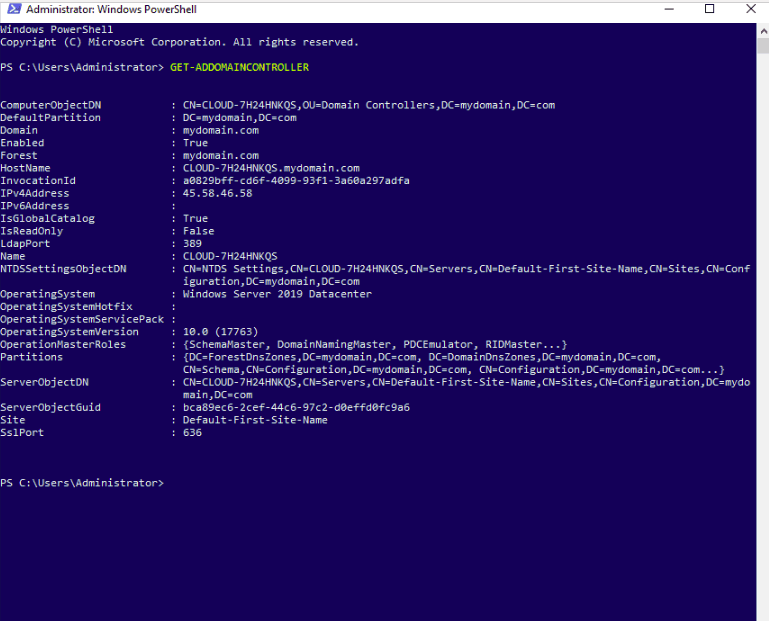
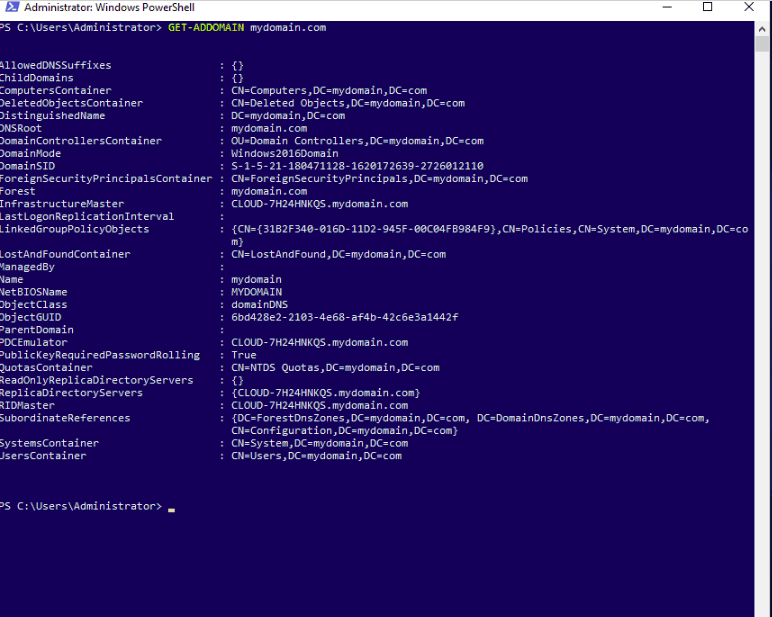
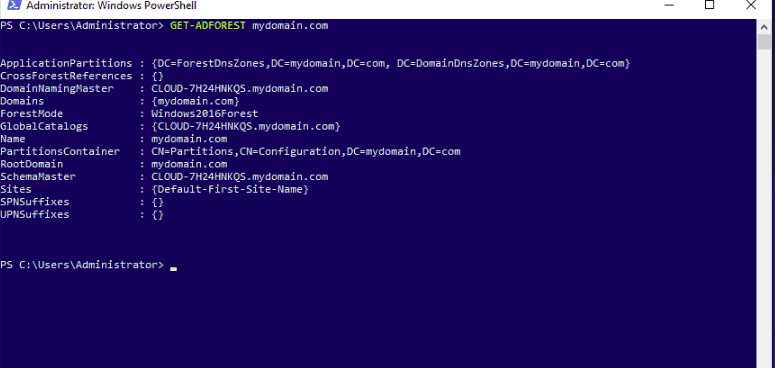
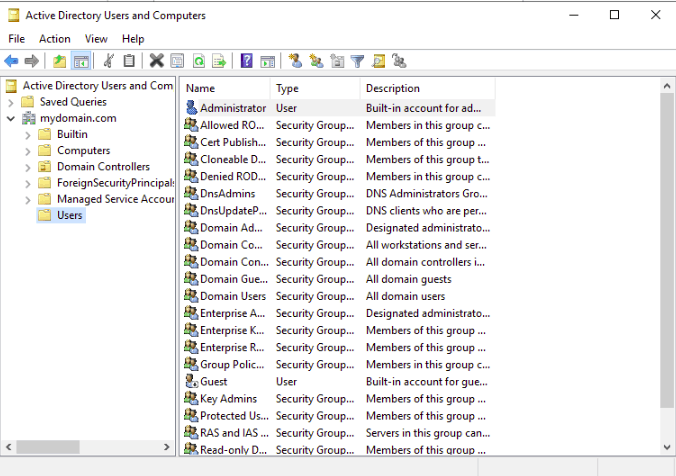
Active Directory (AD) is a directory service developed by Microsoft for Windows domain networks. It is included in most Windows Server operating systems as a set of processes and services.[1][2] Initially, Active Directory was used only for centralized domain management. However, Active Directory eventually became an umbrella title for a broad range of directory-based identity-related services.[3]
A server running the Active Directory Domain Service (AD DS) role is called a domain controller. It authenticates and authorizes all users and computers in a Windows domain type network, assigning and enforcing security policies for all computers, and installing or updating software. For example, when a user logs into a computer that is part of a Windows domain, Active Directory checks the submitted username and password and determines whether the user is a system administrator or normal user.[4] Also, it allows management and storage of information, provides authentication and authorization mechanisms and establishes a framework to deploy other related services: Certificate Services, Active Directory Federation Services, Lightweight Directory Services, and Rights Management Services.[5]
Active Directory uses Lightweight Directory Access Protocol (LDAP) versions 2 and 3, Microsoft’s version of Kerberos,[6] and DNS.[7]
Robert R. King defined it in the following way:[8]
«A domain represents a database. That database holds records about network services-things like computers, users, groups and other things that use, support, or exist on a network. The domain database is, in effect, Active Directory.»
History[edit]
Like many information-technology efforts, Active Directory originated out of a democratization of design using Request for Comments (RFCs). The Internet Engineering Task Force (IETF), which oversees the RFC process, has accepted numerous RFCs initiated by widespread participants. For example, LDAP underpins Active Directory. Also, X.500 directories and the Organizational Unit preceded the Active Directory concept that makes use of those methods. The LDAP concept began to emerge even before the founding of Microsoft in April 1975, with RFCs as early as 1971. RFCs contributing to LDAP include RFC 1823 (on the LDAP API, August 1995),[9] RFC 2307, RFC 3062, and RFC 4533.[10][11][12]
Microsoft previewed Active Directory in 1999, released it first with Windows 2000 Server edition, and revised it to extend functionality and improve administration in Windows Server 2003. Active Directory support was also added to Windows 95, Windows 98 and Windows NT 4.0 via patch, with some features being unsupported.[13][14] Additional improvements came with subsequent versions of Windows Server. In Windows Server 2008, additional services were added to Active Directory, such as Active Directory Federation Services.[15] The part of the directory in charge of the management of domains, which was previously a core part of the operating system,[15] was renamed Active Directory Domain Services (ADDS) and became a server role like others.[3] «Active Directory» became the umbrella title of a broader range of directory-based services.[16] According to Byron Hynes, everything related to identity was brought under Active Directory’s banner.[3]
Active Directory Services[edit]
Active Directory Services consist of multiple directory services. The best known is Active Directory Domain Services, commonly abbreviated as AD DS or simply AD.
Domain Services[edit]
Active Directory Domain Services (AD DS) is the foundation of every Windows domain network. It stores information about members of the domain, including devices and users, verifies their credentials and defines their access rights. The server running this service is called a domain controller. A domain controller is contacted when a user logs into a device, accesses another device across the network or runs a line-of-business Metro-style app sideloaded into a device.
Other Active Directory services (excluding LDS, as described below) as well as most of Microsoft server technologies rely on or use Domain Services; examples include Group Policy, Encrypting File System, BitLocker, Domain Name Services, Remote Desktop Services, Exchange Server and SharePoint Server.
The self-managed Active Directory DS must not be confused with managed Azure AD DS, which is a cloud product.[17]
Lightweight Directory Services[edit]
Active Directory Lightweight Directory Services (AD LDS), formerly known as Active Directory Application Mode (ADAM),[18] is an implementation of the LDAP protocol for AD DS.[19] AD LDS runs as a service on Windows Server. AD LDS shares the code base with AD DS and provides the same functionality, including an identical API, but does not require the creation of domains or domain controllers. It provides a Data Store for the storage of directory data and a Directory Service with an LDAP Directory Service Interface. Unlike AD DS, however, multiple AD LDS instances can run on the same server.
Certificate Services[edit]
Active Directory Certificate Services (AD CS) establishes an on-premises public key infrastructure. It can create, validate, revoke and perform other similar actions, public key certificates for internal uses of an organization. These certificates can be used to encrypt files (when used with Encrypting File System), emails (per S/MIME standard), and network traffic (when used by virtual private networks, Transport Layer Security protocol or IPSec protocol).
AD CS predates Windows Server 2008, but its name was simply Certificate Services.[20]
AD CS requires an AD DS infrastructure.[21]
Federation Services[edit]
Active Directory Federation Services (AD FS) is a single sign-on service. With an AD FS infrastructure in place, users may use several web-based services (e.g. internet forum, blog, online shopping, webmail) or network resources using only one set of credentials stored at a central location, as opposed to having to be granted a dedicated set of credentials for each service. AD FS uses many popular open standards to pass token credentials such as SAML, OAuth or OpenID Connect.[22] AD FS supports encryption and signing of SAML assertions.[23] AD FS’s purpose is an extension of that of AD DS: The latter enables users to authenticate with and use the devices that are part of the same network, using one set of credentials. The former enables them to use the same set of credentials in a different network.
As the name suggests, AD FS works based on the concept of federated identity.
AD FS requires an AD DS infrastructure, although its federation partner may not.[24]
Rights Management Services[edit]
Active Directory Rights Management Services (AD RMS, known as Rights Management Services or RMS before Windows Server 2008) is a server software for information rights management shipped with Windows Server. It uses encryption and a form of selective functionality denial for limiting access to documents such as corporate e-mails, Microsoft Word documents, and web pages, and the operations authorized users can perform on them. These operations can include viewing, editing, copying, saving as or printing for example. IT administrators can create pre-set templates for the convenience of the end user if required. However, end users can still define who can access the content in question and set what they can do. [25]
Logical structure[edit]
As a directory service, an Active Directory instance consists of a database and corresponding executable code responsible for servicing requests and maintaining the database. The executable part, known as Directory System Agent, is a collection of Windows services and processes that run on Windows 2000 and later.[1] Objects in Active Directory databases can be accessed via LDAP, ADSI (a component object model interface), messaging API and Security Accounts Manager services.[2]
Objects[edit]
A simplified example of a publishing company’s internal network. The company has four groups with varying permissions to the three shared folders on the network.
Active Directory structures are arrangements of information about objects. The objects fall into two broad categories: resources (e.g., printers) and security principals (user or computer accounts and groups). Security principals are assigned unique security identifiers (SIDs).
Each object represents a single entity—whether a user, a computer, a printer, or a group—and its attributes. Certain objects can contain other objects. An object is uniquely identified by its name and has a set of attributes—the characteristics and information that the object represents— defined by a schema, which also determines the kinds of objects that can be stored in the Active Directory.
The schema object lets administrators extend or modify the schema when necessary. However, because each schema object is integral to the definition of Active Directory objects, deactivating or changing these objects can fundamentally change or disrupt a deployment. Schema changes automatically propagate throughout the system. Once created, an object can only be deactivated—not deleted. Changing the schema usually requires planning.[26]
Forests, trees, and domains[edit]
The Active Directory framework that holds objects can be viewed at a number of levels. The forest, tree, and domain are the logical divisions in an Active Directory network.
Within a deployment, objects are grouped into domains. The objects for a single domain are stored in a single database (which can be replicated). Domains are identified by their DNS name structure, the namespace.
A domain is defined as a logical group of network objects (computers, users, devices) that share the same Active Directory database.
A tree is a collection of one or more domains and domain trees in a contiguous namespace and is linked in a transitive trust hierarchy.
At the top of the structure is the forest. A forest is a collection of trees that share a common global catalog, directory schema, logical structure, and directory configuration. The forest represents the security boundary within which users, computers, groups, and other objects are accessible.
Organizational units[edit]
The objects held within a domain can be grouped into organizational units (OUs).[27] OUs can provide hierarchy to a domain, ease its administration, and can resemble the organization’s structure in managerial or geographical terms. OUs can contain other OUs—domains are containers in this sense. Microsoft recommends using OUs rather than domains for structure and simplifying the implementation of policies and administration. The OU is the recommended level at which to apply group policies, which are Active Directory objects formally named group policy objects (GPOs), although policies can also be applied to domains or sites (see below). The OU is the level at which administrative powers are commonly delegated, but delegation can be performed on individual objects or attributes as well.
Organizational units do not each have a separate namespace. As a consequence, for compatibility with Legacy NetBios implementations, user accounts with an identical sAMAccountName are not allowed within the same domain even if the accounts objects are in separate OUs. This is because sAMAccountName, a user object attribute, must be unique within the domain.[28] However, two users in different OUs can have the same common name (CN), the name under which they are stored in the directory itself such as «fred.staff-ou.domain» and «fred.student-ou.domain», where «staff-ou» and «student-ou» are the OUs.
In general, the reason for this lack of allowance for duplicate names through hierarchical directory placement is that Microsoft primarily relies on the principles of NetBIOS, which is a flat-namespace method of network object management that, for Microsoft software, goes all the way back to Windows NT 3.1 and MS-DOS LAN Manager. Allowing for duplication of object names in the directory, or completely removing the use of NetBIOS names, would prevent backward compatibility with legacy software and equipment. However, disallowing duplicate object names in this way is a violation of the LDAP RFCs on which Active Directory is supposedly based.
As the number of users in a domain increases, conventions such as «first initial, middle initial, last name» (Western order) or the reverse (Eastern order) fail for common family names like Li (李), Smith or Garcia. Workarounds include adding a digit to the end of the username. Alternatives include creating a separate ID system of unique employee/student ID numbers to use as account names in place of actual users’ names and allowing users to nominate their preferred word sequence within an acceptable use policy.
Because duplicate usernames cannot exist within a domain, account name generation poses a significant challenge for large organizations that cannot be easily subdivided into separate domains, such as students in a public school system or university who must be able to use any computer across the network.
Shadow groups[edit]
In Active Directory, organizational units (OUs) cannot be assigned as owners or trustees. Only groups are selectable, and members of OUs cannot be collectively assigned rights to directory objects.
In Microsoft’s Active Directory, OUs do not confer access permissions, and objects placed within OUs are not automatically assigned access privileges based on their containing OU. This is a design limitation specific to Active Directory. Other competing directories such as Novell NDS can assign access privileges through object placement within an OU.
Active Directory requires a separate step for an administrator to assign an object in an OU as a member of a group also within that OU. Relying on OU location alone to determine access permissions is unreliable, because the object may not have been assigned to the group object for that OU.
A common workaround for an Active Directory administrator is to write a custom PowerShell or Visual Basic script to automatically create and maintain a user group for each OU in their directory. The scripts are run periodically to update the group to match the OU’s account membership but are unable to instantly update the security groups anytime the directory changes, as occurs in competing directories where security is directly implemented into the directory itself. Such groups are known as shadow groups. Once created, these shadow groups are selectable in place of the OU in the administrative tools.
Microsoft refers to shadow groups in the Server 2008 Reference documentation but does not explain how to create them. There are no built-in server methods or console snap-ins for managing shadow groups.[29]
The division of an organization’s information infrastructure into a hierarchy of one or more domains and top-level OUs is a key decision. Common models are by business unit, by geographical location, by IT Service, or by object type and hybrids of these. OUs should be structured primarily to facilitate administrative delegation, and secondarily, to facilitate group policy application. Although OUs form an administrative boundary, the only true security boundary is the forest itself and an administrator of any domain in the forest must be trusted across all domains in the forest.[30]
Partitions[edit]
The Active Directory database is organized in partitions, each holding specific object types and following a specific replication pattern. Microsoft often refers to these partitions as ‘naming contexts’.[31] The ‘Schema’ partition contains the definition of object classes and attributes within the Forest. The ‘Configuration’ partition contains information on the physical structure and configuration of the forest (such as the site topology). Both replicate to all domains in the Forest. The ‘Domain’ partition holds all objects created in that domain and replicates only within its domain.
Physical structure[edit]
Sites are physical (rather than logical) groupings defined by one or more IP subnets.[32] AD also holds the definitions of connections, distinguishing low-speed (e.g., WAN, VPN) from high-speed (e.g., LAN) links. Site definitions are independent of the domain and OU structure and are common across the forest. Sites are used to control network traffic generated by replication and also to refer clients to the nearest domain controllers (DCs). Microsoft Exchange Server 2007 uses the site topology for mail routing. Policies can also be defined at the site level.
Physically, the Active Directory information is held on one or more peer domain controllers, replacing the NT PDC/BDC model. Each DC has a copy of the Active Directory. Servers joined to Active Directory that is not domain controllers are called Member Servers.[33] A subset of objects in the domain partition replicate to domain controllers that are configured as global catalogs. Global catalog (GC) servers provide a global listing of all objects in the Forest.[34][35]
Global Catalog servers replicate to themselves all objects from all domains and, hence, provide a global listing of objects in the forest. However, to minimize replication traffic and keep the GC’s database small, only selected attributes of each object are replicated. This is called the partial attribute set (PAS). The PAS can be modified by modifying the schema and marking attributes for replication to the GC.[36] Earlier versions of Windows used NetBIOS to communicate. Active Directory is fully integrated with DNS and requires TCP/IP—DNS. To be fully functional, the DNS server must support SRV resource records, also known as service records.
Replication[edit]
Active Directory synchronizes changes using multi-master replication.[37] Replication by default is ‘pull’ rather than ‘push’, meaning that replicas pull changes from the server where the change was effected.[38] The Knowledge Consistency Checker (KCC) creates a replication topology of site links using the defined sites to manage traffic. Intra-site replication is frequent and automatic as a result of change notification, which triggers peers to begin a pull replication cycle. Inter-site replication intervals are typically less frequent and do not use change notification by default, although this is configurable and can be made identical to intra-site replication.
Each link can have a ‘cost’ (e.g., DS3, T1, ISDN, etc.) and the KCC alters the site link topology accordingly. Replication may occur transitively through several site links on same-protocol site link bridges, if the cost is low, although KCC automatically costs a direct site-to-site link lower than transitive connections. Site-to-site replication can be configured to occur between a bridgehead server in each site, which then replicates the changes to other DCs within the site. Replication for Active Directory zones is automatically configured when DNS is activated in the domain-based by the site.
Replication of Active Directory uses Remote Procedure Calls (RPC) over IP (RPC/IP). Between Sites, SMTP can be used for replication, but only for changes in the Schema, Configuration, or Partial Attribute Set (Global Catalog) GCs. SMTP cannot be used for replicating the default Domain partition.[39]
Implementation[edit]
In general, a network utilizing Active Directory has more than one licensed Windows server computer. Backup and restore of Active Directory is possible for a network with a single domain controller,[40] but Microsoft recommends more than one domain controller to provide automatic failover protection of the directory.[41] Domain controllers are also ideally single-purpose for directory operations only, and should not run any other software or role.[42]
Certain Microsoft products such as SQL Server[43][44] and Exchange[45] can interfere with the operation of a domain controller, necessitating isolation of these products on additional Windows servers. Combining them can make configuration or troubleshooting of either the domain controller or the other installed software more difficult.[46] A business intending to implement Active Directory is therefore recommended to purchase a number of Windows server licenses, to provide for at least two separate domain controllers, and optionally, additional domain controllers for performance or redundancy, a separate file server, a separate Exchange server, a separate SQL Server,[47] and so forth to support the various server roles.
Physical hardware costs for the many separate servers can be reduced through the use of virtualization, although for proper failover protection, Microsoft recommends not running multiple virtualized domain controllers on the same physical hardware.[48]
Database[edit]
The Active-Directory database, the directory store, in Windows 2000 Server uses the JET Blue-based Extensible Storage Engine (ESE98) and is limited to 16 terabytes and 2 billion objects (but only 1 billion security principals) in each domain controller’s database. Microsoft has created NTDS databases with more than 2 billion objects.[49] (NT4’s Security Account Manager could support no more than 40,000 objects). Called NTDS.DIT, it has two main tables: the data table and the link table. Windows Server 2003 added a third main table for security descriptor single instancing.[49]
Programs may access the features of Active Directory[50] via the COM interfaces provided by Active Directory Service Interfaces.[51]
Trusting[edit]
To allow users in one domain to access resources in another, Active Directory uses trusts.[52]
Trusts inside a forest are automatically created when domains are created. The forest sets the default boundaries of trust, and implicit, transitive trust is automatic for all domains within a forest.
Terminology[edit]
- One-way trust
- One domain allows access to users on another domain, but the other domain does not allow access to users on the first domain.
- Two-way trust
- Two domains allow access to users on both domains.
- Trusted domain
- The domain that is trusted; whose users have access to the trusting domain.
- Transitive trust
- A trust that can extend beyond two domains to other trusted domains in the forest.
- Intransitive trust
- A one way trust that does not extend beyond two domains.
- Explicit trust
- A trust that an admin creates. It is not transitive and is one way only.
- Cross-link trust
- An explicit trust between domains in different trees or the same tree when a descendant/ancestor (child/parent) relationship does not exist between the two domains.
- Shortcut
- Joins two domains in different trees, transitive, one- or two-way.
- Forest trust
- Applies to the entire forest. Transitive, one- or two-way.
- Realm
- Can be transitive or nontransitive (intransitive), one- or two-way.
- External
- Connect to other forests or non-Active Directory domains. Nontransitive, one- or two-way.[53]
- PAM trust
- A one-way trust used by Microsoft Identity Manager from a (possibly low-level) production forest to a (Windows Server 2016 functionality level) ‘bastion’ forest, which issues time-limited group memberships.[54][55]
Management tools[edit]
Microsoft Active Directory management tools include:
- Active Directory Administrative Center (Introduced with Windows Server 2012 and above),
- Active Directory Users and Computers,
- Active Directory Domains and Trusts,
- Active Directory Sites and Services,
- ADSI Edit,
- Local Users and Groups,
- Active Directory Schema snap-ins for Microsoft Management Console (MMC),
- SysInternals ADExplorer
These management tools may not provide enough functionality for efficient workflow in large environments. Some third-party tools extend the administration and management capabilities. They provide essential features for a more convenient administration process, such as automation, reports, integration with other services, etc.
Unix integration[edit]
Varying levels of interoperability with Active Directory can be achieved on most Unix-like operating systems (including Unix, Linux, Mac OS X or Java and Unix-based programs) through standards-compliant LDAP clients, but these systems usually do not interpret many attributes associated with Windows components, such as Group Policy and support for one-way trusts.
Third parties offer Active Directory integration for Unix-like platforms, including:
- PowerBroker Identity Services, formerly Likewise (BeyondTrust, formerly Likewise Software) – Allows a non-Windows client to join Active Directory[56]
- ADmitMac (Thursby Software Systems)[56]
- Samba (free software under GPLv3) – Can act as a domain controller[57][58]
The schema additions shipped with Windows Server 2003 R2 include attributes that map closely enough to RFC 2307 to be generally usable. The reference implementation of RFC 2307, nss_ldap and pam_ldap provided by PADL.com, support these attributes directly. The default schema for group membership complies with RFC 2307bis (proposed).[59] Windows Server 2003 R2 includes a Microsoft Management Console snap-in that creates and edits the attributes.
An alternative option is to use another directory service as non-Windows clients authenticate to this while Windows Clients authenticate to Active Directory. Non-Windows clients include 389 Directory Server (formerly Fedora Directory Server, FDS), ViewDS v7.2 XML Enabled Directory, and Sun Microsystems Sun Java System Directory Server. The latter two are both able to perform two-way synchronization with Active Directory and thus provide a «deflected» integration.
Another option is to use OpenLDAP with its translucent overlay, which can extend entries in any remote LDAP server with additional attributes stored in a local database. Clients pointed at the local database see entries containing both the remote and local attributes, while the remote database remains completely untouched.[citation needed]
Administration (querying, modifying, and monitoring) of Active Directory can be achieved via many scripting languages, including PowerShell, VBScript, JScript/JavaScript, Perl, Python, and Ruby.[60][61][62][63] Free and non-free Active Directory administration tools can help to simplify and possibly automate Active Directory management tasks.
Since October 2017 Amazon AWS offers integration with Microsoft Active Directory.[64]
See also[edit]
- AGDLP (implementing role based access controls using nested groups)
- Apple Open Directory
- Flexible single master operation
- FreeIPA
- List of LDAP software
- System Security Services Daemon (SSSD)
- Univention Corporate Server
References[edit]
- ^ a b «Directory System Agent». MSDN Library. Microsoft. Retrieved 23 April 2014.
- ^ a b Solomon, David A.; Russinovich, Mark (2005). «Chapter 13». Microsoft Windows Internals: Microsoft Windows Server 2003, Windows XP, and Windows 2000 (4th ed.). Redmond, Washington: Microsoft Press. p. 840. ISBN 0-7356-1917-4.
- ^ a b c Hynes, Byron (November 2006). «The Future of Windows: Directory Services in Windows Server «Longhorn»«. TechNet Magazine. Microsoft. Archived from the original on 30 April 2020. Retrieved 30 April 2020.
- ^ «Active Directory on a Windows Server 2003 Network». Active Directory Collection. Microsoft. 13 March 2003. Archived from the original on 30 April 2020. Retrieved 25 December 2010.
