About the System Update Readiness Tool
The System Update Readiness Tool can help fix problems that might prevent Windows updates and service packs from installing. For more information and how to download the tool, see What is the System Update Readiness Tool.
About this update
This update improves the deployment and serviceability of the System Update Readiness Tool for Windows 7 and Windows Server 2008 R2. It also provides the following new features for the tool:
-
Ability to deploy the System Update Readiness Tool through the DISM command-line options.
-
Ability to administratively deploy the latest manifest, mum, and other payload files without the need for downloading the whole package every time that a new release is created. MUM, MANIFEST, and other payload files are very important to maintaining the state of updated components.
-
Ability to create or configure a scheduled task that executes the tool without user interaction.
-
Event logging channel is created for the System Update Readiness engine to provide feedback to an administrator.
Update information
How to obtain this update
Windows Update
This update is available from Windows Update.
Microsoft Download Center
The following files are available for download from the Microsoft Download Center:
|
Operating system |
Update |
|---|---|
|
All supported x86-based versions of Windows 7 |
|
|
All supported x64-based versions of Windows 7 |
|
|
All supported x64-based versions of Windows Server 2008 R2 |
|
|
All supported IA-64-based versions of Windows Server 2008 R2 |
|
For more information about how to download Microsoft support files, click the following article number to view the article in the Microsoft Knowledge Base:
119591 How to obtain Microsoft support files from online services Microsoft scanned this file for viruses. Microsoft used the most current virus-detection software that was available on the date that the file was posted. The file is stored on security-enhanced servers that help prevent any unauthorized changes to the file.
Prerequisites
There is no prerequisite to apply this update.
Registry information
To apply this update, you do not have to make any changes to the registry.
Restart requirement
You have to restart the computer after you apply this update.
Update replacement information
This update does not replace a previously released update.
The global version of this update installs files that have the attributes that are listed in the following tables. The dates and the times for these files are listed in Coordinated Universal Time (UTC). The dates and the times for these files on your local computer are displayed in your local time together with your current daylight saving time (DST) bias. Additionally, the dates and the times may change when you perform certain operations on the files.
Windows 7 and Windows Server 2008 R2 file information notes
-
The files that apply to a specific product, milestone (RTM, SPn), and service branch (LDR, GDR) can be identified by examining the file version numbers as shown in the following table:
Version
Product
Milestone
Service branch
6.1.760 1.18xxx
Windows 7 and Windows Server 2008 R2
SP1
GDR
6.1.760 1.22 xxx
Windows 7 and Windows Server 2008 R2
SP1
LDR
-
The MANIFEST files (.manifest) and the MUM files (.mum) that are installed for each environment are not listed.
For all supported x86-based versions of Windows 7
|
File name |
File version |
File size |
Date |
Time |
Platform |
|---|---|---|---|---|---|
|
Cbsprovider.dll |
6.1.7601.18489 |
1,281,536 |
30-May-2014 |
07:52 |
x86 |
|
Compatprovider.dll |
6.1.7601.18489 |
141,312 |
30-May-2014 |
07:52 |
x86 |
|
Dmiprovider.dll |
6.1.7601.18489 |
318,464 |
30-May-2014 |
07:52 |
x86 |
|
Intlprovider.dll |
6.1.7601.18489 |
250,880 |
30-May-2014 |
07:52 |
x86 |
|
Osprovider.dll |
6.1.7601.18489 |
102,912 |
30-May-2014 |
07:52 |
x86 |
|
Smiprovider.dll |
6.1.7601.18489 |
220,160 |
30-May-2014 |
07:52 |
x86 |
|
Unattendprovider.dll |
6.1.7601.18489 |
243,200 |
30-May-2014 |
07:52 |
x86 |
|
Wimprovider.dll |
6.1.7601.18489 |
345,600 |
30-May-2014 |
07:52 |
x86 |
|
Cbsprovider.dll |
6.1.7601.22706 |
1,286,656 |
31-May-2014 |
02:14 |
x86 |
|
Compatprovider.dll |
6.1.7601.22706 |
144,896 |
31-May-2014 |
02:14 |
x86 |
|
Dmiprovider.dll |
6.1.7601.22706 |
322,048 |
31-May-2014 |
02:14 |
x86 |
|
Intlprovider.dll |
6.1.7601.22706 |
252,416 |
31-May-2014 |
02:14 |
x86 |
|
Osprovider.dll |
6.1.7601.22706 |
105,472 |
31-May-2014 |
02:15 |
x86 |
|
Smiprovider.dll |
6.1.7601.22706 |
222,720 |
31-May-2014 |
02:15 |
x86 |
|
Unattendprovider.dll |
6.1.7601.22706 |
245,248 |
31-May-2014 |
02:15 |
x86 |
|
Wimprovider.dll |
6.1.7601.22706 |
348,160 |
31-May-2014 |
02:15 |
x86 |
|
Dismcore.dll |
6.1.7601.18489 |
230,912 |
30-May-2014 |
07:52 |
x86 |
|
Dismcoreps.dll |
6.1.7601.18489 |
50,688 |
30-May-2014 |
07:52 |
x86 |
|
Dismhost.exe |
6.1.7601.18489 |
82,944 |
30-May-2014 |
07:51 |
x86 |
|
Dismprov.dll |
6.1.7601.18489 |
141,312 |
30-May-2014 |
07:52 |
x86 |
|
Folderprovider.dll |
6.1.7601.18489 |
49,152 |
30-May-2014 |
07:52 |
x86 |
|
Logprovider.dll |
6.1.7601.18489 |
89,600 |
30-May-2014 |
07:52 |
x86 |
|
Dismcore.dll |
6.1.7601.22706 |
233,984 |
31-May-2014 |
02:14 |
x86 |
|
Dismcoreps.dll |
6.1.7601.22706 |
50,688 |
31-May-2014 |
02:14 |
x86 |
|
Dismhost.exe |
6.1.7601.22706 |
84,992 |
31-May-2014 |
02:14 |
x86 |
|
Dismprov.dll |
6.1.7601.22706 |
143,360 |
31-May-2014 |
02:14 |
x86 |
|
Folderprovider.dll |
6.1.7601.22706 |
51,712 |
31-May-2014 |
02:14 |
x86 |
|
Logprovider.dll |
6.1.7601.22706 |
92,160 |
31-May-2014 |
02:14 |
x86 |
For all supported x64-based versions of Windows 7 and Windows Server 2008 R2
|
File name |
File version |
File size |
Date |
Time |
Platform |
|---|---|---|---|---|---|
|
Cbsprovider.dll |
6.1.7601.18489 |
1,672,192 |
30-May-2014 |
08:08 |
x64 |
|
Compatprovider.dll |
6.1.7601.18489 |
183,296 |
30-May-2014 |
08:08 |
x64 |
|
Dmiprovider.dll |
6.1.7601.18489 |
435,712 |
30-May-2014 |
08:08 |
x64 |
|
Intlprovider.dll |
6.1.7601.18489 |
312,832 |
30-May-2014 |
08:08 |
x64 |
|
Osprovider.dll |
6.1.7601.18489 |
127,488 |
30-May-2014 |
08:08 |
x64 |
|
Smiprovider.dll |
6.1.7601.18489 |
271,360 |
30-May-2014 |
08:08 |
x64 |
|
Unattendprovider.dll |
6.1.7601.18489 |
302,080 |
30-May-2014 |
08:08 |
x64 |
|
Wimprovider.dll |
6.1.7601.18489 |
471,040 |
30-May-2014 |
08:08 |
x64 |
|
Cbsprovider.dll |
6.1.7601.22706 |
1,676,288 |
31-May-2014 |
02:42 |
x64 |
|
Compatprovider.dll |
6.1.7601.22706 |
183,296 |
31-May-2014 |
02:42 |
x64 |
|
Dmiprovider.dll |
6.1.7601.22706 |
435,712 |
31-May-2014 |
02:42 |
x64 |
|
Intlprovider.dll |
6.1.7601.22706 |
312,832 |
31-May-2014 |
02:42 |
x64 |
|
Osprovider.dll |
6.1.7601.22706 |
127,488 |
31-May-2014 |
02:42 |
x64 |
|
Smiprovider.dll |
6.1.7601.22706 |
271,360 |
31-May-2014 |
02:42 |
x64 |
|
Unattendprovider.dll |
6.1.7601.22706 |
302,080 |
31-May-2014 |
02:42 |
x64 |
|
Wimprovider.dll |
6.1.7601.22706 |
471,040 |
31-May-2014 |
02:43 |
x64 |
|
Dismcore.dll |
6.1.7601.18489 |
289,792 |
30-May-2014 |
08:08 |
x64 |
|
Dismcoreps.dll |
6.1.7601.18489 |
112,128 |
30-May-2014 |
08:08 |
x64 |
|
Dismhost.exe |
6.1.7601.18489 |
96,768 |
30-May-2014 |
08:07 |
x64 |
|
Dismprov.dll |
6.1.7601.18489 |
186,368 |
30-May-2014 |
08:08 |
x64 |
|
Folderprovider.dll |
6.1.7601.18489 |
53,760 |
30-May-2014 |
08:08 |
x64 |
|
Logprovider.dll |
6.1.7601.18489 |
107,008 |
30-May-2014 |
08:08 |
x64 |
|
Dismcore.dll |
6.1.7601.22706 |
289,792 |
31-May-2014 |
02:42 |
x64 |
|
Dismcoreps.dll |
6.1.7601.22706 |
112,128 |
31-May-2014 |
02:42 |
x64 |
|
Dismhost.exe |
6.1.7601.22706 |
96,768 |
31-May-2014 |
02:42 |
x64 |
|
Dismprov.dll |
