Update Windows 7 KB4474419
Update Windows 7 KB4474419. 2019-09 Security Update for Windows 7 for x86 and x64 based Systems (KB4474419).
A security issue has been identified in a Microsoft software product that could affect your system. You can help protect your system by installing this update KB4474419 for windows 7. After you install this update, you may have to restart your system.
Install resources KB4474419
Architecture: X86 & X64
Classification: Security Updates
Supported products: Windows 7
Supported languages: all
Restart behavior: Can request restart
May request user input: No
Must be installed exclusively: No
Requires network connectivity: No
Uninstall Notes: This software update can be removed by selecting View installed updates in the Programs and Features Control Panel.
Uninstall Steps: n/a
Rate this program
- 1
- 2
- 3
- 4
- 5
4.6 out of 5 stars (11 Ratings)
Update Windows 7 KB4474419 32-bit

6335cd216727be17720c8d67394e309e
Update Windows 7 KB4474419 64-bit

d5ff57b4145dfd534f7e5d1d3b50a5c2
Secure and Fast Download — Software Verified
11 September 2019
| Пресс-Центр
Компания Microsoft выпустила обновления безопасности за сентябрь. В этой статье я расскажу о самых главных моментах этого выпуска.
Общий взгляд
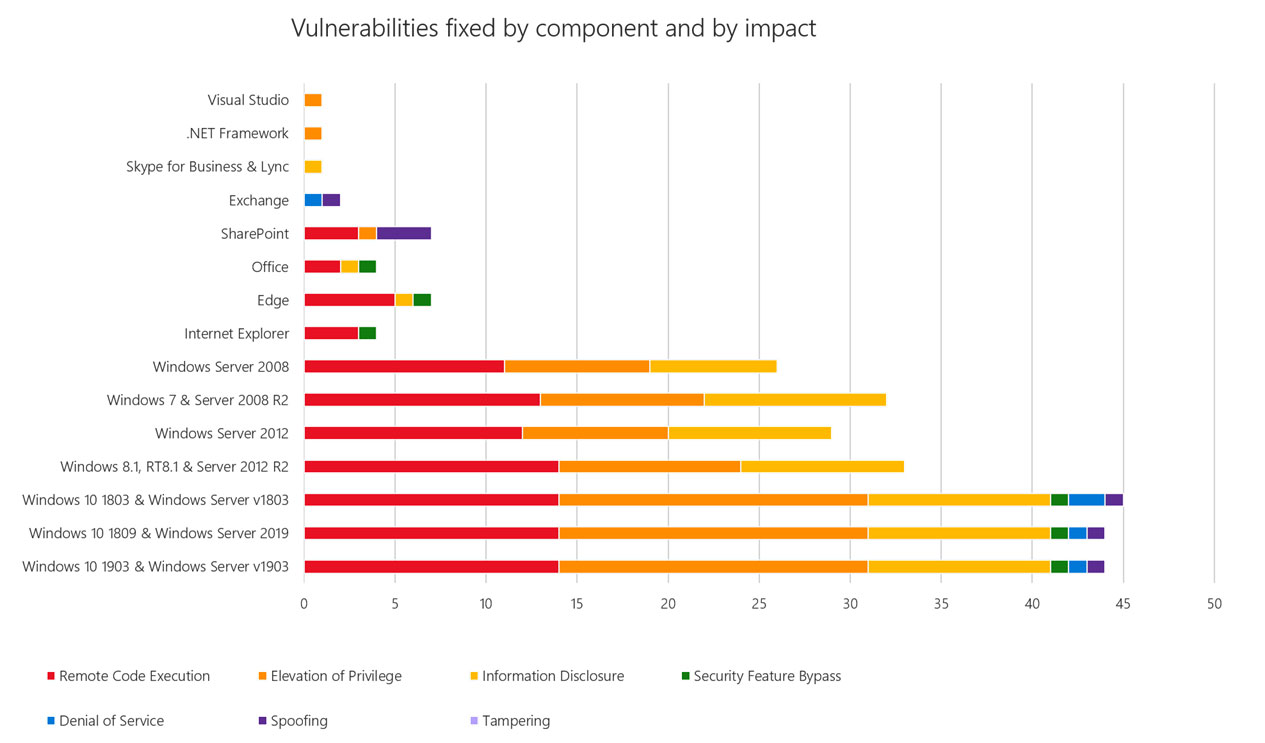
Сводная информация по количеству и типу уязвимостей в соответствующих продуктах приведена на графике ниже:
Обратите внимание
На следующие уязвимости и обновления безопасности следует обратить особое внимание:
Windows
CVE-2019-1235 – Windows Text Service Framework (Publicly disclosed)
CVE-2019-1253 – Windows AppX Deployment Server (Publicly disclosed)
CVE-2019-1294 – Secure Boot (Publicly disclosed)
CVE-2019-1273 – Active Directory Federation Services (Base CVSS Score 8.2)
CVE-2019-1214 – Common Log File System Driver (Exploitation detected)
CVE-2019-1215 – Windows Winsock driver (Exploitation detected)
Microsoft Browsers
CVE-2019-1208 – VBScript Remote Code Execution Vulnerability
Microsoft Office
CVE-2019-1297 – Microsoft Excel (Preview Pane is not an attack vector)
Microsoft SharePoint
CVE-2019-1296 – Microsoft SharePoint Remote Code Execution Vulnerability
Microsoft Exchange
CVE-2019-1233 – Microsoft Exchange Denial of Service Vulnerability
CVE-2019-1266 – Microsoft Exchange Spoofing Vulnerability
Microsoft Skype for Business/Lync
CVE-2019-1209 – Microsoft Lync 2013 Information Disclosure Vulnerability
.NET Framework
CVE-2019-1142 – .NET Framework Elevation of Privilege Vulnerability
CVE-2019-1301 – .NET Core Denial of Service Vulnerability
CVE-2019-1142 – ASP.NET Core Elevation of Privilege Vulnerability
Visual Studio
CVE-2019-1232 – Diagnostics Hub Standard Collector Service Elevation of Privilege Vulnerability
CVE-2019-1305 – Team Foundation Server Cross-site Scripting Vulnerability
CVE-2019-1306 – Azure DevOps and Team Foundation Server Remote Code Execution Vulnerability
Рекомендации по безопасности
Были выпущены следующие рекомендательные документы (security advisory):
ADV190022 – September 2019 Adobe Flash Security Update
Были дополнены и обновлены следующие рекомендательные документы:
ADV990001 – Latest Servicing Stack Updates
New Servicing Stack Update (KB4512937) for all versions of Windows OS.
