Events to Monitor in a Windows Environment
O.K. you have purchased a SIEM, added your Windows servers and you’re ready to create your use-cases. You draw a blank. The amazing part about a SIEM is that you can build use-cases for literally thousands of scenarios. Unfortunately, however, the problem with a SIEM is that you have to create literally tens of thousands of alerts to monitor said use-cases. Monitoring for five failed logins followed by a successful login is great, but what good is the alert if the account locks after three failed attempts? Or if you have 10,000 users to monitor? To add to this, according to Verizon’s 2013 Data Breach Report, 76% of breaches involved stolen or weak credentials. So what to monitor for?
I find that it is often best to start with the basics-to report and/or alert on basic system functionality at the start, and to build more advanced use-cases based on abnormal behaviour outside of your companies policies.
Fortunately, the friendly folks at the NSA have written Spotting the Adversary with Windows Event Log Monitoring, a great guide that walks you through what they have determined are the 16 primary categories to focus on within Windows event logs to ensure system security. We will be going through the first eight in part I, and the second eight in part II.
- Clearing Event Logs
- Account Usage
- Remote Desktop Logon Detection
- Windows Defender Activities
- Application Crashes
- Software and Service Installation
- External Media Detection
- Pass the Hash Detection
- AppLocker
- System or Service Failures
- Windows Update Errors
- Kernel Driver Signing
- Group Policy Errors
- Mobile Device Activities
- Printing Services
- Windows Firewall
Before I start I want to clarify a not-so-obvious gotcha about Windows event logs for newcomers—Windows NT to Windows 2003 event IDs are identified via three digits; however, Windows Vista/Windows 2008 and beyond event IDs are identified by a four-digit ID. Therefore, any event ID with three digits is only applicable to Windows 2003 and before (and four digits beyond 2003.) Another useful tip is Randy’s Ultimate Windows Security, which provides detailed information on nearly every Windows security event.
1. Clearing Event Logs
This is often the first alert I will install in a client’s environment. There are very few reasons to clear the audit log directly, if the audit log is too large the event log’s maximum size should be set to a smaller size. As such, outside of an improperly configured device an event log would only be cleared to hide malicious activities. As such, a simple alert looking for the following events is usually sufficient.
 |
| Table-1: Event Log Cleared |
2. Account Usage
A proper set of alerts and reports for improper account activity is key to a useful SIEM. Setting an alert for X failed logins may drive your SOC crazy every Monday morning after a long weekend, but setting this threshold to alert when it occurs after-hours or on non-user systems could indicate malicious behaviour.
The size of your environment and your companies security policies will weigh heavily on the value of certain actions being an alert or a report—a team of 200 may have a weekly report on created users, whereas a team of 20,000 may have a daily report. As such I will make my recommendations based on generalizations of a business with 1,000 users:
- A weekly report for created users and users added to privileged groups;
- An alert for Security-enabled group modifications;
- An alert for service account failed logins or account lockouts, although this is prone to alert-spamming in the case of an incorrectly configured script or service continually trying to log in;
- An alert for three non-service failed logins to a non-user system after-hours;
- Interactive logins by a service account; and
- A successful user login from a non-whitelisted country
 |
| Table-2: Account Usage |
Of course this is not a complete list of recommended alerts or reports, rather a couple of examples to get you started.
3. Remote Desktop Logon Detection
Remote desktop alerts and reports are tricky. Datacenter jumpboxes are the most used machines—they are the most heavily used, store endless amounts of ‘temporary’ data, and are often the most sought after machine by a hacker. Typically once a hacker gains access to a jumpbox they have access to your most valuable resources, so tracking access is very important.
But how do you identify when access is malicious? In a 24h SOC access will be made 24 hours a day, so after-hour logins are not useful. This is something that I usually need to discuss in length with a client to really understand their environment before making remote desktop alerts. Some general concepts are:
- If your jumpbox is accessed from a specific subnet, alert when the connection is made from a different subnet, such as the DMZ.
- Alert when a service account attempts to connect to a jumpbox
- Alert or report for after-hour connections during non-change-window hours
 |
| Table-3: Remote Desktop Logins |
A remote desktop login is a standard login with a Logon Type of 10. Logon types are indicators of the login methodology used during the login—interactive, network, batch service, etc. They are essential for understanding how someone accessed a system. There is a large difference between a user logging in after hours via an RDP session and a new scheduled task.