- ^ Rackspace Support (27 April 2016). «Install Active Directory Domain Services on Windows Server 2008 R2 Enterprise 64-bit». Rackspace. Rackspace US, Inc. Archived from the original on 30 April 2020. Retrieved 22 September 2016.
- ^ «Microsoft Kerberos — Win32 apps». docs.microsoft.com.
- ^ «Domain Name System (DNS)». docs.microsoft.com.
- ^ King, Robert (2003). Mastering Active directory for Windows server 2003 (3rd ed.). Alameda, Calif.: Sybex. p. 159. ISBN 9780782152012. OCLC 62876800.
- ^ Howes, T.; Smith, M. (August 1995). «The LDAP Application Program Interface». The Internet Engineering Task Force (IETF). Archived from the original on 30 April 2020. Retrieved 26 November 2013.
- ^ Howard, L. (March 1998). «An Approach for Using LDAP as a Network Information Service». Internet Engineering Task Force (IETF). Archived from the original on 30 April 2020. Retrieved 26 November 2013.
- ^ Zeilenga, K. (February 2001). «LDAP Password Modify Extended Operation». The Internet Engineering Task Force (IETF). Archived from the original on 30 April 2020. Retrieved 26 November 2013.
- ^ Zeilenga, K.; Choi, J.H. (June 2006). «The Lightweight Directory Access Protocol (LDAP) Content Synchronization Operation». The Internet Engineering Task Force (IETF). Archived from the original on 30 April 2020. Retrieved 26 November 2013.
- ^ Daniel Petri (8 January 2009). «Active Directory Client (dsclient) for Win98/NT».
- ^ «Dsclient.exe connects Windows 9x/NT PCs to Active Directory». 5 June 2003.
- ^ a b Thomas, Guy (29 November 2000). «Windows Server 2008 — New Features». ComputerPerformance.co.uk. Computer Performance Ltd. Archived from the original on 2 September 2019. Retrieved 30 April 2020.
- ^ «What’s New in Active Directory in Windows Server». Windows Server 2012 R2 and Windows Server 2012 Tech Center. Microsoft.
- ^ «Compare Active Directory-based services in Azure». docs.microsoft.com.
- ^ «AD LDS». Microsoft. Retrieved 28 April 2009.
- ^ «AD LDS versus AD DS». Microsoft. Retrieved 25 February 2013.
- ^ Zacker, Craig (2003). «11: Creating and Managing Digital Certificates». In Harding, Kathy; Jean, Trenary; Linda, Zacker (eds.). Planning and Maintaining a Microsoft Windows server 2003 Network Infrastructure. Redmond, WA: Microsoft Press. pp. 11–16. ISBN 0-7356-1893-3.
- ^ «Active Directory Certificate Services Overview». Microsoft TechNet. Microsoft. Retrieved 24 November 2015.
- ^ «Overview of authentication in Power Apps portals». Microsoft Docs. Microsoft. Retrieved 30 January 2022.
- ^ «How to Replace the SSL, Service Communications, Token-Signing, and Token-Decrypting Certificates». TechNet. Microsoft. Retrieved 30 January 2022.
- ^ «Step 1: Preinstallation Tasks». TechNet. Microsoft. Retrieved 21 October 2021.
- ^ «Test Lab Guide: Deploying an AD RMS Cluster». Microsoft Docs. Microsoft. Retrieved 30 January 2022.
- ^ Windows Server 2003: Active Directory Infrastructure. Microsoft Press. 2003. pp. 1–8–1–9.
- ^ «Organizational Units». Distributed Systems Resource Kit (TechNet). Microsoft. 2011.
An organizational unit in Active Directory is analogous to a directory in the file system
- ^ «sAMAccountName is always unique in a Windows domain… or is it?». Joeware. 4 January 2012. Retrieved 18 September 2013.
examples of how multiple AD objects can be created with the same sAMAccountName
- ^ Microsoft Server 2008 Reference, discussing shadow groups used for fine-grained password policies: https://technet.microsoft.com/en-us/library/cc770394%28WS.10%29.aspx
- ^ «Specifying Security and Administrative Boundaries». Microsoft Corporation. 23 January 2005.
However, service administrators have abilities that cross domain boundaries. For this reason, the forest is the ultimate security boundary, not the domain.
- ^ Andreas Luther. «Active Directory Replication Traffic». Microsoft Corporation. Retrieved 26 May 2010.
The Active Directory is made up of one or more naming contexts or partitions.
- ^
«Sites overview». Microsoft Corporation. 21 January 2005.A site is a set of well-connected subnets.
- ^ «Planning for domain controllers and member servers». Microsoft Corporation. 21 January 2005.
[…] member servers, […] belong to a domain but do not contain a copy of the Active Directory data.
- ^ «What Is the Global Catalog?». Microsoft Corporation. 10 December 2009.
[…] a domain controller can locate only the objects in its domain. […] The global catalog provides the ability to locate objects from any domain […]
- ^ «Global Catalog». Microsoft Corporation.
- ^ «Attributes Included in the Global Catalog». Microsoft Corporation. 26 August 2010.
The isMemberOfPartialAttributeSet attribute of an attributeSchema object is set to TRUE if the attribute is replicated to the global catalog. […] When deciding whether or not to place an attribute in the global catalog remember that you are trading increased replication and increased disk storage on global catalog servers for, potentially, faster query performance.
- ^ «Directory data store». Microsoft Corporation. 21 January 2005.
Active Directory uses four distinct directory partition types to store […] data. Directory partitions contain domain, configuration, schema, and application data.
- ^ «What Is the Active Directory Replication Model?». Microsoft Corporation. 28 March 2003.
Domain controllers request (pull) changes rather than send (push) changes that might not be needed.
- ^ «What Is Active Directory Replication Topology?». Microsoft Corporation. 28 March 2003.
SMTP can be used to transport nondomain replication […]
- ^ «Active Directory Backup and Restore». TechNet. Microsoft. Retrieved 5 February 2014.
- ^ «AD DS: All domains should have at least two functioning domain controllers for redundancy». TechNet. Microsoft. Retrieved 5 February 2014.
- ^ Posey, Brien (23 August 2010). «10 tips for effective Active Directory design». TechRepublic. CBS Interactive. Retrieved 5 February 2014.
Whenever possible, your domain controllers should run on dedicated servers (physical or virtual).
- ^ «You may encounter problems when installing SQL Server on a domain controller (Revision 3.0)». Support. Microsoft. 7 January 2013. Retrieved 5 February 2014.
- ^ Degremont, Michel (30 June 2011). «Can I install SQL Server on a domain controller?». Microsoft SQL Server blog. Retrieved 5 February 2014.
For security and performance reasons, we recommend that you do not install a standalone SQL Server on a domain controller.
- ^ «Installing Exchange on a domain controller is not recommended». TechNet. Microsoft. 22 March 2013. Retrieved 5 February 2014.
- ^ «Security Considerations for a SQL Server Installation». TechNet. Microsoft. Retrieved 5 February 2014.
After SQL Server is installed on a computer, you cannot change the computer from a domain controller to a domain member. You must uninstall SQL Server before you change the host computer to a domain member.
- ^ «Exchange Server Analyzer». TechNet. Microsoft. Retrieved 5 February 2014.
Running SQL Server on the same computer as a production Exchange mailbox server is not recommended.
- ^ «Running Domain Controllers in Hyper-V». TechNet. Microsoft. Planning to Virtualize Domain Controllers. Retrieved 5 February 2014.
You should attempt to avoid creating potential single points of failure when you plan your virtual domain controller deployment.frank
- ^ a b efleis (8 June 2006). «Large AD database? Probably not this large». Blogs.technet.com. Archived from the original on 17 August 2009. Retrieved 20 November 2011.
- ^ Berkouwer, Sander. «Active Directory basics». Veeam Software.
- ^
Active Directory Service Interfaces, Microsoft - ^ «Domain and Forest Trusts Technical Reference». Microsoft Corporation. 28 March 2003.
Trusts enable […] authentication and […] sharing resources across domains or forests
- ^ «Domain and Forest Trusts Work». Microsoft Corporation. 11 December 2012. Retrieved 29 January 2013.
Defines several kinds of trusts. (automatic, shortcut, forest, realm, external)
- ^ «Privileged Access Management for Active Directory Domain Services». docs.microsoft.com.
- ^ «TechNet Wiki». social.technet.microsoft.com.
- ^ a b Edge, Charles S., Jr; Smith, Zack; Hunter, Beau (2009). «Chapter 3: Active Directory». Enterprise Mac Administrator’s Guide. New York City: Apress. ISBN 978-1-4302-2443-3.
- ^ «Samba 4.0.0 Available for Download». SambaPeople. SAMBA Project. Archived from the original on 15 November 2010. Retrieved 9 August 2016.
- ^ «The great DRS success!». SambaPeople. SAMBA Project. 5 October 2009. Archived from the original on 13 October 2009. Retrieved 2 November 2009.
- ^ «RFC 2307bis». Archived from the original on 27 September 2011. Retrieved 20 November 2011.
- ^ «Active Directory Administration with Windows PowerShell». Microsoft. Retrieved 7 June 2011.
- ^ «Using Scripts to Search Active Directory». Microsoft. Retrieved 22 May 2012.
- ^ «ITAdminTools Perl Scripts Repository». ITAdminTools.com. Retrieved 22 May 2012.
- ^ «Win32::OLE». Perl Open-Source Community. Retrieved 22 May 2012.
- ^ «Introducing AWS Directory Service for Microsoft Active Directory (Standard Edition)». Amazon Web Services. 24 October 2017.
External links[edit]
- Microsoft Technet: White paper: Active Directory Architecture (Single technical document that gives an overview about Active Directory.)
- Microsoft Technet: Detailed description of Active Directory on Windows Server 2003
- Microsoft MSDN Library: [MS-ADTS]: Active Directory Technical Specification (part of the Microsoft Open Specification Promise)
- Active Directory Application Mode (ADAM)
- Microsoft MSDN: [AD-LDS]: Active Directory Lightweight Directory Services
- Microsoft TechNet: [AD-LDS]: Active Directory Lightweight Directory Services
- Microsoft MSDN: Active Directory Schema
- Microsoft TechNet: Understanding Schema
- Microsoft TechNet Magazine: Extending the Active Directory Schema
- Microsoft MSDN: Active Directory Certificate Services
- Microsoft TechNet: Active Directory Certificate Services
Organizations of all sizes all over the world use Active Directory to help manage permissions and control access to critical network resources. But what exactly is it, and how can it potentially help your business?
What is Active Directory?
Active Directory (AD) is a directory service that runs on Microsoft Windows Server. The main function of Active Directory is to enable administrators to manage permissions and control access to network resources. In Active Directory, data is stored as objects, which include users, groups, applications, and devices, and these objects are categorized according to their name and attributes.
What Are Active Directory Domain Services?
Active Directory Domain Services (AD DS) are a core component of Active Directory and provide the primary mechanism for authenticating users and determining which network resources they can access. AD DS also provides additional features such as Single Sign-On (SSO), security certificates, LDAP, and access rights management.
The Hierarchical Structure of Active Directory Domain Services
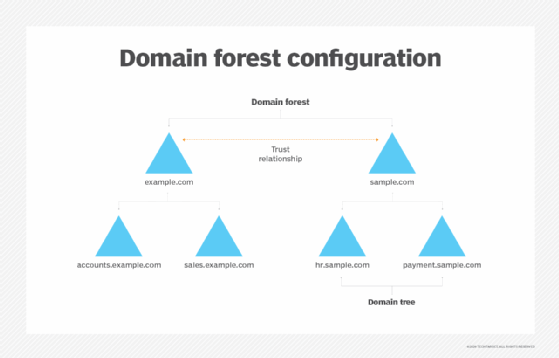
AD DS organizes data in a hierarchical structure consisting of domains, trees, and forests, as detailed below.
Domains: A domain represents a group of objects such as users, groups, and devices, which share the same AD database. You can think of a domain as a branch in a tree. A domain has the same structure as standard domains and sub-domains, e.g. yourdomain.com and sales.yourdomain.com.
Trees: A tree is one or more domains grouped together in a logical hierarchy. Since domains in a tree are related, they are said to “trust” each other.
Forest: A forest is the highest level of organization within AD and contains a group of trees. The trees in a forest can also trust each other, and will also share directory schemas, catalogs, application information, and domain configurations.
Organizational Units: An OU is used to organize users, groups, computers, and other organizational units.
Containers: A container is similar to an OU, however, unlike an OU, it is not possible to link a Group Policy Object (GPO) to a generic Active Directory container.
Other Active Directory Services
Besides Active Directory Domain Services, there are a handful of other critical services that AD provides. Some of those services have been listed below:
Lightweight Directory Services: AD LDS is a Lightweight Directory Access Protocol (LDAP) directory service. It provides only a subset of the AD DS features, which makes it more versatile in terms of where it can be run. For example, it can be run as a stand-alone directory service without needing to be integrated with a full implementation of Active Directory.
Certificate Services: You can create, manage and share encryption certificates, which allow users to exchange information securely over the internet.
Active Directory Federation Services: ADFS is a Single Sign-On (SSO) solution for AD which allows employees to access multiple applications with a single set of credentials, thus simplifying the user experience.
Rights Management Services: AD RMS is a set of tools that assists with the management of security technologies that will help organizations keep their data secure. Such technologies include encryption, certificates, and authentication, and cover a range of applications and content types, such as emails and Word documents.
The server that hosts AD DS is called a domain controller (DC). A domain controller can also be used to authenticate with other MS products, such as Exchange Server, SharePoint Server, SQL Server, File Server, and more.
Getting Started with Windows Active Directory
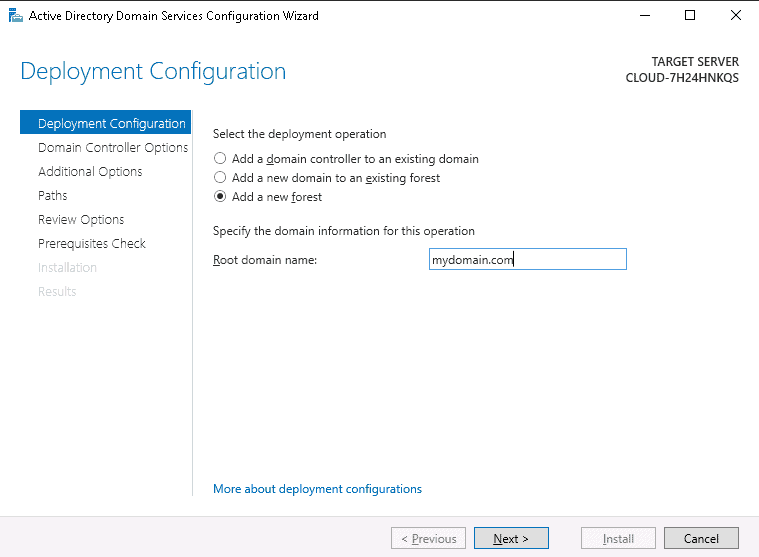
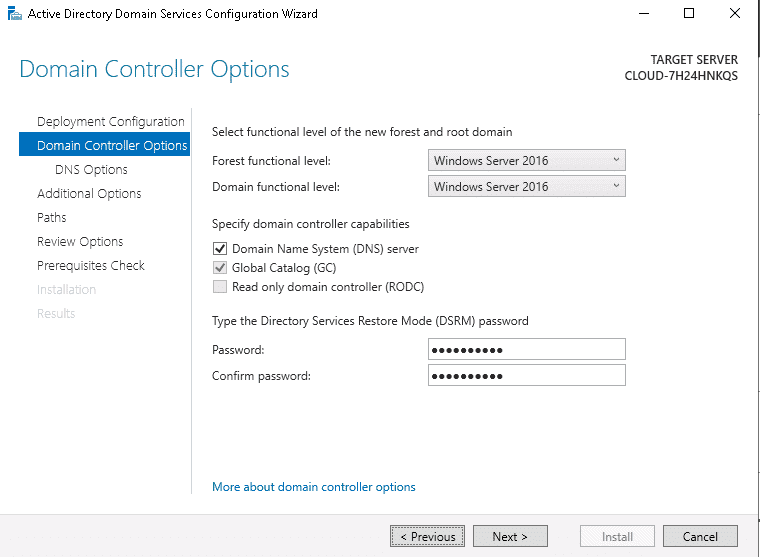
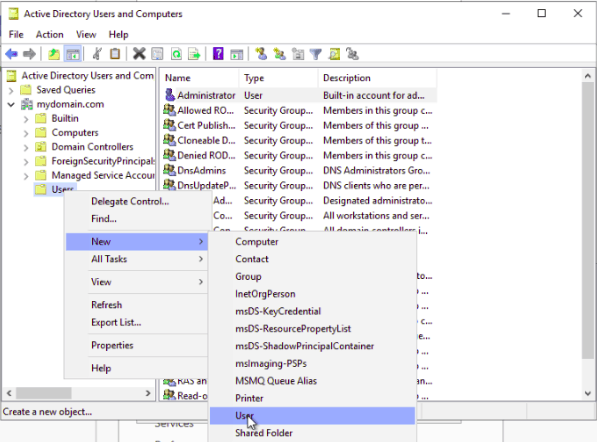
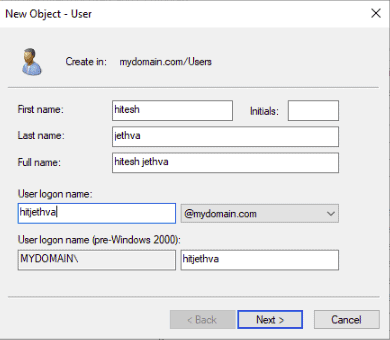
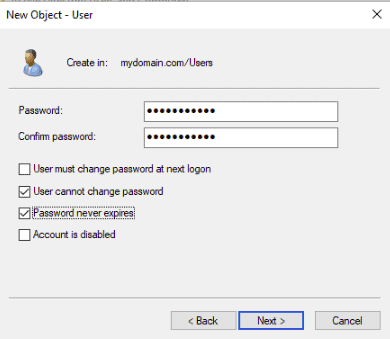
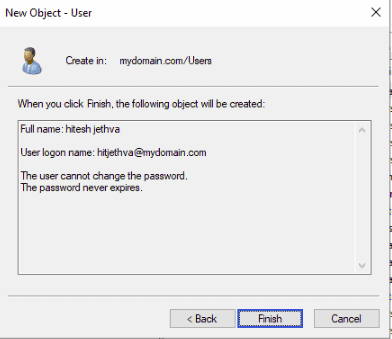
A comprehensive step-by-step guide to setting up Active Directory on Windows Server is beyond the scope of this article. Instead, I will provide a basic summary of the steps required to install AD, which should at least point you in the right direction. Assuming you already have Windows Server (2016) installed, you will need to…
- Change your DNS settings so that your server IP address is the primary DNS server.
- Open the Server Manager, which you can access via PowerShell by logging in as administrator and typing ServerManager.exe.
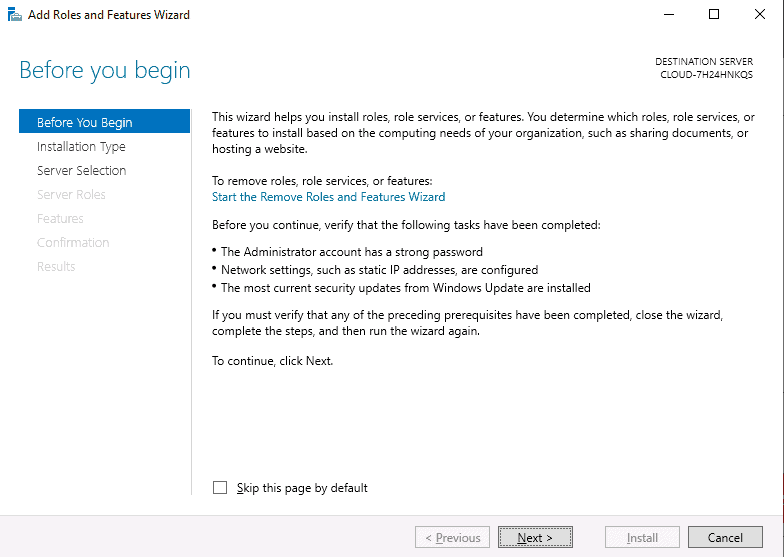
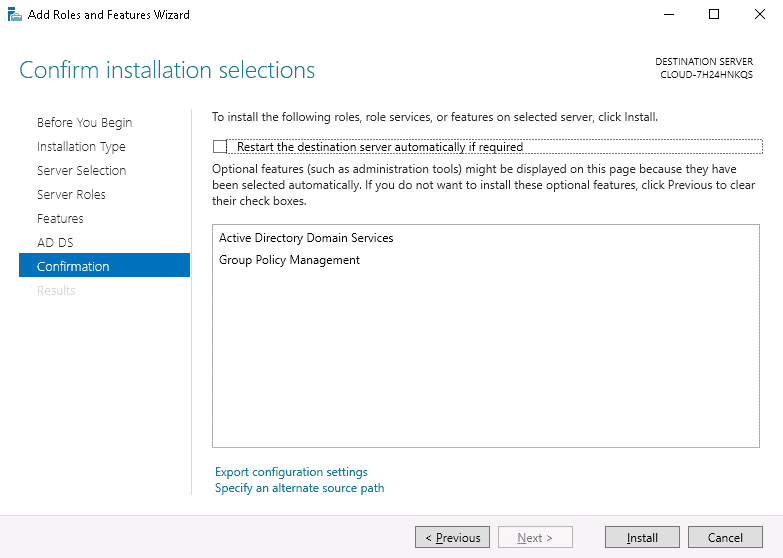
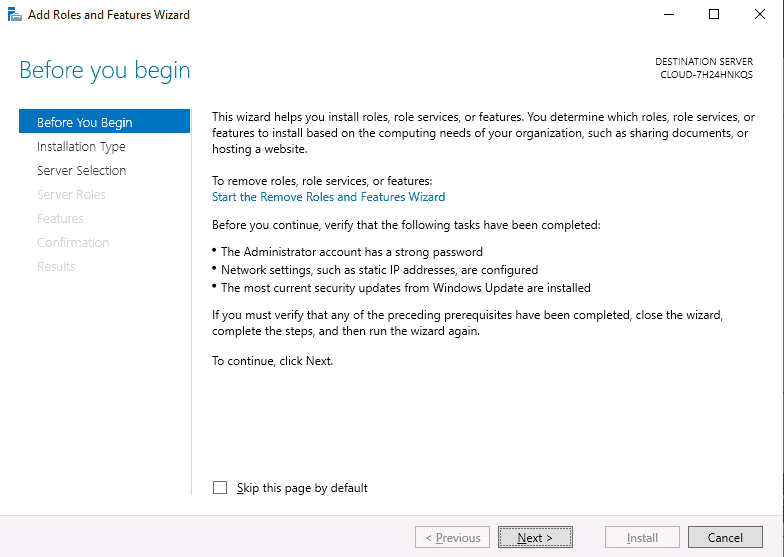
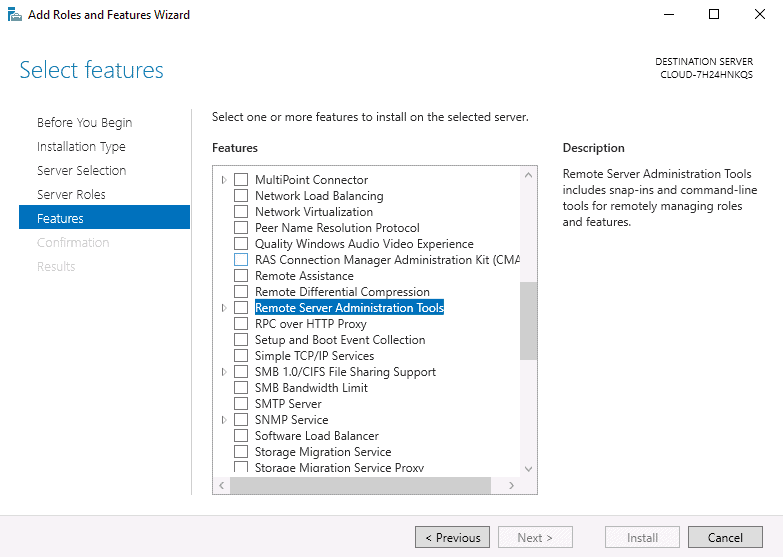
- On the Server Manager window, click on Add roles and features, and click the Next button to start the setup process.
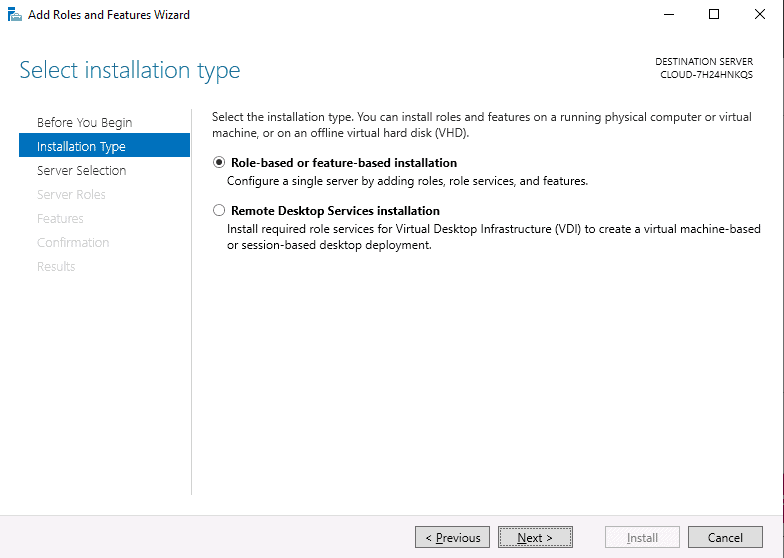
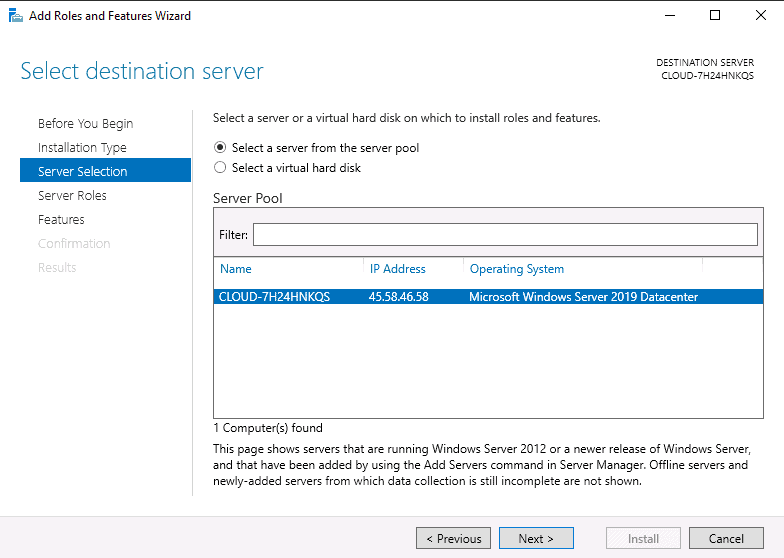
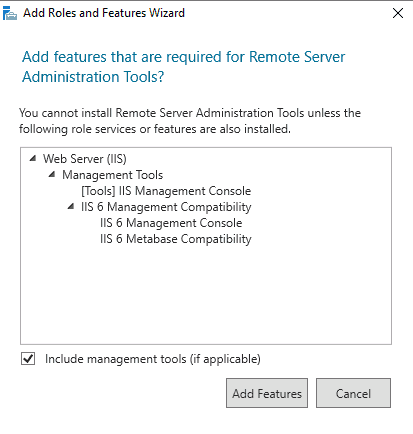
- On the window that says Select Server Roles, check the box that says Active Directory Domain Services. A pop-up box will appear. Click on Add Features, and then click Next to continue.
- Keep clicking the Next button until you get to the final screen. Unless you know what you are doing, you are better off leaving the default settings as they are.
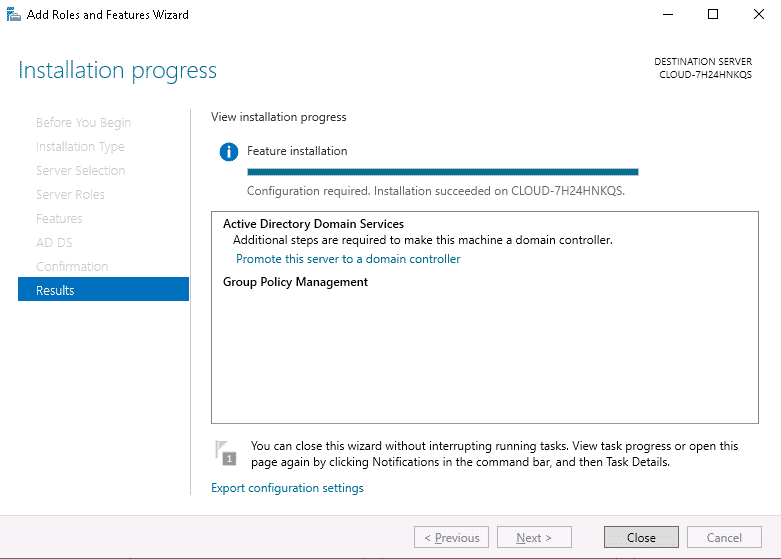
- Once you have got to the end of the wizard, click Install, and wait for the installation process to complete.
Once you have Active Directory Domain Services installed, you will then need to configure your installation, which includes changing default passwords, setting up OUs, domains, trees, and forests. As mentioned, a detailed explanation of setting up and configuring Active Directory is beyond the scope of this article. For detailed up-to-date instructions, you will need to consult the official documentation.
What is Azure Active Directory
Given that increasingly more organizations are shifting their business operations to the cloud, Microsoft has introduced Azure Active Directory (Azure AD), which is their cloud-based version of Windows AD, which can also sync with on-premise AD implementations. Azure AD is said to be the backbone of Office 365 and other Azure products; however, it can also be integrated with other cloud services and platforms. Some of the differences between Windows and Azure AD are as follows.
Communication: Azure AD uses a REST API, whereas Windows AD uses LDAP, as mentioned previously.
Authentication: Windows AD uses Kerberos and NTLM for authentication, whereas Azure AD uses its own built-in web-based authentication protocols.
Structure: Unlike Windows AD, which is organized by OUs, trees, forests, and domains, Azure AD uses a flat structure of users and groups.
Device Management: Unlike Windows AD, Azure AD can be managed via mobile devices. Azure AD does not rely on Group Policy Objects (GPOs) to determine which devices and servers are able to connect to the network.
If you are reading an article about Active Directory, it’s more than likely that you are not already using it. In which case, you might be better off starting with Azure AD as opposed to Windows AD. One of the main reasons why you might want to use Windows AD is if you are storing large amounts of valuable data and have a team of experienced IT professionals managing your cybersecurity program.
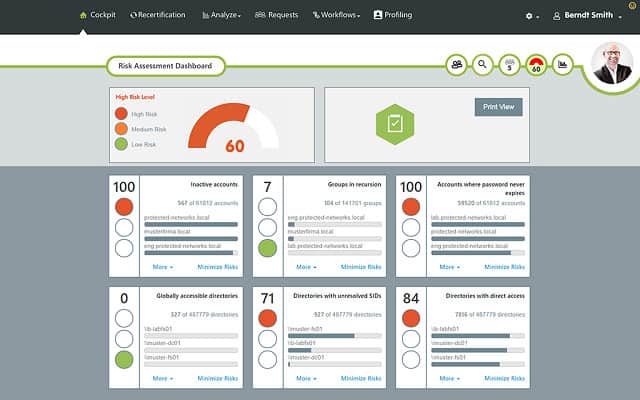
If you would like to see how Lepide Active Directory Auditor helps you to audit Active Directory and ensure AD security, schedule a demo with one of our engineers today or download free trial today.
Keep your Active Directory Secure with Lepide AD Auditor
By using the Active Directory® Domain Services (AD DS) server role, you can create a scalable, secure, and manageable infrastructure for user and resource management, and you can provide support for directory-enabled applications, such as Microsoft® Exchange Server.
In the following sections, learn more about AD DS, features in AD DS, and software and hardware considerations. For more information about planning, deploying, and operating the AD DS server role, see Active Directory Domain Services (http://go.microsoft.com/fwlink/?LinkID=48547).
What is a Directory?
A directory, in the most generic sense, is a comprehensive listing of objects. A phone book is a type of directory that stores information about people, businesses, and government organizations. Phone books typically record names, addresses, and phone numbers.
AD DS is similar to a phone book in several ways, and it is far more flexible. AD DS will store information about organizations, sites, computers, users, shares, and just about any other network object that you can imagine. Not all objects are as similar to
each other as those stored in the phone book, so AD DS includes the ability to record different types of information about different objects.
Lightweight Directory Access Protocol (LDAP)
AD DS reflects Microsoft’s trend toward relying on standard protocols. The Lightweight Directory Access Protocol (LDAP) is a product of the
IETF (Internet Engineering Task Force). It defines how clients and servers exchange information about a directory. LDAP version 2 and version 3 are used in AD DS .
Distinguished Names
It is very important to understand the structure of
distinguished names, as you will be referring to them often in the course of your job. My distinguished name is /O=Internet/DC=COM/DC=Microsoft/ DC=MSPress/CN=Users/CN=Tony Northrup. Consider the following figure, which shows how I fit into a sample AD DS
tree. The distinguished name I gave starts to make some sense—it identifies each container from the very top down to my specific object. Each container is separated by a slash and an identifier. For example, COM, Microsoft, and MSPress are each preceded by
/DC=. The DC stands for Domain Component, which identifies a DNS domain.
.gif)
Distinguished names describe the location of an object in a tree.
To simplify distinguished names, relative distinguished names can also be used. The relative distinguished name of the
previous example is CN=Tony Northrup, identifying the user name but not the context in which it resides. The context must be known already for the relative distinguished name to be an effective identifier.
User Principal Name
Distinguished names are great for computers but too cumbersome for people to remember. People have grown accustomed to e-mail addresses, so AD DS provides these addresses as a shortcut to the full object name. In Figure 11-9, Tony Northrup is a user of
the mspress.microsoft.com domain. An administrator could create a user principal name within the microsoft.com domain to allow simpler access to my user account and hold a place for my e-mail address, like northrup@microsoft.com.
Users will rely on their user principal name to log onto their computers. In other words, user principal names will replace the user names used in older Windows networks. Obviously, this helps the users by saving them the trouble of typing their distinguished
names. However, it also benefits users because the user principal name will stay the same even if administrators move or rename the underlying user account.
What is the AD DS server role?
AD DS provides a distributed database that stores and manages information about network resources and application-specific data from directory-enabled applications. Administrators can use AD DS to organize elements of a network, such as users, computers,
and other devices, into a hierarchical containment structure. The hierarchical containment structure includes the AD DS forest, domains
in the forest, and organizational units (OUs) in each domain. A server that is running AD DS is called a
domain controller.
Organizing network elements into a hierarchical containment structure provides the following benefits:
- The forest acts as a security boundary for an organization and defines the scope of authority for administrators. By default, a forest contains a single domain, which is known as the forest root domain.
- Additional domains can be created in the forest to provide partitioning of AD DS data, which enables organizations to replicate
data only where it is needed. This makes it possible for AD DS to scale globally over a network that has limited available bandwidth. An AD DS domain also supports a number of other core functions that are related to administration, including network-wide
user identity, authentication, and trust relationships. - OUs simplify the delegation of authority to facilitate the management of large numbers of objects. Through delegation, owners can transfer full or limited authority over objects to other users or
groups. Delegation is important because it helps to distribute the management of large numbers of objects to a number of people who are trusted to perform management tasks.
Features in AD DS
Security is integrated with AD DS through logon authentication and access control to resources in the directory. With a single network logon, administrators can manage directory data and organization throughout their network. Authorized network users can
also use a single network logon to access resources anywhere in the network. Policy-based administration eases the management of even the most complex network.
Additional AD DS features include the following:
- A set of rules, the schema, that defines the classes of objects and attributes that are contained in the directory, the constraints and limits on instances of these objects, and the format of their names.
- A global catalog that contains information about every object in the directory. Users and administrators can use the global catalog to find directory information, regardless of which domain in the directory actually contains the data.
- A query and index mechanism, so that objects and their properties can be published and found by network users or applications.
- A replication service that distributes directory data across a network. All writable domain controllers in a domain participate in replication and contain a complete copy of all directory information for their domain. Any change to directory
data is replicated to all domain controllers in the domain. - Operations master roles (also known as flexible single master operations or
FSMO). Domain controllers that hold operations master roles are designated to perform specific tasks to ensure consistency and eliminate conflicting entries in the directory.
Identity Management for UNIX
Identity Management for UNIX is a role service of AD DS that can be installed only on domain controllers. Two Identity Management for UNIX technologies, Server for NIS and Password Synchronization, make it easier to integrate computers running Microsoft
Windows® into your existing UNIX enterprise. AD DS administrators can use Server for NIS to manage Network Information Service (NIS) domains. Password Synchronization automatically synchronizes passwords between Windows and UNIX operating systems.
New AD DS features in Windows Server 2008 R2
| Feature | Description |
|---|---|
|
Active Directory Administrative Center |
Active Directory Administrative Center provides users and network administrators with an improved data management experience and a rich graphical user interface (GUI) to perform common Active Directory object management tasks. Built on Windows PowerShell™ |
|
Active Directory module for Windows PowerShell |
The Active Directory module for Windows PowerShell is a command-line interface that administrators can use to configure and diagnose all instances of Active Directory Domain Services (AD DS) and Active Directory Lightweight Directory Services (AD LDS) in This feature includes a set of Windows PowerShell cmdlets and a provider. The provider exposes the Active Directory database through a hierarchical navigation system, which is very similar to the file system. As with drives in a file system (C:, D:), you |
|
Active Directory Recycle Bin |
Active Directory Recycle Bin minimizes directory service downtime by improving the ability to preserve and restore accidentally deleted Active Directory objects without having to restore Active Directory data from backups, restart AD DS, or restart domain Active Directory Recycle Bin requires the Windows Server 2008 R2 |
|
Active Directory Web Services (ADWS) |
ADWS is a Windows service that provides a Web service interface to AD DS and AD LDS directory service instances and to Active Directory snapshots |
|
Authentication Mechanism Assurance |
Authentication Mechanism Assurance packages information about the type of logon method (smart card or user name/password) that is used to authenticate domain users inside each user’s Kerberos Authentication Mechanism Assurance requires the Windows Server 2008 R2 |
|
Offline domain join |
An offline domain join is a new process that computers running Windows® 7 or Windows Server 2008 R2 can use to join a domain. The offline domain join process can complete the domain join operation without network connectivity. |
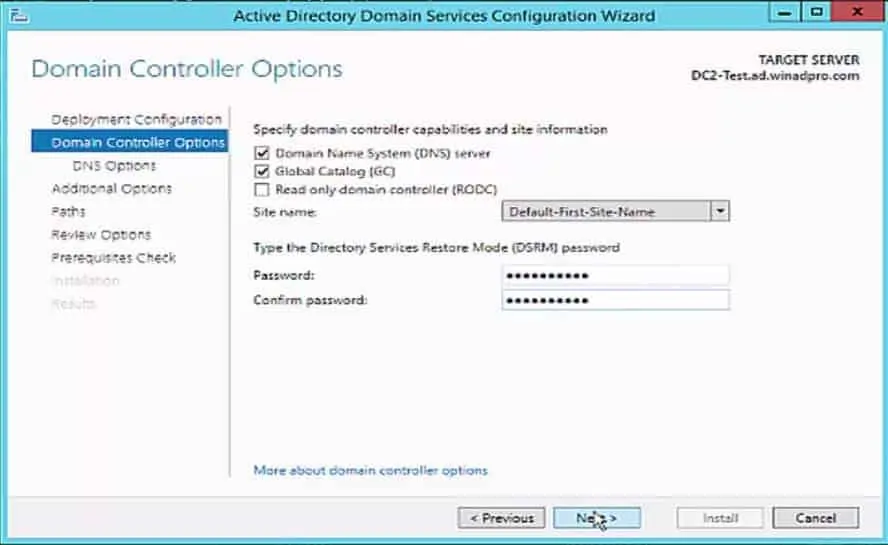
Installing the AD DS server role
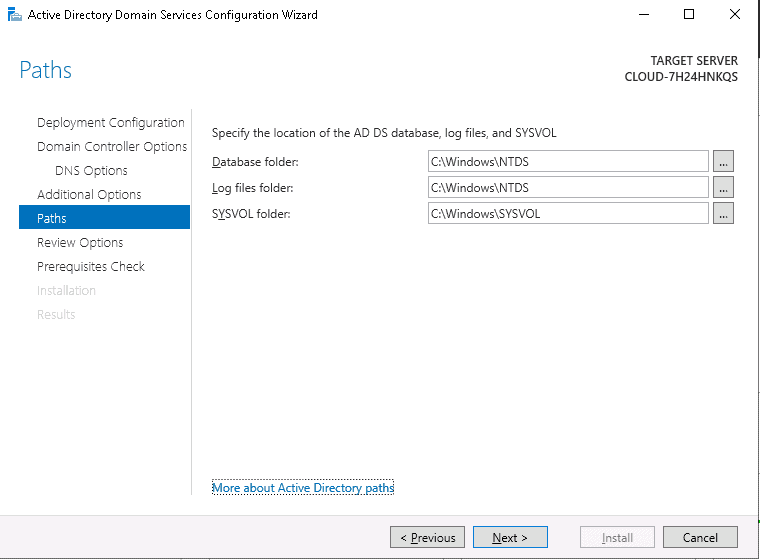
After you finish installing the operating system, you can use Initial Configuration Tasks or Server Manager to install server roles. To install the AD DS server role, click
Add roles to start the Add Roles Wizard, and then click
