I am using Git on Windows. I installed the msysGit package. My test repository has a self signed certificate at the server. I can access and use the repository using HTTP without problems. Moving to HTTPS gives the error:
SSL Certificate problem: unable to get local issuer certificate.
I have the self signed certificate installed in the Trusted Root Certification Authorities of my Windows 7 — client machine. I can browse to the HTTPS repository URL in Internet Explorer with no error messages.
This blog post by Philip Kelley explained that cURL does not use the client machine’s certificate store. I followed the blog post’s advice to create a private copy of curl-ca-bundle.crt and configure Git to use it. I am sure Git is using my copy. If I rename the copy; Git complains the file is missing.
I pasted in my certificate, as mentioned in the blog post, I still get the message «unable to get local issuer certificate».
I verified that Git was still working by cloning a GitHub Repository via HTTPS.
The only thing I see that’s different to the blog post is that my certificate is the root — there is no chain to reach it. My certificate originally came from clicking the IIS8 IIS Manager link ‘Create Self Signed Certificate’. Maybe that makes a certificate different in some way to what cURL expects.
How can I get Git/cURL to accept the self signed certificate?
asked May 27, 2014 at 9:15
RichardHowellsRichardHowells
7,3263 gold badges23 silver badges24 bronze badges
7
The problem is that git by default using the «Linux» crypto backend.
Beginning with Git for Windows 2.14, you can now configure Git to use SChannel, the built-in Windows networking layer as the crypto backend. This means that it will use the Windows certificate storage mechanism and you do not need to explicitly configure the curl CA storage mechanism: https://msdn.microsoft.com/en-us/library/windows/desktop/aa380123(v=vs.85).aspx
Just execute:
git config --global http.sslbackend schannel
That should help.
Using schannel is by now the standard setting when installing git for Windows, also it is recommended to not checkout repositories by SSH anmore if possible, as https is easier to configure and less likely to be blocked by a firewall it means less chance of failure.
answered Oct 30, 2018 at 12:41
5
Open Git Bash and run the command if you want to completely disable SSL verification.
git config --global http.sslVerify false
Note: This solution opens you to attacks like man-in-the-middle attacks.
Therefore turn on verification again as soon as possible:
git config --global http.sslVerify true
static_rtti
53k46 gold badges131 silver badges188 bronze badges
answered Dec 2, 2015 at 17:23
SamirSamir
6,4003 gold badges16 silver badges27 bronze badges
10
I had this issue as well. In my case, I was trying to get a post-receive Git hook to update a working copy on a server with each push. Tried to follow the instructions in the blog you linked to. Didn’t work for me as well and overriding the settings on a per-user basis didn’t seem to work either.
What I ended up having to do was disable SSL verification (as the article mentions) for Git as a whole. Not the perfect solution, but it’ll work until I can figure out a better one.
I edited the Git config text file (with my favorite line-ending neutral app like Notepad++) located at:
C:Program Files (x86)Gitetcgitconfig
In the [http] block, I added an option to disable sslVerify. It looked like this when I was done:
[http]
sslVerify = false
sslCAinfo = /bin/curl-ca-bundle.crt
That did the trick.
NOTE:
-
This disables SSL verification and is not recommended as a long term solution.
-
You can disable this per-repository which still isn’t great, but localizes the setting.
-
With the advent of LetsEncrypt.org, it is now fairly simple, automated and free to set up SSL as an alternative to self-signed certs and negates the need to turn off sslVerify.
answered Aug 6, 2014 at 3:33
kiddaileykiddailey
3,1323 gold badges21 silver badges21 bronze badges
6
kiddailey I think was pretty close, however I would not disable ssl verification but rather rather just supply the local certificate:
In the Git config file
[http]
sslCAinfo = /bin/curl-ca-bundle.crt
Or via command line:
git config --global http.sslCAinfo /bin/curl-ca-bundle.crt
Vimes
9,89717 gold badges62 silver badges86 bronze badges
answered Nov 3, 2014 at 8:36
OliverOliver
34.5k12 gold badges64 silver badges77 bronze badges
6
I faced this issue as well. And finally got resolved by getting guidance from this MSDN Blog.
Update
Actually you need to add the certificate in git’s certificates file curl-ca-bundel.cert that resides in Gitbin directory.
Steps
- Open your github page in browser, and click over lock icon in address bar.
- In the opened little popup up navigate to ‘view certificate’ link, it will open a popup window.
- In which navigate to certificates tab (3rd in my case). Select the top node that is root certificate. And press copy certificate button in the bottom and save the file.
- In file explorer navigate Gitbin directory and open curl-ca-bundle.crt in text editor.
- Open the exported certificate file (in step 3) in text editor as well.
- Copy all of the content from exported certificate to the end of curl-ca-bundle.crt, and save.
Finally check the status. Please note that backup curl-ca-bundle.crt file before editing to remain on safe side.
Franklin Yu
8,2905 gold badges42 silver badges54 bronze badges
answered Jun 23, 2015 at 17:18
Nadeem JamaliNadeem Jamali
1,3333 gold badges16 silver badges26 bronze badges
6
An answer to Using makecert for Development SSL fixed this for me.
I do not know why, but the certificate created by the simple ‘Create Self Signed Certificate’ link in IIS Manager does not do the trick. I followed the approach in the linked question of creating and installing a self-signed CA Root; then using that to issue a Server Authentication Certificate for my server. I installed both of them in IIS.
