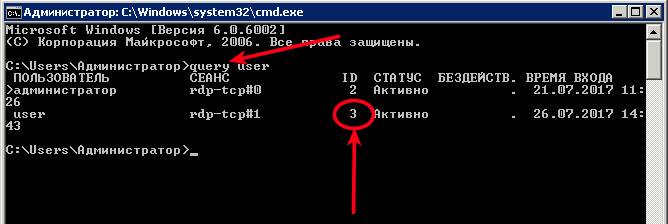
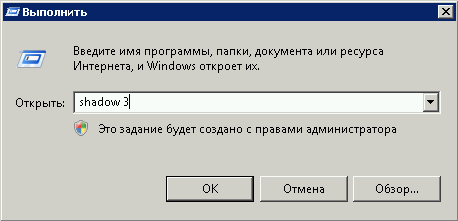
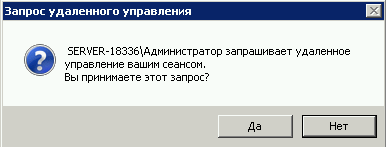
Задался я тут после одного инцидента как сделать быстрый бекап удаленного файла или папки с сетевой папки на сервере и заодно посмотреть кто это сделал.
Ну вопрос, кто это сделал нашли сразу через аудит (это рассмотрит в другой статье)
А вот вопрос, быстрого восстановления файла меня очень сильно заинтересовал. Я по своему обычаю на основной файловой помойке делаю бекап с помощью Acronis и дифференцированного бекапа (это будет отдельная статья)
В итоге решил на файловую помойку прикрутить еще один бекап и тут встал вопрос, либо сделать ее зеркалируемый и что бы один или несколько раз в неделю происходила синхронизация диска например с помощью штатной утилиты robocopy (и ее в одной из статей опишу) либо сделать на теневом копировании. Данный способ после совещания с коллегами был выбран как основой в виду его основного плюса с версиями файла и быстрого восстановления. Сказано сделано.
Поднимаем теневое копирование на Windows Server Standart 2008 R2
Для начала надо включить теневое копирование на диске, для это проделываем следующую операцию:
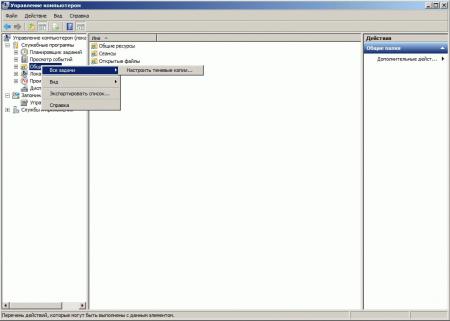
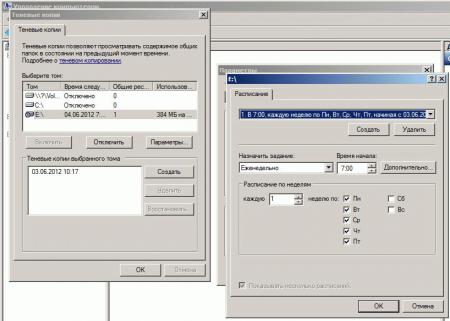
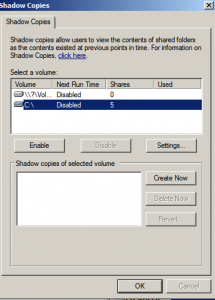
1) Пуск->Мой компьютер -> «щелкаем правой кнопкой» -> Управление Компьютером ->Общие Папки -> «щелкаем правой кнопкой» -> Все задачи -> Настроить теневые копии
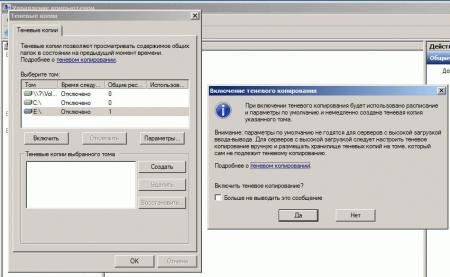
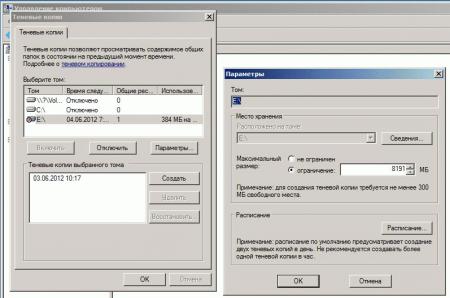
2) Теперь выбираем диск на котором будем делать Теневые копии и нажимаем Параметры. Тут мы задаем место где будут хранится теневые копии и расписание их создания.
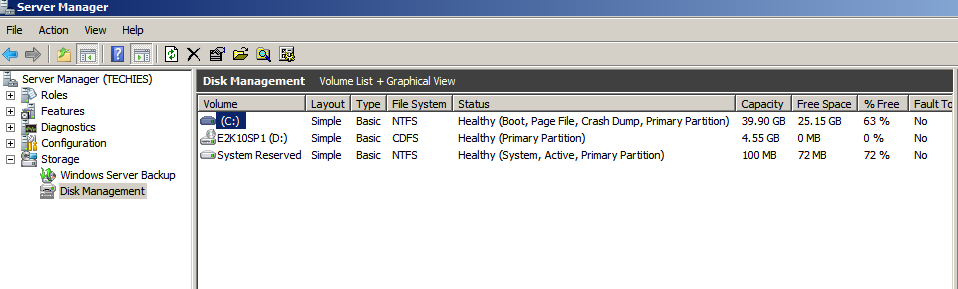
3) Далее выбираем диск на котором включаем теневое копирование, в моем случае это будет диск D и сразу при включении он начнем создавать первую копию диска.
тут же будут отражены все копии по времени когда либо создаваемые теневым копированием, которые можно удалять, либо Восстановить, но это я крайне не советую потому как он тогда затрет выбранной копией все что находится в сетевой папке.
Для работы с теневыми копиями и восстановлением файлов будет пользоваться по другому.
Ситуация 1
Допустим у нас теневая копия снимается один раз в день (в конце дня). И Вас просят восстановить файл который нечаянно был перезаписан (название файлов одно и тоже)
наши действия:
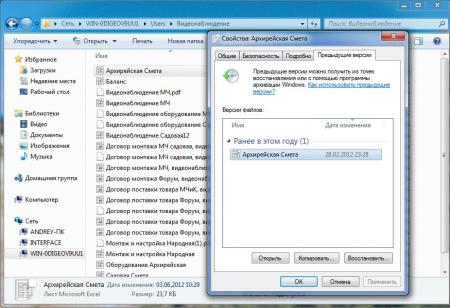
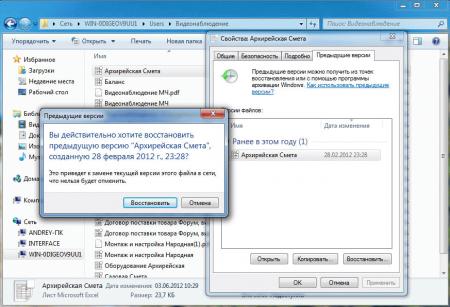
1) «щелкаем правой кнопкой» на файле который надо восстановить -> Свойство -> Предыдущая версия
2) выбираем ту версию которая нам нужна и восстаналиваем
Ситуация 2
К Вам вбегаю манагеры и кричат что кто то удалил их файл или папку с важными документами, а шеф уже ее ждет. 🙂
Действуем так:
1) «щелкаем правой кнопкой» на папке в которой лежал удаленный файл или папка -> Свойство -> Предыдущая версия
2) смотрим последние версии нашего бекапа и восстаналиваем файл или папку
3) ждем от коллег кофе или шоколадку))))
Видео по Теневому копированию (Shadow Copy)
nibbl
Я отец двух сыновей, ITишник, предприниматель и просто человек который любит делиться полезной информацией с другими людьми на такие темы как: Windows, Unix, Linux, Web, SEO и многое другое!
| Previous | Table of Contents | Next |
| Auditing Windows Server 2008 R2 File and Folder Access | Building a Windows Server 2008 R2 Network Load Balancing Cluster |
<google>BUY_WINSERV_2008R2</google>
Windows Server 2008 R2 Volume Shadow Copy is a mechanism whereby the contents of shared folders can be automatically backed up at pre-determined intervals to a shadow volume. Once implemented, shadow copy will backup the previous 64 versions of each file in the shadowed volume and provide users with the ability to restore files from any of the previous 64 versions without administrator intervention, enabling users to independently restore deleted, damaged or overwritten files. In addition to restoring individual files to a previous version, shadow copy also provides the ability to restore an entire volume.
Another use for shadow copy is to enable the backup of locked or open files. Ordinarily, if a file is currently open or locked by an application, tools such as Windows Backup will fail to backup the file. Shadow copy aware backup tools are, however, able to avoid this problem by using the Volume Shadow Copy Service API.
Contents
Contents
|
||
Shadow Copy Considerations
There are a number of issues that need to be considered when implementing shadow copy for shared folders. First and foremost the shared folders which are to be shadowed need to be identified. Secondly, a location for the shadow to be stored must be allocated. This can reside either on the same volume as the shared folders, or on a completely different volume or disk drive. Even before any data is shadowed, the shadow copy system requires 300MB of available space. The total amount of space required will depend on the size of the shared folder which is to be shadowed and the frequency and extent to which the files are likely to change (since shadow copy will only take new snapshots of files which have changed since the last snapshot). Finally, the time and frequency of the volume snapshots needs to be defined. By default, Shadow Copy performs a snapshot twice a day at 7:00am and 12:00pm.
Once the Shadow Copy system has been configured the shadow copy client needs to be set up on the systems of any users that are likely to need to be able to restore files in shared folders.
Using Computer Management to Enable and Configure Volume Shadow Copies
Shadow Copy is enabled on a per volume basis. Once configured on a volume, all shared folders residing on that volume will automatically be shadowed. Shadow Copy can be configured either graphically using the Computer Management tool or via the command prompt. Command-line configuration of Shadow Copy will be covered in a later section of this chapter. This section will focus on Computer Management configuration.
