /c /t /grant %username%:F
& icacls $key /c /t /remove Administrator "Authenticated Users" BUILTINAdministrators BUILTIN Everyone System Users
}
# Verify:
$sshFiles | % {
icacls $_
}
Одна строка в CMD может помочь (как описано здесь: https://serverfault.com/a/883338/550334 ), то есть добавление ключа из stdin вместо изменения разрешений:
cat /path/to/permission_file | ssh-add -k
Чтобы проверить, был ли добавлен ключ:
ssh-add -l
Я пользователь Windows, использую bash для Windows и выполнил все шаги, чтобы установить разрешение с помощью графического интерфейса Windows, но он все еще не работает и жалуется:
Permissions 0555 for 'my_ssh.pem' are too open.
It is required that your private key files are NOT accessible by others.
Я добавил sudoв начале команды ssh, и это просто работает. Надеюсь, что это полезно для других.
Ответ от iBug работает отлично! Вы можете следить за этим и избавиться от этой проблемы.
Но есть несколько вещей, которые необходимо очистить, так как я столкнулся с проблемами при настройке разрешений, и мне понадобилось несколько минут, чтобы выяснить проблему!
После ответа iBug вы удалите все разрешения, но как вы установите для себя разрешение «Полный доступ»? вот где я сначала застрял, так как не знал, как это сделать.
После отключения наследования вы сможете удалить всех разрешенных пользователей или групп.
Как только закончите с этим,
Нажмите на Addзатем нажмите Set a Principalзатем введите Systemи и Administratorsи your email addreddв поле внизу, затем нажмите check names.
Он загрузит имя, если пользователь существует. Затем нажмите OK> Тип Allow> Основные разрешения Full Control>Okay
Это установит разрешение «Полный доступ» для СИСТЕМЫ, Администраторов и Вашего Пользователя.
После этого попробуйте ssh, используя этот ключ. Это должно быть решено сейчас.
У меня была та же проблема, и я решил, что с помощью этого метода. Если есть какой-либо пользователь или группа с таким именем, он будет загружен.
-Screenshots-
Записи разрешений
Выберите принципала / выберите пользователя или группы
I get the following error from ssh:
Permissions 0777 for '/Users/username/.ssh/id_rsa' are too open.
It is recommended that your private key files are NOT accessible by others.
This private key will be ignored.
What permissions should I give to the id_rsa file?
Mateen Ulhaq
23.1k16 gold badges89 silver badges129 bronze badges
asked Feb 14, 2012 at 2:02
Yannick SchallYannick Schall
31.2k6 gold badges29 silver badges42 bronze badges
7
The keys need to be read-writable only by you:
chmod 600 ~/.ssh/id_rsa
Alternatively, the keys can be only readable by you (this also blocks your write access):
chmod 400 ~/.ssh/id_rsa
600 appears to be better in most cases, because you don’t need to change file permissions later to edit it. (See the comments for more nuances)
The relevant portion from the manpage (man ssh)
~/.ssh/id_rsa Contains the private key for authentication. These files contain sensitive data and should be readable by the user but not accessible by others (read/write/execute). ssh will simply ignore a private key file if it is accessible by others. It is possible to specify a passphrase when generating the key which will be used to encrypt the sensitive part of this file using 3DES. ~/.ssh/identity.pub ~/.ssh/id_dsa.pub ~/.ssh/id_ecdsa.pub ~/.ssh/id_rsa.pub Contains the public key for authentication. These files are not sensitive and can (but need not) be readable by anyone.
Zain Rizvi
23.3k20 gold badges90 silver badges129 bronze badges
answered Feb 14, 2012 at 2:05
quickshiftinquickshiftin
64.1k9 gold badges66 silver badges88 bronze badges
18
Using Cygwin in Windows 8.1, there is a command need to be run:
chgrp Users ~/.ssh/id_rsa
Then the solution posted here can be applied, 400 or 600 is OK.
chmod 600 ~/.ssh/id_rsa
Reference here
Cadoiz
1,21320 silver badges26 bronze badges
answered Apr 11, 2014 at 11:17
6
I’ve got the error in my windows 10 so I set permission as the following and it works.
In details, remove other users/groups until it has only ‘SYSTEM’ and ‘Administrators’. Then add your windows login into it with Read permission only.
