I have upgraded my Inteliij IDEA 2019.2 recently and I am getting below error, if I try to pull from my IDE
Git Pull Failed: unable to access ‘https://github.xxx.com/app-Hello-USD/DGS.git/’: SSL certificate problem: self signed certificate in certificate chain.
Could some one help me what option I have to enable.
Thanks
CrazyCoder
382k168 gold badges964 silver badges881 bronze badges
asked Aug 2, 2019 at 13:35
1
git config --global http.sslVerify false
answered Aug 2, 2019 at 21:42
CrazyCoderCrazyCoder
382k168 gold badges964 silver badges881 bronze badges
7
To expand on the answer of @CrazyCoder.
This usually happens because your Git repository server is hosted inside a private network and uses a locally generated (self signed) TLS certificate. Because this certificate is not from a «trusted» source, most software will complain that the connection is not secure.
So you need to disable SSL verification on Git to clone the repository and immediately enable it again, otherwise Git will not verify certificate signatures for any other repository.
- Disable SSL verification on Git globally:
git config --global http.sslVerify false - Clone your repository:
git clone <your repo> - Enable SSL verification on Git globally:
git config --global http.sslVerify true - Change directory into your repo:
cd <your repo> - Disable SSL verification only on your repository:
git config --local http.sslVerify false
In the first step, when turning off SSL verification, if you’re getting this error:
warning: http.sslverify has multiple values
error: cannot overwrite multiple values with a single value
Use a regexp, --add or --replace-all to change http.sslVerify.
Open your .gitconfig file and remove duplicate http.sslverify lines.
answered Feb 23, 2022 at 11:29
Boško BezikBoško Bezik
1,4002 gold badges17 silver badges33 bronze badges
We can use window certificate storage mechanism.
Please try this
git config —global http.sslbackend schannel
answered Sep 15, 2022 at 14:25
Kyu LeeKyu Lee
1211 silver badge3 bronze badges
3
If you want to add the self-signed cert, export the cert you want as a Base-64 encoded .CER file. Locate your Git cert.pem file (for me it is in C:Program FilesGitusrsslcert.pem). Open up your .CER file in a text-editor, and copy/paste the contents at the end of your cert.pem file. Save the file. Then open up your console and type
git config --global http.sslCAInfo "C:Program FilesGitusrsslcert.pem"
answered Mar 16, 2022 at 16:29
codeMonkeycodeMonkey
3,8422 gold badges34 silver badges49 bronze badges
1
If you are connected to a VPN, please try without the VPN. I go this error because of this issue.
answered Jun 30, 2022 at 11:38
From my chief of IT: this can be fixed by disabling SSL checking in the git config for the affected repositories. This should not require elevated privileges to complete.
git config http.sslVerify "false"
This command did not require use of the —global argument.
answered May 11, 2022 at 13:48
brethvoicebrethvoice
3161 gold badge4 silver badges14 bronze badges
1
For github.com you may change protocol from HTTPS to SSH:
-
open .git/config
-
fix url in [remote «origin»] block
old: url = https://github.com/myname/proj1
new: url = git@github.com:myname/proj1.git
answered Dec 22, 2022 at 5:03
VladimirVladimir
5,7712 gold badges29 silver badges35 bronze badges
If you’re using a self-signed certificate on your Bitbucket server, you may receive SSL certificate errors when you try to perform certain actions. This page will help you resolve these errors.
Problem
When trying to perform a clone using instructions stated in Debug logging for Git operations on the client the following error is reported:
$ export GIT_CURL_VERBOSE=1
$ git clone https://username@git.example.com/scm/repository.git
Cloning into 'repository'...
* Couldn't find host git.example.com in the _netrc file; using defaults
* Adding handle: conn: 0x22a7568
* Adding handle: send: 0
* Adding handle: recv: 0
* Curl_addHandleToPipeline: length: 1
* - Conn 0 (0x22a7568) send_pipe: 1, recv_pipe: 0
* About to connect() to git.example.com port 443 (#0)
* Trying 10.253.136.142...
* Connected to git.example.com (10.253.136.142) port 443 (#0)
* successfully set certificate verify locations:
* CAfile: C:Program Files (x86)Git/bin/curl-ca-bundle.crt
CApath: c:/Users/username/Downloads
* SSL certificate problem: self signed certificate in certificate chain
* Closing connection 0
fatal: unable to access 'https://username@git.example.com/scm/repository.git': SSL certificate problem: self signed certificate in certificate chain
Cause
This is caused by git not trusting the certificate provided by your server.
