Introduction
The SSH Permission denied error appears after permission-related settings are modified on the SSH server. Usual scenarios include a new package installation or the creation of new users.
In this tutorial, you will learn how to troubleshoot the SSH Permission denied error and reconnect to your SSH server.
Prerequisites
- SSH client on the local machine and SSH server on the remote system
- A user account to access the remote server (for password-based login)
- A user account with sudo or root privileges
The SSH Permission denied error appears when trying to SSH into a server:
Permission denied (publickey,gssapi-keyex,gssapi-with-mic)
Following the Permission denied statement, the bracket contains the attempted authentication methods that failed at the initiation of the connection. The error suggests that the public key is the issue, which is misleading.
One reason for the error may be sshd_config, the file that contains SSH server configuration. The other possibility is that the authorized_keys file has insufficient permissions. This file contains the list of public keys for the clients allowed to SSH into the server. Consequently, the system’s inability to read from the file results in the Permission denied error.
How to fix SSH Permission denied
Both solutions contain steps you need to perform on the server-side. Start by opening the terminal on your server and proceed with one of the solutions below.
Solution 1: Enable Password Authentication
If you want to use a password to access the SSH server, a solution for fixing the Permission denied error is to enable password login in the sshd_config file.
To do this, open the file in a text editor. This example uses the nano editor:
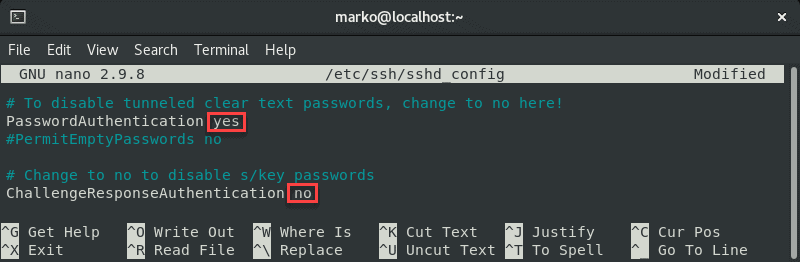
sudo nano /etc/ssh/sshd_configIn the file, find the PasswordAuthentication line and make sure it ends with yes.
Find the ChallengeResponseAuthentication option and disable it by adding no.
If lines are commented out, remove the hash sign # to uncomment them.
Save the file and exit.
Restart the SSH service by typing the following command:
sudo systemctl restart sshdSolution 2: Change File System Permissions
Using the password-based login as the SSH authentication method is not recommended due to security concerns. Therefore, the following solution may be preferable since it troubleshoots the public key authentication method.
First, open the sshd_config file using a text editor:
sudo nano /etc/ssh/sshd_configIn the file, make sure the following options are set as follows:
PermitRootLogin no
PubkeyAuthentication yes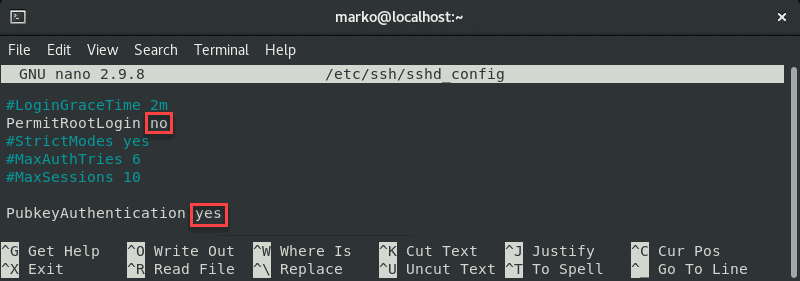
Note: The steps above are considered best security practices. If you need to use root login, set the relevant line to yes.
Comment out the GSSAPI-related options by adding the hash sign at the beginning of the line:
#GSSAPIAuthentication yes
#GSSAPICleanupCredentials no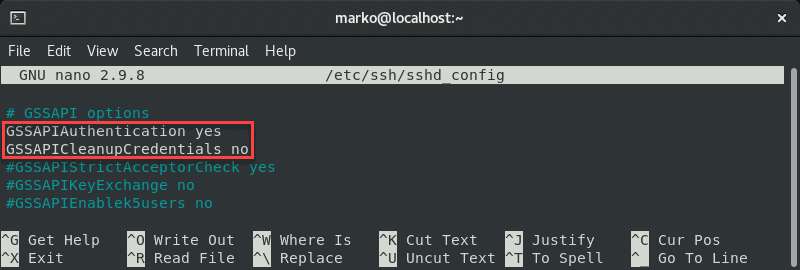
Also, make sure the UsePAM line is set to yes:
UsePAM yes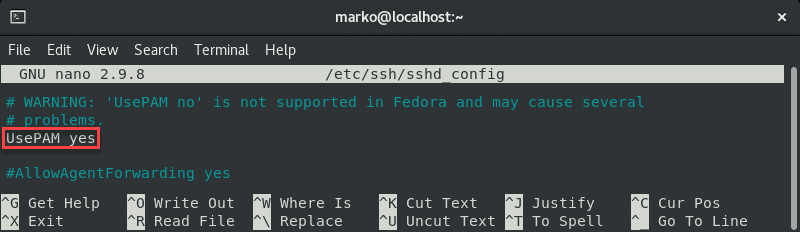
Save the file and restart the sshd service:
systemctl restart sshdNow navigate to your home folder and check the permissions:
ls -ld
If your owner permissions are not set to read, write, and execute (drwx------), use the chmod command to change them:
chmod 0700 /home/[your-username]Now go to the .ssh folder and recheck the permissions:
ls -ld
This directory should also have read, write, and execute permissions for the file owner. To enforce them, use chmod again:
chmod 0700 /home/your_home/.sshThe .ssh folder contains the authorized_keys file. Check its permissions with:
ls -ld authorized_keys
The file owner should have read and write permissions. To set them, use:
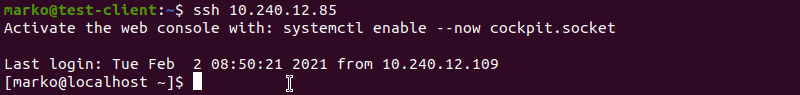
chmod 0600 /home/[username]/.ssh/authorized_keysNow try logging in with the key pair again. The output below shows a successful login attempt.
Conclusion
This tutorial covered the steps necessary to troubleshoot the SSH Permission denied (publickey,gssapi-keyex,gssapi-with-mic) error. By completing the steps in the guide, you should fix the error and successfully SSH into your server.
This question may have been asked before but I don’t understand the concept. Can you please help me here?
Weird issue from this morning .. see i just push my file to google cloud computing then showing below error.. I don’t know where to look that error.
ri@ri-desktop:~$ gcloud compute --project "project" ssh --zone "europe-west1-b" "instance"
Warning: Permanently added '192.xx.xx.xx' (ECDSA) to the list of known hosts.