The first step is to launch the Computer Management configuration tool (Start -> All Programs -> Administrative Tools -> Computer Management). Once invoked, select Storage -> Disk Management from the tree in the left panel to display the disk and volume information for the local system. In the graphical view, right click on a volume and select on Properties to launch the properties dialog. In the properties dialog, select the Shadow Copy tab to display the Shadow Copy properties as illustrated in the following figure:
A useful shortcut to access the Shadow Copy property panel is to run vssuirun from a command prompt with elevated privileges.
The Select a volume section of the properties dialog lists the volumes present on the local system. Select the volume in this list for which Shadow Copy is to be enabled. With the volume selected click on the Settings button to display the following Shadow Copy Settings dialog box:
<google>WIN28BOX</google>
In the Located on this volume specify the volume on which the shadow copies are to be stored. This can be either the current volume or a different volume on the system. The Details button displays free and total disk space information for the currently specified volume. Once a suitable volume for the shadow copies has been selected the maximum size to be made available for the shadow copies may be defined. This can either be set to Maximum size which will use all available space on the specified volume, or capped to a specific size (keeping in mind that a minimum of 300MB is required for the shadow storage volume even before any snapshots are taken). Shadow Copy uses a differential approach to backing up files in that only files that have changed since the last snapshot are copied. For certain files, Shadow Copy also only copies the part of the file that has changed, rather than the entire file. As such, it is not necessary to reserve 64 times the size of the volume to be copied since only parts of the volume will be copied with each snapshot.
Schedule the shadow copy snapshots by clicking on the Schedule… button. By default, Windows configures two snapshots each day (at 7:00am and 12:00pm respectively). To remove a currently defined snapshot, select it from the drop down list and click on Delete. To modify a run, select it from the drop down list, modify the settings in the lower section of the dialog and click on OK.
To specify additional schedules, click on the New button and specify the days and time of the snapshot. Note that snapshots can also be configured to occur at user logon, system startup and even when the system is idle. In fact, Windows Server 2008 provides considerable flexibility in terms of scheduling shadow copies. It is important to keep in mind, however, that there are disadvantages to running a shadow copy too frequently. Firstly, shadow copies are resource intensive tasks, especially on large volumes where many files are subject to frequent changes. Repeated snapshots during periods when the server is heavily utilized may well degrade overall system performance. Secondly, it is important to keep in mind that Shadow Copy retains the last 64 versions of a file. Therefore, if a snapshot is run every hour, the oldest restore point available to a user will be approximately two and half days in the past. If, on the other hand, snapshots are taken twice a day, the user will have the luxury of restoring a file from a point as much as 32 days ago. It is important, therefore, to strike a balance between longevity and frequency.
The following screenshot illustrates the Shadow Copy scheduling dialog:
Once the schedules have been configured, click on OK to dismiss the scheduling dialog. Click OK once again in the Settings dialog to return to the Shadow Copy properties panel. At this point, the volume for which a schedule has been defined will have a small clock image superimposed over the volume icon and will indicate that 0 bytes of shadow copy storage have been used. The next step is to enable shadow copies on the volume by selecting the volume from the list and clicking on the Enable button. The volume in the list will update to display the date and time of the next scheduled copy and provide a summary of the current level of storage space used for the shadow copies.
To initiate a manual shadow copy now, or at any other time, simply select the volume to be copied from the list in the Shadow Copy properties panel and click on the Create Now button.
Restoring an Entire Volume
To restore an entire volume, access the Shadow Copy property panel either from Computer Management as outline above, or by running vssuirun from a command prompt with elevated privileges. Once loaded, select the desired volume followed by a snapshot from which to restore from the Shadow copies of selected volume list and click on the Revert Now… button. This will revert all shared folders on the selected volume to their state at the point that the selected shadow copy was made.
It is important to note that restoration of entire volumes is not possible on system volumes since this would, in all probability, severely interfere with the current system state.
Configuring and Enabling Shadow Copy from the Command Line
A significant amount of Shadow Copy functionality can be accessed via the command line using the vssadmin tool, which is the focus of this section.
In order to obtain information about shadow copies configured on a system, use vssadmin list shadows:
C:Windowssystem32>vssadmin list shadows
vssadmin 1.1 - Volume Shadow Copy Service administrative command-line tool
(C) Copyright 2001-2005 Microsoft Corp.
Contents of shadow copy set ID: {67f25a62-12f1-4e34-b14a-3b57cb03f4f8}
Contained 1 shadow copies at creation time: 8/22/2008 12:29:56 PM
Shadow Copy ID: {bee54c7f-22a4-4bd0-b6c4-20bc51a8cded}
Original Volume: (E:)\?Volume{9fa5f191-6554-11dd-9ce6-000c295707db}
Shadow Copy Volume: \?GLOBALROOTDeviceHarddiskVolumeShadowCopy2
Originating Machine: winserver-2
Service Machine: winserver-2
Provider: 'Microsoft Software Shadow Copy provider 1.0'
Type: ClientAccessible
Attributes: Persistent, Client-accessible, No auto release, No writers,
Differential
Contents of shadow copy set ID: {24c56736-d082-4fa5-ac97-961bd708b4d2}
Contained 1 shadow copies at creation time: 8/22/2008 1:00:04 PM
Shadow Copy ID: {e5a5d032-5449-4375-b4c2-5adf12fedc5d}
Original Volume: (E:)\?Volume{9fa5f191-6554-11dd-9ce6-000c295707db}
Shadow Copy Volume: \?GLOBALROOTDeviceHarddiskVolumeShadowCopy3
Originating Machine: winserver-2
Service Machine: winserver-2
Provider: 'Microsoft Software Shadow Copy provider 1.0'
Type: ClientAccessible
Attributes: Persistent, Client-accessible, No auto release, No writers,
Differential
Contents of shadow copy set ID: {95618a5e-b9f2-4d5c-9654-7fcab5be2c5d}
Contained 1 shadow copies at creation time: 8/23/2008 7:00:03 AM
Shadow Copy ID: {012d8105-ab39-4b17-89c9-bb7dfbeeb1f8}
Original Volume: (E:)\?Volume{9fa5f191-6554-11dd-9ce6-000c295707db}
Shadow Copy Volume: \?GLOBALROOTDeviceHarddiskVolumeShadowCopy4
Originating Machine: winserver-2
Service Machine: winserver-2
Provider: 'Microsoft Software Shadow Copy provider 1.0'
Type: ClientAccessible
Attributes: Persistent, Client-accessible, No auto release, No writers,
Differential
To obtain information about how shadow copy storage is allocated to shadow copies, use the vssadmin list shadowstorage:
C:Windowssystem32>vssadmin list shadowstorage
vssadmin 1.1 - Volume Shadow Copy Service administrative command-line tool
(C) Copyright 2001-2005 Microsoft Corp.
Shadow Copy Storage association
For volume: (E:)\?Volume{9fa5f191-6554-11dd-9ce6-000c295707db}
Shadow Copy Storage volume: (C:)\?Volume{f0c004b0-58c1-11dd-a1fe-000c295707
db}
Used Shadow Copy Storage space: 1.344 MB
Allocated Shadow Copy Storage space: 301.078 MB
Maximum Shadow Copy Storage space: 818 MB
The above command is particularly useful for comparing used and available space for shadow copy storage.
Shadow Copy for a volume may also be enabled from the command-line using vssadmin, the syntax for which is:
vssadmin add shadowstorage /for=volume /on=storevolume
where volume represents the volume on which shadow copy is to be enabled and storevolume is the volume on which the shadow copies are to be stored, for example:
vssadmin add shadowstorage /for=d: /on=e:
The maximum storage size may also be specified using the /maxsize= command-line option:
vssadmin add shadowstorage /for=d: /on=e: /maxsize=8GB
A manual shadow copy of an enabled volume may be triggered from the command prompt at any time by running vssadmin as follows:
C:Windowssystem32>vssadmin create shadow /for=e:
vssadmin 1.1 - Volume Shadow Copy Service administrative command-line tool
(C) Copyright 2001-2005 Microsoft Corp.
Successfully created shadow copy for 'e:'
Shadow Copy ID: {c9235d96-4ea3-4bc2-b2ee-77397a124914}
Shadow Copy Volume Name: \?GLOBALROOTDeviceHarddiskVolumeShadowCopy7
Specific shadow copies may also be deleted from the command line either by specifying that the oldest snapshot is to be deleted or by referencing the specific snapshot by its Shadow Copy Id (which can be obtained from the vssadmin list shadows command). For example, to delete the oldest shadow snapshot:
C:Windowssystem32>vssadmin delete shadows /for=e: /oldest vssadmin 1.1 - Volume Shadow Copy Service administrative command-line tool (C) Copyright 2001-2005 Microsoft Corp. Do you really want to delete 1 shadow copies (Y/N): [N]? y Successfully deleted 1 shadow copies.
Similarly, to delete a specific snapshot from a volume:
C:Windowssystem32>vssadmin delete shadows /shadow={879318ea-2f28-4d0c-b58b-5df5cd761984}
vssadmin 1.1 - Volume Shadow Copy Service administrative command-line tool
(C) Copyright 2001-2005 Microsoft Corp.
Do you really want to delete 1 shadow copies (Y/N): [N]? y
Successfully deleted 1 shadow copies.
The restoration of a shadow from a specific snapshot can be achieved from the command line using the vssadmin revert command combined with the Shadow Copy ID of the required snapshot. Note that the revert cannot be performed if open file handles exist on the volume (the /ForceDismount parameter is available but its use is not recommended since it can result in lost data:
C:Windowssystem32>vssadmin revert shadow /shadow={bf7e3df8-b4f9-4068-b208-3c67
8bc85053}
vssadmin 1.1 - Volume Shadow Copy Service administrative command-line tool
(C) Copyright 2001-2005 Microsoft Corp.