Workaround
One possible workaround is to temporary disable SSL check for your git command in case you only need to perform a one time clone:
GIT_SSL_NO_VERIFY=true git clone https://username@git.example.com/scm/repository.git
or
git remote add origin <gitrepo>
git config --global http.sslVerify falseThe workaround is intended to be used for one-time only operations and not to be used frequently. Removing the SSL verification disproves the whole concept of having SSL implemented.
Resolution
Step1: Get a self-signed certificate of the remote server
There is multiple ways of exporting the certificate, Either from the Browser or using the OpenSSL command
Get Certificate using OpenSSL
Get Certificate using OpenSSL
$ echo | openssl s_client -servername NAME -connect HOST:PORT |
sed -ne '/-BEGIN CERTIFICATE-/,/-END CERTIFICATE-/p' > certificate.pemGet Certificate using the Web browser
Export Certificate in MAC
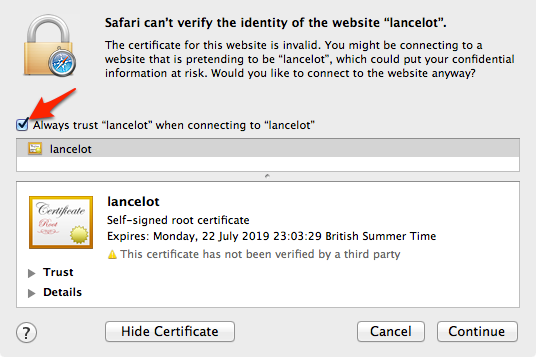
Trust Certificate in your browser
To trust a self-signed certificate, you need to add it to your Keychain.
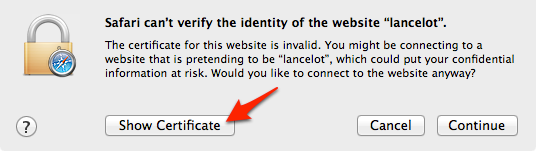
The easiest way to do that is to open the site in question in Safari, upon which you should get this dialog box:
Click ‘Show Certificate’ to reveal the full details:
Export Certificate in .pem format
Git doesn’t use the Mac OS X keychain to resolve this, so you need to trust the certificate explicitly.
- If you haven’t done so already, follow the steps in ‘Trust certificate in your browser, above
- Open Applications > Keychain Access and select ‘Certificates’ in the lower-left pane
- Type the website into the Search field in the top-right
- Select the certificate entry for the website, then in the menu click File > Export Items
- In the Save dialog, change ‘File Format’ to ‘Privacy Enhanced Mail (.pem)’ and save the file somewhere on your drive
Export Certificate From Firefox
- Access the URL of the remote server
- Click the Open padlock in the address bar.
- Click the arrow beside OpenConnection Secure.
- Click More Information. The OpenPage Info dialog box opens.
- Click View Certificate.
- The Certificate page opens.
- Scroll down to the Miscellaneous section.
- In the Download row, click the PEM (cert) link.
- In the dialog box that opens, click OK to save the certificate file to a known location.
- Navigate to the location for saving the file, and then click Save.
Step 2: Configure Git to trust the Certificate
For MAC/Linux:
Once the certificate is saved on the client you can instruct your git client to use it to trust the remote repository by updating the local git config:
# Initial clone
GIT_SSL_CAINFO=/path/to/certificate.pem
git clone https://username@git.example.com/scm/repository.git
# Ensure all future interactions with origin remote also work
cd repository
git config http.sslCAInfo /path/to/certificate.pemFor Windows Client:
Step 1: Import the certificate into the window trust store
Import a signed certificate into the local machine certificate store
- Enter Start | Run | MMC.
- Click File | Add/Remove Snap-in.
- In the Add or Remove Snap-ins window, select Certificates and click Add.
- Select the Computer account radio button when prompted and click Next
- Select Local computer (selected by default) and click Finish.
- Back in the Add or Remove Snap-ins window, click OK.
- In the MMC main console, click on the plus (+) symbol to expand the Certificate snap-in.
- To import the CA certificate, navigate to Trusted Root Certification Authorities | Certificates pane.
- Right-click within the Certificates panel and click All Tasks | Import to start the Certificate Import wizard.