Active Directory Domain Services. Follow the steps in the Add Roles Wizard to install the files for the AD DS server role. After you complete the Add Roles Wizard, click the link to start the Active Directory Domain Services Installation Wizard.
Follow the steps in the Active Directory Domain Services Installation Wizard to complete the installation and configuration of your domain controller. Most wizard pages have a Help link for more information about the settings that you can configure.
To automate domain controller installations, you can use an answer file or you can specify unattended installation parameters at the command line. For more information about installing AD DS, see the AD DS Installation and Removal Step-by-Step Guide (http://go.microsoft.com/fwlink/?LinkId=110897).
Managing the AD DS server role
You can manage server roles with Microsoft Management Console (MMC) snap-ins. To manage a domain controller (that is, a server
that is running AD DS), click Start, click Control Panel, click
Administrative Tools, and then double-click the appropriate snap-in:
- To manage Active Directory objects by using the newest GUI tool, with improved options for viewing and managing
Active Directory data, click Active Directory Administrative Center. - To manage Active Directory objects by using a predefined set of Windows PowerShell cmdlets and a provider, click
Active Directory Module for Windows PowerShell. - To manage user and computer accounts, click Active Directory Users and Computers (dsa.msc).
- To manage Active Directory trusts, functional levels, and forest-wide operations master roles, click
Active Directory Domains and Trusts (domain.msc). - To manage Active Directory sites and site links, click
Active Directory Sites and Services (dssite.msc).
As an alternative, you can double-click the appropriate snap-in on the
Active Directory Domain Services page in Server Manager.
Security
AD DS plays an important role in the future of Windows networking. Administrators must be able to protect their directory from attackers and users, while delegating tasks to other administrators where necessary. This is all possible using the AD DS security
model, which associates an access control list (ACL) with each container, object, and object attribute within the directory. The following figure shows
a step from the Delegation Of Control wizard, a helpful utility for assigning permissions to AD DS objects.
.gif)
The Delegation Of Control wizard makes it simple to assign permissions to objects.
This high level of control allows an administrator to grant individual users and groups varying levels of permissions for objects and their properties. Administrators can even add attributes to objects and hide those attributes from certain groups of users.
For example, the administrator could set the ACLs such that only managers can view the home phone numbers of other users. Nonmanagers would not even know that the attribute existed.
A concept new to Windows Server is delegated administration. This allows administrators to assign administrative tasks to other users, while not granting those users more power than necessary. Delegated administration can be assigned over specific
objects or contiguous subtrees of a directory. This is a much more effective method of giving authority over the networks; rather than granting someone the all powerful Domain Administrator permissions, he or she can be given permissions for just those computers
and users within a specific subtree. AD DS supports inheritance, so any new objects inherit the ACL of their container.
Try to forget what you’ve learned about Windows NT domain trusts. The term
trusts is still used, but trusts have very different functionality. There is no distinction between one-way and two-way trusts because all AD DS trusts are bidirectional. Further, all trusts are transitive. So, if Domain A trusts Domain B, and Domain B
trusts Domain C, then there is an automatic implicit trust between Domain A and Domain C. This new functionality is shown in the following figure.
.gif)
Windows Server trusts are bidirectional and transitive.
Another AD DS security feature is auditing. Just as you can audit NTFS partitions, objects and containers within AD DS can be audited. This is a useful way to determine who is attempting to access objects, and whether or not they succeed.
Use of DNS (Domain Name System)
Domain Name System, or DNS, is necessary to any Internet-connected organization. DNS provides name resolution between common names, such as mspress.microsoft.com, and the raw IP addresses that network layer components use to communicate. AD DS makes extensive
use of DNS technology and relies on DNS to locate objects within AD DS. This is a substantial change from previous Windows operating systems that require NetBIOS
names to be resolved to IP addresses, and to rely on WINS
or another NetBIOS name resolution technique.
AD DS works best when used with Windows Server–based DNS servers. Microsoft has made it easy for administrators to transition to Windows Server–based DNS servers by providing migration wizards that walk the administrator through the process. Other DNS servers
can be used, but administrators will need to spend more time managing the DNS databases. If you decide not to use Windows Server–based DNS servers, you should make sure your DNS servers comply with the new DNS dynamic update protocol. AD DS servers rely on
dynamic update to update their pointer records, and clients rely on these records to locate domain controllers. If dynamic update is not supported, you will have to update the databases manually.
Note: DNS dynamic update protocol is defined in RFC 2136.
Windows domains and Internet domains are now completely compatible. A domain name such as mspress.microsoft.com will identify AD DS domain controllers responsible for the domain, so any client with DNS access can locate a domain controller. AD DS clients
can use DNS resolution to locate any number of services because AD DS servers publish a list of addresses to DNS using the new features of dynamic update. These addresses identify both the domain and the service being provided and are published via Service
Resource Records (SRV RRs). SRV RRs follow this format:
service.protocol.domain
AD DS servers provide the LDAP service for object location, and LDAP relies on TCP as the underlying transport-layer protocol. Therefore,
a client searching for an AD DS server within the mspress.microsoft.com domain would look up the DNS record for ldap.tcp.mspress.microsoft.com.
Global Catalog
AD DS provides a global catalog (GC). No, this does not mean that you can find any piece of information on the planet—but it is still
very significant. AD DS provides a single source to locate any object within an organization’s network.
The global catalog is a service within Windows Server that allows users to find any objects to which they have been granted access. This functionality far surpasses that of the Find Computer application included in previous versions of Windows, because users
can search for any object within AD DS: servers, printers, users, and applications. For example, the following figure shows how a user can search for all color printers in his or her building that have the capability to print double-sided documents.
.gif)
The global catalog helps users find network resources.
This feature is especially important because of the complexity of LDAP names. Older versions of Windows relied on 15-character NetBIOS computer names, which users could often remember. Few people would be able to recall LDAP names, such as the following:
/O=Internet/DC=COM/DC=Microsoft /DC=MSPress/CN=Computers/CN=Server1.
Because users can easily search for objects, remembering names is much less important.
The GC is an index stored on AD DS servers. It contains the names of all objects in the AD DS server, regardless of how the server has been partitioned. The GC also contains a handful of searchable attributes for each object. For example, the GC would store
the distinguished names, first names, and last names of all users—allowing someone to search for anyone named Tony and find the distinguished name of the user. The global catalog is a subset of AD DS, and stores only those attributes that users tend to search
on. Useful defaults are provided by Microsoft, and administrators can specify other attributes to be searchable by using the AD DS Schema, described later in this chapter.
Not All Indexes Are Created Equal!
If you have done any database administration, you already know that some types of information are more useful to index than other types. Naturally, you should index attributes that will be searched for often, but there are other factors involved. Indexes
take up space, so it is not efficient to index everything. Indexes also slow down updates and inserts—if an indexed attribute is modified, the index must be modified as well. Indexing works better when the data being stored varies from user to user. Therefore,
never index true or false attributes or any attribute with less than five possible values. Names are an excellent attribute to index since they are almost unique for each user. Finally, don’t index attributes that aren’t usually filled in. If few users enter
a value for their middle name, the indexing of that attribute is a waste.
As new objects are created in AD DS, they are assigned a unique number called a GUID (globally unique identifier). The GUID is useful because
it stays the same for any given object, regardless of where the object is moved. The GUID is a 128-bit identifier, which isn’t particularly meaningful to users, but applications that reference objects in AD DS can record the GUIDs for objects and use the global
catalog to find them even after they’ve moved.
Replication
Administrators who implement AD DS will quickly discover that their network relies heavily on its services. This reliance means that AD DS must be available on multiple servers—so that if a single server fails, clients can contact a server with duplicate
services and information. Unlike the Windows NT domain databases used with previous versions of Windows NT, updates to the database can be sent to
any of the AD DS servers. While this complicates the replication process, it eliminates the possibility that the failure of a single domain controller would stop updates to the databases. It also reduces the high load placed on Windows NT 4.0 primary
domain controllers.
AD DS includes a replication component that makes this a simple task for administrators. Simply adding domain controllers to an AD DS is sufficient to begin the replication process.
One of the most complex parts of making redundant servers work properly is replicating the information and ensuring that all servers have the most up-to-date content. AD DS uses
multimaster replication, which is another way of stating that updates can occur on any AD DS server. Each server keeps track of which updates it has received from which servers, and can intelligently request only necessary updates in case of a failure.
How AD DS Replication Works
Each update is assigned its own 64-bit unique sequence number (USN) from a counter that is incremented whenever a change is made. These updates
are system-specific, so every AD DS server maintains a separate counter.
When a server replicates an update to other AD DS domain controllers, it sends the USN along with the change. Each server maintains an internal list of replication partners and the highest USN received from them. The server receiving the update requests
only those changes with USNs higher than previously received. This method has the added benefit of stopping updates from propagating endlessly between multiple AD DS domain controllers.
One problem inherent in any multimaster replication scheme is that updates to a single object can occur in multiple places at the same time. For example, if an administrator in Boston changes a user’s name from «Curt» to ‘»Kurt» and an administrator in Chicago
simultaneously changes that same user’s name from «Curt» to «Kirk,» a replication collision will occur. There are two problems to deal with when a collision occurs: detecting the collision and resolving the collision.
AD DS stores property version numbers to allow replication collision detection. These numbers are specific to each property of every object within AD DS and are updated every time the property is modified. These numbers are propagated through AD DS
along with the change, so a server that receives two different updates to the same property with the same property version number can conclude that a replication collision has occurred.
AD DS domain controllers resolve collisions by applying the update with the later timestamp. The timestamp is created by the server that initiated the change, so it is very important to keep system time synchronized between servers.
Note: Use the built-in distributed time synchronization service to keep all servers working together!
Partitioning
Large networks can contain hundreds of thousands of objects. Windows NT required multiple domains to allow that many objects to be manageable. Administrators often divided users and resources into separate domains and created a trust between the domains.
The structure of the databases simply did not allow them to grow to hundreds of thousands of objects. These size limitations are less a factor in AD DS domains, thankfully. However, supporting a very large AD DS could be an incredible burden to any single
domain controller.
Active Directories can be partitioned to lessen this load. Partitioning allows different domain controllers to manage different sections of the database, reducing the load on any individual server. The clients can use resources located within different AD DS
partitions transparently. Therefore, administrators can manage massive AD DS domains without requiring domain controllers to handle the entire database.
Objects
Many people are initially confused by the relationship between object
classes,
attributes, and the objects themselves. Objects are created based on an object class. Attributes describe an object class. When an object
is created, it inherits all the attributes of its object class. Here’s where it gets tricky:
object classes and attributes are also objects in AD DS. Fortunately, most user interfaces hide this fact.
An object can be either a reference to something concrete or the actual useful information itself. For example, every bit of information about a user account is stored within AD DS. However, only a reference to a disk volume is stored in AD CS. While the
reference is not useful by itself, it is used to locate the volume on the file server. When creating new object classes, carefully consider whether the object will store a reference to something external or whether all necessary information will be contained
in the object’s attributes. While AD DS is extremely convenient, it should not be used to store large amounts of information, constantly changing information, or rarely used information.
Anytime you add a user or a computer to AD DS, you are creating an object. Creating an object is often referred to as
publishing, because it kicks off a process of replicating the new information across all AD DS domain controllers in the domain.
Schema: Attributes and Object Classes
A schema is a set of attributes used to describe a particular object class in AD DS. Different types of information need to be tracked for
different object classes, and that’s why the schema is so important. For example, the Users object class needs attributes for a first name, last name, phone number, e-mail address, and mailing address. The Printer object class must have many different attributes—users
will want to know how fast a printer is and whether it can duplex or print in color. These attributes can be viewed and edited using the AD DS Schema MMC snap-in, as shown in the following figure.
Experienced programmers and system administrators can manage the AD DS schema, but the AD DS Schema snap-in is not installed by default. In addition, the Schmmgmt.dll file (regsvr32 schmmgmt.dll) must be registered from an
elevated command prompt before the snap-in can be installed. The AD DS Schema does not have an icon within the Start menu; you must launch the MMC interface and add the snap-in named AD DS Schema.
.gif)
The AD DS Schema allows classes and attributes to be modified.
By default, object classes come with a logical set of attributes that will fit most organization’s needs. However, many organizations will need to track additional information about particular object classes. For example, if employees are assigned a badge
number, it is useful to track that information in the object class. The first step is to create an attribute called BadgeID, as shown in the following figure. The second step is to make the new attribute optional for the Users class.
.gif)
Attributes can be added with the AD DS Schema snap-in.
The schema is stored within AD DS just like other objects. Therefore, the schema inherits the ability to be automatically replicated throughout a domain. It also benefits from the security features of AD DS, and allows administrators to delegate authority
over the schema to different users and groups. By changing the ACLs on a schema object, an administrator can allow any user to add or modify attributes for an object class. The example in the following figure shows that the group East Coast Administrators
has been granted full control over the schema.
.gif)
Modifying the schema can be delegated to groups and users.
New attributes have several properties that must be set. The user creating a new attribute must define a name for the attribute (such as Badge ID #), the type of data to be stored (such as a string or a number), and the range limits (such as string length).
A unique Object Identifier (OID) must also be provided. New attributes can be indexed, which adds the attributes to the global catalog. Indexes should be created for attributes that users will search with. In this example, if security needs to look up user
accounts by the Badge ID number, this attribute should be indexed. For a search to occur on a nonindexed attribute, a slow and processor-intensive walk of the directory tree must be done.
Where Do Object Identifiers Come From?
The only way to ensure Object Identifiers are globally unique is to have a central agency that assigns
OIDs. This is already common practice on the Internet; the InterNIC assigns domain names and the Internet Assigned Numbers Authority (IANA) assigns IP subnets. Object Identifiers are assigned by a National Registration Authority, or NRA. NRAs vary from
country to country. In the United States, the American National Standards Institute (ANSI) provides NRA services. For a modest fee,
ANSI can supply your organization with a root OID. Any objects created by your organization will have this root OID as the prefix, ensuring that Object Identifiers are globally unique.
A list of NRAs can be found at the International Standards Organization’s Web site, at
http://www.iso.ch.
The schema is cached by AD DS domain controllers for performance reasons. It will take up to five minutes for the cache to be updated after you change the schema. So, wait a few minutes before you try to create objects based on your new object classes and
attributes. If you must reload the cache immediately, add the attribute schemaUpdateNow to the root object (the object without a distinguished name), and set the value to 1.
Extending the schema of AD DS is a powerful capability. However, most administrators will never need to use anything but the classes and attributes .Microsoft has provided by default.
ADSI (Active Directory Service Interface)
ADSI (Active Directory Service Interface) allows applications to interact with any directory service without being forced to know the internal
details of the underlying protocols. Administrators can write programs and scripts that make use of ADSI to read or write to legacy Windows NT 4.0 directories, NetWare NDS directories, NetWare 3 binderies, and LDAP directories such as AD DS. Developers can
even create applications that make use of directories at the customer’s site, without previous knowledge of the type of directory being used.
For example, the following Microsoft Visual Basic code uses ADSI to display a list of users in the debug window:
Set ou = GetObject(«ldap://dcserver/OU=Sales,DC=ArcadiaBay,DC=COM»)
For Each obj In ou
Debug.Print obj.Name
Next
As you can see, gathering a list of users is much simpler than in previous Windows operating systems. ADSI makes use of the Component Object Model (COM),
so almost any Windows development environment can immediately make use of the interface. Developers will be interested to know that they can access Active Directory through the LDAP C API
and through
MAPI, though ADSI is the preferred interface.
Note: The LDAP C API is defined in RFC 1823.
Active Directory Wiki Pages
- Active Directory Replication over Firewalls
- Design Considerations for Delegation of Administration in Active Directory
What is Active Directory and how does it work?
Active Directory (AD) is Microsoft’s proprietary directory service. It runs on Windows Server and enables administrators to manage permissions and access to network resources.
Active Directory stores data as objects. An object is a single element, such as a user, group, application or device such as a printer. Objects are normally defined as either resources, such as printers or computers, or security principals, such as users or groups.
Active Directory categorizes directory objects by name and attributes. For example, the name of a user might include the name string, along with information associated with the user, such as passwords and Secure Shell keys.
The main service in Active Directory is Domain Services (AD DS), which stores directory information and handles the interaction of the user with the domain. AD DS verifies access when a user signs into a device or attempts to connect to a server over a network. AD DS controls which users have access to each resource, as well as group policies. For example, an administrator typically has a different level of access to data than an end user.
Other Microsoft and Windows operating system (OS) products, such as Exchange Server and SharePoint Server, rely on AD DS to provide resource access. The server that hosts AD DS is the domain controller.
Active Directory services
Several different services comprise Active Directory. The main service is Domain Services, but Active Directory also includes Lightweight Directory Services (AD LDS), Lightweight Directory Access Protocol (LDAP), Certificate Services, or AD CS, Federation Services (AD FS) and Rights Management Services (AD RMS). Each of these other services expands the product’s directory management capabilities.
- Lightweight Directory Services has the same codebase as AD DS, sharing similar functionalities, such as the application program interface. AD LDS, however, can run in multiple instances on one server and holds directory data in a data store using Lightweight Directory Access Protocol.
- Lightweight Directory Access Protocol is an application protocol used to access and maintain directory services over a network. LDAP stores objects, such as usernames and passwords, in directory services, such as Active Directory, and shares that object data across the network.
- Certificate Services generates, manages and shares certificates. A certificate uses encryption to enable a user to exchange information over the internet securely with a public key.
- Active Directory Federation Services authenticates user access to multiple applications — even on different networks — using single sign-on (SSO). As the name indicates, SSO only requires the user to sign on once, rather than use multiple dedicated authentication keys for each service.
- Rights Management Services control information rights and management. AD RMS encrypts content, such as email or Microsoft Word documents, on a server to limit access.
Major features in Active Directory Domain Services
Active Directory Domain Services uses a tiered layout structure consisting of domains, trees and forests to coordinate networked elements.
Domains are the smallest of the main tiers, while forests are the largest. Different objects, such as users and devices, that share the same database will be on the same domain. A tree is one or more domains grouped together with hierarchical trust relationships. A forest is a group of multiple trees. Forests provide security boundaries, while domains — which share a common database — can be managed for settings such as authentication and encryption.
- A domain is a group of objects, such as users or devices, that share the same AD database. Domains have a domain name system
- A tree is one or more domains grouped together. The tree structure uses a contiguous namespace to gather the collection of domains in a logical hierarchy. Trees can be viewed as trust relationships where a secure connection, or trust, is shared between two domains. Multiple domains can be trusted where one domain can trust a second, and the second domain can trust a third. Because of the hierarchical nature of this setup, the first domain can implicitly trust the third domain without needing explicit trust.
- A forest is a group of multiple trees. A forest consists of shared catalogs, directory schemas, application information and domain configurations. The schema defines an object’s class and attributes in a forest. In addition, global catalog servers provide a listing of all the objects in a forest. According to Microsoft, the forest is Active Directory’s security boundary.
- Organizational Units (OUs) organize users, groups and devices. Each domain can contain its own OU. However, OUs cannot have separate namespaces, as each user or object in a domain must be unique. For example, a user account with the same username cannot be created.
- Containers are similar to OUs, but Group Policy Objects cannot be applied or linked to container objects.
Trusting terminology
Active Directory relies on trusts to moderate the access rights of resources between domains. There are several different types of trusts:
- A one-way trust is when a first domain allows access privileges to users on a second domain. However, the second domain does not allow access to users on the first domain.
- A two-way trust is when there are two domains and each domain enables access to users of the other domain.
- A trusted domain is a single domain that enables user access to another domain, which is called the trusting domain.
- A transitive trust can extend beyond two domains and allow access to other trusted domains within a forest.
- An intransitive trust is a one-way trust that is limited to two domains.
- An explicit trust is a one-way, nontransitive trust that is created by a network admin.
- A cross-link trust is a type of explicit trust. Cross-link trusts take place between domains within 1) the same tree, with no child-parent relationship between the two domains, or 2) different trees.
- A forest trust applies to domains within the entire forest and can be one-way, two-way or transitive.
- A shortcut joins two domains that belong to separate trees. Shortcuts can be one-way, two-way or transitive.
