Posted by
on April 27, 2016
By default in Windows Server 2016 remote desktop is disabled.
Here we cover how to turn on and enable remote desktop protocol (RDP).
Note: In Windows Server 2016 Essentials edition, remote desktop is already enabled by default so you will not need to manually do this.
Remote desktop can be enabled through the graphical user interface (GUI) with the following easy steps.
Allowing Remote Desktop
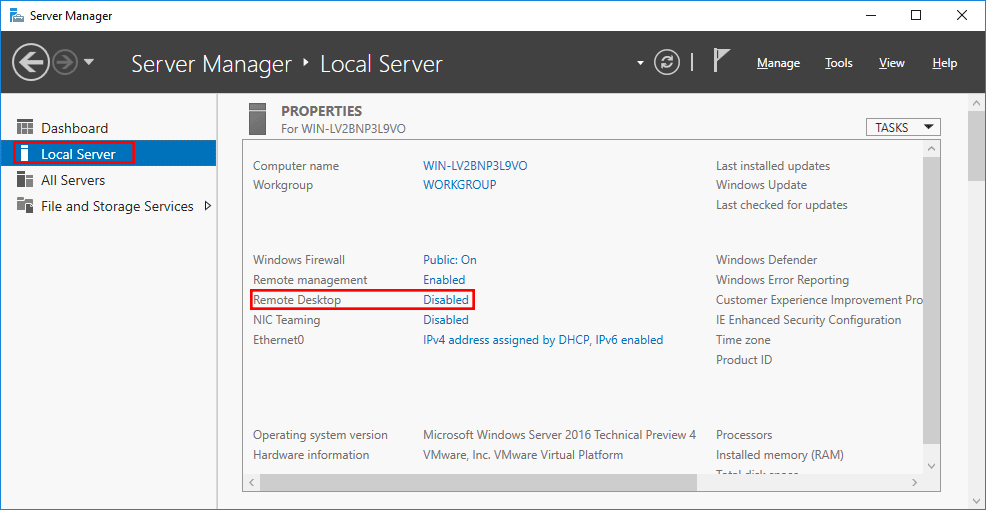
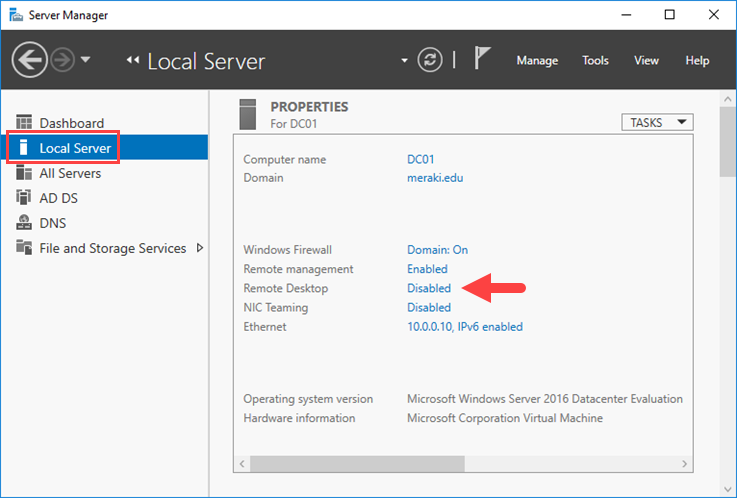
- Open Server Manager. By default Server Manager will open when you log in to the GUI, otherwise you can select it from the task bar.
- Within the Server Manager window, select Local Server from the left hand side. You may need to wait a little for it to detect the current state of your system. You should see that Remote Desktop is listed as Disabled as shown below.
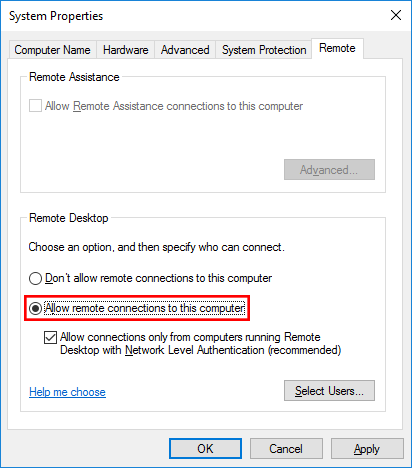
- Click on the Disabled text which will open the System Properties window in the Remote tab.
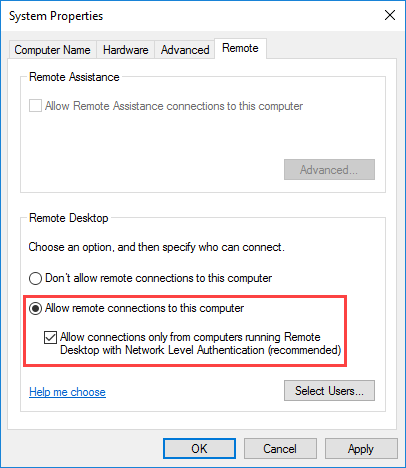
- From the System Properties window, select “Allow remote connections to this Computer” as shown below.
Tip: You can also open the System Properties window shown above by entering “SystemPropertiesRemote” into a Command Prompt or PowerShell terminal.
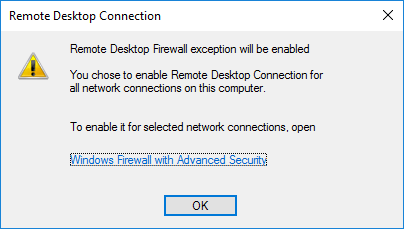
- Once you select “Allow remote connections to this computer” the below warning message will appear, advising that this will create the required firewall rules in Windows firewall to allow remote desktop traffic in from any source address, select OK to proceed.
- At this point you can optionally click the “Select Users…” button to define specific users or groups that have permission to connect via remote desktop. Select the OK button to close out of the System Properties window and enable remote desktop.
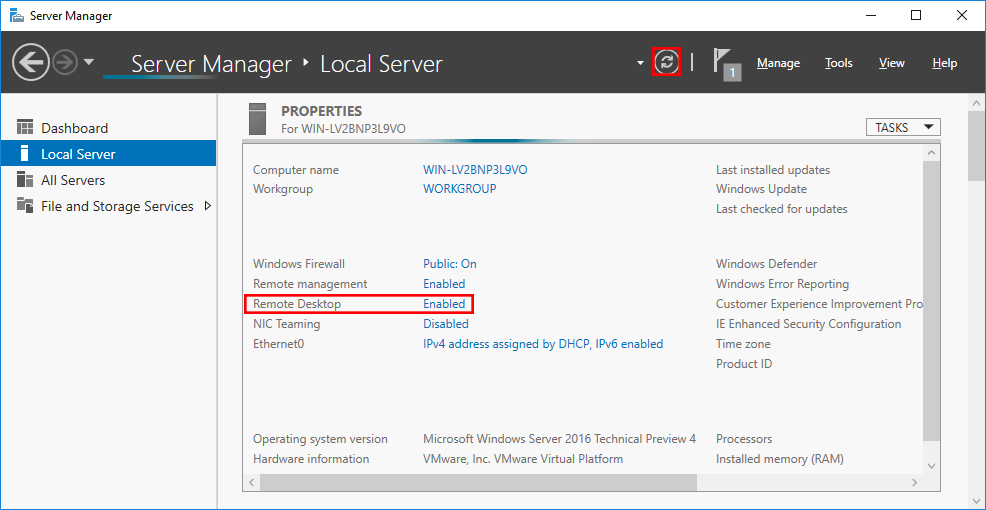
- Back in Server Manager, Remote Desktop may still show as Disabled until you refresh the view. After clicking the refresh button as highlighted below, the status should update to Enabled.
That’s it, remote desktop should now be ready to use!
Summary
By default Windows Server 2016 sets external remote desktop access to disabled as a security measure, we can easily optionally enable it from within the server console to everyone or a specific set of users or groups.
Remote Desktop Protocol (RDP) is a Microsoft-proprietary remote access protocol that is used by Windows systems administrators to manage Windows Server systems remotely. What sets RDP apart from, say, Windows PowerShell or Secure Shell (SSH) remoting is the presence of the full graphical desktop, as shown in Figure 1.
MORE: Best Remote Access Software and Solutions
By default, the RDP server component listens for incoming connections on TCP port 3389 by default, although this can be changed by the administrator for security reasons.
To be sure, Microsoft’s current push is for admins to reduce their reliance upon RDP and instead (a) deploy Windows Servers in Server Core or Nano mode; and (b) employ Windows PowerShell command-line remote administration instead of RDP.
Microsoft’s justification for this advice is two-fold:
- A GUI layer consumes unnecessary system resources
- A GUI layer broadens the attack surface of your servers
Regardless, many admins are accustomed to RDP-based remote administration, and seek to do so even in the newly released Windows Server 2016 operating system. Let’s learn how to enable RDP in Server 2016 (tl;dr: the process is identical to Windows Server 2012 R2).
Server Manager
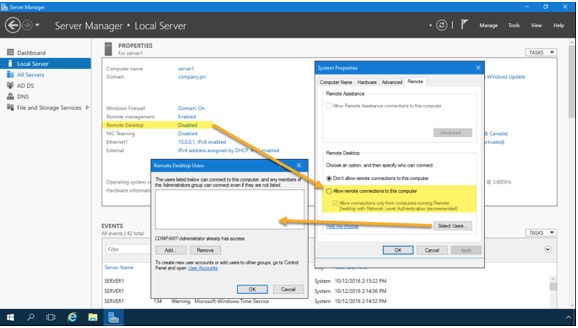
Open the Server Manager console, navigate to the Local Server node, and click the Remote Desktop hyperlink as shown in Figure 2.
The Remote Desktop hyperlink is simply a shortcut to the System Properties sheet from the System Control Panel item. Select Allow remote connections to this computer, and optionally enable Allow connections only from computers running Remote Destkop with Network Level Authentication (recommended).
Network Level Authentication (NLA) protects Windows Server against denial-of-service (DoS) attacks by requiring authentication to take place before any graphical session is established by the server. NLA also conserves server system resources.
Windows PowerShell
From a lower-level perspective, incoming RDP connections are enabled on a server through two Registry values and a Windows Firewall rule.
Open an elevated Windows PowerShell session and run the following commands. This first one creates the fDenyTSConnections value and sets it to 0 (off). This makes sense, because we don’t want to deny Terminal Services (TS) connections.
New-ItemProperty -Path ‘HKLM:SystemCurrentControlSetControlTerminal Server’ -Name ‘fDenyTSConnections’ -Value 0 -PropertyType dword -Force
The next command creates and enables the UserAuthentication (Network Layer Authentication) value; NLA is a good idea and you should consider enabling it by default on your servers.
New-ItemProperty -Path ‘HKLM:SystemCurrentControlSetControlTerminal ServerWinStationsRDP-Tcp’ -Name ‘UserAuthentication’ -Value 1 -PropertyType dword -Force
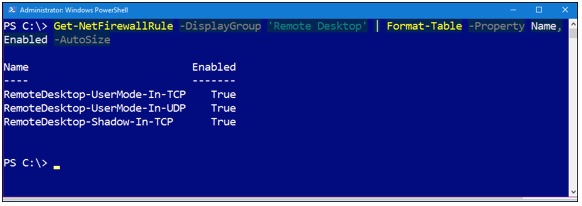
The next command enables the predefined «Remote Desktop» Windows Firewall rule. We can then invoke the Get-NetFirewallRule PowerShell cmdlet to verify as shown in Figure 3.
Enable-NetFirewallRule -DisplayGroup ‘Remote Desktop’
Group Policy
The chances are good that you want to standardize RDP behavior across all your infrastructure servers. Therefore, we turn to Group Policy to accomplish this goal.
Start by creating, linking and scoping a new Group Policy Object (GPO) that targets the servers that should share RDP server settings.
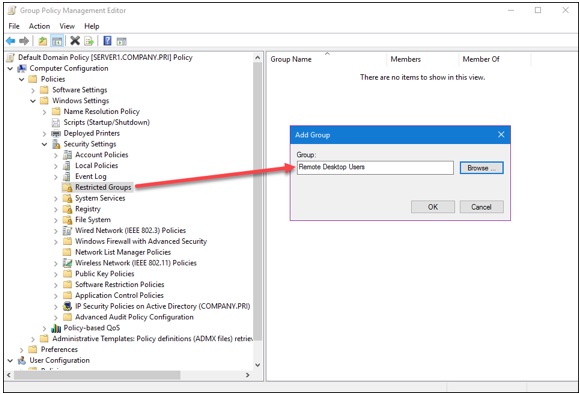
Next, navigate to the following Group Policy path and add a new Restricted Groups entry (shown in Figure 4):
Computer ConfigurationPoliciesWindows SettingsSecurity SettingsRestricted Groups
You can customize the membership in the servers’ built-in Remote Desktop Users group; members of this group can establish RDP sessions to the server. Note that the local Administrators group (and, by extension, the Domain Admins global group) is automatically granted this privilege in Active Directory.
The following three Group Policy settings govern:
- Windows Firewall incoming RDP exceptions
- User right to establish RDP sessions
- Requiring NLA
Computer ConfigurationAdministrative TemplatesNetworkNetwork ConnectionsWindows FirewallDomain ProfileWindows Firewall: Allow Inbound Remote Desktop exceptions
Computer ConfigurationAdministrative TemplatesWindows ComponentsRemote Desktop ServicesRemote Desktop Session HostConnectionsAllow user to connect remotely by using Remote Desktop Services
Computer ConfigurationAdministrative TemplatesWindows ComponentsRemote Desktop ServicesRemote Desktop Session HostSecurityRequire user authentication for remote connections by using NLA
Creating the Client Connection
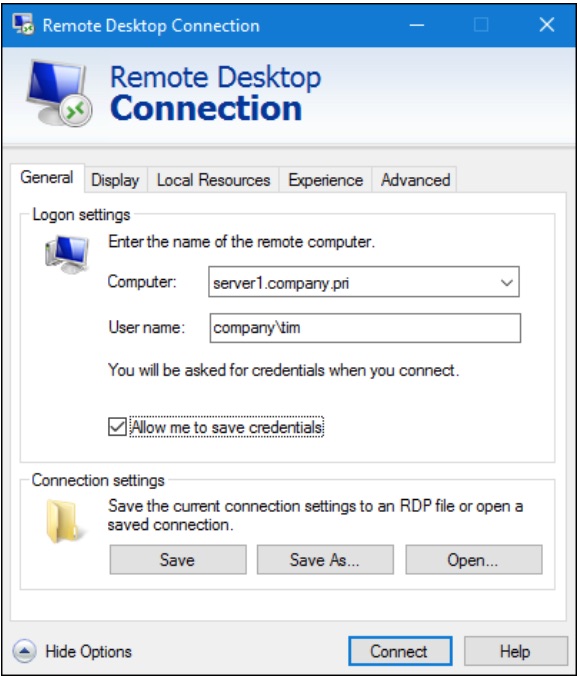
Windows Client and Windows Server both include the Microsoft RDP client, called Remote Desktop Connection. My favorite way to invoke this tool is to:
Press WINDOWS KEY+R
Type mstsc (which stands for «Microsoft Terminal Services Client»)
Press ENTER
I show you the Remote Desktop Connection user interface in Figure 5.
What’s cool about RDP clients is that they are available for just about every desktop or mobile operating system. Here is a representative list:
- Android: Microsoft Remote Desktop
- iOS: Microsoft Remote Desktop
- Linux: rdesktop
- macOS: Microsoft Remote Desktop
- Windows Phone: Microsoft Remote Desktop
Note that Windows Server supports only two simultaneous RDP sessions at once. If you need more than that, then you’ll have to install the Remote Desktop Services (RDS) Session Host server role and purchase additional RDS connection licenses from Microsoft.