That gets my situation the same as the blog post referenced in the original question. Once the root certificate was copy/pasted into curl-ca-bundle.crt the git/curl combo were satisfied.
isherwood
56.4k16 gold badges108 silver badges151 bronze badges
answered May 27, 2014 at 15:12
RichardHowellsRichardHowells
7,3263 gold badges23 silver badges24 bronze badges
2
To avoid disabling ssl verification entirely or duplicating / hacking the bundled CA certificate file used by git, you can export the host’s certificate chain into a file, and make git use it:
git config --global http.https://the.host.com/.sslCAInfo c:/users/me/the.host.com.cer
If that does not work, you can disable ssl verification only for the host:
git config --global http.https://the.host.com/.sslVerify false
Note : Subjected to possible man in the middle attacks when ssl verification is turned off.
answered Feb 1, 2017 at 22:24
zionyxzionyx
1,86719 silver badges14 bronze badges
2
In case of github Repositories (or any none-self-signed certs), choosing below while installing Git-on-windows, resolved the issue.
answered Aug 15, 2017 at 15:01
Jawad Al ShaikhJawad Al Shaikh
2,4152 gold badges28 silver badges40 bronze badges
4
To completely detail out the summary of all the above answers.
Reason
This problem is occuring because git cannot complete the https handshake with the git server were the repository you are trying to access is present.
Solution
Steps to get the certificate from the github server
- Open the github you are trying to access in the browser
- Press on the lock icon in the address bar > click on ‘certificate’
- Go to ‘Certification Path’ tab > select the top most node in the hierarchy of certificates > click on ‘view certificate’
- Now click on ‘Details’ and click on ‘Copy to File..’ > Click ‘Next’ > Select ‘Base 64 encoded X509 (.CER)’ > save it to any of your desired path.
Steps to add the certificate to local git certificate store
-
Now open the certificate you saved in the notepad and copy the content along with —Begin Certificate— and —end certificate—
-
To find the path were all the certificates are stored for your git, execute the following command in cmd.
git config —list
-
Check for the key ‘http.sslcainfo’, the corresponding value will be path.
Note: If u can’t find the key http.sslcainfo check for Git’s default path: C:Program FilesGitmingw64sslcerts
- Now open ‘ca-bundle.crt’ present in that path.
Note 1 : open this file administrator mode otherwise you will not be able to save it after update. (Tip — you can use Notepad++ for this
purpose)Note 2 : Before modifying this file please keep a backup elsewhere.
- Now copy the contents of file mentioned in step 1 to the file in step 4 at end file, like how other certificates are placed in ca-bundle.crt.
- Now open a new terminal and now you should be able to perform operations related to the git server using https.
phifi
2,7131 gold badge20 silver badges39 bronze badges
answered Oct 27, 2020 at 8:58
Paul JasonPaul Jason
2613 silver badges3 bronze badges
1
I’ve just had the same issue but using sourcetree on windows Same steps for normal GIT on Windows as well. Following the following steps I was able to solve this issue.
- Obtain the server certificate tree
This can be done using chrome.
Navigate to be server address.
Click on the padlock icon and view the certificates.
Export all of the certificate chain as base64 encoded files (PEM) format. - Add the certificates to the trust chain of your GIT trust config file
Run «git config —list».
find the «http.sslcainfo» configuration this shows where the certificate trust file is located.
Copy all the certificates into the trust chain file including the «- -BEGIN- -» and the «- -END- -«. - Make sure you add the entire certificate Chain to the certificates file
This should solve your issue with the self-signed certificates and using GIT.
I tried using the «http.sslcapath» configuration but this did not work. Also if i did not include the whole chain in the certificates file then this would also fail. If anyone has pointers on these please let me know as the above has to be repeated for a new install.
If this is the system GIT then you can use the options in TOOLS -> options
GIt tab to use the system GIT and this then solves the issue in sourcetree as well.
answered Jul 19, 2016 at 13:59
JamesDJamesD
2,40623 silver badges38 bronze badges
4
I have had this issue before, and solve it using the following config.
[http "https://your.domain"]
sslCAInfo=/path/to/your/domain/priviate-certificate
Since git 2.3.1, you can put https://your.domain after http to indicate the following certificate is only for it.
answered Nov 9, 2017 at 7:50
1
Jan 2021 — Got around this in VS2019 by setting Menu > Git > Settings > Git Global Settings > Cryptographic Network Provider > [Secure Channel] instead of [OpenSSL]
Git SSL certificate problem unable to get local issuer certificate (fix)
PS: Didn’t need to set —global or —local http.sslVerify false. I was cloning an Azure DevOps repo which wasn’t using any self signed certs.. This seems like an issue with either VS2019 or Git for Windows.. They need to fix it !!
Dharman♦
29.3k21 gold badges79 silver badges131 bronze badges
answered Jan 15, 2021 at 18:28
veenzveenz
1011 silver badge4 bronze badges
1
In my case, as I have installed the ConEmu Terminal for Window 7, it creates the ca-bundle during installation at C:Program FilesGitmingw64sslcerts.
Thus, I have to run the following commands on terminal to make it work:
$ git config --global http.sslbackend schannel
$ git config --global http.sslcainfo /mingw64/ssl/certs/ca-bundle.crt
Hence, my C:Program FilesGitetcgitconfig contains the following:
[http]
sslBackend = schannel
sslCAinfo = /mingw64/ssl/certs/ca-bundle.crt
Also, I chose same option as mentioned here when installing the Git.
Hope that helps!
answered Jan 20, 2020 at 16:32
rc.adhikarirc.adhikari
1,8141 gold badge21 silver badges23 bronze badges
When using Windows, the problem resides that git by default uses the «Linux» crypto backend. Starting with Git for Windows 2.14, you can configure Git to use SChannel, the built-in Windows networking layer as the crypto backend. To do that, just run the following command in the GIT client:
git config --global http.sslbackend schannel
This means that it will use the Windows certificate storage mechanism and you don’t need to explicitly configure the curl CA storage (http.sslCAInfo) mechanism.
answered May 30, 2022 at 7:47
Nirbhay JhaNirbhay Jha
4615 silver badges12 bronze badges
One thing that messed me up was the format of the path (on my Windows PC). I originally had this:
git config --global http.sslCAInfo C:certscacert.pem
But that failed with the «unable to get local issuer certificate» error.
