What is Password Policy?
Password policy is the policy which is used to restrict some credentials on windows server 2016 and previous versions of Server 2012, 2008 and 2003.
A password policy is a set of rules designed to enhance computer security by encouraging users to employ strong passwords and use them properly. A password policy is often part of an organisation’s official regulations and may be taught as part of security awareness training. The password policy may either be advisory or mandated by technical means. Some governments have national authentication frameworks that define requirements for user authentication to government services, including requirements for passwords. So follow the under instructions to know how to configure password policy with windows server 2016. “Wikipedia”
How to Configure Password Policies with Windows Server 2016?
You can open up Group Policy Management Editor into three various ways.
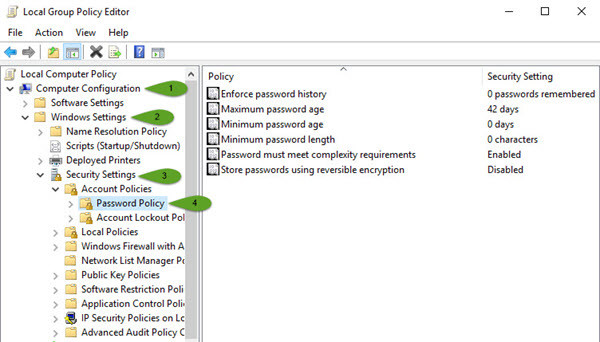
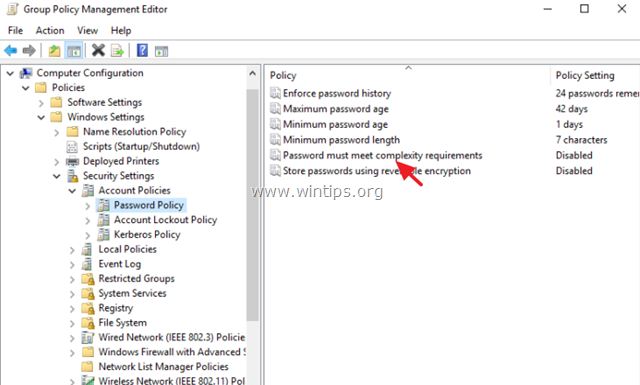
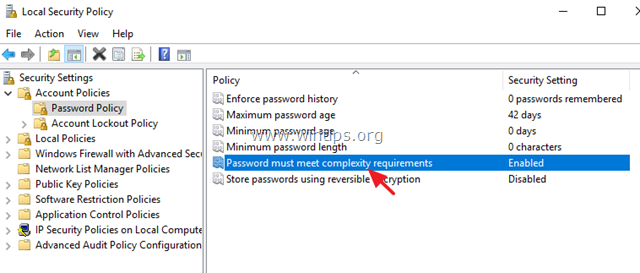
First Method: press windows key and type control panel and now select administrative tools and then select local security policy. A new window will pop up, click account policies, Password Policy. Here you will see about six policies. If you don’t want to use the graphical way just type gpedit.msc on the RUN window then hit enter. Now go to this path. Computer Configuration/Windows Settings/Security Settings/Password Policy.
Local Group Policy Editor
Second Method: If you don’t want to use the graphical way just type gpedit.msc on the RUN window then hit enter. Now go to this path. Computer Configuration>Windows Settings>Security Settings>Password Policy.
Group Policy Editor
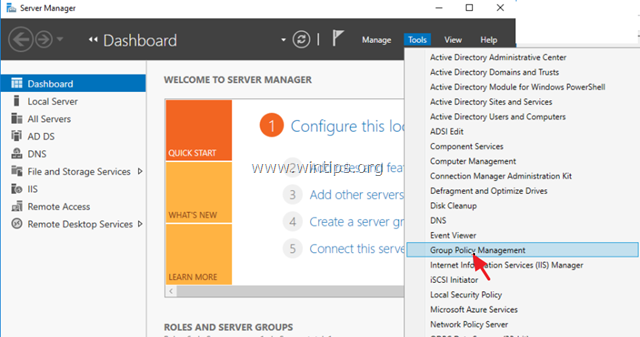
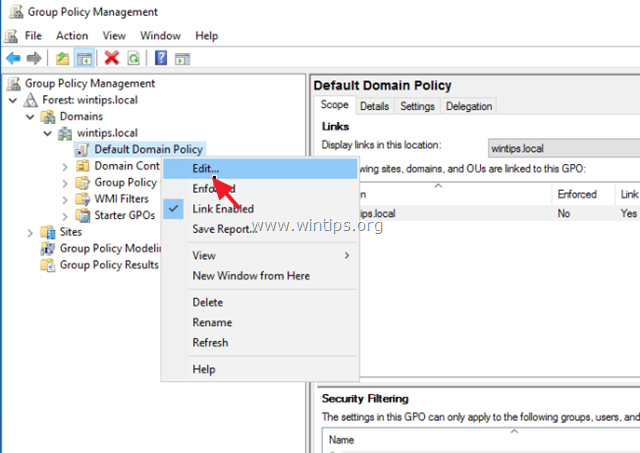
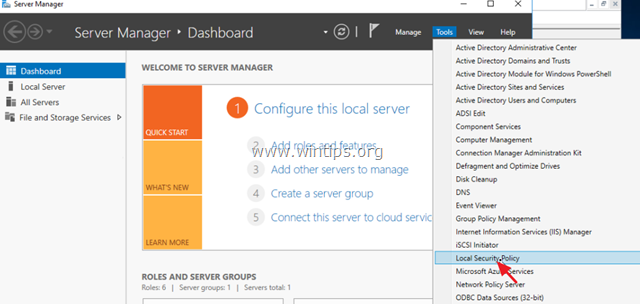
Third Method: Open Server Manager and click on Tools. Scroll down until you see the GPO (Group Policy Management). Right, click on the Domain then choose Edit. Now you will see the same window as before. Go to Computer Configuration> Windows Settings> Security Settings> Password Policy.
These were three different ways that you can apply password policy on the network computers.
What is Enforce Password History?
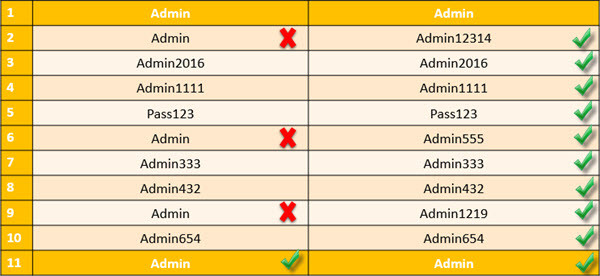
Enforce password history is the policy that doesn’t allow the users to use the same password for many times. For example, Once your Device password is Admin, and for the next time, you can’t use this password for login on your computer. After some months or year, it may expire. When it is expired, so you must use another password. Here I have set it to 10 times. It means that I can’t use my old password less than 10 times. In ten times, I must use a different password. After 10 times, I can use my first password. For more information, look at the chart below.
Enforce Password History rules
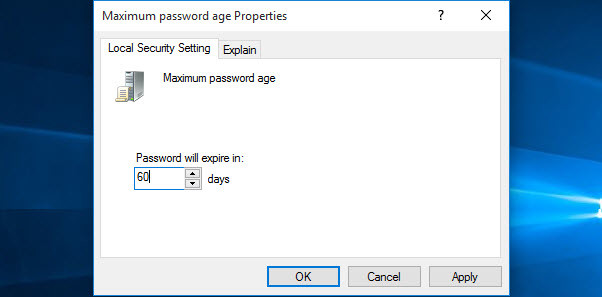
What is Maximum password Age?
This security setting determines the time in days that a password can be used before the system requires the user to change it. You can set passwords to expire after several days between 1 to 999, or you can specify that passwords never expire by setting the number of days to 0 if the maximum password age is between 1 and 999 days. The minimum password age must be less than the maximum password age if the maximum password age is set to 0. The minimum password age can be any value between 0 and 998 days.
Maximum Password Age
Note: It is a security best practice to have passwords expire every 30 to 90 days, depending on your environment. This way, an attacker has a limited amount of time to crack a user’s password and have access to your network resources.
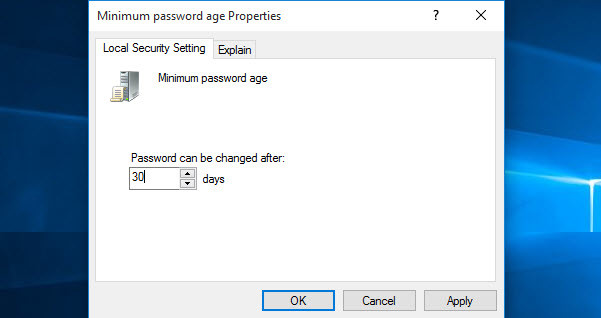
What is the Minimum Password Age?
The minimum password age must be less than the maximum password age unless the maximum password age is set to 0, indicating that passwords will never expire. If the maximum password age is set to 0, the minimum password age can be set to any value between 0 to 998. It’s vital that you have to use the minimum password age. If you don’t use, the user may cycle the password history till they get their old favourite password. If you set the minimum password age, so they will not change their password quickly.
Minimum Password Age
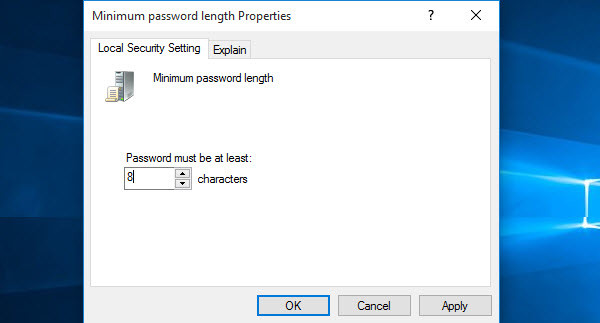
What is the Minimum Password Length?
