Сетевой протокол SMB (Server Message Block) используется для предоставления совместного удаленного доступа к файлам, принтерам и другим устройствам через порт TCP 445. В этой статье мы рассмотрим: какие версии (диалекты) протокола SMB доступны в различных версиях Windows (и как они соотносятся с версиями samba в Linux); как определить версию SMB на вашем компьютере; и как включить/отключить клиент и сервер SMBv1, SMBv2 и SMBv3.
Содержание:
- Версии протокола SMB в Windows
- Как проверить поддерживаемые версии SMB в Windows?
- Вывести используемые версии SMB с помощью Get-SMBConnection
- Об опасности использования SMBv1
- Включение и отключение SMBv1, SMBv2 и SMBv3 в Windows
Версии протокола SMB в Windows
Есть несколько версии протокола SMB (диалектов), которые последовательно появлялись в новых версиях Windows:
Для реализации протокола SMB в Linux/Unix системах используется samba. В скобках мы указали в каких версиях samba поддерживается каждый диалект SMB.
- CIFS — Windows NT 4.0;
- SMB 1.0 — Windows 2000;
- SMB 2.0 — Windows Server 2008 и Windows Vista SP1 (поддерживается в Samba 3.6);
- SMB 2.1 — Windows Server 2008 R2 и Windows 7 (поддерживается в Samba 4.0);
- SMB 3.0 — Windows Server 2012 и Windows 8 (поддерживается в Samba 4.2);
- SMB 3.02 — Windows Server 2012 R2 и Windows 8. 1 (не поддерживается в Samba);
- SMB 3.1.1 – Windows Server 2016 и Windows 10 (не поддерживается в Samba).
Начиная с версии Samba 4.14, по умолчанию используется SMB2.1.
При сетевом взаимодействии по протоколу SMB между клиентом и сервером используется максимальная версия протокола, поддерживаемая одновременно и клиентом, и сервером.
Ниже представлена сводная таблица, по которой можно определить версию протокола SMB, которая выбирается при взаимодействии разных версий Windows:
| Операционная система | Win 10, Server 2016 | Windows 8.1, Server 2012 R2 |
Windows 8, Server 2012 |
Windows 7, Server 2008 R2 |
Windows Vista, Server 2008 |
Windows XP, Server 2003 и ниже |
| Windows 10 , Windows Server 2016 |
SMB 3.1.1 | SMB 3.02 | SMB 3.0 | SMB 2.1 | SMB 2.0 | SMB 1.0 |
| Windows 8.1 , Server 2012 R2 |
SMB 3.02 | SMB 3.02 | SMB 3.0 | SMB 2.1 | SMB 2.0 | SMB 1.0 |
| Windows 8 , Server 2012 |
SMB 3.0 | SMB 3.0 | SMB 3.0 | SMB 2.1 | SMB 2.0 | SMB 1.0 |
| Windows 7, Server 2008 R2 |
SMB 2.1 | SMB 2.1 | SMB 2.1 | SMB 2.1 | SMB 2.0 | SMB 1.0 |
| Windows Vista, Server 2008 |
SMB 2.0 | SMB 2.0 | SMB 2.0 | SMB 2.0 | SMB 2.0 | SMB 1.0 |
| Windows XP, 2003 и ниже | SMB 1.0 | SMB 1.0 | SMB 1.0 | SMB 1.0 | SMB 1.0 | SMB 1.0 |
К примеру, при подключении клиентского компьютера с Windows 8.1 к файловому серверу с Windows Server 2016 будет использоваться протокол SMB 3.0.2.
Согласно таблице Windows XP, Windows Server 2003 для доступа к общим файлам и папкам на сервере могут использовать только SMB 1.0, который в новых версиях Windows Server (2012 R2 / 2016) может быть отключен. Таким образом, если в вашей инфраструктуре одновременно используются компьютеры с Windows XP (снятой с поддержки), Windows Server 2003/R2 и сервера с Windows Server 2012 R2/2016/2019, устаревшие клиенты не смогут получить доступ к файлам и папкам на файловом сервере с новой ОС.
Если Windows Server 2016/2012 R2 с отключенным SMB v1.0 используется в качестве контроллера домена, значить клиенты на Windows XP/Server 2003 не смогут получить доступ к каталогам SYSVOL и NETLOGON на контроллерах домена и авторизоваться в AD.
На старых клиентах при попытке подключиться к ресурсу на файловом сервере с отключенным SMB v1 появляется ошибка:
The specified network name is no longer available
Как проверить поддерживаемые версии SMB в Windows?
Рассмотрим, как определить, какие версии протокола SMB поддерживаются на вашем компьютере Windows.
В Windows 10, 8.1 и Windows Server 2019/2016/2012R2 вы можете проверить состояние различных диалектов SMB протокола с помощью PowerShell:
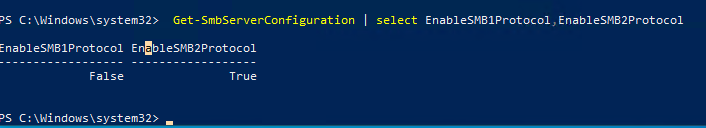
Get-SmbServerConfiguration | select EnableSMB1Protocol,EnableSMB2Protocol
Данная команда вернула, что протокол SMB1 отключен (
EnableSMB1Protocol=False
), а протоколы SMB2 и SMB3 включены (
EnableSMB1Protocol=True
).
Обратите внимание, что протоколы SMBv3 и SMBv2 тесно связаны между собой. Нельзя отключить или включить отдельно SMBv3 или SMBv2. Они всегда включаются/отключаются только совместно, т.к. используют один стек.
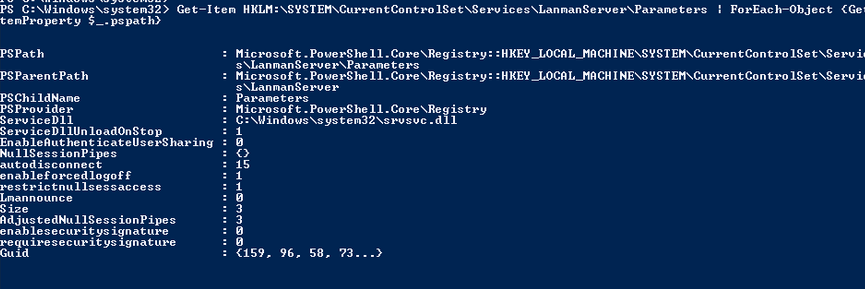
В Windows 7, Vista, Windows Server 2008 R2/2008:
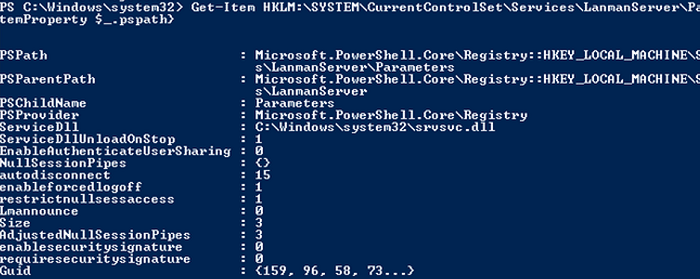
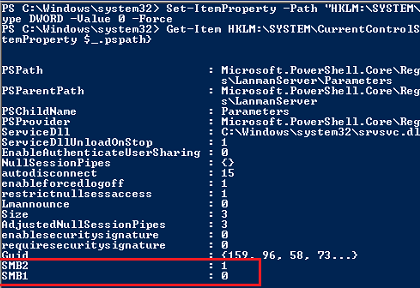
Get-Item HKLM:SYSTEMCurrentControlSetServicesLanmanServerParameters | ForEach-Object {Get-ItemProperty $_.pspath}
Если в данной ветке реестра нет параметров с именами SMB1 или SMB2, значить протоколы SMB1 и SMB2 по умолчанию включены.