ADV190013 – Microsoft Guidance to mitigate Microarchitectural Data Sampling vulnerabilities
New updates provide protections for the 32-bit (x86) versions of: Server 2008, Windows 7, Windows 8.1, Windows 10 v1607, 1703, 1709, 1803, 1809, 1903.
Внимание:
ADV190023 – Microsoft Guidance for Enabling LDAP Channel Binding and LDAP Signing.
В одном из будущих выпусков обновлений в начале 2020 г. компания Microsoft предоставит обновление Windows, которое изменит настройки по умолчанию для параметров подписывания протокола LDAP (LDAP signing) и проверки привязки канала протокола LDAP (LDAP channel binding) для обеспечения более защищенной конфигурации. Когда обновление станет доступно, заказчики будут уведомлены посредством данной рекомендательной статьи.
В настоящее время мы настоятельно рекомендуем при первой возможности предпринять следующее:
- Настройте ваши системы в соответствии с рекомендациями по усилению безопасности контроллеров домена Active Directory (включите параметры подписывания протокола LDAP (LDAP signing) и проверки привязки канала протокола LDAP (LDAP channel binding);
- Выявите и исправьте возможные проблемы совместимости приложений в вашей инфраструктуре.
За подробностями обратитесь к этой статье: https://support.microsoft.com/help/4520412.
Возможные проблемы
Ниже представлен список статей базы знаний для соответствующих пакетов обновлений, с которыми связаны потенциальные проблемы после установки:
| KB Article | Applies To |
| 4512578 | Windows 10, version 1809, Windows Server 2019 |
| 4515384 | Windows 10, version 1903, Windows Server version 1903 |
| 4515832 | Microsoft Exchange Server 2019 and Exchange Server 2016 |
| 4516044 | Windows 10, version 1607, Windows Server 2016 |
| 4516046 | Internet Explorer |
| 4516055 | Windows Server 2012 (Monthly Rollup) |
| 4516058 | Windows 10, version 1803, Windows Server version 1803 |
| 4516062 | Windows Server 2012 (Security-only update) |
| 4516064 | Windows 8.1, Windows Server 2012 R2 (Security-only update) |
| 4516065 | Windows 7 Service Pack 1, Windows Server 2008 R2 Service Pack 1 (Monthly Rollup) |
| 4516066 | Windows 10, version 1709 |
| 4516067 | Windows 8.1, Windows Server 2012 R2 (Monthly Rollup) |
| 4516068 | Windows 10, version 1703 |
| 4516070 | Windows 10 |
Дополнительная информация
Вы также можете посмотреть запись нашего ежемесячного вебинара «Брифинг по безопасности», посвященного подробному разбору текущего выпуска обновлений и бюллетеней безопасности компании Microsoft.
Самую полную и актуальную информацию об уязвимостях и обновлениях безопасности вы можете найти на нашем портале Security Update Guide.
А для того чтобы быть в курсе самых актуальных новостей информационной безопасности Microsoft, подписывайтесь на канал https://aka.ms/artsin.
Помните, для 86% всех уязвимостей были доступны патчи на момент их обнародования*, и своевременно обновляйте ваши системы.
Артём Синицын CISSP, MCSE
руководитель программ информационной безопасности
Microsoft
@ArtyomSinitsyn
*Vulnerability Review Report 2018 by Flexera
Tags: Security, Security Updates
Содержание
- Выпущены обновления безопасности Microsoft за сентябрь 2019
- Общий взгляд
- Обратите внимание
- Рекомендации по безопасности
- Возможные проблемы
- Дополнительная информация
- Как продлить жизнь Windows 7?
- Как отключить всплывающее уведомление о окончании поддержки Windows 7?
- Microsoft Windows Security Updates September 2019 overview
- Microsoft Windows Security Updates September 2019
- Executive Summary
- Operating System Distribution
- Windows Security Updates
- Known Issues
- Security advisories and updates
- Non-security related updates
- Microsoft Office Updates
- How to download and install the September 2019 security updates
- Direct update downloads
- question
- Server 2019 update KB5005568 (Sept 2022) forcing new DCOM authentication prematurely
- 2019 SHA-2 Code Signing Support requirement for Windows and WSUS
- Summary
- Background details
- Product update schedule
- Current status
- Windows 7 SP1 and Windows Server 2008 R2 SP1
- Windows Server 2008 SP2
- Frequently Ask Questions
- General information, planning and issue prevention
- Issue recovery
Выпущены обновления безопасности Microsoft за сентябрь 2019
11 September 2019 | Пресс-Центр
Компания Microsoft выпустила обновления безопасности за сентябрь. В этой статье я расскажу о самых главных моментах этого выпуска.
Общий взгляд
Сводная информация по количеству и типу уязвимостей в соответствующих продуктах приведена на графике ниже:
Обратите внимание
На следующие уязвимости и обновления безопасности следует обратить особое внимание:
Windows
CVE-2019-1235 – Windows Text Service Framework (Publicly disclosed)
CVE-2019-1253 – Windows AppX Deployment Server (Publicly disclosed)
CVE-2019-1294 – Secure Boot (Publicly disclosed)
CVE-2019-1273 – Active Directory Federation Services (Base CVSS Score 8.2)
CVE-2019-1214 – Common Log File System Driver (Exploitation detected)
CVE-2019-1215 – Windows Winsock driver (Exploitation detected)
Microsoft Browsers
CVE-2019-1208 – VBScript Remote Code Execution Vulnerability
Microsoft Office
CVE-2019-1297 – Microsoft Excel (Preview Pane is not an attack vector)
Microsoft SharePoint
CVE-2019-1296 – Microsoft SharePoint Remote Code Execution Vulnerability
Microsoft Exchange
CVE-2019-1233 – Microsoft Exchange Denial of Service Vulnerability
CVE-2019-1266 – Microsoft Exchange Spoofing Vulnerability
Microsoft Skype for Business/Lync
CVE-2019-1209 – Microsoft Lync 2013 Information Disclosure Vulnerability
.NET Framework
CVE-2019-1142 – ASP.NET Core Elevation of Privilege Vulnerability
Visual Studio
CVE-2019-1232 – Diagnostics Hub Standard Collector Service Elevation of Privilege Vulnerability
CVE-2019-1305 – Team Foundation Server Cross-site Scripting Vulnerability
CVE-2019-1306 – Azure DevOps and Team Foundation Server Remote Code Execution Vulnerability
Рекомендации по безопасности
Были выпущены следующие рекомендательные документы (security advisory):
ADV190022 – September 2019 Adobe Flash Security Update
Были дополнены и обновлены следующие рекомендательные документы:
ADV990001 – Latest Servicing Stack Updates
New Servicing Stack Update (KB4512937) for all versions of Windows OS.