What finally worked was this:
git config --global http.sslCAInfo "C:\certs\cacert.pem"
answered Feb 21, 2019 at 18:16
solved my problem
git config —global http.sslBackend schannel
answered Jul 26, 2021 at 14:22
- Download certificate from this link:
https://github.com/bagder/ca-bundle - Add it to
C:Program FilesGitbinandC:Program FilesGitmingw64bin
Then try something like: git clone https://github.com/heroku/node-js-getting-started.git
answered May 6, 2017 at 15:44
ManjeetManjeet
89115 silver badges23 bronze badges
git config —global http.sslVerify false
answered Aug 10, 2021 at 16:49
2
To fix the especific error SSL certificate problem: unable to get local issuer certificate in git
I had the same issue with Let’s Encrypt certificates .
An web site with https we just to need :
SSLEngine On
SSLCertificateFile /etc/letsencrypt/live/example.com/cert.pem
SSLCertificateKeyFile /etc/letsencrypt/live/example.com/privkey.pem
Include /etc/letsencrypt/options-ssl-apache.conf
but git pull says :
fatal: unable to access 'https://example.com/git/demo.git/': SSL certificate problem: unable to get local issuer certificate
To fix it, we need also add:
SSLCertificateChainFile /etc/letsencrypt/live/example.com/chain.pem
answered Feb 20, 2020 at 23:30
SérgioSérgio
6,8381 gold badge47 silver badges52 bronze badges
In my case, I had to use different certificates for different git repositories.
Follow steps below (If you have a certificate of your repository, you can read from step 5)
-
Go to remote repository’s site. Ex: github.com, bitbucket.org, tfs.example…
-
Click Lock icon on the upper left side and click Certificate.
-
Go to Certification Path tab and double click to .. Root Certificate
-
Go to Details tab and click Copy to file.
-
Export/Copy certificate to wherever you want. Ex: C:certsexample.cer
-
Open git bash at your local repository folder and type:
$ git config http.sslCAInfo "C:certsexample.cer"
Now you can use different certificates for each repository.
Remember, calling with the --global parameter will also change the certificates of git repositories in other folders, so you should not use the --global parameter when executing this command.
answered Oct 13, 2020 at 18:02
okanokan
73010 silver badges11 bronze badges
git config --global http.sslbackend secure-transport
(had to do that after update to Big Sюr)
answered Apr 6, 2021 at 10:47
Anton TropashkoAnton Tropashko
5,3245 gold badges39 silver badges63 bronze badges
1
This works for me. I opened cmd line and ran following command. and pulled again.
git config —global http.sslVerify false
answered Jul 12, 2022 at 15:53
1
I’ve had the same problem from Azure DevOps (Visual Studio). Finally I’ve decided to clone my repo using SSH protocol because of i’ve prefered it instead of disabling SSL verification.
You only need to generate a SSH Key, you can do it so… SSH documentation
ssh-keygen
And then, import your public key on yout git host (like Azure Devops, Github, Bitbucket, Gitlab, etc.)
answered Nov 13, 2020 at 21:21
Brian OcampoBrian Ocampo
1,2321 gold badge12 silver badges21 bronze badges
I had this error occur when using visual studio. This occurs when you have the Cryptographic Network provider settings set to OpenSSL in the Visual Studio Options window. When I changed the setting to Secure Channel it solved it for me. This setting must have been set for me when I upgraded my VS.
answered Apr 26, 2021 at 16:51
Error
push failed
fatal: unable to access
SSL certificate problem: unable to get local issuer certificate
Reason
After committing files on a local machine, the «push fail» error can occur when the local Git connection parameters are outdated (e.g. HTTP change to HTTPS).
Solution
- Open the
.gitfolder in the root of the local directory - Open the
configfile in a code editor or text editor (VS Code, Notepad, Textpad) - Replace HTTP links inside the file with the latest HTTPS or SSH link available from the web page of the appropriate Git repo (clone button)
Examples:url = http://git.[host]/[group/project/repo_name] (actual path)replace it with either
url = ssh://git@git.[host]:/[group/project/repo_name] (new path SSH) url = https://git.[host]/[group/project/repo_name] (new path HTTPS)
answered Aug 26, 2020 at 7:25
Sven HaileSven Haile
1,01111 silver badges11 bronze badges
I have resolved the issue by adding below entry in ${HOME}/.gitconfig file
[remote «origin»]
proxy=
In most case it will happen when proxy enabled in your machine so above mentioned entry will fix this problem.
answered Oct 7, 2021 at 6:37
1
You might have a DNS issue and not a certificate issue, so before you disable SSL verification in your Git shell you should rule out a DNS problem. Cases such as these have been mentioned in Q&A forums such as https-issues-possibly-related-to-dns. If you are using WSL on Windows as your terminal, then you can try running sudo echo nameserver 8.8.8.8 > /etc/resolv.conf and then issue the git commands to see if that makes a difference. This does not seem to be a permanent DNS fix (lasting only the lifetime of your terminal session), but it could help you determine whether it is a DNS issue and not a certificate issue. You could also check this document on configuring your network to use a public DNS. Again, this is only to help you determine if your DNS settings might need adjusting in order to help resolve the certificate issues.
answered Aug 10, 2022 at 2:58
Download and install local certificate. Probably it is published at your company site. For instance, *.cer file.
-
Right click it and select
Install Certificate. ‘Certificate Inport Wizard’ will appear. SelectLocal Machine. PressNext, confirm. -
Select
Place all certificates in the following store, pressBrowseand selectTrusted Root Certification Authorities,OK,Finish.