6.1.7601.22706 |
186,368 |
31-May-2014 |
02:42 |
x64 |
|
Folderprovider.dll |
6.1.7601.22706 |
53,760 |
31-May-2014 |
02:42 |
x64 |
|
Logprovider.dll |
6.1.7601.22706 |
107,008 |
31-May-2014 |
02:42 |
x64 |
|
Cbsprovider.dll |
6.1.7601.18489 |
1,281,536 |
30-May-2014 |
07:52 |
x86 |
|
Compatprovider.dll |
6.1.7601.18489 |
141,312 |
30-May-2014 |
07:52 |
x86 |
|
Dmiprovider.dll |
6.1.7601.18489 |
318,464 |
30-May-2014 |
07:52 |
x86 |
|
Intlprovider.dll |
6.1.7601.18489 |
250,880 |
30-May-2014 |
07:52 |
x86 |
|
Osprovider.dll |
6.1.7601.18489 |
102,912 |
30-May-2014 |
07:52 |
x86 |
|
Smiprovider.dll |
6.1.7601.18489 |
220,160 |
30-May-2014 |
07:52 |
x86 |
|
Unattendprovider.dll |
6.1.7601.18489 |
243,200 |
30-May-2014 |
07:52 |
x86 |
|
Wimprovider.dll |
6.1.7601.18489 |
345,600 |
30-May-2014 |
07:52 |
x86 |
|
Cbsprovider.dll |
6.1.7601.22706 |
1,286,656 |
31-May-2014 |
02:14 |
x86 |
|
Compatprovider.dll |
6.1.7601.22706 |
144,896 |
31-May-2014 |
02:14 |
x86 |
|
Dmiprovider.dll |
6.1.7601.22706 |
322,048 |
31-May-2014 |
02:14 |
x86 |
|
Intlprovider.dll |
6.1.7601.22706 |
252,416 |
31-May-2014 |
02:14 |
x86 |
|
Osprovider.dll |
6.1.7601.22706 |
105,472 |
31-May-2014 |
02:15 |
x86 |
|
Smiprovider.dll |
6.1.7601.22706 |
222,720 |
31-May-2014 |
02:15 |
x86 |
|
Unattendprovider.dll |
6.1.7601.22706 |
245,248 |
31-May-2014 |
02:15 |
x86 |
|
Wimprovider.dll |
6.1.7601.22706 |
348,160 |
31-May-2014 |
02:15 |
x86 |
|
Dismcore.dll |
6.1.7601.18489 |
230,912 |
30-May-2014 |
07:52 |
x86 |
|
Dismcoreps.dll |
6.1.7601.18489 |
50,688 |
30-May-2014 |
07:52 |
x86 |
|
Dismhost.exe |
6.1.7601.18489 |
82,944 |
30-May-2014 |
07:51 |
x86 |
|
Dismprov.dll |
6.1.7601.18489 |
141,312 |
30-May-2014 |
07:52 |
x86 |
|
Folderprovider.dll |
6.1.7601.18489 |
49,152 |
30-May-2014 |
07:52 |
x86 |
|
Logprovider.dll |
6.1.7601.18489 |
89,600 |
30-May-2014 |
07:52 |
x86 |
|
Dismcore.dll |
6.1.7601.22706 |
233,984 |
31-May-2014 |
02:14 |
x86 |
|
Dismcoreps.dll |
6.1.7601.22706 |
50,688 |
31-May-2014 |
02:14 |
x86 |
|
Dismhost.exe |
6.1.7601.22706 |
84,992 |
31-May-2014 |
02:14 |
x86 |
|
Dismprov.dll |
6.1.7601.22706 |
143,360 |
31-May-2014 |
02:14 |
x86 |
|
Folderprovider.dll |
6.1.7601.22706 |
51,712 |
31-May-2014 |
02:14 |
x86 |
|
Logprovider.dll |
6.1.7601.22706 |
92,160 |
31-May-2014 |
02:14 |
x86 |
For all supported IA-64-based versions of Windows Server 2008 R2
|
File name |
File version |
File size |
Date |
Time |
Platform |
|---|---|---|---|---|---|
|
Cbsprovider.dll |
6.1.7601.18489 |
3,059,712 |
30-May-2014 |
07:22 |
IA-64 |
|
Compatprovider.dll |
6.1.7601.18489 |
334,848 |
30-May-2014 |
07:22 |
IA-64 |
|
Dmiprovider.dll |
6.1.7601.18489 |
738,816 |
30-May-2014 |
07:22 |
IA-64 |
|
Intlprovider.dll |
6.1.7601.18489 |
564,736 |
30-May-2014 |
07:22 |
IA-64 |
|
Osprovider.dll |
6.1.7601.18489 |
249,344 |
30-May-2014 |
07:22 |
IA-64 |
|
Smiprovider.dll |
6.1.7601.18489 |
588,288 |
30-May-2014 |
07:22 |
IA-64 |
|
Unattendprovider.dll |
6.1.7601.18489 |
618,496 |
30-May-2014 |
07:22 |
IA-64 |
|
Wimprovider.dll |
6.1.7601.18489 |
908,288 |
30-May-2014 |
07:22 |
IA-64 |
|
Cbsprovider.dll |
6.1.7601.22706 |
3,065,856 |
31-May-2014 |
01:50 |
IA-64 |
|
Compatprovider.dll |
6.1.7601.22706 |
334,848 |
31-May-2014 |
01:50 |
IA-64 |
|
Dmiprovider.dll |
6.1.7601.22706 |
738,816 |
31-May-2014 |
01:50 |
IA-64 |
|
Intlprovider.dll |
6.1.7601.22706 |
564,736 |
31-May-2014 |
01:50 |
IA-64 |
|
Osprovider.dll |
6.1.7601.22706 |
249,344 |
31-May-2014 |
01:50 |
IA-64 |
|
Smiprovider.dll |
6.1.7601.22706 |
588,288 |
31-May-2014 |
01:50 |
IA-64 |
|
Unattendprovider.dll |
6.1.7601.22706 |
618,496 |
31-May-2014 |
01:50 |
IA-64 |
|
Wimprovider.dll |
6.1.7601.22706 |
908,288 |
31-May-2014 |
01:50 |
IA-64 |
|
Dismcore.dll |
6.1.7601.18489 |
499,712 |
30-May-2014 |
07:22 |
IA-64 |
|
Dismcoreps.dll |
6.1.7601.18489 |
138,752 |
30-May-2014 |
07:22 |
IA-64 |
|
Dismhost.exe |
6.1.7601.18489 |
201,216 |
30-May-2014 |
07:21 |
IA-64 |
|
Dismprov.dll |
6.1.7601.18489 |
364,544 |
30-May-2014 |
07:22 |
IA-64 |
|
Folderprovider.dll |
6.1.7601.18489 |
130,048 |
30-May-2014 |
07:22 |
IA-64 |
|
Logprovider.dll |
6.1.7601.18489 |
216,576 |
30-May-2014 |
07:22 |
IA-64 |
|
Dismcore.dll |
6.1.7601.22706 |
499,712 |
31-May-2014 |
01:50 |
IA-64 |
|
Dismcoreps.dll |
6.1.7601.22706 |
138,752 |
31-May-2014 |
01:50 |
IA-64 |
|
Dismhost.exe |
6.1.7601.22706 |
201,216 |
31-May-2014 |
01:49 |
IA-64 |
|
Dismprov.dll |
6.1.7601.22706 |
364,544 |
31-May-2014 |
01:50 |
IA-64 |
|
Folderprovider.dll |
6.1.7601.22706 |
130,048 |
31-May-2014 |
01:50 |
IA-64 |
|
Logprovider.dll |
6.1.7601.22706 |
216,576 |
31-May-2014 |
01:50 |
IA-64 |
|
Cbsprovider.dll |
6.1.7601.18489 |
1,281,536 |
30-May-2014 |
07:52 |
x86 |
|
Compatprovider.dll |
6.1.7601.18489 |
141,312 |
30-May-2014 |
07:52 |
x86 |
|
Dmiprovider.dll |
6.1.7601.18489 |
318,464 |
30-May-2014 |
07:52 |
x86 |
|
Intlprovider.dll |
6.1.7601.18489 |
250,880 |
30-May-2014 |
07:52 |
x86 |
|
Osprovider.dll |
6.1.7601.18489 |
102,912 |
30-May-2014 |
07:52 |
x86 |
|
Smiprovider.dll |
6.1.7601.18489 |
220,160 |
30-May-2014 |
07:52 |
x86 |
|
Unattendprovider.dll |
6.1.7601.18489 |
243,200 |
30-May-2014 |
07:52 |
x86 |
|
Wimprovider.dll |
6.1.7601.18489 |
345,600 |
30-May-2014 |
07:52 |
x86 |
|
Cbsprovider.dll |
6.1.7601.22706 |
1,286,656 |
31-May-2014 |
02:14 |
x86 |
|
Compatprovider.dll |
6.1.7601.22706 |
144,896 |
31-May-2014 |
02:14 |
x86 |
|
Dmiprovider.dll |
6.1.7601.22706 |
322,048 |
31-May-2014 |
02:14 |
x86 |
|
Intlprovider.dll |
6.1.7601.22706 |
252,416 |
31-May-2014 |
02:14 |
x86 |
|
Osprovider.dll |
6.1.7601.22706 |
105,472 |
31-May-2014 |
02:15 |
x86 |
|
Smiprovider.dll |
6.1.7601.22706 |
222,720 |
31-May-2014 |
02:15 |
x86 |
|
Unattendprovider.dll |
6.1.7601.22706 |
245,248 |
31-May-2014 |
02:15 |
x86 |
|
Wimprovider.dll |
6.1.7601.22706 |
348,160 |
31-May-2014 |
02:15 |
x86 |
|
Dismcore.dll |
6.1.7601.18489 |
230,912 |
30-May-2014 |
07:52 |
x86 |
|
Dismcoreps.dll |
6.1.7601.18489 |
50,688 |
30-May-2014 |
07:52 |
x86 |
|
Dismhost.exe |
6.1.7601.18489 |
82,944 |
30-May-2014 |
07:51 |
x86 |
|
Dismprov.dll |
6.1.7601.18489 |
141,312 |
30-May-2014 |
07:52 |
x86 |
|
Folderprovider.dll |
6.1.7601.18489 |
49,152 |
30-May-2014 |
07:52 |
x86 |
|
Logprovider.dll |
6.1.7601.18489 |
89,600 |
30-May-2014 |
07:52 |
x86 |
|
Dismcore.dll |
6.1.7601.22706 |
233,984 |
31-May-2014 |
02:14 |
x86 |
|
Dismcoreps.dll |
6.1.7601.22706 |
50,688 |
31-May-2014 |
02:14 |
x86 |
|
Dismhost.exe |
6.1.7601.22706 |
84,992 |
31-May-2014 |
02:14 |
x86 |
|
Dismprov.dll |
6.1.7601.22706 |
143,360 |
31-May-2014 |
02:14 |
x86 |
|
Folderprovider.dll |
6.1.7601.22706 |
51,712 |
31-May-2014 |
02:14 |
x86 |
|
Logprovider.dll |
6.1.7601.22706 |
92,160 |
31-May-2014 |
02:14 |
x86 |
More Information
For more information about the System Update Readiness Tool, click the following article number to view the article in the Microsoft Knowledge Base:
947821 Fix Windows corruption errors by using the DISM or System Update Readiness tool For more information about software update terminology, click the following article number to view the article in the Microsoft Knowledge Base:
824684 Description of the standard terminology that is used to describe Microsoft software updates
Windows System Update Readiness tool
Windows System Update Readiness Tool (KB947821). The System Update Readiness Tool for Windows enables the Windows update service of Windows 7 and Windows Server 2008 R2 which may prevent the successful installation of future updates, service packs, and other software. This tool scans your computer to detect such inconsistencies and attempts to fix any detected problems with Windows Update.