ADV190013 – Microsoft Guidance to mitigate Microarchitectural Data Sampling vulnerabilities
New updates provide protections for the 32-bit (x86) versions of: Server 2008, Windows 7, Windows 8.1, Windows 10 v1607, 1703, 1709, 1803, 1809, 1903.
ADV190023 – Microsoft Guidance for Enabling LDAP Channel Binding and LDAP Signing.
В одном из будущих выпусков обновлений в начале 2020 г. компания Microsoft предоставит обновление Windows, которое изменит настройки по умолчанию для параметров подписывания протокола LDAP (LDAP signing) и проверки привязки канала протокола LDAP (LDAP channel binding) для обеспечения более защищенной конфигурации. Когда обновление станет доступно, заказчики будут уведомлены посредством данной рекомендательной статьи.
В настоящее время мы настоятельно рекомендуем при первой возможности предпринять следующее:
Возможные проблемы
Ниже представлен список статей базы знаний для соответствующих пакетов обновлений, с которыми связаны потенциальные проблемы после установки:
| KB Article | Applies To |
| 4512578 | Windows 10, version 1809, Windows Server 2019 |
| 4515384 | Windows 10, version 1903, Windows Server version 1903 |
| 4515832 | Microsoft Exchange Server 2019 and Exchange Server 2016 |
| 4516044 | Windows 10, version 1607, Windows Server 2016 |
| 4516046 | Internet Explorer |
| 4516055 | Windows Server 2012 (Monthly Rollup) |
| 4516058 | Windows 10, version 1803, Windows Server version 1803 |
| 4516062 | Windows Server 2012 (Security-only update) |
| 4516064 | Windows 8.1, Windows Server 2012 R2 (Security-only update) |
| 4516065 | Windows 7 Service Pack 1, Windows Server 2008 R2 Service Pack 1 (Monthly Rollup) |
| 4516066 | Windows 10, version 1709 |
| 4516067 | Windows 8.1, Windows Server 2012 R2 (Monthly Rollup) |
| 4516068 | Windows 10, version 1703 |
| 4516070 | Windows 10 |
Дополнительная информация
Вы также можете посмотреть запись нашего ежемесячного вебинара «Брифинг по безопасности», посвященного подробному разбору текущего выпуска обновлений и бюллетеней безопасности компании Microsoft.
Самую полную и актуальную информацию об уязвимостях и обновлениях безопасности вы можете найти на нашем портале Security Update Guide.
А для того чтобы быть в курсе самых актуальных новостей информационной безопасности Microsoft, подписывайтесь на канал https://aka.ms/artsin.
Помните, для 86% всех уязвимостей были доступны патчи на момент их обнародования*, и своевременно обновляйте ваши системы.
руководитель программ информационной безопасности
*Vulnerability Review Report 2018 by Flexera
Источник
Как продлить жизнь Windows 7?
Приступим, что бы продлить поддержку нам необходимо установить несколько важных обновлений, программу продленной поддержки и тестовое обновление. За счет чего можно получить продление поддержки? Поддержка корпоративным клиентам будет оказывается еще 2 года, но платно. Мы же под шумок получим туже поддержку но бесплатно.
Смотрите в моем видео как продлить поддержку Windows 7:
Для начала скачайте архив со всеми необходимыми обновлениями. В нем есть обновления как для x86 так и х64 систем, используйте обновления вашей разрядности. Использовать эти обновления можно на любых версиях Windows 7. Устанавливайте обновления в таком порядке:
Теперь ваш компьютер будет получать обновления безопасности и устранение критических уязвимостей еще 2 года!
Как отключить всплывающее уведомление о окончании поддержки Windows 7?
Если вы знаете еще варианты получения расширенной поддержки Windows 7, напишите о этом в комментариях!
Мои действия по переустановке «Bypass_ESU-v4» на версию 5:
1 Проверил установку на компьютере рекомендованных обновлений.
Следующие обновления должны быть установлены и готовы перед использованием BypassESU-v5:
— KB4490628: Servicing stack update, March 2019;
— KB4474419: SHA-2 code signing support update, August 2019;
— KB4536952: Latest Extended Servicing stack update, currently KB4536952 (January 2020)
or later;
— KB4538483: ESU Licensing Preparation Package, 13.02.2020 г.
(требуется только для получения обновлений через WU)
— KB3138612: Updated Windows Update Client.
Примечание: Если вы установили какой-либо накопительный пакет обновлений за июль 2016 года
KB3172605, или обновление безопасности KB4534314 за 13.01.2020 г., или исправление KB4539602
за 10.02.2020, они все уже обновили WUC (Windows Update Client).
2 Все они были установлены и их установку не выполнял.
3 Создал точку восстановления.
5 Перезагрузил компьютер.
6 Центр Обновления Windows 7 должен начать функционировать.
## Важные замечания:
1 После использования WU patcher, если вы все еще не получаете обновления ESU, попробуйте:
— перезагрузитесь, потом проверьте WU;
— остановите службу wuauserv, удалите (переименуйте) папку «C:WindowsSoftwareDistribution»,
затем проверьте WU (Центр обновления Windows).
Источник
Microsoft Windows Security Updates September 2019 overview
It is September 10, 2019 and Microsoft has just released security and non-security updates for its Microsoft Windows operating system and other company products.
Our overview of the September 2019 Patch Day provides system administrators and home users with information on the released updates. It features some stats at the beginning, provides links to all support articles and direct download options, lists known issues and security advisories, and provides other relevant information.
Microsoft Windows Security Updates September 2019
Here is a handy Excel spreadsheet that lists all released security updates for Microsoft products in September 2019. Please download it with a click on the following link: Microsoft Windows Security Updates September 2019
Executive Summary
Operating System Distribution
Windows Server products
Other Microsoft Products
Windows Security Updates
Windows 7 SP1 and Windows Server 2008 R2 SP1
Windows 8.1 and Windows Server 2012 R2
Windows 10 version 1803
Windows 10 version 1809 and Windows Server 1809
Windows 10 version 1903 and Windows Server version 1903
Windows 10 version 1903 and Windows Server 1903
Other security updates
Known Issues
Windows 7 SP1 and Windows Server 2008 R2 (monthly rollup only)
Windows 8.1 and Windows Server 2008 R2
Windows 10 version 1803
Windows 10 version 1809
Security advisories and updates
ADV990001 | Latest Servicing Stack Updates
ADV190022 | September 2019 Adobe Flash Security Update
Microsoft Office Updates
You find Office update information here.
How to download and install the September 2019 security updates
Most home systems receive updates automatically especially when they run Windows 10. Updates are not pushed in real-time to devices running Windows. Some administrators prefer to install security updates the moment they are released, others to wait to make sure that the updates don’t introduce any issues on the system.