Also you can check if other applications can fetch, pull or push data. For instance, in Android Studio or probably IDEA you should select in Settings this checkbox: Use credential helper.
answered Sep 19, 2022 at 7:35
CoolMindCoolMind
25.3k14 gold badges179 silver badges214 bronze badges
I got this error when trying to «clone» the project. One work-around is to just use the «download as zip» on the webpage, which, for me, achieved what I wanted to do.
answered Jan 18 at 18:00
JosephDoggieJosephDoggie
1,5024 gold badges24 silver badges55 bronze badges
This might help some who come across this error. If you are working across a VPN and it becomes disconnected, you can also get this error. The simple fix is to reconnect your VPN.
answered Dec 9, 2020 at 18:22
Platform Notice: Cloud, Server, and Data Center — This article applies equally to all platforms.
Problem
The following is seen on the command line when pushing or pulling:
SSL Certificate problem: unable to get local issuer
Cause
There are two potential causes that have been identified for this issue.
- A Self-signed certificate cannot be verified.
- Default GIT crypto backend (Windows clients)
Resolution
Resolution #1 — Self Signed certificate
Workaround
Tell git to not perform the validation of the certificate using the global option:
git config --global http.sslVerify false Please be advised disabling SSL verification globally might be considered a security risk and should be implemented only temporarily
Resolution — Client Side
Please notice that we refer to the Certificate Authority in this article by the acronym CA.
There are several ways this issue has been resolved previously. Below we suggest possible solutions that should be run on the client side:
- Ensure the root cert is added to git.exe’s certificate store. The location of this file will depend on how/where GIT was installed. For instance, the trusted certificate store directory for Git Bash is C:Program FilesGitmingw64sslcerts. This is also discussed on this Microsoft blog.
-
Tell Git where to find the CA bundle, either by running:
git config --system http.sslCAPath /absolute/path/to/git/certificateswhere
/absolute/path/to/git/certificatesis the path to where you placed the file that contains the CA certificate(s).or by copying the CA bundle to the
/bindirectory and adding the following to thegitconfigfile:sslCAinfo = /bin/curl-ca-bundle.crt - Reinstall Git.
-
Ensure that the complete certificate chain is present in the CA bundle file, including the root cert.
Resolution — Server Side
This issue can also happen on configurations where Bitbucket Server is secured with an SSL-terminating connector rather than a proxy
- Ensure that the Java KeyStore has the entire certificate chain (Intermediate CA and Root CA)
- View the Certificate Chain Details inside the KeyStore using a tool like the KeyStore Explorer to check
Resolution #2 — Default GIT crypto backend
When using Windows, the problem resides that git by default uses the «Linux» crypto backend, so the GIT operation may not complete occasionally. Starting with Git for Windows 2.14, you can configure Git to use SChannel, the built-in Windows networking layer as the crypto backend. To do that, just run the following command in the GIT client:
git config --global http.sslbackend schannelThis means that it will use the Windows certificate storage mechanism and you don’t need to explicitly configure the curl CA storage (http.sslCAInfo) mechanism.
What is the ‘ssl certificate problem unable to get local issuer certificate’ error
The unable to get local issuer certificate is a common issue faced by developers when trying to push, pull, or clone a git repository using Git Bash, a command-line tool specific to Windows.
The unable to get local issuer certificate error often occurs when the Git server’s SSL certificate is self-signed. The issue with self-signed certificates is that the private key associated with them cannot be revoked, making it a security vulnerability.
Alternatively, it can be due to incorrect configuration for Git on your system or when using git inside Visual Studio Code (VS Code) terminal.
What causes ‘ssl certificate problem unable to get local issuer certificate’
The unable to get local issuer certificate error is caused by the misconfiguration of the SSL certificate on your local machine. When pushing, pulling, or cloning, Git cannot verify your SSL certification, which leads to the error.
A valid HTTPS handshake requires both the client and the server to create a secure connection, allowing for safe communication between your local machine and where the source code is hosted. When the SSL certificate cannot be verified, Git cannot complete the HTTPS handshake with the server that hosts the repository.
When the unable to get local issuer certificate error occurs in VS Code, it is often because Visual Studio cannot locate the SSL certificate. This may be due to the path being misconfigured on the local machine.
How can you fix ‘ssl certificate problem unable to get local issuer certificate errors’
When ssl certificate problem unable to get local issuer certificate error is caused by a self-signed certificate, the fix is to add the certificate to the trusted certificate store.
By default, the trusted certificate store is located in the following directory for Git Bash:
C:Program FilesGitmingw64sslcerts
Open the file ca-bundle.crt located in the directory above, then copy and paste the Git SSL certificate to the end of the file. Once completed, save the file and run your git pull, push, or clone command.
Disabling SSL certificate validation is not recommended for security purposes. However, it is an option for fixing the ssl certificate problem unable to get local issuer certificate error.
You can disable SSL certificate validation locally in Git using the following command:
$ git -c http.sslVerify=false clone [URL]
You can also disable SSL certificate validation at a global level using the following command:
$ git config --global http.sslVerify false
To re-enable SSL certificate validation, use the following command:
$ git config --global http.sslVerify true
Another method for fixing the ssl certificate problem unable to get local issuer certificate error is to reinstall Git and choose the SSL transport backend option during the installation process.
If the unable to get local issuer certificate error occurs inside Visual Studio Code, you need to grant your repository access to the SSL certificates. To do this, git can be reconfigured with the --global flag on your SSL certificate configuration. This will give the Git server accessibility to the required SSL certificate.
To do this, run the following command in the Terminal:
git config --global http.sslBackend schannel
Accessibility to SSL certificate verification can also be set at the system level. To do this, you must be running in administrator mode before executing the following command:
git config --system http.sslBackend schannel
If the unable to get local issuer certificate error in Visual Studio Code is not due to accessibility but a location misconfiguration, this can be fixed by reassigning the path. This can be done through the following command:
git config --global http.sslcainfo "Path"
How to prevent ‘ssl certificate problem unable to get local issuer certificate’ errors
The main purpose of a SSL certificate is to confirm authentication so that the information passed between client and server is secure. When an unable to get local issuer certificate error occurs, a secure connection cannot be established, and the git client rejects your attempt to push, pull, or clone a repository for security reasons.