This is security setting determines the least number of characters that a password for a user account may contain. You can set a value of between 1 and 14 characters, or establish that no password is required by setting the number of characters to 0. Here I have set up to 8 characters. Mostly you see this policy on websites or social accounts.
Minimum Password Length
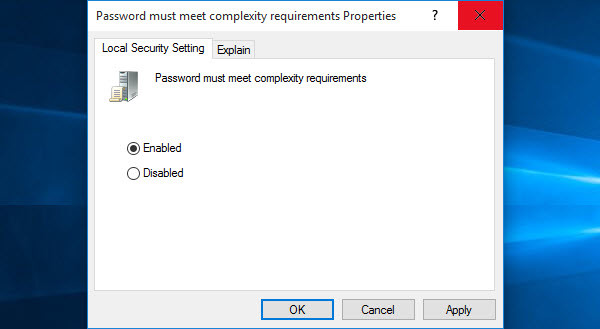
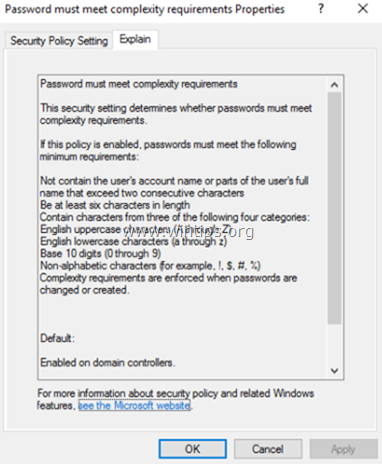
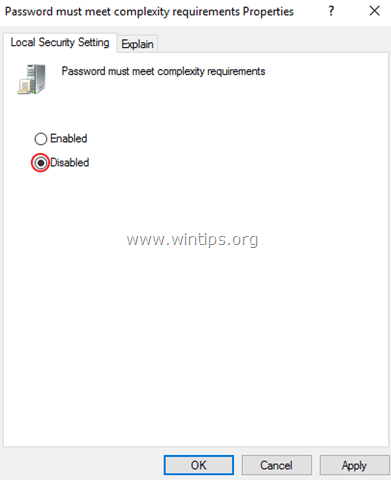
What are Password Complexity Requirements?
If this policy is enabled, passwords must meet the following minimum requirements.
- Be at least six characters in length
- Contain characters from three of the following four categories
- English uppercase letters (A through Z)
- English Lowercase letters (a through z)
- Base 10 digit (0 through 9)
- Non-alphabetic characters ( !,@,#,$,%&,*)
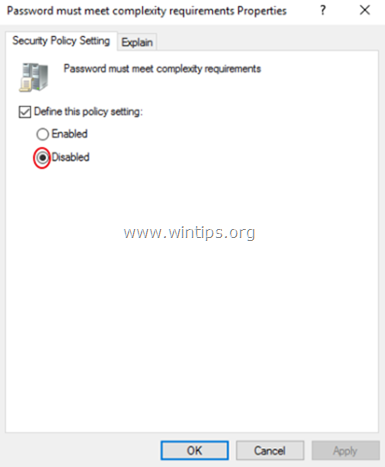
Password Must Meet Complexity Requirements
It’s beneficial and restricts vulnerabilities. You can see this policy when you create an Apple ID.
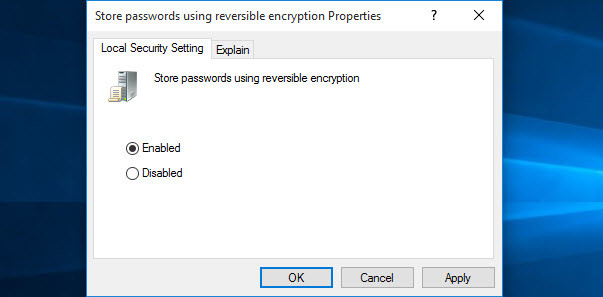
Store Passwords Using Reversible Encryption
This policy provides support for applications that use protocols that require knowledge of the user’s password for authentication purposes. Storing passwords using reversible encryption is essentially the same as storing plaintext versions of the passwords. For this reason, this policy should never be enabled unless application requirements outweigh the need to protect password information. I should tell you when you enabled this option; it will encrypt the password and no-one can access your password very easily.
Store Passwords Using Reversible Encryption
It was all about how to configure password policies with windows server 2016. It does not only work on windows server 2016 but also work on later versions. Thanks for being with us.
Параметр политики «Пароль должен соответствовать требованиям сложности» в Server 2016 определяет минимальные требования при изменении или создании паролей. Правила, включенные в требования к сложности пароля Windows Server, являются частью Passfilt.dll и не могут быть изменены напрямую.
По умолчанию в Server 2016 пароли должны соответствовать следующим минимальным требованиям:
1. Пароли не должны содержать имя учетной записи пользователя или части полного имени пользователя, которые превышают два последовательных символа.
2. Пароли должны быть длиной не менее семи символов.
3. Пароли должны содержать символы из трех следующих четырех категорий:
а. Английские заглавные буквы (от A до Z)
б. Английские строчные буквы (от a до z)
с. Базовые 10 цифр (от 0 до 9)
д. Не алфавитные символы (например,!, $, #,%)
В этом руководстве содержатся инструкции по отключению требований к сложности паролей на автономном сервере 2016 или в контроллере домена Active Directory 2016.
Как удалить требования к сложности паролей в Active Directory Server 2016 или автономном сервере 2016.
Часть 1. Как отключить требования к сложности паролей в Active Directory 2016.
Часть 2. Как отключить требования к сложности паролей на автономном сервере 2016 года.
Часть 1. Как отключить требования сложности пароля в Active Directory Domain Server 2016.
Снять сложность пароля в Active Directory 2016.
1. В контроллере домена AD Server 2016 откройте Диспетчер серверов а затем из инструменты меню, откройте Управление групповой политикой. *
* Кроме того, перейдите к Панель управления -> Инструменты управления -> Управление групповой политикой.
2. Под Домены, выберите свой домен и затем щелкните правой кнопкой мыши в Политика домена по умолчанию и выбрать редактировать.
3. Затем перейдите к:
- Конфигурация компьютера Политики Параметры Windows Параметры безопасности Политики учетных записей Политика паролей
4. На правой панели дважды щелкните на Пароль должен соответствовать требованиям сложности.
5. Выбрать Определите этот параметр политики: отключено а затем нажмите хорошо.
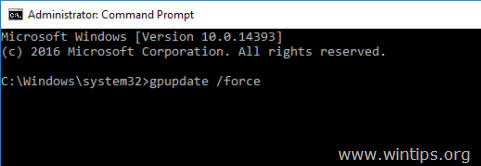
6. Наконец, откройте командную строку от имени администратора и введите следующую команду, чтобы обновить групповую политику.
- gpupdate / force
Часть 2. Как отключить требования сложности пароля в автономном сервере 2016 года.
1. Из диспетчера сервера перейдите на инструменты и открыть Политика локальной безопасности, или (дополнительно) перейдите к Панель управления открыто Инструменты управления а затем откройте Политика локальной безопасности.
2. Под Настройки безопасности, Выбрать Политика паролей.
3. На правой панели дважды щелкните на Пароль должен соответствовать требованиям сложности.
4. Выбрать инвалид а затем нажмите ХОРОШО.
5. Наконец, откройте командную строку от имени администратора и введите следующую команду, чтобы обновить групповую политику.
- gpupdate / force
Это оно! Дайте мне знать, если это руководство помогло вам, оставив свой комментарий о вашем опыте. Пожалуйста, любите и делитесь этим руководством, чтобы помочь другим.
microsoft:server:password_policy
Содержание
Windows Server 2016 Std Edition. Сервер без AD/домена. Парольные политики настраиваются штатными средствами ОС через групповые политики.