This tool is compatible with Windows 7 Service Pack 1 (SP1) and Windows Server 2008 R2 SP1
Rate this program
- 1
- 2
- 3
- 4
- 5
4.9 out of 5 stars (7 Ratings)
Windows System Update Readiness tool 32-bit

fb27b8ff5ccf579be24d25b1f44ca539
Windows System Update Readiness tool 64-bit

19b4b6a83eee79c1028551af5f8ae26c
Secure and Fast Download — Software Verified
Сегодня вашему вниманию предоставляется еще одно пополнение цикла статей о методах восстановления хранилища компонентов Windows. Помимо изобретения широкой общественностью бесчисленного множества «наколеночных» методик восстановления работоспособности компонентной модели, сами разработчики из Microsoft предлагают вполне официальные методы. В данной публикации мы рассмотрим один из подобных методов, который заключается в восстановлении хранилища компонентов при помощи средства проверки готовности системы к обновлению или, иными словами восстановлении хранилища компонентов при помощи SURT. Фактически описываемым методом предусматривается проверка каталогов/файлов компонентной модели при помощи специализированного пакета и попытка устранения найденных ошибок.
Метод подходит только для операционной системы Windows 7. Для более новых ОС (Windows 8+) средство SURT не требуется, поскольку весь функционал интегрирован в систему и доступен через API стека обслуживания, из скриптов Powershell и сервисной утилиты dism.exe. Это подтверждают высказывания некоторых сотрудников Microsoft: Instead of needing to download and run a separate tool, the diagnostic and repair functionality in the System Update Readiness Tool is now built into Windows in Windows 8 and Windows Server 2012.
Что же это за средство проверки готовности системы к обновлению?
Средство проверки готовности системы к обновлению (System Update Readiness Tool, SURT, CheckSUR) — утилита, поставляемая в виде пакета обновления (с целью включения эталонных файлов хранилища компонентов), предназначающаяся для устранения проблем хранилища компонентов Windows.
Представляет собой набор (базу) файлов компонентов, регулярно обновляемый (был, до некоторого времени) по мере выхода новых исправлений. Грубо говоря, утилита SURT это отличный способ для большинства пользователей проанализировать хранилище компонентов в собственной системе на разного рода повреждения, и иметь возможность устранить найденные повреждения в случае, если встроенная база имеет необходимые для восстановления файлы.
Первый запуск SURT
Для начала необходимо получить пакет обновления по ссылке KB947821. Находим на странице ссылку для соответствующей операционной системы и разрядности (например: Средство проверки готовности системы к обновлению для 64-разрядных (x64) версий Windows 7 (KB947821) [май 2014 г.]), напротив пункта жмем кнопку Загрузить и в открывшемся окне находим файл вида windows6.1-kb947821-v33-x64_09970839dac6c42dc911c5b945d0639b07cfc79a.msu. После скачивания запускаем пакет обновления.
Поскольку SURT представляет собой утилиту, в процессе выполнения кода образа KB947821, он обнаруживает несоответствия (фактически ошибки) в хранилище пакетов и пытается исправить их, если находит соответствующие файлы для восстановления в собственной внутренней базе (полезной нагрузке пакета обновления).
При установке пакета SURT стоит набраться терпения, поскольку на практике встречались станции, установка на которых занимала несколько часов.
После завершения процесса установки SURT в систему, появится сообщение Установка завершена, закрываем окно нажатием кнопки Закрыть. Результатом работы утилиты является файл отчета о проверке хранилища компонентов на наличие разного рода ошибок.
Анализ результатов
После окончания установки (статус: Установка завершена) проверяем лог-файл %Windir%LogsCBSCheckSUR.log на предмет наличия записей об ошибках. На наличие проблем в хранилище компонентов обычно указывают сообщения о найденных ошибках (Found X errors) или недоступных файлов для восстановления (Unavailable repair files):
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 |
================================= Checking System Update Readiness. Binary Version 6.1.7601.24499 2019—07—16 14:04 Checking Windows Servicing Packages Checking Package Manifests and Catalogs Checking Package Watchlist Checking Component Watchlist Checking Packages Checking Component Store (f) CSI Manifest Zero Length 0x00000000 winsxsManifestsx86_microsoft—windows—directx—direct3d11_31bf3856ad364e35_7.1.7601.16492_none_e2d7c9f5b7176f4e.manifest x86_microsoft—windows—directx—direct3d11_31bf3856ad364e35_7.1.7601.16492_none_e2d7c9f5b7176f4e (f) CSI Manifest Zero Length 0x00000000 winsxsManifestsamd64_microsoft—windows—ie—htmlrendering_31bf3856ad364e35_11.2.9600.17843_none_f5715a5c3755cc36.manifest amd64_microsoft—windows—ie—htmlrendering_31bf3856ad364e35_11.2.9600.17843_none_f5715a5c3755cc36 Summary: Seconds executed: 2948 Found 2 errors CSI Manifest Zero Length Total count: 2 Unavailable repair files: winsxsmanifestsx86_microsoft—windows—directx—direct3d11_31bf3856ad364e35_7.1.7601.16492_none_e2d7c9f5b7176f4e.manifest winsxsmanifestsamd64_microsoft—windows—ie—htmlrendering_31bf3856ad364e35_11.2.9600.17843_none_f5715a5c3755cc36.manifest |
По изначальному замыслу разработчиков, средство SURT предназначалось для автоматического исправления найденных в хранилище компонентов ошибок, именно для этого в продукт поместили полный каталог эталонных файлов. Тем не менее, со временем ситуация изменилась:
..в последний раз SURT обновлялся в октябре 2014 года (о чем есть информация на странице загрузки Microsoft), а исправлений на операционную систему с того момента вышло довольно большое количество, соответственно многие файлы в базе средства попросту отсутствуют.
Вот именно поэтому, в случае обнаружения в лог-файле %Windir%LogsCBSCheckSUR.log (битых) ненайденных файлов для восстановления, у нас имеется несколько вариантов решения.
Вариант 1: файловая часть
- Проверяем результаты работы утилит восстановления хранилища в лог-файле %Windir%LogsCBSCheckSUR.log. К примеру, в файле журнала могут быть обнаружены следующие данные:
. . .
Unavailable repair files:
servicingpackagesPackage_for_KB3037574~31bf3856ad364e35~amd64~~6.1.1.0.mum
servicingpackagesPackage_for_KB3037574~31bf3856ad364e35~amd64~~6.1.1.0.mum
servicingpackagesPackage_1_for_KB3037574~31bf3856ad364e35~amd64~~6.1.1.0.mum
servicingpackagesPackage_25_for_KB3037574~31bf3856ad364e35~amd64~~6.1.1.0.mum
servicingpackagesPackage_2_for_KB3037574~31bf3856ad364e35~amd64~~6.1.1.0.mum
servicingpackagesPackage_3_for_KB3037574~31bf3856ad364e35~amd64~~6.1.1.0.mum
servicingpackagesPackage_for_KB3037574_SP1~31bf3856ad364e35~amd64~~6.1.1.0.mum
. . .
После того, как вы определили имена, есть несколько возможных вариантов решений:
- найти указанные в логе файлы на работоспособной операционной системе аналогичной редакции/версии;
- по имени проблемных файлов пакетов найти соответствующее [родительское] обновление (KB??????), которому принадлежит недостающие файлы (в примере выше это KB3037574), скачать его из Центра загрузок Майкрософт или Центра обновления Майкрософт, или попросту используя поисковик. Затем распаковать из скачанного обновления все необходимые файлы.