Note: it is recommended that you back up the system partition before you install updates. Use programs like Paragon Backup & Recovery Free or Macrium Reflect for that.
Admins may check for updates manually to retrieve the released updates right away. Here is how that is done:
Updates may also be downloaded from the Microsoft Update Catalog website.
Direct update downloads
Windows 7 SP1 and Windows Server 2008 R2 SP
Windows 8.1 and Windows Server 2012 R2
Windows 10 (version 1803)
Windows 10 (version 1809)
Windows 10 (version 1903)
Источник
question
Server 2019 update KB5005568 (Sept 2022) forcing new DCOM authentication prematurely
Hi,
We recent applied KB5005568 (Sept 21 update) to one of our Server 2019 DCs. After applying, we started receiving many DCOM error events 10036 (Please raise the activation authentication level at least to RPC_C_AUTHN_LEVEL_PKT_INTEGRITY in client application) for a user id function on our Palo Alto FW (It uses a service account to resolve user identification from AD). Having read up on Microsoft’s transition to a minimum of Packet Integrity for DCOM authentication (see June’s KB5004442 and the DCOM issue described in CVE-2022-26414), it would appear that, at least in Server 2019, this feature has been enabled prematurely (Supposed to be Q1 2022 based on the timeline in the KB5004442) and the described reg entry to temporarily bypass the DCOM update does not work (it is supposed to be valid all of 2022 after the feature is enabled).
Our only solution has been to roll back the patch on our DC. I found one reference to someone else encountering the same. They have mixed OS’s for DCs and are only seeing the issue on 2019 (https://www.reddit.com/r/paloaltonetworks/comments/pl5dm7/new_2019_dc_event_log_messages_from_panos_userid/).
Is anyone else seeing this behavior with the pending DCOM update?
First time posting here and really just trying to see if this is on MS’s radar at all.
The fix related to this didn’t work?
Registry key HKEY_LOCAL_MACHINESOFTWAREMicrosoftOleAppCompatRequireIntegrityActivationAuthenticationLevel set to 0x00000000 and Reboot server.
Also go to COM Security, Edit Limits on both options, make sure user is manually added to local and remote access, local launch, remote launch etc.
Give those a go and see if any stick?
Hi the solution for me was to update the client server with the same patches and also using your tip:
Registry key HKEY_LOCAL_MACHINESOFTWAREMicrosoftOleAppCompatRequireIntegrityActivationAuthenticationLevel set to 0x00000000 and Reboot server.
can you explain some more how you resolved it finally?
We are having same issues with 2019.
Do i get it right that you uninstalled the CU of September, then set the Regkey, then installed the small update kb5004442 and then again the CU and then it worked without errors?
Having the same issue on 2019DC’s when we are querying WMI for events (errors/warnings) nightly. We get the error but the Powershell script that runs from a remote server is still able to pull the events. And so far no other clients appear to be creating this error when talking to the DC’s
This update KB5005568 also broke WMI Polling method in our monitoring. (SolarWinds)
WMI Polling fails all the time and we are getting»RPC server is unavailable» when testing WMI connectivity using wbemtest. Uninstalling the update resolved the issue, but we’d like to have the update installed without getting any WMI polling issues at all. Does anyone have this resolved from their end, can you share us what steps were taken to fix it? It would be greatly appreciated.
Keep safe everyone!
Anyone had any luck with this so far? Getting the same as OP (Palo alto service account).
You may need to try a beta firmware. Our vendor happened to release a beta that patches this issue the same day we started seeing the problem.
Источник
2019 SHA-2 Code Signing Support requirement for Windows and WSUS
Summary
To help protect the security of the Windows operating system, updates were previously signed (using both the SHA-1 and SHA-2 hash algorithms). The signatures are used to authenticate that the updates come directly from Microsoft and were not tampered with during delivery. Because of weaknesses in the SHA-1 algorithm and to align to industry standards, we have changed the signing of Windows updates to use the more secure SHA-2 algorithm exclusively. This change was done in phases starting in April 2019 through September 2019 to allow for smooth migration (see the «Product update schedule» section for more details on the changes).
Customers who run legacy OS versions (Windows 7 SP1, Windows Server 2008 R2 SP1 and Windows Server 2008 SP2) are required to have SHA-2 code signing support installed on their devices to install updates released on or after July 2019. Any devices without SHA-2 support will not be able to install Windows updates on or after July 2019. To help prepare you for this change, we released support for SHA-2 signing in starting March 2019 and have made incremental improvements. Windows Server Update Services (WSUS) 3.0 SP2 will receive SHA-2 support to securely deliver SHA-2 signed updates. Please see the «Product update schedule» section for the SHA-2 only migration timeline.
Background details
The Secure Hash Algorithm 1 (SHA-1) was developed as an irreversible hashing function and is widely used as a part of code-signing. Unfortunately, the security of the SHA-1 hash algorithm has become less secure over time because of the weaknesses found in the algorithm, increased processor performance, and the advent of cloud computing. Stronger alternatives such as the Secure Hash Algorithm 2 (SHA-2) are now strongly preferred as they do not experience the same issues. For more information about of the deprecation of SHA-1, see Hash and Signature Algorithms.
Product update schedule
Starting in early 2019, the migration process to SHA-2 support began in stages, and support will be delivered in standalone updates. Microsoft is targeting the following schedule to offer SHA-2 support. Please note that the following timeline is subject to change. We will continue to update this page as needed.
Stand Alone security updates KB4474419 and KB4490628 released to introduce SHA-2 code sign support.
Windows 7 SP1
Windows Server 2008 R2 SP1
Stand Alone update, KB4484071 is available on Windows Update Catalog for WSUS 3.0 SP2 that supports delivering SHA-2 signed updates. For those customers using WSUS 3.0 SP2, this update should be manually installed no later than June 18, 2019.
Stand Alone update, KB4493730 that introduce SHA-2 code sign support for the servicing stack (SSU) was released as a security update.
Windows Server 2008 SP2
Stand Alone security update KB4474419 released to introduce SHA-2 code sign support.
Windows Server 2008 SP2
Stand Alone security update KB4474419re-released to add missing MSI SHA-2 code sign support.
Windows Server 2008 SP2
Windows 10 updates signatures changed from dual signed (SHA-1/SHA-2) to SHA-2 only. No customer action required.
Windows 10, version 1709
Windows 10, version 1803
Windows 10, version 1809
Windows Server 2019
Required: For those customers using WSUS 3.0 SP2, KB4484071 must be manually installed by this date to support SHA-2 updates.