4. Windows Defender Activities
This is pretty straight forward—a windows defender event shows detected malware/failed scan/failed update, etc. Essentially all events should be an alert.
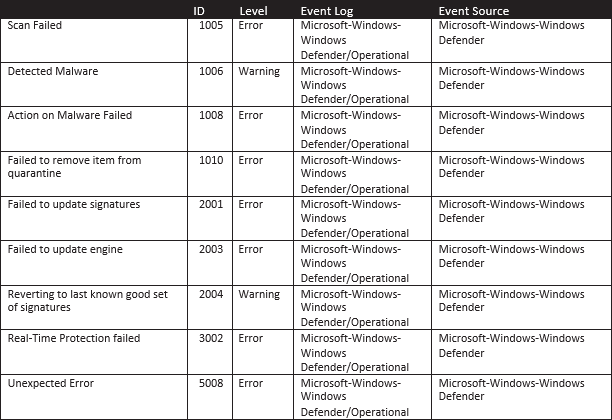 |
| Table-4: Windows Defender |
5. Application Crashes
Application crashes are difficult to judge whether they will be effective alerts or reports in a client’s environment. I tend to try to determine if the company has the resources available to perform an active investigation as towards why the application crashed. In the least a report or alert should be made for your high-value assets. That said, application crashes can be an indication of malicious code interfacing with an application to exploit it or replace it.
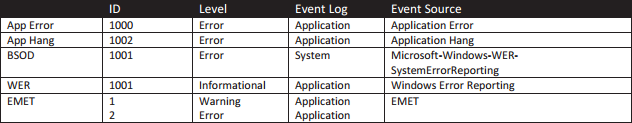 |
| Table-5: Application Crashes |
6. Software and Service Installation
Installed software and services should be at the least a report, and an alert for high priority assets (although change-window time frames can be excluded to avoid false-positives.)
 |
| Table-5: Software and Service Installation |
7. External Media Detection
There should always be a legitimate reason for plugging an external device into a high-value asset. An alert is recommended for medium to high severity events, and it is good to monitor external devices that are plugged in a new service is run within a few minutes on the system as this often indicates that something has executed off of the external media.
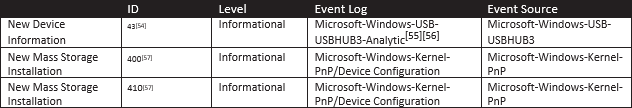 |
| Table-6: External Media Detection |
8. Pass the Hash Detection
Tracking user accounts for detecting Pass the Hash (PtH) requires creating a custom view with XML to configure more advanced filtering options. The event query language is based on XPath, a query language for selecting nodes from an XML document.
Spotting the Adversary has defined a QueryList described below that is limited in detecting PtH attacks. These queries focus on discovering lateral movement by an attacker using local accounts that are not part of the domain. The QueryList captures events that show a local account attempting to connect remotely to another machine not part of the domain. This event is a rarity so any occurrence should be treated as suspicious.
In the QueryList below, substitute the <DOMAIN NAME> section with the desired domain name.
<QueryList>
<Query Id=»0″ Path=»ForwardedEvents»>
<Select Path=»ForwardedEvents»>
*[System[(Level=4 or Level=0) and (EventID=4624)]]
and
*[EventData[Data[@Name=’LogonType’] and (Data=’3′)]]
and
*[EventData[Data[@Name=’AuthenticationPackageName’] = ‘NTLM’]]
and
*[EventData[Data[@Name=’TargetUserName’] != ‘ANONYMOUS LOGON’]]
and
*[EventData[Data[@Name=’TargetDomainName’] != ‘<DOMAIN NAME>’]]
</Select>
</Query>
</QueryList>
These XPath queries are used for the Event Viewer’s Custom Views, and are not applicable to a SIEM itself.
The successful use of PtH for lateral movement between workstations would trigger the following:
— Event ID 4624
— Event level Information
— LogonType of 3
— Logon method is NTLM authentication
— A not-domain logon and not ANONYMOUS account.