Permission denied (publickey,gssapi-keyex,gssapi-with-mic).
ERROR: (gcloud.compute.ssh) [/usr/bin/ssh] exited with return code [255].
Al Lelopath
6,32313 gold badges81 silver badges135 bronze badges
asked Nov 26, 2014 at 15:18
5
This occurs when your compute instance has PermitRootLogin no in it’s SSHD config and you try to login as root. You can change the login user by adding username@ before the instance name. Here is a complete example:
gcloud compute instances create my-demo-compute
--zone us-central1-f
--machine-type f1-micro
--image-project debian-cloud
--image-family debian-8
--boot-disk-size=10GB
gcloud --quiet compute ssh user@hostname --zone us-central1-f
In the example above, gcloud will set the correct credentials and will make sure you login. You can add the --quiet to ignore the ssh-password question.
iBug
34.4k7 gold badges86 silver badges127 bronze badges
answered Mar 3, 2017 at 7:41
M. JepmaM. Jepma
911 silver badge1 bronze badge
One possible cause is that someone else in your project set the per-instance metadata for sshKeys (which overrides the project-wide metadata). When you run gcloud compute instances describe your-instance-name do you see a key called sshKeys in the metadata items?
It would also be helpful to see the contents of the latest log in ~/.config/gcloud/logs/. However, please make sure to scrub it of sensitive information.
answered Nov 26, 2014 at 20:24
2
I have a MacBook after facing with same problem, I re-created my SSH key in this format and works fine.
- Generate your key with:
ssh-keygen -t rsa -C your_username
- Copy the key and paste the ssh key under compute Engine metadata:
cat ~/.ssh/id_rsa.pub
It should work fine
answered Jan 18, 2020 at 14:05
Table of Contents
Hide
- What is Permission Denied (publickey, gssapi-keyex, gssapi-with-mic)?
-
Solution
- Step1: Permission for home and .ssh needs to be 0700 or drwx——
- Step 2: Permission of authorized_keys file needs to be 0600
- Step 3: Prevent insecure password authentication
- Step 4 – Restart SSH service
-
Conclusion
- Related Posts
While trying to ssh a host you might encounter an error – Permission Denied (publickey, gssapi-keyex, gssapi-with-mic). This says that you are not allowed to access the host via ssh.
But why you got this error?
Maybe because your public key is wrong. Or maybe there is another issue in the server and it is returning the wrong message.
Before solving any error, we should know the root causes. Permission denied means you can’t access the server. This could be due to wrong key or ssh server could not access the public keys file, authorized_keys.
Let’s understand the error first. It indicates these 3 things – publickey, gssapi-keyex and gssapi-with-mic.
gssapi stands for Generic Security Services Application Program Interface. According to Oracle docs – “gssapi provides a way for applications to protect data that is sent to peer applications; typically, this might be from a client on one machine to a server on another“.
gssapi is used by Kerberos. If you are not using Kerberos and only authenticating with password or ssh public key then you don’t need gssapi. Hence you can disable them. We will discuss about disabling gssapi in the next section.
Solution
To solve this issue you need to disable gssapi authentication as well as set appropriate permissions to the .ssh directory and .ssh/authorized_keys file.
First of all let’s set the permissions.
Step1: Permission for home and .ssh needs to be 0700 or drwx——
Owner permission for home and .ssh directory needs to be read, write, execute. That is, 0700 or drwx——. Follow these steps –
1. Move to your user folder in home directory using this command –
cd ~
2. Check directory permission using ls -ld command –
ls -ld
After running this command you will get output like this –
drwxr-xr-x 4 akamit akamit 4096 Sep 17 02:16
The owner permission needs to be read, write and execute (rwx). Group and others permission could be none for maximum security. In my case they are set to read and execute (r-x).
What are owner permissions? The first 3 characters after d represents owner permissions, next 3 group permissions and last 3 others permissions. Shown in the below code block –
# Owner Others # | | d rwx r-x r-x # | # Group
If your owner permission is different than this then set it using chmod command. You will need the absolute path to your user directory. If you don’t know that then use ~ to enter into your user directory and then run pwd for getting path –
chmod 0700 ~
# OR
cd ~
pwd
chmod 0700 /home/{YOUR_USERNAME}
3. Check permission for ~/.ssh directory
First move into .ssh directory using the below command –
cd ~/.ssh
Next, check the permission using ls -ld command –
ls -ld
The output should be read, write and execute permission for owner on this directory. For me the output looks like this –
You can see from the terminal image that the permission assigned to my .ssh directory is drwx------.
If it is not the same for you, then change the permission using chmod command –
chmod 0700 ~/.ssh
authorized_keys is the file inside .ssh directory which holds the list of all the public keys that are allowed to login using ssh. So, in order to allow an ssh request, the server needs to open this file and match the provided key with the keys in this file. If there is a match then authentication is successful. Otherwise permission denied.
What if public key is correct but server is not able to access authorized_keys file? In that case server will return permission denied. Although you have passed the correct key. That’s why it is required to have a proper permission on this file for owner account.
Check the permission using the below command –
ls -ld ~/.ssh/authorized_keys
It should return the permission as -rw-------. That is, the owner can read and write but not accessible to anybody else. For me the output looks like this –
[email protected]:~$ ls -la ~/.ssh/authorized_keys -rw------- 1 akamit akamit 553 Apr 17 10:33 /home/akamit/.ssh/authorized_keys [email protected]:~$
If the permission of this file is not the same as shown above then use chmod to change it –
chmod 0600 ~/.ssh/authorized_keys
Step 3: Prevent insecure password authentication
Password authentication should not be used for better security. We need to use public_key based ssh authentication. In this step we will turn off password authentication and enable public key authentication.