- Все найденные/извлеченные недостающие файлы разместить в системе следующим образом:
*.mum— и*.cat-файлы складываются в %Windir%TempCheckSURservicingpackages;*.manifest-файлы складываются в %Windir%TempCheckSURwinsxsmanifests;
- Повторно запустить SURT;
Вариант 2: удаление битого пакета
Этот вариант заключается в ручном удалении проблемного пакета из командной строки.
- По тем же логам вычисляем наименование пакета, в нашем случае это Package_for_KB3037574~31bf3856ad364e35~amd64~~6.1.1.0;
- после этого пробуем удалить его при помощи утилиты dism:
dism /Online /Remove-Package /PackageName:Package_for_KB3037574~31bf3856ad364e35~amd64~~6.1.1.0
- Выполняем повторный запуск SURT;
Если получаем ошибку, к примеру 0x8007005, ошибка 5, отказано в доступе.. тогда переходим к следующему методу.
Вариант 3: реестровая часть
Обычно этот вариант предлагается как последняя надежда, когда остальные способы оказались бессильны.
Этот вариант решения можно выделить в самостоятельный метод, поскольку применять его можно при любых сценариях повреждения компонентной модели. Да, решение неофициальное, тем не менее, при отсутствии грамотной реализации компонентной модели Windows, вполне себя оправдывает, поскольку несколько раз показывало свою состоятельность.
Как мы помним, у компонентной модели Windows имеется часть, размещающаяся в реестре операционной системы.
- запускаем редактор реестра regedit.exe;
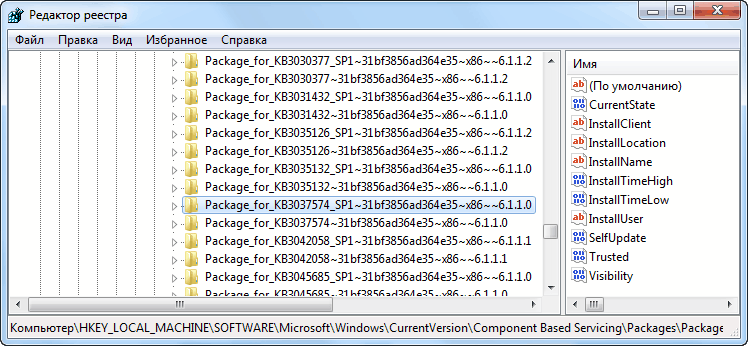
- перемещаемся в ветку HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindowsCurrentVersionComponent Based ServicingPackages и для каждого найденного проблемного файла повторяем следующие шаги:
- ищем интересующий нас подключ реестра (например, Package_for_KB3037574~31bf3856ad364e35~amd64~~6.1.1.0.mum);
- меняем разрешения безопасности подключа: выделяем (ставим курсор) интересующую нас запись, нажимает правую кнопку мыши — пункт меню разрешения — выделяем курсором текущего пользователя — в нижней части окна ставим чекбокс напротив разрешения Полный доступ. Применяем изменения через кнопку OK. В случае необходимости меняем владельца объекта.
- выполняем удаление записи:
- после удаления всех требуемых записей реестра, запускаем Центр обновления Windows и повторно инициируем поиск обновлений. После определения списка устанавливаемых обновлений, выполняем их установку. Проблемный пакет, в этом случае, должен быть повторно загружен и установлен.
- после окончания процесса установки повторно запускаем SURT;
Повторный запуск SURT
После выполнения действий, описанных в вариантах решений (выше), необходимо повторно произвести запуск средства проверки готовности системы к обновлению (используя все тот же скачанный файл обновления KB947821). При повторном запуске средство проверки готовности системы к обновлению сможет «подхватить» распакованные и размещенные нами файлы из каталога %Windir%TempCheckSUR и произвести восстановление хранилища компонентов. Если процедура восстановления завершилась успешно, то в лог-файле %Windir%LogsCBSCheckSUR.log можно будет увидеть следующие записи:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 |
================================= Checking System Update Readiness. Binary Version 6.1.7601.22471 Package Version 26.0 2020—05—29 20:57 Checking Windows Servicing Packages Checking Package Manifests and Catalogs (f) CBS MUM Corrupt 0x800F080D servicingPackagesPackage_for_KB4022168_SP1~31bf3856ad364e35~amd64~~6.1.1.7.mum Line 3009: </ (fix) CBS MUM Corrupt CBS File Replaced Package_for_KB4022168_SP1~31bf3856ad364e35~amd64~~6.1.1.7.mum from Cabinet: C:WindowsCheckSurv1.0windows6.1—7601—x64-clientcab4.cab. (fix) CBS Paired File CBS File also Replaced Package_for_KB4022168_SP1~31bf3856ad364e35~amd64~~6.1.1.7.cat from Cabinet: C:WindowsCheckSurv1.0windows6.1—7601—x64-clientcab4.cab. Checking Package Watchlist Checking Component Watchlist Checking Packages Checking Component Store Summary: Seconds executed: 5121 Found 1 errors Fixed 1 errors CBS MUM Corrupt Total count: 1 Fixed: CBS MUM Corrupt. Total count: 1 Fixed: CBS Paired File. Total count: 1 |
Об успешном восстановлении хранилища компонентов при помощи средства проверки готовности системы к обновлению можно говорить в случае, когда в файле количество найденных ошибок (Found X errors) соответствует количеству исправленных (Fixed X errors). Статус No errors detected говорит о том, что ошибок не было изначально.
Download PC Repair Tool to quickly find & fix Windows errors automatically
System resources, such as file data, registry data, and even in-memory data, can develop inconsistencies during the lifetime of the operating system. These inconsistencies may be caused by various hardware failures or by software issues. In some cases, these inconsistencies can affect the Windows Servicing Store, and they can cause a Windows update to fail. When the update fails, it blocks the user from installing updates and service packs.
System Update Readiness Tool or CheckSUR addresses this issue. These updates contain the Check for System Update Readiness (CheckSUR) tool. The CheckSUR tool will scan for inconsistencies on your computer and fix them as it’s being installed. Please note that the scan may take up to 15 minutes or longer to run on certain computers. Even if the progress bar seems to stop, the scan continues to run, so do not cancel the process.
How to run Microsoft CheckSUR
Users of Windows 7, Windows Vista, Windows Server 2008 R2, and Windows Server 2008 may follow the download links mentioned here and download the package for your operating system and then run it.
What the tool does is that, it verifies the integrity of the files that are located in the following folders and replace the incorrect data, if found:
- %SYSTEMROOT%ServicingPackages
- %SYSTEMROOT%WinSxSManifests
It also verifies the registry data that is located under the following registry subkeys, and resets them to default values if required:
HKEY_LOCAL_MACHINEComponents
HKEY_LOCAL_MACHINESchema
HKEY_LOCAL_MACHINE Software Microsoft WindowsCurrentVersionComponent Based Servicing
The following are the installation errors, CheckSUR can potentially address:
- 0x80070002 ERROR_FILE_NOT_FOUND
- 0x8007000D ERROR_INVALID_DATA
- 0x8007370D ERROR_SXS_IDENTITY_PARSE_ERROR
- 0x8007370B ERROR_SXS_INVALID_IDENTITY_ATTRIBUTE_NAME
- 0x8007371B ERROR_SXS_TRANSACTION_CLOSURE_INCOMPLETE
- 0x80070490 ERROR_NOT_FOUND
- 0x8007370A ERROR_SXS_INVALID_IDENTITY_ATTRIBUTE_VALUE
- 0x80070057 ERROR_INVALID_PARAMETER
- 0x800B0100 TRUST_E_NOSIGNATURE
- 0x800F081F CBS_E_SOURCE_MISSING
- 0x80073712 ERROR_SXS_COMPONENT_STORE_CORRUPT
- 0x800736CC ERROR_SXS_FILE_HASH_MISMATCH
- 0x800705B9 ERROR_XML_PARSE_ERROR
- 0x80070246 ERROR_ILLEGAL_CHARACTER
- 0x80092003 CRYPT_E_FILE_ERROR
- 0x800B0101 CERT_E_EXPIRED
These errors are typically listed in the %systemroot%LogsCBSCBS.log file or in the CBS.persist.log file.
The System Update Readiness Tool supports Windows 7, Windows Vista, Windows Server 2008 R2, and Windows Server 2008.
Windows 10, Windows 8.1 and Windows 8 users may follow these steps to run the built-in Deployment Imaging and Servicing Management. In Windows 11/10/8.1/8, the Inbox Corruption Repair brings the functionality of CheckSUR into Windows. You do not require a separate download to get the tool. You may simply Run DISM Tool.
Press Win+C or swipe and choose Search. Type CMD in the search box and hit ‘Enter’. Then, right-click Command Prompt, and choose the ‘Run as administrator’ option.
In the Administrator: Command Prompt window, type the following commands exactly as they appear. Press the Enter key after each command:
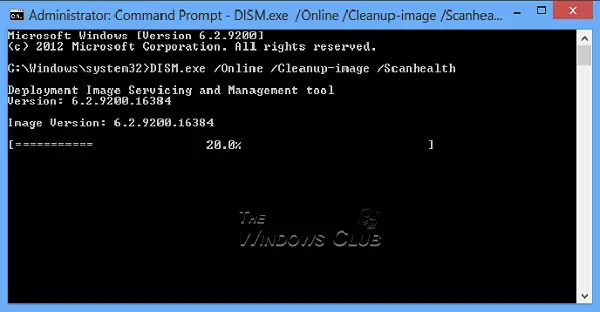
DISM.exe /Online /Cleanup-image /Scanhealth
DISM.exe /Online /Cleanup-image /Restorehealth
When done, type Exit and press Enter. Run Windows Update again.
These posts may also interest you:
- Windows Update not working or page blank
- Windows Update fails to install in Windows.
Post ported from WinVistaClub, updated, and posted here.