Политика паролей
Windows+R → gpedit.msc Enter
-
Local Computer Policy (Политика «Локальный компьютер»
-
Computer Configuration (Конфигурация компьютера)
-
Windows Settings (Конфигурация Windows)
-
Security Settings (Параметры безопасности)
-
Account Policies (Политики учетных записей)
-
Password Policy (Политика паролей)
-
-
-
-
-
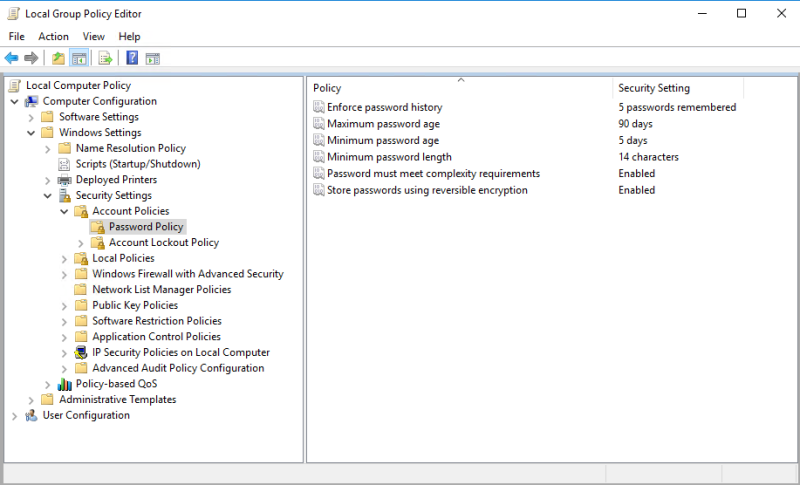
| Политика | Краткое пояснение | Возможные значения | Значение по-умолчанию |
|---|---|---|---|
| Enforce password history Вести журнал паролей |
Параметр определяет число новых уникальных паролей, которые должны быть назначены учетной записи пользователя до повторного использования старого пароля | 0-24 | AD: 24 пароля Stand-alone: 0 |
| Maximum password age Максимальный срок действия пароля |
Параметр определяет период времени (в днях), в течение которого можно использовать пароль, пока система не потребует от пользователя сменить его. | 1-999 | 42 |
| Minimum password age Минимальный срок действия пароля |
Параметр определяет период времени (в днях), в течение которого необходимо использовать пароль, прежде чем пользователь сможет его изменить. | 0-998 | 1 день |
| Minimum password length Минимальная длина пароля |
Параметр определяет минимальное количество знаков, которое должно содержаться в пароле | 0 — без пароля, 1-14 | AD:7 Stand-alone: 0 |
| Password must meet complexity requirements Пароль должен отвечать требованиям сложности |
Параметр определяет должен ли пароль отвечать требованиям:
|
Включена / Отключена | Включено |
| Store passwords using reversible encryption Хранить пароли, используя обратимое шифрование |
Параметр определяет, используется ли операционной системой для хранения паролей обратимое шифрование. | Включена/ Отключена | Отключено |
Политика блокировки учетных записей (Account Lockout Policy)
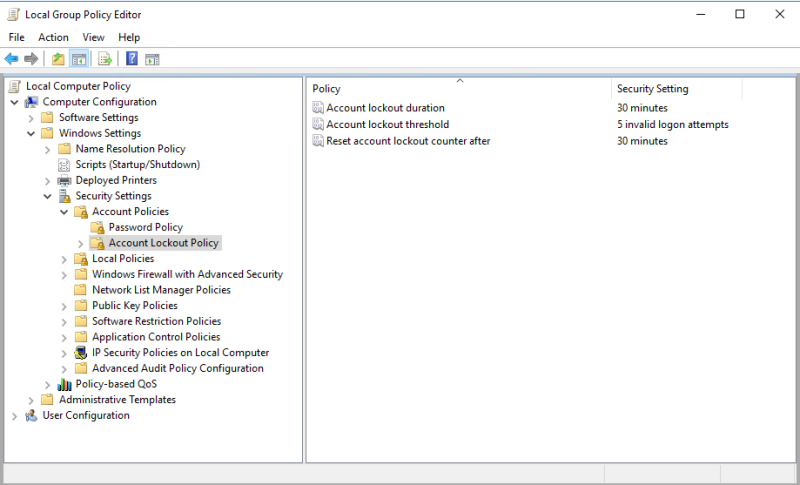
-
Computer Configuration (Конфигурация компьютера)
-
Windows Settings (Конфигурация Windows)
-
Security Settings (Параметры безопасности)
-
Account Policies (Политики учетных записей)
-
Account Lockout Policy (Политика блокировки учётных записей)
-
-
-
-
| Политика | Краткое пояснение | Возможные значения | Значение по-умолчанию |
|---|---|---|---|
| Account lockout duration Время до сброса счетчика блокировки. |
Параметр определяет количество минут, которые должны пройти после неудачной попытки входа в систему до того, как счетчик неудачных попыток входа будет сброшен до 0 | 0-99999 | Не определено |
| Account lockout threshold Пороговое значение блокировки. |
Параметр определяет количество неудачных попыток входа в систему, приводящее к блокировке учетной записи пользователя. | 0-999 | 0 |
| Reset account lockout counter after Продолжительность блокировки учетной записи. |
Параметр определяет количество минут, в течение которых учетная запись остается заблокированной до ее автоматической разблокировки. | 0-99999 | Не определено |
Для немедленного применения изменений необходимо выполнить в cmd
gpupdate /force
Просмотр политик через cmd/powershell
Текущие парольные политики
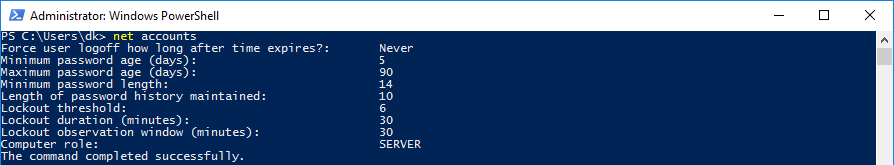
Информация о пользователе
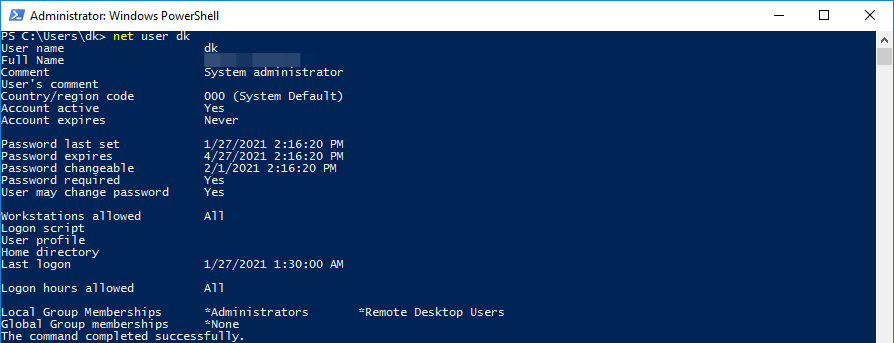
Catch-22 / Уловка-22
Проблема: невозможно установить через RDP новый пароль если у пользователя установлено User must change password at next logon.
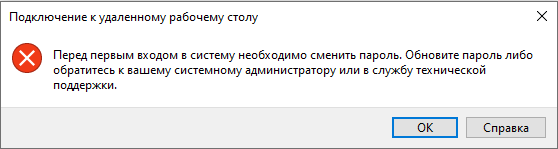
Уловка-22 (англ. Catch-22) — ситуация, возникающая в результате логического парадокса между взаимоисключающими правилами и процедурами.
Нам необходимо войти в систему, чтобы изменить пароль, но мы не можем войти в систему пока не поменяем пароль.
Вот как это объясняет Microsoft.
In the protocol specification for CredSSP, there is no reference to the ability to change the user’s password while NLA is running. Therefore, the observed behavior can be considered «by design.»
Лучшее разъяснение по данному вопросу.
После долгих поисков в сети
я понял, что единственное простое решение это отключить NLA на стороне сервера
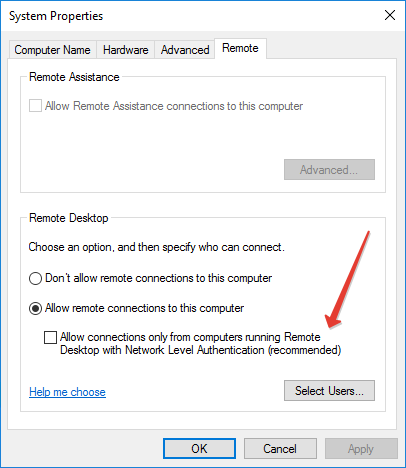
а на стороне клиента отключить CredSSP (отредактировать локальный .RDP файл)
enablecredsspsupport:i:0
Безопасно ли это? Наш Approved Scanning Vendor считает, что риск перехвата сессии или риск удаленного выполнения вредоносного кода минимален ЕСЛИ передача аутентификационных данных осуществляется по защищенному каналу связи (например OpenVPN).
Существует еще один вариант решения проблемы — установить RD Web Access. Но это установка IIS и дополнительный пункт в правильной настройки безопасности сервера. Для сервера без Active Directory это избыточно.
EOM
This website uses cookies. By using the website, you agree with storing cookies on your computer. Also you acknowledge that you have read and understand our Privacy Policy. If you do not agree leave the website.More information about cookies
· Последнее изменение: 2021/01/29 19:16 —
127.0.0.1
Смена пароля AD
Это руководство описывает процедуру изменения пароля для сервера со службой домена Active Directory
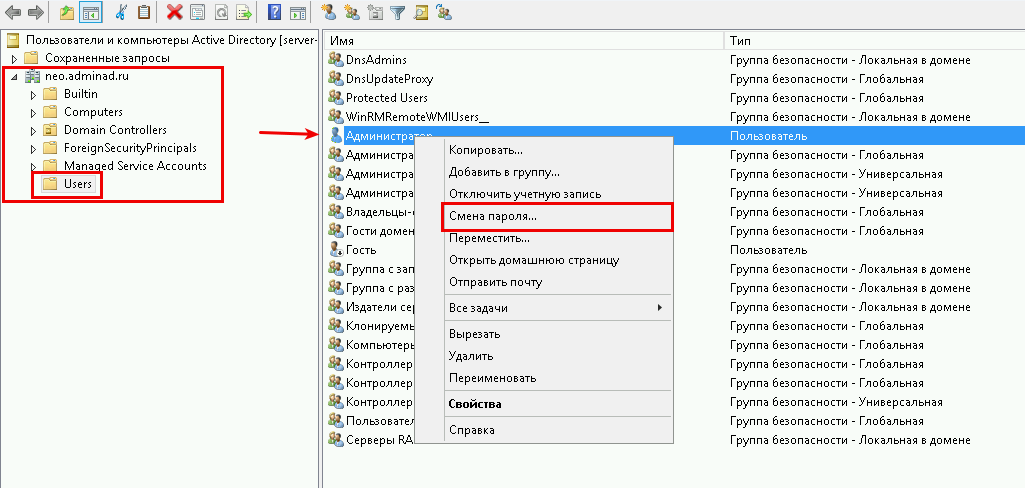
Для этого откройте «Пуск» -> «Средства администрирования» -> «Пользователи и компьютеры Active Directory»
В новом окне, откройте раздел c именем Вашего домена, на скриншоте это «neo.adminad.ru» и нажмите на папку «Users»
Слева появится список пользователей, выберите одного из пользователей по имени и правой кнопкой мыши откройте пункт «Смена пароля…»
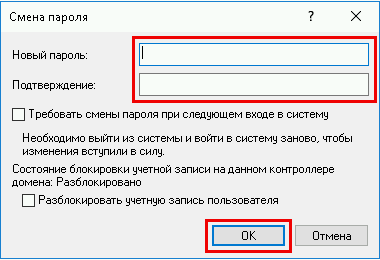
В окне смена пароля,
1. Введите новый пароль (пароль должен быть не меньше 8 символов)
2. Установите галочку на пункте «Требовать смену пароля при следующем входе в систему» — если требуется.
