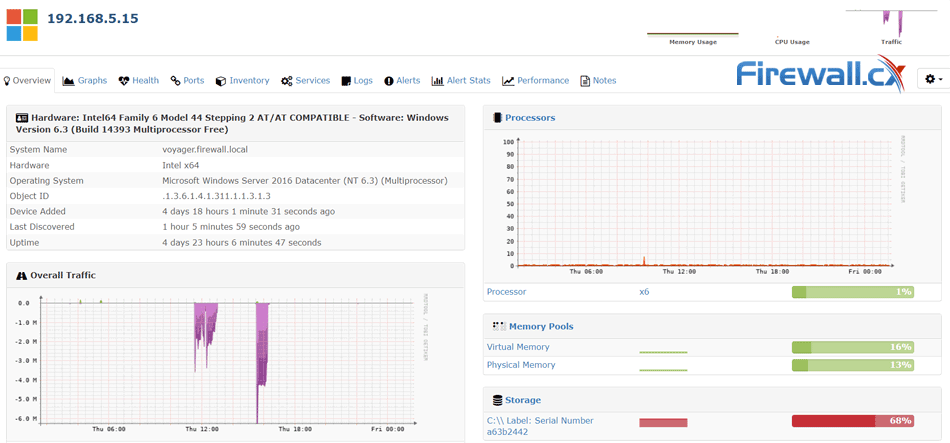
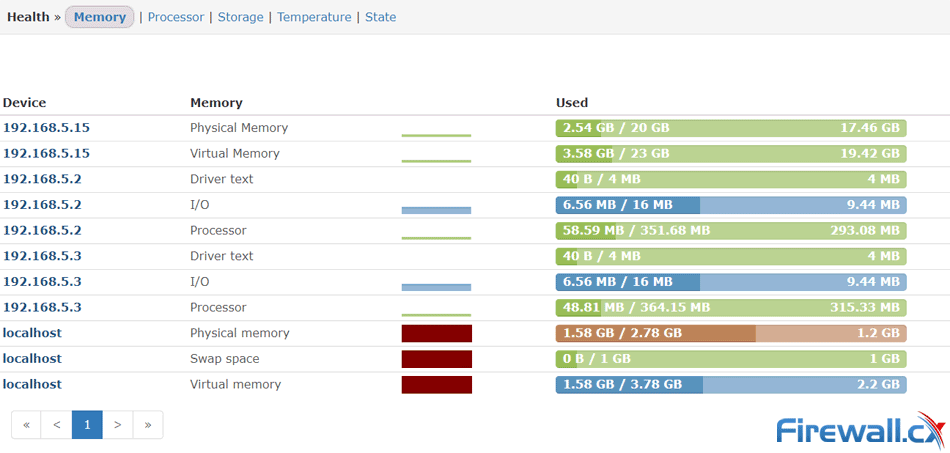
Simple Network Management Protocol (SNMP) is a UDP protocol that uses port 161 to monitor and collect detailed information on any network device supporting the SNMP protocol. All Windows servers support SNMP and we’ll show you how to easily install and configure SNMP on your Windows 2016 or 2012 server, including Read Only (RO) or Read Write (RW) SNMP community string.
In our example we will enable the SNMP agent and configure a SNMP community string to allow our Network Monitoring System (NMS) monitor our server resources.
Execution Time: 10 minutes
Step 1 – Install SNMP on Windows Server 2016
Open the Control Panel on your Windows Server and Double-click on the Program and Features icon:
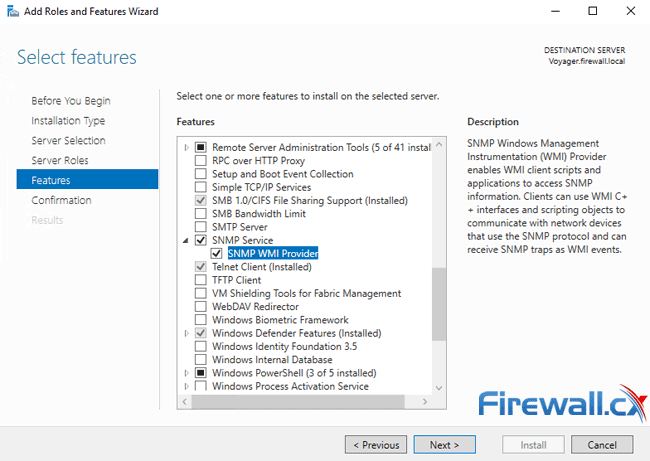
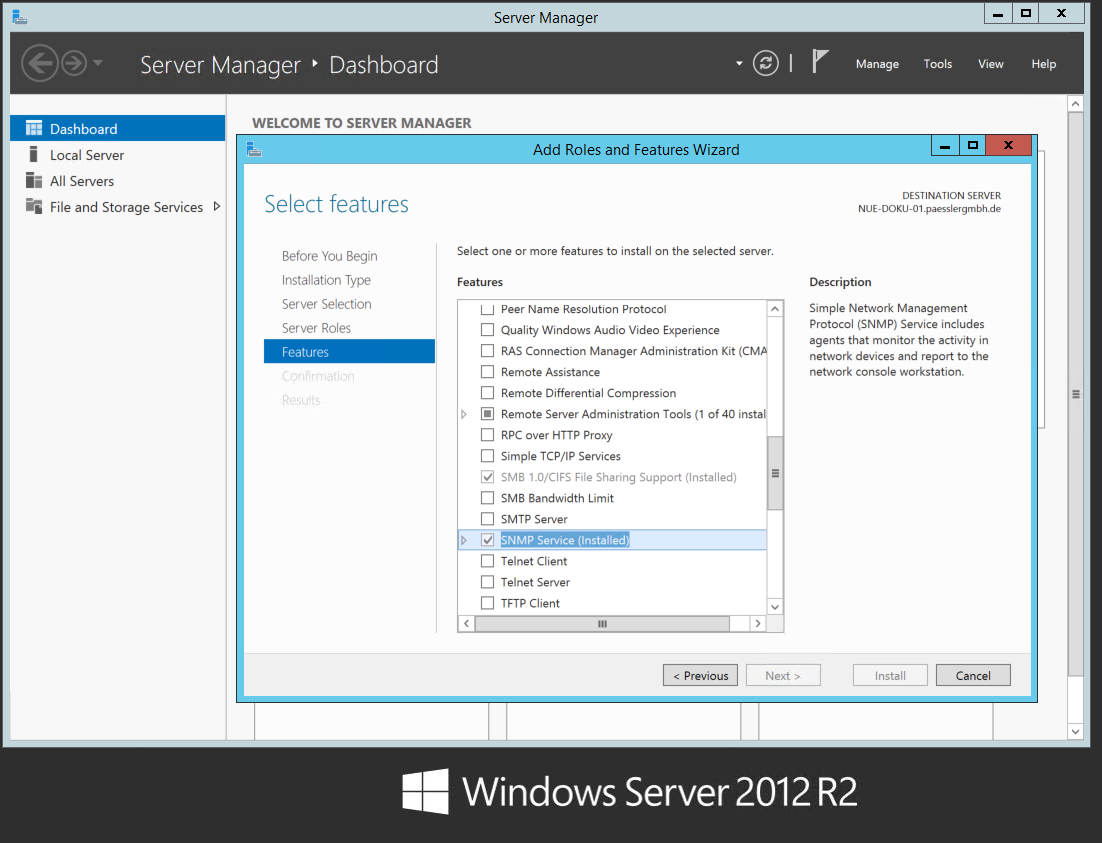
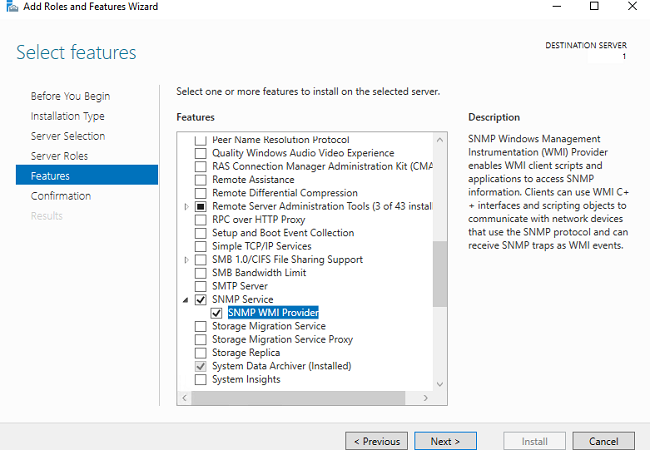
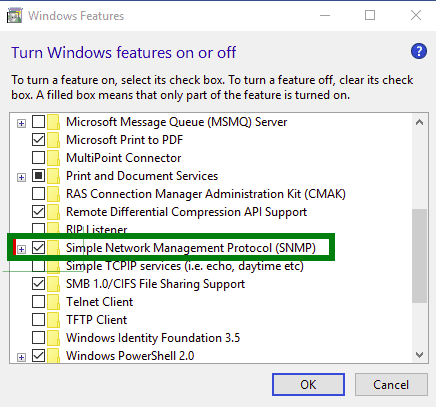
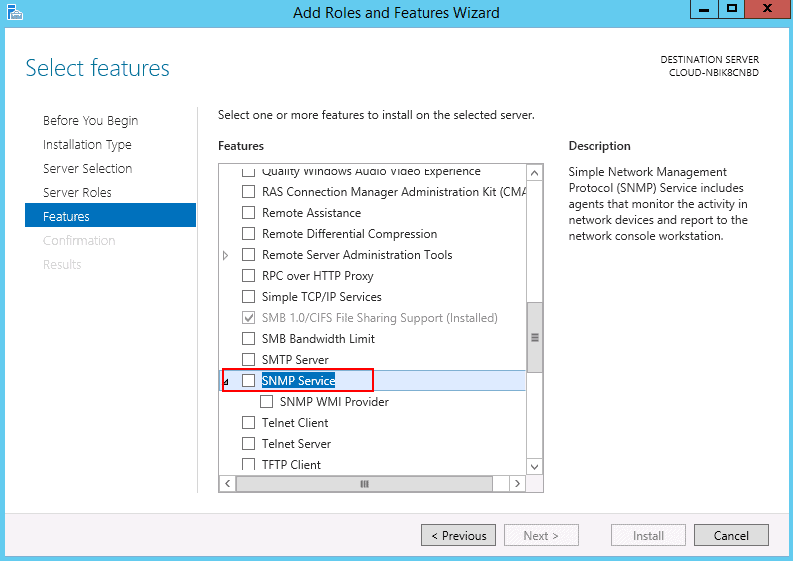
This will open the Add Roles and Features Wizard. Keep clicking on the Next button until you reach the Features section. From there, select the SNMP Service option:
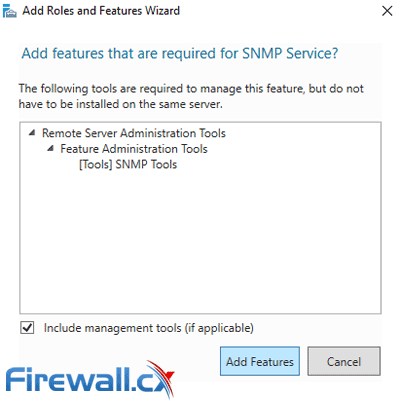
When prompted, click on the Add Features button to include the installation of the Administration SNMP Tools:
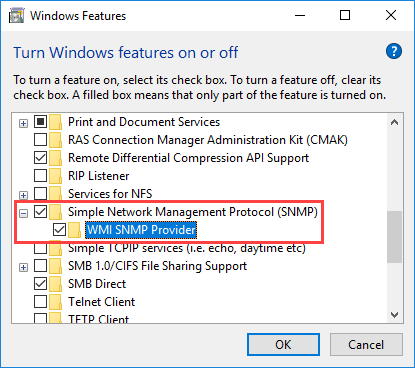
Optionally you can include the SNMP WMI Provider option located under the SNMP Service. When ready click on the Next button.