Anand Khanse is the Admin of TheWindowsClub.com, a 10-year Microsoft MVP (2006-16) & a Windows Insider MVP (2016-2022). Please read the entire post & the comments first, create a System Restore Point before making any changes to your system & be careful about any 3rd-party offers while installing freeware.
If you are having problems installing Service Pack or software updates on Windows Server 2008 R2, Windows 7 or Windows Vista you are not alone. There are lots of people facing the same issue, including me, and hopefully this article will be helpful in understanding and solving the problem. I should point out that I have encountered this problem of installing Service Pack 1 (SP1) on numerous servers (all new installation) as well as existing Windows 7 client. The focus of this article is on Windows Server 2008 R2 but you can apply the same techniques on Windows 7 and Windows Vista.
It took me three full days to find a solution that worked for me. Needless to say I was searching the Web all this time and trying various solutions but some worked and others didn’t. Unlike the old Windows NT days when the patches were considered a risky business, for the past decade or so Microsoft has done a great job to make the updates and security patches fairly reliable. It’s a daunting task to deal with a gazillion updates on various systems and gain the confidence of consumers. Microsoft gained enough of my confidence that I have been configuring all my computers, including servers, to download and install the Windows Update automatically. Even though I have occasionally encountered a few crashes, overall I have been fairly satisfied with the automatic Windows Update service. Well, lately things have not been so rosy. Windows Updates are causing more problems more frequently and therefore starting this year I decided to manually update my computers because of the fear of system crashes and other unexpected results. Microsoft has confirmed my fears of Windows Update by releasing a patch to fix the patches. The patch is called Windows System Update Readiness Tool, essentially a bug fix that fixes other bug fixes. But these days vendors don’t use the term bugs any more because that is admitting that there was a problem with the software in the first place. Instead they refer to them as “patches”, “updates”, “repairs”, “fixes”, and now there is a new term “tool.” Well, you tell me which one sounds better Windows System Update Readiness Tool or Windows Update Bug Fix? Exactly my point!
Microsoft is aware that even the Windows System Update Readiness Tool may not fix the Windows Update problems with Windows Server 2008 R2 and therefore they have posted an article on TechNet for advanced diagnosing and fixing servicing corruption. The article is listed under the Troubleshooting section as Known Issues with Windows Server 2008 R2. So now we know that Microsoft is aware of this issue and have released a bug fix for the bug fixes and also admitted that the bug fix for the bug fixes may not work and therefore we may need to rely on some advance diagnostics to fix the problems with the corruption in Windows servicing store (more on this servicing store in a minute).
Let’s get back to the problem of installing SP1. As I indicated earlier, lately I have been having lots of issues with installing Windows Server 2008 R2 SP1 on several servers. As far as I recall, I have experienced this issue mostly on new server installations. The problem is that the service pack hangs after a minute or so and the installation fails. After spending a lot of time I finally narrowed the problem down to one particular update (KB2620704). I installed all the updates on my new servers (92 to be exact) and then installed KB2620704 that was causing problems. On some servers KB2620704 failed while on others I was able to install it successfully. However, even after I was able to install all the updates, including KB2620704, I still wasn’t able to install SP1. In addition, I was not able to install SharePoint Server 2010 on one of the servers because when I tried to install the software prerequisites it failed.
At one point Windows Update offered me a new update called System Update Readiness Tool for Windows Server 2008 R2 x64 Edition (KB 947821) [August 2011].
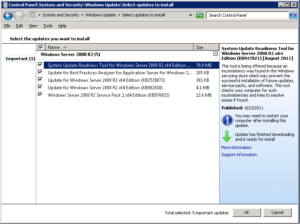
According to Microsoft:
“This tool is being offered because an inconsistency was found in the Windows servicing store which may prevent the successful installation of future updates, service packs, and software. This tool checks your computer for such inconsistencies and tries to resolve issues if found.”
In case you are wondering about the Windows Servicing Store, it’s a component that is required to successfully install the service packs.
There is something very interesting in the above screenshot. Notice that the last update on the list Windows Server 2008 R2 Service Pack 1 x64 Edition (KB976932) is only 13.6MB. If you download SP1 from Microsoft here, the size is 903.2MB. The interesting part was that I was working on several newly installed servers and only one of them showed SP1 as 13.6MB. All the other servers listed KB976932 as 95.5MB – 892.6MB, as shown in the screenshot below.
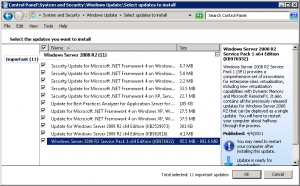
After installing KB947821 I was still not able to installSP1. I went to the SUR log to see what’s going on. See this article for more information.
%windir%logscbschecksur.log
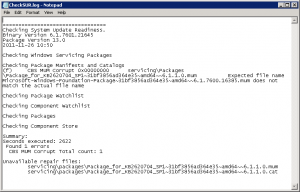
I noticed the log pointed to the KB2620704 which I knew was a problem right from the start. On the server where I was able to install KB2620704 everything was fine but on the server where I wasn’t able to install SP1 I knew I had to install KB2620704. I was left with only 2 updates (KB2620704 & the SP1 update KB976932) so I unchecked KB976932 and tried to install KB2620704 but it failed with the error Code 800F0818.
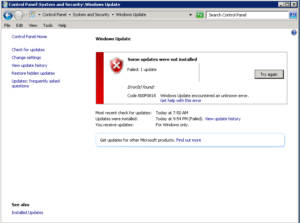
Now you may get lucky after installing KB2620704 but I wasn’t. Here’s what I did next. Per TechNet article Advanced guidelines for diagnosing and fixing servicing corruption I looked at the two files listed at the end of the checksur.log.
servicingpackagesPackage_for_KB2620704_SP1~31bf3856ad364e35~amd64~~6.1.1.0.mum
servicingpackagesPackage_for_KB2620704_SP1~31bf3856ad364e35~amd64~~6.1.1.0.cat
Next I started cmd.exe as an administrator and backed up the two files as a precaution.
copy %windir%servicingpackagesPackage_for_KB2620704_SP1~31bf3856ad364e35~amd64~~6.1.1.0.mum c:temp
copy %windir%servicingpackagesPackage_for_KB2620704_SP1~31bf3856ad364e35~amd64~~6.1.1.0.cat c:temp
Then I took ownership of these files so I can copy these files from another server.
takeown /f %windir%servicingpackagesPackage_for_KB2620704_SP1~31bf3856ad364e35~amd64~~6.1.1.0.mum
takeown /f %windir%servicingpackagesPackage_for_KB2620704_SP1~31bf3856ad364e35~amd64~~6.1.1.0.cat
Next I used icacls to grant administrators permissions to overwrite the files.
icacls %windir%servicingpackagesPackage_for_KB2620704_SP1~31bf3856ad364e35~amd64~~6.1.1.0.mum /grant administrators:F
icacls %windir%servicingpackagesPackage_for_KB2620704_SP1~31bf3856ad364e35~amd64~~6.1.1.0.cat /grant administrators:F
Finally, I logged out and then logged back in so I can copy the two files from another server where I was able to successfully install KB2620704 to the server. Even though I was logged in with a domain account that was a member of the local administrators group the permission to copy the files was denied. I went to Windowsservicingpackages folder in Windows Explorer and gave my domain account full-control permissions to the packages folder. I removed this permission after I was able to copy the two files. I ran the update for KB 2620704 and it was finally successful.
I then tried to install SP1 (KB976932) again. By that time I knew all these KB article numbers better than my address and phone number. Fortunately, this time it worked and I was able to install SP1 on my Windows Server 2008 R2. It only took about 40 hours in three days. Piece of cake!
SharePoint Server 2010 Installation
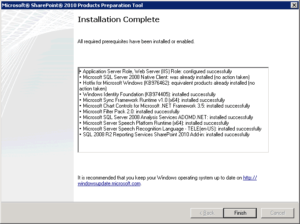
The rest of the article only applies to you if you are installing SharePoint Server 2010 on a new server. Once the service pack was installed, I should be able to install SharePoint, right? Wrong! This time the software prerequisites tool was able to install a couple of prerequisites, including the Web Server (IIS) Role, but was unable to install the hotfix KB976462.
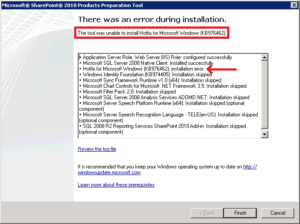
Okay, no problem. I downloaded the hotfix KB976462 for my x64 system (Windows6.1-KB976462-v2-x64.msu) and tried to run it but got an error “The update is not applicable to your computer.” Here’s how I worked around that hurdle. I followed the instructions in yet another KB article KB934307.
- I created a folder C:KB976462 and downloaded the file Windows6.1-KB976462-v2-x64.msu into that folder.
- I created a folder C:TEMP.
- I opened command prompt as an administrator and ran the following command to expand the MSU file to the temp folder which resulted in 4 files in the TEMP folder.
expand -f:* “C:KB976462Windows6.1-KB976462-v2-x64.msu” C:TEMP - Then I ran the following command.
pkgmgr.exe /n:c:tempWindows6.1-KB976462-v2-x64.xml
You will not see any message after you run this command successfully. Just wait a minute or so until the command prompt is returned and that’s how you will know if the command was successfully executed. The only time you will see a message is if something went wrong. - Next I double-clicked the Windows6.1-KB976462-v2-x64.msu file in the C:KB976462 folder where I originally downloaded it. I got a pop up message that “The update is not applicable to your computer.” This is the same message I received when I had double-clicked the file the first time. By the way, some people have reported that they get the message that the patch is already installed.
NOTE: Regardless of what message you see, you should simply ignore it and go to the next step and you will be a happy camper. - I ignored the notice and ran the SharePoint software prerequisites tool again. This time everything worked and I was able to install the software prerequisites.