Также в этих версиях Windows вы можете проверить, какие диалекты SMB разрешено использовать в качестве клиентов с помощью команд:
sc.exe query mrxsmb10
SERVICE_NAME: mrxsmb10 TYPE : 2 FILE_SYSTEM_DRIVER STATE : 4 RUNNING (STOPPABLE, NOT_PAUSABLE, IGNORES_SHUTDOWN) WIN32_EXIT_CODE : 0 (0x0) SERVICE_EXIT_CODE : 0 (0x0) CHECKPOINT : 0x0 WAIT_HINT : 0x0
sc.exe query mrxsmb20
SERVICE_NAME: mrxsmb20 TYPE : 2 FILE_SYSTEM_DRIVER STATE : 4 RUNNING (STOPPABLE, NOT_PAUSABLE, IGNORES_SHUTDOWN) WIN32_EXIT_CODE : 0 (0x0) SERVICE_EXIT_CODE : 0 (0x0) CHECKPOINT : 0x0 WAIT_HINT : 0x0
В обоих случаях службы запущены (
STATE=4 Running
). Значит Windows может подключаться как к SMBv1, так и к SMBv2 серверам.
Вывести используемые версии SMB с помощью Get-SMBConnection
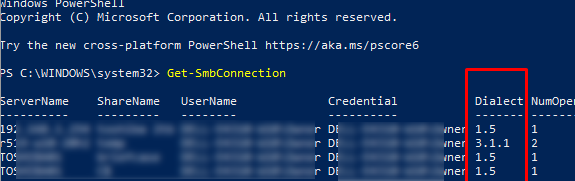
Как мы говорили раньше, компьютеры при взаимодействии по протоколу SMB используют максимальную версию, поддерживаемую как клиентом, так и сервером. Для определения версии SMB, используемой для доступа к удаленному компьютеру можно использовать командлет PowerShell
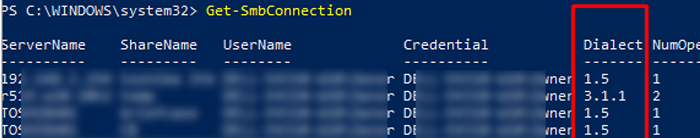
Get-SMBConnection
:
Версия SMB, используемая для подключения к удаленному серверу (ServerName) указана в столбце Dialect.
Можно вывести информацию о версиях SMB, используемых для доступа к конкретному серверу:
Get-SmbConnection -ServerName servername
Если нужно отобразить, используется ли SMB шифрование (появилось в SMB 3.0), выполните:
Get-SmbConnection | ft ServerName,ShareName,Dialect,Encrypted,UserName
В Linux вывести список SMB подключения и используемые диалекты в samba можно командой:
$ sudo smbstatus
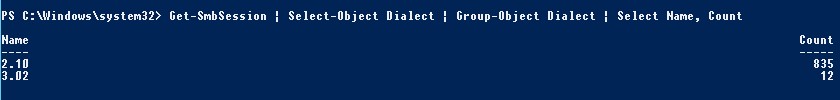
Чтобы на стороне сервера вывести список используемых клиентами версий протокола SMB и количество клиентов, используемых ту или иную версию протокола SMB, выполните команду:
Get-SmbSession | Select-Object -ExpandProperty Dialect | Sort-Object -Unique
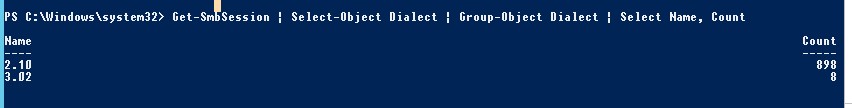
В нашем примере имеется 825 клиентов, подключенных к серверу с помощью SMB 2.1 (Windows 7/Windows Server 2008 R2) и 12 клиентов SMB 3.02.
С помощью PowerShell можно включить аудит версий SMB, используемых для подключения:
Set-SmbServerConfiguration –AuditSmb1Access $true
События подключения затем можно извлечь из журналов Event Viewer с помощью PowerShell:
Get-WinEvent -LogName Microsoft-Windows-SMBServer/Audit
Об опасности использования SMBv1
Последние несколько лет Microsoft из соображений безопасности планомерно отключает устаревший протокол SMB 1.0. Связано это с большим количеством критических уязвимостей в этом протоколе (вспомните историю с эпидемиями вирусов-шифровальщиков wannacrypt и petya, которые использовали уязвимость именно в протоколе SMBv1). Microsoft и другие IT компании настоятельно рекомендуют отказаться от его использования.
Однако отключение SMBv1 может вызвать проблемы с доступом к общий файлам и папкам на новых версиях Windows 10 (Windows Server 2016/2019) с устаревших версий клиентов (Windows XP, Server 2003), сторонних ОС (Mac OSX 10.8 Mountain Lion, Snow Leopard, Mavericks, старые версии Linux), различных старых NAS устройствах.
Если в вашей сети не осталось legacy устройств с поддержкой только SMBv1, обязательно отключайте эту версию диалекта в Windows.
В том случае, если в вашей сети остались клиенты с Windows XP, Windows Server 2003 или другие устройства, которые поддерживают только SMBv1, их нужно как можно скорее обновить или тщательно изолировать.
Включение и отключение SMBv1, SMBv2 и SMBv3 в Windows
Рассмотрим способы включения, отключения различных версий SMB в Windows. Мы рассматриваем отдельно включение клиента и сервера SMB (это разные компоненты).