- On successfully importing the CA certificate the wizard will bring you back to the MMC main console.
- Close the MMC console.
Step 2: Configure git to use the certificate in the windows Trust store
When using Windows, the problem resides that git by default uses the «Linux» crypto backend. Starting with Git for Windows 2.14, you can configure Git to use SChannel, the built-in Windows networking layer as the crypto backend. To do that, just run the following command in the GIT client:
git config --global http.sslbackend schannelThis means that it will use the Windows certificate storage mechanism and you don’t need to explicitly configure the curl CA storage (http.sslCAInfo) mechanism. Once you have updated the git config, Git will use the Certificate in the Windows certificate store and should not require http.sslCAInfo setting.
openssl s_client -connect www.github.com:443
CONNECTED(000001E4)
depth=1 O = AO Kaspersky Lab, CN = Kaspersky Anti-Virus Personal Root Certificate
verify error:num=19:self signed certificate in certificate chain
---
Certificate chain
0 s:/businessCategory=Private Organization/jurisdictionC=US/jurisdictionST=Delaware/serialNumber=5157550/C=US/ST=California/L=San Francisco/O=GitHub, Inc./CN=github.com
i:/O=AO Kaspersky Lab/CN=Kaspersky Anti-Virus Personal Root Certificate
1 s:/O=AO Kaspersky Lab/CN=Kaspersky Anti-Virus Personal Root Certificate
i:/O=AO Kaspersky Lab/CN=Kaspersky Anti-Virus Personal Root Certificate
---
Server certificate
-----BEGIN CERTIFICATE-----
….
-----END CERTIFICATE-----
subject=/businessCategory=Private Organization/jurisdictionC=US/jurisdictionST=Delaware/serialNumber=5157550/C=US/ST=California/L=San Francisco/O=GitHub, Inc./CN=github.com
issuer=/O=AO Kaspersky Lab/CN=Kaspersky Anti-Virus Personal Root Certificate
---
No client certificate CA names sent
Peer signing digest: SHA512
Server Temp Key: ECDH, P-256, 256 bits
---
SSL handshake has read 2418 bytes and written 434 bytes
---
New, TLSv1/SSLv3, Cipher is ECDHE-RSA-AES256-GCM-SHA384
Server public key is 2048 bit
Secure Renegotiation IS supported
Compression: NONE
Expansion: NONE
No ALPN negotiated
SSL-Session:
Protocol : TLSv1.2
Cipher : ECDHE-RSA-AES256-GCM-SHA384
Session-ID: A1BCEE841D4DBF172402BAF63BC9A80D560ED0FBC8F66B89E692206D3613FD7E
Session-ID-ctx:
Master-Key: ************************************************************************
Key-Arg : None
PSK identity: None
PSK identity hint: None
SRP username: None
Start Time: 1527649383
Timeout : 300 (sec)
Verify return code: 19 (self signed certificate in certificate chain)
---
closed`
What is the ‘ssl certificate problem unable to get local issuer certificate’ error
The unable to get local issuer certificate is a common issue faced by developers when trying to push, pull, or clone a git repository using Git Bash, a command-line tool specific to Windows.
The unable to get local issuer certificate error often occurs when the Git server’s SSL certificate is self-signed. The issue with self-signed certificates is that the private key associated with them cannot be revoked, making it a security vulnerability.
Alternatively, it can be due to incorrect configuration for Git on your system or when using git inside Visual Studio Code (VS Code) terminal.
What causes ‘ssl certificate problem unable to get local issuer certificate’
The unable to get local issuer certificate error is caused by the misconfiguration of the SSL certificate on your local machine. When pushing, pulling, or cloning, Git cannot verify your SSL certification, which leads to the error.
A valid HTTPS handshake requires both the client and the server to create a secure connection, allowing for safe communication between your local machine and where the source code is hosted. When the SSL certificate cannot be verified, Git cannot complete the HTTPS handshake with the server that hosts the repository.
When the unable to get local issuer certificate error occurs in VS Code, it is often because Visual Studio cannot locate the SSL certificate. This may be due to the path being misconfigured on the local machine.
How can you fix ‘ssl certificate problem unable to get local issuer certificate errors’
When ssl certificate problem unable to get local issuer certificate error is caused by a self-signed certificate, the fix is to add the certificate to the trusted certificate store.