Note the id_rsa file is under the c:users<username> folder.
answered Dec 8, 2018 at 3:08
5
The locale-independent solution that works on Windows 8.1 is:
chgrp 545 ~/.ssh/id_rsa
chmod 600 ~/.ssh/id_rsa
GID 545 is a special ID that always refers to the ‘Users’ group, even if you locale uses a different word for Users.
answered Feb 21, 2015 at 15:51
thehousethehouse
7,7575 gold badges32 silver badges32 bronze badges
0
Windows 10 ssh into Ubuntu EC2 “permissions are too open” error on AWS
I had this issue trying to ssh into an Ubuntu EC2 instance using the .pem file from AWS.
In windows this worked when I put this key in a folder created under the .ssh folder
C:UsersUSERNAME.sshprivate_key
To change permission settings in Windows 10 :
File Settings > Security > Advanced
Disable inheritance
Convert Inherited Permissions Into Explicit Permissions
Remove all the permission entries except for Administrators
Could then connect securely.
answered Mar 26, 2020 at 12:45
lm5050lm5050
7177 silver badges10 bronze badges
2
AFAIK the values are:
-
700for the hidden directory.sshwhere key files are located -
600for the keyfileid_rsa
Cadoiz
1,21320 silver badges26 bronze badges
answered Nov 13, 2014 at 7:57
ajaaskelajaaskel
1,59911 silver badges12 bronze badges
0
0600 is what mine is set at (and it’s working)
answered Feb 14, 2012 at 2:04
Devin CeartasDevin Ceartas
4,7211 gold badge20 silver badges33 bronze badges
0
I have got a similar issue when i was trying to login to remote ftp server using public keys.
To solve this issue I have done the following process:
- First find the location of the public keys, because when you try to login to ftp, this public key is used.
- Alternatively, you can create a key and set that key’s permissions to
600. - Make sure you are in the correct location and perform this command:
chmod 600 id_rsa
answered May 26, 2020 at 13:50
1
On Windows 10, cygwin’s chmod and chgrp weren’t enough for me. I had to
- right click on the file
- -> Properties
- -> Security (tab)
- and remove all users and groups except for my active user.
Cadoiz
1,21320 silver badges26 bronze badges
answered Jul 21, 2018 at 5:39
Jared BeachJared Beach
2,35132 silver badges36 bronze badges
2
I got success with sudo
sudo chmod 400 pem-file.pem
sudo ssh -i pem-file.pem username@X.X.X.X
answered Mar 3, 2021 at 3:31
Navy FlameNavy Flame
8858 silver badges21 bronze badges
3
provide 400 permission,
execute below command
chmod 400 /Users/username/.ssh/id_rsa
answered Aug 28, 2018 at 11:03
0
There is one exception to the 0x00 permissions requirement on a key. If the key is owned by root and group-owned by a group with users in it, then it can be 0440 and any user in that group can use the key.
I believe this will work with any permissions in the set 0xx0 but I haven’t tested every combination with every version. I have tried 0660 with 5.3p1-84 on CentOS 6, and the group not the primary group of the user but a secondary group, and it works fine.
This would typically not be done for someone’s personal key, but for a key used for automation, in a situation where you don’t want the application to be able to mess with the key.
Similar rules apply to the .ssh directory restrictions.
Cadoiz
1,21320 silver badges26 bronze badges
answered Nov 13, 2013 at 17:18
syberghostsyberghost
3092 silver badges4 bronze badges
0
For windows users Only.
Goto file property —> security —> advanced
- Disable inheritance property
- Convert Inherited Permissions Into Explicit Permissions.
- Remove all the permission entries except the Administrators.
answered Jul 27, 2020 at 4:50
VasuVasu
4815 silver badges7 bronze badges
0
This is what worked for me (on mac)
sudo chmod 600 path_to_your_key.pem
then :
ssh -i path_to_your_key user@server_ip
Hope it help
answered Jan 22, 2019 at 12:14
lansanalsmlansanalsm
3392 silver badges10 bronze badges
0
In case you are using WSL on windows
The most simple answer is to just type: sudo ssh -i keyfile.pem <user>@ip
without changing the file permissions.
The reason why this happens?
Another resource
You can’t modify the permissions of files on Windows’s filesystem
using chmod on Bash on Ubuntu on Windows. You’ll have to copy the
private key to your WSL home directory (~) and do it there.