Windows 10, 8.1, Windows Server 2019/2016/2012R2:
Отключить клиент и сервер SMBv1:
Disable-WindowsOptionalFeature -Online -FeatureName smb1protocol
Отключить только SMBv1 сервер:
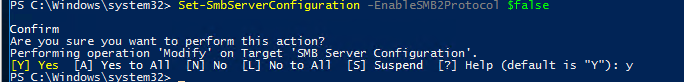
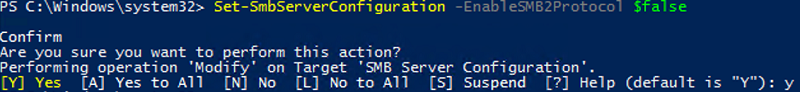
Set-SmbServerConfiguration -EnableSMB1Protocol $false
Включить клиент и сервер SMBv1:
Enable-WindowsOptionalFeature -Online -FeatureName smb1protocol
Включить только SMBv1 сервер:
Set-SmbServerConfiguration -EnableSMB1Protocol $true
Отключить сервер SMBv2 и SMBv3:
Set-SmbServerConfiguration -EnableSMB2Protocol $false
Включить сервер SMBv2 и SMBv3:
Set-SmbServerConfiguration -EnableSMB2Protocol $true
Windows 7, Vista, Windows Server 2008 R2/2008:
Отключить SMBv1 сервер:
Set-ItemProperty -Path "HKLM:SYSTEMCurrentControlSetServicesLanmanServerParameters" SMB1 -Type DWORD -Value 0 –Force
Включить SMBv1 сервер:
Set-ItemProperty -Path "HKLM:SYSTEMCurrentControlSetServicesLanmanServerParameters" SMB1 -Type DWORD -Value 1 –Force
Отключить SMBv1 клиент:
sc.exe config lanmanworkstation depend= bowser/mrxsmb20/nsi
sc.exe config mrxsmb10 start= disabled
Включить SMBv1 клиент:
sc.exe config lanmanworkstation depend= bowser/mrxsmb10/mrxsmb20/nsi
sc.exe config mrxsmb10 start= auto
Отключить SMBv2 сервер:
Set-ItemProperty -Path "HKLM:SYSTEMCurrentControlSetServicesLanmanServerParameters" SMB2 -Type DWORD -Value 0 -Force
Включить SMBv2 сервер
Set-ItemProperty -Path "HKLM:SYSTEMCurrentControlSetServicesLanmanServerParameters" SMB2 -Type DWORD -Value 1 –Force
Отключить SMBv2 клиент:
sc.exe config lanmanworkstation depend= bowser/mrxsmb10/nsi
sc.exe config mrxsmb20 start= disabled
Включить SMBv2 клиент:
sc.exe config lanmanworkstation depend= bowser/mrxsmb10/mrxsmb20/nsi
sc.exe config mrxsmb20 start= auto
Для отключения сервера SMBv1 на всех компьютерах независимо от версии Windows можно распространить параметр реестра типа REG_DWORD с именем SMB1 и значением 0 (HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesLanmanServerParameters)на через GPO.
Для отключения SMBv2 нужно в этой же ветке установить параметр SMB2=0.
Для отключения SMBv1 клиента нужно распространить такой параметр реестра:
- Key: HKEY_LOCAL_MACHINESYSTEMCurrentControlSetservicesmrxsmb10
- Name: Start
- Type: REG_DWORD
- Value: 4
При отключении SMB 1.0/CIFS File Sharing Support в Windows вы можете столкнуться с ошибкой “0x80070035, не найден сетевой путь”, ошибкой при доступе к общим папкам, и проблемами обнаружения компьютеров в сетевом окружении. В этом случае вместо служба обозревателя компьютеров (Computer Browser) нужно использовать службы обнаружения (линк).
| title | description | author | manager | ms.topic | ms.author | ms.date | ms.custom |
|---|---|---|---|---|---|---|---|
|
How to detect, enable and disable SMBv1, SMBv2, and SMBv3 in Windows |
Describes how to enable and disable the Server Message Block protocol (SMBv1, SMBv2, and SMBv3) in Windows client and server environments. |
Deland-Han |
dcscontentpm |
how-to |
delhan |
12/12/2022 |
contperf-fy21q2 |
How to detect, enable and disable SMBv1, SMBv2, and SMBv3 in Windows
Applies to: Windows Server 2022, Windows Server 2019, Windows Server 2016, Windows Server 2012 R2, Windows Server 2012, Windows 11, Windows 10, Windows 8.1, Windows 8
This article describes how to enable and disable Server Message Block (SMB) version 1 (SMBv1), SMB version 2 (SMBv2), and SMB version 3 (SMBv3) on the SMB client and server components.
While disabling or removing SMBv1 might cause some compatibility issues with old computers or software, SMBv1 has significant security vulnerabilities, and we strongly encourage you not to use it.
Disabling SMBv2 or SMBv3 for troubleshooting
We recommend keeping SMBv2 and SMBv3 enabled, but you might find it useful to disable one temporarily for troubleshooting. For more information, see How to detect status, enable, and disable SMB protocols on the SMB Server.
In Windows 10, Windows 8.1, Windows Server 2019, Windows Server 2016, Windows Server 2012 R2, and Windows Server 2012, disabling SMBv3 deactivates the following functionality:
- Transparent Failover — clients reconnect without interruption to cluster nodes during maintenance or failover
- Scale Out — concurrent access to shared data on all file cluster nodes
- Multichannel — aggregation of network bandwidth and fault tolerance if multiple paths are available between client and server
- SMB Direct — adds RDMA networking support for high performance, with low latency and low CPU use
- Encryption — Provides end-to-end encryption and protects from eavesdropping on untrustworthy networks
- Directory Leasing — Improves application response times in branch offices through caching
- Performance Optimizations — optimizations for small random read/write I/O
In Windows 7 and Windows Server 2008 R2, disabling SMBv2 deactivates the following functionality:
- Request compounding — allows for sending multiple SMBv2 requests as a single network request
- Larger reads and writes — better use of faster networks
- Caching of folder and file properties — clients keep local copies of folders and files
- Durable handles — allow for connection to transparently reconnect to the server if there’s a temporary disconnection
- Improved message signing — HMAC SHA-256 replaces MD5 as hashing algorithm
- Improved scalability for file sharing — number of users, shares, and open files per server greatly increased
- Support for symbolic links
- Client oplock leasing model — limits the data transferred between the client and server, improving performance on high-latency networks and increasing SMB server scalability
- Large MTU support — for full use of 10 Gigabit Ethernet (GbE)
- Improved energy efficiency — clients that have open files to a server can sleep
The SMBv2 protocol was introduced in Windows Vista and Windows Server 2008, while the SMBv3 protocol was introduced in Windows 8 and Windows Server 2012. For more information about SMBv2 and SMBv3 capabilities, see the following articles:
- Server Message Block overview
- What’s New in SMB
How to remove SMBv1 via PowerShell
Here are the steps to detect, disable and enable SMBv1 client and server by using PowerShell commands with elevation.
[!NOTE]
The computer will restart after you run the PowerShell commands to disable or enable SMBv1.
-
Detect:
Get-WindowsOptionalFeature -Online -FeatureName SMB1Protocol
-
Disable:
Disable-WindowsOptionalFeature -Online -FeatureName SMB1Protocol
-
Enable:
Enable-WindowsOptionalFeature -Online -FeatureName SMB1Protocol
[!TIP]
You can detect SMBv1 status, without elevation, by running:Get-SmbServerConfiguration | Format-List EnableSMB1Protocol.
Windows Server 2012 Windows Server 2012 R2, Windows Server 2016, Windows Server 2019: Server Manager method
To remove SMBv1 from Windows Server:
- On the Server Manager Dashboard of the server where you want to remove SMBv1, under Configure this local server, select Add roles and features.
- On the Before you begin page, select Start the Remove Roles and Features Wizard, and then on the following page, select Next.
- On the Select destination server page under Server Pool, ensure that the server you want to remove the feature from is selected, and then select Next.
- On the Remove server roles page, select Next.
- On the Remove features page, clear the check box for SMB 1.0/CIFS File Sharing Support and select Next.