Open /etc/ssh/sshd_config file –
sudo vim /etc/ssh/sshd_config
This file will look like this –
# $OpenBSD: sshd_config,v 1.103 2022/04/09 20:41:22 tj Exp $ # This is the sshd server system-wide configuration file. See # sshd_config(5) for more information. # This sshd was compiled with PATH=/usr/bin:/bin:/usr/sbin:/sbin # The strategy used for options in the default sshd_config shipped with # OpenSSH is to specify options with their default value where # possible, but leave them commented. Uncommented options override the # default value. Include /etc/ssh/sshd_config.d/*.conf #Port 22 #AddressFamily any #ListenAddress 0.0.0.0 #ListenAddress :: #HostKey /etc/ssh/ssh_host_rsa_key #HostKey /etc/ssh/ssh_host_ecdsa_key #HostKey /etc/ssh/ssh_host_ed25519_key # Ciphers and keying #RekeyLimit default none # Logging #SyslogFacility AUTH #LogLevel INFO # Authentication: #LoginGraceTime 2m #PermitRootLogin prohibit-password #StrictModes yes #MaxAuthTries 6 #MaxSessions 10 #PubkeyAuthentication yes # Expect .ssh/authorized_keys2 to be disregarded by default in future. #AuthorizedKeysFile .ssh/authorized_keys .ssh/authorized_keys2 #AuthorizedPrincipalsFile none #AuthorizedKeysCommand none #AuthorizedKeysCommandUser nobody # For this to work you will also need host keys in /etc/ssh/ssh_known_hosts #HostbasedAuthentication no # Change to yes if you don't trust ~/.ssh/known_hosts for # HostbasedAuthentication #IgnoreUserKnownHosts no # Don't read the user's ~/.rhosts and ~/.shosts files #IgnoreRhosts yes # To disable tunneled clear text passwords, change to no here! PasswordAuthentication no #PermitEmptyPasswords no # Change to yes to enable challenge-response passwords (beware issues with # some PAM modules and threads) ChallengeResponseAuthentication no # Kerberos options #KerberosAuthentication no #KerberosOrLocalPasswd yes #KerberosTicketCleanup yes #KerberosGetAFSToken no # GSSAPI options #GSSAPIAuthentication no #GSSAPICleanupCredentials yes #GSSAPIStrictAcceptorCheck yes #GSSAPIKeyExchange no # Set this to 'yes' to enable PAM authentication, account processing, # and session processing. If this is enabled, PAM authentication will # be allowed through the ChallengeResponseAuthentication and # PasswordAuthentication. Depending on your PAM configuration, # PAM authentication via ChallengeResponseAuthentication may bypass # the setting of "PermitRootLogin without-password". # If you just want the PAM account and session checks to run without # PAM authentication, then enable this but set PasswordAuthentication # and ChallengeResponseAuthentication to 'no'. UsePAM yes #AllowAgentForwarding yes #AllowTcpForwarding yes #GatewayPorts no X11Forwarding yes #X11DisplayOffset 10 #X11UseLocalhost yes #PermitTTY yes PrintMotd no #PrintLastLog yes #TCPKeepAlive yes #PermitUserEnvironment no #Compression delayed #ClientAliveInterval 0 #ClientAliveCountMax 3 #UseDNS no #PidFile /var/run/sshd.pid #MaxStartups 10:30:100 #PermitTunnel no #ChrootDirectory none #VersionAddendum none # no default banner path #Banner none # Allow client to pass locale environment variables AcceptEnv LANG LC_* # override default of no subsystems Subsystem sftp /usr/lib/openssh/sftp-server # Example of overriding settings on a per-user basis #Match User anoncvs # X11Forwarding no # AllowTcpForwarding no # PermitTTY no # ForceCommand cvs server
We are interested in highlighted lines only. The values of these properties should be –
- PermitRootLogin – no
- PubkeyAuthentication – yes
- GSSAPIAuthentication – no (Or keep it commented out)
- GSSAPICleanupCredentials – yes (Or keep it commented out)
- UsePAM – yes
Step 4 – Restart SSH service
After making these changes, you need to restart SSH service. Use this command –
systemctl restart sshd
Conclusion
SSH throws permission denied error when either the public key is invalid or there is some problem with sshd configuration. It could be missing permissions on .ssh directory or authorized_keys file. In this article we saw the solution to all these issues. Follow the steps and you will be able to successfully log into the system through ssh.
I’m not able to SSH into the Fedora VM hosted in google cloud, from windows command prompt. I have tried to search for the answer in web but I couldn’t find any explanation/solution given for windows specifically.
I have performed below steps:
- Created a VM in google cloud with below image
fedora-cloud-base-gcp-34-1-2-x86-64
-
Allowed access to VM via port 22 in the firewall.
-
In windows command prompt ran below command to generate public and private key:
ssh-keygen -t ecdsa
-
Added the public key to VM.
Now when I run ssh username@host in command prompt from .ssh folder, I get below error:
PS C:Usersuser1.ssh> ssh -i C:/Users/user1/.ssh/id_ecdsa user1@34.19.24.7
The authenticity of host '34.19.24.7 (34.19.24.7)' can't be established.
ECDSA key fingerprint is SHA256:3/NMD26H/bhz9DJYHssTcFAKEpttgpobGac.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '34.19.24.7' (ECDSA) to the list of known hosts.
user1@34.19.24.7: Permission denied (publickey,gssapi-keyex,gssapi-with-mic).
Funny thins is I’m able to connect to other VM under same subnetwork which is created using «Debian» image.
What is causing this failure and how can I fix this ?
PFB the debug logs for this command:
PS C:Usersuser1.ssh> ssh -v -i C:/Users/user1/.ssh/id_ecdsa user1@34.19.24.7
OpenSSH_for_Windows_8.1p1, LibreSSL 3.0.2
debug1: Connecting to 34.19.24.7 [34.19.24.7] port 22.
debug1: Connection established.
debug1: identity file C:/Users/user1/.ssh/id_ecdsa type 2
debug1: identity file C:/Users/user1/.ssh/id_ecdsa-cert type -1
debug1: Local version string SSH-2.0-OpenSSH_for_Windows_8.1
debug1: Remote protocol version 2.0, remote software version OpenSSH_8.5
debug1: match: OpenSSH_8.5 pat OpenSSH* compat 0x04000000
debug1: Authenticating to 34.19.24.7:22 as 'user1'
debug1: SSH2_MSG_KEXINIT sent
debug1: SSH2_MSG_KEXINIT received
debug1: kex: algorithm: curve25519-sha256
debug1: kex: host key algorithm: ecdsa-sha2-nistp256
debug1: kex: server->client cipher: chacha20-poly1305@openssh.com MAC: <implicit> compression: none
debug1: kex: client->server cipher: chacha20-poly1305@openssh.com MAC: <implicit> compression: none
debug1: expecting SSH2_MSG_KEX_ECDH_REPLY
debug1: Server host key: ecdsa-sha2-nistp256 SHA256:3/NMD26H/bhz9DJYHssTcFAKEpttgpobGac
debug1: Host '34.19.24.7' is known and matches the ECDSA host key.