3. Разблокировать учетную запись пользователя — если пользователь был заблокирован системой.
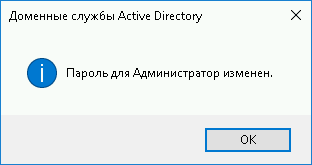
Нажмите «ОК»
Если все данные ввели правильно то появится окно об удачной смене пароля
Готово
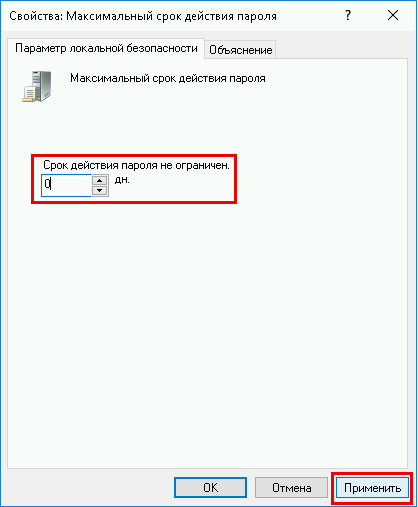
Срок истечения пароля AD
Теперь мы рассмотрим процедуру изменения срока пароля для сервера со службой домена Active Directory
Для этого откройте «Пуск» -> «Средства администрирования» -> «Управление групповой политикой»
Далее откроется окно «Управление групповой политикой», в блоке слева откройте дерево
«Лес: Имя Вашего домена»
-> «Домены»
-> «Имя Вашего домена»
-> «Default Domain Policy»
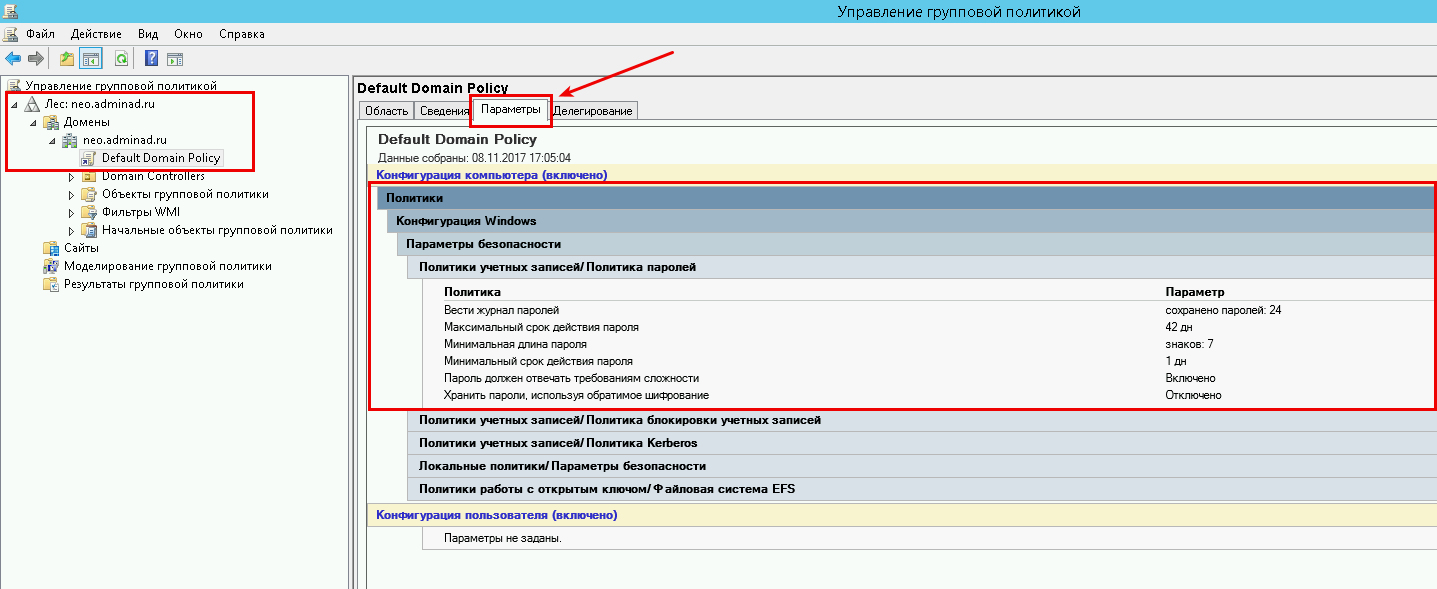
затем в блоке справа выберите вкладку «Параметры».
Во вкладке «Параметры» откройте вкладки «Политики» -> «Конфигурация Windows» -> «Параметры безопасности» -> «Политика учетных записей / Политика паролей»
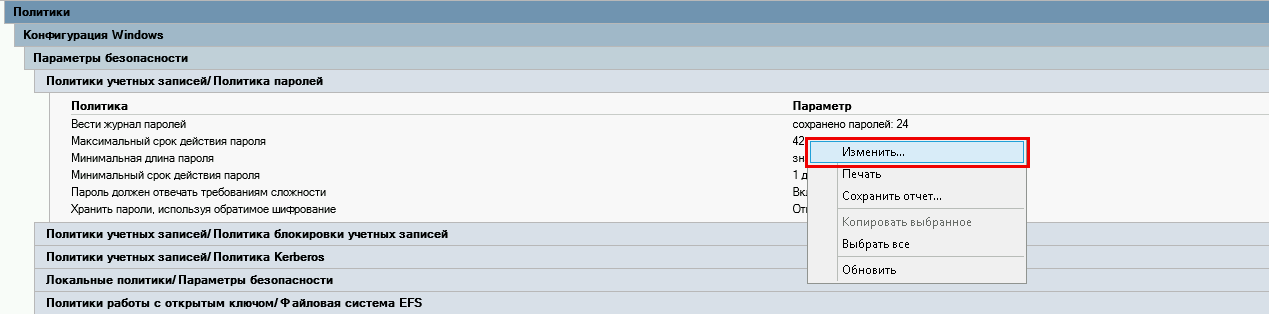
В списке «Политика учетных записей / Политика паролей» нажмите правой кнопкой мыши на «Максимальный срок действия пароля 42 дня» и в контекстном меню выберите «Изменить»
Перед Вами откроется «Редактор управления групповыми политиками»
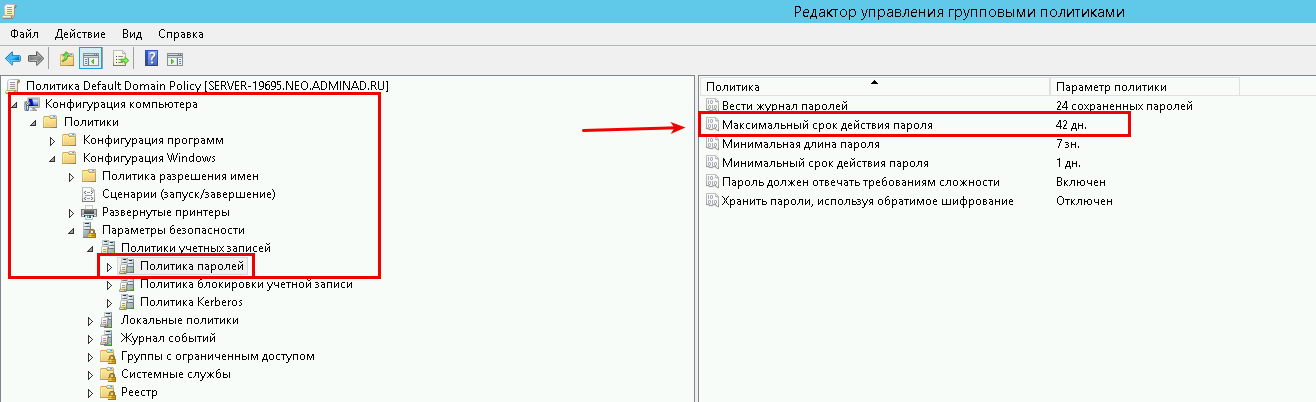
В этом редакторе, в блоке слева откройте дерево «Конфигурация компьютера» -> «Политики» -> «Конфигурация Windows» -> «Параметры безопасности» -> «Политики учетных записей» -> «Политика паролей»
В блоке справа откройте «Максимальный срок действия пароля 42 дня»
В открывшемся окне в значении «Срок истечения действия пароля» введите 0 или нужное Вам значение
Значение «0» — говорит системе о том что — функция «Срок истечения действия пароля» — отключена.
В таком режиме срок действия пароля — бесконечный.