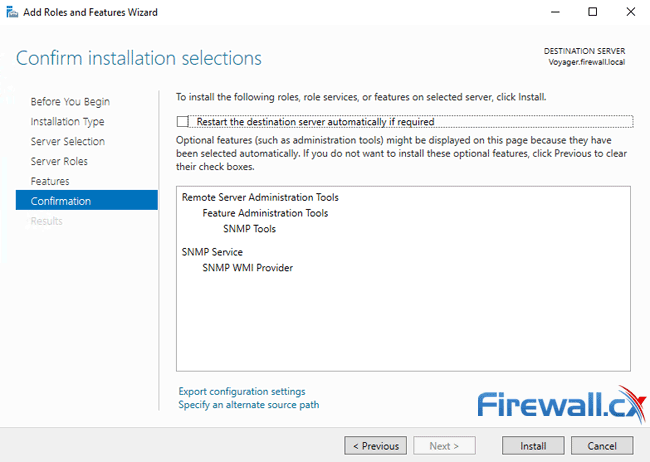
This is the final screen – simply click on the Install button. Ensure the “Restart the destination server automatically if required” option is not selected:
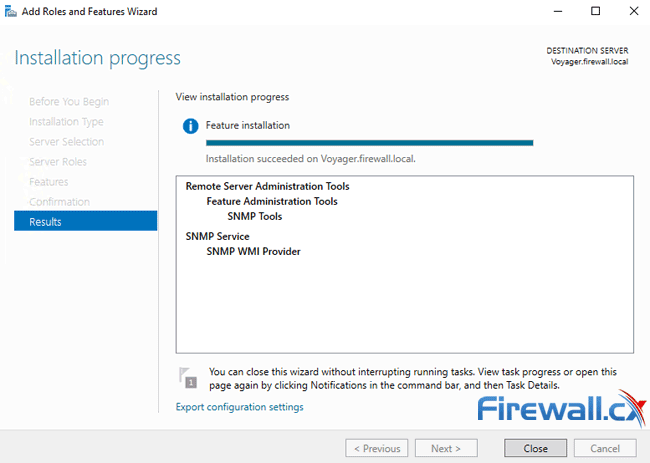
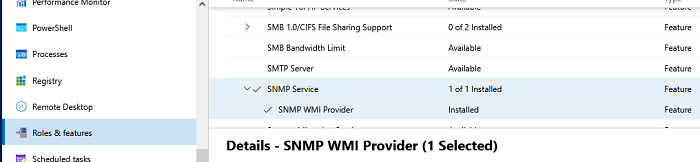
The SNMP Service will now be installed on your Windows 2016 Server. This process will require around 3 minutes to complete. When done, click on the Close button to exit the installation wizard:
Step 2 – Configure SNMP Service and Read-Only or Read-Write Community String
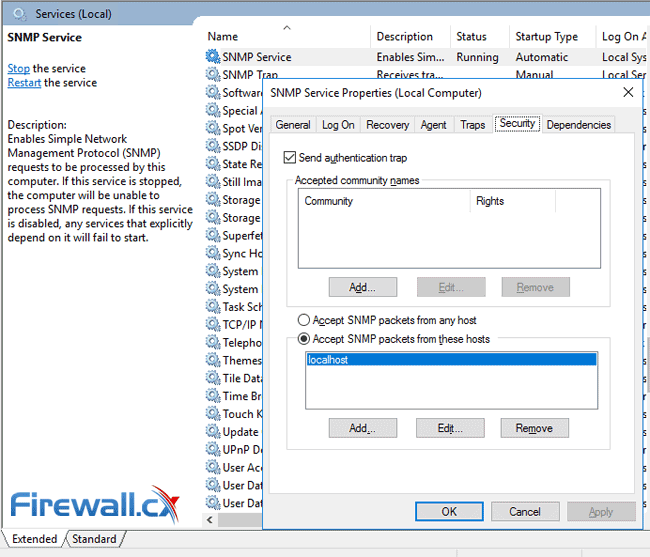
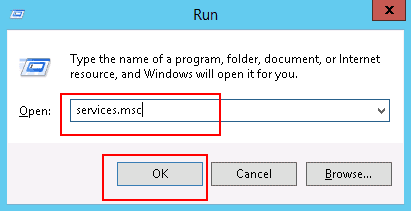
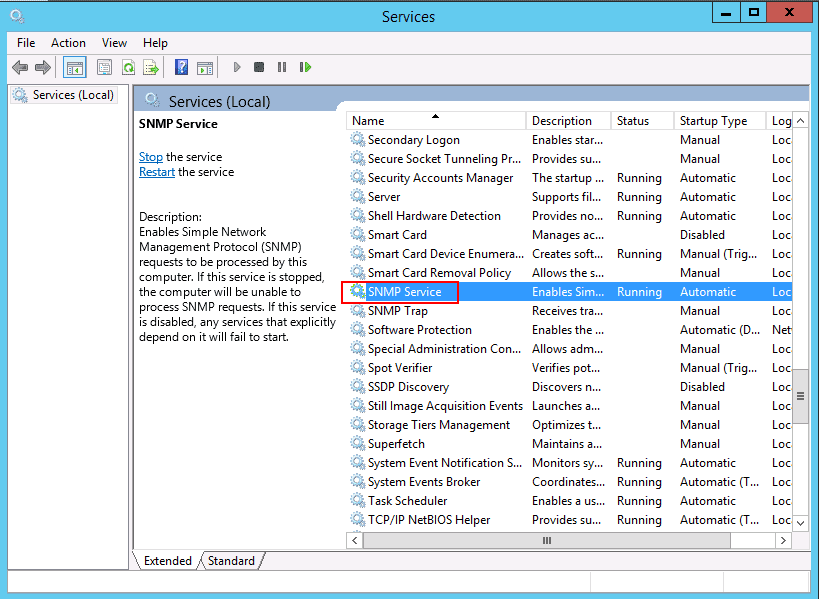
Configuring the Windows 2016 Server SNMP Service is a simple task. As an administrator, run services.msc or open the Services console from the Administrative Tools. Double-click the SNMP Service and go to the Security tab:
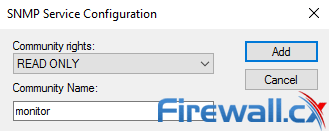
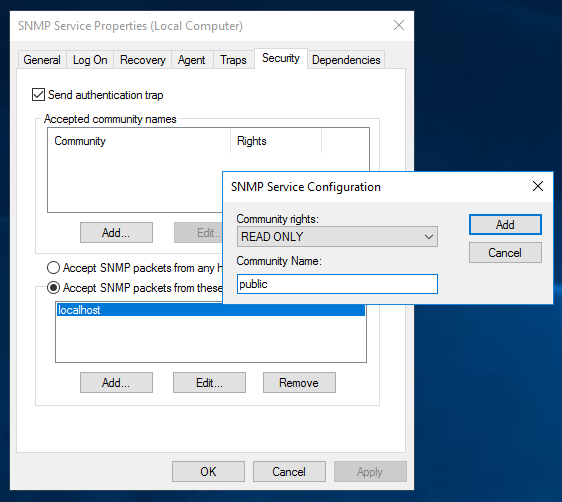
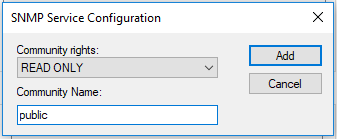
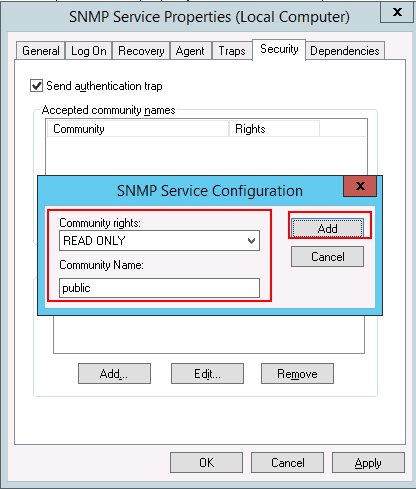
To add a Read-Only community string, click on the Add button under the Accepted community names. Enter the desirable Community Name and set the Community rights to READ ONLY. When done, click on the Add button:
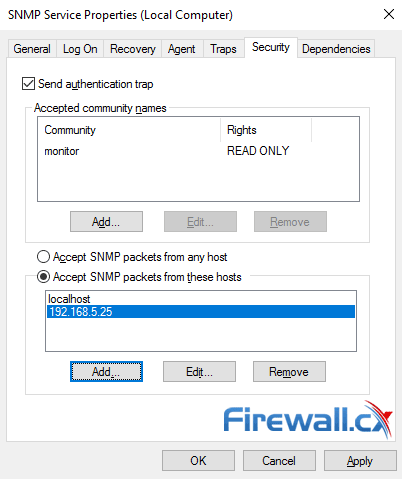
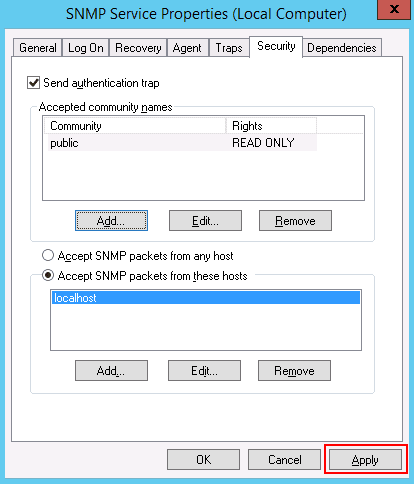
Next, in the lower section of the window, click on the Add button and insert the IP address which will be allowed to poll this server via SNMP. This would be the IP address of your Network Monitoring Service. In our environment our NMS is 192.168.5.25. When done, click on Apply then the OK button:
To confirm SNMP is working correctly, we configured our NMS to query and retrieve information from our server every 5 minutes. After a while we were able to see useful information populating our NMS:
Depending on your Network Monitoring System you’ll be able to obtain detailed information on your server’s status and state of its resources:
Summary
This article briefly explained the purpose of SNMP and how it can be used to monitor network devices and collect useful information such as CPU, RAM and Disk usage, processes running, host uptime and much more. We also showed how to install and configure the SNMP Service for Windows Server 2016. For more technical Windows articles, please visit our Windows Server 2016 section.