On the other hand, sudo should never be utilized with ssh. The reason why issuing with sudo works is that it’s now likely being executed as root, and this is not the correct way to do this and is a massive security risk, as Allowing for anything other the 600/400 permissions defeats the purpose of utilizing an SSH key, compromising the security of the key.
The best way to do that is by copying the file to $HOME/.ssh:
cp keyfile.pem ~/.ssh
Doing sudo chmod 400 keyfile.pem to it.
Then ssh -i keyfile.pem <user>@ip.
answered Nov 15, 2021 at 9:22
Mostafa WaelMostafa Wael
2,2201 gold badge16 silver badges19 bronze badges
For me (using the Ubuntu Subsystem for Windows) the error message changed to:
Permissions 0555 for 'key.pem' are too open
after using chmod 400.
It turns out that using root as a default user was the reason.
Change this using the cmd:
ubuntu config --default-user your_username
answered Dec 2, 2018 at 4:30
what worked for me
chgrp Users FOLDER
chmod 600 FOLDER
answered Mar 26, 2014 at 22:54
Jerome AnsiaJerome Ansia
6,79410 gold badges52 silver badges99 bronze badges
3
I got same issue after migration from another mac.
And it blocked to connect github by my key.
I reset permission as below and it works well now.
chmod 700 ~/.ssh # (drwx------)
cd ~/.ssh
chmod 644 *.pub # (-rw-r--r--)
chmod 600 id_rsa # (-rw-------)
answered Jul 28, 2019 at 3:59
Jeff Gu KangJeff Gu Kang
4,6292 gold badges34 silver badges44 bronze badges
1
700 folder
644 id_rsa.pub
this works for me.
answered Apr 9, 2021 at 9:47
B.KingsunB.Kingsun
3323 silver badges11 bronze badges
As people have said, in Windows, I just dropped my .pem file in C:Users[user].ssh and that solved it. Although you can do chmod and other command line options from a bash or powershell prompt that didn’t work. I didn’t change rsa or anything else. Then when running the connection you have to put the path to the pem file in the .ssh folder:
ssh -i "C:Users[user].sshubuntukp01.pem" ubuntu@ec[ipaddress].us-west-2.compute.amazonaws.com
answered Jun 25, 2020 at 12:22
Win SwarrWin Swarr
691 silver badge1 bronze badge
0
I keep all my own certificates and keys in one directory, and this works for tools like PuTTY, but I got this too open error message from the scp command. I discovered that Windows already maintains a C:usersACCOUNTNAME.ssh folder having the proper access rights for storing SSH keys. So long as you keep the contents backed up (Windows sometimes deletes it during updates), or create your own folder for ssh keys in your user folder, this will work fine, as only you and the administrators have access to that parent folder.
Be very careful about changing access rights on Windows folders. I did this, and once a day Windows is scanning, reading, and writing all the files on my C: drive, a process that slows the computer for many minutes.
answered Dec 29, 2020 at 19:52
0
Interesting message here.
Operating Systems are smart enough to deny remote connections if your private key is too open. It understands the risk where permissions for id_rsa is wide open (read, is editable by anyone).
{One may change your lock first and then open it with the keys he already has}
cd ~/.ssh
chmod 400 id_rsa
While working on the multiple servers (non-production), most of us feel need to connect remote server with ssh. A good idea is to have a piece of application level code (may be java using jsch) to create ssh trusts between servers. This way connection will be password-less. Incase, perl is installed — one may use net ssh module too.
answered May 13, 2015 at 7:35
The other trick is to do that on the downloads folder.
After you download the private key from AWS EC2 instance, the file will be in this folder,then simply type the command
ssh-keygen -y -f myprivateKey.pem > mypublicKey.pub
answered Aug 25, 2020 at 14:48
I am using Windows 10 and trying to connect to EC2 instance via SSH. Rather than using Cygwin for Windows, try using Git Bash. After doing chmod 400 for key I am able to SSH into the EC2 instance, but the same is not working for me from Cygwin. Windows treats the .pem file as coming from internet and blocks it, even disabling inheritance doesn’t work.
I converted the file to .ppk format and it’s working fine from PuTTY also, but it’s not working from Cygwin.
karel
5,01243 gold badges45 silver badges50 bronze badges
answered Apr 3, 2021 at 16:25
AshuAshu
6058 silver badges16 bronze badges
1
for Windows :
Strange, but UI tweaks, described here before did not helped me.