И нажмите кнопку «Применить» , готово.
Содержание
- Configuring Password Policies with Windows Server 2016
- What is Password Policy?
- How to Configure Password Policies with Windows Server 2016?
- What is Enforce Password History?
- What is Maximum password Age?
- What is the Minimum Password Age?
- What is the Minimum Password Length?
- What are Password Complexity Requirements?
- Store Passwords Using Reversible Encryption
- Password must meet complexity requirements
- Reference
- Possible values
- Best practices
- Location
- Default values
- Operating system version differences
- Security considerations
- Vulnerability
- Countermeasure
- Potential impact
- Раздельные (гранулированные) политики паролей Fine-Grained Password Policy в Active Directory
- Множественные политики управления паролями — Fine-Grained Password Policies
- Настройка Password Settings Policy в Active Directory
- Настройка политики паролей PSO с помощью PowerShell
- Passwords technical overview
- How passwords are stored in Windows
- Passwords stored as OWF
- Passwords stored in Active Directory
- Passwords stored in the local SAM
- Cached credentials
- How passwords work in Windows
- How passwords are used in Windows
- Strong passwords
- Passphrases in Windows
- Local password policies available in Windows
- Fine-grained password policy available through Active Directory Domain Services (AD DS)
Configuring Password Policies with Windows Server 2016
What is Password Policy?
Password policy is the policy which is used to restrict some credentials on windows server 2016 and previous versions of Server 2012, 2008 and 2003.
A password policy is a set of rules designed to enhance computer security by encouraging users to employ strong passwords and use them properly. A password policy is often part of an organisation’s official regulations and may be taught as part of security awareness training. The password policy may either be advisory or mandated by technical means. Some governments have national authentication frameworks that define requirements for user authentication to government services, including requirements for passwords. So follow the under instructions to know how to configure password policy with windows server 2016. “Wikipedia”
How to Configure Password Policies with Windows Server 2016?
You can open up Group Policy Management Editor into three various ways.
First Method: press windows key and type control panel and now select administrative tools and then select local security policy. A new window will pop up, click account policies, Password Policy. Here you will see about six policies. If you don’t want to use the graphical way just type gpedit.msc on the RUN window then hit enter. Now go to this path. Computer Configuration/Windows Settings/Security Settings/Password Policy.
» data-medium-file=»https://www.wikigain.com/wp-content/uploads/2015/12/Local-Group-Poliy-Editor-300×171.jpg» data-large-file=»https://www.wikigain.com/wp-content/uploads/2015/12/Local-Group-Poliy-Editor.jpg» loading=»lazy» src=»http://www.wikigain.com/wp-content/uploads/2015/12/Local-Group-Poliy-Editor.jpg» alt=»Local Group Policy Editor» width=»600″ height=»342″ srcset=»https://g6k7x4j6.stackpathcdn.com/wp-content/uploads/2015/12/Local-Group-Poliy-Editor.jpg 600w, https://g6k7x4j6.stackpathcdn.com/wp-content/uploads/2015/12/Local-Group-Poliy-Editor-300×171.jpg 300w» sizes=»(max-width: 600px) 100vw, 600px»/>
Local Group Policy Editor
Second Method: If you don’t want to use the graphical way just type gpedit.msc on the RUN window then hit enter. Now go to this path. Computer Configuration>Windows Settings>Security Settings>Password Policy.
» data-medium-file=»https://www.wikigain.com/wp-content/uploads/2015/12/Group-Policy-Editor-300×180.jpg» data-large-file=»https://www.wikigain.com/wp-content/uploads/2015/12/Group-Policy-Editor.jpg» loading=»lazy» src=»http://www.wikigain.com/wp-content/uploads/2015/12/Group-Policy-Editor.jpg» alt=»Group Policy Editor» width=»471″ height=»282″ srcset=»https://g6k7x4j6.stackpathcdn.com/wp-content/uploads/2015/12/Group-Policy-Editor.jpg 471w, https://g6k7x4j6.stackpathcdn.com/wp-content/uploads/2015/12/Group-Policy-Editor-300×180.jpg 300w, https://g6k7x4j6.stackpathcdn.com/wp-content/uploads/2015/12/Group-Policy-Editor-470×280.jpg 470w» sizes=»(max-width: 471px) 100vw, 471px»/>
Group Policy Editor
Third Method: Open Server Manager and click on Tools. Scroll down until you see the GPO (Group Policy Management). Right, click on the Domain then choose Edit. Now you will see the same window as before. Go to Computer Configuration> Windows Settings> Security Settings> Password Policy.
These were three different ways that you can apply password policy on the network computers.
What is Enforce Password History?
Enforce password history is the policy that doesn’t allow the users to use the same password for many times. For example, Once your Device password is Admin, and for the next time, you can’t use this password for login on your computer. After some months or year, it may expire. When it is expired, so you must use another password. Here I have set it to 10 times. It means that I can’t use my old password less than 10 times. In ten times, I must use a different password. After 10 times, I can use my first password. For more information, look at the chart below.
» data-medium-file=»https://www.wikigain.com/wp-content/uploads/2015/12/Enforce-Password-History-rules-2-300×138.jpg» data-large-file=»https://www.wikigain.com/wp-content/uploads/2015/12/Enforce-Password-History-rules-2.jpg» loading=»lazy» src=»http://www.wikigain.com/wp-content/uploads/2015/12/Enforce-Password-History-rules-2.jpg» alt=»Enforce Password History rules» width=»600″ height=»276″ srcset=»https://g6k7x4j6.stackpathcdn.com/wp-content/uploads/2015/12/Enforce-Password-History-rules-2.jpg 600w, https://g6k7x4j6.stackpathcdn.com/wp-content/uploads/2015/12/Enforce-Password-History-rules-2-300×138.jpg 300w» sizes=»(max-width: 600px) 100vw, 600px»/>
Enforce Password History rules
What is Maximum password Age?
This security setting determines the time in days that a password can be used before the system requires the user to change it. You can set passwords to expire after several days between 1 to 999, or you can specify that passwords never expire by setting the number of days to 0 if the maximum password age is between 1 and 999 days. The minimum password age must be less than the maximum password age if the maximum password age is set to 0. The minimum password age can be any value between 0 and 998 days.
» data-medium-file=»https://www.wikigain.com/wp-content/uploads/2015/12/Maximum-Password-Age-300×148.jpg» data-large-file=»https://www.wikigain.com/wp-content/uploads/2015/12/Maximum-Password-Age.jpg» loading=»lazy» src=»http://www.wikigain.com/wp-content/uploads/2015/12/Maximum-Password-Age.jpg» alt=»Maximum Password Age» width=»602″ height=»297″ srcset=»https://g6k7x4j6.stackpathcdn.com/wp-content/uploads/2015/12/Maximum-Password-Age.jpg 602w, https://g6k7x4j6.stackpathcdn.com/wp-content/uploads/2015/12/Maximum-Password-Age-300×148.jpg 300w» sizes=»(max-width: 602px) 100vw, 602px»/>
Maximum Password Age
Note : It is a security best practice to have passwords expire every 30 to 90 days, depending on your environment. This way, an attacker has a limited amount of time to crack a user’s password and have access to your network resources.
What is the Minimum Password Age?
The minimum password age must be less than the maximum password age unless the maximum password age is set to 0, indicating that passwords will never expire. If the maximum password age is set to 0, the minimum password age can be set to any value between 0 to 998. It’s vital that you have to use the minimum password age. If you don’t use, the user may cycle the password history till they get their old favourite password. If you set the minimum password age, so they will not change their password quickly.
» data-medium-file=»https://www.wikigain.com/wp-content/uploads/2015/12/Minimum-Password-Age-300×159.jpg» data-large-file=»https://www.wikigain.com/wp-content/uploads/2015/12/Minimum-Password-Age.jpg» loading=»lazy» src=»http://www.wikigain.com/wp-content/uploads/2015/12/Minimum-Password-Age.jpg» alt=»Minimum Password Age» width=»601″ height=»318″ srcset=»https://g6k7x4j6.stackpathcdn.com/wp-content/uploads/2015/12/Minimum-Password-Age.jpg 601w, https://g6k7x4j6.stackpathcdn.com/wp-content/uploads/2015/12/Minimum-Password-Age-300×159.jpg 300w» sizes=»(max-width: 601px) 100vw, 601px»/>
Minimum Password Age
What is the Minimum Password Length?
This is security setting determines the least number of characters that a password for a user account may contain. You can set a value of between 1 and 14 characters, or establish that no password is required by setting the number of characters to 0. Here I have set up to 8 characters. Mostly you see this policy on websites or social accounts.
» data-medium-file=»https://www.wikigain.com/wp-content/uploads/2015/12/Minimum-Password-Length-300×162.jpg» data-large-file=»https://www.wikigain.com/wp-content/uploads/2015/12/Minimum-Password-Length.jpg» loading=»lazy» src=»http://www.wikigain.com/wp-content/uploads/2015/12/Minimum-Password-Length.jpg» alt=»Minimum Password Length» width=»600″ height=»323″ srcset=»https://g6k7x4j6.stackpathcdn.com/wp-content/uploads/2015/12/Minimum-Password-Length.jpg 600w, https://g6k7x4j6.stackpathcdn.com/wp-content/uploads/2015/12/Minimum-Password-Length-300×162.jpg 300w» sizes=»(max-width: 600px) 100vw, 600px»/>
Minimum Password Length
What are Password Complexity Requirements?
If this policy is enabled, passwords must meet the following minimum requirements.