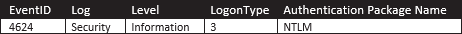 |
| Table-8: Pass the Hash Successful Logon Properties |
A failed PtH logon attempt would have all of the above properties except Event ID 4625 indicating a failed logon:
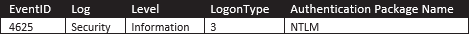 |
| Table-9: Pass the Hash Failed Logon Properties |
Conclusion
The NSA’s Spotting the Adversary with Windows Event Log Monitoring provides an excellent breakdown of key Windows events when creating an initial set of alerts and reports for key windows assets. Part two will break down the second half of the event categories
The NSA released a PDF entitled “Spotting the Adversary with Windows Event Log Monitoring” earlier this year. While there’s a bit of irony in this, given the whole Snowden story that followed the release of this document, the PDF is still chock full of great information on what to watch for in an effort to “spot the adversary.” Now, I must warn you – there’s good news and bad news that comes with this document.
The good news is it’s probably one of the most detailed documents I’ve seen in a long time. Everything from setting up Event Subscriptions, to a hardened use of Windows Remote Management, including the use of authentication and firewalls, this document tells you how to securely setup an environment where you can natively consolidate and monitor event log based entries.
In addition, the NSA goes onto cover a number of areas that should be monitored – complete with event IDs – which I’ve broken into two sections.
Machine-specific issues – which can be indications of malicious activity
- Application Crashes
- System or Service Failures
- Kernel and Device Signing
- The Windows Firewall
Administrator Activity – specific actions performed that may be suspect
- Clearing of Event Logs
- Software and Service Installation
- Remote Desktop Logon
- Account Usage
OK – so what’s the bad news? The bad news is you’re still left to sort out a TON of event log detail and interpret whether the entries are a problem or not.
The real value of event logs is being able to see what specifically has changed. In some cases, like a service failure, it’s easy to see – the once working service now no longer is. Same goes for something simple like the clearing of an event log – you’ll know Joe Smith cleared it at a specific date and time. So what’s the big deal then? Well, when you start looking at more advanced activity, like Account Usage, event logs will only take you so far. Let’s take the one example the NSA document hasn’t taken into consideration – changing the audit policies themselves. Think about it. The entire setup spanning 67 pages only works IF auditing of each type of activity is enabled. So what happens when the “adversary” simply turns off the auditing of, say, Account Usage, and then performs some dastardly deed?
You’ll never catch it. The reason? Changes to Group Policy only show up in the events as a change to the policy, but lack detail on exactly what was changed within the Group Policy.
To truly have a grasp on whether you have an “adversary” within or not and, if so, what that adversary is doing, you’re going to require a solution that not only collects events, but can correlate them into something intelligent. Your solution should:
- Consolidate events
- Focus on the events you are concerned about
- Provide comprehensive detail about the changes to your systems, security and data
The NSA doc will take you to about 2 and a quarter of the three bullets, but it’s the rest of that last bullet that is going to make the difference. Knowing a change to a server was made last night at 11:53pm is well and fine, but knowing exactly what was changed is going to make all the difference in the world when trying to spot and address your enemies within.
Nick Cavalancia is a technical evangelist and founder of IT consulting firm Techvangelism. Nick has over 20 years of enterprise IT experience, 10 years as a tech marketing executive and is an accomplished technology writer, consultant, trainer, speaker, and columnist. He has authored, co-authored and contributed to over a dozen books on Windows, Active Directory, Exchange and other Microsoft technologies and has spoken at many technical conferences on a wide variety of topics.
Previously, Nick has held executive marketing positions at ScriptLogic (acquired by Quest, now DELL Software), SpectorSoft and Netwrix where he was responsible for the global messaging, branding, lead generation and demand generation strategies to market technology solutions to an IT-centric customer base.
In this webinar I will take you through the guidance in NSA’s Spotting the Adversary with Windows Event Log Monitoring. I’m sure you will agree that it’s an intriguing and highly targeted topic for folks like us who geek out on Windows Security Log Event IDs. This in-depth 54-page document is from the NSA’s Information Assurance Directorate. And when I say in-depth, I mean it.
- Application Whitelisting
- Application Crashes
- System or Service Failures
- Windows Update Errors
- Windows Firewall
- Clearing Event Logs
- Software and Service Installation
- Account Usage
- Kernel Driver Signing
- Group Policy Errors
- Windows Defender Activities
- Mobile Device Activities
- External Media Detection
- Printing Services
- Pass the Hash Detection
- Remote Desktop Logon Detection
It definitely has its share of recommendations that only highly classified agencies with large budgets could hope to implement but there’s plenty of useful knowledge and recommendations as well. We will focus on areas that are relevant and practical for the private and corporate sectors.