- On the Confirm removal selections page, confirm that the feature is listed, and then select Remove.
Windows 8.1, Windows 10, and Windows 11: Add or Remove Programs method
To disable SMBv1 for the mentioned operating systems:
- In Control Panel, select Programs and Features.
- Under Control Panel Home, select Turn Windows features on or off to open the Windows Features box.
- In the Windows Features box, scroll down the list, clear the check box for SMB 1.0/CIFS File Sharing Support and select OK.
- After Windows applies the change, on the confirmation page, select Restart now.
How to detect status, enable, and disable SMB protocols
[!NOTE]
When you enable or disable SMBv2 in Windows 8 or Windows Server 2012, SMBv3 is also enabled or disabled. This behavior occurs because these protocols share the same stack.
Server
Windows 8 and Windows Server 2012 introduced the new Set-SMBServerConfiguration Windows PowerShell cmdlet. The cmdlet enables you to enable or disable the SMBv1, SMBv2, and SMBv3 protocols on the server component.
You don’t have to restart the computer after you run the Set-SMBServerConfiguration cmdlet.
SMBv1
-
Detect:
Get-SmbServerConfiguration | Select EnableSMB1Protocol
-
Disable:
Set-SmbServerConfiguration -EnableSMB1Protocol $false
-
Enable:
Set-SmbServerConfiguration -EnableSMB1Protocol $true
For more information, see Server storage at Microsoft.
SMB v2/v3
-
Detect:
Get-SmbServerConfiguration | Select EnableSMB2Protocol
-
Disable:
Set-SmbServerConfiguration -EnableSMB2Protocol $false
-
Enable:
Set-SmbServerConfiguration -EnableSMB2Protocol $true
For Windows 7, Windows Server 2008 R2, Windows Vista, and Windows Server 2008
To enable or disable SMB protocols on an SMB Server that is running Windows 7, Windows Server 2008 R2, Windows Vista, or Windows Server 2008, use Windows PowerShell or Registry Editor.
Additional PowerShell methods
[!NOTE]
This method requires PowerShell 2.0 or later.
SMBv1 on SMB Server
Detect:
Get-Item HKLM:SYSTEMCurrentControlSetServicesLanmanServerParameters | ForEach-Object {Get-ItemProperty $_.pspath}
Default configuration = Enabled (No registry named value is created), so no SMB1 value will be returned
Disable:
Set-ItemProperty -Path "HKLM:SYSTEMCurrentControlSetServicesLanmanServerParameters" SMB1 -Type DWORD -Value 0 -Force
Enable:
Set-ItemProperty -Path "HKLM:SYSTEMCurrentControlSetServicesLanmanServerParameters" SMB1 -Type DWORD -Value 1 -Force
Note You must restart the computer after you make these changes.
For more information, see Server storage at Microsoft.
SMBv2/v3 on SMB Server
Detect:
Get-ItemProperty HKLM:SYSTEMCurrentControlSetServicesLanmanServerParameters | ForEach-Object {Get-ItemProperty $_.pspath}
Disable:
Set-ItemProperty -Path "HKLM:SYSTEMCurrentControlSetServicesLanmanServerParameters" SMB2 -Type DWORD -Value 0 -Force
Enable:
Set-ItemProperty -Path "HKLM:SYSTEMCurrentControlSetServicesLanmanServerParameters" SMB2 -Type DWORD -Value 1 -Force
[!NOTE]
You must restart the computer after you make these changes.
Registry Editor
[!IMPORTANT]
Follow the steps in this section carefully. Serious problems might occur if you modify the registry incorrectly. Before you modify it, back up the registry for restoration in case problems occur.
To enable or disable SMBv1 on the SMB server, configure the following registry key:
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesLanmanServerParameters
Registry entry: SMB1
REG_DWORD: 0 = Disabled
REG_DWORD: 1 = Enabled
Default: 1 = Enabled (No registry key is created)
To enable or disable SMBv2 on the SMB server, configure the following registry key:
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesLanmanServerParameters
Registry entry: SMB2
REG_DWORD: 0 = Disabled
REG_DWORD: 1 = Enabled
Default: 1 = Enabled (No registry key is created)
[!NOTE]
You must restart the computer after you make these changes.
Client
Here is how to detect status, enable, and disable SMB protocols on the SMB Client that is running Windows 10, Windows Server 2019, Windows 8.1, Windows Server 2016, Windows Server 2012 R2, and Windows Server 2012.
SMBv1 on SMB Client
-
Detect
sc.exe qc lanmanworkstation
-
Disable:
sc.exe config lanmanworkstation depend= bowser/mrxsmb20/nsi sc.exe config mrxsmb10 start= disabled
-
Enable:
sc.exe config lanmanworkstation depend= bowser/mrxsmb10/mrxsmb20/nsi sc.exe config mrxsmb10 start= auto
For more information, see Server storage at Microsoft
SMB v2/v3 on SMB Client
-
Detect:
sc.exe qc lanmanworkstation
-
Disable:
sc.exe config lanmanworkstation depend= bowser/mrxsmb10/nsi sc.exe config mrxsmb20 start= disabled
-
Enable:
sc.exe config lanmanworkstation depend= bowser/mrxsmb10/mrxsmb20/nsi sc.exe config mrxsmb20 start= auto
[!NOTE]
- You must run these commands at an elevated command prompt.
- You must restart the computer after you make these changes.
Disable SMBv1 by using Group Policy
This section introduces how to use Group Policy to disable SMBv1. You can use this method on different versions of Windows.
Server
SMBv1
This procedure configures the following new item in the registry:
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesLanmanServerParameters
- Registry entry: SMB1
- REG_DWORD: 0 = Disabled
To use Group Policy to configure this, follow these steps:
-
Open the Group Policy Management Console. Right-click the Group Policy object (GPO) that should contain the new preference item, and then click Edit.
-
In the console tree under Computer Configuration, expand the Preferences folder, and then expand the Windows Settings folder.
-
Right-click the Registry node, point to New, and select Registry Item.
In the New Registry Properties dialog box, select the following:
- Action: Create
- Hive: HKEY_LOCAL_MACHINE
- Key Path: SYSTEMCurrentControlSetServicesLanmanServerParameters
- Value name: SMB1
- Value type: REG_DWORD
- Value data: 0
This procedure disables the SMBv1 Server components. This Group Policy must be applied to all necessary workstations, servers, and domain controllers in the domain.
[!NOTE]
WMI filters can also be set to exclude unsupported operating systems or selected exclusions, such as Windows XP.
[!IMPORTANT]
Be careful when you make these changes on domain controllers on which legacy Windows XP or older Linux and third-party systems (that don’t support SMBv2 or SMBv3) require access to SYSVOL or other file shares where SMB v1 is being disabled.
Client
SMB v1
To disable the SMBv1 client, the services registry key needs to be updated to disable the start of MRxSMB10, and then the dependency on MRxSMB10 needs to be removed from the entry for LanmanWorkstation so that it can start normally without requiring MRxSMB10 to first start.
This guidance updates and replaces the default values in the following two items in the registry:
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetservicesmrxsmb10
Registry entry: Start REG_DWORD: 4= Disabled
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesLanmanWorkstation
Registry entry: DependOnService REG_MULTI_SZ: «Bowser»,»MRxSmb20″,»NSI»
[!NOTE]
The default included MRxSMB10 which is now removed as dependency.
