How do I change a file attribute?
View or change file attributes
To view or change the attributes of a file, right-click the file, and then click Properties. In the “Attributes:” section, enabled attributes have checks beside them. Add or remove the checks from Read-only, Archive, or Hidden to enable or disable these options.
How do you use attribute changer?
Right-click one or many files and choose “Change Attributes,” and you can enable or disable read-only status, hiding, indexing, and even NTFS compression. You can change the file’s date of creation, modification and last access, and tweak a photo’s time of taking.
What are Windows file attributes?
File attributes are pieces of information associated with every file and directory that includes additional data about the file itself or its contents. They can exist in only one of two states – Set or Cleared; like an On or Off state. Attributes can be in files, directories, volumes and certain system objects.
Who can change the attribute of file and directory?
To change a “user” attribute on a file in 4.4BSD-derived operating systems, the user must be the owner of the file or the superuser; to change a “system” attribute, the user must be the superuser.
How do I remove a file attribute?
Change file attributes in Windows 10
- Open File Explorer and go to the folder that contains your files.
- Select the file whose attributes you want to change.
- On the Home tab of the Ribbon, click on the Properties button.
- In the next dialog, under Attributes, you can set or remove the Read-only and Hidden attributes.
3 янв. 2018 г.
How do I remove the readonly attribute?
Read-only Files
- Open Windows Explorer and navigate to the file you want to edit.
- Right-click the file name and select “Properties.”
- Select the “General” tab and clear the “Read-only” check box to remove the read-only attribute or select the check the box to set it. …
- Click the Windows “Start” button and type “cmd” in the Search field.
How do I remove attribute changer?
Or, you can uninstall Attribute Changer from your computer by using the Add/Remove Program feature in the Window’s Control Panel. When you find the program Attribute Changer 6.20, click it, and then do one of the following: Windows Vista/7/8: Click Uninstall.
How do I change the creation date of a file?
Change System Date
Right-click the current time and select the option to “Adjust Date/Time.” Choose the option to “Change Date and Time…” and input the new information in the time and date fields. Press “OK” to save your changes and then open the file you want to change.
How do you make a file writable in Windows 10?
Please follow through.
- In Windows Explorer, right-click the file or folder you want to work with.
- From the pop-up menu, select Properties, and then in the Properties dialog box click the Security tab.
- In the Name list box, select the user, contact, computer, or group whose permissions you want to view.
What are the four main common attributes of a file?
The file may have attributes like name, creator, date, type, permissions etc.
…
Following are some of the attributes of a file :
- Name . …
- Identifier. …
- Type. …
- Location. …
- Size. …
- Protection. …
- Time, date, and user identification.
Which is not a file attribute?
Which one of the following is not attributes of file? Explanation: rename is not the attribute of file rest all are files attributes.
What are two file attributes in the Windows environment?
What are two file attributes in the Windows environment? (Choose two.) Explanation: The file attributes are read-only, archive, hidden, and system. Details, security, and general are tabs on the file Properties applet.
Go to Control Panel and open Folder Options. 2. Go to the View tab and select “Show hidden files and folders”. Then uncheck “Hide protected operating system files”.
What is the attribute command?
You can use the /attribute command to get the total value of an attribute, get the base value of an attribute, set the base value of an attribute, or work with attribute modifiers for a targeted entity in Minecraft.
What is an A attribute on a file?
Prior to windows 8/10 the attributes were: R = READONLY H = HIDDEN S = SYSTEM A = ARCHIVE C = COMPRESSED N = NOT INDEXED L = Reparse Points O = OFFLINE P = Sparse File I = Not content indexed T = TEMPORARY E = ENCRYPTED.
Last Updated on October 24, 2019 by
Cisco ITE latest or ITE 6.0 A+ Cert Practice Exam 2 Answers PC hardware and software (ITE Version 6.00) collection year 2017, 2018 and 2019 Full 100%. IT Essentials has been know as ITE. The following are the questions exam answers. Guarantee Passed. ITE 6.0 A+ Cert Practice Exam 2 answers has some new update from the old version 5. You can review all ITE 6.0 A+ Cert Practice Exam 2 Answers. You will get passed scored 100% with this version 6.0. Good Luck for ITE v6.0 Exam!
-
A server administrator needs to set up a new server with disk fault tolerance technology. The administrator decides to deploy RAID 0+1 technology. What is the minimum number of disks needed to deploy the disk array setting?
- 2
- 3
- 4
- 5
- 6
Explanation:
-
A user has detected that one of the virtual machines in a computer is infected with a virus. Which statement about the situation is likely to be true?
- The host operating system is not necessarily infected with a virus.
- The host machine operating system has a bug.
- All of the virtual machines running on the host are infected with a virus.
- The host machine antivirus program requires an update.
Explanation:
-
Which fire protection system would be best for a university computer/electronics lab?
- an overhead sprinkler system
- an electronic ion spreader
- a nonwater based fire extinguisher
- fire suppressing hazmat blankets and supressors
-
Why should a technician avoid opening the casing of a power supply?
- Power supplies must always be replaced, not repaired.
- Hazardous levels of electricity may be present inside the power supply.
- Power supplies are very fragile, expensive, and easy to damage.
- Only the power supply manufacturer can open the casing of a power supply.
Explanation:
-
What is the first step a technician should take when preparing to work on the inside of a computer?
- Remove the power supply.
- Disconnect the computer from power.
- Disconnect the computer from the network.
- Remove external devices such as a mouse.
Explanation:
-
What tool can be used to find and attempt to fix file structural errors on a hard disk in Windows 7?
- Format
- Sfc
- Rd
- Chkdsk
Explanation:
-
A customer asks for a solution to a printer problem that is beyond the knowledge level of the technician. What should the technician do?
- Try to fix the problem anyway.
- Tell the customer to call the printer manufacturer to fix the problem.
- Gather as much information as possible and escalate the problem.
- Ask the customer to call again when another technician can provide a solution to the problem.
Explanation:
-
Which statement that is related to running 64-bit software is correct?