In particular I think it’s interesting that this document goes beyond just the security log and points out events in other Windows event logs that have high-security value. I’ve been thinking for a long time that I need to show the community some of these other logs and this is a great opportunity to do it.
I’ll also point out areas I think should be addressed differently or additional areas that are missing from the guidance. EventTracker is an apropos sponsor for this event because EventTracker has a purpose-built knowledge and reporting pack for this NSA guidance. And with EventTracker you can avoid the management heavy burden of implementing Windows event forwarding which figures heavily in NSA guidance.
This is will be an interesting real training for free ™ event. Please register now.
| First Name: |
Required |
| Last Name: |
Required |
| Work Email: |
|
| Phone: | Required |
| Job Title: | Required |
| Organization: | Required |
| Country: |
Required |
| City: | Required |
| State: |
Required |
| Street Address: | |
| Zip : | |
| Industry : | |
|
Your information will be shared with the sponsor.
By clicking «Submit», you’re agreeing to our Privacy Policy and consenting to be contacted by us and the sponsor. |
Skip to content
The NSA released a PDF entitled “Spotting the Adversary with Windows Event Log Monitoring” earlier this year. The good news is it’s probably one of the most detailed documents I’ve seen in a long time. Everything from setting up Event Subscriptions, to a hardened use of Windows Remote Management, including the use of authentication and firewalls, this document tells you how to securely setup an environment where you can natively consolidate and monitor event log based entries. In addition, the NSA goes onto cover a number of areas that should be monitored – complete with event IDs:
http://www.redblue.team/2015/09/spotting-adversary-with-windows-event.html
http://www.redblue.team/2015/09/spotting-adversary-with-windows-event_21.html
Event forwarding guidance: https://github.com/iadgov/Event-Forwarding-Guidance
Malware archeology cheat sheets: http://www.malwarearchaeology.com/cheat-sheets/
Machine-specific issues – which can be indications of malicious activity
- Application Crashes
- System or Service Failures
- Kernel and Device Signing
- The Windows Firewall
Administrator Activity – specific actions performed that may be suspect
- Clearing of Event Logs
- Software and Service Installation
- Remote Desktop Logon
- Account Usage
The bad news is you’re still left to sort out a TON of event log detail and interpret whether the entries are a problem or not.
Additionally: Changes to Group Policy only show up in the events as a change to the policy, but lack detail on exactly what was changed within the Group Policy.
To truly have a grasp on whether you have an “adversary” within or not and, if so, what that adversary is doing, you’re going to require a solution that not only collects events, but can correlate them into something intelligent. Your solution should:
- Consolidate events
- Focus on the events you are concerned about
- Provide comprehensive detail about the changes to your systems, security and data
Three software solutions:
- Netwrix Auditor for AD
- Dell change auditor for AD
- IBM QRadar (SIEM)
Splunk (SIEM) : Splunk Windows Auditing using the NSA guide: https://github.com/anthonygtellez/windows_auditing
- http://blogs.splunk.com/2016/06/21/spotting-the-adversary-with-splunk/ https://conf.splunk.com/session/2015/conf2015_MGough_MalwareArchaelogy_SecurityCompliance_FindingAdvnacedAttacksAnd.pdf
- https://github.com/MattUebel/splunk_UF_hardening
- http://conf.splunk.com/files/2016/recordings/universal-forwarder-security-dont-input-more-than-data-into-your-splunk-environment.mp4