Back to Windows Server 2016 Section
Simple Network Management Protocol (SNMP) is an age-old network monitoring protocol still in wide use today. In Windows Server 2016, an SNMP service is still available. You can set it up to provide a way to monitor various resources remotely on a Windows Server 2016 machine.
Contents
- Install the SNMP service
- Configure the permitted manager
- The Install-SNMP function
- Author
- Recent Posts
Adam Bertram is a 20-year IT veteran, Microsoft MVP, blogger, and trainer.
There are a couple of ways to get SNMP set up on Windows Server 2016. For this article, I’m going to focus on how to do this in PowerShell. This will allow you to replicate my work easily and set up the SNMP service on many servers at once should you choose to do so.
For the demo in this article to work, make sure you have PowerShell Remoting (PSRemoting) enabled and available on at least one Windows Server 2016 machine. I’ll be working from a computer in the same Active Directory domain. Once you’ve got this enabled and working, we can now begin to set up SNMP.
Install the SNMP service
To make things simple at first, let’s create an interactive PSRemoting session to our remote Windows Server 2016 machine.
PS> Enter-PSSession -ComputerName 'WINSRV2016' [WINSRV2016]: PS C:>
Once I’ve established a PSRemoting session, I can begin executing commands on the remote server. The first command I need to run is Install-WindowsFeature. I’ll use this command to install the SNMP-Service and RSAT-SNMP features. These two features will install the SNMP service itself and make the options available should we choose to configure the SNMP service via the Services GUI later.
[WINSRV2016]: PS C:> Install-WindowsFeature -Name 'SNMP-Service','RSAT-SNMP'
Success Restart Needed Exit Code Feature Result
------- -------------- --------- --------------
True No Success {SNMP Service}
Configure the permitted manager
After installing the SNMP service feature, we can now configure both the permitted managers and add any community strings. We can add both permitted managers and community strings via the registry. First, let’s add a few permitted managers. The permitted managers are stored in the PermittedManagers key inside the SNMP Windows service key located at HKEY_LOCAL_MACHINE.
I’d like to allow servers called foo.techsnips.local and bar.techsnips.local to query this SNMP service. I can add them both to the PermittedManagers key by using the New-ItemProperty cmdlet. You can see below that incrementing numbers starting at 1 define the permitted managers. By default, 1 is already set for localhost, so I’m starting at 2 and creating each manager entry as a value.
$managers = 'foo.techsnips.local','bar.techsnips.local'
$i = 2
foreach ($manager in $managers) {
New-ItemProperty -Path "HKLM:SYSTEMCurrentControlSetservicesSNMPParametersPermittedManagers" Name $i -Value $manager
$i++
}
After this runs, the PermittedManagers key will now look something like this:
Added permitted managers
Once you’ve added the permitted managers, it’s time to add one or more community strings. We’ll do this again via the registry, but this time the appropriate key is called ValidCommunities. Let’s add a couple here to demonstrate. We’re getting a little fancy here, but that’s what PowerShell is for! In the example below, I’m defining all the community strings and their right levels in a plain-English way. I’ve defined a read-only community string as a 4 and a read/write community string as an 8, but I don’t want to remember this!
$strings = @(
@{
Name = 'ro'
Rights = 'Read Only'
}
@{
Name = 'rw'
Rights = 'Read Write'
}
)
foreach ($string in $strings) {
switch ($string.Rights) {
'Read Only' {
$val = 4
}
'Read Write' {
$val = 8
}
default {
throw "Unrecognized input: [$]"
}
}
New-ItemProperty -Path "HKLM:SYSTEMCurrentControlSetservicesSNMPParametersValidCommunities" Name $string.Name -Value $val
$i++
}
After running this code, you can then go to the Windows Services console and view the SNMP Service Properties –> Security tab to see that the SNMP service recognizes all of the strings.
Viewing SNMP configuration
The Install-SNMP function
Now that you know the basics of setting up SNMP, we can take the code we came up with and easily adapt it to multiple servers as well. To do this, instead of creating an interactive remoting session, we will instead use Invoke-Command to send a prebuilt block of code known as a scriptblock to one or many different computers at once.
We’ll wrap this all up into an easy-to-use function called Install-SNMP we can execute on one or lots of computers.
function Install-SNMP {
[OutputType('void')]
[CmdletBinding()]
param
(
[Parameter(Mandatory)]
[ValidateNotNullOrEmpty()]
[string[]]$ComputerName,
[Parameter()]
[ValidateNotNullOrEmpty()]
[string[]]$PermittedManagers,
[Parameter()]
[ValidateNotNullOrEmpty()]
[hashtable[]]$CommunityStrings,
[Parameter()]
[ValidateNotNullOrEmpty()]
[pscredential]$Credential
)
$ErrorActionPreference = 'Stop'
try {
$scriptBlock = {
$VerbosePreference = $using:VerbosePreference
## Install the service and remote GUI configuraiton ability
$null = Install-WindowsFeature -Name 'SNMP-Service','RSAT-SNMP'
if ($using:PermittedManagers) {
## Set any managers
$i = 2
foreach ($manager in $using:PermittedManagers) {
Write-Verbose -Message "Setting permitted manager [$($manager)]..."
$null = New-ItemProperty -Path "HKLM:SYSTEMCurrentControlSetservicesSNMPParametersPermittedManagers" -Name $i -Value $manager
$i++
}
$strings = @(
@{
Name = 'ro'
Rights = 'Read Only'
}
@{
Name = 'rw'
Rights = 'Read Write'
}
)
}
if ($using:CommunityStrings) {
## Set any community strings
foreach ($string in $using:CommunityStrings) {
Write-Verbose -Message "Setting community string [$($string.Name)]..."
switch ($string.Rights) {
'Read Only' {
$val = 4
}
'Read Write' {
$val = 8
}
default {
throw "Unrecognized input: [$]"
}
}
$null = New-ItemProperty -Path "HKLM:SYSTEMCurrentControlSetservicesSNMPParametersValidCommunities" -Name $string.Name -Value $val
$i++
}
}
}
$icmParams = @{
ComputerName = $ComputerName
ScriptBlock = $scriptBlock
Verbose = $VerbosePreference
}
if ($PSBoundParameters.ContainsKey('Credential')) {
$icmParams.Credential = $Credential
}
Invoke-Command @icmParams
} catch {
Write-Error -Message $_.Exception.Message
}
}
We can now use this function like this:
Subscribe to 4sysops newsletter!
PS> Install-SNMP -ComputerName WINSRV2016 -PermittedManagers 'foo.techsnips.local' -CommunityStrings @{'Name'='ro';'Rights'='Read Only'} Verbose
VERBOSE: Exporting cmdlet 'Get-WindowsFeature'.
VERBOSE: Exporting cmdlet 'Install-WindowsFeature'.
VERBOSE: Exporting cmdlet 'Uninstall-WindowsFeature'.
VERBOSE: Exporting alias 'Add-WindowsFeature'.
VERBOSE: Exporting alias 'Remove-WindowsFeature'.
VERBOSE: Exporting function 'Enable-ServerManagerStandardUserRemoting'.
VERBOSE: Exporting function 'Disable-ServerManagerStandardUserRemoting'.
VERBOSE: Installation started...
VERBOSE: Installation succeeded.
VERBOSE: Setting permitted manager [foo.techsnips.local]...
VERBOSE: Setting community string [ro]...