By default, the trusted certificate store is located in the following directory for Git Bash:
C:Program FilesGitmingw64sslcerts
Open the file ca-bundle.crt located in the directory above, then copy and paste the Git SSL certificate to the end of the file. Once completed, save the file and run your git pull, push, or clone command.
Disabling SSL certificate validation is not recommended for security purposes. However, it is an option for fixing the ssl certificate problem unable to get local issuer certificate error.
You can disable SSL certificate validation locally in Git using the following command:
$ git -c http.sslVerify=false clone [URL]
You can also disable SSL certificate validation at a global level using the following command:
$ git config --global http.sslVerify false
To re-enable SSL certificate validation, use the following command:
$ git config --global http.sslVerify true
Another method for fixing the ssl certificate problem unable to get local issuer certificate error is to reinstall Git and choose the SSL transport backend option during the installation process.
If the unable to get local issuer certificate error occurs inside Visual Studio Code, you need to grant your repository access to the SSL certificates. To do this, git can be reconfigured with the --global flag on your SSL certificate configuration. This will give the Git server accessibility to the required SSL certificate.
To do this, run the following command in the Terminal:
git config --global http.sslBackend schannel
Accessibility to SSL certificate verification can also be set at the system level. To do this, you must be running in administrator mode before executing the following command:
git config --system http.sslBackend schannel
If the unable to get local issuer certificate error in Visual Studio Code is not due to accessibility but a location misconfiguration, this can be fixed by reassigning the path. This can be done through the following command:
git config --global http.sslcainfo "Path"
How to prevent ‘ssl certificate problem unable to get local issuer certificate’ errors
The main purpose of a SSL certificate is to confirm authentication so that the information passed between client and server is secure. When an unable to get local issuer certificate error occurs, a secure connection cannot be established, and the git client rejects your attempt to push, pull, or clone a repository for security reasons.
While disabling SSL certificates altogether is an option and common fix, it is not recommended. It opens up a security vulnerability for your repository and your local machine. Nevertheless, you can negate the unable to get local issuer certificate error by disabling SSL certificates at a local and global level. If SSL certificates are disabled at a global level, it is good to always enable them again so that other projects are not impacted by the intentional security disablement.
To prevent the error, ensure that you have a valid SSL certificate in your certificate store. Alternatively, you can reinstall your Git Bash with SSL Transport backend selected during the installation process.
If you are using Git via Visual Studio Code and have a valid SSL certificate in your certificate store but still encounter the certificate problem error, use the --global flag on your SSL certificate configuration to grant the Git server accessibility.
Kubernetes Troubleshooting With Komodor
We hope that the guide above helps you better understand the troubleshooting steps you need to take in order to fix the unable to get local issuer certificate error.
Keep in mind that this is just one of many Git errors that can pop up in your k8s logs and cause the system to fail. Due to the complex and distributed nature of k8s, the search for the root cause of each such failure can be stressful, disorienting, and time-consuming.
Komodor is a Kubernetes troubleshooting platform that turns hours of guesswork into actionable answers in just a few clicks. Using Komodor, you can monitor, alert and troubleshoot incidents in your entire K8s cluster.
For each K8s resource, Komodor automatically constructs a coherent view, including the relevant deploys, config changes, dependencies, metrics, and past incidents. Komodor seamlessly integrates and utilizes data from cloud providers, source controls, CI/CD pipelines, monitoring tools, and incident response platforms.
- Discover the root cause automatically with a timeline that tracks all changes made in your application and infrastructure.
- Quickly tackle the issue, with easy-to-follow remediation instructions.
- Give your entire team a way to troubleshoot independently, without having to escalate.
First published on MSDN on Dec 19, 2016
One of the most common issue with TFS/GIT users come across is the issue caused by self-signed certificates or the corporate certificates.
Error: SSL certificate problem: unable to get local issuer certificate
This Applied to:
TFS 2015 update 3
Git 2.10.0
Android studio 2.1.2
Java 1.7.45
We used Android studio and VSTS/TFS plugin to clone a GIT repository, we faced issues in retrieving the local issuer certificate. These are certificates that have not been signed by a known trusted certificate authority. The problem is that GIT/JAVA will not accept this certificate automatically. We need to force GIT/JAVA to accept the self-signed certificates.