- 64-bit software requires a 64-bit processor but can run on a 32-bit operating system.
- 64-bit software requires a 64-bit processor and a 64-bit operating system.
- 64-bit software can run on a 32-bit processor but requires a 64-bit operating system.
- 64-bit software can run on a 32-bit processor using a 32-bit operating system but the software performance will be slower.
Explanation:
-
Which statement is correct about installing a 32-bit operating system on a x64 architecture?
- The OS will always make use of all the RAM available.
- The OS will run correctly.
- The OS can address more than 128 GB of memory.
- This combination will provide better security.
Explanation:
-
What action should a technician take before upgrading computers from Vista to Windows 7?
- Run Vista Upgrade Analyzer.
- Run Windows 7 Upgrade Advisor.
- Uninstall all programs.
- Upgrade the video card.
Explanation:
-
What is a possible situation when it might be necessary to boot Windows 7 from a USB device, a CD, or a DVD?
- to disable background services
- to delete registry keys
- to partition the hard drive
- to repair the system
Explanation:
-
What type of partition has the ability to create volumes spanning across more than one disk?
- primary
- active
- extended
- dynamic
Explanation:
-
What type of file system allows the use of files larger than 5 GB and is mostly used on internal hard drives?
- FAT32
- FAT64
- NTFS
- CDFS
- exFAT
Explanation:
-
Which user account should be used only to perform system management and not as the account for regular use?
- guest
- standard user
- administrator
- power user
Explanation:
-
Which type of user account is created automatically during a Windows 8.1 installation?
- Administrator
- Guest
- Remote Desktop user
- Standard user
Explanation:
-
A technician is attempting to repair a Windows 7 laptop that has a missing or corrupt OS file that prevents Windows 7 from starting up. The technician reboots the laptop and accesses the WinRE via the F8 key. Which option must the technician choose in the System Recovery menu to locate and fix the missing or corrupt system files?
- Startup Repair
- System Restore
- System Image Recovery
- Windows Memory Diagnostic
Explanation:
-
When would the PXE option be used when repairing a PC?
- The display cannot be seen clearly.
- There is no response from the mouse or keyboard.
- The computer needs a replacement operating system.
- A newly installed application caused the system to perform erratically.
Explanation:
-
A user wants to extend a primary partition formatted with the NTFS file system with the unallocated space on the hard disk. What must the user do after the primary partition is extended to make it usable?
- Convert the disk type to dynamic.
- Ensure that the disk type is basic.
- Format the disk with the FAT64 file system.
- Partition the new space as a basic disk.
Explanation:
-
A user is viewing the Windows Disk Management utility and notices that one of the disks is marked as Foreign. What does this mean?
- This is a basic disk that has just been converted to a dynamic disk.
- This is a dynamic disk whose partition has been deleted.
- This is a dynamic disk from another PC running Windows.
- This is a disk that does not contain a valid signature.
Explanation:
-
What are two file attributes in the Windows environment? (Choose two.)
- details
- archive
- read-only
- security
- general
Explanation:
-
What are two functions of hypervisors? (Choose two.)
- to partition the hard drive to run virtual machines
- to protect the host from malware infection from the virtual machines
- to manage virtual machines
- to allocate physical system resources to virtual machines
- to share the antivirus software across the virtual machines
Explanation:
-
Which Windows utility can be used to schedule a regular backup for preventive maintenance?
- Windows Task Scheduler
- Windows Task Manager
- Disk Cleanup
- System Restore
Explanation:
-
Which statement is correct about applying firmware updates?
- Firmware updates are sometimes irreversible.
- It is possible to use the Roll Back feature to reverse the change.
- The firmware updates can be installed automatically using the Windows Service Pack utility.
- Firmware updates should not be included as part of the preventive maintenance program.
Explanation:
-
What is true about restore points?
- Once System Restore is used to restore a system, the change is irreversible.
- Restore points back up personal data files.
- Restore points recover corrupted or deleted data files.
- Restore points should always be created before making changes to a system.
Explanation:
-
A user has a computer that is infected with spyware. What should be performed before removing the spyware?
- Delete system restore files.
- Run Windows Update.
- Run a disk defragmentation.
- Create a full backup.
Explanation:
-
A technician is troubleshooting a Windows 7 laptop that takes significantly longer than expected when performing a file search. What is the possible cause?
- The file system is corrupt.
- The disk type is basic.
- The disk type is dynamic.
- The file permissions are not set.
- The index service is not running.
Explanation:
-
A user reports that a PC is losing files, not opening some files, and is performing slowly. The technician suspects problems with the hard drive. What should be done to protect the data that is on the PC and to determine the source of the problem, without risking total drive failure?
- Run the format command, then replace the hard drive.
- Run chkdsk, then run format.
- Back up all important files, then replace the hard drive.
- Back up all important files, then run chkdsk.
- Run chkdsk, then back up all important files.
Explanation:
-
A user logs into Active Directory on a workstation and the user home directory does not redirect to a network share on a file server. A technician suspects that the group policy setting is incorrect. Which command can the technician use to verify the group policy settings?
- rstrui
- runas
- tasklist
- gpresult
- gpupdate
Explanation:
-
A company has recently deployed Active Directory and now a workstation cannot connect to a network resource. A technician takes corrective action by modifying group policy settings. Which command should the technician use to make the workstation synchronize with the new settings?
- runas
- rstrui
- tasklist
- gpresult
- gpupdate
Explanation:
-
A wired network is undergoing several changes that could leave it vulnerable to connection by unauthorized devices while the work is in progress. Which two temporary measures would enable the authorized devices to continue to have network access but prevent unauthorized devices from connecting? (Choose two.)
- Disable DNS.
- Disable SSID broadcast.
- Disable DHCP.
- Subnet the network.
- Assign static IP addresses to the authorized devices.