To configure this by using Group Policy, follow these steps:
-
Open the Group Policy Management Console. Right-click the GPO that should contain the new preference item, and then click Edit.
-
In the console tree under Computer Configuration, expand the Preferences folder, and then expand the Windows Settings folder.
-
Right-click the Registry node, point to New, and select Registry Item.
-
In the New Registry Properties dialog box, select the following:
- Action: Update
- Hive: HKEY_LOCAL_MACHINE
- Key Path: SYSTEMCurrentControlSetservicesmrxsmb10
- Value name: Start
- Value type: REG_DWORD
- Value data: 4
-
Then remove the dependency on the MRxSMB10 that was disabled.
In the New Registry Properties dialog box, select the following:
- Action: Replace
- Hive: HKEY_LOCAL_MACHINE
- Key Path: SYSTEMCurrentControlSetServicesLanmanWorkstation
- Value name: DependOnService
- Value type: REG_MULTI_SZ
- Value data:
- Bowser
- MRxSmb20
- NSI
[!NOTE]
These three strings will not have bullets (see the following screen shot).The default value includes MRxSMB10 in many versions of Windows, so by replacing them with this multi-value string, it is in effect removing MRxSMB10 as a dependency for LanmanWorkstation and going from four default values down to just these three values above.
[!NOTE]
When you use Group Policy Management Console, you don’t have to use quotation marks or commas. Just type each entry on individual lines. -
Restart the targeted systems to finish disabling SMB v1.
Auditing SMBv1 usage
To determine which clients are attempting to connect to an SMB server with SMBv1, you can enable auditing on Windows Server 2016, Windows 10, and Windows Server 2019. You can also audit on Windows 7 and Windows Server 2008 R2 if the May 2018 monthly update is installed, and on Windows 8.1 and Windows Server 2012 R2 if the July 2017 monthly update is installed.
-
Enable:
Set-SmbServerConfiguration -AuditSmb1Access $true
-
Disable:
Set-SmbServerConfiguration -AuditSmb1Access $false
-
Detect:
Get-SmbServerConfiguration | Select AuditSmb1Access
When SMBv1 auditing is enabled, event 3000 appears in the «Microsoft-Windows-SMBServerAudit» event log, identifying each client that attempts to connect with SMBv1.
Summary
If all the settings are in the same GPO, Group Policy Management displays the following settings.
Testing and validation
After completing the configuration steps in this article, allow the policy to replicate and update. As necessary for testing, run gpupdate /force at a command prompt, and then review the target computers to make sure that the registry settings are applied correctly. Make sure SMBv2 and SMBv3 are functioning for all other systems in the environment.
[!NOTE]
Don’t forget to restart the target systems.
The Server Message Block (SMB) network protocol is used to share and access folders, files, printers, and other devices over network (TCP port 445). In this article, we will look at which versions (dialects) of SMB are available in different versions of Windows (and how they relate to samba versions on Linux); how to check the SMB version in use on your computer; and how to enable or disable the SMBv1, SMBv2, and SMBv3 dialects.
Contents:
- SMB Protocol Versions in Windows
- How to Check SMB Version on Windows?
- Checking Used SMB Dialects with Get-SMBConnection
- Stop Using the Insecure SMBv1 Protocol
- How to Enable and Disable SMBv1, SMBv2, and SMBv3 on Windows?
SMB Protocol Versions in Windows
There are several versions of the SMB protocol (dialects) that have consistently appeared in new Windows versions (and samba) :
- CIFS – Windows NT 4.0
- SMB 1.0 – Windows 2000
- SMB 2.0 – Windows Server 2008 and Windows Vista SP1 (supported in Samba 3.6)
- SMB 2.1 – Windows Server 2008 R2 and Windows 7 (Samba 4.0)
- SMB 3.0 – Windows Server 2012 and Windows 8 (Samba 4.2)
- SMB 3.02 – Windows Server 2012 R2 and Windows 8.1 (not supported in Samba)
- SMB 3.1.1 – Windows Server 2016 and Windows 10 (not supported in Samba)
Samba is used to implement the SMB protocol in Linux/Unix . Samba 4.14 and newer uses SMB 2.1 by default.
In SMB network communication, the client and server use the maximum SMB protocol version supported by both the client and the server.
The summary table of SMB version compatibility looks like this. Using this table, you can determine the version of the SMB protocol that is selected when different versions of Windows interact:
| Operating System | Windows 10, Win Server 2016 | Windows 8.1, Win Server 2012 R2 | Windows 8,Server 2012 | Windows 7,Server 2008 R2 | Windows Vista,Server 2008 | Windows XP, Server 2003 and earlier |
| Windows 10, Windows Server 2016 | SMB 3.1.1 | SMB 3.02 | SMB 3.0 | SMB 2.1 | SMB 2.0 | SMB 1.0 |
| Windows 8.1, Server 2012 R2 | SMB 3.02 | SMB 3.02 | SMB 3.0 | SMB 2.1 | SMB 2.0 | SMB 1.0 |
| Windows 8, Server 2012 | SMB 3.0 | SMB 3.0 | SMB 3.0 | SMB 2.1 | SMB 2.0 | SMB 1.0 |
| Windows 7, Server 2008 R2 | SMB 2.1 | SMB 2.1 | SMB 2.1 | SMB 2.1 | SMB 2.0 | SMB 1.0 |
| Windows Vista, Server 2008 | SMB 2.0 | SMB 2.0 | SMB 2.0 | SMB 2.0 | SMB 2.0 | SMB 1.0 |
| Windows XP, 2003 and earlier | SMB 1.0 | SMB 1.0 | SMB 1.0 | SMB 1.0 | SMB 1.0 | SMB 1.0 |
For example, if a client computer running Windows 8.1 connects to a file server with Windows Server 2016, the SMB 3.0.2 protocol will be used.
According to the table, Windows XP and Windows Server 2003 can use only SMB 1.0 to access shared folders and files. The SMBv1 is disabled in newer versions of Windows Server (2012 R2/2016). So, if you are still using Windows XP and Windows Server 2003 devices on your network, they won’t be able to access shared folders on the file server running Windows Server 2016.
If Windows Server 2019/2016 with disabled SMB v1.0 is used as a domain controller, then Windows XP/Server 2003 clients won’t be able to access the SYSVOL and NETLOGON folders on domain controllers and authenticate with AD.
You may receive the following error when trying to connect to a shared folder on a file server with SMBv1 disabled:
The specified network name is no longer available
How to Check SMB Version on Windows?
Let’s look on how to find out which versions of the SMB are enabled on your Windows device.
On Windows 10/8.1 and Windows Server 2019/2016/2012R2, you can check the status of various dialects of the SMB protocol using PowerShell:
Get-SmbServerConfiguration | select EnableSMB1Protocol,EnableSMB2Protocol
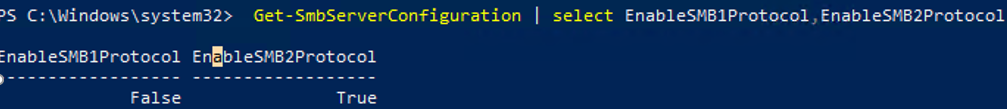
This command returned that the SMB1 protocol is disabled (EnableSMB1Protocol = True), and the SMB2 and SMB3 protocols are enabled (EnableSMB1Protocol = False).