When we use a monitoring tool in an enterprise environment, monitoring data of Windows and Windows Server machines is usually done through WMI (Windows Management Instrumentation). However, there may be cases that you may need to use the Simple Network Management Protocol (SNMP).
SNMP is already installed in versions prior to Windows 8 and Windows Server 2012. However, in Windows 8, Windows 10, Windows Server 2012, and Windows Server 2016 will need to install it. Note: SNMP Service is deprecated since the Windows Server 2012 R2 version.
Of course, if you are going to install SNMP on multiple endpoints (computers, servers, VMs, etc.), then it would be preferable to do so remotely using PowerShell and/or Group Policy.
Check if SNMP is installed
Before we get started, it’s a good idea to first check if the SNMP service is already installed and running on Windows 10 or Windows Server 2016. This can be done very easily through PowerShell by typing the following command.
If the corresponding service does not appear, then it is not installed. Similarly, on Windows Server, you can type the following command.
Get-WindowsFeature SNMP-Service
Alternatively, you can open the Services or Task Manager window and search for the SNMP Service. If it does not exist then it is not installed.
Install SNMP in Windows 10 and Windows Server 2016
In Windows 10, installing SNMP Service is done through the Add Windows Features window. As shown in the figure below, check Simple Network Management Protocol (SNMP) and press OK.
In Windows Server 2016, SNMP is installed through Server Manager. Start the Add Roles and Features wizard, click on Next until you reach the Features section where you will need to check the SNMP Service option. Continue on completing the wizard by pressing Next and Finish.
Installing SNMP is easier with a PowerShell one-liner on Windows Server 2016.
Install-WindowsFeature SNMP-Service -IncludeManagementTools
Configure SNMP on Windows 10 and Windows Server 2016
In both Windows 10 and Windows Server 2016, the SNMP setting is configured through the service properties window. So, open the services.msc window, find the SNMP Service, and open Properties.
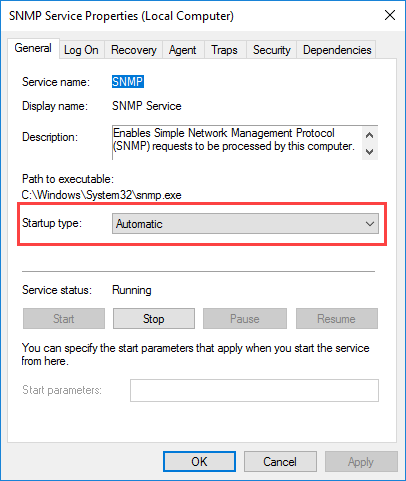
Here, on the General tab, be sure to select Automatic in the Startup Type section so that it is always available even after a restart of the computer or server.
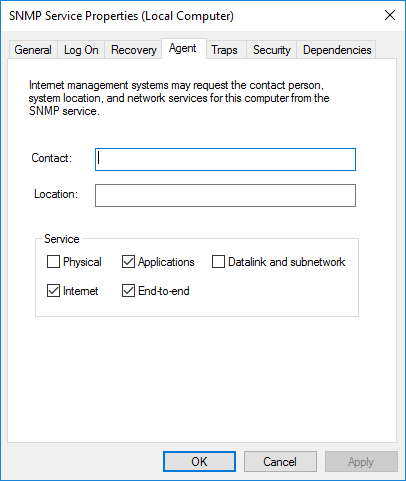
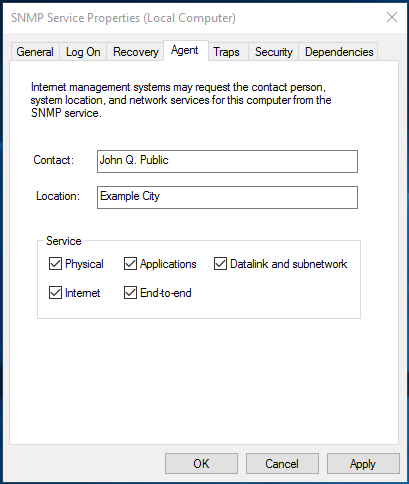
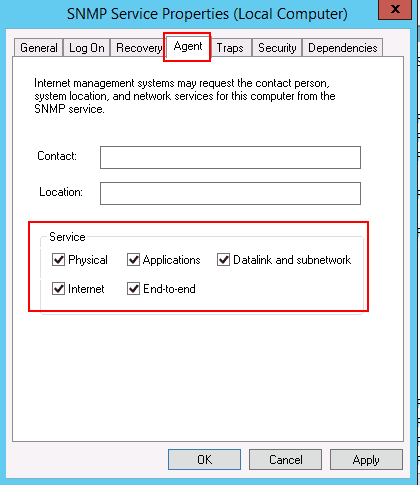
On the Agent tab, be sure to select all the services required by the monitoring tool to collect the data.
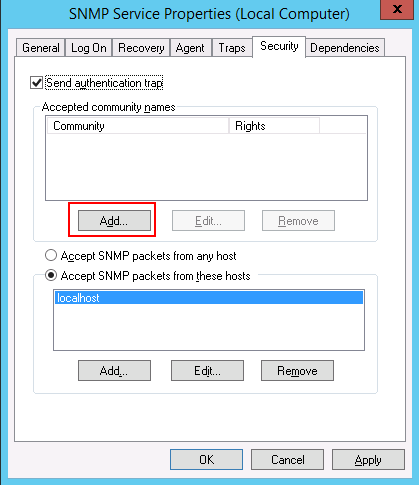
On the Security tab, click the Add button to add the community string, read-only, and the hosts from where SNMP packages will be accepted.
That’s it. Now, the installation and configuration of the SNMP service in Windows 10 and Windows Server 2016 are complete.
This article applies to PRTG Network Monitor 19 or later
Installing and Configuring the SNMP Service on Windows
The best moment to install the SNMP service is immediately after or as part of the installation of the operating system because there are some applications that check for the availability of the SNMP service to install their own SNMP files.
There are some applications (for example, IIS and MS SQL Server) that will not install SNMP support if the service is not installed (and in some cases, running)!
By default, the SNMP service is already installed on Windows systems previous to Windows 8 and Windows Server 2012. To install and configure SNMP on other Windows systems, follow the steps below. This process is very similar on all Windows systems.
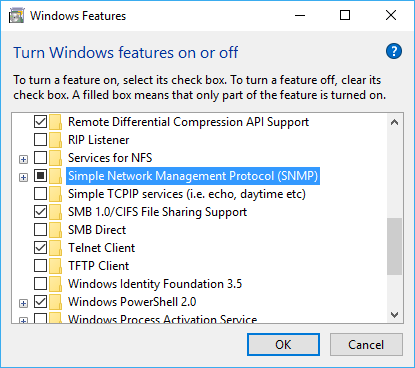
Enabling SNMP on Windows 8 and 10 as well as Windows Server 12, 16, and 19
- Open the Control Panel on your Windows machine.
- Click Turn Windows features on or off in section Programs.
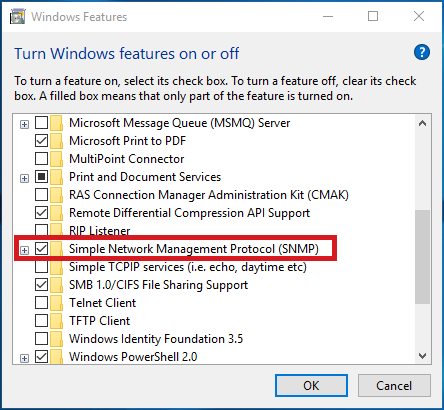
Click to enlarge. - Check Simple Network Management Protocol (SNMP) and install it.
- On Windows Server 2008, you find the SNMP service under Features | Add Features in the Server Manager that opened after completing step 2.
- On Windows Server 2012, 2016, and 2019, click Next after completing step 2 until you reach Features where you can select and install SNMP Service.
Click to enlarge.
- After the SNMP installation is completed, open services.msc as administrator.
- Double-click SNMP Service to open its Properties.
- On the General tab, select Automatic for Startup Type.
- On the Security tab, you can leave the default community name «public» or choose your own (the latter is more secure). To choose your own, click on Add… for accepted community names, leave Community Rights as Read-Only and pick a secure Community Name. Click on OK. Remove the «public» entry.
Click to enlarge. - On the Security tab in the lower half, you can choose which IP addresses are allowed to access the SNMP service. You must at least choose the IP address of the machine running PRTG!
- On the Agent tab, fill out all edit fields and enable all check boxes to make all SNMP values available.
Click to enlarge. - Save the properties and restart the server.
Note: On Windows Server 2012, you might encounter missing Security, Agent, and Traps tabs in SNMP service properties. See this article on joshancel.wordpress.com for a workaround. You can also find information about this issue in Getting SNMP to Work on Windows Server 2012.
Enabling SNMP on Windows 10 version 1809 and later
With Windows 10 version 1809, the process of enabling SNMP changed. SNMP is an optional feature as of this Windows 10 version. You can enable it as follows.
- Open the Settings on your Windows machine.
- Click Apps.
- Choose Manage optional features under Apps & features.
- Click Add a feature.
- Select Simple Network Management Protocol (SNMP) from the list.
Click to enlarge. - Click Install to enable SNMP on your computer.
SNMP is now enabled on your Windows machine!
You can follow this guide as well as an instruction for enabling SNMP on Linux and macOS also on our website How to Enable SNMP on Your Operating System.
SNMP on Windows NT 4/2000/2003/XP
Note: These operating systems are not officially supported for running a PRTG core server or probe on it. If you run PRTG on one of these operating systems, you have to accept limited monitoring functionality. We do not provide support for any issues that might be caused (directly or indirectly) by using these Windows versions.
- Click on Start | Settings | Control Panel.
- Double-click on Add/Remove Programs.
- Click on Add/Remove Windows Components.
- Click on Management and Monitoring Tools and click on Details.
- Check Simple Network Management Protocol and click OK.
- Click on Next and let the install process complete.
- Double-click on Administrative Tools (inside Control Panel).