debug1: Found key in C:\Users\user1/.ssh/known_hosts:2
debug1: rekey out after 134217728 blocks
debug1: SSH2_MSG_NEWKEYS sent
debug1: expecting SSH2_MSG_NEWKEYS
debug1: SSH2_MSG_NEWKEYS received
debug1: rekey in after 134217728 blocks
debug1: pubkey_prepare: ssh_get_authentication_socket: No such file or directory
debug1: Will attempt key: C:/Users/user1/.ssh/id_ecdsa ECDSA SHA256:nGbnvW+SfJQfakeHcpXzw+8nJbtnqQWPNQtro+q/8 explicit
debug1: SSH2_MSG_EXT_INFO received
debug1: kex_input_ext_info: server-sig-algs=<ssh-ed25519,sk-ssh-ed25519@openssh.com,ssh-rsa,rsa-sha2-256,rsa-sha2-512,ssh-dss,ecdsa-sha2-nistp256,ecdsa-sha2-nistp384,ecdsa-sha2-nistp521,sk-ecdsa-sha2-nistp256@openssh.com,webauthn-sk-ecdsa-sha2-nistp256@openssh.com>
debug1: SSH2_MSG_SERVICE_ACCEPT received
debug1: Authentications that can continue: publickey,gssapi-keyex,gssapi-with-mic
debug1: Next authentication method: publickey
debug1: Offering public key: C:/Users/user1/.ssh/id_ecdsa ECDSA SHA256:nGbnvW+SfJQU9fakepXzw+8nJbtnqQWPNQtro+q/8 explicit
debug1: Authentications that can continue: publickey,gssapi-keyex,gssapi-with-mic
debug1: No more authentication methods to try.
1. The purpose of this post
I would demo how to solve this error when do ssh works in linux:
➜ .ssh ssh-copy-id -i id_rsa.pub [email protected]
/usr/bin/ssh-copy-id: INFO: Source of key(s) to be installed: "id_rsa.pub"
/usr/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed
/usr/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you are prompted now it is to install the new keys
[email protected]: Permission denied (publickey,gssapi-keyex,gssapi-with-mic).2. Environments
- Linux CentOS 7
3. Solution and commands
This error is caused by the misconfiguration of SSH service, it does not allow the password login, so the ssh-copy-id complains about the “permission denied(publickey,gssapi-keyex,gssapi-with-mic)”
How to solve it? Just enable the password authentication temporarily:
3.1 Open sshd_config
vi /etc/ssh/sshd_config3.2 find the line
find this line:
PasswordAuthentication no
change to:
PasswordAuthentication yes
3.3 restart ssh service
service sshd restart3.4 retry the ssh command
➜ .ssh ssh-copy-id -i id_rsa.pub [email protected]Everything should be ok now.
3.5 disable the password authentication of SSH service
Just undo the changes in the /etc/ssh/sshd_config, then restart the SSH service again.
Here is an issue hit by one of our trainees from OracleCloud certification (1Zo-160) course. He was trying to copy a file from the on-premise database to Cloud instance but it was failing with error Permission denied. So let me walk you through the issue and the fix.
Before proceeding further, let me first walk you through the different ways to connect to Oracle cloud instance. You can connect to Oracle Cloud instance using below three methods.
- SSH: You can connect to your cloud instance using SSH keys (Private and Public Keys) and Port 22. You have to generate Private and Public key pair (using PuttyGen) on your local PC and then create one cloud instance using that Public key. Then connect to the Cloud instance using private key (via Putty) and SSH Port 22.
- IPSec VPN: You can set up a VPN connection to establish a secure communication channel between your data center and your cloud instance. You can use either a supported third-party VPN device or Corente Services Gateway (an Oracle-provided IPsec solution) installed on a host.
- Fast Connect: This option allows you to access your instances through a direct connection from your on-premises. Transferring data over a direct connection provides better privacy and ensures consistent performance with dedicated bandwidth and controlled latency in your network traffic.
Now let’s look into the issue that trainee was hitting.
Issue:
Trainee was using first method that is SSH to connect to Cloud instance. He was trying to copy a file from on-premise database to cloud instance using scp command as shown below.
oracle@dba12c]$ scp -v –i oracleclouddba.ppk /tmp/test.txt oracle@128.140.230.121:/tmp/test.txt
Executing: program /usr/bin/ssh host 128.140.230.121, user oracle, command scp -v -d -t /tmp/test.txt
OpenSSH_5.3p1, OpenSSL 1.0.1e-fips 11 Feb 2013
debug1: Reading configuration data /etc/ssh/ssh_config
debug1: Applying options for *
debug1: Connecting to 128.140.230.121 [128.140.230.121] port 22.
debug1: Connection established.
debug1: identity file /home/oracle/.ssh/identity type -1
debug1: identity file /home/oracle/.ssh/identity-cert type -1
debug1: identity file /home/oracle/.ssh/id_dsa type -1
debug1: identity file /home/oracle/.ssh/id_dsa-cert type -1
debug1: Remote protocol version 2.0, remote software version OpenSSH_5.3
debug1: match: OpenSSH_5.3 pat OpenSSH*
debug1: Enabling compatibility mode for protocol 2.0
debug1: Local version string SSH-2.0-OpenSSH_5.3
debug1: SSH2_MSG_KEXINIT sent
debug1: SSH2_MSG_KEXINIT received
debug1: kex: server->client aes128-ctr hmac-sha1 none
debug1: kex: client->server aes128-ctr hmac-sha1 none
debug1: SSH2_MSG_KEX_DH_GEX_REQUEST(1024<2048<8192) sent
debug1: expecting SSH2_MSG_KEX_DH_GEX_GROUP
debug1: SSH2_MSG_KEX_DH_GEX_INIT sent
debug1: expecting SSH2_MSG_KEX_DH_GEX_REPLY
debug1: Host ‘129.150.204.101’ is known and matches the RSA host key.
debug1: Found key in /home/oracle/.ssh/known_hosts:2
debug1: ssh_rsa_verify: signature correct
debug1: SSH2_MSG_NEWKEYS sent
debug1: expecting SSH2_MSG_NEWKEYS
debug1: SSH2_MSG_NEWKEYS received
debug1: SSH2_MSG_SERVICE_REQUEST sent
debug1: SSH2_MSG_SERVICE_ACCEPT received
debug1: Authentications that can continue: publickey,gssapi-keyex,gssapi-with-mic
debug1: Next authentication method: gssapi-keyex
debug1: No valid Key exchange context
debug1: Next authentication method: gssapi-with-mic
debug1: Unspecified GSS failure. Minor code may provide more information
Credentials cache file ‘/tmp/krb5cc_54321’ not found
debug1: Unspecified GSS failure. Minor code may provide more information
Credentials cache file ‘/tmp/krb5cc_54321’ not found
debug1: Next authentication method: publickey
debug1: Trying private key: /home/oracle/.ssh/identity
debug1: Offering public key: /home/oracle/.ssh/id_rsa
debug1: Authentications that can continue: publickey,gssapi-keyex,gssapi-with-mic
debug1: Trying private key: /home/oracle/.ssh/id_dsa
debug1: Trying private key: /home/oracle/.ssh/id_ecdsa
debug1: No more authentication methods to try.
Permission denied (publickey,gssapi-keyex,gssapi-with-mic).
lost connection
Cause:
The trainee was using the extension “.ppk” for private key while Copying the file. Extension “.ppk” is only for windows and putty but if you do scp you need open ssh format.