- I deleted both the C:KB976462 and the C:TEMP folders.
- I rebooted the server. Even though I had not received any notices or warnings that I need to restart the server, when I tried to install SharePoint the wizard indicated that I must reboot first before proceeding to install SharePoint.
- After the reboot I continued on with SharePoint Server 2010 installation without a hitch.
References
Here are the download links for Windows System Update Readiness Tool for Windows Server 2008 R2, Windows 7 and Windows Vista (KB947821).
- System Update Readiness Tool for Windows Server 2008 R2 x64 Edition (KB947821) [August 2011] 315.6MB
- System Update Readiness Tool for Windows 7 106.6MB
- System Update Readiness Tool for Windows Vista 121.8MB
Here’s another related article KB947366 that might also help.
KB947366: How to troubleshoot Windows Vista and Windows Server 2008 service pack installation issues
A hotfix for the.NET Framework 3.5 Service Pack 1 is available for Windows 7 and for Windows Server 2008 R2 as a prerequisite for Microsoft Office SharePoint Server 2010.
KB976462: Prerequisite hotfix for Microsoft Office SharePoint Server 2010
This is the hotfix mentioned in the above link. It’s called SharePoint Shared Services Roll-up for Windows Server 2008 R2.
And finally here’s an article which describes the Windows Update Stand-alone Installer. I was able to use the information in this article to get over the last hurdle.
KB934307: Description of the Windows Update Stand-alone Installer (Wusa.exe) and of.msu files in Windows Vista, Windows 7, Windows Server 2008 and in Windows Server 2008 R2
Copyright ©2011 Zubair Alexander. All rights reserved.
Содержание
- Improvements for the System Update Readiness Tool in Windows 7 and Windows Server 2008 R2
- About the System Update Readiness Tool
- About this update
- Update information
- How to obtain this update
- Prerequisites
- Registry information
- Restart requirement
- Update replacement information
- Исправляем ошибки установки обновлений Windows 7
- Fix Windows Update errors by using the DISM or System Update Readiness tool
- Symptom
- Resolution for Windows 8.1, Windows 10 and Windows Server 2012 R2
- Resolution for Windows 7 and Windows Server 2008 R2
- Description of the common corruption errors
- What does the System Update Readiness tool do
- Verify the integrity of resources
- Logging
- How to fix errors that are found in the CheckSUR log file
- Восстановление хранилища компонентов при помощи средства проверки готовности системы к обновлению (SURT)
- Первый запуск SURT
- Анализ результатов
- Вариант 1: файловая часть
- Вариант 2: удаление битого пакета
- Вариант 3: реестровая часть
Improvements for the System Update Readiness Tool in Windows 7 and Windows Server 2008 R2
The System Update Readiness Tool can help fix problems that might prevent Windows updates and service packs from installing. For more information and how to download the tool, see What is the System Update Readiness Tool.
About this update
This update improves the deployment and serviceability of the System Update Readiness Tool for Windows 7 and Windows Server 2008 R2. It also provides the following new features for the tool:
Ability to deploy the System Update Readiness Tool through the DISM command-line options.
Ability to administratively deploy the latest manifest, mum, and other payload files without the need for downloading the whole package every time that a new release is created. MUM, MANIFEST, and other payload files are very important to maintaining the state of updated components.
Ability to create or configure a scheduled task that executes the tool without user interaction.
Event logging channel is created for the System Update Readiness engine to provide feedback to an administrator.
Update information
How to obtain this update
Windows Update
This update is available from Windows Update.
Microsoft Download Center
The following files are available for download from the Microsoft Download Center:
All supported x86-based versions of Windows 7

All supported x64-based versions of Windows 7

All supported x64-based versions of Windows Server 2008 R2

All supported IA-64-based versions of Windows Server 2008 R2

For more information about how to download Microsoft support files, click the following article number to view the article in the Microsoft Knowledge Base:
119591 How to obtain Microsoft support files from online services Microsoft scanned this file for viruses. Microsoft used the most current virus-detection software that was available on the date that the file was posted. The file is stored on security-enhanced servers that help prevent any unauthorized changes to the file.
Prerequisites
There is no prerequisite to apply this update.
Registry information
To apply this update, you do not have to make any changes to the registry.
Restart requirement
You have to restart the computer after you apply this update.
Update replacement information
This update does not replace a previously released update.
The global version of this update installs files that have the attributes that are listed in the following tables. The dates and the times for these files are listed in Coordinated Universal Time (UTC). The dates and the times for these files on your local computer are displayed in your local time together with your current daylight saving time (DST) bias. Additionally, the dates and the times may change when you perform certain operations on the files.
Windows 7 and Windows Server 2008 R2 file information notes
The files that apply to a specific product, milestone (RTM, SPn), and service branch (LDR, GDR) can be identified by examining the file version numbers as shown in the following table:
Источник
Исправляем ошибки установки обновлений Windows 7

Существует правило – если есть обновления, то есть и проблемы с их установкой. Давайте разберем, какие основные проблемы возникают при обновлении Windows 7 через Windows Server Update Services (WSUS) и как их исправить с наименьшими затратами.
Ошибка #1. Failed to find updates with error code 80244010
Эту ошибку вы практически гарантированно будете наблюдать на любой системе, впервые обратившейся к серверу WSUS. В WindowsUpdate.log также встретится предупреждение:
WARNING: Exceeded max server round trips
Причина проблемы в том, что список обновлений стал слишком большим, и клиент не может принять его за один заход. Подробности — blogs.technet.microsoft.com/sus/2008/09/18/wsus-clients-fail-with-warning-syncserverupdatesinternal-failed-0x80244010
Какое решение предлагает Microsoft? Если после ошибки запустить повторный поиск обновлений, то процесс загрузки метаданных продолжится с момента возникновения ошибки. Терпение господа, терпение. Три, пять попыток wuauclt /detectnow – и все образуется. Не забудьте при повторном поиске дождаться окончания предыдущего цикла поиска, иначе магия не сработает!
Ошибка #2. Не устанавливаются обновления Windows с ошибкой 0x80070308
Встречается эпизодически, и в одном случае из 100 у нее есть единственное и очень специфическое решение — удалить ключ
HKLMComponentsPendingRequired=1
Перезагрузиться. Здесь важно не переусердствовать, не следует удалять никакие другие ключи в этом разделе, даже если они вам очень не нравятся, потому что после этого обновления прекратят ставиться навсегда.
Ошибка #3. Все другие ошибки
Summary:
Seconds executed: 1164
Found 16 errors
Fixed 4 errors
Проблема заключается в том, что во время установки обновлений в системе могут появиться битые файлы. Что является причиной — неисправная сеть, диск, оперативная память, сам Windows Update – выяснить не получится, а исправить ошибки для установки последующих обновлений придется.
Как правило, повреждаются *.cat, *.mum, *.manifest файлы. У кого-то повреждаются *.dll, но я на практике не сталкивался. И вроде бы средство SURT должно само исправить ошибки, поскольку внутри него есть огромный каталог эталонных файлов. Только в последний раз SURT обновлялся в октябре 2014 года, а исправлений на операционную систему с тех пор вышло бесчисленное множество, и многих файлов в каталоге не хватает.
Ниже я опишу последовательность действий, необходимых для исправления ошибок установки обновлений на Windows 7 x64 с использованием SURT. Для редакции x86 просто потребуется другой пакет SURT из KB947821.
Последовательность действий будет следующая.
1. Запустить первый проход Windows6.1-KB947821-v34-x64.msu
Пользователя от работы отвлекать не потребуется, все сделаем удаленно. Создаем следующий командный файл и запускаем его:
где BUHWKS02 – целевая машина.
Когда скрипт отработает и встанет на паузу, проверяем %windir%LogsCBSCheckSUR.log
Если ошибок не найдено – дело не в битых обновлениях.
Если он заканчивается
Summary:
Seconds executed: 1164
Found 16 errors
Fixed 4 errors
CSI Manifest All Zeros Total count: 6
CSI Catalog Corrupt Total count: 3
Fixed: CSI Catalog Corrupt. Total count: 3
CBS MUM Corrupt Total count: 3
CBS Catalog Corrupt Total count: 3
CSI Catalog Thumbprint Invalid Total count: 1
Fixed: CSI Catalog Thumbprint Invalid. Total count: 1
Unavailable repair files:
winsxsmanifestswow64_microsoft-windows-gdi32_31bf3856ad364e35_6.1.7601.19091_none_c19fa2719495aca9.manifest
winsxsmanifestsamd64_microsoft-windows-capi2-weakcrypto_31bf3856ad364e35_6.1.7601.23290_none_5e936c9c5ce2e8e6.manifest
winsxsmanifestswow64_microsoft-windows-gdi32_31bf3856ad364e35_6.1.7601.23290_none_c22840d8adb43043.manifest
winsxsmanifestsamd64_microsoft-windows-gdi32_31bf3856ad364e35_6.1.7601.19091_none_b74af81f6034eaae.manifest
winsxsmanifestsamd64_microsoft-windows-capi2-weakcrypto_31bf3856ad364e35_6.1.7601.19091_none_5e0ace3543c4654c.manifest
winsxsmanifestsamd64_microsoft-windows-gdi32_31bf3856ad364e35_6.1.7601.23290_none_b7d3968679536e48.manifest
servicingpackagesPackage_2_for_KB3123479
то будем исправлять.
2. Копируем эталонные файлы на целевую машину
Microsoft предлагает нам длинную, путанную процедуру с извлечением хороших файлов из обновлений и размещением их в определенные каталоги средства SURT. При этом пути в статьях неверные. Где-то и вовсе рекомендуют подкладывать оригинальные msu файлы.