Password Must Meet Complexity Requirements
» data-medium-file=»https://www.wikigain.com/wp-content/uploads/2015/12/Password-Must-Meet-Complexity-Requirements-300×165.jpg» data-large-file=»https://www.wikigain.com/wp-content/uploads/2015/12/Password-Must-Meet-Complexity-Requirements.jpg» loading=»lazy» src=»http://www.wikigain.com/wp-content/uploads/2015/12/Password-Must-Meet-Complexity-Requirements.jpg» alt=»Password Must Meet Complexity Requirements» width=»600″ height=»329″ srcset=»https://g6k7x4j6.stackpathcdn.com/wp-content/uploads/2015/12/Password-Must-Meet-Complexity-Requirements.jpg 600w, https://g6k7x4j6.stackpathcdn.com/wp-content/uploads/2015/12/Password-Must-Meet-Complexity-Requirements-300×165.jpg 300w» sizes=»(max-width: 600px) 100vw, 600px»/>
Password Must Meet Complexity Requirements
It’s beneficial and restricts vulnerabilities. You can see this policy when you create an Apple ID.
Store Passwords Using Reversible Encryption
This policy provides support for applications that use protocols that require knowledge of the user’s password for authentication purposes. Storing passwords using reversible encryption is essentially the same as storing plaintext versions of the passwords. For this reason, this policy should never be enabled unless application requirements outweigh the need to protect password information. I should tell you when you enabled this option; it will encrypt the password and no-one can access your password very easily.
Store Passwords Using Reversible Encryption
» data-medium-file=»https://www.wikigain.com/wp-content/uploads/2015/12/Store-Passwords-Using-Reversible-Encryption-300×148.jpg» data-large-file=»https://www.wikigain.com/wp-content/uploads/2015/12/Store-Passwords-Using-Reversible-Encryption.jpg» loading=»lazy» src=»http://www.wikigain.com/wp-content/uploads/2015/12/Store-Passwords-Using-Reversible-Encryption.jpg» alt=»Store Passwords Using Reversible Encryption» width=»603″ height=»297″ srcset=»https://g6k7x4j6.stackpathcdn.com/wp-content/uploads/2015/12/Store-Passwords-Using-Reversible-Encryption.jpg 603w, https://g6k7x4j6.stackpathcdn.com/wp-content/uploads/2015/12/Store-Passwords-Using-Reversible-Encryption-300×148.jpg 300w» sizes=»(max-width: 603px) 100vw, 603px»/>
Store Passwords Using Reversible Encryption
It was all about how to configure password policies with windows server 2016. It does not only work on windows server 2016 but also work on later versions. Thanks for being with us.
Источник
Password must meet complexity requirements
Applies To: Windows Vista, Windows Server 2008, Windows 7, Windows 8.1, Windows Server 2008 R2, Windows Server 2012 R2, Windows Server 2012, Windows 8
This security policy reference topic for the IT professional describes the best practices, location, values, and security considerations for this policy setting.
Reference
The Passwords must meet complexity requirements policy setting determines whether passwords must meet a series of guidelines that are considered important for a strong password. Enabling this policy setting requires passwords to meet the following requirements:
Passwords may not contain the user’s samAccountName (Account Name) value or entire displayName (Full Name value). Both checks are not case sensitive.
The samAccountName is checked in its entirety only to determine whether it is part of the password. If the samAccountName is less than three characters long, this check is skipped.
The displayName is parsed for delimiters: commas, periods, dashes or hyphens, underscores, spaces, pound signs, and tabs. If any of these delimiters are found, the displayName is split and all parsed sections (tokens) are confirmed to not be included in the password. Tokens that are less than three characters are ignored, and substrings of the tokens are not checked. For example, the name «Erin M. Hagens» is split into three tokens: «Erin», «M», and «Hagens». Because the second token is only one character long, it is ignored. Therefore, this user could not have a password that included either «erin» or «hagens» as a substring anywhere in the password.
The password contains characters from three of the following categories:
Uppercase letters of European languages (A through Z, with diacritic marks, Greek and Cyrillic characters)
Lowercase letters of European languages (a through z, sharp-s, with diacritic marks, Greek and Cyrillic characters)
Base 10 digits (0 through 9)
Any Unicode character that is categorized as an alphabetic character but is not uppercase or lowercase. This includes Unicode characters from Asian languages.
Complexity requirements are enforced when passwords are changed or created.
The rules that are included in the Windows Server password complexity requirements are part of Passfilt.dll, and they cannot be directly modified.
Enabling the default Passfilt.dll may cause some additional Help Desk calls for locked-out accounts because users might not be used to having passwords that contain characters other than those found in the alphabet. However, this policy setting is liberal enough that all users should be able to abide by the requirements with a minor learning curve.
Additional settings that can be included in a custom Passfilt.dll are the use of non–upper-row characters. Upper-row characters are those that are typed by holding down the SHIFT key and typing any of the digits from 1 through 10.
This policy setting is supported on versions of Windows that are designated in the Applies To list at the beginning of this topic.
Possible values
Best practices
Set Passwords must meet complexity requirements to Enabled. This policy setting, combined with a minimum password length of 8, ensures that there are at least 218,340,105,584,896 different possibilities for a single password. This makes a brute force attack difficult, but still not impossible.
The use of ALT key character combinations can greatly enhance the complexity of a password. However, requiring all users in an organization to adhere to such stringent password requirements can result in unhappy users and an extremely busy Help Desk. Consider implementing a requirement in your organization to use ALT characters in the range from 0128 through 0159 as part of all administrator passwords. (ALT characters outside of this range can represent standard alphanumeric characters that do not add additional complexity to the password.)
Passwords that contain only alphanumeric characters are easy to compromise by using publicly available tools. To prevent this, passwords should contain additional characters and meet complexity requirements.
Location
GPO_nameВ Computer ConfigurationWindows SettingsSecurity SettingsAccount PoliciesPassword Policy
Default values
The following table lists the actual and effective default policy values for the most recent supported versions of Windows. Default values are also listed on the policy’s property page.
| Server type or Group Policy Object (GPO) | Default value |
|---|---|
| Default domain policy | Enabled |
| Default domain controller policy | Enabled |
| Stand-alone server default settings | Disabled |
| Domain controller effective default settings | Enabled |
| Member server effective default settings | Enabled |
| Effective GPO default settings on client computers | Disabled |
Operating system version differences
There are no differences in the way this policy setting works between supported versions of Windows.
Security considerations
This section describes how an attacker might exploit a feature or its configuration, how to implement the countermeasure, and the possible negative consequences of countermeasure implementation.
Vulnerability
Passwords that contain only alphanumeric characters are extremely easy to discover with several publicly available tools.
Countermeasure
Configure the Passwords must meet complexity requirements policy setting to Enabled and advise users to use a variety of characters in their passwords.
When combined with a Minimum password length of 8, this policy setting ensures that the number of different possibilities for a single password is so great that it is difficult (but not impossible) for a brute force attack to succeed. (If the Minimum password length policy setting is increased, the average amount of time necessary for a successful attack also increases.)
Potential impact
If the default password complexity configuration is retained, additional Help Desk calls for locked-out accounts could occur because users might not be accustomed to passwords that contain non-alphabetical characters, or they might have problems entering passwords that contain accented characters or symbols on keyboards with different layouts. However, all users should be able to comply with the complexity requirement with minimal difficulty.
If your organization has more stringent security requirements, you can create a custom version of the Passfilt.dll file that allows the use of arbitrarily complex password strength rules. For example, a custom password filter might require the use of non-upper-row symbols. (Upper-row symbols are those that require you to press and hold the SHIFT key and then press any of the digits between 1 and 0.) A custom password filter might also perform a dictionary check to verify that the proposed password does not contain common dictionary words or fragments.
The use of ALT key character combinations can greatly enhance the complexity of a password. However, such stringent password requirements can result in additional Help Desk requests. Alternatively, your organization could consider a requirement for all administrator passwords to use ALT characters in the 0128–0159 range. (ALT characters outside of this range can represent standard alphanumeric characters that would not add additional complexity to the password.)
Источник
Раздельные (гранулированные) политики паролей Fine-Grained Password Policy в Active Directory
Раздельные (гранулированные) политики паролей Fine-Grained Password Policies (FGPP) позволяют создать отдельные политики паролей для определенных пользователей или групп. Множественные политики паролей FGPP доступны, начиная с версии Active Directory в Windows Server 2008. В предыдущих версиях AD 2000 можно было создать только одну политику паролей в каждом домене (в рамках Default Domain Policy).