Fix:
Please make sure to follow below points before copying on Cloud instance:
1. We need to convert the private key (.ppk) file as it will not work on Linux. We will use this converted open ssh file while copying the data on cloud from source. Steps to concert private file via puttygen are below
- Open Puttygen and click on conversion and Import file to import your private file.
- Click on conversions and then Export OpenSSH Key.
- Now give any name to the file without any Extension and select All Files(*) under save as and save the file.
2. After copying converted open ssh file on your server, give permission 600 to the file before running scp command.
If you want to learn more about Oracle Cloud and troubleshooting like above then check our Oracle Database Cloud Service (DBCS) Certification (1Z0-160), where we cover each and every topic required to clear your 1z0-160 certification with both a theoretical and practical approach.
====================================================================
UPDATE:
It turned out the configuration of sshd on host2 wont allow password
login. Thanks to people answered this.
====================================================================
Scenario:
Working with a company for my college project.
I need to use PuTTy to SSH into host1 first, and from there SSH into host2 (see below).
I was given a username and password on host2.
I do not have access of host2 at all, so I have no knowledge of its sshd_config.
This is what happened when I was trying to SSH into host2 from host1 :
ff@host1:~$ ssh -v host2
OpenSSH_5.1p1 Debian-5, OpenSSL 0.9.8g 19 Oct 2007
debug1: Reading configuration data /home/ff/.ssh/config
debug1: Applying options for *
debug1: Reading configuration data /etc/ssh/ssh_config
debug1: Applying options for *
debug1: Connecting to host2 [192.*.*.*] port 22.
debug1: Connection established.
debug1: identity file /home/ff/.ssh/identity type -1
debug1: identity file /home/ff/.ssh/id_rsa type -1
debug1: identity file /home/ff/.ssh/id_dsa type -1
debug1: Remote protocol version 2.0, remote software version OpenSSH_4.3
debug1: match: OpenSSH_4.3 pat OpenSSH_4*
debug1: Enabling compatibility mode for protocol 2.0
debug1: Local version string SSH-2.0-OpenSSH_5.1p1 Debian-5
debug1: SSH2_MSG_KEXINIT sent
debug1: SSH2_MSG_KEXINIT received
debug1: kex: server->client aes128-cbc hmac-md5 none
debug1: kex: client->server aes128-cbc hmac-md5 none
debug1: SSH2_MSG_KEX_DH_GEX_REQUEST(1024<1024<8192) sent
debug1: expecting SSH2_MSG_KEX_DH_GEX_GROUP
debug1: SSH2_MSG_KEX_DH_GEX_INIT sent
debug1: expecting SSH2_MSG_KEX_DH_GEX_REPLY
debug1: Host 'sd01' is known and matches the RSA host key.
debug1: Found key in /home/ff/.ssh/known_hosts:1
debug1: ssh_rsa_verify: signature correct
debug1: SSH2_MSG_NEWKEYS sent
debug1: expecting SSH2_MSG_NEWKEYS
debug1: SSH2_MSG_NEWKEYS received
debug1: SSH2_MSG_SERVICE_REQUEST sent
debug1: SSH2_MSG_SERVICE_ACCEPT received
debug1: Authentications that can continue: publickey,gssapi-with-mic,password
debug1: Next authentication method: gssapi-with-mic
debug1: Unspecified GSS failure. Minor code may provide more information
No credentials cache found
debug1: Unspecified GSS failure. Minor code may provide more information
No credentials cache found
debug1: Unspecified GSS failure. Minor code may provide more information
debug1: Next authentication method: publickey
debug1: Trying private key: /home/ff/.ssh/identity
debug1: Trying private key: /home/ff/.ssh/id_rsa
debug1: Trying private key: /home/ff/.ssh/id_dsa
debug1: Next authentication method: password
ff@sd01's password:
debug1: Authentications that can continue: publickey,gssapi-with-mic,password
Permission denied, please try again.
ff@sd01's password:
debug1: Authentications that can continue: publickey,gssapi-with-mic,password
Permission denied, please try again.
ff@sd01's password:
debug1: Authentications that can continue: publickey,gssapi-with-mic,password
debug1: No more authentication methods to try.
Permission denied (publickey,gssapi-with-mic,password).
and my /home/ff/.ssh/config :
Host *
# ForwardAgent no
# ForwardX11 no
# ForwardX11Trusted yes
# RhostsRSAAuthentication no
# RSAAuthentication yes
# HostbasedAuthentication no
BatchMode no
# CheckHostIP yes
# AddressFamily any
# ConnectTimeout 0
# StrictHostKeyChecking ask
# IdentityFile ~/.ssh/identity
# IdentityFile ~/.ssh/id_rsa
# IdentityFile ~/.ssh/id_dsa
# Port 22
# Protocol 2,1
# AuthorizedKeysFile .ssh/authorized_keys
# Cipher 3des
# Ciphers aes128-cbc,3des-cbc,blowfish-cbc,cast128-cbc,arcfour,aes192-cbc,aes256-cbc
# EscapeChar ~
# Tunnel no
# TunnelDevice any:any
# PermitLocalCommand no
SendEnv LANG LC_*
HashKnownHosts yes
GSSAPIAuthentication yes
GSSAPIDelegateCredentials no
I wonder is there anything I can do before go to the company.
I’m trying to ssh into a CentOS server which I have no control over.. the admin has added my public key to the server and insists the fault lies with me but I can’t figure out what is wrong.
Config in .ssh:
tim@tim-UX31A:~$ cat ~/.ssh/config
User root
PasswordAuthentication no
IdentityFile ~/.ssh/id_rsa
Permission on my key-files:
tim@tim-UX31A:~$ ls -l ~/.ssh/id_rsa*
-rw------- 1 tim tim 3326 Okt 20 17:28 /home/tim/.ssh/id_rsa
-rw-r--r-- 1 tim tim 746 Okt 20 17:28 /home/tim/.ssh/id_rsa.pub
Connection log which I can’t make any sense of:
tim@tim-UX31A:~$ ssh -vvv root@10.0.12.28
OpenSSH_7.2p2 Ubuntu-4ubuntu2.1, OpenSSL 1.0.2g 1 Mar 2016
debug1: Reading configuration data /home/tim/.ssh/config
debug1: Reading configuration data /etc/ssh/ssh_config
debug1: /etc/ssh/ssh_config line 19: Applying options for *
debug2: resolving "10.0.12.28" port 22
debug2: ssh_connect_direct: needpriv 0
debug1: Connecting to 10.0.12.28 [10.0.12.28] port 22.
debug1: Connection established.