Required: Updates for legacy Windows versions will require that SHA-2 code signing support be installed. The support released in April and May (KB4493730 and KB4474419) will be required in order to continue to receive updates on these versions of Windows.
All legacy Windows updates signatures changed from SHA1 and dual signed (SHA-1/SHA-2) to SHA-2 only at this time.
Windows Server 2008 SP2
Windows 10 updates signatures changed from dual signed (SHA-1/SHA-2) to SHA-2 only. No customer action required.
Windows 10, version 1507
Windows 10, version 1607
Windows Server 2016
Windows 10, version 1703
Required: Updates for legacy Windows versions will require that SHA-2 code signing support be installed. The support released in March (KB4474419 and KB4490628) will be required in order to continue to receive updates on these versions of Windows. If you have a device or VM using EFI boot, please see the FAQ section for additional steps to prevent an issue in which your device may not start.
All legacy Windows updates signatures changed from SHA-1 and dual signed (SHA-1/SHA-2) to SHA-2 only at this time.
Windows 7 SP1
Windows Server 2008 R2 SP1
Legacy Windows update signatures changed from dual-signed (SHA-1/SHA-2) to SHA-2 only. No customer action required.
Windows Server 2012
Windows 8.1
Windows Server 2012 R2
Stand Alone security update KB4474419 was re-released to add missing EFI boot mangers. Please make sure that this version is installed.
Windows 7 SP1
Windows Server 2008 R2 SP1
Windows Server 2008 SP2
Signatures on the Certificate Trust Lists (CTLs) for the Microsoft Trusted Root Program changed from dual-signed (SHA-1/SHA-2) to SHA-2 only. No customer action required.
All supported Windows platforms
Windows Update SHA-1 based service endpoints are discontinued. This only impacts older Windows devices which have not updated with appropriate security updates. For more information, see KB4569557.
Windows 7
Windows 7 SP1
Windows Server 2008
Windows Server 2008 SP2
Windows Server 2008 R2
Windows Server 2008 R2 SP1
Microsoft retired content that is Windows-signed for Secure Hash Algorithm 1 (SHA-1) from the Microsoft Download Center. For more information, see the Windows IT pro blog SHA-1 Windows content to be retired August 3, 2020.
Windows Server 2000
Windows XP
Windows Server 2003
Windows Vista
Windows Server 2008
Windows 7
Windows Server 2008 R2
Windows 8
Windows Server 2012
Windows 8.1
Windows Server 2012 R2
Windows 10
Windows 10 Server
Current status
Windows 7 SP1 and Windows Server 2008 R2 SP1
The following required updates must be installed and then the device restarted before installing any update released August 13, 2019 or later. The required updates can be installed in any order and do not need to be reinstalled, unless there is a new version of the required update.
Servicing stack update (SSU) (KB4490628). If you use Windows Update, the required SSU will be offered to you automatically.
SHA-2 update (KB4474419) released September 10, 2019. If you use Windows Update, the required SHA-2 update will be offered to you automatically.
Important You must restart your device after installing all the required updates, before installing any Monthly Rollup, Security-only update, Preview of Monthly Rollup, or standalone update.
Windows Server 2008 SP2
The following updates must be installed and then the device restarted before installing any Rollup released September 10, 2019 or later. The required updates can be installed in any order and do not need to be reinstalled, unless there is a new version of the required update.
Servicing stack update (SSU) (KB4493730). If you use Windows Update, the required SSU update will be offered to you automatically.
The latest SHA-2 update (KB4474419) released September 10, 2019. If you use Windows Update, the required SHA-2 update will be offered to you automatically.
Important You must restart your device after installing all the required updates, before installing any Monthly Rollup, Security-only update, Preview of Monthly Rollup, or standalone update.
Frequently Ask Questions
General information, planning and issue prevention
The SHA-2 code-signing support was shipped early to ensure that most customers would have the support well in advance of Microsoft’s change to SHA-2 signing for updates to these systems. The stand-alone updates include some additional fixes and are being made available to ensure that all of the SHA-2 updates are in a small number of easily identifiable updates. Microsoft recommends that customers that maintain system images for these OSes to apply these updates to the images.
Starting with WSUS 4.0 on Windows Server 2012, WSUS already supports SHA-2-signed updates, and no customer action is needed for these versions.
Only WSUS 3.0 SP2 needs KB4484071installed to support SHA2 only signed updates.
Assume you run Windows Server 2008 SP2. If you dual-boot with Windows Server 2008 R2 SP1/Windows 7 SP1, the boot manager for this type of system is from the Windows Server 2008 R2/Windows 7 system. In order to successfully update both of these systems to use SHA-2 support, you must first update the Windows Server 2008 R2/Windows 7 system so that the boot manager is updated to the version that supports SHA-2. Then, update the Windows Server 2008 SP2 system with SHA-2 support.
Similar to the dual-boot scenario, the Windows 7 PE environment must be updated to SHA-2 support. Then, the Windows Server 2008 SP2 system must be updated to SHA-2 support.
Run Windows setup to completion and boot into Windows prior to installing August 13, 2019 or later updates
Open an administrator command prompt window, run bcdboot.exe. This copies the boot files from the Windows directory and sets up the boot environment. See BCDBoot Command-Line Options for more details.
Before installing any additional updates, install the August 13, 2019 re-release of KB4474419 and KB4490628 for Windows 7 SP1 and Windows Server 2008 R2 SP1.
Restart the operating system. This restart is required
Install any remaining updates.
Install the image on the disk and boot into Windows.
At the command prompt, run bcdboot.exe. This copies the boot files from the Windows directory and sets up the boot environment. See BCDBoot Command-Line Options for more details.
Before installing any additional updates, install the September 23, 2019 re-release of KB4474419 and KB4490628 for Windows 7 SP1 and Windows Server 2008 R2 SP1.
Restart the operating system. This restart is required
Install any remaining updates.
Yes, you will need to install the required updates before proceeding: SSU (KB4490628) and SHA-2 update (KB4474419). Also, you are required to restart your device after installing the required updates before installing any further updates.
Windows 10, version 1903 supports SHA-2 since it’s release and all updates are already SHA-2 only signed. There is no action needed for this version of Windows.
Windows 7 SP1 and Windows Server 2008 R2 SP1
Boot into Windows prior to installing any August 13, 2019 or later updates.
Before installing any additional updates, install the September 23, 2019 re-release of KB4474419 and KB4490628for Windows 7 SP1 and Windows Server 2008 R2 SP1.
Restart the operating system. This restart is required
Install any remaining updates.
Windows Server 2008 SP2
Boot into Windows prior to installing any July 9, 2019 or later updates.
Before installing any additional updates, install the September 23, 2019 re-release of KB4474419 and KB4493730 for Windows Server 2008 SP2.