Final Thoughts
If you’ve configured RDP on previous Windows Server versions, then you’ll find that Windows Server 2016 behaves the exact same way. Keep in mind, however, that Microsoft’s ever-widening embrace of «assume breach» security posture and the hybrid cloud scenario and its accompanying «manage herds, not pets» philosophy means the emphasis is on command-line automation rather than on-off RDP GUI sessions.
- 10 Best New Features in Windows Server 2016
- Windows 10 for IT Pros: Tutorials, Tips and Tricks
- Top 6 Windows 10 Apps for IT Pros
Get instant access to breaking news, in-depth reviews and helpful tips.
Remote management of Windows Server 2016 is enabled by default, but Remote Desktop, on the other hand, is disabled. So, you have to turn it on in order to access a Windows Server remotely.
Depending on the case, we can enable the Remote Desktop directly using the graphical user interface, PowerShell or by implementing the appropriate policies through Group Policy.
Note: In Windows Server 2016 Essentials, Remote Desktop is enabled by default.
Enable Remote Desktop using the GUI
Open Server Manager and click Local Server from the left pane. Here, click Disable in the Remote Desktop field.
In the window that appears, enable the Allow remote connections to this computer setting. At this point, you can choose whether to allow NLA connections by enabling the corresponding setting but also to select which additional users or groups to connect other than administrators.
Once you’ve enabled the above setting, you’ll see a message to enable the corresponding Windows Firewall rule that will allow Remote Desktop Connection from any source address.
That’s it! Once you upgrade to Server Manager, you will see that the Remote Desktop setting has changed to Enabled.
Enable Remote Desktop using PowerShell
To enable Remote Desktop through PowerShell, you will need to add two keys to the registry and a rule in the Windows Firewall. Commands should run in a PowerShell window with administrator privileges.
By running the following command, the Remote Desktop will be enabled, allowing connections via Terminal Services.
New-ItemProperty -Path 'HKLM:SystemCurrentControlSetControlTerminal Server' - Name "fDenyTSConnections" -Value 0 -PropertyType dword -Force
By running the following command, the predefined Windows Firewall rules will be activated for the Remote Desktop on all profiles.
Enable-NetFirewallRule -DisplayGroup "Remote Desktop"
Finally, the following command enables Network Level Authentication (NLA) for Remote Desktop connections.
New-ItemProperty -Path 'HKLM:SystemCurrentControlSetControlTerminal ServerWinStationsRDP-Tcp' -Name "UserAuthentication" -Value 1 -PropertyType dword -Force
Enable Remote Desktop using Group Policy
To enable Remote Desktop Connection, follow the path below and set the Allow users to connect remotely using Remote Desktop Services to Enabled.
Computer Configuration Policies Administrative Templates Remote Desktop Services Remote Desktop Session Host Connections
To enable user authentication through Network Level Authentication (NLA), follow the path below and set the Require Network User Authentication policy to Enabled.
Computer Configuration Policies Administrative Templates Remote Desktop Services Remote Desktop Session Host Security
To enable the rules in the Windows Firewall, follow the path below and set the policy Windows Firewall: Allow inbound Remote Desktop exceptions to Enabled.
Computer Configuration Policies Administrative Templates Network Network Connections Windows Firewall Domain Profile
These were the three basic methods to enable Remote Desktop connections in Windows Server 2016. Of course, depending on your business security level, you may need to go ahead with further settings for who can access and from where.
This article contains step by step instructions on how to install and configure the Remote Desktop Services on a Windows Server 2016 or 2012. In Windows Server 2016 & 2012 the Terminal Services role has been replaced by the Remote Desktop Session Host (RDSH) role service and is part of Remote Desktop Services (RDS). A Remote Desktop Session Host (RDSH) server, provides to remote users the ability to access the applications on the RDS host server and the company resources from anywhere by using an RDP client.
In this tutorial you ‘ll learn how to setup and configure a Windows Server 2016 or 2012 as a Remote Desktop Session Host (Terminal) server, in order to provide remote desktop sessions, based on the number of Remote Desktop Services client access licenses (RDS CALs) installed on the RDSH server.
How to Setup and Configure a Windows Server 2016/2012 as a Remote Desktop Session Host Server (Terminal Server).
Notes:
1. The mentioned steps below, can be applied either on a Domain Controller or in a standalone server 2016/2012.
2. If the Terminal services are installed on a server that will act as a Domain Controller also, then first install the Active Directory Domain Service (AD DS) role service and promote the Server to a Domain Controller, before installing the Remote Desktop Session Host (RDSH) role service (Terminal Service).
3. Keep in mind that the below configuration does provide access to RemoteApp programs or the RDWeb site, because the Remote Desktop Connection Broker role service will not be installed.
Step 1. Install Remote Desktop Services on Server 2016/2012.
Step 2. Activate the Remote Desktop License Server.
Step 3. Install Licenses on the Remote Desktop License Server.
Step 4. Configure RD Session Host role to use the local Remote Desktop Licensing server & Set the Remote Desktop licensing mode.
Step 5. Add RD Clients (Users) to the Remote Desktop Users Group.
Step 6. Allow the log on through remote desktop Services.
Step 1. Install Remote Desktop Licensing and Remote Desktop Session Host role services.
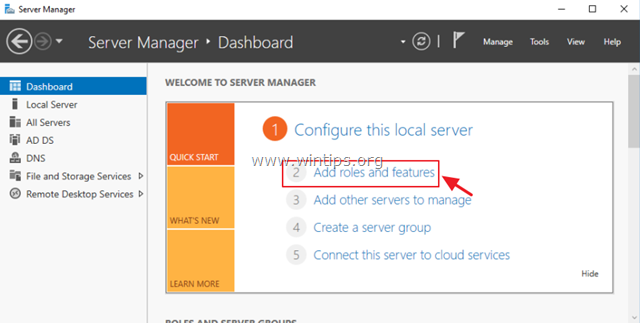
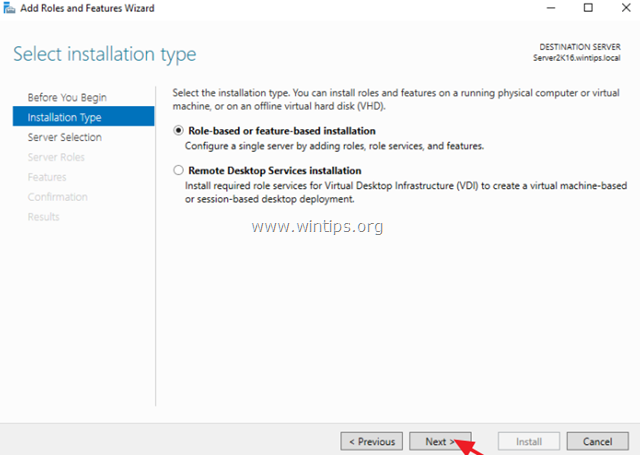
1. Open ‘Server Manager’ and click on Add Roles and Features.
2. At the first screen of ‘Add Roles and Features wizard’ leave the Role-based or feature-based installation option and click Next.
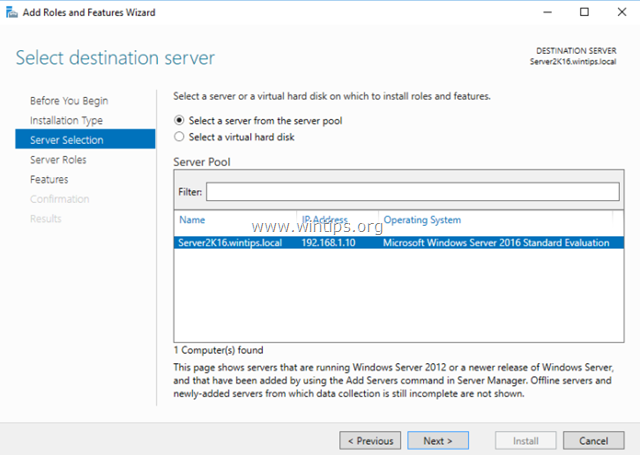
3. At the next screen, leave the default option «Select server from the server pool» and click Next.
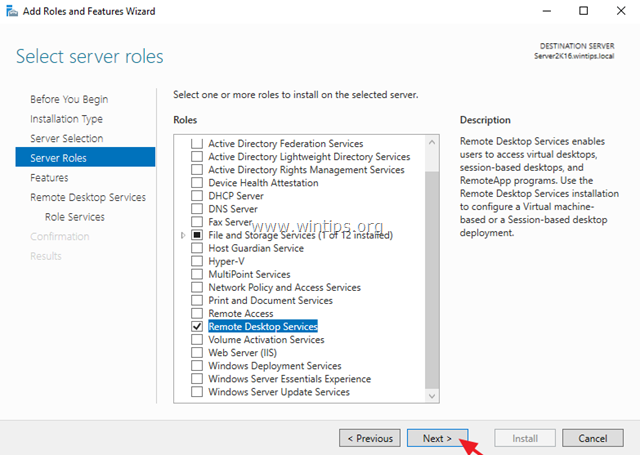
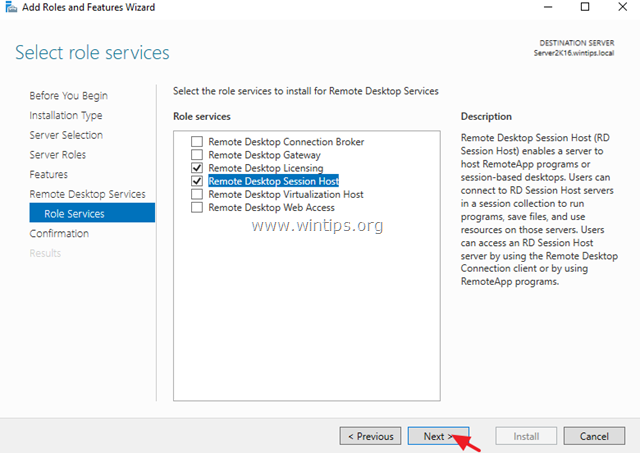
4. Select the Remote Desktop Services and click Next.
5. Leave the default settings and click Next at Features and Remote Desktop Services screens.
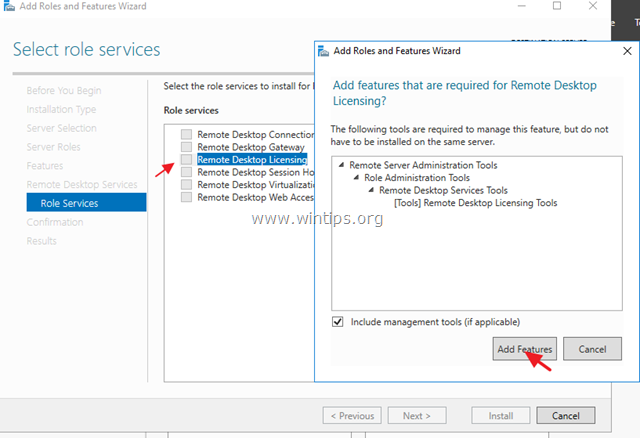
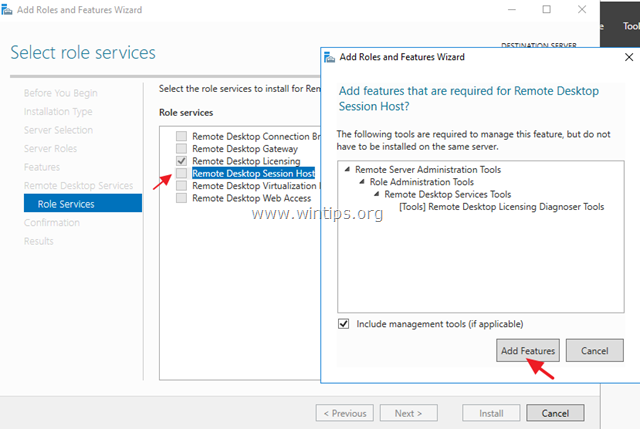
6. At Role Services screen, select the Remote Desktop Licensing role service and then click Add Features.
7. Then select the Remote Desktop Session Host role service and click Add Features again.
8. When done, click Next to continue.
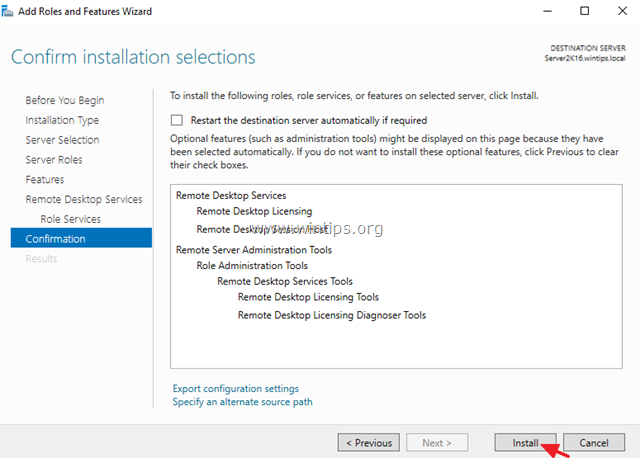
9. Finally click Install to install the Remote Desktop Services: Remote Desktop Licensing and Remote Desktop Session Host.
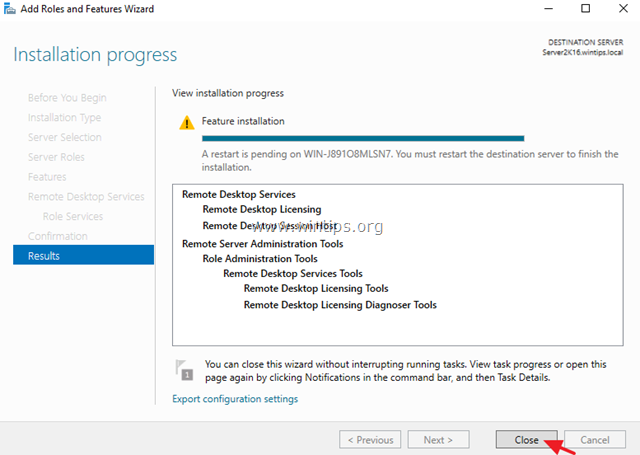
10. When the installation is completed close the ‘Add Roles and Features Wizard’ and restart your server.
Step 2. Activate the Remote Desktop License Server.
1. Simultaneously press the Windows + R keys to open run command box.
2. Type licmgr.exe and press Enter to open the RD Licensing Manager *
* Note: Alternately, you can launch the RD Licensing Manager, from Control Panel –> Administrative Tools –> Remote Desktop Services –> Remote Desktop Licensing Manager.
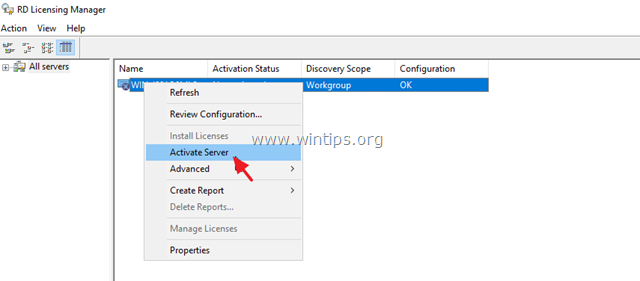
3. At the right pane, right click on the server name and select Activate Server.
4. Click Next at the Welcome screen and then click Next again at Connection method options.
5. At ‘Company Information’ window, fill the required fields and click Next twice to activate your License Server.
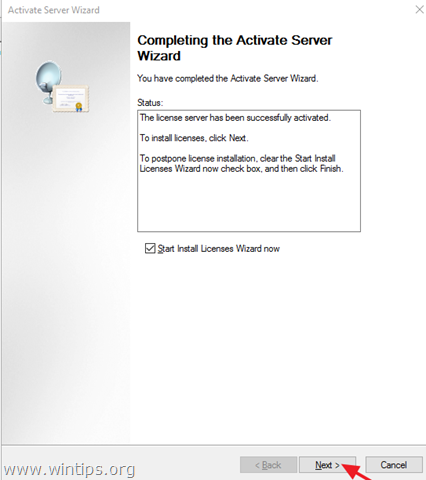
6. When the activation is completed, leave checked the ‘Start Install Licenses Wizard’ checkbox and click Next.
7. Continue to next step.
Step 3. Install Licenses on the Remote Desktop License Server.