Do you really want to revert to this shadow copy (Y/N): [N]? y
Finally, Shadow Copying on a volume may be disabled via the command prompt using the vssadmin delete shadowstorage command, although the command will only work once all snapshots associated with the volume have been deleted from the shadow storage. Assuming there are no existing shapshots, the following example will disable shadow copy on the volume represented as the e: drive:
vssadmin delete shadowstorage /for=e:
Restoring Shadow Copy Snapshots from Clients
Once shadow copy has been configured for volumes on the server, the next step is to learn how to access the previous version of files from client systems. This is achieved using a feature of Windows Server 2008 R2 and Windows Vista called Previous Versions.
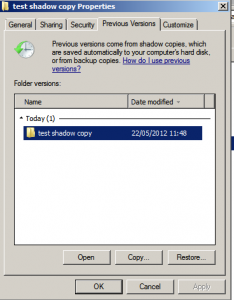
To access previous versions of a file on a client, navigate to the shared folder (or subfolder of a shared folder) or network drive using Start -> Network. Once the desired network drive or shared folder is visible, right click on it and select Restore Previous Versions (or just Previous Versions on Windows Vista). Once selected, the Properties dialog box will appear with the Previous Versions tab pre-selected as illustrated in the following figure:
As shown in the previous figure, the Previous Versions property page lists the previous versions of the shared folder that are available for restoration. A number of options are available for each shadow copy snapshot listed in the properties dialog. Open will open the folder in Windows Explorer so that individual files and sub-folders can be viewed and copied. The Copy… button allows the snapshot of the folder and its contents to be copied to a different location. Finally, Restore… restores the folder and files to its state at the time of the currently selected shadow copy snapshot. As outlined in the warning dialog, this action cannot be undone once performed.
<google>BUY_WINSERV_2008R2_BOTTOM</google>
Прочитано:
7 133
Порой сталкиваешься на рабочем месте, что к тебе как к системному администратору обращается пользователь с просьбой восстановить файл который он редактировал весь день, а потом вернулся к рабочему месту, но весь его труд утерян. Да, на его совести тот момент если он отошел от своего компьютера и не заблокировал вручную экран (приучаю нажимать сочетание клавиш: Win + L), а таймаут выставленный групповой политикой еще не активировался. Использовать такую отговорку, что можно восстановить файл(ы) только из вчерашнего бекапа — ну это не профессионализм. Вот в этом случае каждый системный администратор должен совершенствоваться и знать, что система Windows имеет такую важную настройку как использование «Теневых копий».
За основу функции/настройки теневого копирования отвечает служба теневого копирования (Volume Shadow Copies, VSS). Служба VSS применяется ко всему логическому диску и создаем снимок всех находящихся на нем файлов. После через запланированные промежутки времени отслеживает изменения и снова создает снимок.
Покажу на примере, как такая настройка «Теневые копии» включается и что она дает обычному пользователю.
Есть файловый сервер под управлением Windows Server 2016 Standard (на заметку: настройка «Теневые копии» работает и на Server 2008 R2,Server 2012/R2).
На заметку: логический диск с общими папками должен располагаться не на системном диске и не на диске с бекапами — это мое мнение.
На заметку: при использовании настройки «Теневые копии» следует под общие папки (файловый ресурс) заложить большой логический диск для хранения снимков. Если используется система виртуализации Hyper-V или ESXi то проблем с его расширением быть не должно и отрепетирована процедура его расширения.
На логическом диске D: создана папка с именем fileserver и настроена как общая с отключенным наследованием.
Запускаю оснастку «Управление компьютером»:
Win + R → control.exe — Просмотр: Категория — Мелкие значки — «Администрирование» — «Управление компьютером» — «Служебные программы» — и на «Общие папки» через правый клик мышью выбираю «Все задачи» — «Настроить теневые копии», выделяю том, в моем случае том D: и нажимаю «Настроить».
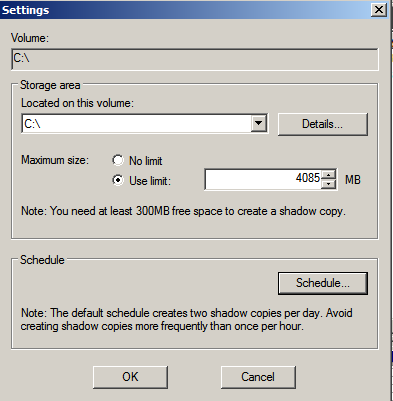
В данных настройках задается максимальный размер использования теневой копии, но не менее 300 МБ. По умолчанию хранилище теневых копий занимает 10 % от размера диска, а в снимках хранятся только изменения, а не сами изменившиеся файлы. Если места не достаточно, то при создании нового снимка старые снимки удаляют.
Как выбрать какой размер задать, прикинем, всего файлов под файловый ресурс 50 Gb, то я бы выбрал 50% от размера диска или: Максимальный размер: => не ограничен.
После нажимаю «Расписание» чтобы указать как часто будут делаться теневые копии. Если обратить внимание на рекомендацию, то не следует указывать создание одной теневой копии в час, вот только здесь уже каждый системный администратор должен все правильно взвесить как отразится потеря данных на продуктивной работе организации. Т.к. у меня жесткий диск под 2Tb, а данных всего 500Gb, то я делаю под себя следующее расписание:
Нажимаю «Дополнительно…»
- Дата начала: текущая дата
- Повторять задание: отмечаю галочкой
- Каждые: 2 часа
- Выполнять: в течение: 10 час
и получается расписание: Каждые 2 часа с 09.00 по 10 час начиная с текущей даты и каждый день.
В процессе эксплуатации я подкорректирую данное расписание.
и нажимаю кнопку Ok окна настройки расписания для тома D: — кнопку OK окна «Параметры» и выделив том D: нажимаю «Создать» тем самым создаю теневую копию текущего диска.
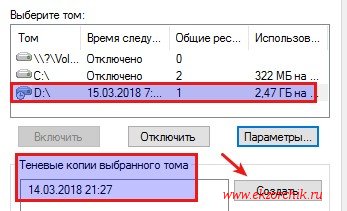
Также функцию теневые копии можно включить если перейти из оснастки «Управление компьютером» — «Запоминающие устройства» — «Управление дисками» — через правый клик по тому D: вызвать «Свойства» и перейдя во вкладку «Теневые копии».
Если сымитировать добавление файлов и последующее нажатие создания снимка можно будет видеть как изменяется размер и количество теневые копий в оснастке тома:
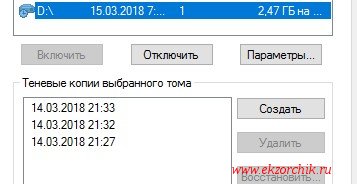
Под Windows 10 Pro:
Шаг №1: Перейти на файловый ресурс
Шаг №2: По каталогу (или по файлу) внутри которого располагаются его файлы нажать на нем через правый клик мышью перейти на меню «Восстановить прежнюю версию» после чего на вкладку «Предыдущие версии».
Шаг №3: Тут он увидит сделанные снимки и открывая последний ориентируясь на дату и время будут открываться экраны с файлами/или файл за указанный временной промежуток при нажатии на кнопку «Открыть» или через правый клик мышью по нему «Изменить» ту версию где результаты его работы самые последние.
Шаг №4: После чтобы его восстановить нужно либо когда файл найден и открыт сделать «Файл» — «Сохранить как» и сохранить в ту директорию где он был затерев не актуальный или же нажать кнопку «Восстановить» и воспользоваться мастером восстановления:
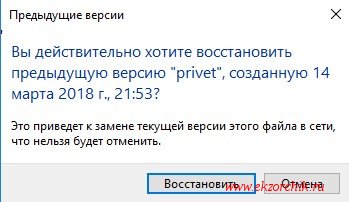
Шаг №5: Пользователь возвращается к редактированию на том месте файл(ы) которого были восстановлены.
Шаг №6: После этого момента пользователь становится чуть счастливее от того что теперь он сам может это делать и ему не надо писать заявку на helpdesk или подходить к Вам лично.
На заметку: Не советую включать теневые копии на системном диске, т. к. обновления, логирование и многое другое будет все заполоняется никому не нужными снимками и расходуемым местом. Возьмите за правило, один логический диск под систему, другой под данные.
На заметку: если выключить «Теневое копирование тома» в свойства диска, то все снимки будут удалены, а файлы будут оставлены как есть.
На заметку: Теневые копии — это не то же самое что и резервная копия, так что не советую полностью на них надеяться, ведь это всего лишь дельта изменения от первого и последующих снимков, а бекап — это наше все.
Итого, я для себя оформил те моменты с которыми сталкиваешься когда задействуешь «Теневые копии» для тома и что пользователь может сам сделать в случае проблемы с потерей файла(ов).
На этом я прощаюсь, если что будет интересного я дополню данную заметку, а пока собственно и всё, с уважением автор блога Олло Александр aka ekzorchik.
| description | title | ms.date | author | manager | ms.author | ms.topic |
|---|---|---|---|---|---|---|
|
Learn more about: Volume Shadow Copy Service |
Volume Shadow Copy Service |
12/06/2022 |
JasonGerend |
elizapo |
jgerend |
article |
Volume Shadow Copy Service
Applies to: Windows Server 2022, Windows Server 2019, Windows Server 2016, Windows Server 2012 R2, Windows Server 2012, and Windows Server 2008 R2, Windows Server 2008, Windows 10, Windows 8.1, Windows 8, Windows 7
Backing up and restoring critical business data can be very complex due to the following issues:
-
The data usually needs to be backed up while the applications that produce the data are still running. This means that some of the data files might be open or they might be in an inconsistent state.
-
If the data set is large, it can be difficult to back up all of it at one time.
Correctly performing backup and restore operations requires close coordination between the backup applications, the line-of-business applications that are being backed up, and the storage management hardware and software. The Volume Shadow Copy Service (VSS), which was introduced in Windows Server® 2003, facilitates the conversation between these components to allow them to work better together. When all the components support VSS, you can use them to back up your application data without taking the applications offline.
VSS coordinates the actions that are required to create a consistent shadow copy (also known as a snapshot or a point-in-time copy) of the data that is to be backed up. The shadow copy can be used as-is, or it can be used in scenarios such as the following:
-
You want to back up application data and system state information, including archiving data to another hard disk drive, to tape, or to other removable media.