Explanation:
-
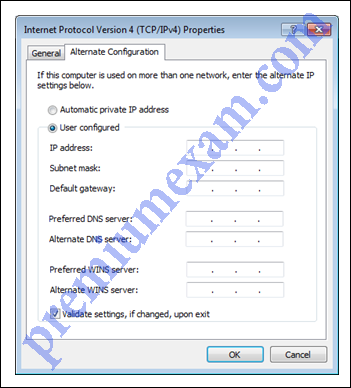
Refer to the exhibit. In what situation would a technician use this tab?
ITE 6.0 A+ Cert Practice Exam 2 Answers 2018 2019 100% 01
- When the device will not be using the Internet.
- When a laptop is used both at work with DHCP and at home with a static IP address.
- When a device is behind a firewall and software is being used that needs access to a remote network.
- When the computer will be using a VPN connection and accessing the Internet while connected through the VPN.
Explanation:
-
On a PC that is running Windows 7 Ultimate, a user sets up a home entertainment system and creates a homegroup. The user then joins two other PCs to the workgroup, one PC running Windows 7 Starter and the other running Windows 7 Home Basic. What else must the user do in order to have the user accounts on the Windows 7 Home Basic and Windows 7 Starter PCs access the shares on the home entertainment system?
- Users have to be added to the user accounts on the home entertainment PC.
- Users on the PC that is running Windows Starter cannot join the homegroup.
- Users on the PC that is running Windows Home Basic will have to be manually added to the homegroup.
- User accounts on all three PCs have to be added to the homegroup.
- Nothing has to be done. All users accounts on all the PCs will automatically be added to the homegroup.
Explanation:
-
A user is reporting that a file has been shared specifically with another user on the network, but the other user opens the file and is unable to save it once edited. What is the probable cause?
- The user shared the document with Read permissions.
- The user forgot to share the parent folder.
- The file has the Archive attribute enabled.
- The file has been deleted.
Explanation:
-
Which character of the Cloud model provides easy monitoring, controlling, reporting, and billing for both the provider and customers?
- rapid elasticity
- resource pooling
- measured service
- broad network access
- on-demand self-service
Explanation:
-
A business organization is configuring security on the mobile devices that are used in the organization. The security policy states that business data on mobile devices should only ever be accessed by employees. Which mobile device security feature can be used to best ensure that business data is rendered completely inaccessible if the device is lost or stolen?
- remote lock
- remote wipe
- passcode lock
- sandbox
Explanation:
-
An administrative assistant tries to link a Bluetooth keyboard and mouse to a computer. The keyboard does not work, but the mouse works fine. What are two issues that could cause this situation? (Choose two.)
- Wi-Fi is turned off.
- The keyboard battery is dead.
- Bluetooth is turned off.
- The Num Lock key has been inadvertently pressed.
- The keyboard is too far from the computer
-
What is needed from Apple and Google in order for individual programmers to develop apps for iOS and Android devices?
- SLA
- SDK
- firmware
- iOS or Android device
Explanation:
-
Which type of malware is disguised as a legitimate program?
- adware
- worm
- Trojan
- spyware
Explanation:
Trojan horses disguise themselves as legitimate programs. Worms replicate themselves across a network. Adware may attach to a legitimate program, but does not disguise itself. Spyware monitors the activities of a user.
-
After complaints from users, a technician identifies that the college web server is running very slowly. A check of the server reveals that there are an unusually large number of TCP requests coming from multiple locations on the Internet. What is the source of the problem?
- A DDoS attack is in progress.
- The server is infected with a virus.
- There is insufficient bandwidth to connect to the server.
- There is a replay attack in progress.
Explanation:
-
Which security threat hides the resources that it uses from antivirus programs?
- worm
- Trojan
- rootkit
- spyware
Explanation:
-
A user receives an email requesting verification of the password that is used to access bank files. What type of security threat is this?
- virus
- social engineering
- phishing
- malware
Explanation:
-
A cleaner attempts to enter a computer lab but is denied entry by the receptionist because there is no scheduled cleaning for that day. What type of attack was just prevented?
- Trojan
- shoulder surfing
- war driving
- social engineering
- phishing
Explanation:
-
Which two precautions can help prevent social engineering? (Choose two.)
- Always ask for the ID of unknown persons.
- Escort all visitors.
- Keep your password securely under your keyboard.
- Do not allow any customers into the workplace.
- Always require a user name and password to be configured.
Explanation:
-
A company has replaced five desktop computers in the accounting and finance department with new computers. The plan is to donate the recovered computers in a fully functional state to a not-for-profit community organization. How can the company ensure that sensitive financial data cannot be accessed once the computers are donated?
- Data wipe the hard drives by using specialized software.
- Perform a high-level format on the hard drives.
- Drill holes through the hard drive platters.
- Delete all the files and directories on the hard drives.
Explanation:
-
A technician needs to permanently destroy data on some drives before disposing of them. What is the best way to do this?
- Partition the hard drives.
- Perform a full format.
- Overwrite the drives
- Shatter the drive platters with a hammer.
Explanation:
-
Which technology allows a mobile device to automatically rotate what is being displayed on the screen as the physical orientation of the device is changed?
- Time Machine
- accelerometer
- screen calibration
- geocaching
Explanation:
-
What three technologies enable virtual assistants to interact with end users via voice commands? (Choose three.)
- VoIP
- multi-threading
- machine learning
- voice recognition
- data fault tolerance
- artificial intelligence
Explanation:
-
Which two guidelines are appropriate for creating strong passwords? (Choose two.)
- Use at least eight characters.
- Include letters, numbers, and symbols.
- Change the password once each year.
- Use only upper case and numeric values in passwords.
- Passwords should contain symbols only.
Explanation:
-
A user is able to only access files required to perform a specific task. What type of security practice is being applied?
- principle of privileges
- principle of necessary privilege
- principle of most privilege
- principle of least privilege
Explanation:
Limiting access to files or folders that are needed to perform a specific job is known as the principle of least privilege. The other options do not exist.
-
Which three items are biometric security devices? (Choose three.)