- Double-click on Computer Management.
- Expand the Services and Applications tree on the left frame.
- Click on Services on the left frame.
- Locate SNMP Service on right frame and double-click on it.
- On the General tab, select Automatic for Startup Type.
- On the Security tab, you can leave the default community name «public» or choose your own (which is more secure). To choose your own, click on Add… for accepted community names, leave Community Rights as Read-Only and pick a secure Community Name. Click on OK. Remove the «public» entry
- On the Security tab in the lower half, you can choose which IP addresses are allowed to access the SNMP service. You must at least choose the IP address of the machine running PRTG!
- On the Agent tab, fill out all edit fields and enable all check boxes to make all SNMP values available.
- For added flexibility we recommend that you install the freeware SNMP Helper that comes with your PRTG installation
SNMP (
Simple Network Management Protocol
) — это классический протокол для мониторинга и сбора информации о сетевых устройствах (сервера, сетевое оборудование, рабочие станции, принтеры и т.д.). Протокол SNMP довольно легкий, быстрый, для передачи данных использует UDP порты 161 и 162. В этой статье мы рассмотрим, как установить и настроить службу SNMP в Windows Server 2022/2019 и Windows 10/11.
Содержание:
- Установка службы SNMP в Windows Server 2022/2019
- Установка SNMP агента в Windows Server Core
- Установка службы SNMP в Windows 10/11
- Настройка службы SNMP в Windows Server и Windows 10/11
Установка службы SNMP в Windows Server 2022/2019
В Windows Server службу SNMP можно установить с помощью Server Manager.
Выберите Add roles and features -> Features. Выберите SNMP Service (если нужно отметьте также SNMP WMI Providers).
Служба SNMP WMI Provider позволяет опрашивать SNMP устройство через WMI.
Нажмите Next -> Install и дождитесь окончания установки.
Установка SNMP агента в Windows Server Core
В Windows Server Core можно установить SNMP с помощью веб-интерфеса Windows Admin Center и PowerShell.
Если вы используете Windows Admin Center, подключитесь к хосту Windows Server, выберите Roles and Features -> SNMP Service.
Т.к. в Windows Server Core отсутствует графический интерфейс, а для его управления используется командная строка, вы можете установить службу SNMP из командной строки PowerShell.
Для установки ролей в Windows Server из PowerShell используется командлет Install-WindowsFeature.
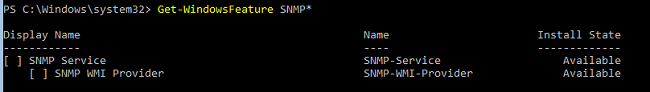
Проверьте, что служба SNMP не установлена:
Get-WindowsFeature SNMP*
Установите роль SNMP и WMI провайдер:
Install-WindowsFeature SNMP-Service,SNMP-WMI-Provider -IncludeManagementTools
Проверьте, что службы SNMP запущены:
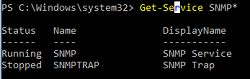
Get-Service SNMP*
В нашем примере SNMP служба запущена, а SNMPTRAP остановлена.
Установка службы SNMP в Windows 10/11
Вы можете использовать службу SNMP не только в Windows Server, но и в десктопных редакциях Windows 10 и 11.
В Windows 10/11 служба SNMP, вынесена в отдельный компонент Feature On Demand (как RSAT и OpenSSH).
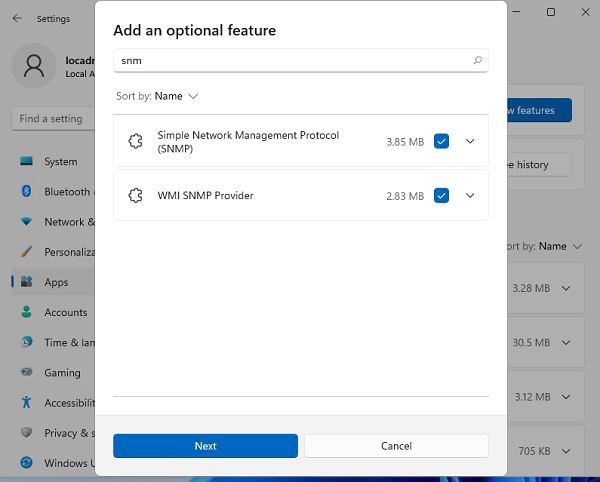
Вы можете установить SNMP через панель Settings. Перейдите в Apps -> Optional features -> Add an optional feature -> View features.
В списке доступных компонентов выберите Simple Network Management Protocol (SNMP) и WMI SNMP Provider. Для начала установки нажмите Next (понадобится интернет подключение к серверам Microsoft).
Для установки службы SNMP через PowerShell, используйте команду:
Add-WindowsCapability -Online -Name SNMP.Client~~~~0.0.1.0
Для установки службы SNMP без подключения к интернету, вам понадобится скачать ISO образ Windows 10/11 Features on Demand из личного кабинета на сайте лицензирования Volume Licensing Service Center (VLSC).
Для офлайн установки службы SNMP с такого ISO образа используется команда:
Add-WindowsCapability -Online -Name SNMP.Client~~~~0.0.1.0 -LimitAccess -Source \msk-fs01DistrWindows-FODWin11
Настройка службы SNMP в Windows Server и Windows 10/11
Вы можете настроить параметры службы SNMP в консоли services.msc. Найдите службу SNMP Services в списке и откройте ее свойства.
Обратите внимание, что у службы SNMP есть несколько дополнительных вкладок:
- Agent
- Traps
- Security
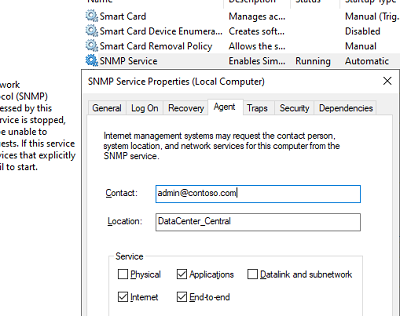
На вкладке Agent указывается базовая информация об устройстве (контакты администратора, местоположение). Здесь же можно указать тип информации, который может отправлять данное устройство при SNMP опросе.
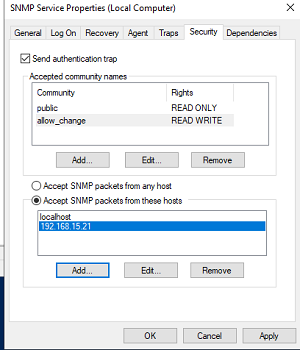
В старых версиях протокола SNMP (SNMP v.1 и SNMP v.2) для авторизации пользователя используется строка сообщества (community string). На вкладке Security можно создать несколько строк подключения.
Можно выбрать один из пяти уровней доступа для сообщества:
- READ ONLY — позволяет получать данные с устройства;
- READ WRITE — позволяет получать данные и изменять конфигурацию устройства;
- NOTIFY — позволяет получать SNMP ловушки;
- READ CREATE – позволяет читать данные, изменять и создавать объекты;
- NONE
Вы можете создать несколько community string. Для этого нужно задать имя и выбрать права/ Для мониторинга состояние сервера достаточно выбрать READ ONLY.
В списке Accept SNMP packets from these hosts можно указать имена/IP адреса серверов, которым разрешено опрашивать данное устройство. Если вы не хотите ограничивать список разрешенных устройств, оставьте здесь Accept SNMP packets from any hosts.
На вкладке Traps указываются адрес серверов, на который SNMP агент должен отправлять SNMP-ловушка (SNMP trap). SNMP Trap это широковещательный USP пакет, используемый для асинхронного уведомления менеджера (например, сообщение о критическом событии).
Не забудьте открыть в Windows Defender Firewall правила, разрешающие входящий и исходящий трафик для SNMP запросов и ловушек (TRAP). Нужные правила фаейрвола можно включить с помощью PowerShell.
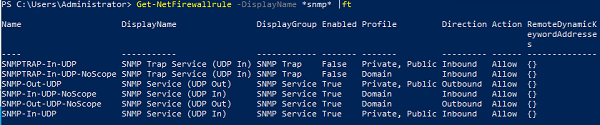
В Windows Firewall есть несколько готовых правил для SNMP трафика:
Get-NetFirewallrule -DisplayName *snmp* |ft
- SNMPTRAP-In-UDP
- SNMPTRAP-In-UDP-NoScope
- SNMP-Out-UDP
- SNMP-In-UDP-NoScope
- SNMP-Out-UDP-NoScope
- SNMP-In-UDP
Можно включить все правила, или только определенное:
Get-NetFirewallrule -DisplayName *snmp* | Enable-NetFirewallRule
Get-NetFirewallrule SNMP-Out-UDP | Disable-NetFirewallRule
В списке служб Windows есть еще одна служба SNMP Trap. Она используется для получения сообщений от других SNMP агентов и пересылки на SNMP сервера (обычно это система мониторинга, опрашивающая устройства по SNMP, например PRTG или Zabbix).
Если вы настраиваете SNMP на Windows Server Core, вы не сможете использовать графический интерфейс службы SNMP для настройки ее параметров. Вместо этого придется вносить изменения в реестр с помощью PowerShell. Настройки службы SNMP хранятся в ветке реестра HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesSNMPParameters.
Следующие команды зададут описание агента:
New-ItemProperty -Path "HKLM:SYSTEMCurrentControlSetservicesSNMPParametersRFC1156Agent" -Name "sysContact" -Value "[email protected]" -PropertyType REG_SZ
New-ItemProperty -Path "HKLM:SYSTEMCurrentControlSetservicesSNMPParametersRFC1156Agent" -Name "sysLocation" -Value "MSK_Datacenter1" -PropertyType REG_SZ
Для каждой ловушки SNMP придется создать отдельный ключ в HKLMSYSTEMCurrentControlSetservicesSNMPParametersTrapConfiguration с именем community.