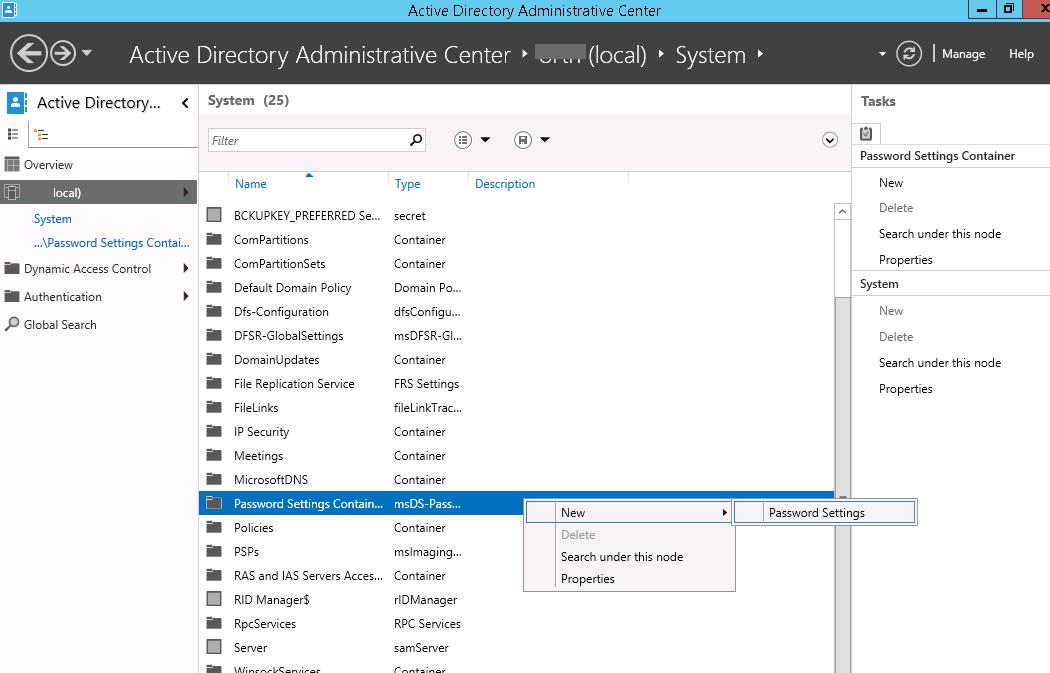
В этой статье мы покажем, как создать и настроить раздельные политики управления паролями (Password Setting Objects) в домене.
Множественные политики управления паролями — Fine-Grained Password Policies
Fine-Grained Password Policies позволяют администратору создать в одном домене несколько специальных политик управления паролями (Password Settings Policy — PSO). В PSO объектах задаются требования к паролям (длина, сложность, история) и настройки блокировки учетных записей. Политики PSO можно назначать на конкретных пользователей или группы, но не на контейнеры (OU) Active Directory. Если к пользователю/группе привязана политика PSO, то настройки парольной политики из GPO Default Domain Policy к нему более не применяются.
С помощью политик FGPP можно задать более высокие требования на длину и сложность пароля для учетных записей администраторов, сервисных учетных записей или пользователей, имеющих внешний доступ в домена (через VPN или DirectAccess).
Основные требования для использования множественных политик паролей FGPP в домене:
Настройка Password Settings Policy в Active Directory
Вы можете создавать и редактировать парольные политики Fine-Grained Password Policies из графического интерфейса консоли Active Directory Administration Center (ADAC).
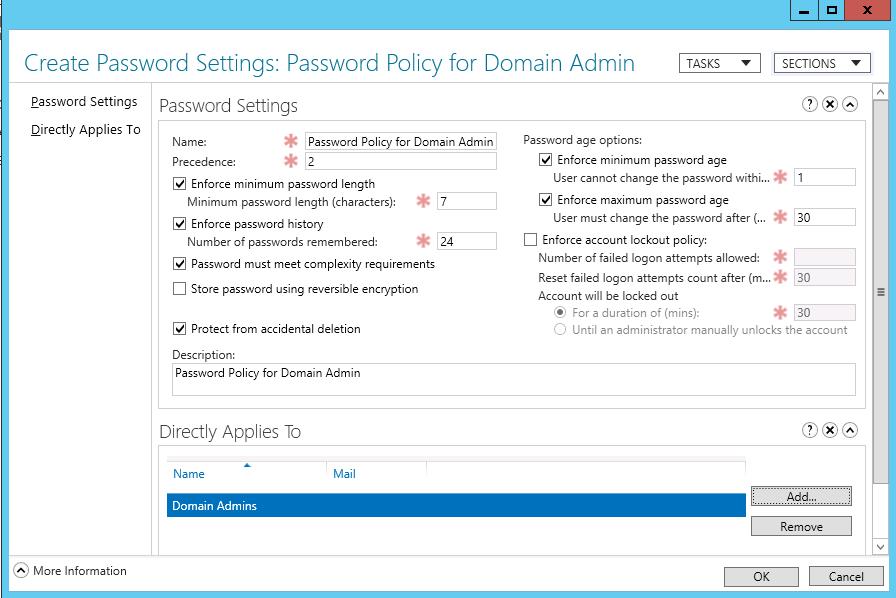
В данном примере мы покажем, как создать и назначить отдельную парольную политику на доменную группу Domain Admins.
Укажите имя политики паролей (например, Password Policy for Domain Admins) и задайте настройки. Все поля стандартные: минимальная длина и сложность пароля, количество хранимых паролей в истории, частота смены пароля, параметры блокировки при неправильном введении пароля и т.д.
Обратите внимание на атрибут Precedence. Данный атрибут определяет приоритет данной политики паролей. Если на пользователя AD действуют несколько политик PSO, то к нему будет применена политика с меньшим значением в поле Precedence.
Затем в секции Direct Applies To добавьте группы или пользователей, на которых должна действовать политика (в этом примере Domain Admins). Сохраните политику.
С этого момента данная парольная политика будет применяться на всех членов группы Domain Admins.
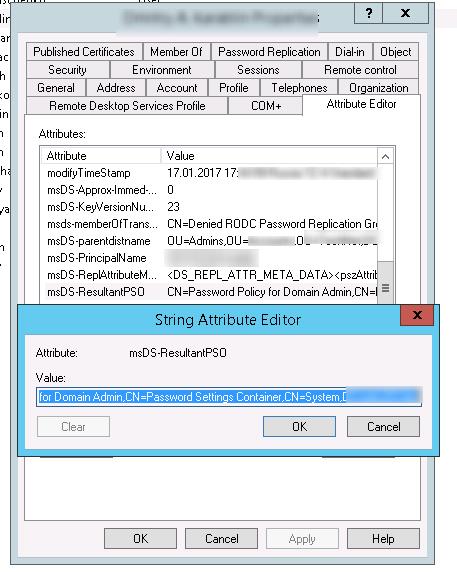
Запустите консоль Active Directory Users and Computers (с установленной опцией Advanced Features) и откройте свойства любого пользователя из группы Domain Admins. Перейдите на вкладку редактора атрибутов (Attribute Editor) и в поле Filter выберите опцию Constructed.
Найдите атрибут пользователя msDS-ResultantPSO. В этом атрибуте указывается действующая на пользователя парольная политика FGPP ( CN=Password Policy for Domain Admins,CN=Password Settings Container,CN=System,DC=winitpro,DC=ru ).
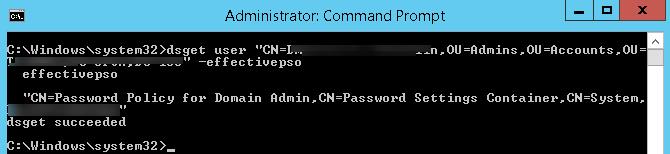
Также действующую политику PSO для пользователя можно получить с помощью dsget:
dsget user «CN=Dmitriy,OU=Admins,DC=winitpro,DC=ru» –effectivepso
Настройка политики паролей PSO с помощью PowerShell
Вы можете управлять политиками паролей PSO с помощью PowerShell (на компьютере должен быть установлен модуль RSAT-AD-PowerShell).
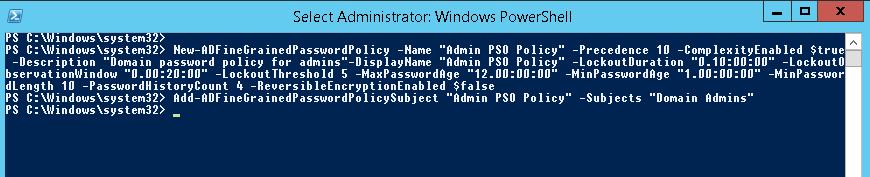
Для создания новой политики используется командлет New-ADFineGrainedPasswordPolicy:
Теперь можно назначить политику на группу пользователей:
Чтобы изменить настройки политики PSO:
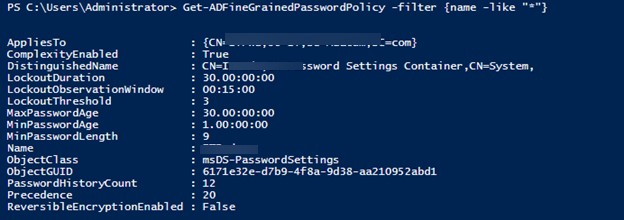
Вывести все политики FGPP в домене:
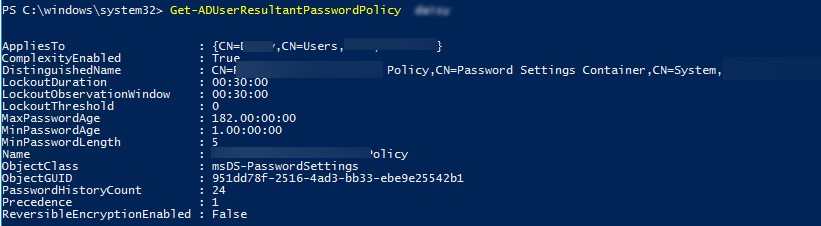
Для получения результирующей парольной политики, которая применяется к конкретному пользователю используется команды. Имя политики PSO, которая действует на пользователя указано в поле Name.
Список политик PSO, назначенных на группу Active Directory, можно вывести с помощью командлета:
Чтобы вывести настройки политики паролей по-умолчанию из Default Domain Policy, выполните команду:
Источник
Passwords technical overview
Applies to: Windows Server 2022, Windows Server 2019, Windows Server 2016, Windows 10, Windows Server 2012 R2, Windows 8.1, Windows Server 2012, Windows 8, Windows 7, Windows Server 2003, Windows Server 2008, Windows Server 2008 R2, Windows Vista
This topic for the IT professional explains how Windows implements passwords in versions of Windows beginning with Windows Server 2012 and Windows 8.1. It also discusses strong passwords, passphrases, and password policies.