debug1: identity file /home/tim/.ssh/id_rsa type 1
debug1: key_load_public: No such file or directory
debug1: identity file /home/tim/.ssh/id_rsa-cert type -1
debug1: Enabling compatibility mode for protocol 2.0
debug1: Local version string SSH-2.0-OpenSSH_7.2p2 Ubuntu-4ubuntu2.1
debug1: Remote protocol version 2.0, remote software version OpenSSH_6.6.1
debug1: match: OpenSSH_6.6.1 pat OpenSSH_6.6.1* compat 0x04000000
debug2: fd 3 setting O_NONBLOCK
debug1: Authenticating to 10.0.12.28:22 as 'root'
debug3: hostkeys_foreach: reading file "/home/tim/.ssh/known_hosts"
debug3: record_hostkey: found key type ECDSA in file /home/tim/.ssh/known_hosts:3
debug3: load_hostkeys: loaded 1 keys from 10.0.12.28
debug3: order_hostkeyalgs: prefer hostkeyalgs: ecdsa-sha2-nistp256-cert-v01@openssh.com,ecdsa-sha2-nistp384-cert-v01@openssh.com,ecdsa-sha2-nistp521-cert-v01@openssh.com,ecdsa-sha2-nistp256,ecdsa-sha2-nistp384,ecdsa-sha2-nistp521
debug3: send packet: type 20
debug1: SSH2_MSG_KEXINIT sent
debug3: receive packet: type 20
debug1: SSH2_MSG_KEXINIT received
debug2: local client KEXINIT proposal
debug2: KEX algorithms: curve25519-sha256@libssh.org,ecdh-sha2-nistp256,ecdh-sha2-nistp384,ecdh-sha2-nistp521,diffie-hellman-group-exchange-sha256,diffie-hellman-group-exchange-sha1,diffie-hellman-group14-sha1,ext-info-c
debug2: host key algorithms: ecdsa-sha2-nistp256-cert-v01@openssh.com,ecdsa-sha2-nistp384-cert-v01@openssh.com,ecdsa-sha2-nistp521-cert-v01@openssh.com,ecdsa-sha2-nistp256,ecdsa-sha2-nistp384,ecdsa-sha2-nistp521,ssh-ed25519-cert-v01@openssh.com,ssh-rsa-cert-v01@openssh.com,ssh-ed25519,rsa-sha2-512,rsa-sha2-256,ssh-rsa
debug2: ciphers ctos: chacha20-poly1305@openssh.com,aes128-ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.com,aes128-cbc,aes192-cbc,aes256-cbc,3des-cbc
debug2: ciphers stoc: chacha20-poly1305@openssh.com,aes128-ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.com,aes128-cbc,aes192-cbc,aes256-cbc,3des-cbc
debug2: MACs ctos: umac-64-etm@openssh.com,umac-128-etm@openssh.com,hmac-sha2-256-etm@openssh.com,hmac-sha2-512-etm@openssh.com,hmac-sha1-etm@openssh.com,umac-64@openssh.com,umac-128@openssh.com,hmac-sha2-256,hmac-sha2-512,hmac-sha1
debug2: MACs stoc: umac-64-etm@openssh.com,umac-128-etm@openssh.com,hmac-sha2-256-etm@openssh.com,hmac-sha2-512-etm@openssh.com,hmac-sha1-etm@openssh.com,umac-64@openssh.com,umac-128@openssh.com,hmac-sha2-256,hmac-sha2-512,hmac-sha1
debug2: compression ctos: none,zlib@openssh.com,zlib
debug2: compression stoc: none,zlib@openssh.com,zlib
debug2: languages ctos:
debug2: languages stoc:
debug2: first_kex_follows 0
debug2: reserved 0
debug2: peer server KEXINIT proposal
debug2: KEX algorithms: curve25519-sha256@libssh.org,ecdh-sha2-nistp256,ecdh-sha2-nistp384,ecdh-sha2-nistp521,diffie-hellman-group-exchange-sha256,diffie-hellman-group-exchange-sha1,diffie-hellman-group14-sha1,diffie-hellman-group1-sha1
debug2: host key algorithms: ssh-rsa,ecdsa-sha2-nistp256
debug2: ciphers ctos: aes128-ctr,aes192-ctr,aes256-ctr,arcfour256,arcfour128,aes128-gcm@openssh.com,aes256-gcm@openssh.com,chacha20-poly1305@openssh.com,aes128-cbc,3des-cbc,blowfish-cbc,cast128-cbc,aes192-cbc,aes256-cbc,arcfour,rijndael-cbc@lysator.liu.se
debug2: ciphers stoc: aes128-ctr,aes192-ctr,aes256-ctr,arcfour256,arcfour128,aes128-gcm@openssh.com,aes256-gcm@openssh.com,chacha20-poly1305@openssh.com,aes128-cbc,3des-cbc,blowfish-cbc,cast128-cbc,aes192-cbc,aes256-cbc,arcfour,rijndael-cbc@lysator.liu.se
debug2: MACs ctos: hmac-md5-etm@openssh.com,hmac-sha1-etm@openssh.com,umac-64-etm@openssh.com,umac-128-etm@openssh.com,hmac-sha2-256-etm@openssh.com,hmac-sha2-512-etm@openssh.com,hmac-ripemd160-etm@openssh.com,hmac-sha1-96-etm@openssh.com,hmac-md5-96-etm@openssh.com,hmac-md5,hmac-sha1,umac-64@openssh.com,umac-128@openssh.com,hmac-sha2-256,hmac-sha2-512,hmac-ripemd160,hmac-ripemd160@openssh.com,hmac-sha1-96,hmac-md5-96
debug2: MACs stoc: hmac-md5-etm@openssh.com,hmac-sha1-etm@openssh.com,umac-64-etm@openssh.com,umac-128-etm@openssh.com,hmac-sha2-256-etm@openssh.com,hmac-sha2-512-etm@openssh.com,hmac-ripemd160-etm@openssh.com,hmac-sha1-96-etm@openssh.com,hmac-md5-96-etm@openssh.com,hmac-md5,hmac-sha1,umac-64@openssh.com,umac-128@openssh.com,hmac-sha2-256,hmac-sha2-512,hmac-ripemd160,hmac-ripemd160@openssh.com,hmac-sha1-96,hmac-md5-96
debug2: compression ctos: none,zlib@openssh.com
debug2: compression stoc: none,zlib@openssh.com
debug2: languages ctos:
debug2: languages stoc:
debug2: first_kex_follows 0
debug2: reserved 0
debug1: kex: algorithm: curve25519-sha256@libssh.org
debug1: kex: host key algorithm: ecdsa-sha2-nistp256
debug1: kex: server->client cipher: chacha20-poly1305@openssh.com MAC: <implicit> compression: none
debug1: kex: client->server cipher: chacha20-poly1305@openssh.com MAC: <implicit> compression: none
debug3: send packet: type 30
debug1: expecting SSH2_MSG_KEX_ECDH_REPLY
debug3: receive packet: type 31
debug1: Server host key:
debug3: hostkeys_foreach: reading file "/home/tim/.ssh/known_hosts"
debug3: record_hostkey: found key type ECDSA in file /home/tim/.ssh/known_hosts:3
debug3: load_hostkeys: loaded 1 keys from 10.0.12.28
debug1: Host '10.0.12.28' is known and matches the ECDSA host key.