-
You are data mining.
-
You are performing disk-to-disk backups.
-
You need a fast recovery from data loss by restoring data to the original Logical Unit Number (LUN) or to an entirely new LUN that replaces an original LUN that failed.
Windows features and applications that use VSS include the following:
-
Windows Server Backup (https://go.microsoft.com/fwlink/?LinkId=180891)
-
Shadow Copies of Shared Folders (https://go.microsoft.com/fwlink/?LinkId=142874)
-
System Center Data Protection Manager (https://go.microsoft.com/fwlink/?LinkId=180892)
-
System Restore (https://support.microsoft.com/windows/use-system-restore-a5ae3ed9-07c4-fd56-45ee-096777ecd14e)
How Volume Shadow Copy Service Works
A complete VSS solution requires all of the following basic parts:
VSS service Part of the Windows operating system that ensures the other components can communicate with each other properly and work together.
VSS requester The software that requests the actual creation of shadow copies (or other high-level operations like importing or deleting them). Typically, this is the backup application. The Windows Server Backup utility and the System Center Data Protection Manager application are VSS requesters. Non-Microsoft® VSS requesters include nearly all backup software that runs on Windows.
VSS writer The component that guarantees we have a consistent data set to back up. This is typically provided as part of a line-of-business application, such as SQL Server® or Exchange Server. VSS writers for various Windows components, such as the registry, are included with the Windows operating system. Non-Microsoft VSS writers are included with many applications for Windows that need to guarantee data consistency during back up.
VSS provider The component that creates and maintains the shadow copies. This can occur in the software or in the hardware. The Windows operating system includes a VSS provider that uses copy-on-write. If you use a storage area network (SAN), it is important that you install the VSS hardware provider for the SAN, if one is provided. A hardware provider offloads the task of creating and maintaining a shadow copy from the host operating system.
The following diagram illustrates how the VSS service coordinates with requesters, writers, and providers to create a shadow copy of a volume.
Figure 1 Architectural diagram of Volume Shadow Copy Service
How a Shadow Copy Is Created
This section puts the various roles of the requester, writer, and provider into context by listing the steps that need to be taken to create a shadow copy. The following diagram shows how the Volume Shadow Copy Service controls the overall coordination of the requester, writer, and provider.
Figure 2 Shadow copy creation process
To create a shadow copy, the requester, writer, and provider perform the following actions:
-
The requester asks the Volume Shadow Copy Service to enumerate the writers, gather the writer metadata, and prepare for shadow copy creation.
-
Each writer creates an XML description of the components and data stores that need to be backed up and provides it to the Volume Shadow Copy Service. The writer also defines a restore method, which is used for all components. The Volume Shadow Copy Service provides the writer’s description to the requester, which selects the components that will be backed up.
-
The Volume Shadow Copy Service notifies all the writers to prepare their data for making a shadow copy.
-
Each writer prepares the data as appropriate, such as completing all open transactions, rolling transaction logs, and flushing caches. When the data is ready to be shadow-copied, the writer notifies the Volume Shadow Copy Service.
-
The Volume Shadow Copy Service tells the writers to temporarily freeze application write I/O requests (read I/O requests are still possible) for the few seconds that are required to create the shadow copy of the volume or volumes. The application freeze is not allowed to take longer than 60 seconds. The Volume Shadow Copy Service flushes the file system buffers and then freezes the file system, which ensures that the file system metadata is recorded correctly and the data to be shadow-copied is written in a consistent order.
-
The Volume Shadow Copy Service tells the provider to create the shadow copy. The shadow copy creation period lasts no more than 10 seconds, during which all write I/O requests to the file system remain frozen.
-
The Volume Shadow Copy Service releases file system write I/O requests.
-
VSS tells the writers to thaw application write I/O requests. At this point applications are free to resume writing data to the disk that is being shadow-copied.
[!NOTE]
The shadow copy creation can be aborted if the writers are kept in the freeze state for longer than 60 seconds or if the providers take longer than 10 seconds to commit the shadow copy.
-
The requester can retry the process (go back to step 1) or notify the administrator to retry at a later time.
-
If the shadow copy is successfully created, the Volume Shadow Copy Service returns the location information for the shadow copy to the requester. In some cases, the shadow copy can be temporarily made available as a read-write volume so that VSS and one or more applications can alter the contents of the shadow copy before the shadow copy is finished. After VSS and the applications make their alterations, the shadow copy is made read-only. This phase is called Auto-recovery, and it is used to undo any file-system or application transactions on the shadow copy volume that were not completed before the shadow copy was created.
How the Provider Creates a Shadow Copy
A hardware or software shadow copy provider uses one of the following methods for creating a shadow copy:
Complete copy This method makes a complete copy (called a «full copy» or «clone») of the original volume at a given point in time. This copy is read-only.
Copy-on-write This method does not copy the original volume. Instead, it makes a differential copy by copying all changes (completed write I/O requests) that are made to the volume after a given point in time.
Redirect-on-write This method does not copy the original volume, and it does not make any changes to the original volume after a given point in time. Instead, it makes a differential copy by redirecting all changes to a different volume.
Complete copy
A complete copy is usually created by making a «split mirror» as follows:
-
The original volume and the shadow copy volume are a mirrored volume set.
-
The shadow copy volume is separated from the original volume. This breaks the mirror connection.
After the mirror connection is broken, the original volume and the shadow copy volume are independent. The original volume continues to accept all changes (write I/O requests), while the shadow copy volume remains an exact read-only copy of the original data at the time of the break.
Copy-on-write method
In the copy-on-write method, when a change to the original volume occurs (but before the write I/O request is completed), each block to be modified is read and then written to the volume’s shadow copy storage area (also called its «diff area»). The shadow copy storage area can be on the same volume or a different volume. This preserves a copy of the data block on the original volume before the change overwrites it.
| Time | Source data (status and data) | Shadow copy (status and data) |
|---|---|---|
|
T0 |
Original data: 1 2 3 4 5 |
No copy: — |
|
T1 |
Data changed in cache: 3 to 3′ |
Shadow copy created (differences only): 3 |
|
T2 |
Original data overwritten: 1 2 3′ 4 5 |
Differences and index stored on shadow copy: 3 |
Table 1 The copy-on-write method of creating shadow copies
The copy-on-write method is a quick method for creating a shadow copy, because it copies only data that is changed. The copied blocks in the diff area can be combined with the changed data on the original volume to restore the volume to its state before any of the changes were made. If there are many changes, the copy-on-write method can become expensive.
Redirect-on-write method
In the redirect-on-write method, whenever the original volume receives a change (write I/O request), the change is not applied to the original volume. Instead, the change is written to another volume’s shadow copy storage area.
| Time | Source data (status and data) | Shadow copy (status and data) |
|---|---|---|
|
T0 |
Original data: 1 2 3 4 5 |
No copy: — |
|
T1 |
Data changed in cache: 3 to 3′ |
Shadow copy created (differences only): 3′ |
|
T2 |
Original data unchanged: 1 2 3 4 5 |
Differences and index stored on shadow copy: 3′ |
Table 2 The redirect-on-write method of creating shadow copies
Like the copy-on-write method, the redirect-on-write method is a quick method for creating a shadow copy, because it copies only changes to the data. The copied blocks in the diff area can be combined with the unchanged data on the original volume to create a complete, up-to-date copy of the data. If there are many read I/O requests, the redirect-on-write method can become expensive.
Shadow Copy Providers
There are two types of shadow copy providers: hardware-based providers and software-based providers. There is also a system provider, which is a software provider that is built in to the Windows operating system.
Hardware-based providers
Hardware-based shadow copy providers act as an interface between the Volume Shadow Copy Service and the hardware level by working in conjunction with a hardware storage adapter or controller. The work of creating and maintaining the shadow copy is performed by the storage array.
Hardware providers always take the shadow copy of an entire LUN, but the Volume Shadow Copy Service only exposes the shadow copy of the volume or volumes that were requested.
A hardware-based shadow copy provider makes use of the Volume Shadow Copy Service functionality that defines the point in time, allows data synchronization, manages the shadow copy, and provides a common interface with backup applications. However, the Volume Shadow Copy Service does not specify the underlying mechanism by which the hardware-based provider produces and maintains shadow copies.
Software-based providers
Software-based shadow copy providers typically intercept and process read and write I/O requests in a software layer between the file system and the volume manager software.
These providers are implemented as a user-mode DLL component and at least one kernel-mode device driver, typically a storage filter driver. Unlike hardware-based providers, software-based providers create shadow copies at the software level, not the hardware level.
A software-based shadow copy provider must maintain a «point-in-time» view of a volume by having access to a data set that can be used to re-create volume status before the shadow copy creation time. An example is the copy-on-write technique of the system provider. However, the Volume Shadow Copy Service places no restrictions on what technique the software-based providers use to create and maintain shadow copies.
A software provider is applicable to a wider range of storage platforms than a hardware-based provider, and it should work with basic disks or logical volumes equally well. (A logical volume is a volume that is created by combining free space from two or more disks.) In contrast to hardware shadow copies, software providers consume operating system resources to maintain the shadow copy.
For more information about basic disks, see What Are Basic Disks and Volumes?.
System provider
One shadow copy provider, the system provider, is supplied in the Windows operating system. Although a default provider is supplied in Windows, other vendors are free to supply implementations that are optimized for their storage hardware and software applications.
To maintain the «point-in-time» view of a volume that is contained in a shadow copy, the system provider uses a copy-on-write technique. Copies of the blocks on volume that have been modified since the beginning of the shadow copy creation are stored in a shadow copy storage area.
The system provider can expose the production volume, which can be written to and read from normally. When the shadow copy is needed, it logically applies the differences to data on the production volume to expose the complete shadow copy.
For the system provider, the shadow copy storage area must be on an NTFS volume. The volume to be shadow copied does not need to be an NTFS volume, but at least one volume mounted on the system must be an NTFS volume.
The component files that make up the system provider are swprv.dll and volsnap.sys.