Let’s now consider how to go about with the resolution,
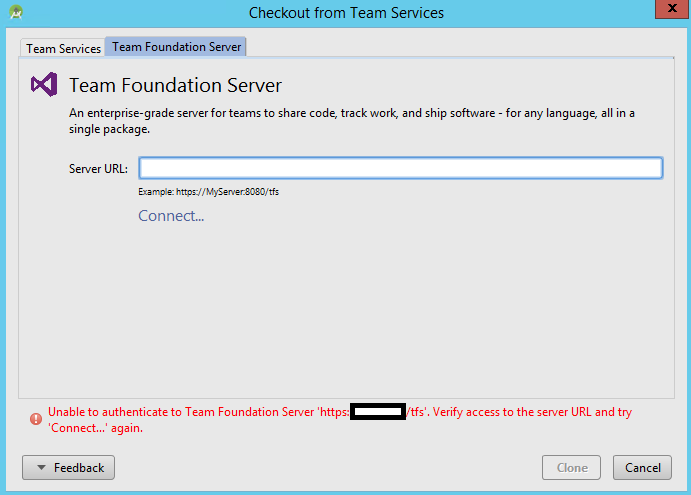
Initially, we faced issues with TFS authentication,
Unable to authenticate to TFS ‘https://server:8080/tfs». verify access to the server URL and try ‘Connect…’ again.
Very often this error can be interpreted to be the result of self-signed certificate. If the certificate in use is Self-signed or any other certificate that is private to the internal network. Java doesn’t trust such certificates and for which, we can
import the cert
into the trust store and make it to work.
The link explains how the certificate import works in a Linux machine (which is also applicable for Windows).
the “
keytool
” is under “
<JAVA_HOME>binkeytool.exe
”, and
the “
cacerts
” trust store is under “
<JAVA_HOME>jrelibsecuritycacerts
”.
<JAVA_HOME>
should be the
jre/jdk installation
used by IntelliJ.
This should have resolved the above TFS connectivity failure.
Note:
If you are using self-signed certificate, you may not be able to connect to TFS from the plugin
Error message:
Caused by: javax.net.ssl.SSLPeerUnverifiedException: Host name ‘server’ does not match the certificate subject provided by the peer (CN=server.corp.fabricam.com)
Providing the complete FQDN(
https://server.corp.fabricam.com/tfs
) instead of the server or the machine name (
https://server/tfs
) is mandatory as the canonical name is set to map to the FQDN.
After getting past the connectivity issue, there are instances in which we get error like the one below:
SSL certificate problem: unable to get local issuer certificate
In the android logs,
#git4idea.commands.GitHandler — fatal: unable to access ‘
https://server/tfs/DefaultCollection/_git/gitRepo/
‘: SSL certificate problem: unable to get local issuer certificate
Exception : javax.ws.rs.ProcessingException: javax.net.ssl.SSLHandshakeException: sun.security.validator.ValidatorException: PKIX path building failed: sun.security.provider.certpath.SunCertPathBuilderException: unable to find valid certification path to requested target
at org.glassfish.jersey.apache.connector.ApacheConnector.apply(ApacheConnector.java:498)
at org.glassfish.jersey.client.ClientRuntime.invoke(ClientRuntime.java:225)
at org.glassfish.jersey.client.JerseyInvocation$1.call(JerseyInvocation.java:655)
at org.glassfish.jersey.client.JerseyInvocation$1.call(JerseyInvocation.java:652)
at org.glassfish.jersey.internal.Errors.process(Errors.java:315)
at org.glassfish.jersey.internal.Errors.process(Errors.java:297)
at org.glassfish.jersey.internal.Errors.process(Errors.java:228)
at org.glassfish.jersey.process.internal.RequestScope.runInScope(RequestScope.java:423)
at org.glassfish.jersey.client.JerseyInvocation.invoke(JerseyInvocation.java:652)
at org.glassfish.jersey.client.JerseyInvocation$Builder.method(JerseyInvocation.java:387)
at org.glassfish.jersey.client.JerseyInvocation$Builder.get(JerseyInvocation.java:291)
at com.microsoft.alm.plugin.context.rest.VstsHttpClient.sendRequest(VstsHttpClient.java:30)
at com.microsoft.alm.plugin.context.ServerContextManager.checkTfsVersionAndConnection(ServerContextManager.java:257)
atcom.microsoft.alm.plugin.context.ServerContextManager.validateServerConnection(ServerContextManager.java:206) at com.microsoft.alm.plugin.context.ServerContextManager.validateServerConnection(ServerContextManager.java:171)
at com.microsoft.alm.plugin.idea.common.services.CredentialsPromptImpl.validateCredentials(CredentialsPromptImpl.java:68)
atcom.microsoft.alm.plugin.authentication.TfsAuthenticationProvider$TfsAuthenticator.run(TfsAuthenticationProvider.java:100)
There are 2 methods of dealing with this issue.