- A realm is a trust that is transitive, intransitive, one-way or two-way.
- An external trust is a trust that links domains across separate forests or domains that are non-AD. External trusts can be nontransitive, one-way or two-way.
- A private access management (PAM) trust is a one-way trust that is created by Microsoft Identity Manager between a production forest and a bastion forest.
History and development of Active Directory
Microsoft offered a preview of Active Directory in 1999 and released it a year later with Windows 2000 Server. Microsoft continued to develop new features with each successive Windows Server release.
Windows Server 2003 included a notable update to add forests and the ability to edit and change the position of domains within forests. Domains on Windows Server 2000 could not support newer AD updates running in Server 2003.
Windows Server 2008 introduced AD FS. Additionally, Microsoft rebranded the directory for domain management as AD DS, and AD became an umbrella term for the directory-based services it supported.
Windows Server 2016 updated AD DS to improve AD security and migrate AD environments to cloud or hybrid cloud environments. Security updates included the addition of PAM.
PAM monitored access to an object, the type of access granted and what actions the user took. PAM added bastion AD forests to provide an additional secure and isolated forest environment. Windows Server 2016 ended support for devices on Windows Server 2003.
In December 2016, Microsoft released Azure AD Connect to join an on-premises Active Directory system with Azure Active Directory (Azure AD) to enable SSO for Microsoft’s cloud services, such as Office 365. Azure AD Connect works with systems running Windows Server 2008, Windows Server 2012, Windows Server 2016 and Windows Server 2019.
Domains vs. workgroups
The workgroup is Microsoft’s term for Windows machines connected over a peer-to-peer network. Workgroups are another unit of organization for Windows computers in networks. Workgroups allow these machines to share files, internet access, printers and other resources over the network. Peer-to-peer networking removes the need for a server for authentication. There are several differences between domains and workgroups:
- Domains, unlike workgroups, can host computers from different local networks.
- Domains can be used to host many more computers than workgroups. Domains can include thousands of computers, unlike workgroups, which typically have an upper limit close to 20.
- In domains, at least one server is a computer, which is used to control permissions and security features for every computer within the domain. In workgroups, there is no server and computers are all peers.
- Domain users typically require security identifiers such as logins and passwords, unlike workgroups.
Main competitors to Active Directory
Other directory services on the market that provide similar functionality to AD include Red Hat Directory Server, Apache Directory and OpenLDAP.
Red Hat Directory Server manages user access to multiple systems in Unix environments. Similar to AD, Red Hat Directory Server includes user ID and certificate-based authentication to restrict access to data in the directory.
Apache Directory is an open source project that runs on Java and operates on any LDAP server, including systems on Windows, macOS and Linux. Apache Directory includes a schema browser and an LDAP editor and browser. Apache Directory supports Eclipse plugins.
OpenLDAP is a Windows-based open source LDAP directory. OpenLDAP enables users to browse, search and edit objects in an LDAP server. OpenLDAP features include copying, moving and deleting trees in the directory, as well as enabling schema browsing, password management and LDAP SSL (Secure Sockets Layer) support.
Read this overview to learn about Active Directory basics.
Learn what techniques can be used to troubleshoot common issues in Active Directory, and tips on replication troubleshooting.
This was last updated in June 2021
Continue Reading About active directory
- Make the right move with the Active Directory Migration Tool
- Automate Active Directory jobs with PowerShell scripts
- Debug an Active Directory domain join failure on Windows Server
- How to use Azure Active Directory differently than classic AD
- Organize Active Directory with these strategies
Dig Deeper on IT operations and infrastructure management
-
Avoid clock skew issues with external time source setup
By: Brien Posey
-
Active Directory tree
By: Rahul Awati
-
Active Directory Domain Services (AD DS)
By: Ben Lutkevich
-
Active Directory forest (AD forest)
By: Brien Posey
Directory services are becoming a key part in managing IT infrastructure. Microsoft’s service, Active Directory, is one of the most well-known directory services in the world. In this article, we will cover the basics and explain exactly what Active Directory is and how to use it.
UPDATED: January 18, 2023
As the complexity of networking resources has grown, directory services have become ever more important for managing IT infrastructure. There is no directory service with a bigger name than Active Directory. Microsoft’s directory service has been established as a staple tool amongst network administrators. In this Active Directory tutorial we’re going to look at what Active Directory is, how to use it, and Active Directory tools like SolarWinds Access Rights Manager and ManageEngine AD360. Topics to learn include:
- What is Active Directory?
- What does Active Directory do?
- How to Set Up Active Directory
- How to Use Active Directory: Setting Up a Domain Controller, Creating Directory Users
- Active Directory Events to Monitor
- Trust Relationships (and Trust Types)
- An Overview of Active Directory Forests and Trees
- Active Directory Reporting (with SolarWinds Access Rights Manager)
- How to Find the Source of Account Lockouts in Active Directory
What is Active Directory?
Active Directory is a directory service or container which stores data objects on your local network environment. The service records data on users, devices, applications, groups, and devices in a hierarchical structure.
The structure of the data makes it possible to find the details of resources connected to the network from one location. In essence, Active Directory acts like a phonebook for your network so you can look up and manage devices easily.
What does Active Directory do?
There are many reasons why enterprises use directory services like Active Directory. The main reason is convenience. Active Directory enables users to log on to and manage a variety of resources from one location. Login credentials are unified so that it is easier to manage multiple devices without having to enter account details to access each individual machine.
How to Setup Active Directory (with RSAT)
To begin you will need to first make sure that you have Windows Professional or Windows Enterprise installed otherwise you won’t be able to install Remote Server Administration Tools. Then do the following:
For Windows 10 Version 1809 and Windows 11:
- Right-click on the Start button and go to Settings > Apps > Manage optional features > Add feature.
- Now select RSAT: Active Directory Domain Services and Lightweight Directory Tools.
- Finally, select Install then go to Start > Windows Administrative Tools to access Active Directory once the installation is complete.
For Windows 8 (And Windows 10 Version 1803)
- Download and install the correct version of Server Administrator Tools for your device: Windows 8, Windows 10.
- Next, right-click the Start button and select Control Panel > Programs > Programs and Features > Turn Windows features on or off.
- Slide down and click on the Remote Server Administration Tools option.
- Now click on Role Administration Tools.
- Click on AD DS and AD LDS Tools and verify AD DS Tools has been checked.
- Press Ok.
- Go to Start > Administrative Tools on the Start menu to access Active Directory.
How to use Active Directory: How to Setup a Domain Controller, Creating Directory Users
How to Setup A Domain Controller
One of the first things you need to do when using Active Directory is to set up a domain controller. A domain controller is a central computer that will respond to authentication requests and authenticate other computers throughout the network. The domain controller stores the login credentials of all other computers and printers.
All other computers connect to the domain controller so that the user can authenticate every device from one location. The advantage of this is that the administrator won’t have to manage dozens of login credentials.
The process of setting up a domain controller is relatively simple. Assign a static IP address to your Domain Controller and install Active Directory Domain Services or ADDS. Now follow these instructions:
- Open Server Manager and click Roles Summary > Add roles and features.
- Click Next.
- Select Remote Desktop Services installation if you’re deploying a domain controller in a virtual machine or select role-based or feature-based installation.
- Select a server from the server pool.
- Select Active Directory Domain Services from the list and click Next.
- Leave the Features checked by default and press Next.
- Click Restart the destination server automatically if required and click Install. Close the window once the installation is complete.
- Once the ADDS role has been installed a notification will display next to the Manage menu. Press Promote this server into a domain controller.
- Now click Add a new forest and enter a Root domain name. Press Next.
- Select the Domain functional level you desire and enter a password into the Type the Directory Services Restore Mode (DSRM password) section. Click Next.
- When the DNS Options page displays click Next again.
- Enter a domain in the NetBios Domain name box (preferably the same as the root domain name). Press Next.
- Select a folder to store your database and log files. Click Next.
- Press Install to finish. Your system will now reboot.
Add a Domain Controller to an Existing Domain in Windows Server 2016
The procedures for adding a domain controller to an existing domain in Active Directory are the same, no matter which operating system you have. However, these instructions were organized during an exercise on Windows Server 2016. It is always a good idea to have at least two domain controllers in your AD domain just in case one goes down.
The second Domain Controller is a separate computer from the one identified for your first Domain Controller. That second computer needs to be set up with Windows Server 2016. Get it fully patched and assign it an IP address before starting the AD setup on that machine. Then follow these steps:
- Open Server Manager, click on the Manage option on the menu ribbon and select Add Roles and Features.
- In the opening screen of the wizard, click on Next.
- In the Installation Type screen select the Role-based or feature-based installation radio button and click on Next.
- In Server Selection leave the only server in the list highlighted and press Next.
- In the Server Roles screen, Check the Active Directory Domain Services box. A dialogue box appears. Click on the Add Features button.
- Back in the main feature selection screen, click the Next button.
- This cycles through to the Features screen. Just click on the Next button. In the AD DS screen, click on the Next button.
- Finally, click the Install button. Once the installation process finishes, you will see a notice telling you that additional steps are required. Click on the link that says Promote this server to a domain controller. This brings up the Deployment Configuration screen.
- Leave the Add a domain controller to an existing domain radio button active. At the bottom of the list of options, you will see <no credentials provided>. Click on the Change button next to that.
- Enter the username and password of the Administrator account on the AD instance that you first set up. This username should be in the format <domain>Administrator. Click OK.
- On return from the login popup, you will see that the Domain field has been populated with the domain that you entered for the user account. Click on the Next button.
- Decide whether to make this a read-only domain controller (RODC). If so, check that box in the Options screen, if not, check both the DNS server and Global Catalogue boxes.
- Enter a DSRM password and confirm it. Click on the Next button. You will see a warning but just click on the Next button again.
- In Additional Options choose your original domain controller for the Replicate from: field. Click on Next.
- Leave all of the paths in their default settings and click on Next. In the Review Options screen, click Next.
- The system will perform a prerequisites check. If that completes satisfactorily, the Install button will become active. Click it.
- Wait for the installation to complete. The computer will reboot. Log in to the machine.
Go back to your original domain controller computer and open Active Directory Users and Computers and you will see that your new DC is listed there in the Domain Controllers folder.
Creating Active Directory Users
Users and computers are the two most basic objects that you will need to manage when using Active Directory. In this section, we’re going to look at how to create new user accounts. The process is relatively simple, and the easiest way to manage users is through the Active Directory Users and Computer or ADUC tool that comes with the Remote Server Administration Tools or RSAT pack. You can install ADUC by following the instructions listed below:
Install ADUC on Windows 10 Version 1809 and Higher or Windows 11:
- Right-click on the Start button and click Settings > Apps, then click Manage optional features > Add feature.
- Select RSAT: Active Directory Domain Services and Lightweight Directory Tools.
- Select Install and wait for the installation to complete.
- Go to Start > Windows Administrative Tools to access the feature.
Install ADUC on Windows 8 and Windows 10 Version 1803 or Lower:
- Download and install Remote Server Administrator Tools for your version of Windows. You can do so from one of these links here:
Remote Server Administrator Tools for Windows 10, Remote Server Administrator Tools for Windows 8, or Remote Server Administrator Tools for Windows 8.1.
- Right-click on Start > Control Panel > Programs > Programs and Features > Turn Windows features on or off.
- Scroll down and select Remote Server Administration Tools.
- Expand Role Administrator Tools > AD DS and AD LDS Tools.
- Check AD DS Tools and press Ok.
- Go to Start > Administrative Tools and select Active Directory Users and Computers.
How to Create New Users with ADUC
- Open the Server Manager, go to the Tools menu and select Active Directory Users and Computers.
- Expand the domain and click Users.
- Right-click on the right pane and press New > User.
- When the New Object-User box displays enter a First name, Last name, User logon name, and click Next.
- Enter a password and press Next.
- Click Finish.
- The new user account can be found in the Users section of ADUC.
Active Directory Events to Monitor
Like all forms of infrastructure, Active Directory needs to be monitored to stay protected. Monitoring the directory service is essential for preventing cyber-attacks and delivering the best end-user experience to your users.
Below we’re going to list some of the most important network events that you should look out for. If you see any of these events then you should investigate further ASAP to make sure that your service hasn’t been compromised.
| Current Windows Event ID | Legacy Windows Event ID | Description |
|---|---|---|
| 4618 | N/A | A security event pattern has been recognized. |
| 4649 | N/A | A replay attack was detected (potentially a false positive). |
| 4719 | 612 | A system audit policy was changed. |
| 4765 | N/A | SID History added to an account. |
| 4766 | N/A | The attempt failed to add SID History to account. |
| 4794 | N/A | Attempt to launch Directory Services Restore Mode. |
| 4897 | 801 | Role separation enabled. |
| 4964 | N/A | Special groups have been assigned a new logon. |
| 5124 | N/A | Security updated on OCSP Responder Service. |
| N/A | 550 | Potential DoS attack. |
| 1102 | 517 | Audit log was cleared. |
An Overview of Active Directory Forests and Trees
Forest and trees are two terms you will hear a lot when delving into Active Directory. These terms refer to the logical structure of Active Directory. Briefly, a tree is an entity with a single domain or group of objects that is followed by child domains. A forest is a group of domains put together. When multiple trees are grouped together they become a forest.
Trees in the forest connect to each other through a trust relationship, which enables different domains to share information. All domains will trust each other automatically so you can access them with the same account info you used on the root domain.
Each forest uses one unified database. Logically, the forest sits at the highest level of the hierarchy and the tree is located at the bottom. One of the challenges that network administrators have when working with Active Directory is managing forests and keeping the directory secure.
For example, a network administrator will be tasked with choosing between a single forest design or multi-forest design. The single-forest design is simple, low-cost and easy to manage with only one forest comprising the entire network. In contrast, a multi-forest design divides the network into different forests which is good for security but makes administration more complicated.
Trust Relationships (and Trust Types)
As mentioned above, trusts are used to facilitate communication between domains. Trusts enable authentication and access to resources between two entities. Trusts can be one-way or two-way in nature. Within a trust, the two domains are divided into a trusting domain and a trusted domain.
In a one-way trust, the trusting domain accesses the authentication details of the trusted domain so that the user can access resources from the other domain. In a two-way trust, both domains will accept the other’s authentication details. All domains within a forest trust each other automatically, but you can also set up trusts between domains in different forests to transfer information.
You can create trusts through the New Trusts Wizard. The New Trust Wizard is a configuration wizard that allows you to create new trust relationships. Here you can view the Domain Name, Trust Type, and Transitive status of existing trusts and select the type of trust you want to create.
Trust Types
There is a range of trust types in Active Directory. We’ve listed these in the table below:
| Trust Type | Transit Type | Direction | Default? | Description |
|---|---|---|---|---|
| Parent and child | Transitive | Two-way | Yes | A parent and child trust is established when a child domain is added to a domain tree. |
| Tree-root | Transitive | Two-way | Yes | A tree-root trust is established the moment a domain tree is created within a forest. |
| External | Non-transitive | One-way or two-way | No | Provides access to resources in a Windows NT 4.0 domain or a domain located in a different forest that isn’t supported by a forest trust. |
| Realm | Transitive or non-transitive | One-way or two-way | No | Forms a trust relationship between a non-Windows Kerberos realm and a Windows Server 2003 domain. |
| Forest | Transitive | One-way or two-way | No | Shares resources between forests. |
| Shortcut | Transitive | One-way or two-way | No | Reduces user logon times between two domains within a Windows Server 2003 forest. |
Active Directory Reporting with SolarWinds Access Rights Manager (FREE TRIAL)
Generating reports on Active Directory is essential for optimizing performance and staying in accordance with regulatory compliance. One of the best Active Directory reporting tools is SolarWinds Access Rights Manager (ARM). The tool has been created to increase visibility into how directory credentials are used and managed. For example, you can view accounts with insecure configurations and credential abuse that could indicate a cyber attack.
Using a third-party tool like SolarWinds Access Rights Manager is beneficial because it provides you with information and features that would be much more difficult or impossible to access through Active Directory directly.
Pros:
- Makes AD management easier through visualizations and reporting
- Provides a clear look into permission and file structures through automatic mapping and visualizations
- Preconfigured reports make it easy to demonstrate compliance
- Any compliance issues are outlined after the scan and paired with remediation actions
- Sysadmins can customize access rights and control in Windows and other applications
Cons:
- SolarWinds Access Rights Manager is an in-depth platform designed for sysadmin which may take time to fully learn
As well as generating reports you can automatically delete inactive or expired accounts that cybercriminals target. SolarWinds Access Rights Manager starts at $3,444 (£2,829). There is also a 30-day free trial version that you can download.
SolarWinds Access Rights Manager
Download 30- day FREE Trial
See also: Access Rights Management
How to Find the Source of Account Lockouts in Active Directory
The easiest way to find account lockouts in Active Directory is to use the Event Viewer, which is built into Windows. Active Directory generates Windows Events messages for each of its actions, so your first task is to track down the right event log.
- Open a PowerShell window by pressing the Windows key and R together. In the Run popup, type powershell and hit ENTER.
- At the command line type (get-addomain).pdcemulator
- Note down the address of the PCD Emulator domain controller, which will be shown on the next line.
- Type exit to close the PowerShell window.
- The standard event log viewer that is built into the Windows operating system will help you find the account lockouts.
- Go to the DC named as the PDC Emulator.
- Open the Event Viewer by expanding Windows Administrative Tools in the Start menu and clicking on the Event Viewer entry in that submenu.
- In the Event Viewer, expand the Windows Logs node in the left-hand menu tree. Click on Security. The Security events list will appear in the central panel of the Event Viewer.
- In the right panel of the Event Viewer, click on Filter Current Log, which will open a popup window.
- In the Event IDs field replace <All Event IDs> with 4740.
- Select a time horizon in the Logged drop-down list at the top of the form.
- Optionally, enter a username or a hostname if you are specifically looking for a lockout on a specific user or resource.
- Press OK.
- Double click on the log entry that relates to the user or resource that interests you and that has a timestamp that matches the moment you think the lockout occurred. This will open the Event Report.
The Event Report will show you the user that was locked out, the computer that the event occurred on, and the source, or reason for the lockout.
Active Directory Management with ManageEngine AD360 (FREE TRIAL)
ManageEngine AD360 is a compendium of ManageEngine Active Directory management systems plus a backup and recovery service. This package represents a good example of the tools that are available to automate the management tasks surrounding Active Directory usage. It is able to interface to AD implementations for SharePoint, Microsoft 365, Azure, and AWS, as well as the Active Directory system that you have in your Windows Server operating system.
Pros:
- Package of AD tools
- Enforces multi-factor authentication
- Audits AD objects to improve group management
- Detects inactive accounts
- User behavior analytics
Cons:
- You might only need one of the component tools
ManageEngine AD360 is available on a 30-day free trial.
ManageEngine AD360
Start 30-day FREE Trial
Active Directory Tutorial: The Basics
Active Directory is one of the best tools for managing resources in your network. In this article, we’ve just scratched the surface of the potential of this tool. If you’re using Active Directory remember that it is a potential entry point for cyber attackers. Making a note of key directory events and use a directory monitor will go a long way towards minimizing the risk of a malicious attack and protecting the availability of your service.
Active Directory FAQs
What is the difference between an Active directory and a Domain controller?
Active Directory is an authentication system. A domain is a collection of objects, which are users, computers, and devices that all have access rights managed in the same Active Directory database. The domain controller is the authentication management system that implements Active Directory functions on the domain’s database objects.
How to enable the Security Auditing of Active Directory?
In order to start security auditing within Active Directory:
- Log in to Windows Server as an administrator.
- Go to Start, click on Administrative tools, and select Group policy management console.
- Get to the domain/OU to be audited.
- Right-click on the Group Policy Object, and choose Edit. This will open the Group Policy Management Editor.
- In the left-hand tree menu, expand Computer Configuration, then Policies, expand Windows Settings, then Security Settings, and finally Local Policies. Click on Audit Policies.
- In the main panel of the Editor, click on Audit object access and select both the Success and Failure options.
- Click on Audit directory service access and select both the Success and Failure options.
What is the difference between Active Directory and LDAP?
The Lightweight Directory Access Protocol (LDAP) is an open standard that outlines how access rights can be managed. Active Directory is an access rights management system, written by Microsoft. Active Directory is an evolution of the concepts defined in LDAP.
What are Active Directory and Single sign-on and what are the differences between them?
Single sign-on (SSO) gives each user access to several systems with just one authentication procedure. Active Directory (AD) is an access rights management system that can implement an SSO environment.
Can I install Active Directory on client operating systems?
No. Active Directory is a server function and it is integrated into the Windows Server operating system. Logically, any client running Active Directory would become a server.
What should you look for in Active Directory tools?
We reviewed the market for Active Directory monitoring software and analyzed the options based on the following criteria:
- An interface that offers an easier way to organize Active Directory
- Reporting functions for auditing
- The ability to monitor many AD instances
- Tracking for replication, synchronization, backup, and migration
- Fast account status identification
- A free trial that provides a no-cost assessment period
- Value for money from a tool that pays for itself in efficiency improvements
In this post, we’ll learn about the Structure and components of the Active Directory domain controller with examples. Before you actually install a domain controller, you need to understand what it does and the environment to which it works.