While disabling SSL certificates altogether is an option and common fix, it is not recommended. It opens up a security vulnerability for your repository and your local machine. Nevertheless, you can negate the unable to get local issuer certificate error by disabling SSL certificates at a local and global level. If SSL certificates are disabled at a global level, it is good to always enable them again so that other projects are not impacted by the intentional security disablement.
To prevent the error, ensure that you have a valid SSL certificate in your certificate store. Alternatively, you can reinstall your Git Bash with SSL Transport backend selected during the installation process.
If you are using Git via Visual Studio Code and have a valid SSL certificate in your certificate store but still encounter the certificate problem error, use the --global flag on your SSL certificate configuration to grant the Git server accessibility.
Kubernetes Troubleshooting With Komodor
We hope that the guide above helps you better understand the troubleshooting steps you need to take in order to fix the unable to get local issuer certificate error.
Keep in mind that this is just one of many Git errors that can pop up in your k8s logs and cause the system to fail. Due to the complex and distributed nature of k8s, the search for the root cause of each such failure can be stressful, disorienting, and time-consuming.
Komodor is a Kubernetes troubleshooting platform that turns hours of guesswork into actionable answers in just a few clicks. Using Komodor, you can monitor, alert and troubleshoot incidents in your entire K8s cluster.
For each K8s resource, Komodor automatically constructs a coherent view, including the relevant deploys, config changes, dependencies, metrics, and past incidents. Komodor seamlessly integrates and utilizes data from cloud providers, source controls, CI/CD pipelines, monitoring tools, and incident response platforms.
- Discover the root cause automatically with a timeline that tracks all changes made in your application and infrastructure.
- Quickly tackle the issue, with easy-to-follow remediation instructions.
- Give your entire team a way to troubleshoot independently, without having to escalate.
While cloning a Git repository using Git Bash (Git for Windows), you may get an error as follows:
fatal: unable to access ‘<URL>’: SSL certificate problem: unable to get local issuer certificate
In this short note i will show a fast workaround of this problem and how to resolve it properly.
Cool Tip: Decode SSL certificates using OpenSSL! Read more →
“Unable to get local issuer certificate” error usually happens when the Git server’s SSL certificate is Self-Signed or it has been issued by the corporate Certificate Authority (CA).
Workaround
As a workaround you can disable SSL certificate validation in Git as follows:
$ git -c http.sslVerify=false clone <URL>
Also you can temporary disable SSL certificate validation globally:
$ git config --global http.sslVerify false
To enable it back again, run:
$ git config --global http.sslVerify true
Resolution
The resolution of the “SSL certificate problem” is to add the Git server’s Self-Signed SSL certificate or the Root and Certificate Authority (CA) SSL certificates (if the Git server’s SSL certificate has been issued by your enterprise) to the trusted certificate store.
If you don’t have them locally, you can download these certificates from the Git server using your web-browser or using the command-line.
Cool Tip: How to get SSL certificate from a server (site’s URL)! Read more →
By default, the certificates store for Git Bash is located in the following directory:
C:Program FilesGitmingw64sslcerts
You can also open this directory in File Explorer by executing these commands in Git Bash:
$ cd /mingw64/ssl/certs/ $ explorer .
In this directory you should find a file called ca-bundle.crt.
Open ca-bundle.crt in a text-editor and copy/paste the Git server’s Self-Signed SSL certificate or the Root and Certificate Authority (CA) SSL certificates at the end of the file.
Once the file is saved, you should be able to run the git clone command in Git Bash without getting the “SSL certificate problem: Unable to get local issuer certificate”.
First published on MSDN on Dec 19, 2016
One of the most common issue with TFS/GIT users come across is the issue caused by self-signed certificates or the corporate certificates.
Error: SSL certificate problem: unable to get local issuer certificate
This Applied to:
TFS 2015 update 3
Git 2.10.0
Android studio 2.1.2
Java 1.7.45
We used Android studio and VSTS/TFS plugin to clone a GIT repository, we faced issues in retrieving the local issuer certificate. These are certificates that have not been signed by a known trusted certificate authority. The problem is that GIT/JAVA will not accept this certificate automatically. We need to force GIT/JAVA to accept the self-signed certificates.
Let’s now consider how to go about with the resolution,
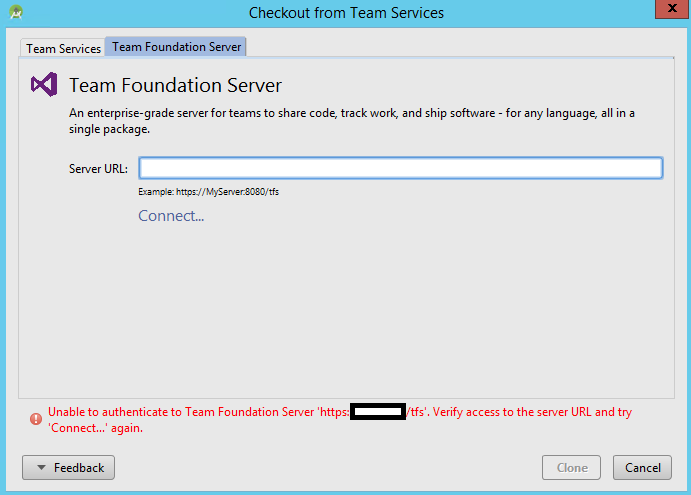
Initially, we faced issues with TFS authentication,
Unable to authenticate to TFS ‘https://server:8080/tfs». verify access to the server URL and try ‘Connect…’ again.