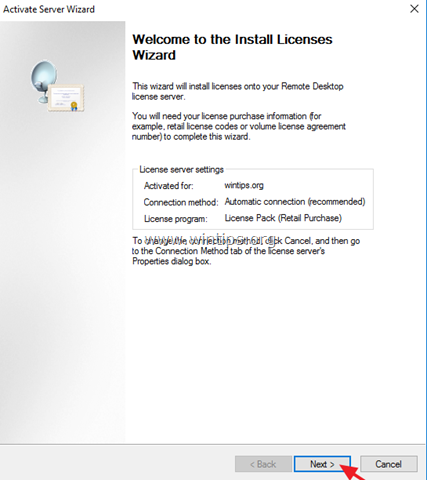
1. At ‘Welcome to the install licenses wizard’, click Next
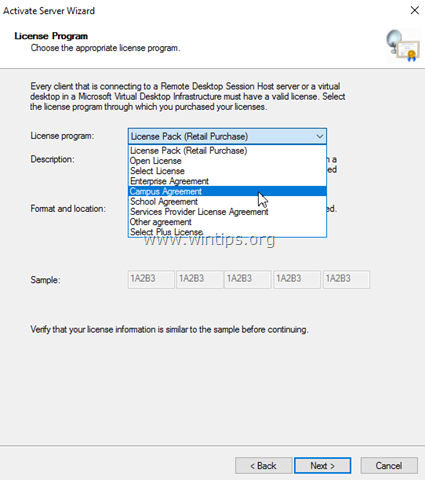
2. On the License Program page, select the appropriate program through which you purchased your RDS CALs, and then click Next.
3. According the License Program you selected on the previous page, type either the license code or the agreement number provided when you purchased your RDS CALs and then click Next.
4. On the Product Version and License Type page, select the appropriate product version, license type, and the quantity of the RDS CALs based on your RDS CAL purchase agreement, and then click Next.
5. When the RDS CALs installed on the server, click Finish. *
TIP: If you cannot activate the RDS Server automatically, then try to activate it using the Web Browser or via Telephone. To do that:
a. Right-click on the Server’s name and select Properties.
b. Change the Connection Method to Web Browser or to Telephone. When done, click OK.
c. Finally, right click on the server name, select Activate Server and follow the onscreen instructions to completed the activation.
Step 4. Configure RD Session Host role to use the local Remote Desktop Licensing server & Set the Remote Desktop licensing mode.
1. Open Group Policy Editor. To do that:
1. Simultaneously press the Windows
+ R keys to open run command box.
2. Type gpedit.msc and press Enter.
2. In Group Policy Editor navigate to:
- Computer ConfigurationAdministrative TemplatesWindows ComponentsRemote Desktop ServicesRemote Desktop Session Host Licensing
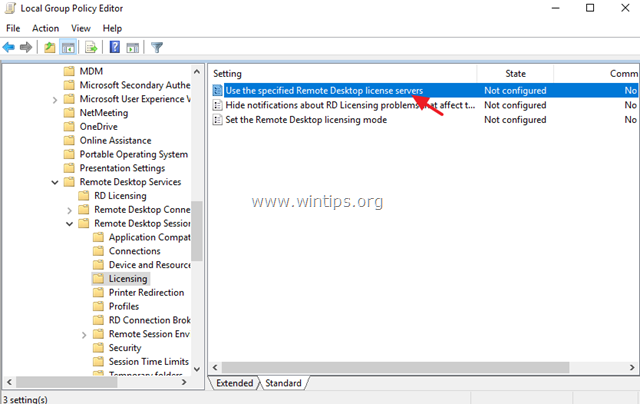
3. At the right pane, double click at Use the specified Remote License Servers.
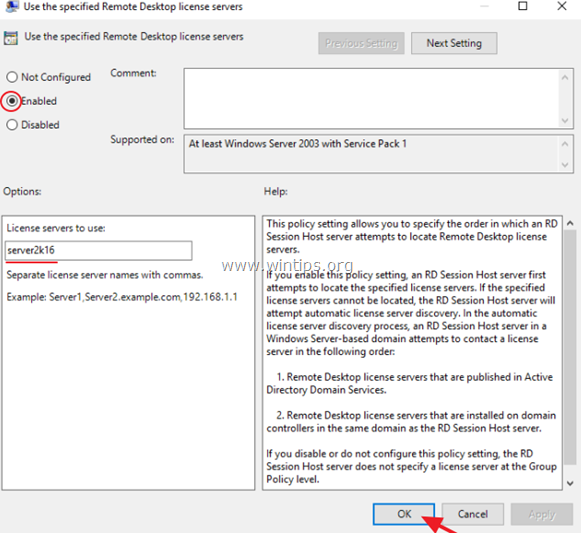
4. Click Enabled, and then at ‘License server to use‘ field, type the RDS license server name and click OK.
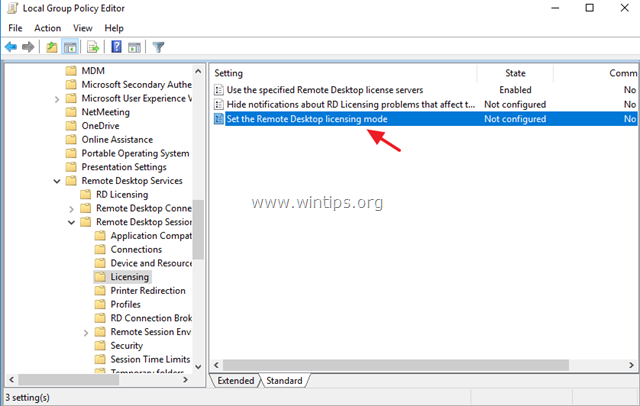
5. Then open the Set the Remote Desktop licensing mode setting.
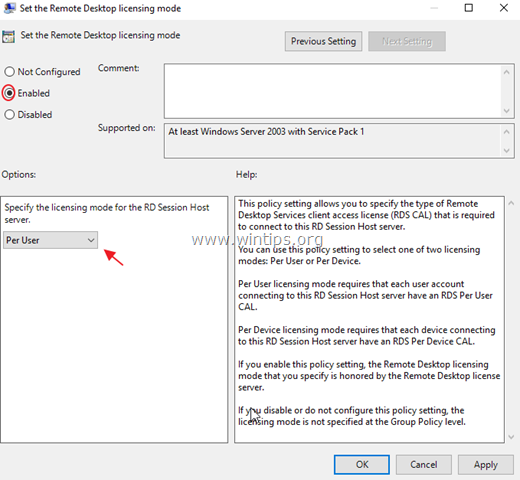
6. Click Enabled and then specify the licensing mode (Per User or Per Device) for the RDS host server and then click OK again.
7. Close Group Policy Editor.
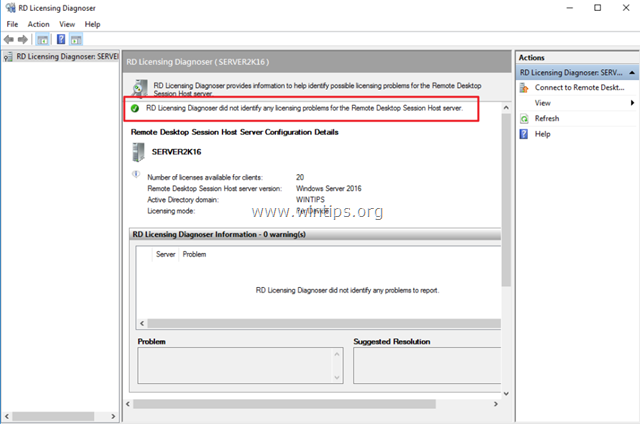
8. Verify the RD Licensing configuration, by going to: Windows Control Panel –> Administrative Tools –> Remote Desktop Services –> RD Licensing Diagnoser.
Step 5. Add RD Clients (Users) to the Remote Desktop Users Group.
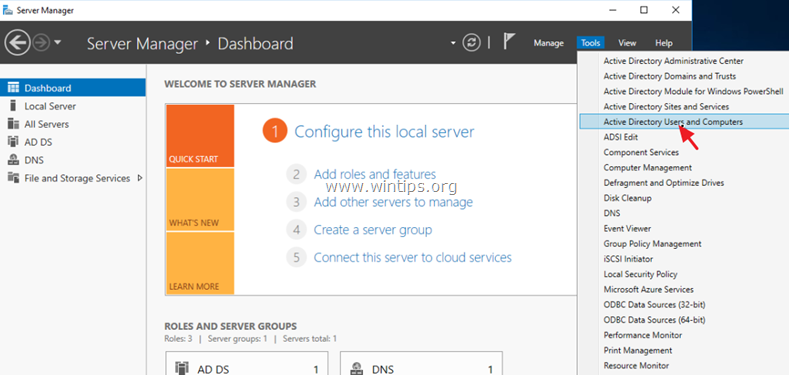
1. Open Server Manager.
2. From Tools menu, select Active Directory Users and Computers. *
* Note: If the RD Session Host Service is not installed on the Domain Controller, use the ‘Local Users and Groups’ snap-in or the ‘Remote’ tab in the ‘System Properties’ on the RDS host server, to add the remote desktop users.
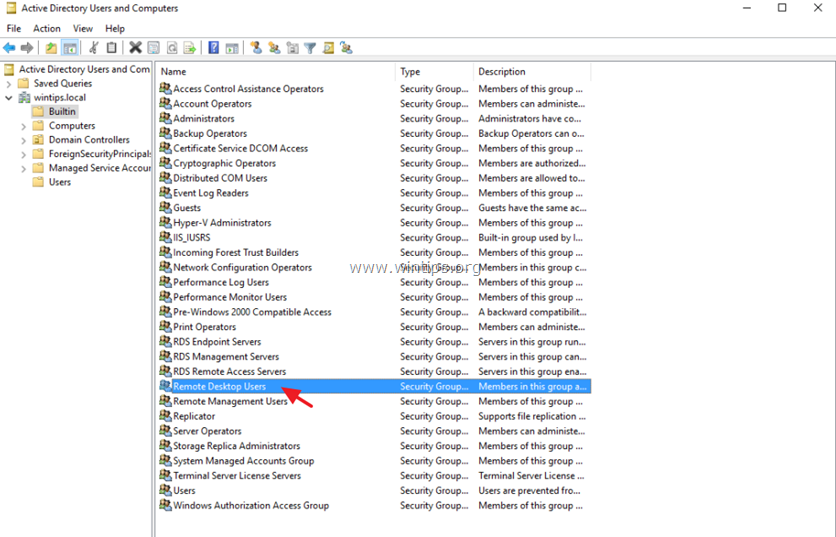
3. Double click at your domain on the left and then select Builtin.
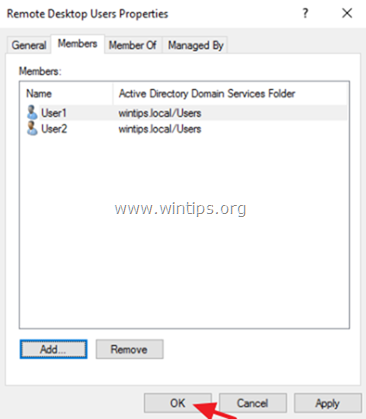
4. Open Remote Desktop Users on the right pane.
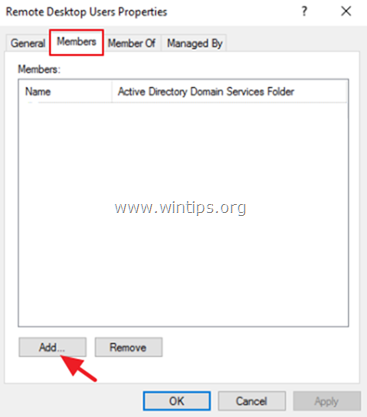
5. At Members tab, click Add.
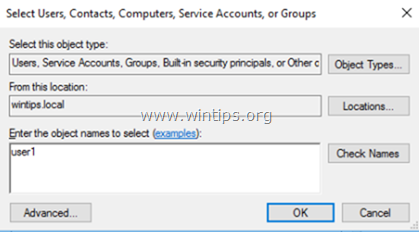
6. Type the name(s) of the users that you want to give Remote access to the RDS Server and click OK.
7. After selecting the remote desktop users, click OK again to close the window.
8. Continue to step-6 below.
Step 6. Allow the log on through remote desktop Services.
1. Open the Local Group Policy Editor. To do that:
1. Simultaneously press the Windows
+ R keys to open run command box.
2. Type gpedit.msc and press Enter.
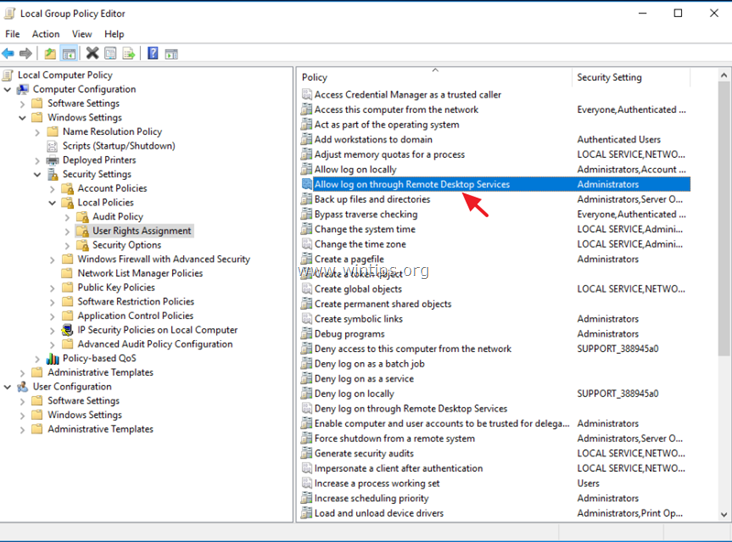
2. In Group Policy Editor navigate to: Computer Configuration > Windows Settings > Security Settings > Local Policies > User Rights Assignment.
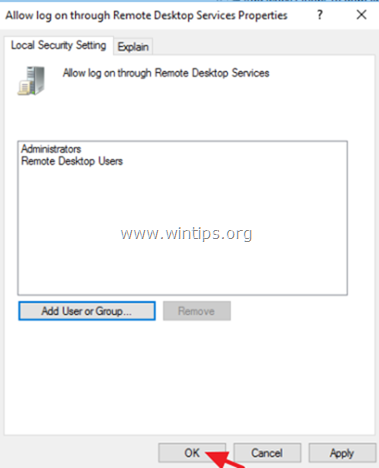
3. At the right Pane: double click at Allow log on through Remote Desktop Services.
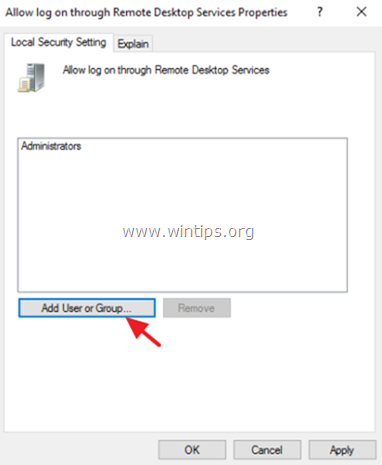
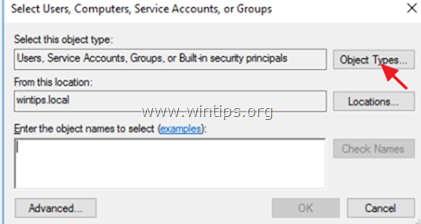
4. Click Add User or Group.
5. Click Object Types, check all the available objects (Users, Groups, & Built-in security principals) and then click OK.