Note that the SMBv3 and SMBv2 protocols are closely related. You cannot disable or enable SMBv3 or SMBv2 separately. They are always enabled/disabled only together because they share the same stack.
On Windows 7, Vista, and Windows Server 2008 R2/2008:
Get-Item HKLM:SYSTEMCurrentControlSetServicesLanmanServerParameters | ForEach-Object {Get-ItemProperty $_.pspath}
If there are no parameters named SMB1 or SMB2 in this registry key, then the SMBv1 and SMBv2 protocols are enabled by default.
Also on these Windows versions, you can check which SMB client dialects are allowed to connect to remote hosts:
sc.exe query mrxsmb10
SERVICE_NAME: mrxsmb10 TYPE : 2 FILE_SYSTEM_DRIVER STATE : 4 RUNNING (STOPPABLE, NOT_PAUSABLE, IGNORES_SHUTDOWN) WIN32_EXIT_CODE : 0 (0x0) SERVICE_EXIT_CODE : 0 (0x0) CHECKPOINT : 0x0 WAIT_HINT : 0x0
sc.exe query mrxsmb20
SERVICE_NAME: mrxsmb20 TYPE : 2 FILE_SYSTEM_DRIVER STATE : 4 RUNNING (STOPPABLE, NOT_PAUSABLE, IGNORES_SHUTDOWN) WIN32_EXIT_CODE : 0 (0x0) SERVICE_EXIT_CODE : 0 (0x0) CHECKPOINT : 0x0 WAIT_HINT : 0x0
In both cases, the services are running (STATE = 4 Running). This means that the current Windows device can connect to both SMBv1 and SMBv2 hosts.
Checking Used SMB Dialects with Get-SMBConnection
When communicating over SMB, computers use the maximum SMB version supported by both the client and the server. The Get-SMBConnection PowerShell cmdlet can be used to check the SMB version used to access a remote computer:
The SMB version used to connect to the remote server (ServerName) is listed in the Dialect column.
You can display information about the SMB versions used to access a specific server:
Get-SmbConnection -ServerName srvfs01
If you want to display if SMB encryption is in use (introduced in SMB 3.0):
Get-SmbConnection | ft ServerName,ShareName,Dialect,Encrypted,UserName
On Linux, you can display a list of SMB connections and used dialects in samba using the command:
$ sudo smbstatus
On the Windows SMB server side, you can display a list of the versions of the SMB protocols that the clients are currently using. Run the command:
Get-SmbSession | Select-Object -ExpandProperty Dialect | Sort-Object -Unique
You can use PowerShell to enable auditing of the SMB versions used for the connection:
Set-SmbServerConfiguration –AuditSmb1Access $true
SMB connection events can then be exported from Event Viewer logs:
Get-WinEvent -LogName Microsoft-Windows-SMBServer/Audit
Stop Using the Insecure SMBv1 Protocol
Over the past few years, Microsoft has systematically disabled the legacy SMB 1.0 protocol in all products for security reasons. This is due to the large number of critical vulnerabilities in this protocol (remember the incidents with wannacrypt and petya ransomware, which exploited a vulnerability in the SMBv1 protocol). Microsoft and other IT companies strongly recommend that you stop using SMBv1 in your network.
However, disabling SMBv1 can cause problems with accessing shared files and folders on newer versions of Windows 10 (Windows Server 2016/2019) from legacy clients (Windows XP, Windows Server 2003), third-party OS (Mac OSX 10.8 Mountain Lion, Snow Leopard, Mavericks, old Linux distros), old NAS devices.
If there are no legacy devices left on your network that support only SMBv1, be sure to disable this SMB dialect in Windows.
If you have clients running Windows XP, Windows Server 2003, or other devices that only support SMBv1, they should be updated or isolated.
How to Enable and Disable SMBv1, SMBv2, and SMBv3 on Windows?
Let’s look at ways to enable and disable different SMB versions on Windows. We’ll cover SMB client and server management (they are different Windows components).
Windows 10, 8.1, and Windows Server 2019/2016/2012R2:
Disable SMBv1 client and server:
Disable-WindowsOptionalFeature -Online -FeatureName smb1protocol
Disable SMBv1 server only:
Set-SmbServerConfiguration -EnableSMB1Protocol $false
Enable SMBv1 client and server:
Enable-WindowsOptionalFeature -Online -FeatureName smb1protocol
Enable only SMBv1 server:
Set-SmbServerConfiguration -EnableSMB1Protocol $true
Disable SMBv2 and SMBv3 server:
Set-SmbServerConfiguration -EnableSMB2Protocol $false
Enable SMBv2 and SMBv3 server:
Set-SmbServerConfiguration -EnableSMB2Protocol $true
Windows 7, Vista, and Windows Server 2008 R2/2008:
Disable SMBv1 server:
Set-ItemProperty -Path "HKLM:SYSTEMCurrentControlSetServicesLanmanServerParameters" SMB1 -Type DWORD -Value 0 –Force
Enable SMBv1 server:
Set-ItemProperty -Path "HKLM:SYSTEMCurrentControlSetServicesLanmanServerParameters" SMB1 -Type DWORD -Value 1 –Force
Disable SMBv1 client:
sc.exe config lanmanworkstation depend= bowser/mrxsmb20/nsi
sc.exe config mrxsmb10 start= disabled
Enable SMBv1 client:
sc.exe config lanmanworkstation depend= bowser/mrxsmb10/mrxsmb20/nsi
sc.exe config mrxsmb10 start= auto
Disable SMBv2 server:
Set-ItemProperty -Path "HKLM:SYSTEMCurrentControlSetServicesLanmanServerParameters" SMB2 -Type DWORD -Value 0 -Force
Enable SMBv2 server:
Set-ItemProperty -Path "HKLM:SYSTEMCurrentControlSetServicesLanmanServerParameters" SMB2 -Type DWORD -Value 1 –Force
Disable SMBv2 client:
sc.exe config lanmanworkstation depend= bowser/mrxsmb10/nsi
sc.exe config mrxsmb20 start= disabled
Enable SMBv2 client:
sc.exe config lanmanworkstation depend= bowser/mrxsmb10/mrxsmb20/nsi
sc.exe config mrxsmb20 start= auto
You can disable SMBv1 server on domain joined computers by deploying the following registry parameter through the GPO:
- Key: HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesLanmanServerParameters
- Name: SMB1
- Type: REG_DWORD
- Value: 0
Set the registry parameter SMB2=0 in order to disable the SMBv2 server.
To disable the SMBv1 client, you need to propagate the following registry setting:
- Key: HKEY_LOCAL_MACHINESYSTEMCurrentControlSetservicesmrxsmb10
- Name: Start
- Type: REG_DWORD
- Value: 4
How do I configure SMB Security in Windows Server 2012?