debug1: Found key in /home/tim/.ssh/known_hosts:3
debug3: send packet: type 21
debug2: set_newkeys: mode 1
debug1: rekey after 134217728 blocks
debug1: SSH2_MSG_NEWKEYS sent
debug1: expecting SSH2_MSG_NEWKEYS
debug3: receive packet: type 21
debug2: set_newkeys: mode 0
debug1: rekey after 134217728 blocks
debug1: SSH2_MSG_NEWKEYS received
debug2: key: /home/tim/.ssh/id_rsa (0x55ee619ab2b0), explicit, agent
debug2: key: /home/tim/.ssh/id_rsa (0x55ee619bcfa0), agent
debug2: key: tim@Tim-UX31A-Debian (0x55ee619b9370), agent
debug3: send packet: type 5
debug3: receive packet: type 6
debug2: service_accept: ssh-userauth
debug1: SSH2_MSG_SERVICE_ACCEPT received
debug3: send packet: type 50
debug3: receive packet: type 51
debug1: Authentications that can continue: publickey,gssapi-keyex,gssapi-with-mic,password
debug3: start over, passed a different list publickey,gssapi-keyex,gssapi-with-mic,password
debug3: preferred gssapi-keyex,gssapi-with-mic,publickey,keyboard-interactive
debug3: authmethod_lookup gssapi-keyex
debug3: remaining preferred: gssapi-with-mic,publickey,keyboard-interactive
debug3: authmethod_is_enabled gssapi-keyex
debug1: Next authentication method: gssapi-keyex
debug1: No valid Key exchange context
debug2: we did not send a packet, disable method
debug3: authmethod_lookup gssapi-with-mic
debug3: remaining preferred: publickey,keyboard-interactive
debug3: authmethod_is_enabled gssapi-with-mic
debug1: Next authentication method: gssapi-with-mic
debug1: Unspecified GSS failure. Minor code may provide more information
No Kerberos credentials available
debug1: Unspecified GSS failure. Minor code may provide more information
No Kerberos credentials available
debug1: Unspecified GSS failure. Minor code may provide more information
debug1: Unspecified GSS failure. Minor code may provide more information
No Kerberos credentials available
debug2: we did not send a packet, disable method
debug3: authmethod_lookup publickey
debug3: remaining preferred: keyboard-interactive
debug3: authmethod_is_enabled publickey
debug1: Next authentication method: publickey
debug1: Offering RSA public key: /home/tim/.ssh/id_rsa
debug3: send_pubkey_test
debug3: send packet: type 50
debug2: we sent a publickey packet, wait for reply
debug3: receive packet: type 51
debug1: Authentications that can continue: publickey,gssapi-keyex,gssapi-with-mic,password
debug1: Offering RSA public key: /home/tim/.ssh/id_rsa
debug3: send_pubkey_test
debug3: send packet: type 50
debug2: we sent a publickey packet, wait for reply
debug3: receive packet: type 51
debug1: Authentications that can continue: publickey,gssapi-keyex,gssapi-with-mic,password
debug1: Offering RSA public key: tim@Tim-UX31A-Debian
debug3: send_pubkey_test
debug3: send packet: type 50
debug2: we sent a publickey packet, wait for reply
debug3: receive packet: type 51
debug1: Authentications that can continue: publickey,gssapi-keyex,gssapi-with-mic,password
debug2: we did not send a packet, disable method
debug1: No more authentication methods to try.
Permission denied (publickey,gssapi-keyex,gssapi-with-mic,password).
In my view «SCP permission denied» error, is the most common error in the world of Linux. So, whether you are Linux admin or newbie, Every one of us would have encountered this error. At least, once in a lifetime, that I can bet.
As a Linux user for many years. I have faced this issue during SCP and SSH operations. So I am sure, if you will land on this page, you will get the solution to all your «permission denied error in Linux». Below mentioned are the samples of a few errors, you generally encounter. I am sure, at least one of the 9 solutions provided in this post will help you to resolve these issues.

- SCP permission denied
- SCP permission denied (publickey)
- Saving key «.ssh/id_rsa» failed: permission denied when SCP
- SCP permission denied ec2
- SCP permission denied AWS
- SCP permission denied, please try again
- SCP permission denied (publickey gssapi-keyex gssapi-with-mic)
- SCP permission denied (publickey). lost connection
Before explaining anything, Let me tell you all these problems occurs during file copy using SCP. So let’s understand about SCP utility first —
Table of Contents
- 1 What is SCP file transfer?
- 2 How do you SCP?
- 3 SCP permission denied issue
- 4 SCP permission denied (publickey) — AWS EC2 instance
- 5 Frequently Asked Questions (FAQ’s)
- 6 Video tutorial
- 7 Conclusion
What is SCP file transfer?
SCP stands for Secure copy. This program helps in copying a file or folder between two computers securely, whether local or remote. it uses SSH (secure shell) protocol in background. Additionally, The data and password are encrypted to secure sensitive information.
Using scp, you have option of file or directory copy between —
- Local to the local system
- Remote system to local system
- Local system to remote system
- Local system to AWS EC2 instance
How do you SCP?
There are a lot of options and switches to use with SCP command. Let me show you some basic commands, just to give you some understanding of SCP.
SCP syntax:-
$ scp [-346BCpqrTv] [-c cipher] [-F ssh_config] [-i identity_file] [-l limit] [-o ssh_option] [-P port] [-S program] [[user@]host1:]file1 … [[user@]host2:]file2
- Visit scp man page for more information on options or syntax.
$ man scp
How to Copy local files to remote host with SCP
$ scp file user@host:path
Host :- can be IP address or hostname of remote system
: (colon) :- helps scp to identify remote host
Username:- on remote host
SSH key or password :- is required to copy file using scp
Path :- Absolute or relative path for local file or directory
For example —
$ scp test.txt user1@ubuntu:/tmp
Copy Remote file to local host
$ scp user@host:file path
How to Copy directories to local host using SCP
$ scp -r user@host:directory_path path
Copy file between two remote hosts
$ scp user1@host1:file1.txt user2@host1:directory_path
Now when you know, what are basic scp commands. Time to know about public key authentication-
SCP requires a password to authenticate to the remote system. But in case you want to avoid it or using SCP in scripts, Public key is required.