Enterprise networks that run Windows operating systems depend on Active Directory Domain Services (ADDS) and its related services for many functions. The ADDS database contains all the domain objects, such as user accounts, computer accounts, and groups for your network.
Installing and configuring an ADDS domain controller enables you to create and store the ADDS database.
ADDS is a distributed database that stores and manage information about network resources and application-specific data from directory-enable applications. It helps administrators to organize network objects such as user accounts, computer accounts, and devices into a hierarchical collection of containers or folders – This is known as the logical structure of Active Directory.
Active Directory consists of Both physical and logical structures. The Physical structure is made up of the domain tree and the corresponding domain controller, it contains objects such as user accounts, computer accounts, group accounts, organizational units, and printers.
Structure of Active Directory
Active Directory Logical structure consists of the logical objects you create or (Windows server 2012 R2 creates automatically) for organizational and administrative purposes.
For example, when you install the first windows domain controller, Windows Server 2012 R2 creates the logical forest, domain tree, and the domain at the top level of the domain tree.
When you install additional domain controllers, you can add them to the forest root domain or create a child domain below the forest root domain.
For example, look at the figure below. You will see the forest root domain named serverroompro.com, with two child domains named Boston.serverroompro.com and Texas.serverroompro.com.
Please know that both the Serverrroompro.com domain (The Head Quarters) and the Texas domain are located in Texas being housed in a single office.
Microsoft recommends that you create a site that contains both (Serverrroompro.com and Texas.serverroompro.com) because they are connected by high-speed networks. A second site should also be created for Boston because the networks in Texas connect to Boston’s networks through a wide area network (WAN) connections.
This is done by Microsoft to reduce the amount of time it takes to manage domain objects. You can delegate administrative rights or permissions at any level with Active Directory.
For example, you can create a new user account and grant it an administrative privilege at the child domain level of Texas.serverroompro.com domain. These permission enable the user to administer the contents of the domain.
Another example, You can create a user account to which you assign administrative permissions at the forest root domain level Serverrroompro.com.
This user could then manage all the objects within the forest root domain and also both child domains. Additionally, you can also assign a user administrative permissions at the organizational unit (OU) level, this will enable the user to administer only the contents of the OU.
Leaf Objects
These are objects in Active Directory that have no child objects. They are the most basic components in the ADDS logical structure. Examples are Computer accounts, user accounts, group accounts, printers.
Active Directory Components
There are two components of Active Directory namely, Physical Components and Logical Components.
Physical components include the following:
- Domain controller: These is the server that holds the server role Active Directory Domain Services (ADDS) and store the content if the AD Database. The file contained in the AD Database can be called the data store
- Global Catalog Server: This server contains a partial read-only copy of the objects in the forest. This was implemented by Microsoft to make it possible for faster searches of objects in a different domain in the forest.
- Read-Only Domain Controller (RODC): These are domain controllers that host a read-only copy of the AD database. RODCs are configured in office locations with low security or in-experienced administrators. In case someone hacks into the server at this location, the hacker won’t be able to change anything in the AD database.
Logical components include the following:
- Domain: A domain is a collection of an administrative defined object that shares a common directory database, security policy and trust relationships with other domains. Domains exist within a forest and share common logical structure, global catalog, directory schema, and directory configurations.
- Tree: A tree is a collection of domains that are arranged in hierarchical structures. When you add a domain to a tree, it becomes a child of the tree root domain, and also know that a domain to which a child is joined to is called its parent domain. The name of a child domain is combined with the name of its parent domain to form its own unique DNS name such as boston.serverroompro.com so that each tree has a similar namespace.
- Forest: A forest is a complete instance of Active Directory. Each forest acts as a top-level container for all the domain containers for a particular Active Directory instance. A forest can contain one or more domain controller objects, as well as an automatic two-way transitive trust relationship. The name of that domain refers to the forest, such as serverroompro.com. By default, information in the Active Directory is only shared within the forest. So the forest is known as the security boundary for information that is contained in that instance of Active Directory. Simply put, a forest is a collection of domain trees that share ADDS
- Site: Sites helps to organize users, groups, and computers based on their geographic location and the speed of their connection. At their most basic, sites are just groups of well-connected IP subnets
- OU: These are container objects, that you can use to arrange other objects to support your administrative works. It helps in arranging objects. OU makes it easier to locate and manage your AD objects
- Partition: You can create partitions to create logical sections within the Active Directory database. Using partitions enables you to optimize tasks such as replications.
- Schema: Lastly, Microsoft uses the schema to define all attributes for each type of object you can create and store in Active Directory. For example, the schema contains attributes of user objects such as the user’s first name, last name, address, group membership, date of birth, etc. The schema is extensible which mean it can be modified or you can insert additional attributes for an object.
What is Active Directory?
Active Directory is a Microsoft product that operates on Windows Server. It is a database and set of services developed to help you with access, management, and permissions for your network resources. The organizational data is stored as an object in the Active Directory, and it can be in the form of devices, files, users, applications, groups, or shared folders. In addition, these objects can be categorized by their name or attribute.
The directory or database stores critical information related to your IT environment, including essential details about users, user permissions, and computers. In short, it helps you control various activities going on in your IT environment. Most importantly, AD also ensures user authentication, generally via user ID and passwords, and allows them to access data they’re authorized to use.
How does Active Directory work?
In the AD, the domain is the primary unit in a logical structure. The objects named under the same directory database, trust relationships, and security policies with other domains are called Domains. Each domain will store data about objects belonging to that domain only.
Settings and security policies, for example, Access Control Lists (ACLs), admin rights, etc., do not pass from one domain to another. In short, the admin can set policies only for the domain they belong to. Domains allow admins to set boundaries for objects and handle security policies for shared network resources.
One of the primary Active Directory services is the AD DS (Active Directory Domain Services), a crucial part of the Windows Server OS. The AD DS runs on servers known as Domain Controllers (DCs). An enterprise usually has multiple DCs, and each of these controllers has a copy of the main directory for the domain. Any changes made to the directory on one DC- for example, deleting a user account or changing a password are all applied to the other DCs in a domain to keep them up-to-date.
Another DC called Global Catalog server stores a copy of all objects within a directory of its domain along with a partial copy of all objects of other domains within a forest. This allows applications and users to find objects in any domain of its forest quickly.
Other laptops, desktops, and devices that run Windows (instead of Windows Server) do not run AD DS, but they can be a part of an Active Directory environment.
AD DS depends upon standards and protocols, such as DNS, Kerberos, and LDAP (Lightweight Directory Access Protocol). An important thing to know is that AD is exclusive to On-prem Microsoft environments. To run it in cloud Microsoft environments, you need to use Azure Active Directory, which works similar to the On-prem variant. Azure AD and AD are different but can run together if an organization has a hybrid deployment (cloud and on-prem).
Why is Active Directory So Important?
To simplify and understand the concept of AD better, consider Active Directory as the “Contacts” application on your mobile phone. The Contacts app itself acts as an Active Directory, while individual contacts in the app would be its “objects”. The values stored in each object, such as phone number, address, email, etc., would be your Active Directory. The only difference is that objects like in the mobile app aren’t just limited to people, but AD may also contain group objects such as printers, computers, devices, etc.
Active Directory is vital for organizations as it helps you efficiently manage company users, computers, devices, and applications. For example, IT managers can leverage Active Directory to systematically organize company data in a hierarchy structure, which states which users or computers belong to which network, or which users have access to which network resources, and so forth.
How to Setup Active Directory Domain Controller?
A domain controller contains many computers on the network and allows the system administrators to manage them from the central place. It is a server or computer used to authenticate other computers throughout the network. It stores the login credentials of all other computers and printers in the network.
This section will show you how to install Active Directory Domain Services and set up a domain controller on Windows server 2019.
Follow the below steps to install Active Directory Domain Services:
Step 1 – Login to Windows server 2019 as an administrator and open the Server Manager as shown below:
Step 2 – Click on the Add Roles and Features. This will open the Add Roles and Features Wizard as shown below:
Step 3 – Click on the Next button. You will be asked to select the installation type as shown below:
Step 4 – Select Add Roles and Features Wizard and click on the Next button. Next, you will be asked to select a destination server as shown below:
Step 5 – Select “Select a server from the server pool” and click on the Next button. Next, you will be asked to select server roles as shown below:
Step 6 – Select Active Directory Domain Services and click on the Next button. You will be asked to select features as shown below:
Step 7 – Leave all default settings and click on the Next button. Next, you should see the confirm installations selections page.
Step 8 – Click on the Install button to start the installation. Once the installation has been finished. You should see the following page.
Step 9 – Click on the Close button. You should see the following page.
Step 10– Click on the yellow notification icon. You should see the following page:
Step 11 – Click on Promote this server to a domain controller. You should see the deployment configuration page:
Step 12 – Select add a new forest, define your domain name and click on the Next button. You should see the domain controller options page:
Step 13 – Define your directory service restore mode password and click on the Next button. You should see the DNS options page:
Step 14 – Leave the default configuration and click on the Next button. You will be asked to set a NetBIOS name as shown below:
Step 15 – Set your NetBIOS name and click on the Next button. You will be asked to define AD DS database path location:
Step 16 – Leave the default path as it is and click on the Next button. You should see the review all options page:
Step 17 – Review all the configurations and click on the Next button. You should see the prerequisites check page:
Step 18 – Make sure all prerequisite checks are successfully then click on the Install button. Once the installation has been finished, your system will be restarted automatically.
Verify Domain Controller
Next, you will need to verify whether the Domain Controller is adequately set up or not. Again, you can prove it from PowerShell.
To confirm the successful installation of the services, run the following command on Windows PowerShell.
Get-Service adws,kdc,netlogon,dns
You should see the status of all services on the following screen:
To display all the configuration details of the domain controller, run the following command:
Get-ADDomainController
You should see all the information on the following screen:
To get detailed information about your domain, run the following command:
Get-ADDomain mydomain.com
You should see the next screen:
To display your Active Directory Forest details, run the following command:
Get-ADForest mydomain.com
You should see the next screen:
Create Active Directory Users
After setting up the Active Directory Domain controller, you must create users for the network computers. So that all users are login to the Active Directory Domain Controller from the network computer. You can create a user, group, and computer using the Active Directory Users and Computer tool.
Follow the below steps to create a new user on Active Directory:
Step 1 – Open the Server Manager, go to the Tools menu and select Active Directory Users and Computers as shown below:
Step 2 – Right-click on the Users. You should see the following page:
Step 3 – Click on the New => User. You should see the following page:
Step 4 – Provide your First name, Last name, Logon name, and click on the Next button. You should see the following page:
Step 5 – Set your password and click on the Next button. You should see the following page:
Step 6 – Verify your user information and click on the Finish button.
Install Active Directory Remote Server Administration Tools
Active Directory Remote Server Administration Tools (RSAT) is a handy tool that allows the system administrators to manage Active Directory Domain Controller on a windows server from a computer running Windows 10 or other servers.
RSAT tools set can manage the following service running on the Windows server:
- Server Manager
- Consoles
- Microsoft Management Console (MMC) snap-ins
- Windows PowerShell cmdlets and providers
- Command-line tools to run features on Windows Server
- IP Address Management (IPAM) Tools
- DHCP Tools
- Routing and Remote Access Tools
- Network Policy Server Tools
Follow the below steps to install the RSAT tool on Windows Server 2019:
Step 1 – Open the Server Manager as shown below:
Step 2 – Click on the Add roles and features. You should see the following page:
Step 3 – Select Role-based or feature-based installation and click on the Next button. You should see the following page:
Step 4 – Select “Select a server from the server pool” and click on the Next button. You should see the following page:
Step 5 – Select “Remote Server Administration Tools” and click on the Next button. You should see the following page:
Step 6 – Click on the Add Features. You should see the following page:
Step 7 – Click on the Next button. You should see the following page:
Step 8 – Leave the default settings and click on the Next button. You should see the following page:
Step 9 – Confirm all settings and click on the Install button. Once the installation has been completed, click on the Close button to exit the window.
Step 10 – Now click on the Server Manager => Tools to access the RSAT as shown below:
What Are Active Directory Domain Services?
Active Directory Domain Services (AD DS) is one of the core directory services offered by AD. The main objective of AD DS is to employ authentication and authorization for easier management of access controls for network resources. It is the foundation of your Windows domain network. AD DS will store information about domain members, such as users/devices, verify their credentials and define their rights to access. Domain controller runs this service. Whenever a user logs into a device or tries to access another device in a network, the domain controller is alerted.
Multiple unique services fall under the category of AD DS to manage permissions, identities, and access rights to network resources. These services are as follows:
- Active Directory Certificate Services (AD CS) AD CS is a server role with which you can create a PKI (Public Key Infrastructure) and provide digital certificates for your company. These certificates can be used to authenticate computers and users and encrypt network traffic and application traffic. For example, if you see a browser address with “https”, the “s” stands for security certificate that it uses to encrypt the established communication between server and client.
- Active Directory Federation Services (AD FS) With AD Federation Services, you can employ single sign-on to external systems such as applications and websites. One typical example of the use of AD FS is Office 365. When a user signs in to Office 365, the user ID and password are redirected via the federation server to check whether the entered credentials are authentic against your On-prem AD. This is how it provides authentication to external systems through the local Active Directory.
- Active Directory Lightweight Directory Services (AD LDS) AD LDS offers directory services with the help of LDAP protocol without having to deploy any DCs. The service is used to provide directory service functionally to directory-enabled applications. But, it does not replace AD DS.
- Active Directory Rights Management Services (AD RMS) The service allows you to protect information within digital content. It secures the documents by defining which users can modify, open, view, print, forward, or take similar documents. For enhanced security, you can use local certificates to encrypt documents.
The Hierarchical Structure of Active Directory Domain Services
AD DS systematically organizes company data in a hierarchy that contains domains, trees, and forests. Here’s what the hierarchical structure of AD DS comprises of:
- Domains: A domain contains objects such as devices, groups, and users that fall under the same AD database. Think of a domain as a branch of a tree. A domain will have a structure the same as that of standard domains and subdomains.
- Trees: A tree is formed by grouping one or more domains in a logical hierarchy. All domains within a tree are logically linked; hence they “trust” each other.
- Forest: A forest is a topmost level in the Active Directory of your organization. It contains one or more trees grouped. Trees within a forest are also said to “trust” each other and share catalogs, directory schemas, domain configurations, and application data.
- Organizational units: Organizations Units or OU are used to organize groups, users, computers, and other entities.
- Containers: A container is almost similar to an OU; the only difference is that you cannot link a GPO (Group Policy Object) to a generic container within AD.
Introduction to Active Directory Forests and Trees
An object is a physical element present within a network, and an AD can have multiple objects. Two such objects are Forest and Tree.
Forests
A Forest comprises multiple grouped trees that share a standard global catalog, directory schema, logical structure, and configuration. It features two ways transitive trust relationships by default. The first and foremost domain created within a forest is known as the forest root domain.
In the case of different naming schemas, Forests allows organizations to group their divisions which may need to operate individually. But a company seeks to communicate with their various departments through transitive trusts and share the same schema and configuration container.
Tree
A tree features a group of one or more domains that allow the user to share resources globally. Single or multiple domains exist here in the contiguous namespaces. If you add a domain in the tree, it will become the child of the tree root domain, while the domain it is linked to becomes the parent domain. The child domain utilizes the parent domain’s name and attains the unique DNS (Domain Name System).
For example, if sbs.com is a root domain, you can create one or more child domains to this parent domain, such as sales.sbs.com or transfer.sbs.com. These child domains can also further have sub-child domains such as xyz.sales.sbs.com.
The domains within a tree have a two-way relationship, also known as Kerberos transitive trust relationship. For example, a Kerberos transitive trust implies that if Domain 1 trusts Domain 2, and Domain 2 trusts Domain 3, then Domain 1 trusts Domain 3 as well. In short, it means that a domain added to a tree will immediately establish trust relationships with every other domain inside that tree.
Difference between the Forest and the Tree
The Forest in an Active Directory sits at the highest level and contains multiple trees, while the Tree in an AD includes one or more domains.
Active Directory Trust Relationships and Types
A trust relationship is the formation of a logical link between two domains. One of them is known as the trusting domain, and the other is called the trusted domain. With a trust relationship, the trusting domain will honor the login authentication of the trusted domain.
Usually, the trusted domain stores the users, while the trusting domain comprises network resources. Thus, the users in the trusted domain are trusted and are allowed to access resources stored in the trusting domain.
Trusts can be created manually or automatically. These trusts are further classified into two categories viz—transitive and non-transitive trust. Transitive trust simply implies that if Domain 1 trusts Domain 2 and Domain 2 trusts Domain 3, then Domain 1 trusts Domain 3 as well. Non-transitive trust means that if Domain 1 trusts Domain 2, and Domain 2 trusts Domain 3, then Domain 1 DOES NOT trust Domain 3.
Trusts can further be one-way or two-way. Following are the types of trust relationships that are either one-way or two-way by default:
- Tree-root trust A tree-root trust implicitly forms when a user adds a new tree root domain within a forest. Only the domains at the topmost part of each tree can take part in the tree-root trust. Tree-root trust is a type of two-way transitive trust that is formed automatically.
- Parent-Child trust When a user adds a child domain in a tree, a parent-child trust relationship is implicitly formed. The DCPROMO process will automatically create a parent-child trust relationship in a DNS namespace hierarchy between the new domain and the preceding domain. This type of trust is a two-way transitive trust formed automatically.
- Shortcut trust A system admin manually needs to create a shortcut trust between two domains within a forest. This type of trust is often made in extensive forests to enhance user logon time, specifically for users who logon into computers of other domains within the forest. It is a transitive type of trust, and you can configure it as one-way or two-way.
- External trust A system admin creates an external trust between two domains belonging to different forests or between a domain in an AD forest and a domain in Windows NT 4.0 or earlier version. This type of trust is commonly created when users migrate resources from a Windows NT 4.0 domain to another domain in an AD. It is a non-transitive type of trust, which can be either one-way or two-way.
- Forest Trust A system admin creates a forest trust explicitly between two forest root domains (functional for Windows Server 2003 and later domains). Such a type of trust allows all domains in one forest to trust all domains in another forest. Though it is a transitive trust, it will not be transitive against three or more forests. And it can either be one-way or two-way.
- Realm Trust A system admin may create a realm trust explicitly between a Windows 2003 or later domain and a non-Windows Kerberos realm. This type of trust can be one-way or two-way and transitive or non-transitive.
Those were the core types of trust relationships in an Active Directory. Organizations need to have precise planning in place for trust relationships to ensure users get timely access to network resources they need.
What is Active Directory basics?
Active Directory is a Windows Server utility that controls access rights to system resources. There are two elements to the connection between a user and a resource. The first is credentials management of each user account and the second is a link from each account to a specific resource and the level of access permission granted. Each user will have access rights to many resources. The concept of user groups makes the allocation of access rights a lot easier. Rather than mapping each user account to each resource, the user is allocated to a group and then the permissions of the group to access a list of resources is mapped. Inheritance within the access rights system means that a group member gains all the access rights that are allocated to the group.
What is Active Directory structure?
Active Directory is structured in a hierarchy of three levels. Each collection of access rights definitions is called a Domain. The identity of this package is called a Domain Controller. The Domain Controller is based on a single database instance. Domains can be grouped together in a tree. The tree is like a circle of trust. All of the domains that belong to the same tree share a catalog, so a domain can be thought of a subdivision of the global catalog. For example, each department in a business could be a domain, which contains some of the users that are members of the business. A forest is a collection of trees that use a common catalog be guard different systems. For example, one tree might control on-premises access and the other, a SaaS platform’s accounts that give employees on the site access to the cloud platform’s services.
What are the 4 most important benefits of Active Directory?
Active Directory provides management of four resources:
- Security certificates
- Single Sign-On (SSO)
- Lightweight Directory Access Protocol (LDAP)
- Access rights management (ARM)
- Learn
- Windows
- Active Directory & Group Policy
What is Active Directory? Understanding the basics