In-Box VSS Writers
The Windows operating system includes a set of VSS writers that are responsible for enumerating the data that is required by various Windows features.
For more information about these writers, see In-Box VSS Writers.
How Shadow Copies Are Used
In addition to backing up application data and system state information, shadow copies can be used for a number of purposes, including the following:
-
Restoring LUNs (LUN resynchronization and LUN swapping)
-
Restoring individual files (Shadow Copies for Shared Folders)
-
Data mining by using transportable shadow copies
Restoring LUNs (LUN resynchronization and LUN swapping)
In Windows Server 2008 R2 and Windows 7, VSS requesters can use a hardware shadow copy provider feature called LUN resynchronization (or «LUN resync»). This is a fast-recovery scheme that allows an application administrator to restore data from a shadow copy to the original LUN or to a new LUN.
The shadow copy can be a full clone or a differential shadow copy. In either case, at the end of the resync operation, the destination LUN will have the same contents as the shadow copy LUN. During the resync operation, the array performs a block-level copy from the shadow copy to the destination LUN.
[!NOTE]
The shadow copy must be a transportable hardware shadow copy.
Most arrays allow production I/O operations to resume shortly after the resync operation begins. While the resync operation is in progress, read requests are redirected to the shadow copy LUN, and write requests to the destination LUN. This allows arrays to recover very large data sets and resume normal operations in several seconds.
LUN resynchronization is different from LUN swapping. A LUN swap is a fast recovery scenario that VSS has supported since Windows Server 2003 SP1. In a LUN swap, the shadow copy is imported and then converted into a read-write volume. The conversion is an irreversible operation, and the volume and underlying LUN cannot be controlled with the VSS APIs after that. The following list describes how LUN resynchronization compares with LUN swapping:
-
In LUN resynchronization, the shadow copy is not altered, so it can be used several times. In LUN swapping, the shadow copy can be used only once for a recovery. For the most safety-conscious administrators, this is important. When LUN resynchronization is used, the requester can retry the entire restore operation if something goes wrong the first time.
-
At the end of a LUN swap, the shadow copy LUN is used for production I/O requests. For this reason, the shadow copy LUN must use the same quality of storage as the original production LUN to ensure that performance is not impacted after the recovery operation. If LUN resynchronization is used instead, the hardware provider can maintain the shadow copy on storage that is less expensive than production-quality storage.
-
If the destination LUN is unusable and needs to be recreated, LUN swapping may be more economical because it doesn’t require a destination LUN.
[!WARNING]
All of the operations listed are LUN-level operations. If you attempt to recover a specific volume by using LUN resynchronization, you are unwittingly going to revert all the other volumes that are sharing the LUN.
Restoring individual files (Shadow Copies for Shared Folders)
Shadow Copies for Shared Folders uses the Volume Shadow Copy Service to provide point-in-time copies of files that are located on a shared network resource, such as a file server. With Shadow Copies for Shared Folders, users can quickly recover deleted or changed files that are stored on the network. Because they can do so without administrator assistance, Shadow Copies for Shared Folders can increase productivity and reduce administrative costs.
For more information about Shadow Copies for Shared Folders, see Shadow Copies for Shared Folders (https://go.microsoft.com/fwlink/?LinkId=180898) on TechNet.
Data mining by using transportable shadow copies
With a hardware provider that is designed for use with the Volume Shadow Copy Service, you can create transportable shadow copies that can be imported onto servers within the same subsystem (for example, a SAN). These shadow copies can be used to seed a production or test installation with read-only data for data mining.
With the Volume Shadow Copy Service and a storage array with a hardware provider that is designed for use with the Volume Shadow Copy Service, it is possible to create a shadow copy of the source data volume on one server, and then import the shadow copy onto another server (or back to the same server). This process is accomplished in a few minutes, regardless of the size of the data. The transport process is accomplished through a series of steps that use a shadow copy requester (a storage-management application) that supports transportable shadow copies.
To transport a shadow copy
-
Create a transportable shadow copy of the source data on a server.
-
Import the shadow copy to a server that is connected to the SAN (you can import to a different server or the same server).
-
The data is now ready to be used.
Figure 3 Shadow copy creation and transport between two servers
[!NOTE]
A transportable shadow copy that is created on Windows Server 2003 cannot be imported onto a server that is running Windows Server 2008 or Windows Server 2008 R2. A transportable shadow copy that was created on Windows Server 2008 or Windows Server 2008 R2 cannot be imported onto a server that is running Windows Server 2003. However, a shadow copy that is created on Windows Server 2008 can be imported onto a server that is running Windows Server 2008 R2 and vice versa.
Shadow copies are read-only. If you want to convert a shadow copy to a read/write LUN, you can use a Virtual Disk Service-based storage-management application (including some requesters) in addition to the Volume Shadow Copy Service. By using this application, you can remove the shadow copy from Volume Shadow Copy Service management and convert it to a read/write LUN.
Volume Shadow Copy Service transport is an advanced solution on computers running Windows Server 2003 Enterprise Edition, Windows Server 2003 Datacenter Edition, Windows Server 2008, or Windows Server 2008 R2. It works only if there is a hardware provider on the storage array. Shadow copy transport can be used for a number of purposes, including tape backups, data mining, and testing.
Frequently Asked Questions
This FAQ answers questions about Volume Shadow Copy Service (VSS) for system administrators. For information about VSS application programming interfaces, see Volume Shadow Copy Service (https://go.microsoft.com/fwlink/?LinkId=180899) in the Windows Developer Center Library.
When was Volume Shadow Copy Service introduced? On which Windows operating system versions is it available?
VSS was introduced in Windows XP. It is available on Windows XP, Windows Server 2003, Windows Vista®, Windows Server 2008, Windows 7, and Windows Server 2008 R2.
What is the difference between a shadow copy and a backup?
In the case of a hard disk drive backup, the shadow copy created is also the backup. Data can be copied off the shadow copy for a restore or the shadow copy can be used for a fast recovery scenario—for example, LUN resynchronization or LUN swapping.
When data is copied from the shadow copy to tape or other removable media, the content that is stored on the media constitutes the backup. The shadow copy itself can be deleted after the data is copied from it.
What is the largest size volume that Volume Shadow Copy Service supports?
Volume Shadow Copy Service supports a volume size of up to 64 TB.
I made a backup on Windows Server 2008. Can I restore it on Windows Server 2008 R2?
It depends on the backup software that you used. Most backup programs support this scenario for data but not for system state backups.
Shadow copies that are created on either of these versions of Windows can be used on the other.
I made a backup on Windows Server 2003. Can I restore it on Windows Server 2008?
It depends on the backup software you used. If you create a shadow copy on Windows Server 2003, you cannot use it on Windows Server 2008. Also, if you create a shadow copy on Windows Server 2008, you cannot restore it on Windows Server 2003.
How can I disable VSS?
It is possible to disable the Volume Shadow Copy Service by using the Microsoft Management Console. However, you should not do this. Disabling VSS adversely affects any software you use that depends on it, such as System Restore and Windows Server Backup.
For more information, see the following Microsoft TechNet Web sites:
-
System Restore (https://go.microsoft.com/fwlink/?LinkID=157113)
-
Windows Server Backup (https://go.microsoft.com/fwlink/?LinkID=180891)
Can I exclude files from a shadow copy to save space?
VSS is designed to create shadow copies of entire volumes. Temporary files, such as paging files, are automatically omitted from shadow copies to save space.
To exclude specific files from shadow copies, use the following registry key: FilesNotToSnapshot.
[!NOTE]
The FilesNotToSnapshot registry key is intended to be used only by applications. Users who attempt to use it will encounter limitations such as the following:
- It cannot delete files from a shadow copy that was created on a Windows Server by using the Previous Versions feature.
- It cannot delete files from shadow copies for shared folders.
- It can delete files from a shadow copy that was created by using the Diskshadow utility, but it cannot delete files from a shadow copy that was created by using the Vssadmin utility.
- Files are deleted from a shadow copy on a best-effort basis. This means that they are not guaranteed to be deleted.
For more information, see Excluding Files from Shadow Copies (https://go.microsoft.com/fwlink/?LinkId=180904) on MSDN.
My non-Microsoft backup program failed with a VSS error. What can I do?
Check the product support section of the Web site of the company that created the backup program. There may be a product update that you can download and install to fix the problem. If not, contact the company’s product support department.
System administrators can use the VSS troubleshooting information on the following Microsoft TechNet Library Web site to gather diagnostic information about VSS-related issues.
For more information, see Volume Shadow Copy Service (https://go.microsoft.com/fwlink/?LinkId=180905) on TechNet.
What is the «diff area»?
The shadow copy storage area (or «diff area») is the location where the data for the shadow copy that is created by the system software provider is stored.
Where is the diff area located?
The diff area can be located on any local volume. However, it must be located on an NTFS volume that has enough space to store it.
How is the diff area location determined?
The following criteria are evaluated, in this order, to determine the diff area location:
-
If a volume already has an existing shadow copy, that location is used.
-
If there is a preconfigured manual association between the original volume and the shadow copy volume location, then that location is used.
-
If the previous two criteria do not provide a location, the shadow copy service chooses a location based on available free space. If more than one volume is being shadow copied, the shadow copy service creates a list of possible snapshot locations based on the size of free space, in descending order. The number of locations provided is equal to the number of volumes being shadow copied.
-
If the volume being shadow copied is one of the possible locations, then a local association is created. Otherwise an association with the volume with the most available space is created.
Can VSS create shadow copies of non-NTFS volumes?
Yes. However, persistent shadow copies can be made only for NTFS volumes. In addition, at least one volume mounted on the system must be an NTFS volume.
What’s the maximum number of shadow copies I can create at one time?
The maximum number of shadow copied volumes in a single shadow copy set is 64. Note that this is not the same as the number of shadow copies.
What’s the maximum number of software shadow copies created by the system provider that I can maintain for a volume?
The max number is of software shadow copies for each volume is 512. However, by default you can only maintain 64 shadow copies that are used by the Shadow Copies of Shared Folders feature. To change the limit for the Shadow Copies of Shared Folders feature, use the following registry key: MaxShadowCopies.