Very often this error can be interpreted to be the result of self-signed certificate. If the certificate in use is Self-signed or any other certificate that is private to the internal network. Java doesn’t trust such certificates and for which, we can
import the cert
into the trust store and make it to work.
The link explains how the certificate import works in a Linux machine (which is also applicable for Windows).
the “
keytool
” is under “
<JAVA_HOME>binkeytool.exe
”, and
the “
cacerts
” trust store is under “
<JAVA_HOME>jrelibsecuritycacerts
”.
<JAVA_HOME>
should be the
jre/jdk installation
used by IntelliJ.
This should have resolved the above TFS connectivity failure.
Note:
If you are using self-signed certificate, you may not be able to connect to TFS from the plugin
Error message:
Caused by: javax.net.ssl.SSLPeerUnverifiedException: Host name ‘server’ does not match the certificate subject provided by the peer (CN=server.corp.fabricam.com)
Providing the complete FQDN(
https://server.corp.fabricam.com/tfs
) instead of the server or the machine name (
https://server/tfs
) is mandatory as the canonical name is set to map to the FQDN.
After getting past the connectivity issue, there are instances in which we get error like the one below:
SSL certificate problem: unable to get local issuer certificate
In the android logs,
#git4idea.commands.GitHandler — fatal: unable to access ‘
https://server/tfs/DefaultCollection/_git/gitRepo/
‘: SSL certificate problem: unable to get local issuer certificate
Exception : javax.ws.rs.ProcessingException: javax.net.ssl.SSLHandshakeException: sun.security.validator.ValidatorException: PKIX path building failed: sun.security.provider.certpath.SunCertPathBuilderException: unable to find valid certification path to requested target
at org.glassfish.jersey.apache.connector.ApacheConnector.apply(ApacheConnector.java:498)
at org.glassfish.jersey.client.ClientRuntime.invoke(ClientRuntime.java:225)
at org.glassfish.jersey.client.JerseyInvocation$1.call(JerseyInvocation.java:655)
at org.glassfish.jersey.client.JerseyInvocation$1.call(JerseyInvocation.java:652)
at org.glassfish.jersey.internal.Errors.process(Errors.java:315)
at org.glassfish.jersey.internal.Errors.process(Errors.java:297)
at org.glassfish.jersey.internal.Errors.process(Errors.java:228)
at org.glassfish.jersey.process.internal.RequestScope.runInScope(RequestScope.java:423)
at org.glassfish.jersey.client.JerseyInvocation.invoke(JerseyInvocation.java:652)
at org.glassfish.jersey.client.JerseyInvocation$Builder.method(JerseyInvocation.java:387)
at org.glassfish.jersey.client.JerseyInvocation$Builder.get(JerseyInvocation.java:291)
at com.microsoft.alm.plugin.context.rest.VstsHttpClient.sendRequest(VstsHttpClient.java:30)
at com.microsoft.alm.plugin.context.ServerContextManager.checkTfsVersionAndConnection(ServerContextManager.java:257)
atcom.microsoft.alm.plugin.context.ServerContextManager.validateServerConnection(ServerContextManager.java:206) at com.microsoft.alm.plugin.context.ServerContextManager.validateServerConnection(ServerContextManager.java:171)
at com.microsoft.alm.plugin.idea.common.services.CredentialsPromptImpl.validateCredentials(CredentialsPromptImpl.java:68)
atcom.microsoft.alm.plugin.authentication.TfsAuthenticationProvider$TfsAuthenticator.run(TfsAuthenticationProvider.java:100)
There are 2 methods of dealing with this issue.
1.Disable SSL verification using below command,
git config —global http.sslVerify false
NOTE:
If you disable SSL certificates verification, then you are susceptible to Man in middle attacks.
2.The preferred method is import certificate authority (CA) to trusted certificate authority store.
If we can verify that disabling SSL verification works, then this article may help:https://blogs.msdn.microsoft.com/phkelley/2014/01/20/adding-a-corporate-or-self-signed-certific…
But, in case if the article doesn’t help,
Try exporting the certificate in all the levels again, following the instructions on the blog.Test certificates with curl.exe, to check if the SSL handshake is successful.
«c:Program FilesGitmingw64bincurl.exe» -v
https://server-name
-cacert c:pathtocertfile.cer
Now, import the certificate into the Git.exe cert store as we did before (also from blog). After importing the certificate, GIT clone’s files from the master branch.
For the complete encryption and the decryption, import the certificate into the Java cert store for Android Studio.
JRE that is now packaged with Android Studio 2.2. You can find it at the root of the Android Studio folder. “C:program filesAndroidAndroid Studiojre”
Hope this helps!
Content:
Ramandeep Singh
Review:
Romit Gulati
20 мая 2022
Как научить git доверять незнакомому CA сертификату, а не выключать верификацию SSL
Мануал сделан под Windows, но работать должен работать и с *nix/ использовать мы будем Openssl.
Илья Зверев
Архитектор IT-решений
Собственно, так выглядит ошибка
C:Git>git clone https://domain/gitrep/
Cloning into 'gitrep'...
fatal: unable to access 'https://domain/gitrep/': SSL certificate problem: unable to get local issuer certificateЧто нам может потребоваться из софта
- Cобственно git.
- Браузер — в статье я буду описывать вариант для chromium.
- Notepad++ или любой другой редактор, который аккуратно относится к кодировкам и символам переноса строк.
- Openssl — опционально. Можно посмотреть информацию о сертификатах.
- Keytool из jdk или jre, что бы прочитать файл со связкой сертификатов.