Introduction
In the early days of personal computing, PCs were all stand-alone machines that had difficulty talking with one another. While it is still possible to run a similar setup, nowadays called a workgroup, there is another option availble: The directory service.
In short, a directory service stores information regarding objects on your network. These objects can be computers, users, groups, etc.
Active Directory (AD) is a directory service that was developed specifically for Microsoft Windows domains and comes packaged with most versions of Windows Server. If you’ve worked with a Windows network, you’ve likely interacted with AD at some point.
In this article, we’ll go over some basics of AD and talk about how it can make life easier (when it comes to managing your Windows network, anyhow).
What is AD used for?
AD has many different tasks that are defined by roles. Primarily, though, AD is used as a directory for objects (it is a directory service, after all). These objects help control access rights, authentication, tasks, policies, etc.
Also, while not strictly more secure than using a workgroup, AD does provide some ease in security management. For example, security rights can be controlled from a central location by a single admin. This prevents a jumble of security rights spread across different machines on the network.
In addition, AD provides the infrastructure necessary to utilize other Microsoft tools such as Group Policy and Exchange.
Getting started with Active Directory
Unless you’re setting up a new domain, AD is likely already installed. Still, AD and its various components can be installed within Server Manager at Start > Administrative Tools > Server Manager.
You’ll find the various AD components under the Roles list and can add individual components by clicking Add Roles. We’ll go over those roles in just a bit.
Once AD is installed, it can be accessed from Start > Administrative Tools. Depending on what you’ll be doing, you may be working with one of many AD roles listed below.
AD Roles
Active Directory consists of several roles that work together to provide full directory services for your Windows network.
- Active Directory Domain Services is the core of AD. It provides the hierarchy structure for network objects such as computers, users, groups, etc.
- Active Directory Users and Computers allows for creating, editing, and viewing of users and computers within AD. This is where many folks spend most of their time working with AD.
- Active Directory Federation Services allows for securing sharing of information, specifically identification-related information, between trusted entities. It enables features like Single Sign-On (SSO).
- Active Directory Lightweight Directory Services acts like an independent version of AD. It is most often used to provide a directory service for testing and development.
- Active Directory Rights Management Services is AD’s information rights management (IRM) component. It uses encryption and functionality denial techniques to limit document access.
- Active Directory Certificate Services allows for a public key infrastructure as well as the creation of digital certificates and signatures.
Conclusion
Active Directory is a helpful tool when managing a Windows environment. It provides different roles to handle a myriad of tasks and allows for easier management of user rights, file permissions, and other security-related tasks compared to a simple workgroup. In addition, it allows the addition of other Microsoft tools like Group Policy and Exchange.
Additional reading:
- Getting started with Active Directory
- Understanding Windows Server Roles
Jul 5, 2018 at 09:46 UTC
Very good writeup Jonathan, this helped a lot when learning about what AD was and does. Is there anything for a Mac environment that is similar to AD at all?

