- Remove From My Forums
-
Question
-
The explanation of this and the immediately related settings appear inconsistent and/or incorrect. For example:
«To enable client-side SMB packet signing, set Microsoft network client: Digitally sign communications (if server agrees). Computers that have this policy set will not be able to communicate with computers that do not have server-side packet signing
enabled.»The setting reads «if server agrees» so if the server does not agree, then signing is not enforced, right? Why would computers with this setting be unable to communicate with systems lacking SMB signing?
Similarly, the Countermeasures section instructs us to disable the «always» settings and enable the «if agree» settings. This would leave communications vulnerable for any connections where either side does not have SMB signing
enabled, right? That’s not a reliable countermeasure!The relationship between these settings should be clarified. Is there a reason why two registry entries were used, rather than a single entry with three values: OFF; If agreed; Always?
What is the interaction between the «always» setting and the «if agree» setting? Does «always» over-ride «if agree»?
Jaime Castells, CISSP CSSLP
Information Security Architect
CareSource
937-531-3441
Answers
-
Hi
Jaime,Based on my research, the differences between “always” (required) and “if agree” (enabled) are:
- When enable “if agree”, SMB packet signing will be
negotiated between client and server side. - When enable “always” (“if agree” also needs to be enabled) on one side, this side
will not be able to establish a session with another side unless it agrees to perform SMB packet signing.
By default,
client-side SMB signing is enabled on workstations, servers, and domain controllers, server-side SMB signing is enabled only on domain controllers.Here are some links below I suggest you refer to:
Overview of Server Message Block signing
http://support.microsoft.com/kb/887429
Server Message Block communication between a client-side SMB component and a server-side SMB component is not completed if the SMB signing settings are mismatched in Group Policy
or in the registryhttp://support.microsoft.com/kb/916846
Microsoft network client: Digitally sign communications (always)
http://technet.microsoft.com/en-us/library/cc728025(v=WS.10).aspx
Microsoft network client: Digitally sign communications (if server agrees)
http://technet.microsoft.com/en-us/library/cc785861(v=ws.10).aspx
Best Regards,
Amy Wang
-
Marked as answer by
Monday, November 25, 2013 2:12 AM
- When enable “if agree”, SMB packet signing will be
- Remove From My Forums
-
Question
-
The explanation of this and the immediately related settings appear inconsistent and/or incorrect. For example:
«To enable client-side SMB packet signing, set Microsoft network client: Digitally sign communications (if server agrees). Computers that have this policy set will not be able to communicate with computers that do not have server-side packet signing
enabled.»The setting reads «if server agrees» so if the server does not agree, then signing is not enforced, right? Why would computers with this setting be unable to communicate with systems lacking SMB signing?
Similarly, the Countermeasures section instructs us to disable the «always» settings and enable the «if agree» settings. This would leave communications vulnerable for any connections where either side does not have SMB signing
enabled, right? That’s not a reliable countermeasure!The relationship between these settings should be clarified. Is there a reason why two registry entries were used, rather than a single entry with three values: OFF; If agreed; Always?
What is the interaction between the «always» setting and the «if agree» setting? Does «always» over-ride «if agree»?
Jaime Castells, CISSP CSSLP
Information Security Architect
CareSource
937-531-3441
Answers
-
Hi
Jaime,Based on my research, the differences between “always” (required) and “if agree” (enabled) are:
- When enable “if agree”, SMB packet signing will be
negotiated between client and server side. - When enable “always” (“if agree” also needs to be enabled) on one side, this side
will not be able to establish a session with another side unless it agrees to perform SMB packet signing.