How can I control the space that is used for shadow copy storage space?
Type the vssadmin resize shadowstorage command.
For more information, see Vssadmin resize shadowstorage (https://go.microsoft.com/fwlink/?LinkId=180906) on TechNet.
What happens when I run out of space?
Shadow copies for the volume are deleted, beginning with the oldest shadow copy.
Volume Shadow Copy Service Tools
The Windows operating system provides the following tools for working with VSS:
-
DiskShadow (https://go.microsoft.com/fwlink/?LinkId=180907)
-
VssAdmin (https://go.microsoft.com/fwlink/?LinkId=84008)
DiskShadow
DiskShadow is a VSS requester that you can use to manage all the hardware and software snapshots that you can have on a system. DiskShadow includes commands such as the following:
-
list: Lists VSS writers, VSS providers, and shadow copies
-
create: Creates a new shadow copy
-
import: Imports a transportable shadow copy
-
expose: Exposes a persistent shadow copy (as a drive letter, for example)
-
revert: Reverts a volume back to a specified shadow copy
This tool is intended for use by IT professionals, but developers might also find it useful when testing a VSS writer or VSS provider.
DiskShadow is available only on Windows Server operating systems. It is not available on Windows client operating systems.
VssAdmin
VssAdmin is used to create, delete, and list information about shadow copies. It can also be used to resize the shadow copy storage area («diff area»).
VssAdmin includes commands such as the following:
-
create shadow: Creates a new shadow copy
-
delete shadows: Deletes shadow copies
-
list providers: Lists all registered VSS providers
-
list writers: Lists all subscribed VSS writers
-
resize shadowstorage: Changes the maximum size of the shadow copy storage area
VssAdmin can only be used to administer shadow copies that are created by the system software provider.
VssAdmin is available on Windows client and Windows Server operating system versions.
Volume Shadow Copy Service Registry Keys
The following registry keys are available for use with VSS:
-
VssAccessControl
-
MaxShadowCopies
-
MinDiffAreaFileSize
VssAccessControl
This key is used to specify which users have access to shadow copies.
For more information, see the following entries on the MSDN Web site:
-
Security Considerations for Writers (https://go.microsoft.com/fwlink/?LinkId=157739)
-
Security Considerations for Requesters (https://go.microsoft.com/fwlink/?LinkId=180908)
MaxShadowCopies
This key specifies the maximum number of client-accessible shadow copies that can be stored on each volume of the computer. Client-accessible shadow copies are used by Shadow Copies for Shared Folders.
For more information, see the following entry on the MSDN Web site:
MaxShadowCopies under Registry Keys for Backup and Restore (https://go.microsoft.com/fwlink/?LinkId=180909)
MinDiffAreaFileSize
This key specifies the minimum initial size, in MB, of the shadow copy storage area.
For more information, see the following entry on the MSDN Web site:
MinDiffAreaFileSize under Registry Keys for Backup and Restore (https://go.microsoft.com/fwlink/?LinkId=180910)
Supported Operating System Versions
The following table lists the minimum supported operating system versions for VSS features.
| VSS feature | Minimum supported client | Minimum supported server | ||
|---|---|---|---|---|
|
LUN resynchronization |
None supported |
Windows Server 2008 R2 |
||
|
FilesNotToSnapshot registry key |
Windows Vista |
Windows Server 2008 |
||
|
Transportable shadow copies |
None supported |
Windows Server 2003 with SP1 |
||
|
Hardware shadow copies |
None supported |
Windows Server 2003 |
||
|
Previous versions of Windows Server |
Windows Vista |
Windows Server 2003 |
||
|
Fast recovery using LUN swap |
None supported |
Windows Server 2003 with SP1 |
||
|
Multiple imports of hardware shadow copies
|
None supported |
Windows Server 2008 |
||
|
Shadow Copies for Shared Folders |
None supported |
Windows Server 2003 |
||
|
Transportable auto-recovered shadow copies |
None supported |
Windows Server 2008 |
||
|
Concurrent backup sessions (up to 64) |
Windows XP |
Windows Server 2003 |
||
|
Single restore session concurrent with backups |
Windows Vista |
Windows Server 2003 with SP2 |
||
|
Up to 8 restore sessions concurrent with backups |
Windows 7 |
Windows Server 2003 R2 |
Additional References
Volume Shadow Copy Service in Windows Developer Center
| description | title | ms.date | author | manager | ms.author | ms.topic |
|---|---|---|---|---|---|---|
|
Learn more about: Volume Shadow Copy Service |
Volume Shadow Copy Service |
12/06/2022 |
JasonGerend |
elizapo |
jgerend |
article |
Volume Shadow Copy Service
Applies to: Windows Server 2022, Windows Server 2019, Windows Server 2016, Windows Server 2012 R2, Windows Server 2012, and Windows Server 2008 R2, Windows Server 2008, Windows 10, Windows 8.1, Windows 8, Windows 7
Backing up and restoring critical business data can be very complex due to the following issues:
-
The data usually needs to be backed up while the applications that produce the data are still running. This means that some of the data files might be open or they might be in an inconsistent state.
-
If the data set is large, it can be difficult to back up all of it at one time.
Correctly performing backup and restore operations requires close coordination between the backup applications, the line-of-business applications that are being backed up, and the storage management hardware and software. The Volume Shadow Copy Service (VSS), which was introduced in Windows Server® 2003, facilitates the conversation between these components to allow them to work better together. When all the components support VSS, you can use them to back up your application data without taking the applications offline.
VSS coordinates the actions that are required to create a consistent shadow copy (also known as a snapshot or a point-in-time copy) of the data that is to be backed up. The shadow copy can be used as-is, or it can be used in scenarios such as the following:
-
You want to back up application data and system state information, including archiving data to another hard disk drive, to tape, or to other removable media.
-
You are data mining.
-
You are performing disk-to-disk backups.
-
You need a fast recovery from data loss by restoring data to the original Logical Unit Number (LUN) or to an entirely new LUN that replaces an original LUN that failed.
Windows features and applications that use VSS include the following:
-
Windows Server Backup (https://go.microsoft.com/fwlink/?LinkId=180891)
-
Shadow Copies of Shared Folders (https://go.microsoft.com/fwlink/?LinkId=142874)
-
System Center Data Protection Manager (https://go.microsoft.com/fwlink/?LinkId=180892)
-
System Restore (https://support.microsoft.com/windows/use-system-restore-a5ae3ed9-07c4-fd56-45ee-096777ecd14e)
How Volume Shadow Copy Service Works
A complete VSS solution requires all of the following basic parts:
VSS service Part of the Windows operating system that ensures the other components can communicate with each other properly and work together.
VSS requester The software that requests the actual creation of shadow copies (or other high-level operations like importing or deleting them). Typically, this is the backup application. The Windows Server Backup utility and the System Center Data Protection Manager application are VSS requesters. Non-Microsoft® VSS requesters include nearly all backup software that runs on Windows.
VSS writer The component that guarantees we have a consistent data set to back up. This is typically provided as part of a line-of-business application, such as SQL Server® or Exchange Server. VSS writers for various Windows components, such as the registry, are included with the Windows operating system. Non-Microsoft VSS writers are included with many applications for Windows that need to guarantee data consistency during back up.
VSS provider The component that creates and maintains the shadow copies. This can occur in the software or in the hardware. The Windows operating system includes a VSS provider that uses copy-on-write. If you use a storage area network (SAN), it is important that you install the VSS hardware provider for the SAN, if one is provided. A hardware provider offloads the task of creating and maintaining a shadow copy from the host operating system.
The following diagram illustrates how the VSS service coordinates with requesters, writers, and providers to create a shadow copy of a volume.
Figure 1 Architectural diagram of Volume Shadow Copy Service
How a Shadow Copy Is Created
This section puts the various roles of the requester, writer, and provider into context by listing the steps that need to be taken to create a shadow copy. The following diagram shows how the Volume Shadow Copy Service controls the overall coordination of the requester, writer, and provider.
Figure 2 Shadow copy creation process
To create a shadow copy, the requester, writer, and provider perform the following actions:
-
The requester asks the Volume Shadow Copy Service to enumerate the writers, gather the writer metadata, and prepare for shadow copy creation.
-
Each writer creates an XML description of the components and data stores that need to be backed up and provides it to the Volume Shadow Copy Service. The writer also defines a restore method, which is used for all components. The Volume Shadow Copy Service provides the writer’s description to the requester, which selects the components that will be backed up.
-
The Volume Shadow Copy Service notifies all the writers to prepare their data for making a shadow copy.
-
Each writer prepares the data as appropriate, such as completing all open transactions, rolling transaction logs, and flushing caches. When the data is ready to be shadow-copied, the writer notifies the Volume Shadow Copy Service.
-
The Volume Shadow Copy Service tells the writers to temporarily freeze application write I/O requests (read I/O requests are still possible) for the few seconds that are required to create the shadow copy of the volume or volumes. The application freeze is not allowed to take longer than 60 seconds. The Volume Shadow Copy Service flushes the file system buffers and then freezes the file system, which ensures that the file system metadata is recorded correctly and the data to be shadow-copied is written in a consistent order.
-
The Volume Shadow Copy Service tells the provider to create the shadow copy. The shadow copy creation period lasts no more than 10 seconds, during which all write I/O requests to the file system remain frozen.
-
The Volume Shadow Copy Service releases file system write I/O requests.
-
VSS tells the writers to thaw application write I/O requests. At this point applications are free to resume writing data to the disk that is being shadow-copied.
[!NOTE]
The shadow copy creation can be aborted if the writers are kept in the freeze state for longer than 60 seconds or if the providers take longer than 10 seconds to commit the shadow copy.
-
The requester can retry the process (go back to step 1) or notify the administrator to retry at a later time.
-
If the shadow copy is successfully created, the Volume Shadow Copy Service returns the location information for the shadow copy to the requester. In some cases, the shadow copy can be temporarily made available as a read-write volume so that VSS and one or more applications can alter the contents of the shadow copy before the shadow copy is finished. After VSS and the applications make their alterations, the shadow copy is made read-only. This phase is called Auto-recovery, and it is used to undo any file-system or application transactions on the shadow copy volume that were not completed before the shadow copy was created.