New-Item -Path "HKLM:SYSTEMCurrentControlSetservicesSNMPParametersTrapConfigurationpublic1"
Укажите разрешения для community:
New-ItemProperty -Path "HKLM:SYSTEMCurrentControlSetServicesSNMPParametersValidCommunities" -Name "public1" -Value 4 -PropertyType DWord
Возможные значения:
- 1 — NONE
- 2 — NOTIFY
- 4 — READ ONLY
- 8 — READ WRITE
- 16 — READ CREATE
Для каждого community можно указать список серверов, с которых разрешено принимать запросы:
New-ItemProperty -Path "HKLM:SYSTEMCurrentControlSetServicesSNMPParametersPermittedManagers" -Name "1" -Value "server1.winitpro.ru" -PropertyType REG_SZ
Перезапустите службу SNMP для применения новых настроек из реестра:
Get-Service SNMP|Restart Service
Если нужно распространить эти SNMP настройки на множество компьютеров/серверов Windows в домене, используйте возможности внесения изменений в реестр через GPO.
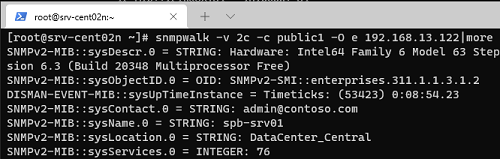
Проверить работу службы SNMP можно с помощью утилиты snmpwalk (доступна в любом Linux дистрибутиве):
# snmpwalk -v 2c -c public1 -O e 192.168.13.122
В этом примере мы опросили наш Windows хост через версию протокола SNMPv2.
Утилита вернула базовыую информацию о хосте (syscontact, sysname, syslocation) и довольно большое количество информации о состоянии сервера Windows.
Install and Enable SNMP Service in Windows 10 / 8 / 7 & Windows Server 2016 / 2012 (R2)
SNMP (Simple Network Management Protocol) is an internet protocol used in network management systems to monitor network-attached devices such as computers, servers, routers, switches, gateways, wireless access points, VoIP phones, and etc. for conditions that warrant administrative attention.
SNMP provides management data in the form of variables on the managed systems, which describe the system configuration parameter or current status value. These variables can then be read and queried (or sometimes set or write) by managing applications.
Windows system, including Windows XP, Windows Vista, Windows 7, Windows Server 2003, Windows Server 2008 (R2), Windows 8, Windows 8.1, Windows Server 2012 (R2), Windows 10, Windows Server 2016, either does not have SNMP service installed by default, or does not turn on SNMP service by default, or does not configure SNMP service by default, thus users need to manually install, enable or configure SNMP service before they can monitor the system via SNMP.
Note that you must be logged on as an administrator or a member of the Administrators group in order to complete this procedure. If your computer is connected to a network, network policy settings may also prevent you from completing this procedure.
How to Install and Enable the SNMP Service
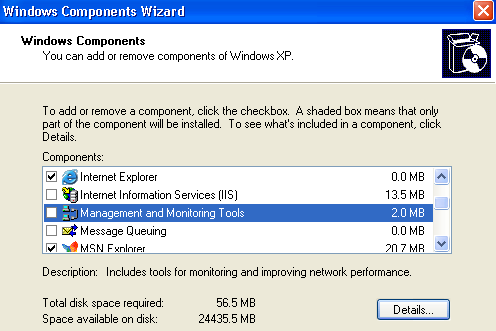
- In Windows XP and Windows Server 2003, click Start button, then go to Control Panel and run Add or Remove Programs applet. On Add or Remove Programs dialog, click Add/Remove Windows Components to open “Windows Components” wizard.
In Windows Vista, Windows 7, Windows Server 2008 and Windows Server 2008 R2, click Start button, then go to Control Panel. Click on Programs -> Programs and Features link and then click on Turn Windows features on or off. If you’re prompted with User Account Control dialog, click “Continue”.
In Windows 8, Windows 8.1, Windows 10, Windows Server 2012, Windows Server 2012 R2, Windows Server 2016 or later, open the Control Panel, then click or tap on Programs -> Programs and Features link, followed by Turn Windows features on or off. If you’re prompted with User Account Control dialog, click “Continue” or “Yes”.
- In Components of Windows XP or Windows Server 2003, click on the Management and Monitoring Tools (make sure that you do not select or clear, tick or untick its check box to change the existing selection), and then click Details.
- Select and tick the check box of Simple Network Management Protocol (SNMP), Simple Network Management Protocol or SNMP feature.
- Click OK. In Windows XP or Windows Server 2003, you need to click additional Next button.
SNMP service will be installed on the system. You may require to insert the Windows setup CD/DVD disc into optical drive.
- SNMP will start automatically after installation. But it’s recommended to verify the service status from Services in Control Panel or Task Manager, and if it’s stopped, you can start the SNMP service from there.
Two new services will be created:
- SNMP Service which is the main engine with agents that monitor the activity in the network devices and report the information to the monitoring console workstation.
- SNMP Trap Service which receives trap messages generated by local or remote SNMP agents and forwards the messages to SNMP management programs running on this computer.
Windows doesn’t assign any community string to the SNMP service by default, and also only allow access from localhost (this computer only) or local devices. Further configuration is needed to add in desired community string, which act as the password to grant reply to any SNMP request from remote system.
How to Configure Security Community String for SNMP Service
Note: The following guide public community string as example.
- Open Control Panel.
- In Windows XP, go to Performance and Maintenance, while the other versions of Windows, System and Maintenance link.
- Open Administrative Tools.
- Run Services applet.
- Locate and right click on SNMP Service, then select Properties.
- In SNMP Service Properties window, click on Services tab.
- Under “Accepted community names” section, click Add button.
- Select the appropriate permission level for the community string in the “Community Rights” drop down list to specify the authentication that the host used to process and grant SNMP requests from the selected community. Normally READ ONLY is recommended.
- In the “Community Name” box, type public or any case-sensitive community name that you want.
- Click on Add button.
- In order for the SNMP service to accept and receive SNMP request packets from any host on the network, including external remote host regardless of identity, click Accept SNMP packets from any host.
To limit the acceptance of SNMP packets, click Accept SNMP packets from these hosts, and then click Add, and then type the appropriate host name, IP or IPX address in the Host name, IP or IPX address box. You can restrict the access to local host or limited servers only by using this setting. Finish off by clicking Add button again.
- Click OK when done. Note that you may need to reboot for the settings to take effect.
Optionally, if you requires to send SNMP traps to remote trap destination, you can configure it at the “Traps” tab.
How to Configure SNMP Traps
- Open Control Panel.
- In Windows XP, go to Performance and Maintenance, while the other versions of Windows, System and Maintenance link.
- Open Administrative Tools.
- Run Services applet.
- Locate and right click on SNMP Service, then select Properties.
- Go to Traps tab.
- In SNMP Service Properties window, click on Traps tab.
- In the “Community name” text box, enter public or any other case-sensitive SNMP community name to which this computer will send trap messages.
- Click on Add to list button.
- Then, click or tap on the Add button below “Trap destinations” to enter IP addresses, host names or IPX addresses of the remove server that will receive SNMP traps.
About the Author: LK
Page load link
If you run Windows Server as Core Installation, like Windows Server 2016 Core or any Microsoft Hyper-V Server edition and you want to use SNMP (Simple Network Management Protocol) on that system, you first have to install the SNMP feature on that Core Server. After that you can use the MMC to remotely connect to the services list on the Core Server.
Install SNMP on Windows Server Core
First lets see if the SNMP feature is installed, using PowerShell:
Get-WindowsFeature *SNMP*
By default the SNMP feature is not installed. To install the SNMP feature on Windows Server Core, you can run the following command:
Install-WindowsFeature SNMP-Service -IncludeAllSubFeature -Verbose
Configure SNMP on Windows Server Core
After you have installed the SNMP feature, you and you have enabled Remote Management you can mange and configure smtp via remote MMC.
Simply open up MMC click on File and then on Add/Remove Snap-in. Now you can select the Services snap-in and enter the name or IP address of the Windows Server Core you want to configure the SNMP services.
Important: If you need to configure the SNMP Service on a remote machine using the MMC, you have to install the RSAT-SNMP feature on the local administrative computer. Otherwise, you will not see the SNMP specific tabs. In older versions of Windows and Windows Server, you needed to install the SNMP feature instead of the RSAT-SNMP feature.
Install-WindowsFeature RSAT-SNMP -verbose
I hope this blog post was helpful. And it helps you to install and configure the SNMP feature on Windows Server. Especially you should have a look at the remote management part for the SNMP service. It works with all the latest Windows Server versions like 2008 R2, 2012, 2016 and event Windows Server 2019. If you have any question, feel free to comment on this post.
Tags: Core Server, Hyper-V, Install SNMP, Microsoft, mmc, Monitoring, PowerShell, Remote SNMP, RSAT SNMP, snmp, SNMP Feature, SNMP Trap, Windows Server, Windows Server 2012 R2, Windows Server 2016, Windows Server 2019, Windows Server Core Last modified: March 10, 2021
About the Author / Thomas Maurer
Thomas works as a Senior Cloud Advocate at Microsoft. He engages with the community and customers around the world to share his knowledge and collect feedback to improve the Azure cloud platform. Prior joining the Azure engineering team, Thomas was a Lead Architect and Microsoft MVP, to help architect, implement and promote Microsoft cloud technology.
If you want to know more about Thomas, check out his blog: www.thomasmaurer.ch and Twitter: www.twitter.com/thomasmaurer
- Remove From My Forums
-
Question
-
We have a new Win 2016 Standard edition which as far as i know, it doens’t have SNMP Service installed by default. But when i go to Server Management — features, I don’t see the SNMP Service option to install.
Also tried from powershell but get-windowsfeature shows a 20% then disappear and nothing changes. Using -LogPath i see:
116: 2018-05-17 12:26:10.033 [ServerManagerPS] Complete initializing log file.