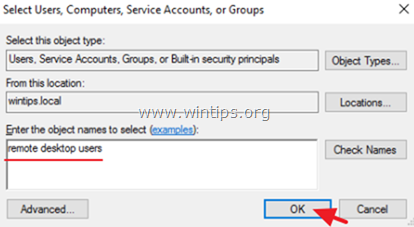
6. Type remote desktop users and then click OK.
7. Finally click OK again and close Group Policy Editor.
8. Now you ‘re ready to connect to the Remote Desktop Session Host Server 2016/2012 from any Remote desktop client.
That’s it! Let me know if this guide has helped you by leaving your comment about your experience. Please like and share this guide to help others.
If this article was useful for you, please consider supporting us by making a donation. Even $1 can a make a huge difference for us in our effort to continue to help others while keeping this site free:

If you want to stay constantly protected from malware threats, existing and future ones, we recommend that you install Malwarebytes Anti-Malware PRO by clicking below (we
do earn a commision from sales generated from this link, but at no additional cost to you. We have experience with this software and we recommend it because it is helpful and useful):
Full household PC Protection — Protect up to 3 PCs with NEW Malwarebytes Anti-Malware Premium!
Table of Contents
- Introduction
- Prerequisites
- Install The Remote Desktop Roles
- Activate The RDS Licenses
- Activate Remote Desktop License Server
- RDS Rest Configuration
- See Also
Introduction
This is a comprehensive guide for installing RDS services to a Windows Server 2016. We will see in great detail how to enable the Remote Desktop Roles, Activate the RDS licenses and make the final configuration to make it work.
Prerequisites
- Remote Desktop Licensing
- Remote Desktop Session Host
At the following steps we proceed with the installation of the required roles.
Install The Remote Desktop Roles
From the Server Manager, select Manage — Add Roles and Features, to start the roles installation.
1. The Add Roles and Features Wizard opens, and we click
Next > to begin
2. Next we have to choose the installation type, we leave the default type {Role-based or feature-based installation}, and click
Next >
3. In the next step, we select the destination server that the role will be installed, for the needs of the post we have only one server, named
test with IP Address 10.0.1.4. Leave the default server and click
Next >
4. In the fourth step, we need to select the server roles, that will be installed in the server, select the
Remote Desktop Services, and click Next >, to continue.
5. In the features form, click Next >
6. At the next step, we have to select Next >
7. In the Remote Desktop Role Services, select from the Role services list the
Remote Desktop Licensing and the Remote Desktop Session Host roles and click
Next >
8. In the Confirm installation selections form, we confirm the Remote Desktop Services that will be installed and select
Install.
9. The installation progress finished, so we need to select the Close button and restart the Server to apply the changes.
Activate The RDS Licenses
After the roles are installed, we need to activate the RDS licenses. To do this we follow the next steps.
1. From the Server Manager, select Tools — Remote Desktop Licensing Manager
2. In the RD Licensing Manager windows, we can see the server test which is Not yet activated.
3. Right click on the server test and select Activate Server.
Activate Remote Desktop License Server
1. A new Activate Server Wizard starts, and to continue click Next >
2. At the Connection Method form, select Automatic connection (recommended), and click
Next >
3. Provide the requested company information and click Next >.
 Note |
|---|
| This information are used by Microsoft if we need assistance. |
4. At the next form, we type some other optional information, like Email, OU, City, and click
Next >.
5. At the final step in the Activation Server Wizard, check the Start Install Licenses Wizard now
option and select Next >
6. Automatically the Install Licenses Wizard opens, and to proceed with the licenses installation we select
Next >
 Note |
|---|
| In this part we must be sure that we have bought a valid RDS license. |
7. The next step is to select the license program that we will activate the RDS licenses.
| License Program | Format Of The License |
| License Pack (Retail Purchase) | The format of the license code is 5 sets of 5 alphanumeric digits, 25 |
| Open License | For this type of license we need an authorization number of 15 alphanumeric digits and a license number of 8 numeric digits. |
| Enterprise Agreement |
For all these six License Programs, the enrollment number is 7 number digits. |
| Campus Agreement | |
| School Agreement | |
| Services Provider License Agreement | |
| Other Agreement | |
| Select Plus License |
8. In this post, we activate an Open License, for that reason we selected on the previous step (7) as licensed program {Open License}, type the
Authorization and License numbers and click
Next > to continue.
9. In the Product Version and License Type form, select Windows Server 2016 and RDS Per User CAL and type into the Quantity field the number of the licenses that will be activated, and click
Next >
10. We have successfully installed the licenses, and we select Finish to close the Install Licenses Wizard.
RDS Rest Configuration
The last step for the RDS activation is to make two changes to the Windows Group Policies.
1. Open the Run -> type gpedit.msc and click OK.
2. Move to the path {Computer Configuration Administrative Templates Windows Components Remote Desktop Services Remote Desktop Session Host Licensing} and make the following changes :
2a. In the Use the specified Remote Desktop license servers setting
Select the value Enabled, type the local server IP, e.g.
10.0.1.4, and click OK
2b. The second change we must do is on the Set the Remote Desktop licensing mode setting
In this setting we select Enabled and also from the Options:, choose the
Per User licensing mode and click OK.
3. The final of all the steps is to confirm that the licenses are activated. We can do this from the
Server Manager — Tools —Remote Desktop Services —
Remote Desktop Licensing Diagnoser
4. The Remote Desktop Licensing Diagnoser opens and we can see that the licenses are activated.
See Also
- License your RDS deployment with client access licenses (CALs)
- Activate the Remote Desktop Services license server
- Install RDS client access licenses on the Remote Desktop license server
- Remote Desktop Services
- Remote Desktop Services Overview
Эта большая инструкция посвящена особенностям установки, настройки и эксплуатации фермы терминальных серверов на базе роли Remote Desktop Services (RDS) в Windows Server. Статья поможет вам развернуть службы удаленных столов на Windows Server 2022, 2019 и 2016 в домене Active Directory.
Содержание:
- Компоненты Remote Desktop Services в Windows Server 2022/2016/2016/2012R2
- Создаем новую конфигурацию Remote Desktop Services в Windows Server
- Создаем коллекции Remote Desktop Services в Windows Server
- Публикация RemoteApp в Remote Desktop Services
- Настройка фермы Remote Desktop services с помощью PowerShell
Компоненты Remote Desktop Services в Windows Server 2022/2016/2016/2012R2
В состав роли RDS в Windows Server входя следующие компоненты:
- Remote Desktop Session Host (RDSH) – узлы сеансов RDS. Основные рабочие лошадки фермы RDS, на которых работают приложения пользователей;
- Remote Desktop Connection Broker (RDCB) – посредник RDS подключений. Используется для управления фермой RDS, распределения нагрузки, обеспечивает переподключение пользователей к своим сеансам, хранит коллекции RDS и опубликованные приложения RemoteApps;
- Remote Desktop Gateway (RDGW) – обеспечивает безопасный доступ к сервисам RDS из Интернета;
- RD Web Access (RDWA) – веб интерфейс для доступа к рабочим столам, программам RemoteApp;
- Remote Desktop Licensing (RD Licensing) — служба лицензирования, управляет RDS лицензиями (CAL) пользователей.
В нашем небольшом стенде будут всего три сервера со следующим распределением ролей
-
msk-rds1.winitpro.ru
— RDSH -
msk-rds2.winitpro.ru
– RDSH -
msk-rdsman.winitpro.ru
– RDSH, RDWA, RDCB, RD License
Предварительные требования, которые нужно выполнить перед созданием RDS фермы:
- Установите одинаковую версию Windows Server на все сервера, настроить их, и добавить в один домен AD;
- Откройте консоль ADUC (
dsa.msc
) и переместите все хосты с ролью RDSH в одну OU в AD. Так будет удобнее применять единые настройки через GPO; - Создайте в домене группу для RDSH серверов (например,
msk-rdsh
) и добавьте в нее все хосты; - Если вы хотите использовать диски User Profile Disk (UPD) для хранения профилей пользователей RDS (или перемещаемые профили), нужно создать на файловом сервере сетевой каталог, в котором они будут хранится (желательно расположить этот каталог на отказоустойчивом файловом кластере Windows Server). Предоставьте права Full Control на этот сетевой каталог для группы
msk-rdsh
.
Создаем новую конфигурацию Remote Desktop Services в Windows Server
Рассмотрим, как создать и настроить RDS конфигурацию с помощью графического интерфейса Server Manager.
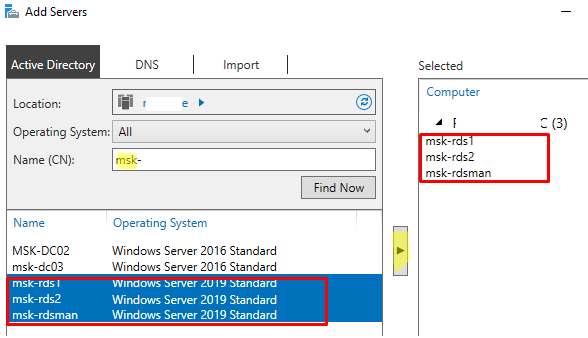
Откройте Server Manager и добавьте все планируемые RDS сервера в консоль. Щелкните All Server -> Add servers.
Теперь в меню Server Manager выберите Add Roles and Features -> Remote Desktop Services installation -> Standard deployment –> Session-based deployment.
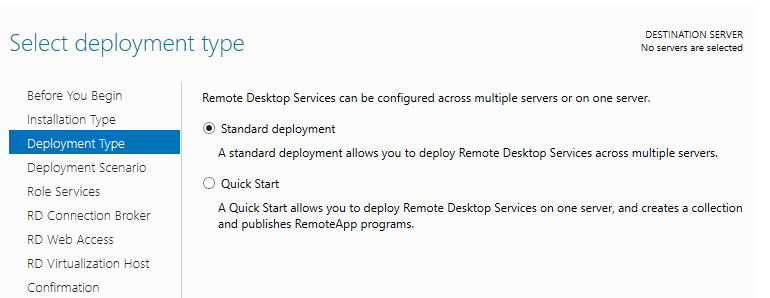
Режим Quick Start используется для развертывания всех компонентов RDS на одном сервере. В RDS ферме минимум может быть один сервер, который совмещает все роли RDS (RD Session Host, RD Web Access и RD Connection broker). Но такая конфигурация не обеспечивает отказоустойчивость и балансировку нагрузки в службах удаленных рабочей столов Windows Server.
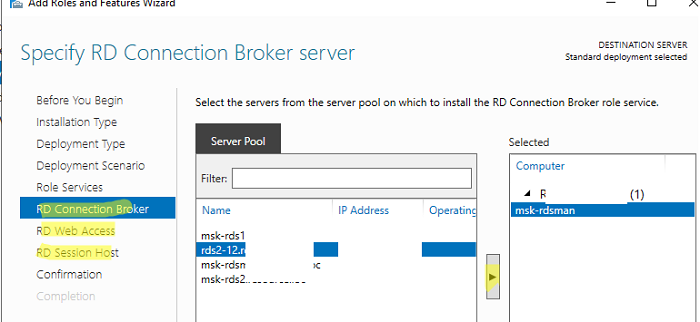
Далее нужно указать, как вы хотите распределить роли RDS по вашим серверам. В мастере построения фермы RDS нужно выбрать сервера для соответствующих ролей. В моем случае я хочу построить такую конфигурацию:
- RD Connection Broker –
msk-rdsman - RD Web Access —
msk-rdsman - RD Session hosts —
msk-rdsman, msk-rds1, msk-rds2
Вы можете распределить RDS роли по серверам в любой другой конфигурации.
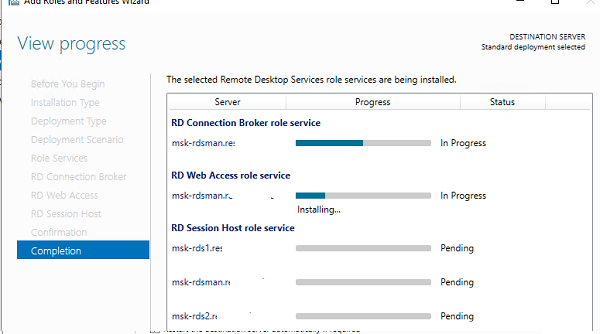
Поставьте галку Restart destination server automatically if required и нажмите кнопку Deploy. Дождитесь установки ролей RDS на всех серверах.
Итак, ваша ферма RDS создана.
Следующий этап установка и настройка сервера лицензирования RDS. Вы можете установить роль RD Licensing на один из серверов в вашей ферме или использовать существующий в домене сервер лицензирования RDS. Подробная инструкция по установке, настройке и активации роли RD Licensing доступа по ссылке.
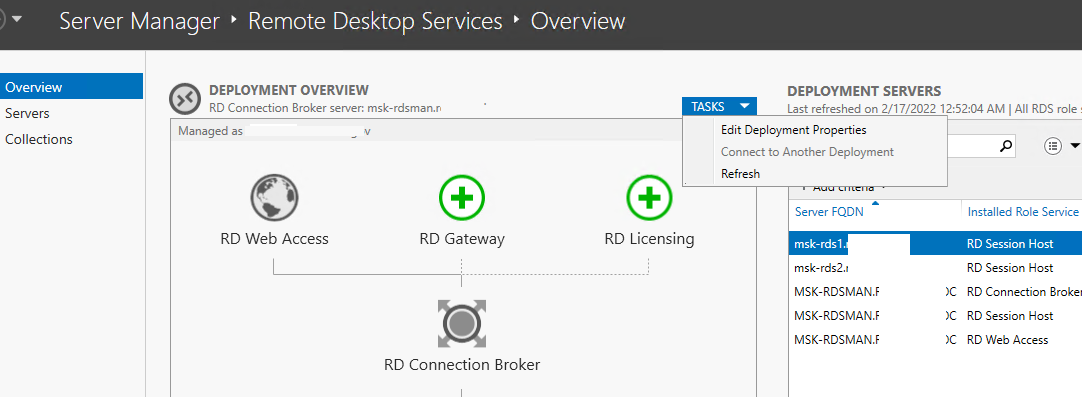
Для управления вашим развертыванием RDS нужно перейти в раздел Server Manager -> Remote Desktop Services. На вкладке Overview показана текущая конфигурация RDS фермы.
Чтобы изменить настройки RDS фермы выберите Tasks -> Edit Deployment Properties в разделе Deployment Overview.
Здесь можно изменить:
- Параметры RD Gateway;
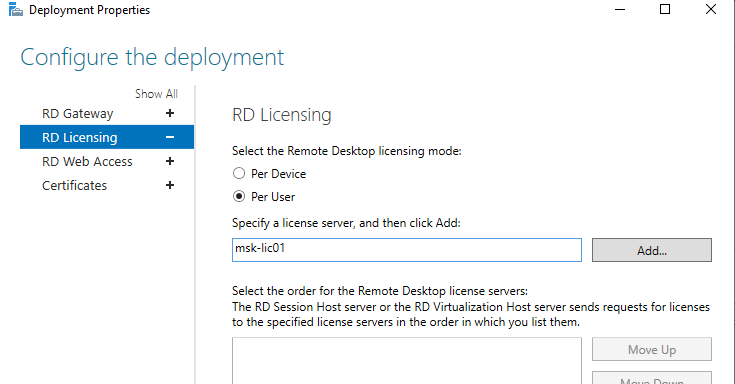
- Адрес сервер сервера лицензирования и тип пользовательских лицензий RDS CAL (per user/per device);
- Посмотреть URL адреса RD Web Access;
- Добавить SSL сертификаты для служб RDS (в инструкции мы пропустим этот пункт).