Самый простой и правильный вариант следующий — скопировать эталонные файлы с рабочей системы:
*.mum and *.cat из C:WindowsservicingPackages складываются в %windir%TempCheckSURservicingpackages
*.manifest из C:WindowswinsxsManifests складываются в %windir%TempCheckSURwinsxsmanifests
Проблема в том, что битых файлов обычно десятки, и их очень сложно выбрать и скопировать. Тогда на помощь приходит следующий скрипт PowerShell (эталонной считается машина, с которой вы запускаете скрипт)
Как видите, скрипт прост и может быть легко заточен напильником под вашу инфраструктуру.
3. Запускаем второй проход Windows6.1-KB947821-v34-x64.msu
=================================
Checking System Update Readiness.
Binary Version 6.1.7601.22471
Package Version 26.0
2016-03-03 09:15
Checking Windows Servicing Packages
Checking Package Manifests and Catalogs
Checking Package Watchlist
Checking Component Watchlist
Checking Packages
Checking Component Store
Summary:
Seconds executed: 1435
No errors detected
Ошибка #4. Если SURT отработал нормально, а обновления все равно не ставятся
Попробуйте прибегнуть к старому приему – сбросить службу Windows Update в исходное состояние. Для этого необходимо удалить каталог %windir%SoftwareDistribution.
Ошибка #5
Клиент исчезает из консоли WSUS. Любопытная ошибка, связанная с неправильным клонированием машин и задвоением (затроением и т.д.) идентификаторов клиентов. Решается так:
Ошибка #6
GetCookie failure, error = 0x8024400D, soap client error = 7, soap error code = 300, HTTP status code = 200
SyncUpdates failure, error = 0x80072EE2, soap client error = 5, soap error code = 0, HTTP status code = 200
Windows Update Client failed to detect with error 0x80072ee2
Ошибка связана с нехваткой ресурсов в AppPool WSUS. Решение — снять лимит на потребляемую память. Как это сделать — статья.
Коротко: Открываем IIS, Application Pools, WsusPool, Advanced Settings.
Параметр Private Memory Limit устанавливаем в 0.
Продолжение темы настройки WSUS — в моей следующей статье: https://habrahabr.ru/post/329440/
PS:
Многие ошибки решены в новом клиенте WSUS:
1. KB3125574 «Windows 7 post SP1 Convenience Rollup Update». Внимательно ознакомьтесь с разделом Known issues!
Предварительно необходимо установить KB3020369 «April 2015 servicing stack update for Windows 7 and Windows Server 2008 R2».
Источник
Fix Windows Update errors by using the DISM or System Update Readiness tool
Applies to: В Windows 10, version 1809 and later versions, Windows 8.1, Windows Server 2012 R2, Windows 7, Windows Server 2008 R2
Original KB number: В 947821
Symptom
Windows updates and service packs may fail to install if there are corruption errors. For example, an update might not install if a system file is damaged. The DISM or System Update Readiness tool may help you to fix some Windows corruption errors.
This article is intended for Support agents and IT professionals. If you are home users and looking for more information about fixing Windows update errors, see Fix Windows Update errors.
Resolution for Windows 8.1, Windows 10 and Windows Server 2012 R2
To resolve this problem, use the inbox Deployment Image Servicing and Management (DISM) tool. Then, install the Windows update or service pack again.
Open an elevated command prompt. To do this, open Start menu or Start screen, type Command Prompt, right-select Command Prompt, and then select Run as administrator. If you are prompted for an administrator password or for a confirmation, type the password, or select Allow.
Type the following command, and then press Enter. It may take several minutes for the command operation to be completed.
When you run this command, DISM uses Windows Update to provide the files that are required to fix corruptions. However, if your Windows Update client is already broken, use a running Windows installation as the repair source, or use a Windows side-by-side folder from a network share or from a removable media, such as the Windows DVD, as the source of the files. To do this, run the following command instead:
Replace the C:RepairSourceWindows placeholder with the location of your repair source. For more information about using the DISM tool to repair Windows, reference Repair a Windows Image.
Type the sfc /scannow command and press Enter. It may take several minutes for the command operation to be completed.
Close the command prompt, and then run Windows Update again.
DISM creates a log file (%windir%/Logs/CBS/CBS.log) that captures any issues that the tool found or fixed. %windir% is the folder in which Windows is installed. For example, the %windir% folder is C:Windows.
Resolution for Windows 7 and Windows Server 2008 R2
To resolve this problem, use the System Update Readiness tool. Then, install the Windows update or service pack again.
Download the System Update Readiness tool.
Go to Microsoft Update Catalog and download the tool that corresponds to the version of Windows that is running on your computer. For more information about how to find the version of Windows that you installed, see Find out if your computer is running the 32-bit or 64-bit version of Windows.
This tool is updated regularly, we recommend that you always download the latest version. This tool is not available in every supported language. Check the link below to see if it is available in your language.
Install and run the tool.
Select Download on the Download Center webpage, then do one of the following:
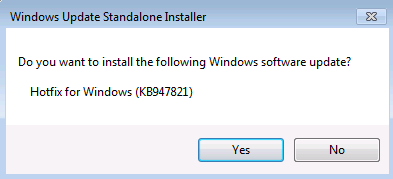
In the Windows Update Standalone Installer dialog box, select Yes.
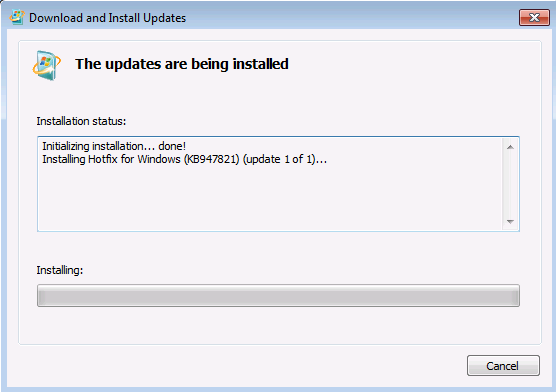
When the tool is being installed, it automatically runs. Although it typically takes less than 15 minutes to run, it might take much longer on some computers. Even if the progress bar seems to stop, the scan is still running, so don’t select Cancel.
When you see Installation complete, select Close.
Reinstall the update or service pack you were trying to install previously.
To manually fix corruption errors that the tool detects but can’t be fixed, see How to fix errors that are found in the CheckSUR log file.
You can also try to directly download the update package from Microsoft Update Catalog, and then install the update package manually.
For example, you may have problems when you try to install updates from Windows Update. In this situation, you can download the update package and try to install the update manually. To do this, follow these steps:
Open Microsoft Update Catalog in Internet Explorer.
In the search box, input the update number that you want to download. In this example, input 3006137. Then, select Search.
Find the update that applies to your operating system appropriately in the search results, and then select Add to add the update to your basket.
Select view basket to open your basket.
Select Download to download the update in your basket.
Select Browse to choose a location for the update you are downloading, and then select Continue.
Select Close after the download process is done. Then, you can find a folder that contains the update package in the location that you specified.
Open the folder, and then double-select the update package to install the update.
If the Windows update or service pack installed successfully, you are finished. If the problem is not fixed, or if System Update Readiness Tool cannot find the cause, contact us for more help.
Description of the common corruption errors
The following table lists the possible error code with Windows Update for your reference:
| Code | Error | Description |
|---|---|---|
| 0x80070002 | ERROR_FILE_NOT_FOUND | The system cannot find the file specified. |
| 0x8007000D | ERROR_INVALID_DATA | The data is invalid. |
| 0x800F081F | CBS_E_SOURCE_MISSING | The source for the package or file not found. |
| 0x80073712 | ERROR_SXS_COMPONENT_STORE_CORRUPT | The component store is in an inconsistent state. |
| 0x800736CC | ERROR_SXS_FILE_HASH_MISMATCH | A component’s file does not match the verification information present in the component manifest. |
| 0x800705B9 | ERROR_XML_PARSE_ERROR | Unable to parse the requested XML data. |
| 0x80070246 | ERROR_ILLEGAL_CHARACTER | An invalid character was encountered. |
| 0x8007370D | ERROR_SXS_IDENTITY_PARSE_ERROR | An identity string is malformed. |
| 0x8007370B | ERROR_SXS_INVALID_IDENTITY_ATTRIBUTE_NAME | The name of an attribute in an identity is not within the valid range. |
| 0x8007370A | ERROR_SXS_INVALID_IDENTITY_ATTRIBUTE_VALUE | The value of an attribute in an identity is not within the valid range. |
| 0x80070057 | ERROR_INVALID_PARAMETER | The parameter is incorrect. |
| 0x800B0100 | TRUST_E_NOSIGNATURE | No signature was present in the subject. |
| 0x80092003 | CRYPT_E_FILE_ERROR | An error occurred while Windows Update reads or writes to a file. |
| 0x800B0101 | CERT_E_EXPIRED | A required certificate is not within its validity period when verifying against the current system clock or the time stamp in the signed file. |
| 0x8007371B | ERROR_SXS_TRANSACTION_CLOSURE_INCOMPLETE | One or more required members of the transaction are not present. |
| 0x80070490 | ERROR_NOT_FOUND | Windows could not search for new updates. |
| 0x800f0984 | PSFX_E_MATCHING_BINARY_MISSING | Matching component directory exist but binary missing |
| 0x800f0986 | PSFX_E_APPLY_FORWARD_DELTA_FAILED | Applying forward delta failed |
| 0x800f0982 | PSFX_E_MATCHING_COMPONENT_NOT_FOUND | Can’t identify matching component for hydration |
Verify the integrity of resources
The System Update Readiness tool verifies the integrity of the following resources:
This list may be updated at any time.
When the System Update Readiness tool detects incorrect manifests, Cabinets, or registry data, it may replace the incorrect data with a corrected version.