Как подтвердить ошибку
C:Git>openssl s_client -connect domain:443
CONNECTED(00000194)
depth=0 C = XX, ST = Xxxxxx, O = Xxxxxxxxx, OU = Xxxxxxxxx, CN = xxxxxxxx
verify error:num=20:unable to get local issuer certificate
verify return:1
depth=0 C = XX, ST = Xxxxxx, O = Xxxxxxxxx, OU = Xxxxxxxxx, CN = xxxxxxxx
verify error:num=21:unable to verify the first certificate
verify return:1Как видим, openssl тоже ничего не знает о сертификатах. Правда, openssl и git могут смотреть на разные хранилища известных корневых сертификатов (git сам отдаст ему нужное) − ошибка не обязательно воспроизведется. Поэтому нужно отдать openssl то же самое, что отдаст ему git.
Выполняем команду в git и находим расположение хранилища доверенных сертификатов:
C:Git>git config --system --list
http.sslcainfo=C:/Program Files/Git/mingw64/ssl/certs/ca-bundle.crt
http.sslbackend=openssl
diff.astextplain.textconv=astextplain
filter.lfs.clean=git-lfs clean -- %f
filter.lfs.smudge=git-lfs smudge --skip -- %f
filter.lfs.process=git-lfs filter-process --skip
filter.lfs.required=true
credential.helper=managerМы видим, что git хранит цепочку сертификатов в файле C:Program FilesGitmingw64sslcertsca-bundle.crt
Проверим, что выдаст openssl:
C:Git>openssl s_client -connect domain:443 -CAfile C:Program FilesGitmingw64sslcertsca-bundle.crt
CONNECTED(00000194)
depth=0 C = XX, ST = Xxxxxx, O = Xxxxxxxxx, OU = Xxxxxxxxx, CN = xxxxxxxx
verify error:num=20:unable to get local issuer certificate
verify return:1
depth=0 C = XX, ST = Xxxxxx, O = Xxxxxxxxx, OU = Xxxxxxxxx, CN = xxxxxxxx
verify error:num=21:unable to verify the first certificate
verify return:1Мы убедились — openssl не может подтвердить git корректность сертификатов, т.к. не знает корневого издателя сертификата.
При желании мы можем сами прочитать, что лежит в ca-bundle.crt используя keytool. Т.к. выдача будет длинная, сразу стоит отправить её в текстовый файл:
C:Git>keytool -printcert -v -file C:Program FilesGitmingw64sslcertsca-bundle.crt > certs_info.txtНачало файла будет выглядеть приблизительно так:
Certificate[1]:
Owner: C=ES, O=ACCV, OU=PKIACCV, CN=ACCVRAIZ1
Issuer: C=ES, O=ACCV, OU=PKIACCV, CN=ACCVRAIZ1
Serial number: 5ec3b7a6437fa4e0
Valid from: Thu May 05 13:37:37 MSK 2011 until: Tue Dec 31 12:37:37 MSK 2030
Certificate fingerprints:
MD5: D0:A0:5A:EE:05:B6:09:94:21:A1:7D:F1:B2:29:82:02
SHA1: 93:05:7A:88:15:C6:4F:CE:88:2F:FA:91:16:52:28:78:BC:53:64:17
SHA256: 9A:6E:C0:12:E1:A7:DA:9D:BE:34:19:4D:47:8A:D7:C0:DB:18:22:FB:07:1D:F1:29:81:49:6E:D1:04:38:41:13
Signature algorithm name: SHA1withRSA
Subject Public Key Algorithm: 4096-bit RSA key
Version: 3
Extensions:
...В файле будет весь список CA сертификатов, которым git доверяет.
Как сделать так, что бы git начал доверять CA сертификату сервера
Подготовим CA сертификат нашего https репозитория к дальнейшему использованию:
- Заходим браузером на адрес, и вне зависимости от того, выдает он ошибку подключения или нет, открываем на просмотр сертификат.
- Переходим на вкладку с цепочкой сертификации и ищем CA сертификат (самый верхний в цепочке). Открываем его на просмотр.
- Переходим на вкладку Details/Состав для CA сертификата. Нажимаем кнопку Copy to File/Копировать в файл в мастере выбираем X.509 (.CER) в Base64 кодировке. Сохраняем файл, например, с названием ca.crt.
Альтернативно можно выгрузить его с помощью openssl, т.к. в его выдаче при выполнении подключения мы получаем сертификат сервера (или цепочку сертификатов). Cохранив их в файл .cer, можно с помощью оснастки так же найти корневой сертификат.
Подготавливаем цепочку доверенных сертификатов к изменению
Выполняем команду в git и находим расположение хранилища доверенных сертификатов:
Ранее мы уже нашли, где git хранит свою цепочку доверенных ssl CA сертификатов: C:ProgramFilesGitmingw64sslcerts
Мне не понравилась папка, в которой расположен текущий. Поэтому я переместил файл и затем указал новый путь командой:
git config --system http.sslcainfo C:/Git/_certs/ca-bundle.crtЕсли вы не являетесь администратором машины или хотите сохранить изменения только для себя, команда немного изменится:
git config --global http.sslcainfo C:/Git/_certs/ca-bundle.crtВажно! По-хорошему, папка, в которой должна храниться цепочка, должна быть недоступна для редактирования никому, кроме администратора машины. В целях безопасности. Поэтому перемещение — опционально, и только если вы понимаете, что делаете.
Теперь открываем текстовым редактором (крайне желательно — не notepad! и желательно — делайте резервные копии!) наш ca-bundle.crt и видим сертификаты:
-----BEGIN CERTIFICATE-----
куча символов в Base64
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
еще одна куча
-----END CERTIFICATE-----
...Открываем файл ca.crt и извлекаем из него текст нашего CA сертификата.
Аккуратно копируем сертификат из ca.crt в конец файла ca-bundle.crt так, чтобы не сломать структуру файла, и сохраняем.
Можем убедиться, что все ок, последовательно, теми же командами, что помогли локализовать ошибку:
C:Git>keytool -printcert -v -file C:Git_certsca-bundle.crt > certs_info.txtВ конце файла последним мы должны увидеть данные нашего добавленного сертификата.