By default,
client-side SMB signing is enabled on workstations, servers, and domain controllers, server-side SMB signing is enabled only on domain controllers.Here are some links below I suggest you refer to:
Overview of Server Message Block signing
http://support.microsoft.com/kb/887429
Server Message Block communication between a client-side SMB component and a server-side SMB component is not completed if the SMB signing settings are mismatched in Group Policy
or in the registryhttp://support.microsoft.com/kb/916846
Microsoft network client: Digitally sign communications (always)
http://technet.microsoft.com/en-us/library/cc728025(v=WS.10).aspx
Microsoft network client: Digitally sign communications (if server agrees)
http://technet.microsoft.com/en-us/library/cc785861(v=ws.10).aspx
Best Regards,
Amy Wang
-
Marked as answer by
Monday, November 25, 2013 2:12 AM
- When enable “if agree”, SMB packet signing will be
The Server Message Block (SMB) protocol is used to provide file and print sharing in a Microsoft based network. To help detect man in the middle (MITM) attacks that may modify SMB traffic in transit, we can configure SMB signing via group policy. By digitally signing SMB packets the client and server can confirm where they originated from as well as their authenticity.
SMB packet signing is available in all supported versions of Windows. Microsoft also note that depending on factors such as the SMB version, file sizes, and specific hardware in use, SMB packet signing can degrade the performance of SMB, which is to be expected as we’re signing every packet that goes across the network, which adds overhead.
It’s important to note that this is not encrypting the SMB traffic, we are only going to configure SMB signing so that the client and server can determine if SMB traffic has been modified. SMB encryption has been added as of SMB version 3.0 and newer.
This post is part of our Microsoft 70-744 Securing Windows Server 2016 exam study guide series. For more related posts and information check out our full 70-744 study guide.
Configure SMB Signing via Group Policy
To begin open up Group Policy Management, this can be done either through Server Manager > Tools > Group Policy Management, or by running ‘gpmc.msc’ in PowerShell or Command Prompt. At this point you can either create a new policy for SMB packet signing, or edit an existing policy.
Within the policy navigate to Computer Configuration > Policies > Windows Settings > Security Settings > Local Policies > Security Options.
There are 4 policy items which we will cover below. All of these policy items can either be enabled or disabled. The policies all look like this when editing through GPME, you simply tick to define the policy setting, then choose between enabled or disabled. You can also view the Explain tab to get detailed information on what each option does.
SMB Server Packet Signing
The following two policy items apply to SMB server, that is Windows systems that serve out files or printers for instance over SMB to clients witin the network.
Microsoft network server: Digitally sign communications (always)
This policy option controls whether the server providing SMB requires packet signing, it determines whether or not SMB packet signing must be negotiated before further communication with an SMB client is allowed.
By default this setting is enabled for domain controllers, but disabled for other member servers within the domain.
Microsoft network server: Digitally sign communications (if client agrees)
This policy option determines whether the SMB server will negotiate SMB packet signing with clients that request it. With this setting enabled, the SMB server will negotiate SMB packet signing as per the request of the client. If SMB packet signing is enabled on the client then it will be negotiated by the server. By default this policy is only enabled on domain controllers.
SMB Client Packet Signing
The following two policy items apply to SMB clients, that is Windows systems that connect to an SMB server.
Microsoft network client: Digitally sign communications (always)
Enabling this policy ensures that the SMB client will always require SMB packet signing. If the server does not agree to support SMB packet signing with the client, the client will not communicate with the server. By default this policy is set to disabled, that is SMB is allowed by default without requiring packet signing. It is still possible for packet signing to be negotiated, it is just not required to operate.
Microsoft network client: Digitally sign communications (if server agrees)
This policy is enabled by default, and determines whether the SMB client attempts to negotiate SMB packet signing with the server. If this is instead set to disabled, the client will not attempt to negotiate SMB packet signing at all.
Microsoft no longer recommend using the “if server agrees” or “if client agrees” options, as these options only affect SMB version 1, which you may want to disable anyway.
Summary
We can configure SMB signing via group policy on both the server and client side. By default it’s primarily used on domain controllers in a domain, however by modifying the four policy items outlined above we can protect SMB traffic at the packet level.
This post is part of our Microsoft 70-744 Securing Windows Server 2016 exam study guide series. For more related posts and information check out our full 70-744 study guide.