Basically, you generate a public-private key pair on the client (local) and copy the public key to a remote system (server) into the authorized key.
To make you understand scp commands easily, i have shared my LAB details
Lab setup details —
Local server name — Server1 (Ubuntu 18.04)
Remote server name — Server2 (Ubuntu 20.04)
Source file — /test/file1.txt
Target directory — /remote-test
username — dev

Scenario1-
I am trying to copy /test/file1.txt from server1 (local) to server2 (remote) in /remote-test directory. I am also getting permission denied.
$ scp "local-file" "user@remote-host:/path-to-remote-dir"
Reference output


To resolve these error — perform below mentioned steps-
Solution 1 :- Double check your user and password
Please make sure, you have mentioned correct username and password in the command. This is one of the very basic mistakes, we do. So, you can try writing your password in notepad, copy and paste it in command prompt. When asked during SCP command.
i have validated username and password is correct in my case.
Solution 2 :- Check for remote path
Make sure, the path you have mentioned as the remote directory is correct. For example, in my case /remote-test is the remote directory and it’s correct.
Solution 3 :- Check for Read write access on remote directory
Double-check, whether your user mentioned in command have read-write (RW) access on the remote directory. For example, in my case «/remote-dir» must-have RW access to user «dev«.
Follow these steps to check —
-> Login to remote system (server2)
-> Run «ls» -ld command to check permissions of /remote-dir.
$ ls -ld "your-remote-dir"
Reference output

So, if you will see in image, /remote-dir only allows read, write and execute (rwx) permission to root user only. For group and others, it has read and execute (r-x) permission. So my user «dev» will be treated as other, and it won’t be able to write. As a result, I am getting SCP permission denied error.
-> Now to resolve this error, assign Read-write-execute (rwx) permission to everyone.
$ sudo chmod 777 "path-to-your-remote-directory"
Reference output

-> Run scp command again

Warning
Setting 777 permission on any directory is not secure. So once you are able to isolate the «SCP permission denied» issue. Either change ownership and set permission to 755.
If you are still facing permission denied error, move to next step
Solution 4 :- ownership issues (directory should be owned by user)
-> Login to your remote system (server2)
-> Change ownership of your remote directory for your user. For example, I will change ownership of /remote-dir to my user «dev» instead of «root«.
$ sudo chown -R dev:dev "path to your remote directory"
Reference output

-> Run scp command and it must work for you

Solution 5 :- Diagnose problem with scp -v command
Try to use -v (verbose) option to diagnose the issue with scp command.
For example
$ scp -v /test/file1.txt dev@192.168.126.129:/remote-dir output truncated - debug1: Sending environment. debug1: Sending env LANG = en_IN debug1: Sending command: scp -v -t /remote-dir Sending file modes: C0644 0 file1.txt Sink: C0644 0 file1.txt scp: /remote-dir/file1.txt: Permission denied
Check message after scp -v -t command, if it shows permission denied, Follow solution 3 or 4 as described in the post. it will resolve your issue.

Solution 6 :- Validate option -P is used for port not -p
When running SCP command Option -P is used to mention custom port, in case default port TCP 22 is not used. Sometimes, instead of -P, we use -p (lowercase) by mistake. For better understanding let me tell you the difference between these two —
- -p (lowercase):- Preserve access, modification and modes from the original file.
- -P (uppercase):- Specified customize port to connect remote host.
For example port 2314 is custom port instead of 22.
$ scp -P 2314 dev@192.168.126.129:/remote-dir/file1.txt /test/
SCP permission denied (publickey) — AWS EC2 instance

Scenario 2-
Try below mentioned solution, in case of SCP permission denied (publickey) with AWS ec2 instance —
If you have set up password-less authentication or you have permission key with you to authenticate remote system, you may encounter this error.
Have a check from Solution 1-6 mentioned in the post, if it doesn’t help move further —
Solution 7 :- Use -i option and provide «.pem» private key always
When you use SCP and don’t use -i option. It uses default ssh key under (~/.ssh/) directory. So always use -i option and provide the path to «.pem» key file.
For example «ubuntu.pem» is key file in my case.
$ scp -i ~/Desktop/ubuntu.pem ~/Desktop/test/code/www/index.html dev2@server:/var/wwwSolution 8 :- if using permission key SSH is working but not SCP
If you are able to ssh to the remote host using -i option and not able to scp. It means you are hitting a bug.
So instead of using -i «path to .pem file»
$ scp -i ~/Desktop/ubuntu.pem ~/Desktop/test/code/www/index.html dev@server2:/var/wwwuse -o "IdentityFile" option.
$ scp -o IdentityFile ~/Desktop/ubuntu.pem ~/Desktop/test/code/www/index.html dev@server2:/var/wwwSolution 9 :- Try removing your host entry from «known_hosts» file
Sometime, there may be issue due to old or incorrect host key. Delete that particular host from know_hosts file using editor or command as follows.
$ ssh-keygen -R hostname
or
$ vim ~/.ssh/known_hostsFrequently Asked Questions (FAQ’s)

Can ssh but not SCP permission denied?
Answer
Run SCP command -vv option and try to debug the issue. Depending upon error, follow solution 1-9 mentioned in this post to resolve your issue.
Will SCP overwrite existing file?
Answer
Yes, SCP utility finds a file with the same name on target, and you have write permission on it. SCP command will overwrite it. You can change the permission of the target file or directory. So that SCP complaints about permission issue and can avoid overwriting. Alternatively, you can use rsync tool, which has a lot of options to sync data.
Does SCP copy or move?
Answer
SCP mean secure copy, as name suggest it only copy files or directories. There is no file movement occurs.
Why SCP is not working?
Answer
There may be many reasons if SCP is not working. check SCP «-vvv» option and try to debug, why it’s not working. I have given 9 solutions to tackle different permission denied errors. you can refer to them.
How do I know if SCP is working?
Answer
if the exit status of your command is «0 » and you are able to copy your file or directory to remote host or AWS EC2 instance. You can be assured, SCP is working.
Why is permission denied error in Linux?
Answer
A lot of scenarios may be there for «permission denied error in Linux«. For example, if you don’t have read-write access on file or directory. Also, if you are trying to run a command which only root can run. You would need either root or sudo access to run these commands. For example, chmod or chown is one of these commands.
Video tutorial
If you need some video guidance. Check out this video on «SCP permission denied error«, The basic or common troubleshooting to start with.
Conclusion
There is no limit to issues or errors when you are in the technical world or on the way of learning. But I think your question on «why am I getting permission denied with SCP» will be resolved, once you will read the solution mentioned in this post. One or other solution will resolve your issue depending upon error code.
I hope you will leave with smile on your face, once your permission denied issue during scp will get resolve.
See you soon in the next post. Till that time keep learning.