- fingerprint reader
- retina scanner
- voice recognition
- smart card
- key fob
- password
Explanation:
Fingerprint readers, retina scanners, and voice recognition are all biometric devices, comparing physical characteristics of the user to stored data to authenticate the user. Smart cards, key fobs, and passwords are all security measures, but do not rely on biometrics.
-
How can a user prevent specific applications from accessing a Windows computer over a network?
- Enable MAC address filtering.
- Disable automatic IP address assignment.
- Block specific TCP or UDP ports in Windows Firewall.
- Change default usernames and passwords.
Explanation:
-
A technician is troubleshooting a workstation in a domain that has been infected with a virus. What is the first step the technician should take to clean the infected workstation?
- Run the antivirus software.
- Update the antivirus software.
- Turn off system restore.
- Disconnect the workstation from the network.
Explanation:
-
What is required in order to connect a Wi-Fi enabled laptop to a WPA secured wireless network?
- a security encryption key
- a MAC address
- a username and password
- an updated wireless driver
Explanation:
-
A technician is about to install and configure a wireless network at a small branch office. What is the first security measure the technician should apply immediately upon powering up the wireless router?
- Configure encryption on the wireless router and the connected wireless devices.
- Disable the wireless network SSID broadcast.
- Change the default user-name and password of the wireless router.
- Enable MAC address filtering on the wireless router.
Explanation:
-
A company has a guest wireless network available for visitors while on the company premises. A technician has noted that unauthorized users are connecting to this wireless network from outside the premises. Which action can be taken to reduce unauthorized connections to the guest wireless network while enabling visitors to still connect quickly and easily without assistance while on the company premises?
- Disable SSID broadcast.
- Enable MAC address filtering.
- Configure WPA encryption.
- Reduce the radio power level.
Explanation:
-
What is the most commonly used method to close an application that appears to be frozen on an OS X-based computer?
- Use Force Quit.
- Use Task Manager.
- Access the Status menu.
- Access the Notification Center.
Explanation:
-
In a Linux operating system, which component interprets user commands and forwards them to the OS?
- CLI
- shell
- kernel
- application program
Explanation:
-
In the context of a Linux operating system, which command can be used to display the syntax and parameters for a specific command?
- cat
- man
- grep
- crontab
Explanation:
-
In Linux and OS X, which CLI command can be used to display the name of the current directory?
- ps
- pwd
- sudo
- chmod
Explanation:
-
A system administrator issues the apt-get command on a laptop that has Ubuntu installed. What is the function provided by the command?
- to display or configure a wireless NIC
- to install, configure, and remove packages
- to list the applications currently running in the system
- to allow a user to login as another user or to become a super user
Explanation:
-
A computer technician is notified by a user that there are no automated backups being created on an Apple computer. What is the first thing the technician should check?
- correct date and time configuration
- whether Time Machine is turned on
- if space is available on the local drive
- whether Remote Disc is enabled
Explanation:
-
A user has been using a smartphone for several hours, but now the applications on the device have become unresponsive. What action should the user take?
- Reconfigure settings.
- Restore the mobile operating system from a backup.
- Restart the device.
- Reset the device to factory defaults.
Explanation:
-
A customer is explaining a problem with a computer to a technician. The technician recognizes the problem prior to the customer finishing the explanation. What should the technician do?
- Interrupt the customer and let the customer know that the technician knows what the problem is.
- Start working on the PC while listening to the customer at the same time.
- Ask the customer to repeat the problem so that the technician can document it and verify all the facts.
- Wait politely for the customer to finish explaining the problem.
Explanation:
-
After consulting the manufacturer manuals, a technician applies a series of recommended solutions that resolve a problem with a workstation computer. What is the next step in the troubleshooting process that the technician should perform?
- Verify the solution and confirm full system functionality.
- Document the findings, actions, and outcomes.
- Test the theory of probable cause.
- Determine the next steps to resolve the problem.
Explanation:
-
A security audit for the human resources office finds that most employees leave confidential information on the screen when they are out of office for a short period of time. Which Windows control panel link should be used to make the monitor show a screen saver after a few minutes of inactivity and require that the user re-authenticate?
- Windows Firewall
- Device Manager
- Personalization
- Network and Sharing Center
Explanation:
-
When a user tries to run a program a missing or corrupt DLL message is displayed. What are two possible solutions to this problem? (Choose two.)
- Reinstall the correct drivers.
- Use the msconfig command to adjust the startup settings for the program.
- Run Windows Startup Repair.
- Run sfc/scannow in Safe Mode.
- Register the DLL file using the regsvr32 command.
Explanation:
-
After questioning a user about the problems being experienced with a PC operating system, the support technician suspects that a recent service pack installation has failed. Which step of the troubleshooting process has the technician just concluded?
- Test the theory to determine the cause of the problem.
- Establish a plan of action to resolve the problem.
- Establish a theory of probable cause.
- Document findings, actions, and outcomes.
Explanation:
-
A support desk technician is asking a customer a series of questions about a problem connecting to the network. Which step of the troubleshooting process is the technician applying?
- Identify the problem.
- Establish a theory of probable cause.
- Establish a plan of action to resolve the problem.
- Test the theory to determine cause.
Explanation:
-
A computer technician has successfully returned a laptop to full operation and verified system functionality. Actions the technician performed included modifying the registry and applying patches to the operating systems. What is the next step in the troubleshooting process that the technician should do?
- Reboot the computer.
- Document the solution.
- Consult manufacturer manuals and repair logs.
- Re-attach and test all peripherals.
Explanation:
-
What is a feature that can be used by an administrator to prevent unauthorized users from connecting to a wireless access point?
- MAC filtering
- software firewall
- proxy server
- WPA encryption
Explanation:
-
A user reports that a computer is unable to print on an inkjet printer. The technician has determined that there is no paper in the paper bin. What is the next step in the troubleshooting process?
- Establish a plan of action.
- Determine the exact cause.
- Verify system functionality.
- Document the findings.
Explanation:
-
A support desk technician is dealing with an angry customer. Which two approaches should the technician take in dealing with the customer? (Choose two.)
- Ask socially related questions to direct the customer away from the problem.