116: 2018-05-17 12:26:10.065 [ServerManagerPS] Enumerate server component started. Component names: SNMP-Service
116: 2018-05-17 12:26:10.471 [ServerManagerPS] Enumerate server component ended with Success.What am i missing ? is there other way to installing it or am I doing something wrong ?
Thanks in advance
-
Edited by
Thursday, May 17, 2018 5:08 PM
-
Edited by
What is SNMP?
SNMP also known as “Simple Network Management Protocol” is an application-layer protocol used to measure and monitor the performance of the devices within a network. It helps the system administrator to ensure that networks stay up and running. Today, SNMP is one of the most popular networking protocols in the world. All modern manufacturers create SNMP-enabled devices that enterprises can use to obtain performance data from the devices.
How SNMP Works?
SNMP uses the device’s Management Information Database (MIB) to collect the performance data. The MIB is a database that records information about the hardware and contains MIB files. The MIB resides within the SNMP manager designed to collect information and organize it into a hierarchical format. SNMP uses this information from the MIB to interpret messages before sending them onwards to the end-user.
There are different types of queries managers used to poll the information from the SNMP agent including, GET or GET-NEXT commands. The GET command uses the agent’s hostname and Object Identifiers (OID) to obtain the information from the MIB. The GET-NEXT command obtains the data from the next OID.
What is SNMPWALK?
SNMPWALK is a command-line utility used to collect the information from remote SNMP-enabled devices including, routers and switches. It allows you to see all the OID variables available on remote devices. It sends multiple GET-NEXT commands to OIDs then the manager collects the data from all OIDs. SNMPWALK is a command-line utility that can be installed on Linux and Windows operating systems.
In this guide, we will show you how to install SNMPWALK on Windows and Linux. We will also explain how to use it to get the information from the remote devices.
Install SNMP and SNMPWALK on Linux
In this section, we will show you how to install SNMP and SNMPWALK on Debian and RPM-based Linux operating systems.
For RPM-based operating system including, RHEL/CentOS/Fedora, install the SNMP and SNMPWALK using the following command:
yum install net-snmp net-snmp-libs net-snmp-utils -y
For Debian based operating system including, Debian/Ubuntu, install the SNMP and SNMPWALK using the following command:
apt-get install snmpd snmp libsnmp-dev -y
Once the installation has been finished, start the SNMP service and enable it to start at system reboot with the following command:
systemctl start snmpd
systemctl enable snmpd
You can check the status of the SNMP with the following command:
systemctl status snmpd
You should get the following output:
● snmpd.service - Simple Network Management Protocol (SNMP) Daemon.
Loaded: loaded (/lib/systemd/system/snmpd.service; enabled; vendor preset: enabled)
Active: active (running) since Fri 2021-05-14 06:36:48 UTC; 3min 22s ago
Main PID: 36724 (snmpd)
Tasks: 1 (limit: 4691)
Memory: 8.7M
CGroup: /system.slice/snmpd.service
└─36724 /usr/sbin/snmpd -LOw -u Debian-snmp -g Debian-snmp -I -smux mteTrigger mteTriggerConf -f -p /run/snmpd.pid
May 14 06:36:48 ubuntu2004 systemd[1]: Starting Simple Network Management Protocol (SNMP) Daemon....
May 14 06:36:48 ubuntu2004 systemd[1]: Started Simple Network Management Protocol (SNMP) Daemon..By default, SNMP does not allow retrieving all available SNMP information. So you will need to edit the SNMP default configuration file and make some changes so we can retrieve all information using the SNMPWALK command.
nano /etc/snmp/snmpd.conf
Find the following lines:
rocommunity public default -V systemonly
rocommunity6 public default -V systemonly
And, replace them with the following lines:
rocommunity public default
rocommunity6 public default
Save and close the file then restart the SNMP service to apply the changes:
systemctl restart snmpd
Now, open your command-line interface and print help information of SNMPWALK command as shown below:
snmpwalk -h
You should get the following output:
USAGE: snmpwalk [OPTIONS] AGENT [OID]
Version: 5.8
Web: http://www.net-snmp.org/
Email: net-snmp-coders@lists.sourceforge.net
OPTIONS:
-h, --help display this help message
-H display configuration file directives understood
-v 1|2c|3 specifies SNMP version to use
-V, --version display package version number
SNMP Version 1 or 2c specific
-c COMMUNITY set the community string
SNMP Version 3 specific
-a PROTOCOL set authentication protocol (MD5|SHA|SHA-224|SHA-256|SHA-384|SHA-512)
-A PASSPHRASE set authentication protocol pass phrase
-e ENGINE-ID set security engine ID (e.g. 800000020109840301)
-E ENGINE-ID set context engine ID (e.g. 800000020109840301)
-l LEVEL set security level (noAuthNoPriv|authNoPriv|authPriv)
-n CONTEXT set context name (e.g. bridge1)
-u USER-NAME set security name (e.g. bert)
-x PROTOCOL set privacy protocol (DES|AES)
-X PASSPHRASE set privacy protocol pass phrase
-Z BOOTS,TIME set destination engine boots/time
General communication options
-r RETRIES set the number of retries
-t TIMEOUT set the request timeout (in seconds)
Debugging
-d dump input/output packets in hexadecimal
-D[TOKEN[,...]] turn on debugging output for the specified TOKENs
(ALL gives extremely verbose debugging output)
Install SNMP and SNMPWALK on Windows 10 Windows Server 2016 and Windows Server 2019
In this section, we will show you how to install SNMP and SNMPWALK on the Windows operating system.
Follow the below steps to install SNMP on Windows:
Step 1 – Open the Control Panel as shown below:
Step 2 – Click on the Programs and Features you should see in the page below:
Step 3 – Click on the Turn Windows features on or off.
Step 4 – On Windows 10, select Simple Network Management Protocol (SNMP) and install it.
Step 5 – On Windows Server 2016 and 2019, click on the Add Roles and Features Wizard until you reach the Features section then select SNMP service.
Step 6 – Install SNMP Service.
This will automatically install the SNMP service on your Windows system.
After installing SNMP, you will need to configure it.
Follow the below steps to configure the SNMP service:
Step 1 – Press Windows + R and type services.msc as shown below:
Step 2 – Press OK to open the Windows service configuration wizard.
Step 3 – Select the SNMP service, right-click and click on the properties as shown below:
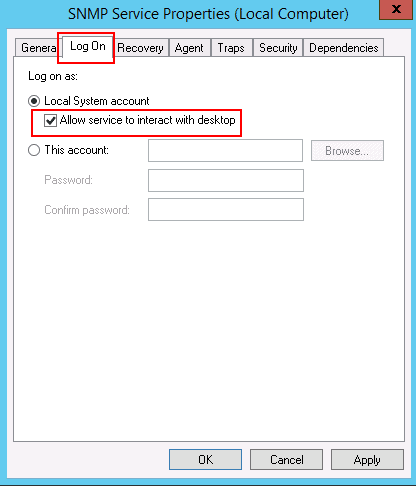
Step 4 – In the Log On tab, select “Allow service to interact with desktop”. Then click on the Agent tab as shown below:
Step 5 – Select all services and click on the Security tab as shown below:
Step 6 – Click on the Add button. You should see the following screen:
Step 7 – Provide community rights and community name then click on the Add button. You should see the following page:
Step 8 – Click on the Apply button to apply the changes.
For full SNMP functionality, you will need to download the SolarWinds MIB Walk module from their Engineer’s Toolset to your windows system. However, you can download the free snmpwalk files from the SourceForge website and follow along with this post.
Once SNMPWALK is downloaded, extract it to the download folder. You can now use snmpwalk.exe to launch and use the SNMPWALK.
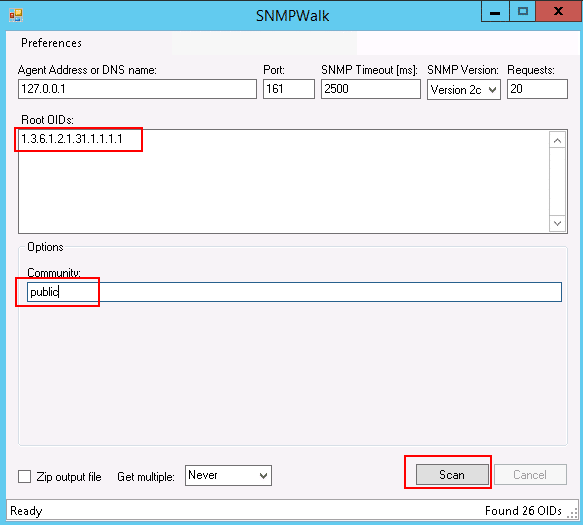
Provide your agent address, OID, community, and click the Scan button. This will generate a complete system information report based on the OID.
How to Use SNMPWALK to Retrieve the System Information
In this section, we will show you how to use the SNMPWALK command in Linux to retrieve the system information.
You can use the following options with the SNMPWALK command to retrieve the system information:
- -v: Specify the SNMP version.
- -c: Specify the community string which you have configured on the SNMP.
- hostname: Specify the hostname or IP address of the system where the SNMP agent is installed.
- OID: Specify the OID to return all SNMP objects.