1.Disable SSL verification using below command,
git config —global http.sslVerify false
NOTE:
If you disable SSL certificates verification, then you are susceptible to Man in middle attacks.
2.The preferred method is import certificate authority (CA) to trusted certificate authority store.
If we can verify that disabling SSL verification works, then this article may help:https://blogs.msdn.microsoft.com/phkelley/2014/01/20/adding-a-corporate-or-self-signed-certific…
But, in case if the article doesn’t help,
Try exporting the certificate in all the levels again, following the instructions on the blog.Test certificates with curl.exe, to check if the SSL handshake is successful.
«c:Program FilesGitmingw64bincurl.exe» -v
https://server-name
-cacert c:pathtocertfile.cer
Now, import the certificate into the Git.exe cert store as we did before (also from blog). After importing the certificate, GIT clone’s files from the master branch.
For the complete encryption and the decryption, import the certificate into the Java cert store for Android Studio.
JRE that is now packaged with Android Studio 2.2. You can find it at the root of the Android Studio folder. “C:program filesAndroidAndroid Studiojre”
Hope this helps!
Content:
Ramandeep Singh
Review:
Romit Gulati
If you get the following error:
fatal: unable to access <git>: SSL certificate problem: self signed certificate in certificate chain
..when trying to clone a git repo, then you can quickly get around it by doing one of the following.
Note that both of these solutions are merely workarounds and should be done at absolute worst case.
Workaround Solution 1
Disable SSL verification while running the git clone.
git -c http.sslVerify=false clone <repository-name>
Workaround Solution 2
Disable SSL verification globally while running the git clone.
git config --global http.sslVerify false
Solution 3 (recommended)
This solution is recommended, but takes a lot more work.
Download the actual certificate/certificate chain from the Git server and install it locally by pointing your --system configuration for http.sslCAPath to it.
git config --system http.sslCAPath /path/to/cacerts
How do you fix self-signed certificate in certificate chain?
If the certificate is self-signed, that means that you have the local cert file itself. You can then:
git config --system http.sslCAPath /your/self-signed/cacerts
How do I remove SSL certificate problem self-signed certificate in certificate chain?
You can follow the above solutions, or workarounds. Remember that it’s best to assign a valid cacerts files. If one doesn’t exist, you can always ignore ssl by passing the -c http.sslVerify=false flag.
What does self-signed certificate in certificate chain mean?
Self-signed certificates are where you have created a certificate yourself to be able to take advantage of TLS/SSL encryption in flight. As you created it yourself, this means that it was not signed by a trusted certificate authority, so other users of the service that uses this self-signed certificate will get a warning saying that the connection is not trusted.
How can I make git accept a self-signed certificate?
You will need to follow one of the steps above, dependent on the one that most meets your needs.
Behind a firewall, using chrome, I am able to access a github repository like so:
https://github.com/Squirrel/Squirrel.Windows
Chrome uses our certificate for this access. If I try to access the same url using GitExtensions, I get this error:
SSL certificate problem: self signed certificate in certificate chain
Can I cause GitExtensions to use our certificate to allow access?
EDIT: more info:
On my machine, I don’t see mysysGit, but I do see mingw/curl, so I assume Git is using these. These apparently do not use Windows trust certificates when building the certificate chain. The error that I get, SSL certificate problem: self signed certificate in certificate chain, indicates that the root certificate used by Git/Github is not present in the built-in certificate authority (CA) root bundle. As @Akber Choudhry has pointed out, the CA certificate that is the root of the chain of the certs served by Github SSL server is DigiCert High Assurance EV Root CA and I do see that CA in C:Program Files (x86)Gitbincurl-ca-bundle.crt.
To verify that the problem is with Git, not GitExtensions, I did this on the command line:
>>git clone https://github.com/Squirrel/Squirrel.Windows.git
And received the same SSL certificate problem error.
It gives the appearance that Git is not using this certificate, thus I tried configuring Git like so:
>>git config --system http.sslcainfo "C:Program Files (x86)Gitbincurl-ca-bundle.crt"
but this had no effect..