Для построения отказоустойчивой фермы Remote Desktop Services нужно обеспечить высокую доступность роли RD Connection Broker. Это достигается за счет запуска нескольких экземпляров RDCB (Active/Active) на разных серверах с общей базой данных SQL, в которой хранится конфигурация брокера подключений. Для обеспечения высокой доступности SQL базы RDCB ее можно размесить в группе высокой доступности SQL Server Always On. Ранее мы публиковали подробный гайд по настройке RDS Connection Broker с высокой доступностью.
Создаем коллекции Remote Desktop Services в Windows Server
Следующий этап настройки – создание коллекций сеансов RDS. Коллекции Remote Desktop позволяют разделить хосты в ферме RDSH на отдельные группы или создать разный набор настроек и доступных приложений Remote App для разных групп пользователей.
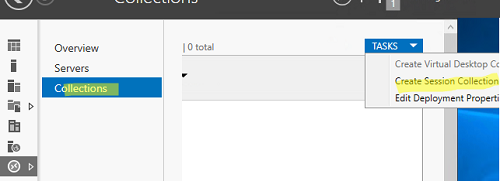
Перейдите в раздел Collections, выберите Edit -> Create Session Collection.
Здесь нужно задать:
- Имя коллекции RDS:
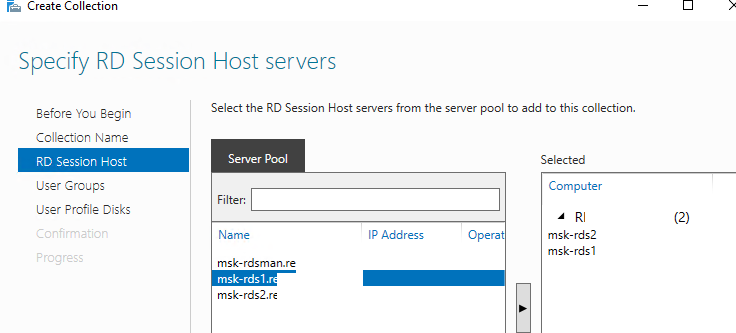
rds-Msk-Managers - Выберите какие хосты RDSH будут обслуживать пользователей коллекции (один RDSH хост может находиться в одной коллекций; не рекомендуется объединять в одну коллекцию сервера с разными версиями Windows Server);
- На вкладке User Groups указываются группы пользователей, которым разрешено подключаться к коллекции. Уберите из групп Domain users и добавьте вашу группу (msk-Managers);
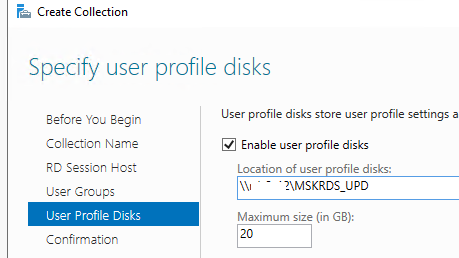
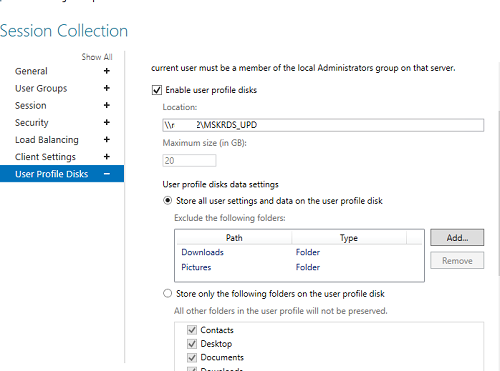
- На вкладке User Profile Disk нужно указать, хотите ли вы использовать формат UPD для хранения профилей пользователей (Enable user profile disks). В поле Location of user profile disks укажите UNC путь к сетевому каталогу(например,
\msk-fs01mskrds_upd
), в котором будут хранится профили пользователей в форматер UPD виртуальных дисков (в этом случае при входе на любой сервер коллекции RDS, пользователь будет всегда загружать свой профиль) и максимальный размер диска (20 Гб по умолчанию); - Нажмите Create чтобы создать новую RDS коллекцию;
- Убедитесь, что в указанном каталоге создался UPD файл с шаблоном профиля пользователя UVHD-template.vhdx.
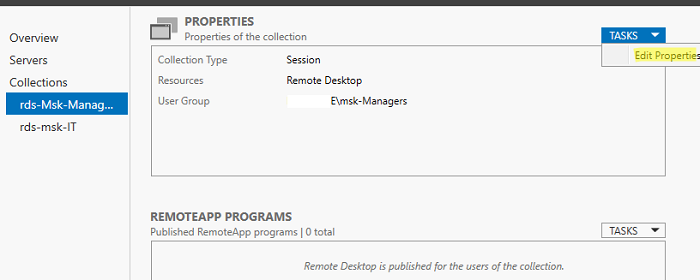
Чтобы задать параметры коллекции RDS, выберите ее и нажмите Tasks -> Edit Properties.
Здесь можно изменить базовые параметры коллекции (имя, описание, группы доступа) и ряд других важных настроек.
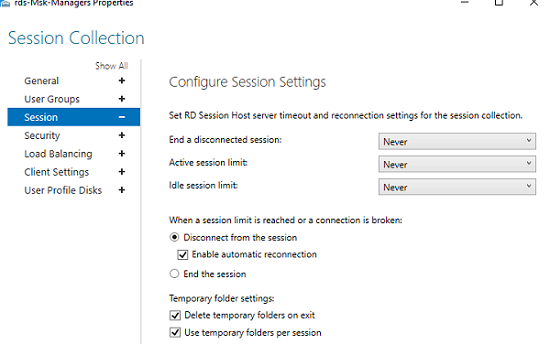
В разделе Session можно задать параметры переподключения/ автоматического отключения простаивающих RDP сессий (подробнее рассматривалось в статье Настройка таймаутов для RDP сессий).
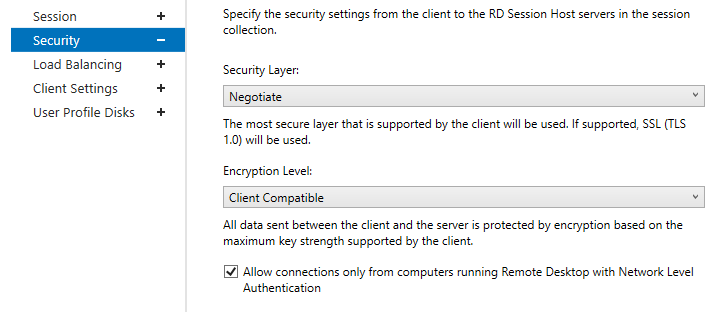
На вкладке Security можно выбрать настройки безопасности (Negotiate, RDP Security level или SSL/TLS) и шифрования (Low, High, Client compatible или FIPS compliant) для сессий RDP. Здесь также можно включить/отключить Network Level Authentication для RDP.
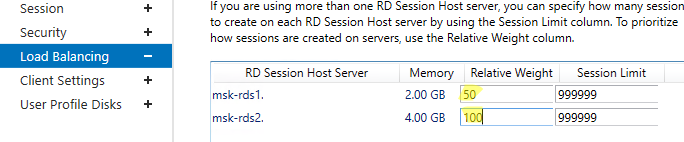
В секции Load Balancing можно изменить веса (
Relative Weight
) RDSH хостов в вашей ферме. Если характеристики серверов (RAM, CPU) в коллекции сильно отличаются, нужно задать меньший вес для менее производительных серверов. В этом случае RDCB будет распределять сессии пользователей по серверам в зависимости от их веса.
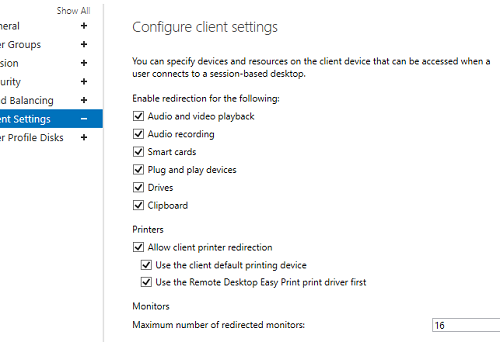
На вкладке Client Settings можно указать, какие устройства пользователям разрешено пробрасывать в RDP сессию. Например, вы можете разрешить/запретить пробрасывать с локального компьютера пользователя в RDS сеанс принтера, сетевые диски, аудио устройства, буфер обмена.
В разделе User Profile Disks можно более тонко настроить параметры UPD профилей пользователей. Можно исключить из синхронизации определенные папки или файлы. Это позволит уменьшить размер профиля UPD в сетевом каталоге и увеличить скорость загрузки профиля (не забывайте, что он загружается по сети из сетевой папки при входе пользователя).
Настройка и эксплуатация UPD обычно гораздо проще, чем использование перемещаемых профилей или folder redirection. Один UPD профиль не может использоваться в разных коллекциях RDS.
Для уменьшения размера UPD диска пользователя можно использовать стандартный PowerShell командлет
Resize-VHD
, используемый для изменения размеров виртуальных VHDX дисков Hyper-V.
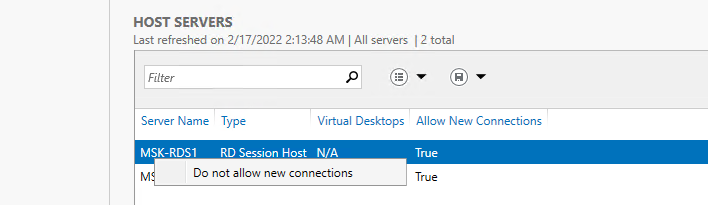
В секции HOST SERVERS коллекции RDS можно перевести любой сервер фермы в режим обслуживания RDSH (Drain Mode). Для этого щелкните по нему и выберите Do not allow new connection. В результате Connection Broker не будет отправлять новые подключения пользователей на этот сервер. В таком режиме вы можете спокойно установить обновления Windows или обновлять на сервере приложения, не затрагивая пользователей.
Здесь же можно добавить/удалить RDS Host из коллекции.
Если RDSH хост вышел из строя и не доступен, его можно корректно удалить из фермы Remote Desktop Services по этой инструкции.
Публикация RemoteApp в Remote Desktop Services
RemoteApps – это опубликованные для пользователей приложения на RDS серверах. Благодаря RemoteApp можно использовать приложения, установленные на терминальном RDSH сервере так, как будто оно запущено непосредственно на компьютере пользователя. Пользователь не видит всего рабочего стола Windows Server RDS и работает только с теми программами, которые опубликовал для него администратор. На компьютере пользователя будет отображаться только окно запущенной на RDS программы.
Если вы не создаете RemoteApp, пользователи будут работать непосредственно на собственных рабочих столах на Windows Server. Поэтому не забудьте скопировать все необходимые пользователю ярлыки приложений в папку C:UsersPublicDesktop. Файлы из этой папки будут отображаться на рабочем столе всех пользователей. Если вы устанавливаете на RDSH пакет MS Office 365, обратите внимание что Office нужно разворачивать в режиме SharedComputerLicensing.
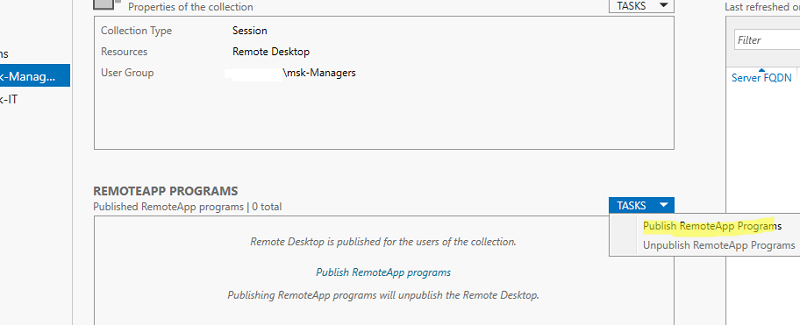
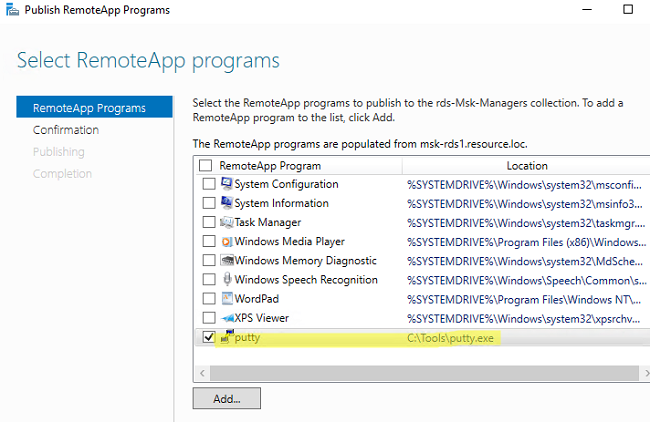
RemoteApp приложения создаются в настройках коллекций RDS. Выберите пункт Tasks -> Publish RemoteApp Programs в секции REMOTEAPP PROGRAMS.
Windows отобразит все приложения, установленные на текущем сервере. Можете выбрать одно из них. Если вашего приложения нет в списке, но оно установлено на других хостах RDS, нажмите кнопку Add и укажите полный путь к исполняемому файлу приложения (exe, bat, cmd и т.д.).
Опубликуйте приложение RemoteApp.
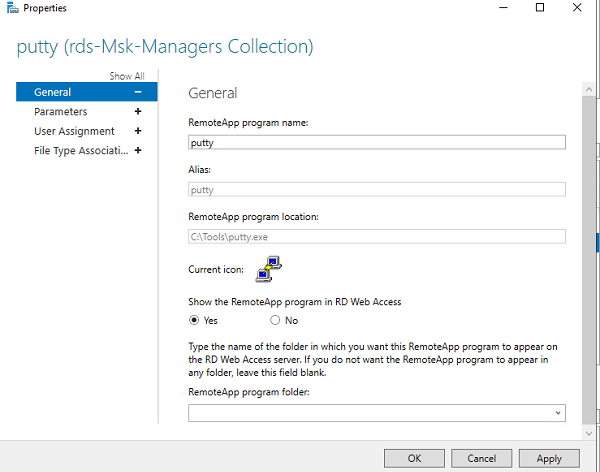
Затем в настройках RemoteApp можно указать дополнительные параметры приложения.
- Нужно ли показывать опубликованное RemoteApp приложение в веб интерфейсе RD Web Access;
- Задать параметры запуска (аргументы) приложения (Command-line Parameters -> Always use the following command-line parameters);
- На вкладке User Assignment можно дополнительно ограничить каким группам пользователей разрешено запускать приложение.
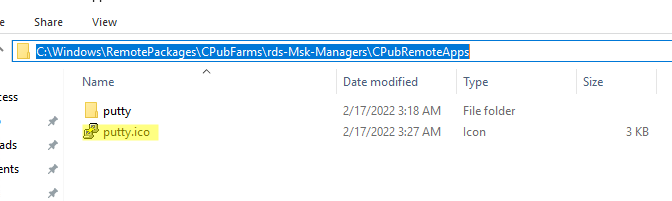
Если вы хотите изменить иконку опубликованного RemoteApp, нужно открыть следующую папку на сервере с ролью RDS Connection Broker:
C:WindowsRemotePackagesCPubFarmsrds-Msk-ManagersCPubRemoteApps
Замените иконку приложения другим ico файлом.
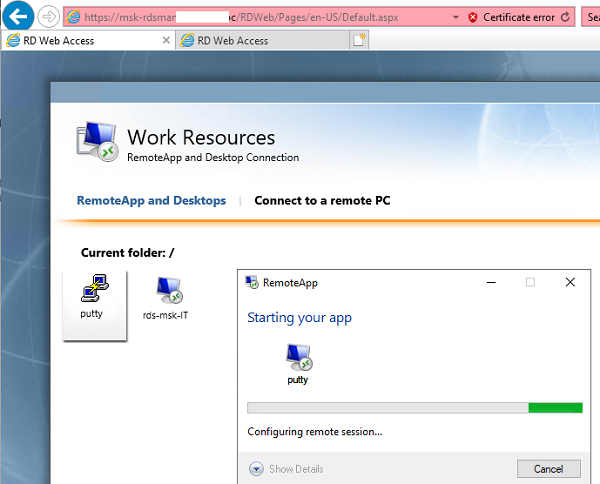
Теперь пользователь может запустить RemoteApp приложение из RD Web Access (
https://msk-rdsman.wintpro.ru/RDWeb
) или с помощью специального RDP файла.