to enable IT peers to see that you are a professional.
Jul 5, 2018 at 10:51 UTC
Thanks for this 

to enable IT peers to see that you are a professional.
Jul 5, 2018 at 11:29 UTC
harryh5 wrote:
Very good writeup Jonathan, this helped a lot when learning about what AD was and does. Is there anything for a Mac environment that is similar to AD at all?
I believe there is but apple are scrapping it. Macs can now work in a windows AD network much better than they did before.
Jul 5, 2018 at 12:30 UTC
Would it be as simple as just loading windows server into a VM and using this to connect all the Mac machines to this?

to enable IT peers to see that you are a professional.
Jul 5, 2018 at 12:33 UTC
Nice writeup! I like AD a lot. ADUC is super easy to use. Could use an easy feature to undelete a user, as this has cropped up once when I was away on bereavement. Other than that, 5 stars!

to enable IT peers to see that you are a professional.
Jul 5, 2018 at 12:54 UTC
Good, basic definition of Active Directory and it’s various guises.

to enable IT peers to see that you are a professional.
Jul 5, 2018 at 13:18 UTC
harryh5 wrote:
Very good writeup Jonathan, this helped a lot when learning about what AD was and does. Is there anything for a Mac environment that is similar to AD at all?
Yes, Apple Open Directory: https://en.wikipedia.org/wiki/Apple_Open_Directory