В версии протокола Server Message Block (SMB) 3.0, представленном в Windows Server 2012 / Windows 8, появилась возможность шифровать данные, передаваемые по сети между файловым сервером SMB и клиентом. Шифрование SMB трафика позволяет защитить от перехвата и модификации данные, передаваемые по недоверенной или открытой сети. Шифрование данных выполняется прозрачно с точки зрения клиента и не требует существенных организационных и ресурсных затрат, как при внедрении VPN, IPSec и PKI инфраструктуры. В последней версии протокола SMB 3.1.1 (представлен в Windows 10 и Windows Server 2016) используется тип шифрования AES 128 GCM, а производительность алгоритма шифрования существенно увеличена. Кроме того осуществляется автоматическое подписывание и проверка целостности данных.
Разберемся в особенностях внедрения шифрования SMB в Windows Server 2012. В первую очередь нужно понять, что в том случае, если клиент и сервер поддерживают разные версии протокола SMB, то при установлении подключения между сервером и клиентом, для взаимодействия выбирается самая высокая версия SMB, поддерживаемая одновременно клиентом и сервером. Это означает, что все клиенты с ОС ниже Windows 8 / Server 2012, не смогут взаимодействовать с сетевым каталогом, для которого включено шифрование SMB.
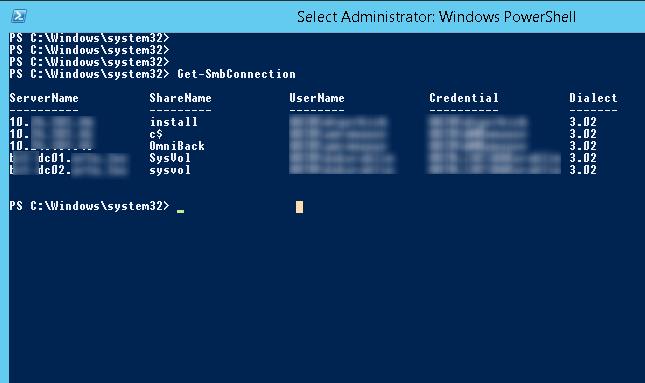
На файловом сервере можно получить версию протокола SMB используемого тем или иным клиентом (версия используемого протокола выбранного в рамках соединения указаны в столбце Dialect):
Get-SmbConnection
Если нужно включить шифрование на конкретного каталога, на сервере откройте консоль Server Manager и перейдите в раздел File and Storage Services –> Shares. Выберите нужную общую папку и откройте ее свойства. Затем перейдите на вкладку Settings, где включите опцию Encrypt Data Access. Сохраните изменения.
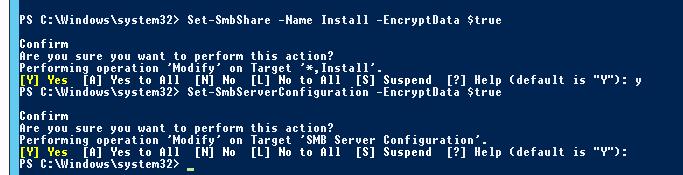
Кроме того, включить SMB шифрование можно из консоли PowerShell. Включаем шифрование для одной папки:
Set-SmbShare –Name Install -EncryptData $true
Либо для всех SMB подключений к серверу (будь то общие папки или административные ресурсы):
Set-SmbServerConfiguration –EncryptData $true
После включения SMB шифрования для общей сетевой папки, все устаревшие клиенты (до Windows 8), не смогут подключаться к данному каталогу, т.к. не поддерживают версию протокола SMB 3.0. Чтобы разрешить доступ таким Windows клиентам (как правило, такой доступ организуется временно, иначе теряется смысл от включения шифрования), можно разрешить подключаться к серверу без шифрования:
Set-SmbServerConfiguration –RejectUnencryptedAccess $false
Совет. После включения данного режима, подключающийся клиент в процессе согласования поддерживаемой версии протокола сможет переключится на совсем устаревшую версию SMB 1.0, что не безопасно (в Windows Server 2012 R2 протокол SMB 1.0 по умолчанию уже отключен). В этом случае, чтобы хотя бы частично обезопасить сервер, желательно отключить поддержку SMB 1.0:
Set-SmbServerConfiguration –EnableSMB1Protocol $false