Для запуска опубликованного приложения RemoteApp, нужно добавить в RDP файл такие строки:
remoteapplicationmode:i:1 remoteapplicationname:s:putty remoteapplicationprogram:s:"C:Toolsputty.exe" disableremoteappcapscheck:i:1 alternate shell:s:rdpinit.exe
Несколько полезных мелочей для удобной эксплуатации фермы RDS:
- Для роли RDWeb можно настроить поддержку HTML5, это позволит пользователям подключаться к RDS серверам из любого браузера и ОС даже без клиента RDP;
- На веб сервере RD Web Access можно опубликовать ссылку на смену истекшего пароля пользователя (по умолчанию при включенном NLA вы не сможете аутентифицироваться на RDSH с истекшим паролем пользователя Active Directory);
- Инструкция для пользователей по смене пароля в RDP сессии;
- Администратор может использовать теневые подключения RD Session Shadow для подключения/просмотра рабочего стола сеанса пользователя на сервере RDS;
- Чтобы быстро найти, на каких RDS серверах есть сессии определенного пользователя, можно использовать PowerShell:
Import-Module RemoteDesktop
Get-RDUserSession -ConnectionBroker msk-rdsman.winitpro.ru | where {$_.UserName -eq "a.ivanov"} | Select HostServer - Вы можете использовать PowerShell скрипты для просмотра и анализа логов RDP подключений пользователей к серверам RDS;
- Для дополнительной защиты можно настроить двухфакторную аутентификацию (2FA) пользователей на RDS серверах Windows с помощью сторонних средств.
Настройка фермы Remote Desktop services с помощью PowerShell
Если вы четко представляете себе концепцию RDS фермы, вы можете быстро разворачивать RDS конфигурацию с помощью PowerShell.
Следующие PowerShell команды для создания RDS фермы лучше запускать с другого на другом сервера, т.к. управляемые RDS хосты придется перезагружать.
Задайте имена серверов в вашей ферме RDS. В этом примере я установлю роли RDCB и RDS Licensing на отдельный сервер (в дальнейшем рекомендуется настроить отказоустойчивую конфигурацию RDCB).
$RDSH1 = "msk-rds1.winitpro.ru"
$RDSH2 = "msk-rds2.winitpro.ru"
$RDSCB = "msk-rdcb.winitpro.ru"
$RDSGW = "msk-rdsgw.winitpro.ru"
Import-Module RemoteDesktop
Установите RDS роли на сервера:
Add-WindowsFeature –ComputerName $RDSH1, $RDSH2 -Name RDS-RD-Server –IncludeManagementTools
Add-WindowsFeature –ComputerName $RDSCB -Name RDS-Connection-Broker -IncludeManagementTools
Add-WindowsFeature –ComputerName $RDSGW -Name RDS-Web-Access, RDS-Gateway –IncludeManagementTools
Перезагрузите все хосты:
Restart-Computer -ComputerName $RDSH1,$RDSH2,$RDSCB,$RDSGW
Создайте новый инстанс RDSessionDeployment:
New-RDSessionDeployment -ConnectionBroker $RDSCB -SessionHost $RDSH1,$RDSH2 –Verbose
Добавить в ферму сервера RDWA и RDGW:
Add-RDServer -Server $RDSGW -Role RDS-WEB-ACCESS -ConnectionBroker $RDSCB
Add-RDServer -Server $RDSGW -Role RDS-GATEWAY -ConnectionBroker $RDSCB -GatewayExternalFqdn "rds.winitpro.ru"
Текущее распределение RDS ролей по серверам фермы можно вывести так:
Get-RDServer -ConnectionBroker $RDSGW
Установка роли лицензирования RDS:
Add-WindowsFeature –ComputerName $RDSCB -Name RDS-Licensing, RDS-Licensing-UI
Задайте режим лицензирования PerUser:
Invoke-Command -ComputerName $RDSCB -ScriptBlock {Set-RDLicenseConfiguration -Mode PerUser -LicenseServer $RDSCB -ConnectionBroker $RDSCB}
Add-RDServer -Server $RDSCB -Role RDS-LICENSING -ConnectionBroker $RDSCB
Добавить сервер лицензирования в доменную группу с помощью Add-ADGroupMember:
Add-ADGroupMember "Terminal Server License Servers" -Members "msk-rdcb$"
Если у вас есть сертификат для RDS можно его добавить в конфигурацию фермы (можно использовать бесплатный SSL сертификат Let’s Encrypt для вашего RDS хоста):
Path = "C:psRDSCert.pfx"
$Password = ConvertTo-SecureString -String "CertPAssddr0w11-" -AsPlainText -Force
Set-RDCertificate -Role RDGateway -ImportPath $Path -Password $Password -ConnectionBroker $RDSCB -Force
Set-RDCertificate -Role RDWebAccess -ImportPath $Path -Password $Password -ConnectionBroker $RDSCB -Force
Set-RDCertificate -Role RDPublishing -ImportPath $Path -Password $Password -ConnectionBroker $RDSCB -Force
Set-RDCertificate -Role RDRedirector -ImportPath $Path -Password $Password -ConnectionBroker $RDSCB -Force
Информацию об установленных SSL сертификатах можно получить так:
Get-RDCertificate
Теперь можно создать коллекции RDS:
$CollectionName = "DEVdept"
New-RDSessionCollection –CollectionName $CollectionName –SessionHost $RDSH1,$RDSH2 –ConnectionBroker $RDSCB –CollectionDescription “Develovers”
Разрешить доступ к RDS серверам для групп:
$UserGroup [email protected]("WINITPROmsk-developers","WINITPROmsk_devops")
Set-RDSessionCollectionConfiguration -CollectionName $CollectionName -UserGroup $UserGroup
Опубликовать приложение RemoteAPP:
New-RDRemoteapp -Alias GoogleChrome -DisplayName GoogleChrome -FilePath "C:Program Files (x86)GoogleChromeApplicationchrome.exe" -ShowInWebAccess 1 -CollectionName $CollectionName -ConnectionBroker $RDSCB
В статье мы рассмотрели, как установить и настроить ферму Remote Desktop Services на базе Windows Server 2019/2022 с помощью графического интерфейса Server Manager и с помощью PowerShell. За рамками статьи осталось более подробное описание ролей RD Web Access и RD Gateway. Мы рассмотрим настройку этих ролей отдельно в следующих статьях.
This year has been a year like none other with organizations scrambling to bolster their remote work infrastructure. It has meant that businesses have had to provision the infrastructure needed to allow workers to connect to business-critical applications, services, and data to carry out essential job functions. One of the technologies that has been around for a while is Remote Desktop Services (RDS). Remote Desktop Services is newer technology iteration of the older Terminal Services technology that many remember from older Windows Server operating systems. Remote Desktop Services is fairly easy to provision and provides the ability to allow remote workers to easily connect to business infrastructure. In this post, we will take a look at Windows Server 2016 install remote desktop services steps to see how you can easily provision a Windows Server 2016 RDS server.
Remote Desktop Services (RDS) allows delivering virtualized applications, providing secure mobile and remote desktop access, and providing end users with the ability to run business-critical applications from the cloud.
Windows Server 2016 Remote Desktop Services delivers a wide array of flexibility for your end-users when accessing your organization’s infrastructure. This includes:
- Session-based virtualization – This is the traditional concept of leveraging a Windows Server to deliver a full-blown desktop to an end-user who needs to access applications, data, and services.
- Virtual Desktop Infrastructure (VDI) – With VDI, you can deliver individual virtual desktops to your end-users. This provides a great option for users who need a highly customized desktop with individualized toolsets
What other benefits and features does Windows Server Remote Desktop give to your end-users? Within the capabilities of RDS, you also have the ability to deliver:

- Desktops – Either with session-based virtualization or full-blown VDI desktops, you can deliver a full desktop to your end-users who need this functionality
- RemoteApps – Remote applications are often a much more efficient way of delivering applications to end users since you are only publishing the application and not the desktop environment. Often, an end-user only needs to access an application. If they only need to interact with an application, offering the full desktop is very inefficient from a resource perspective.
Windows Server 2016 Remote Desktop Services Best Practices
There are a few best practices with Windows Server 2016 Remote Desktop Services install. Consider the following as recommended by Microsoft:
- For your forward-facing environment including Web Access, Gateway, Connection Broker, and license server, use Windows Server 2019 when possible. Windows Server 2019 is backward compatible which means you can still use Windows Server 2016 or Windows Server 2012 R2 RD session hosts.
- Your RDSH servers need to be the same version of Windows, so you would need to group your RDSH servers into collections like Windows Server 2016 Session Hosts and Windows Server 2019 Session Hosts.
- If you upgrade your RD Session host, be sure to upgrade your license server as well.
- Upgrade your environment in the proper order
- For HA, make sure your connection brokers are at the same version of Windows Server
Windows Server 2016 Install Remote Desktop Services
Let’s now take a look at the process to install Windows Server 2016 RDS in your environment. With Windows Server 2016, Microsoft has made this process fairly easy and wizard-driven with the Server Manager console. Also, it automates the process of installing the needed roles so you don’t have to do this individually on the different servers for the Remote Desktop Services infrastructure.
My infrastructure is as follows:
- win2016rdgw – This will be used to host connection broker, gateway, and web access
- win2016rds – This is the session host server
Below, I have added both my RDSH server as well as the server that I am going to use to host the Connection Broker, Web Access, and Gateway. This is the server manager located on the RDS server. In server manager, right-click on All Servers and choose Add Server.
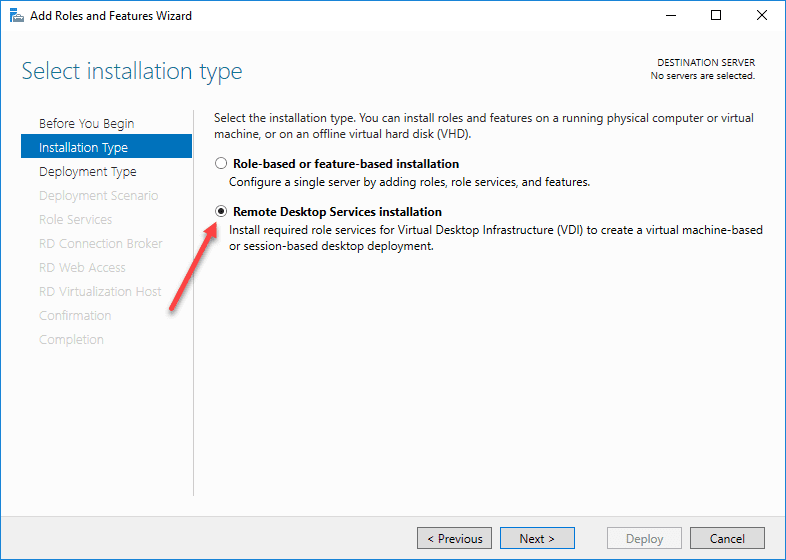
Next, in Server Manager, choose to Add Roles and Features. The wizard will ask you the installation type. Choose Remote Desktop Services installation.
I am performing the Standard deployment type here which allows you to deploy Remote Desktop Services across multiple servers.
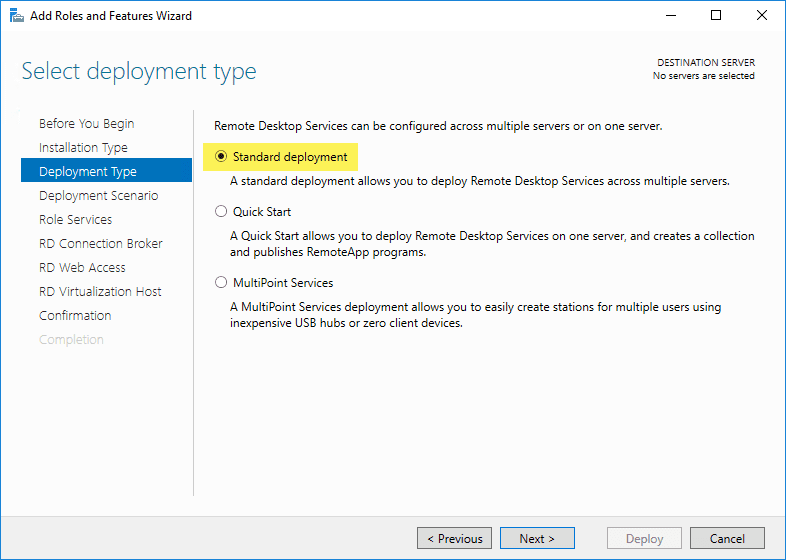
Next, you choose the deployment scenario. I am deploying a session-based desktop deployment so this is what I am choosing here. If you are doing Hyper-V and want to deploy VDI, you choose the Virtual machine-based desktop deployment.
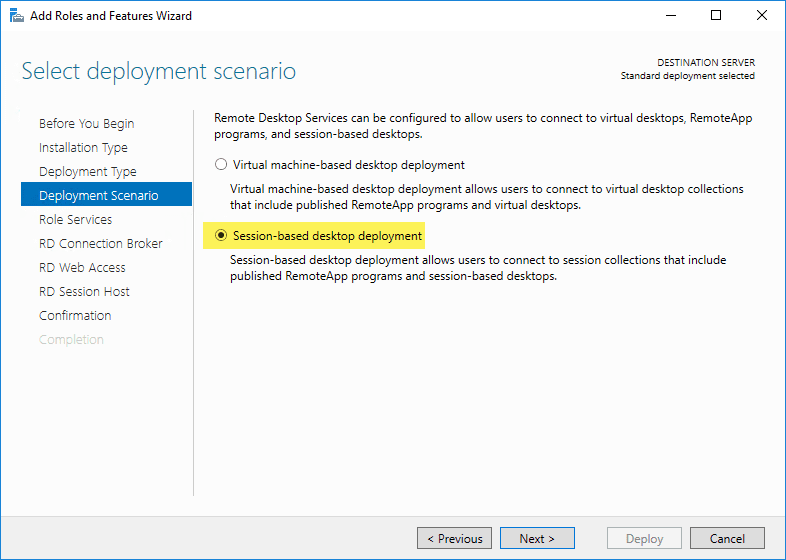
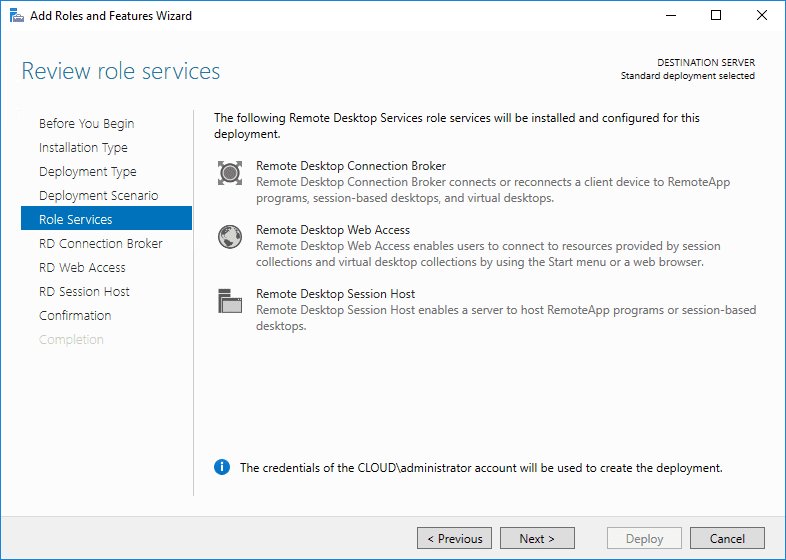
On the role services screen, the wizard displays the roles services that will be deployed as part of the Windows Server 2016 Remote Desktop Services installation.