How the Provider Creates a Shadow Copy
A hardware or software shadow copy provider uses one of the following methods for creating a shadow copy:
Complete copy This method makes a complete copy (called a «full copy» or «clone») of the original volume at a given point in time. This copy is read-only.
Copy-on-write This method does not copy the original volume. Instead, it makes a differential copy by copying all changes (completed write I/O requests) that are made to the volume after a given point in time.
Redirect-on-write This method does not copy the original volume, and it does not make any changes to the original volume after a given point in time. Instead, it makes a differential copy by redirecting all changes to a different volume.
Complete copy
A complete copy is usually created by making a «split mirror» as follows:
-
The original volume and the shadow copy volume are a mirrored volume set.
-
The shadow copy volume is separated from the original volume. This breaks the mirror connection.
After the mirror connection is broken, the original volume and the shadow copy volume are independent. The original volume continues to accept all changes (write I/O requests), while the shadow copy volume remains an exact read-only copy of the original data at the time of the break.
Copy-on-write method
In the copy-on-write method, when a change to the original volume occurs (but before the write I/O request is completed), each block to be modified is read and then written to the volume’s shadow copy storage area (also called its «diff area»). The shadow copy storage area can be on the same volume or a different volume. This preserves a copy of the data block on the original volume before the change overwrites it.
| Time | Source data (status and data) | Shadow copy (status and data) |
|---|---|---|
|
T0 |
Original data: 1 2 3 4 5 |
No copy: — |
|
T1 |
Data changed in cache: 3 to 3′ |
Shadow copy created (differences only): 3 |
|
T2 |
Original data overwritten: 1 2 3′ 4 5 |
Differences and index stored on shadow copy: 3 |
Table 1 The copy-on-write method of creating shadow copies
The copy-on-write method is a quick method for creating a shadow copy, because it copies only data that is changed. The copied blocks in the diff area can be combined with the changed data on the original volume to restore the volume to its state before any of the changes were made. If there are many changes, the copy-on-write method can become expensive.
Redirect-on-write method
In the redirect-on-write method, whenever the original volume receives a change (write I/O request), the change is not applied to the original volume. Instead, the change is written to another volume’s shadow copy storage area.
| Time | Source data (status and data) | Shadow copy (status and data) |
|---|---|---|
|
T0 |
Original data: 1 2 3 4 5 |
No copy: — |
|
T1 |
Data changed in cache: 3 to 3′ |
Shadow copy created (differences only): 3′ |
|
T2 |
Original data unchanged: 1 2 3 4 5 |
Differences and index stored on shadow copy: 3′ |
Table 2 The redirect-on-write method of creating shadow copies
Like the copy-on-write method, the redirect-on-write method is a quick method for creating a shadow copy, because it copies only changes to the data. The copied blocks in the diff area can be combined with the unchanged data on the original volume to create a complete, up-to-date copy of the data. If there are many read I/O requests, the redirect-on-write method can become expensive.
Shadow Copy Providers
There are two types of shadow copy providers: hardware-based providers and software-based providers. There is also a system provider, which is a software provider that is built in to the Windows operating system.
Hardware-based providers
Hardware-based shadow copy providers act as an interface between the Volume Shadow Copy Service and the hardware level by working in conjunction with a hardware storage adapter or controller. The work of creating and maintaining the shadow copy is performed by the storage array.
Hardware providers always take the shadow copy of an entire LUN, but the Volume Shadow Copy Service only exposes the shadow copy of the volume or volumes that were requested.
A hardware-based shadow copy provider makes use of the Volume Shadow Copy Service functionality that defines the point in time, allows data synchronization, manages the shadow copy, and provides a common interface with backup applications. However, the Volume Shadow Copy Service does not specify the underlying mechanism by which the hardware-based provider produces and maintains shadow copies.
Software-based providers
Software-based shadow copy providers typically intercept and process read and write I/O requests in a software layer between the file system and the volume manager software.
These providers are implemented as a user-mode DLL component and at least one kernel-mode device driver, typically a storage filter driver. Unlike hardware-based providers, software-based providers create shadow copies at the software level, not the hardware level.
A software-based shadow copy provider must maintain a «point-in-time» view of a volume by having access to a data set that can be used to re-create volume status before the shadow copy creation time. An example is the copy-on-write technique of the system provider. However, the Volume Shadow Copy Service places no restrictions on what technique the software-based providers use to create and maintain shadow copies.
A software provider is applicable to a wider range of storage platforms than a hardware-based provider, and it should work with basic disks or logical volumes equally well. (A logical volume is a volume that is created by combining free space from two or more disks.) In contrast to hardware shadow copies, software providers consume operating system resources to maintain the shadow copy.
For more information about basic disks, see What Are Basic Disks and Volumes?.
System provider
One shadow copy provider, the system provider, is supplied in the Windows operating system. Although a default provider is supplied in Windows, other vendors are free to supply implementations that are optimized for their storage hardware and software applications.
To maintain the «point-in-time» view of a volume that is contained in a shadow copy, the system provider uses a copy-on-write technique. Copies of the blocks on volume that have been modified since the beginning of the shadow copy creation are stored in a shadow copy storage area.
The system provider can expose the production volume, which can be written to and read from normally. When the shadow copy is needed, it logically applies the differences to data on the production volume to expose the complete shadow copy.
For the system provider, the shadow copy storage area must be on an NTFS volume. The volume to be shadow copied does not need to be an NTFS volume, but at least one volume mounted on the system must be an NTFS volume.
The component files that make up the system provider are swprv.dll and volsnap.sys.
In-Box VSS Writers
The Windows operating system includes a set of VSS writers that are responsible for enumerating the data that is required by various Windows features.
For more information about these writers, see In-Box VSS Writers.
How Shadow Copies Are Used
In addition to backing up application data and system state information, shadow copies can be used for a number of purposes, including the following:
-
Restoring LUNs (LUN resynchronization and LUN swapping)
-
Restoring individual files (Shadow Copies for Shared Folders)
-
Data mining by using transportable shadow copies
Restoring LUNs (LUN resynchronization and LUN swapping)
In Windows Server 2008 R2 and Windows 7, VSS requesters can use a hardware shadow copy provider feature called LUN resynchronization (or «LUN resync»). This is a fast-recovery scheme that allows an application administrator to restore data from a shadow copy to the original LUN or to a new LUN.
The shadow copy can be a full clone or a differential shadow copy. In either case, at the end of the resync operation, the destination LUN will have the same contents as the shadow copy LUN. During the resync operation, the array performs a block-level copy from the shadow copy to the destination LUN.
[!NOTE]
The shadow copy must be a transportable hardware shadow copy.
Most arrays allow production I/O operations to resume shortly after the resync operation begins. While the resync operation is in progress, read requests are redirected to the shadow copy LUN, and write requests to the destination LUN. This allows arrays to recover very large data sets and resume normal operations in several seconds.
LUN resynchronization is different from LUN swapping. A LUN swap is a fast recovery scenario that VSS has supported since Windows Server 2003 SP1. In a LUN swap, the shadow copy is imported and then converted into a read-write volume. The conversion is an irreversible operation, and the volume and underlying LUN cannot be controlled with the VSS APIs after that. The following list describes how LUN resynchronization compares with LUN swapping:
-
In LUN resynchronization, the shadow copy is not altered, so it can be used several times. In LUN swapping, the shadow copy can be used only once for a recovery. For the most safety-conscious administrators, this is important. When LUN resynchronization is used, the requester can retry the entire restore operation if something goes wrong the first time.
-
At the end of a LUN swap, the shadow copy LUN is used for production I/O requests. For this reason, the shadow copy LUN must use the same quality of storage as the original production LUN to ensure that performance is not impacted after the recovery operation. If LUN resynchronization is used instead, the hardware provider can maintain the shadow copy on storage that is less expensive than production-quality storage.
-
If the destination LUN is unusable and needs to be recreated, LUN swapping may be more economical because it doesn’t require a destination LUN.
[!WARNING]
All of the operations listed are LUN-level operations. If you attempt to recover a specific volume by using LUN resynchronization, you are unwittingly going to revert all the other volumes that are sharing the LUN.
Restoring individual files (Shadow Copies for Shared Folders)
Shadow Copies for Shared Folders uses the Volume Shadow Copy Service to provide point-in-time copies of files that are located on a shared network resource, such as a file server. With Shadow Copies for Shared Folders, users can quickly recover deleted or changed files that are stored on the network. Because they can do so without administrator assistance, Shadow Copies for Shared Folders can increase productivity and reduce administrative costs.
For more information about Shadow Copies for Shared Folders, see Shadow Copies for Shared Folders (https://go.microsoft.com/fwlink/?LinkId=180898) on TechNet.
Data mining by using transportable shadow copies
With a hardware provider that is designed for use with the Volume Shadow Copy Service, you can create transportable shadow copies that can be imported onto servers within the same subsystem (for example, a SAN). These shadow copies can be used to seed a production or test installation with read-only data for data mining.
With the Volume Shadow Copy Service and a storage array with a hardware provider that is designed for use with the Volume Shadow Copy Service, it is possible to create a shadow copy of the source data volume on one server, and then import the shadow copy onto another server (or back to the same server). This process is accomplished in a few minutes, regardless of the size of the data. The transport process is accomplished through a series of steps that use a shadow copy requester (a storage-management application) that supports transportable shadow copies.
To transport a shadow copy
-
Create a transportable shadow copy of the source data on a server.
-
Import the shadow copy to a server that is connected to the SAN (you can import to a different server or the same server).
-
The data is now ready to be used.
Figure 3 Shadow copy creation and transport between two servers
[!NOTE]
A transportable shadow copy that is created on Windows Server 2003 cannot be imported onto a server that is running Windows Server 2008 or Windows Server 2008 R2. A transportable shadow copy that was created on Windows Server 2008 or Windows Server 2008 R2 cannot be imported onto a server that is running Windows Server 2003. However, a shadow copy that is created on Windows Server 2008 can be imported onto a server that is running Windows Server 2008 R2 and vice versa.