to enable IT peers to see that you are a professional.
Jul 5, 2018 at 13:20 UTC
harryh5 wrote:
Would it be as simple as just loading windows server into a VM and using this to connect all the Mac machines to this?
Mac’s and AD don’t «play well» together, typically. If you have an all Mac environment you should look at other options like Apple OD. If you start a post here I’m sure you’ll get some good feedback on all this.

to enable IT peers to see that you are a professional.
Jul 5, 2018 at 13:40 UTC
I appreciate the good, clear, concise writeup. Personally, I’d make one adjustment, because Active Directory Users and Computers is less of a role that can be installed, than a management tool to be used, though you are correct that this is where we spend the majority of our time when tinkering with Active Directory, and so from a Sysadmin standpoint, it kind of is a role. I’d say something more like, «Active Directory Users and Computers, though not an installable role, is a tool that allows for creating,…»

to enable IT peers to see that you are a professional.
Jul 5, 2018 at 14:40 UTC
Mac’s and AD don’t play well together is a correct assumption. To make it work you have to have third party tools. Apple OD is pretty good but you need Apple Server. I have never been in an environment that was all Mac. It has always been 85 to 90 percent Windows so Macs have to somehow work in that world. A round peg into a square hole.
Jul 5, 2018 at 14:49 UTC
another good one to share with internals

to enable IT peers to see that you are a professional.
Jul 5, 2018 at 20:47 UTC
Thanks for the AD warm-up post!.
I have to say, when @harryh5 wrote:
Would it be as simple as just loading windows server into a VM and using this to connect all the Mac machines to this?
I nearly died!
My brain immediately thought of all of the Microsoft Licensing HELL (yes, it qualifies for caps) one must wade through in order to determine which method of licensing CALS (Users? Devices?) that you’d like to spend money on for the rest of your lifetime for such minimal use of AD, I couldn’t help but mentally feel the spike in my skull being hammered into place.
For my *u*x hosts, AD provides four data points ONLY — UserID, GroupID, OS shell (bash/csh/tcsh/zsh), and unixHomeDirectory. Unless you need to share data with Windows users, I would not use AD at all.
Any decent (and free) LDAP service can do this, which can be run on nearly anything.
The intent of using AD at my site is to keep all UIDs/GIDs aligned across several platforms. Many are Windows users, compiling for Unix systems, and sharing the code base via a shared mount point, by both Unix/Linux and Windows systems.
For Mac users, unless you have a true business need to have AD managing your user base across OS platforms, I would highly recommend that you investigate utilizing LDAP instead.

to enable IT peers to see that you are a professional.
Jul 5, 2018 at 21:15 UTC
Good write up. This is a great refresher. It’s been a while since I actually studied the topic.

to enable IT peers to see that you are a professional.
Jul 5, 2018 at 21:58 UTC
harryh5 wrote:
Very good writeup Jonathan, this helped a lot when learning about what AD was and does. Is there anything for a Mac environment that is similar to AD at all?
You can try Jamf for Mac computers (and Apple devices) management.
https://www.jamf.com

to enable IT peers to see that you are a professional.
Jul 6, 2018 at 17:42 UTC
harryh5 wrote:
Is there anything for a Mac environment that is similar to AD at all?
They have ‘Open Directory’, but they have been slowly ending support for anything related to business. Apple is pushing anything business related out to third party development.
Jul 18, 2018 at 17:26 UTC
Yeah, recently I was asked to explain what active directory
was during a telephonic job interview. This is just the article I needed to
read through to freshen up my description of Active Directory. Even though I’d
been working with AD for years it was another matter altogether putting the
concept into words, let alone in an interview.
Nice job with this, thank you
Dec 3, 2018 at 20:36 UTC
Very helpful. good succinct definition. Thank you!

to enable IT peers to see that you are a professional.
Feb 6, 2019 at 20:09 UTC
Concise explanation. As a new user of AD, I found this to be a helpful synthesis of its components.

to enable IT peers to see that you are a professional.
Apr 11, 2019 at 15:35 UTC
Thank you for the write-up. This is very helpful information for me as a new user of AD.
Feb 14, 2023 at 19:00 UTC