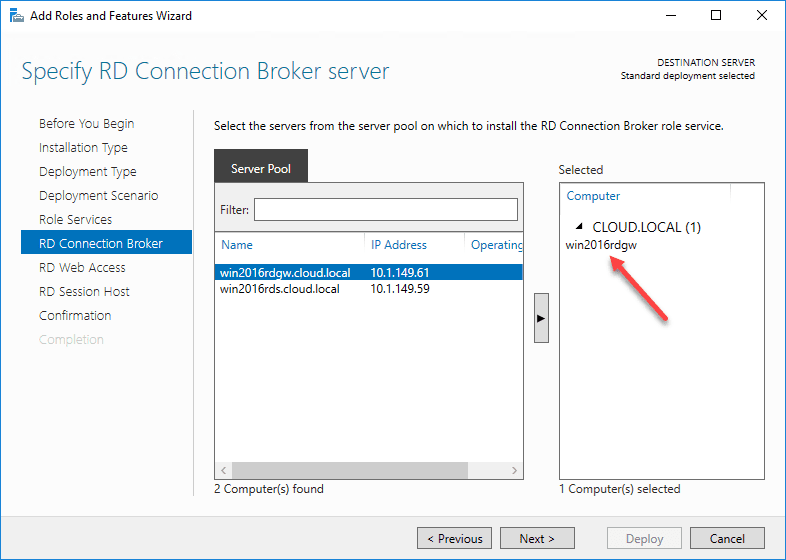
Next, you get to the part of the wizard where you start choosing the servers that you want to use for each role. The first choice is the RD Connection Broker.
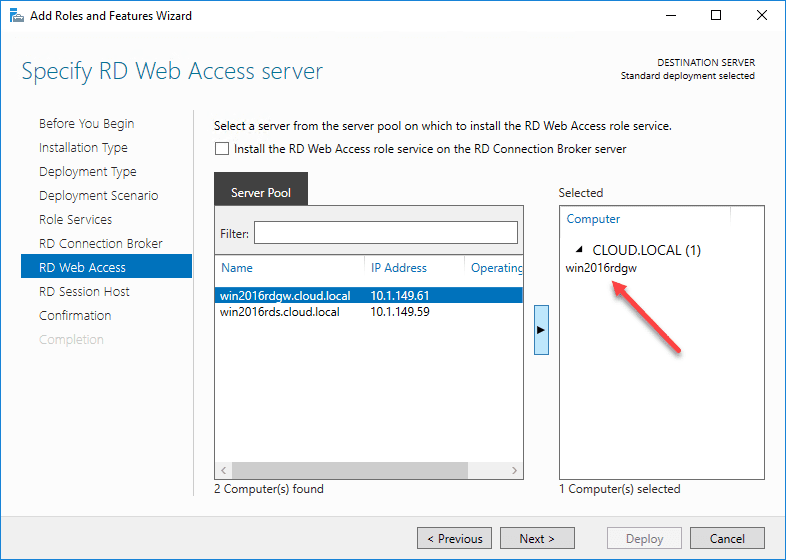
Next, is the RD Web Access Server.
Finally, you choose the RD Session Host servers.
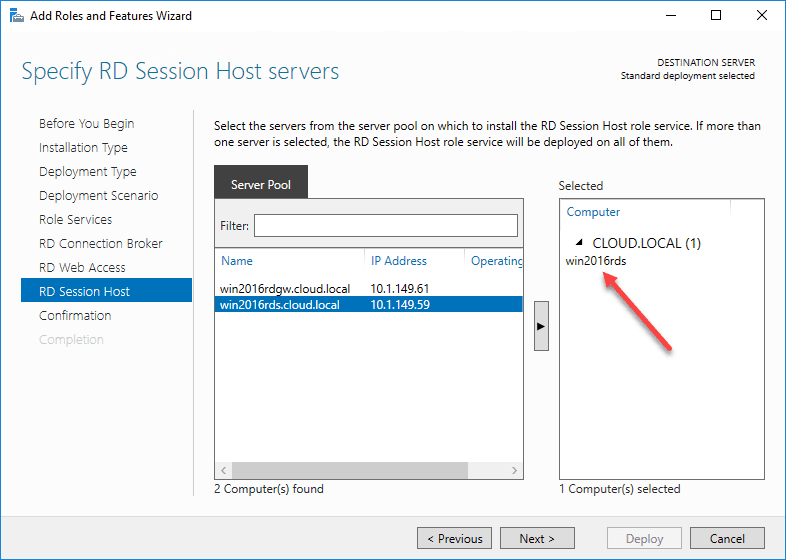
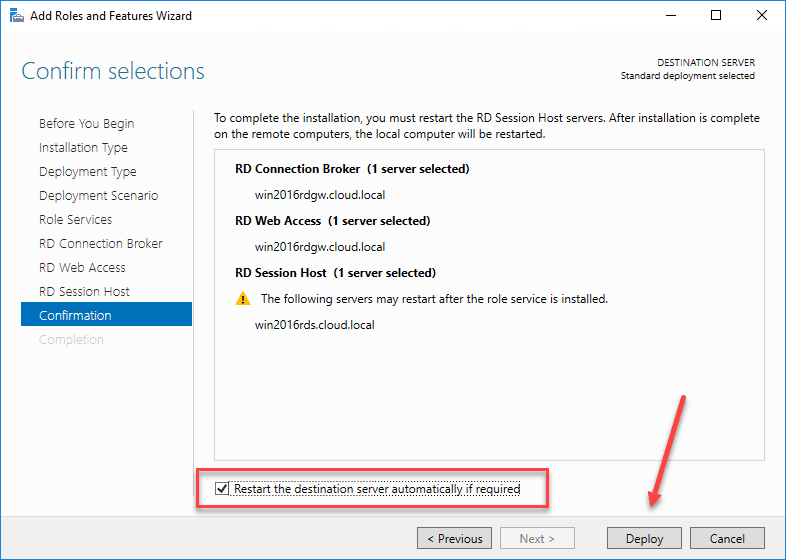
Now that we have selected the servers that will house each role, we can begin the deployment of the solution. I have selected the box to restart the destination server automatically if required. The Remote Desktop Services box that will host the RDSH role will need to be rebooted after the role service is installed.
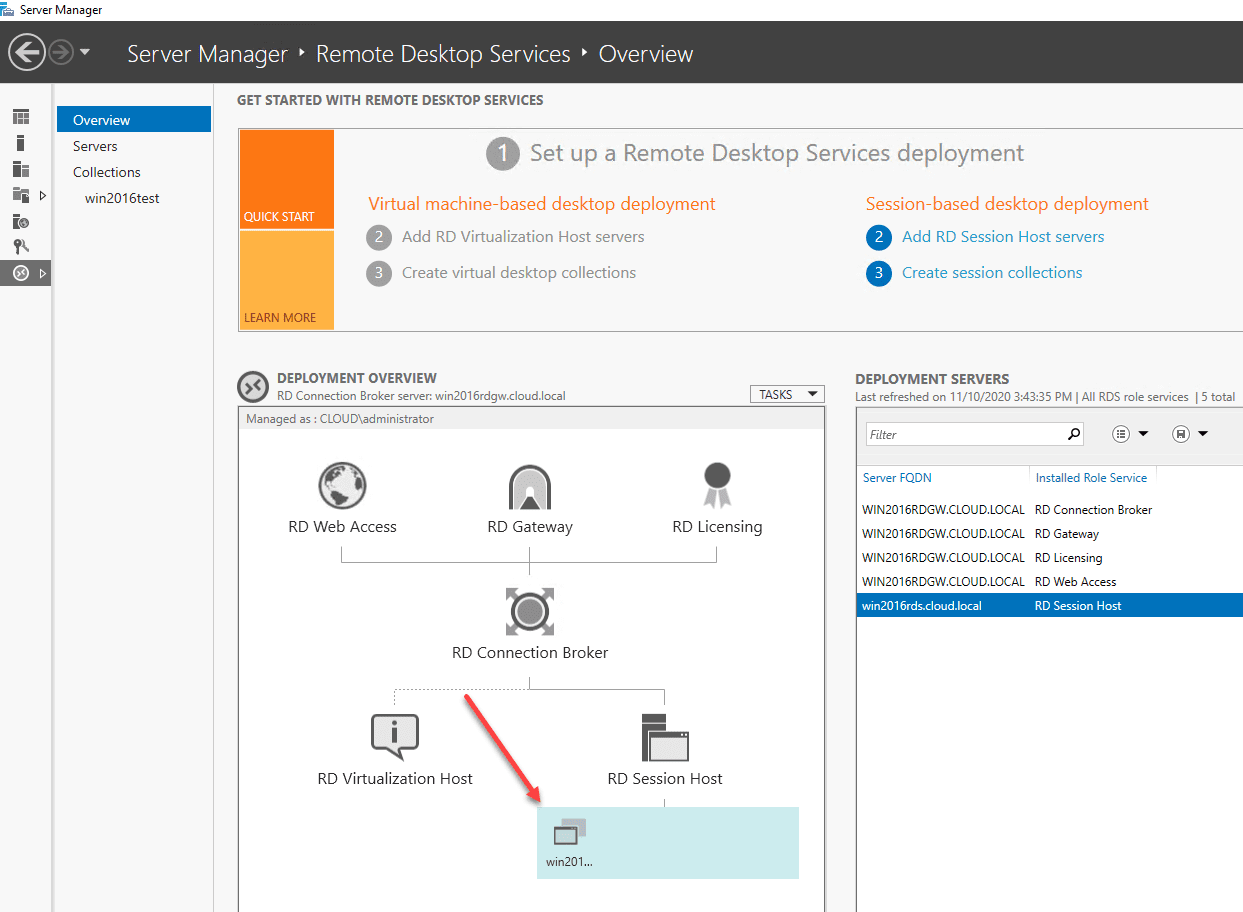
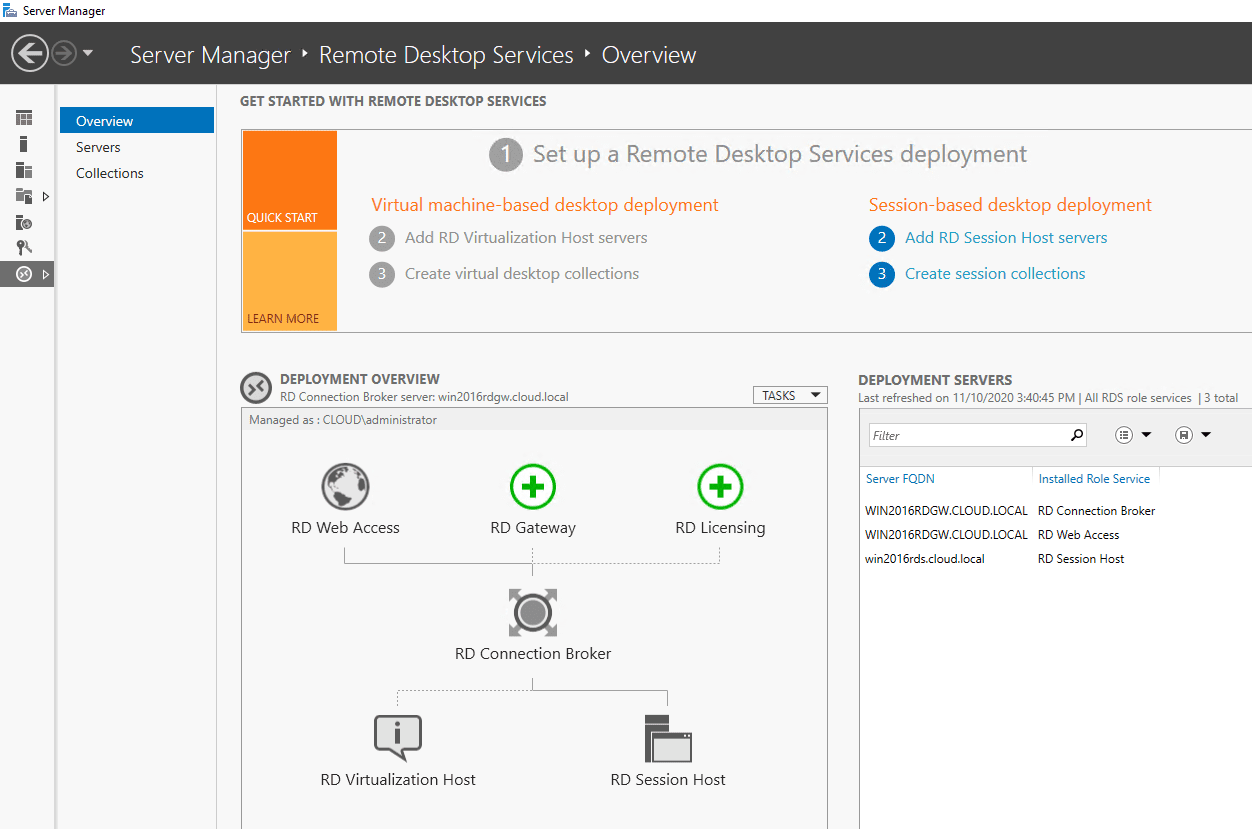
After the server comes back up from a reboot, go back to Server Manager and you will see the Remote Desktop Services role listed in Server Manager. Click this role and it will display the Set up a Remote Desktop Services deployment.
At this stage, we have merely installed the role services. So, we need to configure things such as the remote desktop gateway URL and setup the session collections. The items with a “green plus” sign need to be configured.
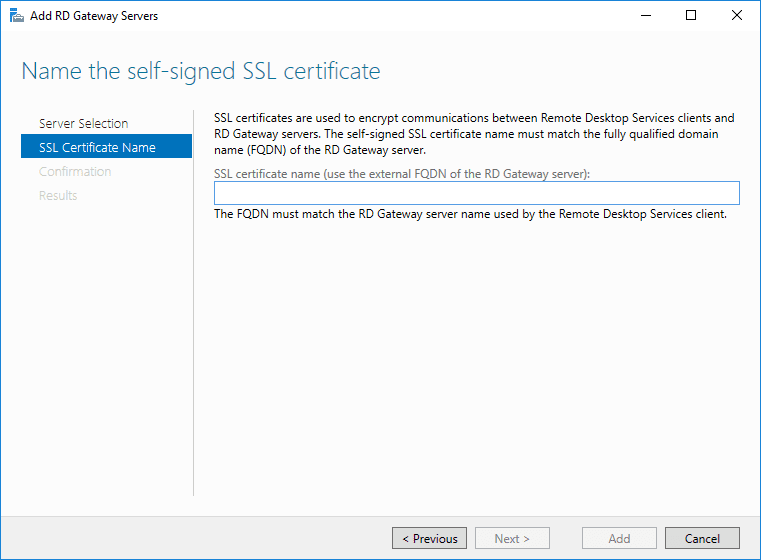
First I go through the Add RD Gateway Servers wizard. Adding the RD Gateway Server role to a server effectively installs the Network Policy Server role on the server chosen to serve as the RD Gateway.
You will be able to see the Remote Desktop Gateway Manager administrative console installed on the RDGW server. By default it will install the default Connection authorization policy and resource authorization policy on the gateway server. By default <DOMAIN>Domain Users will be authorized. You can tweak this.
Let’s go through the wizard. Enter the FQDN you want to use as the FQDN for the RD Gateway server.
After you are done configuring, click Add to finish the deployment.