Restart the operating system. This restart is required
Install any remaining updates.
Issue recovery
If you are seeing error 0xc0000428 with the message “Windows cannot verify the digital signature for this file. A recent hardware or software change might have installed a file that is signed incorrectly or damaged, or that might be malicious software from an unknown source.” please follow these steps to recover.
Start the operating system using recovery media.
Before installing any additional updates, install update KB4474419 that is dated September 23, 2019 or a later date using Deployment Image Servicing and Management (DISM) for Windows 7 SP1 and Windows Server 2008 R2 SP1.
At the command prompt, run bcdboot.exe. This copies the boot files from the Windows directory and sets up the boot environment. See BCDBoot Command-Line Options for more details.
Restart the operating system.
Halt deployment to other devices and do not restart any devices or VMs that have not already restarted.
Identify devices and VMs in restart pending state with updates released August 13, 2019 or later and open an elevated command prompt
Find the package identity for the update you want to remove by using the following command using the KB number for that update (replace 4512506 with the KB number you are targeting, if it is not the Monthly rollup released August 13, 2019): dism /online /get-packages | findstr 4512506
Use the following command to remove the update, replacing
with what was found in the previous command: Dism.exe /online /remove-package /packagename:
You will now need to install the required updates listed in the How to get this update section of the update you are trying to install, or the required updates listed above in the Current status section of this article.
Note Any device or VM you are currently receiving an error 0xc0000428 or that is starting into the recovery environment, you will need to follow the steps in the FAQ question for error 0xc0000428.
If you encounter these errors, you need to install the required updates listed in the How to get this update section of the update you are trying to install, or the required updates listed above in the Current status section of this article.
If you are seeing error 0xc0000428 with the message “Windows cannot verify the digital signature for this file. A recent hardware or software change might have installed a file that is signed incorrectly or damaged, or that might be malicious software from an unknown source.” please follow these steps to recover.
Start the operating system using recovery media.
Install the latest SHA-2 update (KB4474419) released on or after August 13, 2019, using Deployment Image Servicing and Management (DISM) for Windows 7 SP1 and Windows Server 2008 R2 SP1.
Reboot into the recovery media. This restart is required
At the command prompt, run bcdboot.exe. This copies the boot files from the Windows directory and sets up the boot environment. See BCDBoot Command-Line Options for more details.
Restart the operating system.
If you encounter this issue, you can mitigate this issue by opening a command prompt window and run the following command to install the update (replace the placeholder with the actual location and file name of the update):
This issue is resolved in KB4474419 released October 8, 2019. This update will install automatically from Windows Update and Windows Server Update Services (WSUS). If you need to install this update manually, you will need to use the workaround above.
Note If you previously installed KB4474419 released September 23, 2019, then you already have the latest version of this update and do not need to reinstall.
Источник
Item Preview
There Is No Preview Available For This Item
This item does not appear to have any files that can be experienced on Archive.org.
Please download files in this item to interact with them on your computer.
Show all files
1,792
Views
DOWNLOAD OPTIONS
Uploaded by
nguyenquanganh
on August 19, 2021
SIMILAR ITEMS (based on metadata)
September is upon us and with it brings the latest security patches from Microsoft and Adobe. Take a break from your regularly scheduled activities and join us as we review the details for security patches for this month.
Adobe Patches for September 2019
Adobe had a small release for September with only two patches covering a total of three CVEs in Adobe Flash and Application Manager. The update for Flash addresses two CVEs, both of which were reported through the ZDI program. The patch corrects a Use-After-Free (UAF) bug and a Same Origin Method Execution bug, both of which are rated Critical in severity. The Application Manager patch fixes an Important-severity DLL hijacking bug.
Neither of these bugs are listed as being publicly known or under active attack at the time of release.
Microsoft Patches for September 2019
This month, Microsoft released security patches for 80 CVEs plus two advisories. The updates cover Microsoft Windows, Internet Explorer, Microsoft Edge, ChakraCore, Office and Microsoft Office Services and Web Apps, Skype for Business and Microsoft Lync, Visual Studio, .NET Framework, Exchange Server, Microsoft Yammer, and Team Foundation Server. Of these 80 CVEs, 17 are listed as Critical, 62 are listed as Important, and one is listed as Moderate in severity. A total of 18 of these CVEs came through the ZDI program. Two of the bugs this month are listed as publicly known at the time of release, and two other bugs are listed as under active attack.
Let’s take a closer look at some of the more interesting patches for this month, starting with the bugs under active attack:
Note: Post-release, Microsoft revised their advisories to indicate these two CVEs are not under active attack.
— CVE-2019-1215 – Windows Elevation of Privilege Vulnerability
This patch corrects a local privilege escalation (LPE) in the Winsock2 Integrated File System Layer (ws2ifsl.sys). An attacker who exploits this vulnerability could go from User level to Administrator level access. Microsoft reports this is being actively used against both newer and older supported OSes, but they don’t indicate where. Interestingly, this file has been targeted by malware in the past, with some references going back as far as 2007. Not surprising, since malware often targets low-level Windows services. Regardless, since this is being actively used, put this one on the top of your patch list.
— CVE-2019-1214 – Windows Common Log File System Driver Elevation of Privilege Vulnerability
The other bug under active attack this month is also a Windows LPE, this time in the Common Log File System (CLFS) Driver. Again, an attacker could use this to elevate from a regular user to one with Administrative privileges. According to Microsoft, this CVE is only being seen targeting older operating systems. This is a fine time to remind you that Windows 7 is less than six months from end of support, which means you won’t be getting updates for bugs like this one next February. Patch your systems, then work on your upgrade strategy.
— CVE-2019-1289 – Windows Update Delivery Optimization Elevation of Privilege Vulnerability
This patch corrects a rather intriguing bug in the Windows Update Delivery Optimization (WUDO) feature found in Windows 10. This component is designed to reduce network bandwidth by having PCs grab updates from other peers on a network that already have downloaded the update. A local attacker could use this vulnerability to overwrite files they would normally not have permissions to. While this clearly could lead to an LPE on the local system, it’s not clear if it could be used to impact other systems through WUDO. If you’re using this feature, definitely roll this patch out quickly or disable the feature entirely.
— CVE-2019-1257 – Microsoft SharePoint Remote Code Execution Vulnerability
This patch addresses one of three Critical-rated deserialization bugs in the Business Data Connectivity Service of SharePoint. All three were reported by Markus Wulftange through the ZDI program. For this particular case, an attacker could execute their code under the context of the SharePoint application pool identity by uploading a specially crafted SharePoint application package to an affected server. Normally, you would need to authenticate to upload such a package – unless you have enabled anonymous access. But you wouldn’t do that. Would you? We’ll also have more details about these bugs on our blog in the near future. Stay tuned…
Here’s the full list of CVEs released by Microsoft for September 2019.