But this solved the issue :
- Open PowerShell under admin rights
- Go to directory with your keys (using cd command)
- Enter commands one by one
:
$path = ".{your private key file name}" //for example "myKey"
Then remove your explicit permissions by typing:
icacls.exe $path /reset
Then assign to current user read-permission:
icacls.exe $path /GRANT:R "$($env:USERNAME):(R)"
Then remove inheritance:
icacls.exe $path /inheritance:r
Hope, will help someone
answered Sep 5, 2022 at 11:16
NigrimmistNigrimmist
8,9984 gold badges49 silver badges50 bronze badges
In my case the issue was a whitespace too much.
ssh -i mykey.pem ubuntu@instace.eu-north-1.compute.amazonaws.com
but
ssh -i mykey.pem ubuntu@instace.eu-north-1.compute.amazonaws.com
worked fine. The problem is that the whitespace is taken as part of the username.
answered Mar 19, 2021 at 13:00
coorassecoorasse
5,0881 gold badge32 silver badges43 bronze badges
I was getting this issue on WSL on Windows while connecting to AWS instance. My issue got resolved by switching to classic Command prompt. You can try switching to a different terminal interface and see if that helps.
answered Feb 19, 2021 at 19:06
LeenaLeena
6371 gold badge11 silver badges19 bronze badges
I tried 600 level of permission for my private key and it worked for me.
chmod 600 privateKey
[dev]$ ssh -i privateKey user@ip
On the other hand,
chmod 755 privateKey
[dev]$ ssh -i privateKey user@ip
was giving below issue:
Permissions 0755 for 'privateKey' are too open.
It is required that your private key files are NOT accessible by others.
This private key will be ignored.
Load key "privateKey": bad permissions
answered Feb 14, 2019 at 8:41
I have came across with this error while I was playing with Ansible. I have changed the permissions of the private key to 600 in order to solve this problem. And it worked!
chmod 600 .vagrant/machines/default/virtualbox/private_key
answered Apr 2, 2018 at 15:53
vildhjartavildhjarta
5542 gold badges5 silver badges15 bronze badges
For Windows 10 this is what I’ve found works for me:
- Move your key to the Linux file system:
mv ~/.ssh /home/{username} - Set the permission on that key:
chmod 700 /home/{username}/.ssh/id_rsa - Create a symbolic link to the key:
ln -s /home/{username}/.ssh ~/.ssh
This happens if you have set your home directory (~) to be stored in Windows instead of Linux (under /mnt/ vs /home/).
answered Jul 26, 2020 at 21:06
theEpsilontheEpsilon
1,67016 silver badges28 bronze badges
Обновлено 07.04.2022
Добрый день! Уважаемые читатели и гости одного из крупнейших IT блогов в рунете Pyatilistnik.org. В прошлый раз мы с вами разобрали ошибку, что для устройства не установлены драйверы (код 28). Идем далее и сегодня хочу с вами поделиться практическими знаниями, по устранению ошибки в open ssh клиенте Windows. Звучит она вот так, что на секретный ключ id_rca bad permissions (WARNING: UNPROTECTED PRIVATE KEY FILE, Permission denied publickey). В результате подключиться не получается. Давайте переходить от слов к делу.
Как выглядит ошибка id_rsa bad permissions
В командной строке Windows при попытке подключения выскакивает ошибка:
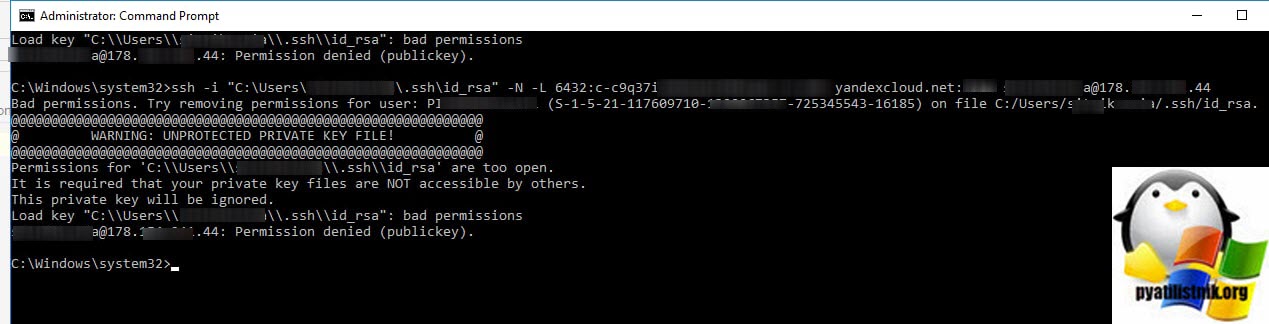
Bad permissions. Try removing permissions for user: Pyatilistnik\seminivan (S-1-5-21-117609710-5564564-725645543-16185) on file C:/Users/barboskin/.ssh/id_rsa.