- http://conf.splunk.com/files/2016/slides/universal-forwarder-security-dont-input-more-than-data-into-your-splunk-environment.pdf
MS white-paper best practices to secure AD: http://aka.ms/bpsadtrd
MS Advanced threat analytics (MS ATA): https://www.microsoft.com/en-us/server-cloud/products/advanced-threat-analytics/
Windows Event IDs useful for intrusion detection:
| Category | Event ID | Description |
|---|---|---|
| User Account Changes | 4720 | Created |
| 4722 | Enabled | |
| 4723 | User changed own password | |
| 4724 | Privileged User changed this user’s password | |
| 4725 | Disabled | |
| 4726 | Deleted | |
| 4738 | Changed | |
| 4740 | Locked out | |
| 4767 | Unlocked | |
| 4781 | Name change | |
| Domain Controller Authentication Events | 4768 | TGT was requested |
| 4771 | Kerberos pre-auth failed | |
| 4772 | TGT request failed | |
| Logon Session Events | 4624 | Successful logon |
| 4647 | User initiated logoff | |
| 4625 | Logon failure | |
| 4776 | NTLM logon failed | |
| 4778 | Remote desktop session reconnected | |
| 4779 | Remote desktop session disconnected | |
| 4800 | Workstation locked | |
| 4801 | Workstation unlocked | |
| Domain Group Policy | 4739 | Domain GPO changed |
| 5136 | GPO changed | |
| 5137 | GPO created | |
| 5141 | GPO deleted | |
| Security | 1102 | Event log cleared |
| Software and Service Installation | 6 | New Kernel Filter Driver |
| 7045 | New Windows Service | |
| 1022, 1033 | New MSI File Installed | |
| 903, 904 | New Application Installation | |
| 905, 906 | Updated Application | |
| 907, 908 | Removed Application | |
| 4688 | New Process Created | |
| 4697 | New Service Installed | |
| 4698 | New Scheduled Task | |
| External Media Detection | 43 | New Device Information |
| 400 | New Mass Storage Installation | |
| 410 | New Mass Storage Installation |
| Group Changes | Created | Changed | Deleted | Members | ||
|---|---|---|---|---|---|---|
| Added | Removed | |||||
| Security | Local | 4731 | 4737 | 4734 | 4732 | 4733 |
| Global | 4727 | 4735 | 4730 | 4728 | 4729 | |
| Universal | 4754 | 4755 | 4758 | 4756 | 4757 | |
| Distribution | Local | 4744 | 4745 | 4748 | 4746 | 4747 |
| Global | 4749 | 4750 | 4753 | 4751 | 4752 | |
| Universal | 4759 | 4760 | 4763 | 4761 | 4762 |
IT Pro: 27 years experience for large companies — Technical manager and solution architect: Directory services and Identity Managemen expert, Azure AD, Office 365, Azure infrastructures, Microsoft AD Security (ADDS,ADFS,ADCS), PowerShell, Quest solutions architect. Operating systems (Win/Lin). Unix and Microsoft interoperability. Data center Operations. Company integrations. Network architectures. Virtualization and storage infrastructures. HP/Dell servers deployments.
Certifications: MCSE, MCPs, MCITS, ITIL, VCP, CCNA, CyberArk
View more posts
29.04.2014
•
Views
Share
Embed
Flag
Spotting the Adversary with Windows Event Log Monitoring
Spotting the Adversary with Windows Event Log Monitoring
SHOW MORE
SHOW LESS
ePAPER READ
DOWNLOAD ePAPER
- TAGS
- winrm
- firewall
- server
- collector
- authentication
- configuration
- subscription
- domain
- policies
- subscriptions
- spotting
- adversary
- monitoring
- www.nsa.gov
nsa.gov
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
START NOW
-
More documents
-
Similar magazines
-
Info
National Security Agency/Central Security Service Information Assurance Directorate <strong>Spotting</strong> <strong>the</strong> <strong>Adversary</strong> <strong>with</strong> <strong>Windows</strong> <strong>Event</strong> <strong>Log</strong> <strong>Monitoring</strong> February 28, 2013 A product of <strong>the</strong> Network Components and Applications Division TSA-13-1004-SG
- Page 2 and 3: Contents 1 Introduction ………..