Of the public patches, one was highly publicized through a blog just after last patch Tuesday. The update closes a hole that could possibly allow attackers to hijack just about any application. Although we haven’t seen this being used in the wild yet, there’s a strong possibility that will happen. The other publicly known issue involves a bypass in the secure boot functionality. It sounds worse than it actually is, as this bug could only allow attackers with physical access to get debugging functionality.
You’ll notice there are Remote Desktop bugs being patched in this release as well, but unlike BlueKeep and DejaBlue, these members of the Blue Bug Group are all client-side. An attacker would need to convince someone to connect to their malicious RDP server or otherwise intercept (MITM) the traffic. It’s good to see these issues patched, but they don’t carry the urgency of the recent wormable bugs.
Of the remaining Critical-rated patches, nine correct browse-and-own scenarios in either a browser or a browser component. In reading these, Microsoft now seems to be referring to older Edge versions as “Microsoft Edge (EdgeHTML-based)” or “Microsoft Edge based on EdgeHTML” in order to distinguish it from Edge based on the Chromium source code.
More interestingly, this is the second month in a row with patch for an LNK vulnerability. Considering the history of exploits using LNK vulnerabilities, including recent malware campaigns using fileless execution and (of course) Stuxnet, these bugs always get attention from attackers.
The final Critical patch for September fixes a bug in the Azure DevOps (ADO) and Team Foundation Server (TFS) that could allow an attacker to execute code on the server in the context of the TFS or ADO service account. An attacker would need permissions to upload a file on a target repo, but if they do, they can achieve code execution once the affected server indexes their file. We’ll have additional details (with video!) about this bug in the near future as well.
Moving on to the Important-rated patches, the first that pops out is a Denial-of-Service (DoS) bug impacting Microsoft Exchange. An attacker could shut down an affected server just by sending it a specially crafted email. No user interaction is required. Neat. There’s also a patch that addresses an Exchange spoofing vulnerability, but that one requires a user to click a link.
Info disclosure bugs get their fair share of attention this month with 16 patches impacting Windows and Office components. There are also three cross-site scripting (XSS) and three spoofing bugs fixed this month to go with the many EoP and RCEs. Rounding out this month’s release, there are a few updates for the JET Database, Office, SharePoint, .NET and ASP.NET, and other various Windows components.
Looking at the advisories for September, the first is Microsoft’s version of the aforementioned patch for Flash in Internet Explorer. The other is the update to the Windows Servicing Stack, which adds updates for Windows 10 version 1607, Windows Server 2016, Windows 10 version 1809, and Windows Server 2019.
Looking Ahead
The next patch Tuesday falls on October 8, and we’ll return with details and patch analysis then. Until then, happy patching and may all your reboots be smooth and clean!
Описание и рекомендации
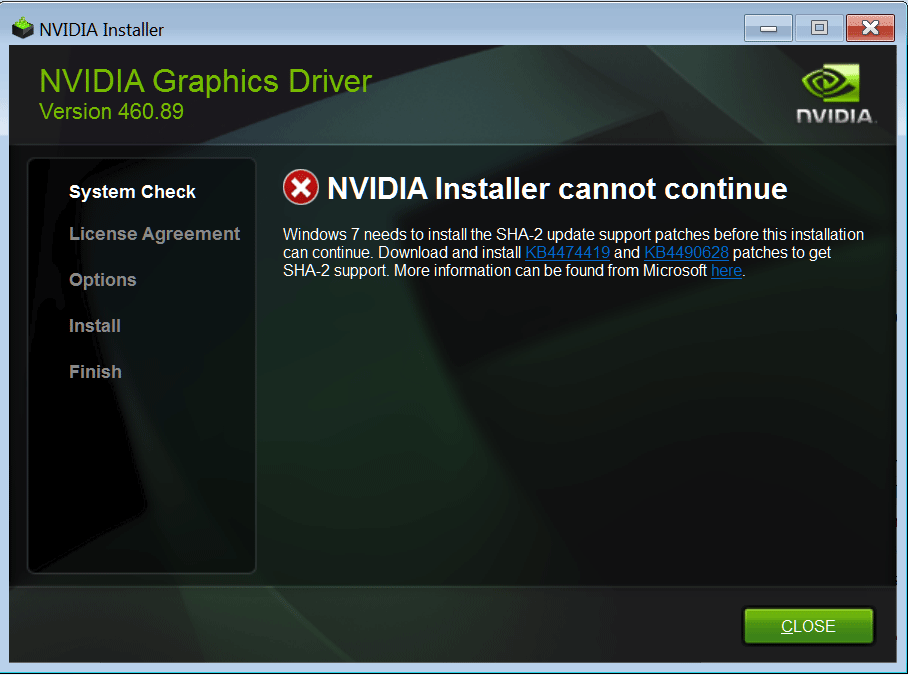
KB4474419 – критическое обновление Windows. Пакет предназначен для адаптации операционной системы при переходе к проверке подлинности патчей только на базе цифровой подписи SHA 2.
Предлагаемое обновление безопасности совместимо с «Семеркой», а также версиями OS – Windows Server 2008 R2, WSUS 3.0. Утилита распространяется бесплатно, поддерживает архитектуры процессора x64 и x32.
Обновления KB4474419 и KB4490628 для Windows 7
Причина выпуска софта – уязвимость алгоритма хеширования SHA-1. Прежняя концепция Виндовс предусматривала проверку подлинности системных обновлений и пользовательских программ на базе обоих стандартов. Применялась двойная подпись с кодировкой через SHA-1 и усовершенствованное семейство хэш-функций SHA-2.
Исключение потенциально уязвимого алгоритма вызывает системную проблему. Обновления, подписанные исключительно стандартом SHA-2, невозможно верифицировать для Windows 7.
В таком формате (без SHA-1) корпорация Microsoft начала выпуск патчей с 16 июля 2019. Все они несовместимы с «Семеркой» без апгрейда.
Адаптировать новые обновления под Windows 7 позволяет установка пакетов KB4474419 и KB4490628. Перечисленные утилиты встраивают поддержку верификации софта только через подписи SHA-2.
В последующих версиях операционных систем – Windows 10, 11 используется исключительно усовершенствованный алгоритм хэширования. Поэтому дополнительных действий со стороны пользователя не требуется.
Причины для инсталляции патчей
Переход на верификацию подлинности программных продуктов только по алгоритму SHA-2 – вопрос уже решенный.