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@ WARNING: UNPROTECTED PRIVATE KEY FILE! @
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
Permissions for ‘C:\Users\barboskin\.ssh\id_rsa’ are too open.
It is required that your private key files are NOT accessible by others.
This private key will be ignored.
Load key «C:\Users\barboskin\.ssh\id_rsa»: bad permissions
barboskin@178.15.24.44: Permission denied (publickey).
Как устранить ошибку Permission denied (publickey)
Проблема тут в том, что файл id_rca, который располагается в директории пользователя от имени которого запускается команда, имеет в списке доступа другие группы и пользователей, и вам это нужно избежать. Тут три варианта решения задачи:
Используем скрипт PowerShell
Запустите в режиме администратора оснастку PowerShell ISE и запустите в нем такой скрипт.
# Устанавливаем переменную для ключевого файла:
New-Variable -Name Key -Value «$env:UserProfile.sshid_rsa»
# Удаляем наследование:
Icacls $Key /c /t /Inheritance:d
# Делаем владельцем файла текущего пользователя:
# Key’s within $env:UserProfile:
Icacls $Key /c /t /Grant ${env:UserName}:F
# Ключ вне $env:UserProfile:
TakeOwn /F $Key
Icacls $Key /c /t /Grant:r ${env:UserName}:F
# Удаляем всех пользователей, кроме владельца из ACL:
Icacls $Key /c /t /Remove:g Administrator «Authenticated Users» BUILTINAdministrators BUILTIN Everyone System Users
# Проверка:
Icacls $Key
# Удаляем переменную:
Remove-Variable -Name Key
Иногда, данный скрипт все же не всех удалят пользователей из ACL, так, что если опять получаете ошибку, то зайдите и проверьте через графический интерфейс.
Редактирование ACL через графический интерфейс
Тут все просто, переходите в расположение файла:
C:Usersимя_пользователя.sshid_rsa
Щелкаем по файлу правым кликом, из контекстного меню выбираем пункт свойства и переходим на вкладку «Безопасность«. Нажмите кнопку «Дополнительно (Advanced)«
Отключаем наследование и сохраняем текущие разрешения «Преобразовать унаследованные разрешения в явные разрешения данного объекта (Convert inherited permission into explicit permissions on this object«.
Далее если вы не являетесь текущим владельцем данного файла, то сделайте себя им и так же удалите потом всех кроме себя в данном списке доступа.
Сохраняем все, после этого у вас должна пропасть ошибка «id_rsa»: bad permissions» и «Permission denied (publickey)».
Используем скрипт командной строки
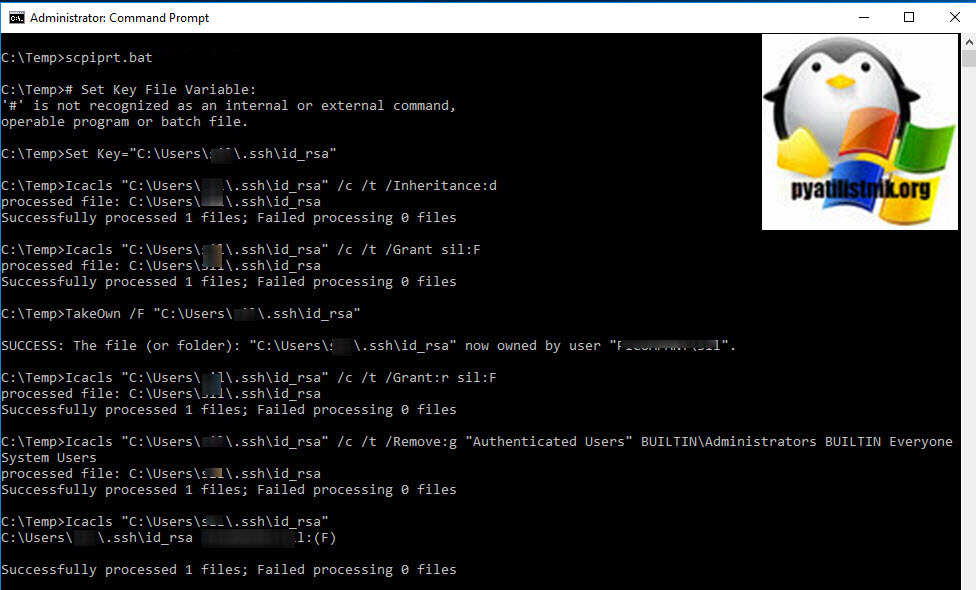
Во первых вам необходимо создать bat-файл. После чего запустите командную строку от имени администратора и запустите созданный ранее bat-файл.