Logging
The System Update Readiness tool creates a log file that captures any issues that the tool found or fixed. The log file is located here:
How to fix errors that are found in the CheckSUR log file
To manually fix corruption errors that the System Update Readiness tool detects but can’t fix, follow these steps:
%SYSTEMROOT% is an environment variable that saves the folder in which Windows is installed. For example, generally the %SYSTEMROOT% folder is C:Windows.
Identify the packages that the tool can’t fix. For example, you may find the following in the log file:
In this case, the package that is corrupted is KB958690.
Copy the package (.msu) to the %SYSTEMROOT%CheckSURpackages directory. By default, this directory doesn’t exist and you need to create the directory.
Источник
Восстановление хранилища компонентов при помощи средства проверки готовности системы к обновлению (SURT)
Сегодня вашему вниманию предоставляется еще одно пополнение цикла статей о методах восстановления хранилища компонентов Windows. Помимо изобретения широкой общественностью бесчисленного множества «наколеночных» методик восстановления работоспособности компонентной модели, сами разработчики из Microsoft предлагают вполне официальные методы. В данной публикации мы рассмотрим один из подобных методов, который заключается в восстановлении хранилища компонентов при помощи средства проверки готовности системы к обновлению или, иными словами восстановлении хранилища компонентов при помощи SURT. Фактически описываемым методом предусматривается проверка каталогов/файлов компонентной модели при помощи специализированного пакета и попытка устранения найденных ошибок.
Что же это за средство проверки готовности системы к обновлению?
Представляет собой набор (базу) файлов компонентов, регулярно обновляемый (был, до некоторого времени) по мере выхода новых исправлений. Грубо говоря, утилита SURT это отличный способ для большинства пользователей проанализировать хранилище компонентов в собственной системе на разного рода повреждения, и иметь возможность устранить найденные повреждения в случае, если встроенная база имеет необходимые для восстановления файлы.
Первый запуск SURT
Для начала скачиваем пакет для вашего языка и разрядности системы: KB947821 (x32) или KB947821 (x64). Запускаем только что выкачанный пакет обновления с повышенными привилегиями.
Анализ результатов
После окончания установки (статус: Установка завершена ) проверяем лог-файл %Windir%LogsCBSCheckSUR.log на предмет наличия записей об ошибках. На наличие проблем в хранилище компонентов обычно указывают сообщения о найденных ошибках ( Found X errors ) или недоступных файлов для восстановления ( Unavailable repair files ):
По изначальному замыслу разработчиков, средство SURT предназначалось для автоматического исправления найденных в хранилище компонентов ошибок, именно для этого в продукт поместили полный каталог эталонных файлов. Тем не менее, со временем ситуация изменилась:
Вот именно поэтому, в случае обнаружения в лог-файле %Windir%LogsCBSCheckSUR.log (битых) ненайденных файлов для восстановления, у нас имеется несколько вариантов решения.
Вариант 1: файловая часть
После того, как вы определили имена, есть несколько возможных вариантов решений:
Вариант 2: удаление битого пакета
Этот вариант заключается в ручном удалении проблемного пакета из командной строки.
dism /Online /Remove-Package /PackageName:Package_for_KB3037574
Если получаем ошибку, к примеру 0x8007005, ошибка 5, отказано в доступе.. тогда переходим к следующему методу.
Вариант 3: реестровая часть
Обычно этот вариант предлагается как последняя надежда, когда остальные способы оказались бессильны.
Как мы помним, у компонентной модели Windows имеется часть, размещающаяся в реестре операционной системы.
Источник
|
Корпорация Microsoft представила обновленную версию утилиты System Update Readiness Tool, служащей для проверки операционной системы к установке тех или иных обновлений.
System Update Readiness Tool является программой, устанавливаемой посредством системы Windows Update и работающей в автоматическом режиме. System Update Readiness Tool сканирует систему на наличие некорректных данных, например «битых» веток реестра, неверных системных файлов, оставшихся после неверного удаления или установки различного программного обеспечения – если такие данные могут способствовать неверному процессу установки обновлений, то утилита предупредит об этом пользователя и предложит варианты решения. Загрузка System Update Readiness Tool должна пройти автоматически, причем сама утилита работает во всех современных операционных системах: Windows Vista/Server 2008, Windows 7/Server 2008 R2. Подробную информацию о работе утилиты можно получить здесь Оцените статью: Голосов |
After you use your Windows for a long time, some inconsistencies issues will occur. You can use the System Update Readiness Tool to fix the issues on Windows 7/Vista/2008 R2/2008 and use Deployment Imaging and Servicing Management (DISM) to fix the issues on Windows 10/8.1/8. MiniTool Software will show you how to use these two tools in this post.
When you run your Windows operating system for a long time, the system resources like file data, registry data, and in-memory data may go into inconsistencies. The causes of the inconsistencies are various like hardware failures or software issues.
The situation may be even worse: the inconsistency issue may influence the Windows Servicing Store and your Windows update may be failed due to this.
Since the inconsistency issue can bring troubles to you, you’d better fix the issue and then you can use your Windows as normal and update your Windows to enjoy its new features.
So, here we will talk about System Update Readiness Tool.
System Update Readiness Tool, which is also known as CheckSUR, can address the inconsistency issue. It is a tool that can scan for inconsistency on your Windows computer and then fix them when it is being installed.
Then, in the following part, we will walk you through on how to use System Update Readiness Tool/CheckSUR to fix the inconsistency issue.
How to Use Microsoft CheckSUR?
Note: Before using Microsoft CheckSUR, you should know that the whole scanning and fixing process will last for 15 minutes or even longer. Sometimes, you may find that the process bar stops, but it is still running. You should not cancel it before the whole process ends.
If you are still using Windows 7, Windows Vista, Windows Server 2008 R2, and Windows Server 2008:
You can go to the Microsoft official site to download this tool on your computer and then get the operating system package. Then, you can run it.
The System Update Readiness Tool can verify the integrity of the files that are contained in the following two folders and then replace the found incorrect data:
- %SYSTEMROOT%ServicingPackages
- %SYSTEMROOT%WinSxSManifests
CheckSUR can also verify the registry data that is contained in the following registry subkeys:
- HKEY_LOCAL_MACHINEComponents
- HKEY_LOCAL_MACHINESchema
- HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersionComponent Based Servicing
When necessary, the CheckSUR tool will reset them to the default values.
How to Use Deployment Imaging and Servicing Management (DISM)?
The System Update Readiness Tool only supports Windows 7, Windows Vista, Windows Server 2008 R2, and Windows Server 2008. If you are using Windows 10, Windows 8.1 and Windows 8, you need to use the Windows snap-in Deployment Imaging and Servicing Management (DISM) to solve the inconsistency issue on your computer.
If you are running Windows 10, Windows 8.1 and Windows 8:
You do not need to use the CheckSUR tool into Windows 10/8.1/8. You can just use the DISM tool instead.
Here is a guide on how to use this tool to fix the Windows update issue:
1. Click Windows and search for CMD in the search box.
2. Right-click on the first search result and select Run as administrator.
3. Type the following command line into the Command Prompt window and press Enter after each command:
DISM.exe /Online /Cleanup-image /Scanhealth
DISM.exe /Online /Cleanup-image /Restorehealth
After these steps, you can exit the Command Prompt window and reboot your computer. Then you can go to update your Windows to see whether the update process can work normally.
What is System Update Readiness Tool?
How to use it in Windows 10/8/7?
What is System Update Readiness Tool?
System Update Readiness Tool is a tiny software released by Microsoft that is used for repairing or fixing Windows Update Problems. If you are unable to update windows 10/8/7 or update becomes fail meanwhile the process along with 0x000000 error then the System Update Readiness Tool might be a lifesaver. Here, in this article, I will explain how you can use this utility to fix Windows Update Problem.
How it works?
System Update Readiness Tool regularly scans and fix inconsistency in files and registry settings for installed updates. When you install System Update Readiness Tool, it may take 15 minutes or more to complete. It is not recommended to exit SUR tool meanwhile the installation. However, it doesn’t display the scanning result on the screen but you can find the log report at %windir%LogsCBSCheckSUR.log
Windows 10/8
The System Update Readiness Tool is only available to Windows Vista, Windows 7, Windows Server 2008 and Windows Server 2008 R2. However, if you are running Windows 10 or Windows 8 then this tool is inbuilt into it and you can use it by DISM command and sfc /scannow command. Here, is the great step by step guideline to use these both commands.
How to Run DISM Command in Windows 10/8
How to run sfc /scannow command in Windows 10/8
Windows 7 and Windows Server
In order to use System Update Readiness tool in Windows 7 and Windows Server; you must download this tool from Microsoft website. You can search for “Download System Update Readiness Tool for Windows 7” and you will see the various links to download this tool. Select your Windows Version and download this tool.
Installation
Step 1: Double click on Installer to install tool. Installation is quite simple and easy.
Step 2: When Installation done, it automatically starts scanning process. Keep patience and let the scan complete. It will take around 15 minutes.
Step 3: When Installation completes click to close.
Step 4: Now try to install Windows Update again and hopefully you will not get the Windows Update Error.
What if System Update Readiness Tool doesn’t work?
In most cases, System Update Readiness Tool fails to repair PC problem and you will still be unable to install updates. In this situation, you need to use more powerful and effective solution to fix Windows Error. Download Advanced System Repair Tool and scan your PC problems using it. It is an awesome tool that quickly scans and lists out all the PC problem and lets you fix all by clicking one simple button. You can download this tool from here:
3 Steps to Fix this Error
Summary
System Update Readiness Tool is a great tiny utility that is released by Microsoft to fix Update Problems. However, it is only available for Windows 7 and Windows Server user. In Windows 10 It is inbuilt in DISM command.