- Work to redirect the conversation to solving the problem.
- Immediately transfer the customer to a higher level technician.
- Reply to the customer with the same level of anger.
- Let the customer explain the problem without interrupting.
Explanation:
-
A technician working on a computer discovers what is suspected to be illegal activity. Which three pieces of information should be immediately documented? (Choose three.)
- duration of the suspected illegal activity
- evidence of the suspected illegal activity
- why the computer was accessed by the technician
- details of all past users of the computer
- technical specifications of the computer
- location of the computer
Explanation:
-
A Windows PC that was formatted with the NTFS file system displays a missing or corrupt DLL error message when a certain program is run. What is the cause of this?
- The DLL file was not installed with the program.
- The NTFS file system does not support DLLs.
- The OS must be 64 bit in order to support the DLL.
- The DLL file was not registered during installation of the program.
Explanation:
-
What are two possible symptoms of MBR/GPT corruption in a workstation? (Choose two.)
- The workstation continually restarts.
- The workstation displays an “Invalid Boot Disk” error.
- The workstation displays a black or blue screen of death.
- The workstation displays a “BOOTMGR is missing” error.
- The workstation displays an “Inaccessible Boot Device” error.
Explanation:
-
When installing application software on a Windows 7 workstation, the user sees an error message indicating that the installation is unsuccessful. What should the user try next?
- Run the chkdsk /R command.
- Run the installation under compatibility mode.
- Restart the installation process with the services.msc utility.
- Use the bootrec /fixmbr command from the System Recovery option.
Explanation:
-
A new computer workstation has been installed in a small office. The user of the workstation can print a document using a network printer on the LAN, but cannot access the Internet. What is a possible cause of the problem?
- The TCP/IP stack is not functional.
- The gateway IP address is misconfigured.
- The DHCP server IP address is misconfigured.
- The workstation is configured with a static IP address.
Explanation:
-
What is a result when the DHCP servers are not operational in a network?
- Workstations are assigned with the IP address 0.0.0.0.
- Workstations are assigned with the IP address 127.0.0.1.
- Workstations are assigned with IP addresses in the 10.0.0.0/8 network.
- Workstations are assigned with IP addresses in the 169.254.0.0/16 network.
Explanation:
-
A user reports that during the boot up process of a Windows 7 workstation, the message “MBR has been changed or modified” appears. What is the most probable cause of the message?
- A virus has damaged the MBR.
- A virus has damaged the boot sector.
- A boot sector virus has changed the MBR.
- A virus damaged the Windows system files.
Explanation:
-
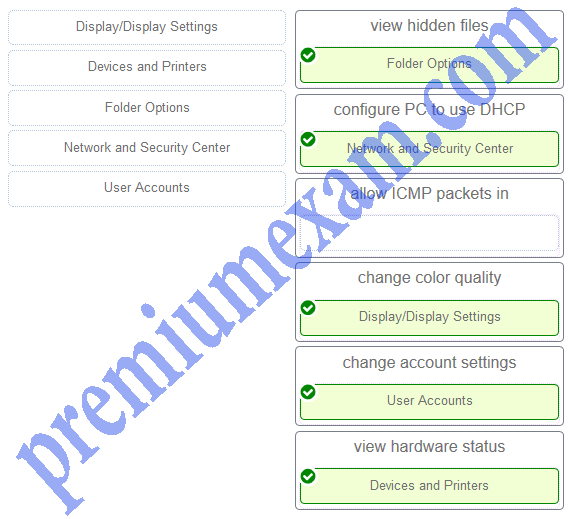
Match the task to the Windows Control Panel utility. (Not all options are used.)
ITE 6.0 A+ Cert Practice Exam 2 Answers 2018 2019 100% 02
A server administrator needs to set up a new server with disk fault tolerance technology. The administrator decides to deploy RAID 0+1 technology. What is the minimum number of disks needed to deploy the disk array setting?
The host operating system is not necessarily infected with a virus
A user has detected that one of the virtual machines in a computer is infected with a virus. Which statement about the situation is likely to be true?
a nonwater based fire extinguisher
Which fire protection system would be best for a university computer/electronics lab?
Hazardous levels of electricity may be present inside the power supply.
Why should a technician avoid opening the casing of a power supply?
Disconnect the computer from power
What is the first step a technician should take when preparing to work on the inside of a computer?
What tool can be used to find and attempt to fix file structural errors on a hard disk in Windows 7?
Gather as much information as possible and escalate the problem.
A customer asks for a solution to a printer problem that is beyond the knowledge level of the technician. What should the technician do?
64-bit software requires a 64-bit processor and a 64-bit operating system
Which statement that is related to running 64-bit software is correct?
The OS will run correctly.
Which statement is correct about installing a 32-bit operating system on a x64 architecture?
Run Windows 7 Upgrade Advisor
What action should a technician take before upgrading computers from Vista to Windows 7?
What is a possible situation when it might be necessary to boot Windows 7 from a USB device, a CD, or a DVD?
What type of partition has the ability to create volumes spanning across more than one disk?
What type of file system allows the use of files larger than 5 GB and is mostly used on internal hard drives?
Which user account should be used only to perform system management and not as the account for regular use?
Which type of user account is created automatically during a Windows 8.1 installation?
A technician is attempting to repair a Windows 7 laptop that has a missing or corrupt OS file that prevents Windows 7 from starting up. The technician reboots the laptop and accesses the WinRE via the F8 key. Which option must the technician choose in the System Recovery menu to locate and fix the missing or corrupt system files?
The computer needs a replacement operating system
When would the PXE option be used when repairing a PC?
Convert the disk type to dynamic
A user wants to extend a primary partition formatted with the NTFS file system with the unallocated space on the hard disk. What must the user do after the primary partition is extended to make it usable?
This is a dynamic disk from another PC running Windows
A user is viewing the Windows Disk Management utility and notices that one of the disks is marked as Foreign. What does this mean?
What are two file attributes in the Windows environment? (Choose two.)