How passwords are stored in Windows
This article provides information about the storage of passwords «at rest».
Windows represents passwords in 256-character UNICODE strings, but the logon dialog box is limited to 127 characters. Therefore, the longest possible password has 127 characters. Programs such as services can use longer passwords, but they must be set programmatically.
The Windows operating system stores passwords many different ways for different purposes.
Passwords stored as OWF
For use in Windows networking, including Active Directory domains, the password is stored two different ways by default: as the LAN Manager one-way function (LM OWF) and as the NT OWF. «One-way function» is a term that denotes a one-way mathematical transformation of data. The data that is being transformed can only be converted through encryption one way and cannot be reversed. The most common type of one-way function in use is a cryptographic hash. A hash is a small set of data that is mathematically tied to some larger set of data from which the hash is calculated. If the larger set of data is changed, the hash also changes. Hashes are useful, for example, as a checksum to verify that data has not been modified in transmission. A cryptographic hash is a hash that fulfills certain properties. A cryptographic hash must, for instance, be created in such a way that it is mathematically infeasible in a reasonable amount of time to infer the larger set of data from only the hash. Likewise, it is mathematically infeasible to find two sets of large data that generate the same hash.
There are many different types of one-way functions. All hash functions are, by definition, one-way functions. However, ordinary cryptographic functions that are typically reversible can also be used to create a one-way function. This can be done by swapping the data and the key in a cryptographic function and encrypting the fixed value (the key) by using the data as the key. This is how the LM hash is computed. The LM hash is computed as follows:
The LM OWF algorithm is included in Windows for backward compatibility with software and hardware that cannot use newer algorithms.
The NT hash is simply a hash. The password is hashed by using the MD4 algorithm and stored. The NT OWF is used for authentication by domain members in both Windows NT 4.0 and earlier domains and in Active Directory domains.
Neither the NT hash nor the LM hash is salted. Salting is a process that combines the password with a random numeric value (the salt) before computing the one-way function.
Passwords stored in Active Directory
Passwords at rest are stored in several attributes of the Active Directory database (NTDS.DIT file). These attributes are listed in the following table:
The storage of LM hashes is disabled by default since Windows Vista and Windows Server 2008.
When stored in the DIT file, the NT hash is protected by two layers of encryption. In Windows Server 2016/Windows 10 and later versions, it is first encrypted with DES for backwards compatibility and then with CNG BCrypt AES-256 (see CNG BCRYPT_AES_ALGORITHM). Previous Windows versions encrypt NT hashes using two layers of DES + RC4 encryption.
Passwords stored in the local SAM
On domain members and workstations, local user account password hashes are stored in a local Security Account Manager (SAM) Database located in the registry. They are encrypted using the same encryption and hashing algorithms as Active Directory. The passwords in the supplementalCredentials attribute for local user accounts are also stored in the local SAM Database since Windows Server 2016.
Cached credentials
Windows also stores a password verifier on domain members when a domain user logs on to that domain member. This verifier can be used to authenticate a domain user if the computer is not able to access the domain controller. The password verifier is also commonly called a cached credential. It is computed by taking the NT hash, concatenating the user name to it, and then hashing the result by using the MD4 hash function.
How passwords work in Windows
In Windows and many other operating systems, one method for authenticating a user’s identity is to use a secret passphrase or password.
We recommend using secure multi-factor authentication such as Smart Card, FIDO, and Windows Hello for Business. However, password authentication is still required in some scenarios.
Securing your network environment requires that strong passwords be used by all users. This helps avoid the threat of a malicious user guessing a weak password, whether through manual methods or by using tools, to acquire the credentials of a compromised user account. This is especially true for administrative accounts. When you change a complex password regularly, it reduces the likelihood of a successful password attack.
Password policy settings control the complexity and lifetime of passwords. Password policies affect Windows passwords, not necessarily feature passwords.
Users’ ability to modify their passwords is governed by the password policies and the available interfaces. For example, through the Secure Desktop, users can change their password at any time based upon the password policies administered by the system administrator or domain administrator. Features such as Windows Vault, BitLocker, and Encrypting File System allow users to modify passwords specific to that feature.
How passwords are used in Windows
When a user logs on, the password the user types is converted into both types of one-way functions and held in memory by the Local Security Authority Subsystem Service (LSASS) process. If the user using a local account for authentication, the NT OWF is compared against the locally stored NT hash, and if the two match, the user is logged on. If the user is authenticating against an Active Directory domain by using a host name to access a resource, the NT hash is used in a Kerberos logon against the Key Distribution Center (KDC), which is typically the domain controller.
Kerberos cannot be used in the following situations:
In these situations, the authentication process uses two different protocols, called LAN Manager and NTLM. The process starts with the client requesting a challenge from the authentication server. After the challenge is received, the client computes a response to this challenge. This is done by first padding the two hashes of the password with null values to 168 bits. The 168 bits of each hash are then split into three 56-bit DES keys. The six DES keys are then used to encrypt the challenge. The three cipher texts produced by using the LM hash are concatenated and become the LAN Manager response. The three cipher texts produced by using the NT hash are concatenated and become the NTLM response.
The functions used to compute the response may be modified by the LM Compatibility Level setting in the Network security: LAN Manager authentication level Group Policy setting. If that value is set to 1 or lower, the client will send the original LAN Manager and NTLM responses. If it is set to 2, only the NTLM response is sent. If it is set to 3 or higher, a new version of both protocols is used. The NTLM version is called NTLMv2. The LAN Manager version is often referred to as LMv2. Both protocols use the NT hash to compute the response, and both use a client-side challenge, either instead of or in addition to the server challenge. In addition, if the LM Compatibility Level setting is set to 1 or higher, the NTLM response is time-stamped to help prevent replay attacks. For information about the LM Compatibility Level setting, see Network security: LAN Manager authentication level.
Strong passwords
Passwords provide the first line of defense against unauthorized access to your organization. Beginning with Windows Server 2003, Windows checks the complexity of the password for the Administrator account during setup of the operating system. If the password is blank or does not meet complexity requirements, the Windows Setup dialog box prompts you to create a strong password for the Administrator account. If you leave this password blank, you will not be able to access this account over the network.
Weak passwords provide attackers with easy access to your computers and network, while strong passwords are considerably more difficult to crack. The following table compares weak and strong passwords.
| Weak password | Strong password |
|---|---|
| Blank | Is at least seven characters long |
| Contains easily discoverable or known information, such as user name or domain name | Contains «secret» or random information |
| Is similar to previous passwords | Is significantly different from previous passwords |
| Contains a complete dictionary word | Contains a mix of the following characters:
— Symbols including spaces |
An example of a strong password is J*p2leO4>F.
A password can meet most of the criteria of a strong password but still be rather weak. For example, Hello2U! is a relatively weak password even though it meets most of the criteria for a strong password and also meets the complexity requirements of password policy. H!elZl2o is a strong password because the dictionary word is interspersed with symbols, numbers, and other letters. It is important to educate users about the benefits of using strong passwords and to teach them how to create passwords that are actually strong.
You can create passwords that contain characters from the extended ANSI character set. Using extended ANSI characters increases the number of characters that you can choose when you create a password. As a result, it might take more time for password-cracking software to crack passwords that contain these extended ANSI characters than it does to crack other passwords. Before using extended ANSI characters in your password, test them thoroughly to make sure that passwords containing extended ANSI characters are compatible with the applications that your organization uses. Be especially cautious about using extended ANSI characters in passwords if your organization uses several different operating systems. For example, these systems may standardize in ISO-8859-15. The actual protocol implementation on Windows often use UNICODE or UTF8 rather than actual ANSI encoding.
Examples of passwords that contain characters from the extended ANSI character set are kUµ!¶0o and Wf©$0k#»g¤5ªrd.
Passphrases in Windows
A passphrase is a different form of token-based password in which the tokens are words instead of symbols from a character set. An example of a passphrase is a sentence that contains special characters, numerals, uppercase letters, and lowercase letters. The key differences between passphrases and passwords are:
Passphrases that conform to the character limit as set in the policy are generally, more difficult to crack than passwords because they contain more characters. It is the LM and NT hash that stores the password or passphrase, and the LM hash is the weaker of the two.
There are several ways to ensure the LM hash is not stored; one of them is to use passwords or passphrases longer than 14 characters. You can also use the Network security: Do not store LAN Manager hash value on next password change Group Policy setting. Using this policy setting globally turns off storage LM hashes for all accounts. The change will take effect the next time the password is changed. Because the policy’s effect is not immediate, you will not immediately notice any potential interoperability problems caused by not storing LM hashes.
Local password policies available in Windows
You can implement a password policy setting that enforces password complexity requirements. For more information about this policy setting, see Password must meet complexity requirements. For information about how to apply a password policy, see Apply or Modify a Password Policy. For information about all available password policy settings, see Password Policy.
Fine-grained password policy available through Active Directory Domain Services (AD DS)
Beginning with Windows Server 2008, you can use fine-grained password policies to specify multiple password policies and apply different password restrictions and account lockout policies to different sets of users within a single domain. For example, to increase the security of privileged accounts, you can apply stricter settings to the privileged accounts and then apply less strict settings to the accounts of other users. Or in some cases, you may want to apply a special password policy for accounts whose passwords are synchronized with other data sources.
To store fine-grained password policies, two new object classes exist in the AD DS schema:
For more information about these policies, see AD DS: Fine-Grained Password Policies.
Источник