Следовательно, отсутствие патчей KB4474419, KB4490628 может привести к нежелательным последствиям:
- невозможность обновлять далее операционную систему;
- сбой при установке антивирусов;
- отказ в инсталляции пользовательского софта;
- проблемы с обновлением драйверов.
Применительно к системным патчам – файлам формата msi, msu возникает стандартное сообщение «Произошла неизвестная ошибка Windows Update». Аналогичные сложности наблюдаются при попытке установки новых редакций антивирусов Касперский, ESET NOD 32 и прочих.
Как понять, что необходим действительно патч?
Простейший способ – инсталляция KB4474419, KB4490628. Пользователю даже неважно, какая редакция Windows 7 установлена на компьютере. Патчи, не совместимые с ОС, попросту не будут инсталлированы.
Если в процессе установки возникают сбои, рекомендуется:
- отключить антивирусный софт;
- убедиться, что в системе присутствует SP1;
- проверить ПК на наличие зловредного программного обеспечения и устранить его при обнаружении.
Разрешить ситуацию в последнем пункте лучше всего при помощи Dr.Web CureIt!. Действительно, другие антивирусные приложения могут не устанавливаться вследствие отсутствия патча.
Лечащая утилита CureIt! входит в состав пакета Dr.Web и распространяется бесплатно. Сразу после запуска приложения желательно убедиться, что закачаны последние обновления антивирусных баз.
Другое препятствие к установке KB4474419 – отсутствие сервисного пакета. Мы предлагаем не только патчи. Также вы можете скачать Service Pack 1 для Windows 7 без торрента, по прямой ссылке у нас на сайте.
Наиболее серьезный сбой происходит, когда инсталляция KB4474419 приостанавливается на 30% после перезагрузки ОС. Обоснованные объяснения для этой проблемы отсутствуют и уже не появятся, поскольку Windows 7 более не поддерживается разработчиком. В этом случае разрешить ситуацию поможет переустановка операционной системы.
Service Pack 1 для Windows 7
Фактически, это сервисный пакет, содержащий все обновления операционной системы, выпущенные до момента выхода SP1 (KB976932). Сравнительно с прежними версиями OS – Vista и XP, комплект патчей не столь масштабный. Но установка Service Pack 1 остается критически важной для работы некоторых системных программ и пользовательских приложений.
Заключение
Наши посетители могут скачать KB4474419 (KB4490628) бесплатно. Напоминаем, что инсталляция обновлений требует предварительной установки SP 1. Если сервисный пакет отсутствует, загрузить инсталлятор Service Pack 1 можно прямо с нашего сайта.
Скриншоты
Другие версии
Скачать KB4474419 для Windows 64-бита (ZIP)
Скачать KB4474419 для Windows 32-бита (ZIP)
Скачать KB4490628 для Windows 64-бита (ZIP)
Скачать KB4490628 для Windows 32-бита (ZIP)
Скачать Service Pack 1 (KB976932) для Windows 7 64-бита (ZIP)
Скачать Service Pack 1 (KB976932) для Windows 7 32-бита (ZIP)
Похожие программы
- Remove From My Forums
-
Question
-
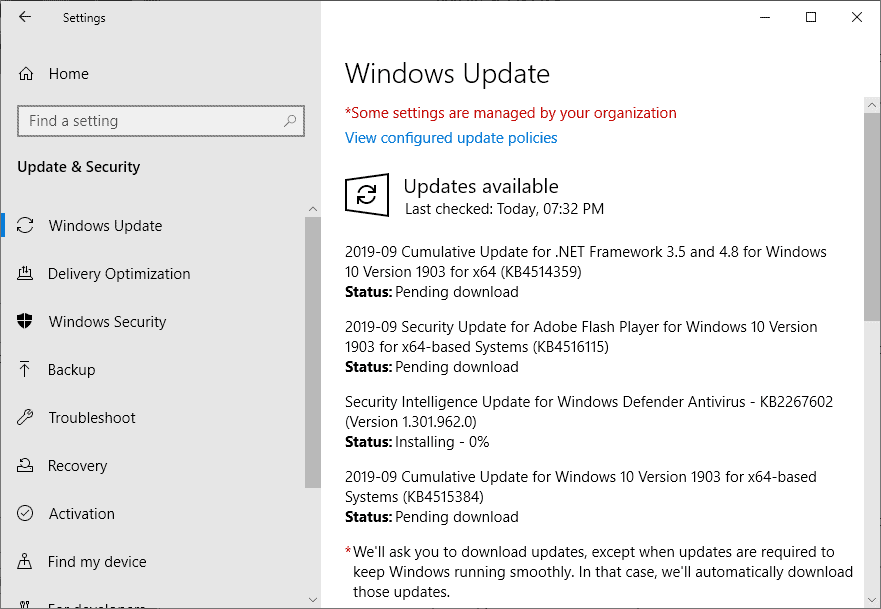
I’m on Windows 10 Professional Version 1903 (OS Build 18362.295). Everything has been working OK, and updates had been installing OK until now. I’ve received three updates;
2019-09 Cumulative Update for .NET Framework 3.5 and 4.8 for Windows 10 Version 1903 for x64 (KB4514359) — Error 0x800f0922
2019-09 Cumulative Update for Windows 10 Version 1903 for x64-based Systems (KB4515384) — Error 0x800f0922
2019-09 Security Update for Adobe Flash Player for Windows 10 Version 1903 for x64-based Systems (KB4516115) — Error 0x800f0922
And suddenly those won’t install and the only message displayed is, «There were problems installing some updates, but we’ll try again later.».
Earlier this year I had a similar problem on different computer, and someone gave me a fix that worked, but now I can’t find that post. There used to be a «My Posts» link, but it’s not there anymore, and I don’t remember the title to search
for it.I’d be very grateful if someone could either tell me how to clear the problem or how to find my earlier posts.
Capt. Dinosaur
Answers
-
Hello,
Please run Windows Update troubleshooter from Settings app > Update & security > Troubleshoot. See if it works.
If that doesn’t work, try this:
Open administrative Command Prompt and type following commands one-by-one followed by Enter key.
net stop wuauserv
net stop cryptSvc
net stop bits
net stop msiserver
Ren C:WindowsSoftwareDistribution SoftwareDistribution.old
Ren C:WindowsSystem32catroot2 Catroot2.old
net start wuauserv
net start cryptSvc
net start bits
net start msiserver
Close Command Prompt and see if Windows Updates works then.
Let us know if this helps!
Microsoft MVP (Windows and Devices for IT)
Windows Insider MVP
Windows Help & Support [www.kapilarya.com]
-
Marked as answer by
Wednesday, September 11, 2019 5:09 PM
-
Marked as answer by