— to manage virtual machines — to allocate physical system resources to virtual machines
What are two functions of hypervisors? (Choose two.)
Which Windows utility can be used to schedule a regular backup for preventive maintenance?
Firmware updates are sometimes irreversible
Which statement is correct about applying firmware updates?
Restore points should always be created before making changes to a system
What is true about restore points?
A user has a computer that is infected with spyware. What should be performed before removing the spyware?
The index service is not running
A technician is troubleshooting a Windows 7 laptop that takes significantly longer than expected when performing a file search. What is the possible cause?
Back up all important files, then run chkdsk
A user reports that a PC is losing files, not opening some files, and is performing slowly. The technician suspects problems with the hard drive. What should be done to protect the data that is on the PC and to determine the source of the problem, without risking total drive failure?
A user logs into Active Directory on a workstation and the user home directory does not redirect to a network share on a file server. A technician suspects that the group policy setting is incorrect. Which command can the technician use to verify the group policy settings?
A company has recently deployed Active Directory and now a workstation cannot connect to a network resource. A technician takes corrective action by modifying group policy settings. Which command should the technician use to make the workstation synchronize with the new settings?
— Disable DHCP — Assign static IP addresses to the authorized devices
A wired network is undergoing several changes that could leave it vulnerable to connection by unauthorized devices while the work is in progress. Which two temporary measures would enable the authorized devices to continue to have network access but prevent unauthorized devices from connecting? (Choose two.)
When a laptop is used both at work with DHCP and at home with a static IP address
Refer to the exhibit. In what situation would a technician use this tab?
Nothing has to be done. All users accounts on all the PCs will automatically be added to the homegroup
On a PC that is running Windows 7 Ultimate, a user sets up a home entertainment system and creates a homegroup. The user then joins two other PCs to the workgroup, one PC running Windows 7 Starter and the other running Windows 7 Home Basic. What else must the user do in order to have the user accounts on the Windows 7 Home Basic and Windows 7 Starter PCs access the shares on the home entertainment system?
The user shared the document with Read permissions
A user is reporting that a file has been shared specifically with another user on the network, but the other user opens the file and is unable to save it once edited. What is the probable cause?
Which character of the Cloud model provides easy monitoring, controlling, reporting, and billing for both the provider and customers?
A business organization is configuring security on the mobile devices that are used in the organization. The security policy states that business data on mobile devices should only ever be accessed by employees. Which mobile device security feature can be used to best ensure that business data is rendered completely inaccessible if the device is lost or stolen?
— The keyboard battery is dead — The keyboard is too far from the computer
An administrative assistant tries to link a Bluetooth keyboard and mouse to a computer. The keyboard does not work, but the mouse works fine. What are two issues that could cause this situation? (Choose two.
What is needed from Apple and Google in order for individual programmers to develop apps for iOS and Android devices?
Which type of malware is disguised as a legitimate program?
A DDoS attack is in progress
After complaints from users, a technician identifies that the college web server is running very slowly. A check of the server reveals that there are an unusually large number of TCP requests coming from multiple locations on the Internet. What is the source of the problem?
Which security threat hides the resources that it uses from antivirus programs?
A cleaner attempts to enter a computer lab but is denied entry by the receptionist because there is no scheduled cleaning for that day. What type of attack was just prevented?
— Always ask for the ID of unknown persons. — Escort all visitors
Which two precautions can help prevent social engineering? (Choose two.)
Data wipe the hard drives by using specialized software
A company has replaced five desktop computers in the accounting and finance department with new computers. The plan is to donate the recovered computers in a fully functional state to a not-for-profit community organization. How can the company ensure that sensitive financial data cannot be accessed once the computers are donated?
Match the task to the Windows Control Panel utility. (Not all options are used.)
A user receives an email requesting verification of the password that is used to access bank files. What type of security threat is this?
Содержание
- What are file attributes in Windows?
- File attributes
- File date time
- File Attributes Перечисление
- Определение
- Примеры
- Комментарии
- What are file attributes in windows
- What are File Attributes and What are They Used For?
- Listing of the Commonly Used Attributes
- How to View and Modify attributes?
- Viewing Attributes from Windows Explorer
- Viewing Attributes from DOS prompt
- Conclusion
What are file attributes in Windows?
As you know, computer’s system mostly consists of files, some of them intended for a system, others for a human. To divide from one another and determine system behavior, to each file added some metadata, which known as file attributes. These attributes can have only one of two states: set and clear. The easiest way to change these attributes is to use Attribute Manager. Let’s take a look what kind of attributes are in Windows.
File attributes
From the time of DOS, Microsoft Windows accepted four attributes for files and folders:
- Archive: it indicates that the file has changed since the last backup operation. The file system of the Windows sets this attribute on any file that has changed.
- Hidden: indicates that the file hidden. Windows File Explorer does not show hidden files by default. To make them visible you need to enable the option: «Show hidden files, folders, and drives» in the Control Panel. «Show hidden files, folders, and drives» in the Control Panel.
- System: indicates that it is a critical system file, that is necessary for the computer to operate correctly. Microsoft Windows use it to mark important system files. Windows File Explorer does not show system files by default. To make them visible, you need to disable option: Hide protected operating system files » at the Folder Options dialogue.
- Read-only: indicates that a file should not be modified. File system API usually does not grant write permission to the requesting application, unless the application explicitly requests it. Read-only attributes on folders typically ignored.
As new versions of Windows came out, Microsoft has introduced new file system NTFS and subsequently NTFS5, which has some new attributes:
- Compressed: When set, Windows compresses the file. The best use of compression is for files that are repetitive, seldom written, usually accessed sequentially, and not themselves compressed. Log files are an ideal example.
- Encrypted: When set, Windows encrypts the file to prevent unauthorized access. Encrypting File System provides secure and user-transparent encryption of any file or folder on a NTFS volume.
- Indexed: When set, Indexing Service or Windows Search do not include the file in their indexing operation.