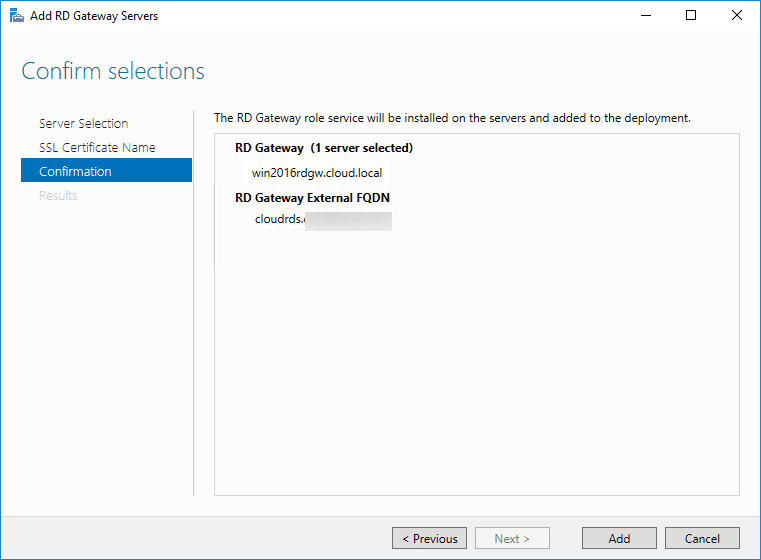
Next, is RD Licensing servers. Add the server that you want to use for RD licensing.
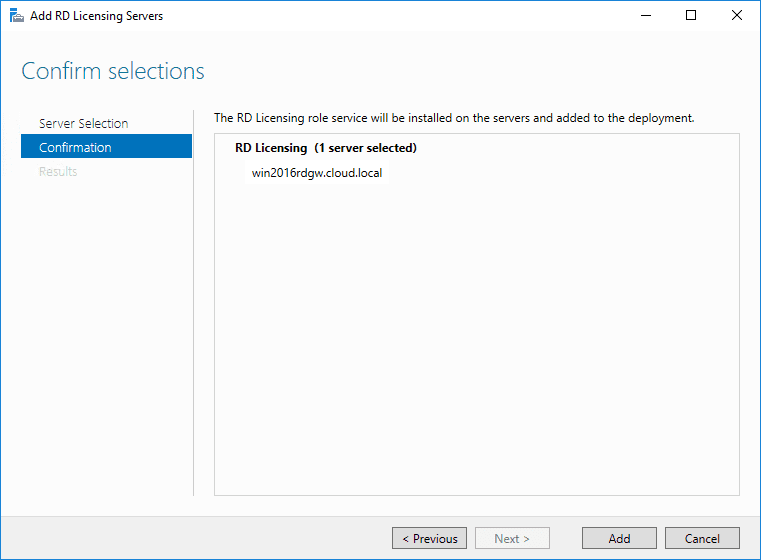
You will now note that all required roles are grey meaning they have been configured. You will see the servers selected and configured for each role under the Deployment Servers pane.
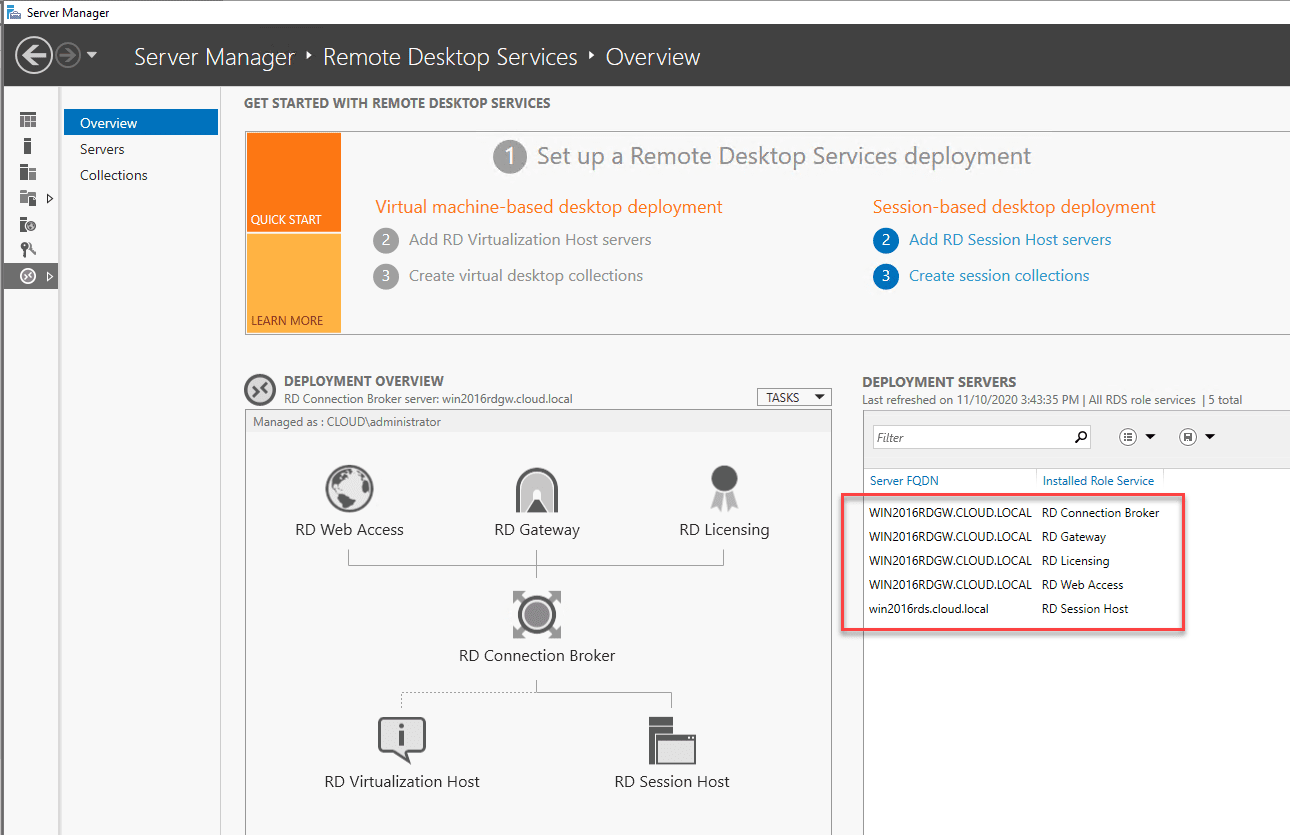
We now need to configure a session collection. This is another wizard that you launch from the deployment screen above under Session-based desktop deployment.
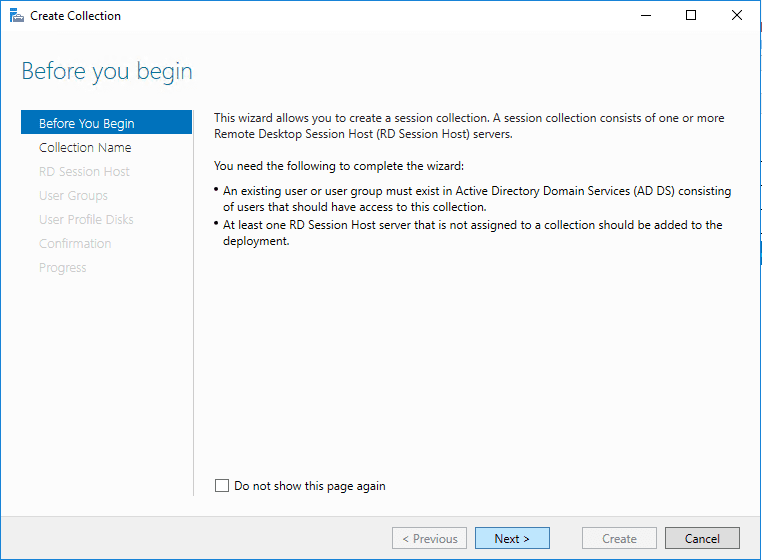
Choose the collection name.
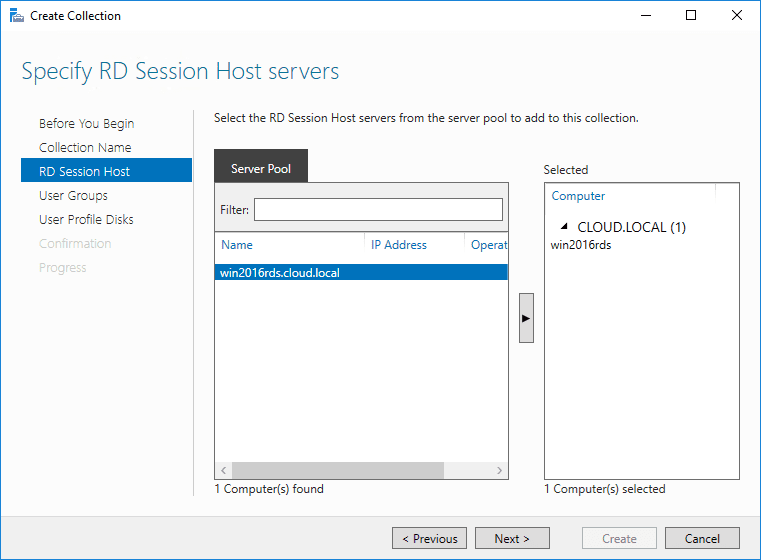
Select the RDSH server(s) that will participate in the session collection.
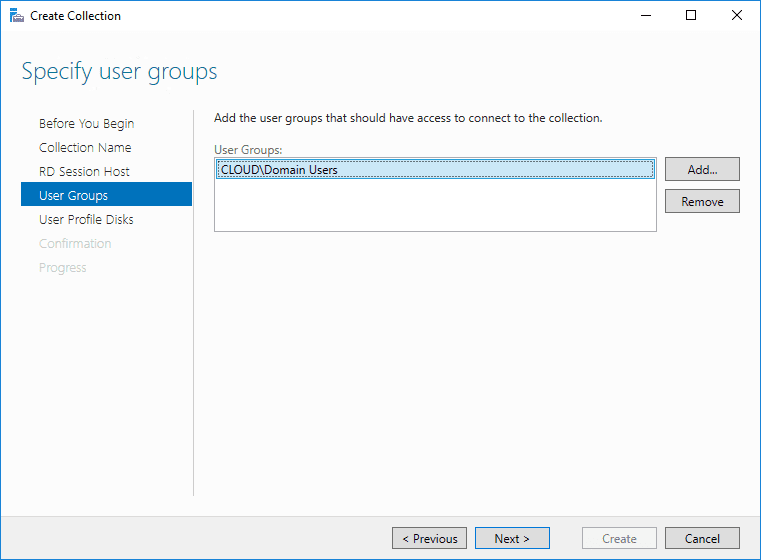
Specify user groups you want to have access to the session collection.
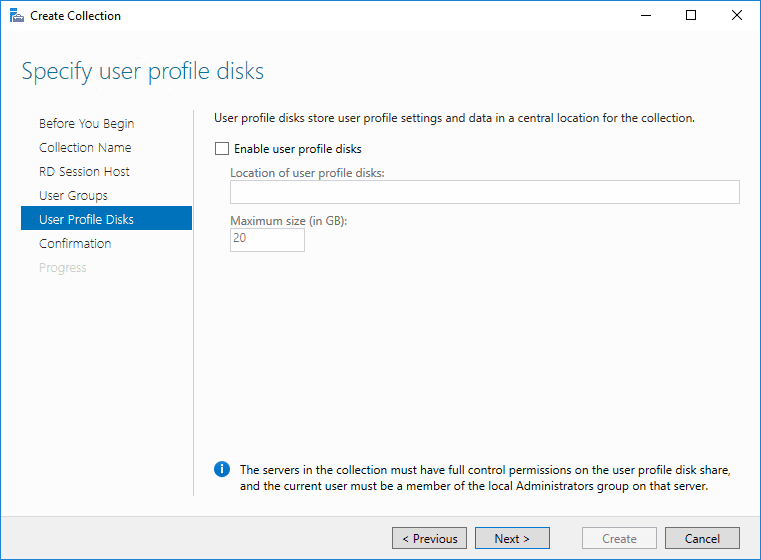
You can specify user profile disks to be used for profile settings and data in a central location for the collection if you want.
Finally, choose Create to create the session collection.
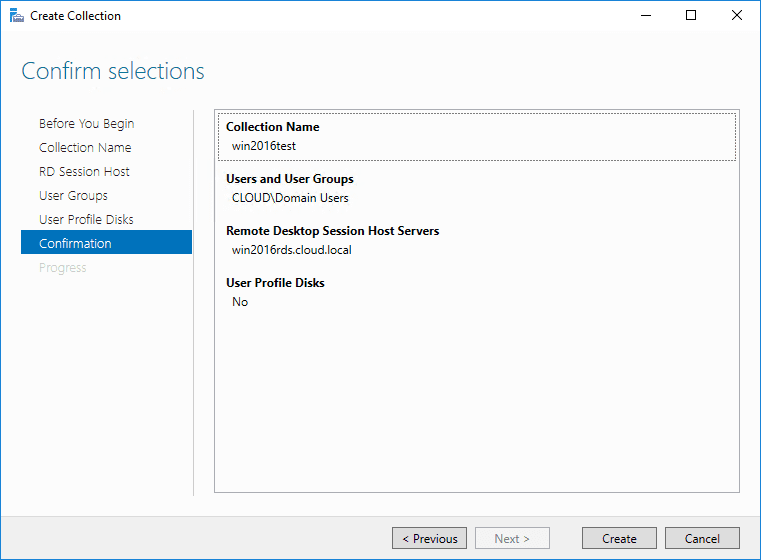
The new session collection is created successfully.
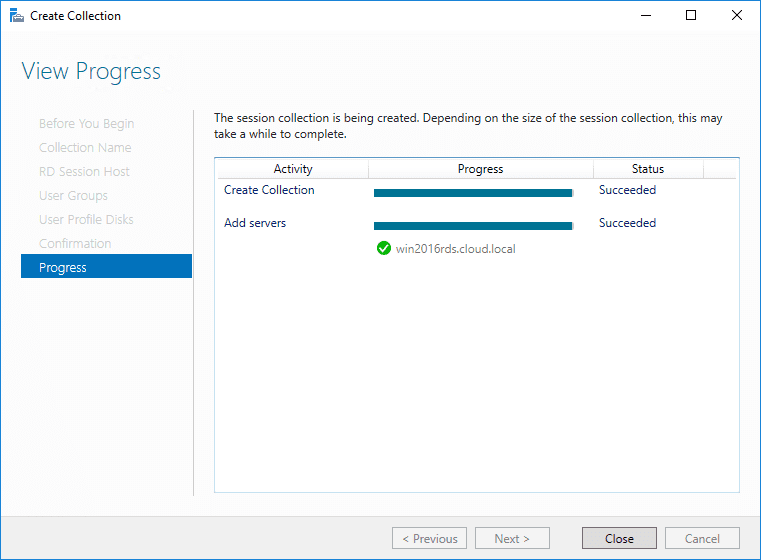
You now see the session collection in the deployment overview pane under your RD Session host.
Next Steps for Windows Server 2016 RDS Configuration
At this point, we have most of the configuration in place for a functional RDS environment with the exception of configuring the Remote Desktop Gateway Server with a proper SSL certificate. Without a proper SSL certificate from a CA, you will have to import the self-signed cert to all clients who will use the RDGW server to connect to the environment.
Additionally, you will most likely want to setup high-availability for the remote desktop gateway as well as add multiple remote desktop session hosts to the pool.
Check out my post I wrote not long ago covering the configuration of Remote Desktop Gateway Server in either Windows Server 2016 or 2019.
- Remote Desktop Gateway Server 2016 or 2019 Configuration
Concluding Thoughts
The Windows Server 2016 Install Remote Desktop Services process is made very intuitive with the built-in wizards found in Server Manager. It makes installing all the necessary roles needed for your Remote Desktop Services infrastructure straightforward.
Hopefully this walkthrough of the basic steps will help any who want to see what this process looks like. Additionally, this process is the exact same for Windows Server 2019 so not much has changed there.