Now, open your command-line interface and run the following command to list all existing OIDs on the network..
snmpwalk -v 2c -c public localhost
You should get the following output:
iso.3.6.1.2.1.1.1.0 = STRING: "Linux ubuntu2004 5.4.0-29-generic #33-Ubuntu SMP Wed Apr 29 14:32:27 UTC 2020 x86_64"
iso.3.6.1.2.1.1.2.0 = OID: iso.3.6.1.4.1.8072.3.2.10
iso.3.6.1.2.1.1.3.0 = Timeticks: (19907) 0:03:19.07
iso.3.6.1.2.1.1.4.0 = STRING: "Me <me@example.org>"
iso.3.6.1.2.1.1.5.0 = STRING: "ubuntu2004"
iso.3.6.1.2.1.1.6.0 = STRING: "Sitting on the Dock of the Bay"
iso.3.6.1.2.1.1.7.0 = INTEGER: 72
iso.3.6.1.2.1.1.8.0 = Timeticks: (3) 0:00:00.03
iso.3.6.1.2.1.1.9.1.2.1 = OID: iso.3.6.1.6.3.10.3.1.1
iso.3.6.1.2.1.1.9.1.2.2 = OID: iso.3.6.1.6.3.11.3.1.1
iso.3.6.1.2.1.1.9.1.2.3 = OID: iso.3.6.1.6.3.15.2.1.1
iso.3.6.1.2.1.1.9.1.2.4 = OID: iso.3.6.1.6.3.1
iso.3.6.1.2.1.1.9.1.2.5 = OID: iso.3.6.1.6.3.16.2.2.1
iso.3.6.1.2.1.1.9.1.2.6 = OID: iso.3.6.1.2.1.49
iso.3.6.1.2.1.1.9.1.2.7 = OID: iso.3.6.1.2.1.4
iso.3.6.1.2.1.1.9.1.2.8 = OID: iso.3.6.1.2.1.50
iso.3.6.1.2.1.1.9.1.2.9 = OID: iso.3.6.1.6.3.13.3.1.3
iso.3.6.1.2.1.1.9.1.2.10 = OID: iso.3.6.1.2.1.92
iso.3.6.1.2.1.1.9.1.3.1 = STRING: "The SNMP Management Architecture MIB."
iso.3.6.1.2.1.1.9.1.3.2 = STRING: "The MIB for Message Processing and Dispatching."
iso.3.6.1.2.1.1.9.1.3.3 = STRING: "The management information definitions for the SNMP User-based Security Model."
iso.3.6.1.2.1.1.9.1.3.4 = STRING: "The MIB module for SNMPv2 entities"
iso.3.6.1.2.1.1.9.1.3.5 = STRING: "View-based Access Control Model for SNMP."
iso.3.6.1.2.1.1.9.1.3.6 = STRING: "The MIB module for managing TCP implementations"
iso.3.6.1.2.1.1.9.1.3.7 = STRING: "The MIB module for managing IP and ICMP implementations"
iso.3.6.1.2.1.1.9.1.3.8 = STRING: "The MIB module for managing UDP implementations"
iso.3.6.1.2.1.1.9.1.3.9 = STRING: "The MIB modules for managing SNMP Notification, plus filtering."
iso.3.6.1.2.1.1.9.1.3.10 = STRING: "The MIB module for logging SNMP Notifications."
You can see the different OIDs in the above output. The typical format of an OID is shown below:
1.3.6.1.4.1.2021.10.1
A brief explanation of the most commonly used OIDs are shown below:
- 1 – ISO – International Organization for Standardization (ISO)
- 3 – org – Organizations according to ISO/IEC 6523-2
- 6 – dod – US Department of Defense (DOD)
- 1 – Internet protocol
- 4 – Private – Device manufactured by a private company
- 2021 – It is the particular device manufacturer number.
To get the hostname of the system, run the following command:
snmpwalk -v 2c -c public 127.0.0.1 .1.3.6.1.2.1.1.5
You should get the following output:
iso.3.6.1.2.1.1.5.0 = STRING: "ubuntu2004"
To get the hostname and kernel information, run the following command:
snmpwalk -v 2c -c public 127.0.0.1 .1.3.6.1.2.1.1.1
You should get the following output:
iso.3.6.1.2.1.1.1.0 = STRING: "Linux ubuntu2004 5.4.0-29-generic #33-Ubuntu SMP Wed Apr 29 14:32:27 UTC 2020 x86_64"
To get the network interface information, run the following command:
snmpwalk -v 2c 127.0.0.1 -c public .1.3.6.1.2.1.2.2.1.1
You should get the following output:
iso.3.6.1.2.1.2.2.1.1.1 = INTEGER: 1
iso.3.6.1.2.1.2.2.1.1.2 = INTEGER: 2
iso.3.6.1.2.1.2.2.1.1.3 = INTEGER: 3
To get the MAC address information, run the following command:
snmpwalk -v 2c 127.0.0.1 -c public .1.3.6.1.2.1.2.2.1.6
You should get the following output:
iso.3.6.1.2.1.2.2.1.6.1 = ""
iso.3.6.1.2.1.2.2.1.6.2 = Hex-STRING: 00 00 2D 3A 26 A4
iso.3.6.1.2.1.2.2.1.6.3 = Hex-STRING: 00 00 0A 3A 26 A4
To get a list of all network interface, run the following command:
snmpwalk -v 2c -c public 127.0.0.1 .1.3.6.1.2.1.31.1.1.1.1
You should get the following output:
iso.3.6.1.2.1.31.1.1.1.1.1 = STRING: "lo"
iso.3.6.1.2.1.31.1.1.1.1.2 = STRING: "eth0"
iso.3.6.1.2.1.31.1.1.1.1.3 = STRING: "eth1"
To get an IP address of the system, run the following command:
snmpwalk -v 2c -c public 127.0.0.1 .1.3.6.1.2.1.4.20.1.1
You should get the following output:
iso.3.6.1.2.1.4.20.1.1.45.58.38.164 = IpAddress: 45.58.38.164
iso.3.6.1.2.1.4.20.1.1.127.0.0.1 = IpAddress: 127.0.0.1
To get the Subnet Mask of the system, run the following command:
snmpwalk -v 2c -c public 127.0.0.1 .1.3.6.1.2.1.4.20.1.3
You should get the following output:
iso.3.6.1.2.1.4.20.1.3.45.58.38.164 = IpAddress: 255.255.255.0
iso.3.6.1.2.1.4.20.1.3.127.0.0.1 = IpAddress: 255.0.0.0
To get the CPU information, run the following command:
snmpwalk -v 2c -c public 127.0.0.1 .1.3.6.1.2.1.25.3.2.1.3 |grep -i cpu
You should get the following output:
iso.3.6.1.2.1.25.3.2.1.3.196608 = STRING: "GenuineIntel: QEMU Virtual CPU version 2.5+"
iso.3.6.1.2.1.25.3.2.1.3.196609 = STRING: "GenuineIntel: QEMU Virtual CPU version 2.5+"
To get the system load information, run the following command:
snmpwalk -v 2c -c public 127.0.0.1 .1.3.6.1.4.1.2021.10.1
You should get the following output:
iso.3.6.1.4.1.2021.10.1.1.1 = INTEGER: 1
iso.3.6.1.4.1.2021.10.1.1.2 = INTEGER: 2
iso.3.6.1.4.1.2021.10.1.1.3 = INTEGER: 3
iso.3.6.1.4.1.2021.10.1.2.1 = STRING: "Load-1"
iso.3.6.1.4.1.2021.10.1.2.2 = STRING: "Load-5"
iso.3.6.1.4.1.2021.10.1.2.3 = STRING: "Load-15"
iso.3.6.1.4.1.2021.10.1.3.1 = STRING: "0.00"
iso.3.6.1.4.1.2021.10.1.3.2 = STRING: "0.01"
iso.3.6.1.4.1.2021.10.1.3.3 = STRING: "0.00"
iso.3.6.1.4.1.2021.10.1.4.1 = STRING: "12.00"
iso.3.6.1.4.1.2021.10.1.4.2 = STRING: "12.00"
iso.3.6.1.4.1.2021.10.1.4.3 = STRING: "12.00"
iso.3.6.1.4.1.2021.10.1.5.1 = INTEGER: 0
iso.3.6.1.4.1.2021.10.1.5.2 = INTEGER: 1
iso.3.6.1.4.1.2021.10.1.5.3 = INTEGER: 0
iso.3.6.1.4.1.2021.10.1.6.1 = Opaque: Float: 0.000000
iso.3.6.1.4.1.2021.10.1.6.2 = Opaque: Float: 0.010000
iso.3.6.1.4.1.2021.10.1.6.3 = Opaque: Float: 0.000000
iso.3.6.1.4.1.2021.10.1.100.1 = INTEGER: 0
iso.3.6.1.4.1.2021.10.1.100.2 = INTEGER: 0
iso.3.6.1.4.1.2021.10.1.100.3 = INTEGER: 0
iso.3.6.1.4.1.2021.10.1.101.1 = ""
iso.3.6.1.4.1.2021.10.1.101.2 = ""
iso.3.6.1.4.1.2021.10.1.101.3 = ""
To get the system uptime information, run the following command:
snmpwalk -v 2c -c public 127.0.0.1 .1.3.6.1.2.1.1.3.0
You should get the following output:
iso.3.6.1.2.1.1.3.0 = Timeticks: (66282) 0:11:02.82
Conclusion
In the above post, you learned how to install and use SNMP and SNMPWALK on Windows and Linux to get the system information across the connected devices. I hope this will help you to monitor the network devices.
SNMPWALK FAQs
What is a snmpwalk tool?
SNMPWALK is a process of exploring the Management Information Base (MIB) structure of an SNMP report. The MIB has a tree structure that is denoted by a dot-notation number and the “walk” crawls through these numbers, recreating the tree. An SNMPWALK tool can construct a MIB tree by mapping the relationship between the values in a MIB. Each number that identifies a node on the MIB tree will have a label and a value. The OID (Object ID) is a reference code for the label.
Is SNMP v3 TCP or UDP?
All versions of SNMP use the same ports – there are two and they are both UDP. Regular SNMP transactions involve the SNMP Manager sending out a broadcasted request, to which the SNMP device agents reply with a MIB. This communication occurs on UDP port 161. The SNMP agent can send out a warning message without waiting for a request. This is called a Trap and it goes to UDP port 162.
What is OID in Linux?
OID is short for Object ID. It is the level code that identifies a node in a tree structure that is used for reporting in SNMP. An SNMP report is called a Management Information Base (MIB). It has a set number of fields that are identified by OIDs. The OID uses a dot-notation format to indicate the inheritance of a node on the tree.