- Sparse file: Indicates that the file is sparse. Sparse file attempts to use file system space more efficiently when blocks allocated to the file are mostly empty. Achieved by writing brief information representing the empty blocks to disk instead of the actual «empty» space which makes up the block, using less disk space.
- Temporary: A file that used for temporary storage. File systems avoid writing data back to mass storage if sufficient cache memory is available, because typically, an application deletes a temporary file after the handle is closed.
- Offline: The data of a file is not available immediately. This attribute indicates that the file data physically moved to offline storage. Attribute used by Remote Storage, which is the hierarchical storage management software.
File date time
Every file or folder has the date and time information about its creation, access and modify.
- Creation Time: the date and time the file or directory created.
- Last Access Time: the date and time the file or directory was last accessed. The last access time includes the last time the file or directory was written to, read from, or, in the case of executable files, run.
- Last Write Time: the date and time the file or directory was last written to, truncated, or overwritten. This date and time are not updated when file attributes or security descriptors changed.
File Attributes Перечисление
Определение
Предоставляет атрибуты для файлов и каталогов. Provides attributes for files and directories.
Это перечисление имеет атрибут FlagsAttribute, который разрешает побитовое сочетание значений его элементов.
Этот файл помечается для включения в операцию добавочного резервного копирования. This file is marked to be included in incremental backup operation. Windows устанавливает этот атрибут при каждом изменении файла, и программному обеспечению резервного копирования нужно снимать его при обработке файла в рамках добавочного резервного копирования. Windows sets this attribute whenever the file is modified, and backup software should clear it when processing the file during incremental backup.
Файл сжат. The file is compressed.
Зарезервировано для будущего использования. Reserved for future use.
Файл является каталогом. The file is a directory. Directory поддерживается в Windows, Linux и macOS. Directory is supported on Windows, Linux, and macOS.
Файл или каталог зашифрован. The file or directory is encrypted. Для файла это означает, что все данные в файле зашифрованы. For a file, this means that all data in the file is encrypted. Для каталога это означает, что шифрование производится по умолчанию для вновь создаваемых файлов и каталогов. For a directory, this means that encryption is the default for newly created files and directories.
Файл скрытый и, таким образом, не включается в обычный список каталога. The file is hidden, and thus is not included in an ordinary directory listing. Hidden поддерживается в Windows, Linux и macOS. Hidden is supported on Windows, Linux, and macOS.
Файл или каталог включает поддержку целостности данных. The file or directory includes data integrity support. Когда это значение применяется к файлу, все потоки данных в этом файле имеют поддержку целостности. When this value is applied to a file, all data streams in the file have integrity support. Когда это значение применяется к каталогу, все новые файлы и подкаталоги этого каталога по умолчанию включают поддержку целостности. When this value is applied to a directory, all new files and subdirectories within that directory, by default, include integrity support.
Файл является стандартным файлом без специальных атрибутов. The file is a standard file that has no special attributes. Этот атрибут действителен, только если он используется отдельно. This attribute is valid only if it is used alone. Normal поддерживается в Windows, Linux и macOS. Normal is supported on Windows, Linux, and macOS.
Файл или каталог исключен из проверки целостности данных. The file or directory is excluded from the data integrity scan. Когда это значение применяется к каталогу, по умолчанию для всех новых файлов и подкаталогов этого каталога поддержка целостности исключается. When this value is applied to a directory, by default, all new files and subdirectories within that directory are excluded from data integrity.
Файл не будет индексироваться службой индексирования содержимого операционной системы. The file will not be indexed by the operating system’s content indexing service.
Файл находится в автономном режиме. The file is offline. Данные этого файла недоступны непосредственно. The data of the file is not immediately available.
Файл доступен только для чтения. The file is read-only. ReadOnly поддерживается в Windows, Linux и macOS. ReadOnly is supported on Windows, Linux, and macOS. В Linux и macOS изменение флага ReadOnly — это операция с разрешениями. On Linux and macOS, changing the ReadOnly flag is a permissions operation.
Файл содержит точку повторной обработки, блокирующую определяемые пользователем данные, связанные с файлом или каталогом. The file contains a reparse point, which is a block of user-defined data associated with a file or a directory. ReparsePoint поддерживается в Windows, Linux и macOS. ReparsePoint is supported on Windows, Linux, and macOS.
Файл является разреженным. The file is a sparse file. Разреженными файлами обычно являются большие файлы, в которых содержатся в основном нулевые данные. Sparse files are typically large files whose data consists of mostly zeros.
Файл является системным. The file is a system file. То есть файл является частью операционной системы или используется исключительно операционной системой. That is, the file is part of the operating system or is used exclusively by the operating system.
Файл является временным. The file is temporary. Временный файл содержит данные, необходимые во время выполнения приложения, но не требуемые после завершения приложения. A temporary file contains data that is needed while an application is executing but is not needed after the application is finished. Файловые системы для ускорения доступа стремятся держать все данные в памяти, а не сбрасывать их обратно на запоминающее устройство. File systems try to keep all the data in memory for quicker access rather than flushing the data back to mass storage. Приложение должно стереть временный файл сразу после того, как он перестанет быть нужным. A temporary file should be deleted by the application as soon as it is no longer needed.
Примеры
В следующем примере показано, как получить атрибуты для файла и проверить, доступен ли файл только для чтения. The following example shows how to retrieve the attributes for a file and check if the file is read-only.
Комментарии
Вы можете получить атрибуты для файлов и каталогов, вызвав File.GetAttributes метод, и вы можете задать их, вызвав File.SetAttributes метод. You can get attributes for files and directories by calling the File.GetAttributes method, and you can set them by calling the File.SetAttributes method.
Невозможно изменить состояние сжатия File объекта с помощью File.SetAttributes метода. It is not possible to change the compression status of a File object by using the File.SetAttributes method. Вместо этого необходимо сжать файл с помощью средства сжатия или одного из классов в System.IO.Compression пространстве имен. Instead, you must actually compress the file using either a compression tool or one of the classes in the System.IO.Compression namespace.