# Установить переменную ключевого файла::
Set Key=»%UserProfile%.sshid_rsa»
::# Удалить наследование:
Icacls %Key% /c /t /Inheritance:d
::# Установить право собственности на владельца:
:: # Key’s within %UserProfile%:
Icacls %Key% /c /t /Grant %UserName%:F
:: # Ключ outside на %UserProfile%:
TakeOwn /F %Key%
Icacls %Key% /c /t /Grant:r %UserName%:F
::# Удалить всех пользователей, кроме владельца:
Icacls %Key% /c /t /Remove:g «Authenticated Users» BUILTINAdministrators BUILTIN Everyone System Users
::# Проверять:
Icacls %Key%
::# Удалить переменную:
set «Key=»
На этом все. Мы рассмотрели три метода позволяющих исправить ошибки «id_rsa»: bad permissions» и «Permission denied (publickey)» при попытке установить ssh соединение через OpenSSH в Windows. С вами был Иван Сёмин, автор и создатель IT проекта Pyatilistni.org.
Установил xfce вместо unity на ubuntu. После чего git fetch начал отдавать такую штуку:
$ git fetch @@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@ @ WARNING: UNPROTECTED PRIVATE KEY FILE! @ @@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@ Permissions 0644 for '/home/username/.ssh/id_rsa' are too open. It is required that your private key files are NOT accessible by others. This private key will be ignored. Load key "/home/username/.ssh/id_rsa": bad permissions Permission denied (publickey). fatal: Could not read from remote repository. Please make sure you have the correct access rights and the repository exists.
Permissions 0644 for ‘~/.ssh/id_rsa’ are too open — т.е. файл ключа id_rsa имеет слишком много прав.
Смотрим текущие права:
$ ls -la ~/.ssh/ total 24 drwx------ 2 eugeney eugeney 4096 Jun 6 16:42 . drwxr-xr-x 33 eugeney eugeney 4096 Jun 13 12:10 .. -rw-r--r-- 1 eugeney eugeney 1679 Mar 11 2013 id_rsa -rw-r--r-- 1 eugeney eugeney 398 Mar 11 2013 id_rsa.pub -rw-r--r-- 1 eugeney eugeney 5534 Jun 13 10:35 known_hosts
Основная проблема в том, что с такими правами наш ключ могут читать и другие пользователи. Поэтому система обязывает нас изменить права. Запретим другим пользователям читать наш id_rsa, выставив права только для нашего пользователя с помощью команды chmod.
Задаём права 700 либо 600 на приватный ключ ~/.ssh/id_rsa
chmod 700 ~/.ssh/id_rsa
Теперь у текущего пользователя будут права на запись, чтение и выполнение (цифра 7). А у остальных пользователей не будет никаких прав на этот файл (цифра 0).
600 и 700 оба варианта подходят.
После этого ssh авторизация по ключу должна проходить без ошибок.
Дата добавления:
7 лет назад
Add Answer
|
View In TPC Matrix
Technical Problem Cluster First Answered On
May 22, 2021
Popularity
7/10
Helpfulness
2/10
Contributions From The Grepper Developer Community
Contents
Code Examples
Related Problems
TPC Matrix View Full Screen
pem file is too open
Comment
0
Popularity
7/10 Helpfulness
2/10
Language
whatever
Source: superuser.com
Tags: file
pem
whatever
Contributed on May 22 2021
Dinith
3 Answers Avg Quality 5/10