Windows Server 2012 (and Windows 
Disable SMB 1.o
Microsoft recommends that unless you have clients running Windows XP or earlier, you should disable SMB 1.0. Do this in a preproduction lab environment before rolling out the change to your production systems. However, there are still certain scenarios where SMB 1.0 is still required, such as when the computer browser service is enabled in Vista (or later).
Windows Server 2012 has a new PowerShell command that makes it easy to get the configuration status of SMB protocols on the server, and optionally enable or disable SMB protocol support.
To get the current SMB protocol status on Windows Server 2012: Logon to the server as a local administrator, open a PowerShell prompt from the Start screen or icon on the desktop Taskbar, and run the following command:
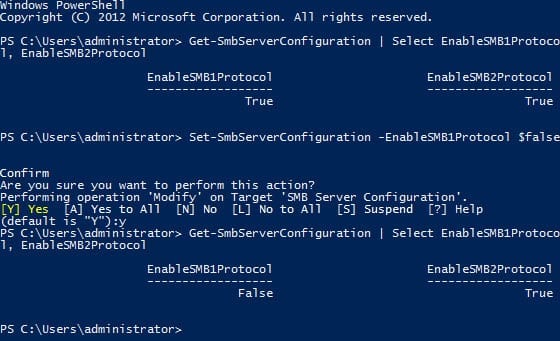
Get-SmbServerConfiguration | Select EnableSMB1Protocol, EnableSMB2Protocol
Note that there’s no separate command to enable or disable SMB 3.0, as it cannot operate independently of SMB 2.1.
Now, run the following command to disable SMB 1.0 and confirm the action when prompted:
Set-SmbServerConfiguration -EnableSMB1Protocol $false
After that, run the first command again. You should see that SMB 1 has been successfully disabled.
Enable SMB 3.0 Encryption
You can enable encryption per file share or for the entire server. SMB 3.0 uses the AES-CCM algorithm for both encryption and signing. Using the same PowerShell cmdlet as above, run the following command to enable SMB 3.0 Encryption for all file shares:
Set-SmbServerConfiguration –EncryptData $true
To enable encryption for a specific file share, run the following PowerShell command, replacing <sharename> with name of the file share for which you want to enable encryption:
Set-SmbShare –Name <sharename> -EncryptData $true
When enabled, SMB 3.0 encryption will encrypt file data between devices that support SMB 3.0. Clients that don’t support SMB 3.0 will not be able to connect to the file server or share where encryption is turned on. While not recommended, this behavior can be changed by running the Set-SmbServerConfiguration –RejectUnencryptedAccess $false PowerShell command.
How to enable and disable SMBv1, SMBv2, and SMBv3 in Windows Vista, Windows Server 2008, Windows 7, Windows Server 2008 R2, Windows 8, and Windows Server 2012
This article describes how to enable and disable Server Message Block (SMB) version 1 (SMBv1), SMB version 2 (SMBv2), and SMB version 3 (SMBv3) on the SMB client and server components.
Summary
In Windows 7 and Windows Server 2008 R2, disabling SMBv2 deactivates the following functionality:
- Request compounding — allows for sending multiple SMB 2 requests as a single network request
- Larger reads and writes — better use of faster networks
- Caching of folder and file properties — clients keep local copies of folders and files
- Durable handles — allow for connection to transparently reconnect to the server if there is a temporary disconnection
- Improved message signing — HMAC SHA-256 replaces MD5 as hashing algorithm
- Improved scalability for file sharing — number of users, shares, and open files per server greatly increased
- Support for symbolic links
- Client oplock leasing model — limits the data transferred between the client and server, improving performance on high-latency networks and increasing SMB server scalability
- Large MTU support — for full use of 10-gigabye (GB) Ethernet
- Improved energy efficiency — clients that have open files to a server can sleep
In Windows 8 and Windows Server 2012, disabling SMBv3 deactivates the following functionality (and also the SMBv2 functionality that is described in the previous list):
- Transparent Failover — clients reconnect without interruption to cluster nodes during maintenance or failover
- Scale Out concurrent access to shared data on all file cluster nodes
- Multichannel — aggregation of network bandwidth and fault tolerance if multiple paths are available between client and server
- SMB Direct adds RDMA networking support for very high performance, with low latency and low CPU utilization
- Encryption Provides end-to-end encryption and protects from eavesdropping on untrustworthy networks
- Directory Leasing — Improves application response times in branch offices through caching
- Performance Optimizations — optimizations for small random read/write I/O
More information
The SMBv2 protocol was introduced in Windows Vista and Windows Server 2008.
The SMBv3 protocol was introduced in Windows 8 and Windows Server 2012.
For more information about the capabilities of SMBv2 and SMBv3 capabilities, go to the following Microsoft TechNet websites:
Server Message Block overview
What’s New in SMB
-
How to enable or disable SMB protocols on the SMB server
Windows 8 and Windows Server 2012
Windows 8 and Windows Server 2012 introduce the new Set-SMBServerConfiguration Windows PowerShell cmdlet. The cmdlet enables you to enable or disable the SMBv1, SMBv2, and SMBv3 protocols on the server component.
Notes When you enable or disable SMBv2 in Windows 8 or in Windows Server 2012, SMBv3 is also enabled or disabled. This behavior occurs because these protocols share the same stack.
You do not have to restart the computer after you run the Set-SMBServerConfiguration cmdlet.
- To obtain the current state of the SMB server protocol configuration, run the following cmdlet:
Get-SmbServerConfiguration | Select EnableSMB1Protocol, EnableSMB2Protocol
- To disable SMBv1 on the SMB server, run the following cmdlet:
Set-SmbServerConfiguration -EnableSMB1Protocol $false
- To disable SMBv2 and SMBv3 on the SMB server, run the following cmdlet:
Set-SmbServerConfiguration -EnableSMB2Protocol $false
- To enable SMBv1 on the SMB server, run the following cmdlet:
Set-SmbServerConfiguration -EnableSMB1Protocol $true
- To enable SMBv2 and SMBv3 on the SMB server, run the following cmdlet:
Set-SmbServerConfiguration -EnableSMB2Protocol $true
Windows 7, Windows Server 2008 R2, Windows Vista, and Windows Server 2008
To enable or disable SMB protocols on an SMB Server that is runningWindows 7, Windows Server 2008 R2, Windows Vista, or Windows Server 2008, use Windows PowerShell or Registry Editor.
Windows PowerShell 2.0 or a later version of PowerShell
- To disable SMBv1 on the SMB server, run the following cmdlet:
Set-ItemProperty -Path «HKLM:SYSTEMCurrentControlSetServicesLanmanServerParameters» SMB1 -Type DWORD -Value 0 -Force
- To disable SMBv2 and SMBv3 on the SMB server, run the following cmdlet:
Set-ItemProperty -Path «HKLM:SYSTEMCurrentControlSetServicesLanmanServerParameters» SMB2 -Type DWORD -Value 0 -Force
- To enable SMBv1 on the SMB server, run the following cmdlet:
Set-ItemProperty -Path «HKLM:SYSTEMCurrentControlSetServicesLanmanServerParameters» SMB1 -Type DWORD -Value 1 -Force
- To enable SMBv2 and SMBv3 on the SMB server, run the following cmdlet:
Set-ItemProperty -Path «HKLM:SYSTEMCurrentControlSetServicesLanmanServerParameters» SMB2 -Type DWORD -Value 1 -Force
Note You must restart the computer after you make these changes.