Следующие атрибуты не поддерживаются .NET Core в Linux и macOS: The following attributes are not supported by .NET Core on Linux and macOS:
What are file attributes in windows
We use digital files every day, but it’s relatively rare we need to recognize the attributes of a digital file. This article is all about understanding File Attributes in Windows.
You might for example have wondered how the Windows operating system differentiates files that are visible from those that are hidden. Or let’s say a text editor program pops up an error message informing you the file is “read-only” when you’re trying to save changes to the file — you might ask yourself: how does the text editor know that the file is read-only? File Attributes tag files with additional information that Windows uses to act on.
Knowing a little about File Attributes will help you understand why certain things happen with files, and why certain things can’t happen if an attribute is defined in a certain way.
What are File Attributes and What are They Used For?
File attributes are pieces of information associated with every file and directory that includes additional data about the file itself or its contents. They can exist in only one of two states – Set or Cleared; like an On or Off state. Attributes can be in files, directories, volumes and certain system objects. They are used by the operating system and software applications to define file system behavior.
Listing of the Commonly Used Attributes
A byte stores the attributes of a file, with each specific attribute assigned to a bit of a byte. To enable a certain attribute, the system will assign a ‘one’ to the corresponding bit, which represents the ‘On’ state. (These are referred to as flagging or setting the attribute). A Windows operating system (Win32) stores the file attributes as 32-bit quantity, while the original MS-DOS file attributes only have 8 bits to store file attributes.
Below are the common attributes and the bits that represent them:
Not Content Indexed (I)
A file may have more than one attribute mapped to it by adding the bits to form the byte attribute. A read-only, hidden directory would have the attribute byte of 00010011, a result of the three attributes added together. Below are the descriptions of each attribute:
- Read-Only (R) : Read-Only attribute will prevent software programs from saving changes to a file. This is useful if you want to write protect a file. Note that a Read-Only file will not prevent it from being deleted.
- Hidden (H) : A file marked with the hidden attribute will be hidden from view under normal viewing conditions.
- System (S) : A file or directory used exclusively by the operating system which should not be altered or deleted.
- Directory (D) : This attribute is tagged to folders or sub-folders to differentiate them from files.
- Archive (A) : This bit is used by software applications that modify files as well as backup software as a “communication link”. Some PC backup software (for example SyncBackPro and SyncBackSE) allows incremental backups by the user, which only backs up files that have changed since the previous backup. When the backup software archives or backs up the file, it resets the archive bit (tagging it zero or Off). Any software that subsequently make changes to the file is expected to set the archive bit. Thus, when the backup software runs the next time, it will be able to identify the modified files by analyzing the archive bits, and backs up those files with the modified bits.
Note that certain programs may modify the files without marking the archive attribute. If the backup software uses incremental backups to backup these files, it will rely on the software to set the bit appropriately. It is therefore important to note that you should not rely solely on this setting to ensure critical files are backed up.
Not Content Indexed (I) : Windows has a search function which indexes all the files and directories in the drive in order to achieve faster results. By default, this attribute is not set, thereby allowing the operating system to include the file into the indexing list. A user could choose to opt out certain files by setting this attribute to On . When set, Windows will skip files that have this option checked.
How to View and Modify attributes?
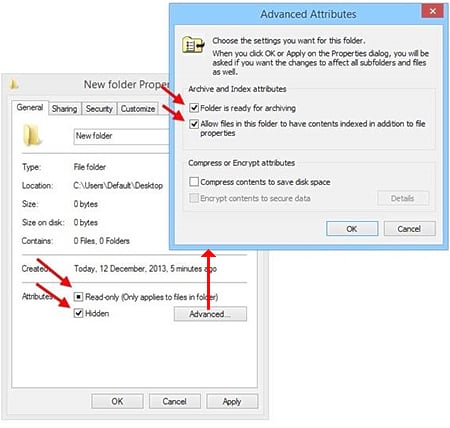
There are a few ways to view and change attributes. Two of them are via the file or folder properties from Windows Explorer or using the ATTRIB command from MS-DOS prompt (type CMD command to bring up the DOS window).
Viewing Attributes from Windows Explorer
Right-clicking and selecting Properties on any file or folder in Windows Explorer will bring up the Properties window, which shows the attributes of the selected item.
Note: The extended attributes (compress and encrypt) will not be shown when you use the ATTRIB command. However, you can view these attributes by executing the Compact and Cipher commands, respectively.
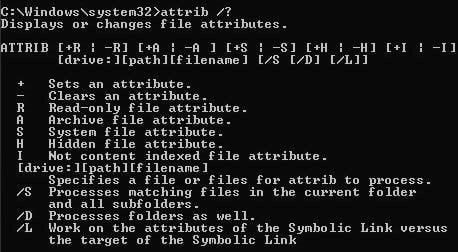
Viewing Attributes from DOS prompt
To view attributes, you can type ATTRIB command from the DOS prompt.
Typing ATTRIB /? will bring up a list of all the syntax available to query a file.
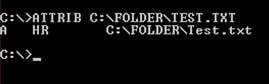
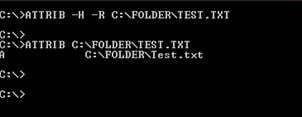
To view what attributes are assigned to a file, type the following:
From here, we can see that the TEST.TXT file has the Archive, Hidden and Read-Only attribute enabled (A, H & R are shown).
Using the ATTRIB command allows a user to Set or Clear an attribute of a file. For the above example, if we wish to remove the attribute of Hide and Read-Only from the file, we could type:
ATTRIB -H -R C:FOLDERTEST.TXT
The example above shows that the hidden and Read-Only attribute have been removed from TEST.TXT.
Conclusion
This article has hopefully helped you understand a little more about Windows file attributes. Being familiar with file attributes will help you better understand how the file system works in a Windows environment. You could use this knowledge to your advantage by selecting the Fast Backup (scanning the Archive Attribute) option in SyncBackSE and SyncBackPro to greatly reduce the time needed for each backup, thereby increasing your productivity and freeing up your system resources for other tasks.