- Page 4 and 5: Table 21: WinRM Version Update URLs
- Page 6 and 7: 1 Introduction It is increasingly d
- Page 8 and 9: A policy, named Generate security a
- Page 10 and 11: Create two new groups: EventSources
- Page 12 and 13: Figure 1: Creating a Subscription F
- Page 14 and 15: General Event Descriptions General
- Page 16 and 17: False ForwardedEvents 2 1 1000
- Page 18 and 19: Figure 8: Enabling WinRM listeners
- Page 20 and 21: Figure 11: Configuration of Subscri
- Page 22 and 23: alternate methods to enable WinRM f
- Page 24 and 25: netsh advfirewall firewall set rule
- Page 26 and 27: 5985:TCP:192.168.1.2:Enabled:Window
- Page 28 and 29: 3.1 WinRM Authentication Hardening
- Page 30 and 31: 3.1.4 Negotiate Authentication Nego
- Page 32 and 33: 3.2 Security Log in Windows XP By d
- Page 34 and 35: Windows 7 ID Level Event Log Event
- Page 36 and 37: ID Level Event Log Event Source Fir
- Page 38 and 39: Windows 7 ID Level Event Log Event
- Page 40 and 41: would have a LogonType of 3 using N
- Page 42 and 43: The maximum log file sizes are inte
- Page 44 and 45: Node Subscription SubscriptionId De
- Page 46 and 47: Logons SourceInitiated Non-Kerberos
- Page 48 and 49: MSI Packages Installed (MsiPackages
- Page 50 and 51: WhitelistingLogs SourceInitiated Ap
- Page 52 and 53:
wecutil ss SubscriptionId /cf:Rende
- Page 54 and 55:
domain administrator privileges. It
- Page 56 and 57:
The above command will get the publ
- Page 58 and 59:
Config MaxEnvelopeSizekb = 150 MaxT
- Page 60 and 61:
Parameters RootSDDL MaxConcurrentOp
- Page 62 and 63:
Registry Values HKLMSOFTWAREPolic
- Page 64 and 65:
:: WinRM does not need to be Locals
- Page 66 and 67:
The listing below is not an exhaust
- Page 68 and 69:
WinRM logs all activities to Micros
- Page 70 and 71:
ID Level Event Log Event Source Ope
- Page 72:
Figure 24: Subscription Manager Pol
show all
Delete template?
Are you sure you want to delete your template?
Save as template?
Title
Description
no error
products
- FREE
- adFREE
- WEBKiosk
- APPKiosk
- PROKiosk
Resources
- Blog
- API
- Help & Support
- Status
- tuxbrain.com
- ooomacros.org
- nubuntu.org
Company
- Contact us
- Careers
- Terms of service
- Privacy policy
- Cookie policy
- Cookie settings
- Imprint
Terms of service
Privacy policy
Cookie policy
Cookie settings
Imprint
Change language
Made with love in Switzerland
© 2023 Yumpu.com all rights reserved
Skip to main content
Information Assurance Directorate: Spotting the Adversary with Windows Event Log Monitoring: National Security Agency: 9781508532323: Amazon.com: Books
-
Books
›
-
Reference
This item cannot be shipped to your selected delivery location. Please choose a different delivery location.
|
This item cannot be shipped to your selected delivery location. Please choose a different delivery location. |

There was a problem loading your book clubs. Please try again.

Join or create book clubs
Choose books together
Track your books
Bring your club to Amazon Book Clubs, start a new book club and invite your friends to join, or find a club that’s right for you for free.

Download the free Kindle app and start reading Kindle books instantly on your smartphone, tablet, or computer — no Kindle device required. Learn more
Read instantly on your browser with Kindle for Web.
Using your mobile phone camera — scan the code below and download the Kindle app.


Flip to back Flip to front
Listen Playing… Paused You’re listening to a sample of the Audible audio edition.
Learn more
- Paperback
$17.79
1 Used from $16.81 5 New from $17.03
- Mass Market Paperback
from $56.98
2 Used from $56.98 1 New from $56.98
Purchase options and add-ons
It is increasingly difficult to detect malicious activity, which makes it extremely important to monitor and collect log data from as many useful sources as possible. This paper provides an introduction to collecting important Windows workstation event logs and storing them in a central location for easier searching and monitoring of network health. The focus of this guidance document is to assist United States Government and Department of Defense administrators in configuring central event log collection and recommend a basic set of events to collect on an enterprise network using Group Policy.
-
Publication date
June 26, 2015
-
Dimensions
8.5 x 0.13 x 11 inches
Product details
- Publisher
:
CreateSpace Independent Publishing Platform (June 26, 2015) - Language
:
English - Paperback
:
54 pages - ISBN-10
:
150853232X - ISBN-13
:
978-1508532323 - Item Weight
:
5.4 ounces - Dimensions
:
8.5 x 0.13 x 11 inches
- Best Sellers Rank: #1,634,586 in Books (See Top 100 in Books)
- #134,296 in Reference (Books)
- Customer Reviews:
Brief content visible, double tap to read full content.
Full content visible, double tap to read brief content.
Videos
Help others learn more about this product by uploading a video!
Upload your video
Customer reviews
3 global ratings
Top review from the United States
There was a problem filtering reviews right now. Please try again later.
Reviewed in the United States 🇺🇸 on May 3, 2020
Great product and service!!!



