Registry Editor
Important This article contains information about how to modify the registry. Make sure that you back up the registry before you modify it. Make sure that you know how to restore the registry if a problem occurs. For more information about how to back up, restore, and modify the registry, click the following article number to view the article in the Microsoft Knowledge Base:
322756 How to back up and restore the registry in Windows
To enable or disable SMBv1 on the SMB server, configure the following registry key:
Registry subkey:
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesLanmanServerParametersRegistry entry: SMB1
REG_DWORD: 0 = Disabled
REG_DWORD: 1 = Enabled
Default: 1 = Enabled To enable or disable SMBv2 on the SMB server, configure the following registry key:Registry subkey:HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesLanmanServerParameters
Registry entry: SMB2
REG_DWORD: 0 = Disabled
REG_DWORD: 1 = Enabled
Default: 1 = EnabledHow to enable or disable SMB protocols on the SMB client
Windows Vista, Windows Server 2008, Windows 7, Windows Server 2008 R2, Windows 8, and Windows Server 2012
Note When you enable or disable SMBv2 in Windows 8 or in Windows Server 2012, SMBv3 is also enabled or disabled. This behavior occurs because these protocols share the same stack.
- To disable SMBv1 on the SMB client, run the following commands:
sc.exe config lanmanworkstation depend= bowser/mrxsmb20/nsisc.exe config mrxsmb10 start= disabled
- To enable SMBv1 on the SMB client, run the following commands:
sc.exe config lanmanworkstation depend= bowser/mrxsmb10/mrxsmb20/nsi sc.exe config mrxsmb10 start= auto
- To disable SMBv2 and SMBv3 on the SMB client, run the following commands:
sc.exe config lanmanworkstation depend= bowser/mrxsmb10/nsi sc.exe config mrxsmb20 start= disabled
- To enable SMBv2 and SMBv3 on the SMB client, run the following commands:
sc.exe config lanmanworkstation depend= bowser/mrxsmb10/mrxsmb20/nsi sc.exe config mrxsmb20 start= auto
Notes
- You must run these commands at an elevated command prompt.
- You must restart the computer after you make these changes.
- To obtain the current state of the SMB server protocol configuration, run the following cmdlet:
Published: 21/10/16 — 08:51:30 (Amanda Higgins)
Related Articles
Running DE8 on Windows Servers, do and dont’s (SMB1,SMB2,SMB3 and OpLocks)
With the release of DataEase 8.0, 8.1, 8.2 and Windows 7, 8 , 8.1 and Windows Server 2012 R2, we are frequently asked about how new versions of DataEase work when connecting to old versions of Windows servers and old versions of DataEase connecting to new…
Other sources of Network problems
This is a little old, but it is still useful. If you have switched off SMB2 and SMB3 on your networ as well as disabled OpLocks for SMB1 and still have problems with corruption, have a look below and see if some of these things might apply to your network…
Environment Variables in Windows XP, WIndows 7 and 8 (Complete List)
Environment variables is very useful to make general code. You can include them in paths directly to access files native to an active user/workstation/profile/session etc….
Home →
Windows 10 →
Operating System →
How to enable and disable SMBv1, SMBv2, and SMBv3 in Windows Vista, Windows Server 2008, Windows 7, Windows Server 2008 R2, Windows 8, Windows 10, and Windows Server 2012
The SMBv2 protocol was introduced in Windows Vista and Windows Server 2008.
The SMBv3 protocol was introduced in Windows 8 and Windows Server 2012.
For more information about the capabilities of SMBv2 and SMBv3 capabilities, go to the following Microsoft TechNet websites:
Windows 8 and Windows Server 2012
Windows 8 and Windows Server 2012 introduce the new Set-SMBServerConfiguration Windows PowerShell cmdlet. The cmdlet enables you to enable or disable the SMBv1, SMBv2, and SMBv3 protocols on the server component.
Notes When you enable or disable SMBv2 in Windows 8 or in Windows Server 2012, SMBv3 is also enabled or disabled. This behavior occurs because these protocols share the same stack.
You do not have to restart the computer after you run the Set-SMBServerConfiguration cmdlet.
- To obtain the current state of the SMB server protocol configuration, run the following cmdlet:
Get-SmbServerConfiguration | Select EnableSMB1Protocol, EnableSMB2Protocol
- To disable SMBv1 on the SMB server, run the following cmdlet:
Set-SmbServerConfiguration -EnableSMB1Protocol $false
- To disable SMBv2 and SMBv3 on the SMB server, run the following cmdlet:
Set-SmbServerConfiguration -EnableSMB2Protocol $false
- To enable SMBv1 on the SMB server, run the following cmdlet:
Set-SmbServerConfiguration -EnableSMB1Protocol $true
- To enable SMBv2 and SMBv3 on the SMB server, run the following cmdlet:
Set-SmbServerConfiguration -EnableSMB2Protocol $true
Windows 7, Windows Server 2008 R2, Windows Vista, and Windows Server 2008
To enable or disable SMB protocols on an SMB Server that is runningWindows 7, Windows Server 2008 R2, Windows Vista, or Windows Server 2008, use Windows PowerShell or Registry Editor.
Windows PowerShell 2.0 or a later version of PowerShell
- To disable SMBv1 on the SMB server, run the following cmdlet:
Set-ItemProperty -Path «HKLM:SYSTEMCurrentControlSetServicesLanmanServerParameters» SMB1 -Type DWORD -Value 0 -Force
- To disable SMBv2 and SMBv3 on the SMB server, run the following cmdlet:
Set-ItemProperty -Path «HKLM:SYSTEMCurrentControlSetServicesLanmanServerParameters» SMB2 -Type DWORD -Value 0 -Force
- To enable SMBv1 on the SMB server, run the following cmdlet:
Set-ItemProperty -Path «HKLM:SYSTEMCurrentControlSetServicesLanmanServerParameters» SMB1 -Type DWORD -Value 1 -Force
- To enable SMBv2 and SMBv3 on the SMB server, run the following cmdlet:
Set-ItemProperty -Path «HKLM:SYSTEMCurrentControlSetServicesLanmanServerParameters» SMB2 -Type DWORD -Value 1 -Force
Note You must restart the computer after you make these changes.
Registry Editor
Important This article contains information about how to modify the registry. Make sure that you back up the registry before you modify it. Make sure that you know how to restore the registry if a problem occurs. For more information about how to back up, restore, and modify the registry, click the following article number to view the article in the Microsoft Knowledge Base:
322756 How to back up and restore the registry in Windows
To enable or disable SMBv1 on the SMB server, configure the following registry key:
Registry subkey: HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesLanmanServerParametersRegistry entry: SMB1
REG_DWORD: 0 = Disabled
REG_DWORD: 1 = Enabled
Default: 1 = Enabled
To enable or disable SMBv2 on the SMB server, configure the following registry key:
Registry subkey:HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesLanmanServerParametersRegistry entry: SMB2
REG_DWORD: 0 = Disabled
REG_DWORD: 1 = Enabled
Default: 1 = Enabled