Далее убедимся, что openssl не выдаст больше ошибку о том, что не может подтвердить ssl сертификат сервера:
C:Git>openssl s_client -connect domain:443 -CAfile C:Git_certsca-bundle.crt
CONNECTED(00000194)
depth=0 C = XX, ST = Xxxxxx, O = Xxxxxxxxx, OU = Xxxxxxxxx, CN = xxxxxxxx
verify return:1
depth=0 C = XX, ST = Xxxxxx, O = Xxxxxxxxx, OU = Xxxxxxxxx, CN = xxxxxxxx
verify return:1Ошибки исправлены — теперь нужно снова попробовать склонировать git-репозиторий.
PROFIT! 
Если было полезно, подписывайтесь на наши каналы с экспертными материалами:
Youtube >
Telegram >
Quick step by step to fix SSL certificate problem: Unable to get local issuer certificate error.
Have you experienced the ‘SSL certificate problem unable: to get local issuer certificate’ problem while attempting to move from HTTP to HTTPS? We know how overwhelming it can be to deal with this issue but don’t let that frighten you. Here, we can help you fix it with this piece of writing and don’t make the wrong decisions like uninstalling your SSL certificate.
Regardless of which error pops up or the complexities involved in fixing it, never uninstall your SSL Certificate to get rid of SSL errors as doing that could prove to be fatal and expose you to serious security risks. Always remember that your SSL certificate protects the communication exchanged between the server and the browser, which prevents data interception of a third party.
Even, data privacy laws are getting stricter by the day, and therefore, you cannot make the unwise decision to uninstall your SSL. So, your only option is to get to the bottom of the ‘unable to get local issuer certificate’ error and fix it.
Before we help you do that, let us figure out how an SSL Certificate works and why it shows up the ‘curl: (60) SSL certificate problem: unable to get local issuer certificate’ or the ‘git SSL certificate problem unable to get local issuer certificate’ errors.
Why SSL Certificate Problem: Unable to get Local Issuer Certificate Error Happen?
Your SSL certificate’s primary purpose is to confirm authentication and ensure a secure exchange of information between the server and the client by referring to the HTTPS protocol. That is only possible when you have a working root certificate that is either directly or indirectly signed by a Certificate Authority. However, the error unable to get local issuer certificate’ occurs when the root certificate is not working properly especially when an SSL client makes an HTTPS request and during this, the client has to share an SSL certificate for identity verification.
Therefore, you need to take the necessary actions required to help bridge the gap.
How to Fix SSL Certificate Problem: Unable to get Local Issuer Certificate?
Now that we know the reasons for the ‘unable to get local issuer certificate’ glitch, it’s time to act. You could be experiencing this glitch due to many reasons, and those reasons could vary from software interfering in the SSL/TSL session or your Git application. Once you identify the cause, it becomes a whole lot easier to fix it. If you are unable to do that, then we recommend that you try out all the fixes one after another and something will work.
Unverified Self-signed SSL Certificate
Anyone can sign an SSL certificate by generating a signing key; however, the OS and the Web Browser may not be able to identify that. This could be the reason why you see the ‘SSL certificate problem: unable to get local issuer certificate’ or the ‘curl: (60) SSL certificate problem: unable to get local issuer certificate’ error.
Solution – Buy an SSL Certificate that is authenticated by a reputed certificate Authority and install it.
Alter the php.ini file to solve ‘unable to get local issuer certificate’
Log in to your web control panel such as cPanel and locate the file manager. You will then find the PHP software, and inside that, you can find the php.ini file that you need to edit. Follow the below-mentioned steps.
Change Php.ini
- Click on http://curl.haxx.se/ca/cacert.pem and download cacert.pem.
- After that, copy cacert.pem to openssl/zend, like ‘/usr/local/openssl-0.9.8/certs/cacert.pem’.
- Finally, navigate to the php.ini file, modify CURL. Add “cainfo = ‘/usr/local/openssl-0.9.8/certs/cacert.pem’” to modify it.
- Restart PHP
- Confirm if CURL can now read the HTTPS URL.
Without Altering php.ini file
Use the code given below:
$ch = curl_init();
$certificate_location = ‘/usr/local/openssl-0.9.8/certs/cacert.pem’;
curl_setopt($ch, CURLOPT_SSL_VERIFYHOST, $certificate_location);
curl_setopt($ch, CURLOPT_SSL_VERIFYPEER, $certificate_location);
Git Users
Most Git users experience the ‘SSL certificate problem: unable to get local issuer certificate’ or the ‘git SSL certificate problem unable to get local issuer certificate’ error at some point in time. If you have encountered it, then there are two ways of solving this — the first one is a permanent fix and the second one is a temporary fix, which we shall discuss below.
Permanent Fix
If you are a Git user-facing the ‘git SSL certificate problem unable to get local issuer certificate’ error, then you need to tell Git where the CA bundle is located.
To help Git find the CA bundle, use the below-mentioned command:
git config –system http.sslCAPath /absolute/path/to/git/certificates
Temporary Fix
To temporarily fix the ‘SSL certificate problem: unable to get local issuer certificate’ error, you could disable the verification of your SSL certificate. However, we recommend that you use it sparingly as it could lower your website’s security.
Use the following command to disable the verification of your SSL certificate:
git config –global http.sslVerify false
If neither of the two options work, consider removing and reinstalling Git.
Conclusion:
We are confident that one of the above ‘SSL certificate problem: unable to get local issuer certificate’ error fixes would work for you. Finally, we strongly recommend that you entirely avoid removing your SSL certificate. Your website needs to be protected, and one of your most robust defenses is an active SSL certificate.
Related SSL Errors:
- ERR_CONNECTION_REFUSED
- Secure Connection Failed in Firefox
- NET::ERR_CERT_AUTHORITY_INVALID
- ERR_SSL_VERSION_INTERFERENCE
- ERR_SSL_PROTOCOL_ERROR