Shadow copies are read-only. If you want to convert a shadow copy to a read/write LUN, you can use a Virtual Disk Service-based storage-management application (including some requesters) in addition to the Volume Shadow Copy Service. By using this application, you can remove the shadow copy from Volume Shadow Copy Service management and convert it to a read/write LUN.
Volume Shadow Copy Service transport is an advanced solution on computers running Windows Server 2003 Enterprise Edition, Windows Server 2003 Datacenter Edition, Windows Server 2008, or Windows Server 2008 R2. It works only if there is a hardware provider on the storage array. Shadow copy transport can be used for a number of purposes, including tape backups, data mining, and testing.
Frequently Asked Questions
This FAQ answers questions about Volume Shadow Copy Service (VSS) for system administrators. For information about VSS application programming interfaces, see Volume Shadow Copy Service (https://go.microsoft.com/fwlink/?LinkId=180899) in the Windows Developer Center Library.
When was Volume Shadow Copy Service introduced? On which Windows operating system versions is it available?
VSS was introduced in Windows XP. It is available on Windows XP, Windows Server 2003, Windows Vista®, Windows Server 2008, Windows 7, and Windows Server 2008 R2.
What is the difference between a shadow copy and a backup?
In the case of a hard disk drive backup, the shadow copy created is also the backup. Data can be copied off the shadow copy for a restore or the shadow copy can be used for a fast recovery scenario—for example, LUN resynchronization or LUN swapping.
When data is copied from the shadow copy to tape or other removable media, the content that is stored on the media constitutes the backup. The shadow copy itself can be deleted after the data is copied from it.
What is the largest size volume that Volume Shadow Copy Service supports?
Volume Shadow Copy Service supports a volume size of up to 64 TB.
I made a backup on Windows Server 2008. Can I restore it on Windows Server 2008 R2?
It depends on the backup software that you used. Most backup programs support this scenario for data but not for system state backups.
Shadow copies that are created on either of these versions of Windows can be used on the other.
I made a backup on Windows Server 2003. Can I restore it on Windows Server 2008?
It depends on the backup software you used. If you create a shadow copy on Windows Server 2003, you cannot use it on Windows Server 2008. Also, if you create a shadow copy on Windows Server 2008, you cannot restore it on Windows Server 2003.
How can I disable VSS?
It is possible to disable the Volume Shadow Copy Service by using the Microsoft Management Console. However, you should not do this. Disabling VSS adversely affects any software you use that depends on it, such as System Restore and Windows Server Backup.
For more information, see the following Microsoft TechNet Web sites:
-
System Restore (https://go.microsoft.com/fwlink/?LinkID=157113)
-
Windows Server Backup (https://go.microsoft.com/fwlink/?LinkID=180891)
Can I exclude files from a shadow copy to save space?
VSS is designed to create shadow copies of entire volumes. Temporary files, such as paging files, are automatically omitted from shadow copies to save space.
To exclude specific files from shadow copies, use the following registry key: FilesNotToSnapshot.
[!NOTE]
The FilesNotToSnapshot registry key is intended to be used only by applications. Users who attempt to use it will encounter limitations such as the following:
- It cannot delete files from a shadow copy that was created on a Windows Server by using the Previous Versions feature.
- It cannot delete files from shadow copies for shared folders.
- It can delete files from a shadow copy that was created by using the Diskshadow utility, but it cannot delete files from a shadow copy that was created by using the Vssadmin utility.
- Files are deleted from a shadow copy on a best-effort basis. This means that they are not guaranteed to be deleted.
For more information, see Excluding Files from Shadow Copies (https://go.microsoft.com/fwlink/?LinkId=180904) on MSDN.
My non-Microsoft backup program failed with a VSS error. What can I do?
Check the product support section of the Web site of the company that created the backup program. There may be a product update that you can download and install to fix the problem. If not, contact the company’s product support department.
System administrators can use the VSS troubleshooting information on the following Microsoft TechNet Library Web site to gather diagnostic information about VSS-related issues.
For more information, see Volume Shadow Copy Service (https://go.microsoft.com/fwlink/?LinkId=180905) on TechNet.
What is the «diff area»?
The shadow copy storage area (or «diff area») is the location where the data for the shadow copy that is created by the system software provider is stored.
Where is the diff area located?
The diff area can be located on any local volume. However, it must be located on an NTFS volume that has enough space to store it.
How is the diff area location determined?
The following criteria are evaluated, in this order, to determine the diff area location:
-
If a volume already has an existing shadow copy, that location is used.
-
If there is a preconfigured manual association between the original volume and the shadow copy volume location, then that location is used.
-
If the previous two criteria do not provide a location, the shadow copy service chooses a location based on available free space. If more than one volume is being shadow copied, the shadow copy service creates a list of possible snapshot locations based on the size of free space, in descending order. The number of locations provided is equal to the number of volumes being shadow copied.
-
If the volume being shadow copied is one of the possible locations, then a local association is created. Otherwise an association with the volume with the most available space is created.
Can VSS create shadow copies of non-NTFS volumes?
Yes. However, persistent shadow copies can be made only for NTFS volumes. In addition, at least one volume mounted on the system must be an NTFS volume.
What’s the maximum number of shadow copies I can create at one time?
The maximum number of shadow copied volumes in a single shadow copy set is 64. Note that this is not the same as the number of shadow copies.
What’s the maximum number of software shadow copies created by the system provider that I can maintain for a volume?
The max number is of software shadow copies for each volume is 512. However, by default you can only maintain 64 shadow copies that are used by the Shadow Copies of Shared Folders feature. To change the limit for the Shadow Copies of Shared Folders feature, use the following registry key: MaxShadowCopies.
How can I control the space that is used for shadow copy storage space?
Type the vssadmin resize shadowstorage command.
For more information, see Vssadmin resize shadowstorage (https://go.microsoft.com/fwlink/?LinkId=180906) on TechNet.
What happens when I run out of space?
Shadow copies for the volume are deleted, beginning with the oldest shadow copy.
Volume Shadow Copy Service Tools
The Windows operating system provides the following tools for working with VSS:
-
DiskShadow (https://go.microsoft.com/fwlink/?LinkId=180907)
-
VssAdmin (https://go.microsoft.com/fwlink/?LinkId=84008)
DiskShadow
DiskShadow is a VSS requester that you can use to manage all the hardware and software snapshots that you can have on a system. DiskShadow includes commands such as the following:
-
list: Lists VSS writers, VSS providers, and shadow copies
-
create: Creates a new shadow copy
-
import: Imports a transportable shadow copy
-
expose: Exposes a persistent shadow copy (as a drive letter, for example)
-
revert: Reverts a volume back to a specified shadow copy
This tool is intended for use by IT professionals, but developers might also find it useful when testing a VSS writer or VSS provider.
DiskShadow is available only on Windows Server operating systems. It is not available on Windows client operating systems.
VssAdmin
VssAdmin is used to create, delete, and list information about shadow copies. It can also be used to resize the shadow copy storage area («diff area»).
VssAdmin includes commands such as the following:
-
create shadow: Creates a new shadow copy
-
delete shadows: Deletes shadow copies
-
list providers: Lists all registered VSS providers
-
list writers: Lists all subscribed VSS writers
-
resize shadowstorage: Changes the maximum size of the shadow copy storage area
VssAdmin can only be used to administer shadow copies that are created by the system software provider.
VssAdmin is available on Windows client and Windows Server operating system versions.
Volume Shadow Copy Service Registry Keys
The following registry keys are available for use with VSS:
-
VssAccessControl
-
MaxShadowCopies
-
MinDiffAreaFileSize
VssAccessControl
This key is used to specify which users have access to shadow copies.
For more information, see the following entries on the MSDN Web site:
-
Security Considerations for Writers (https://go.microsoft.com/fwlink/?LinkId=157739)
-
Security Considerations for Requesters (https://go.microsoft.com/fwlink/?LinkId=180908)
MaxShadowCopies
This key specifies the maximum number of client-accessible shadow copies that can be stored on each volume of the computer. Client-accessible shadow copies are used by Shadow Copies for Shared Folders.
For more information, see the following entry on the MSDN Web site:
MaxShadowCopies under Registry Keys for Backup and Restore (https://go.microsoft.com/fwlink/?LinkId=180909)
MinDiffAreaFileSize
This key specifies the minimum initial size, in MB, of the shadow copy storage area.
For more information, see the following entry on the MSDN Web site:
MinDiffAreaFileSize under Registry Keys for Backup and Restore (https://go.microsoft.com/fwlink/?LinkId=180910)
Supported Operating System Versions
The following table lists the minimum supported operating system versions for VSS features.
| VSS feature | Minimum supported client | Minimum supported server | ||
|---|---|---|---|---|
|
LUN resynchronization |
None supported |
Windows Server 2008 R2 |
||
|
FilesNotToSnapshot registry key |
Windows Vista |
Windows Server 2008 |
||
|
Transportable shadow copies |
None supported |
Windows Server 2003 with SP1 |
||
|
Hardware shadow copies |
None supported |
Windows Server 2003 |
||
|
Previous versions of Windows Server |
Windows Vista |
Windows Server 2003 |
||
|
Fast recovery using LUN swap |
None supported |
Windows Server 2003 with SP1 |
||
|
Multiple imports of hardware shadow copies
|
None supported |
Windows Server 2008 |
||
|
Shadow Copies for Shared Folders |
None supported |
Windows Server 2003 |
||
|
Transportable auto-recovered shadow copies |
None supported |
Windows Server 2008 |
||
|
Concurrent backup sessions (up to 64) |
Windows XP |
Windows Server 2003 |
||
|
Single restore session concurrent with backups |
Windows Vista |
Windows Server 2003 with SP2 |
||
|
Up to 8 restore sessions concurrent with backups |
Windows 7 |
Windows Server 2003 R2 |
Additional References
Volume Shadow Copy Service in Windows Developer Center
Утилита Shadow
Как подключиться к сессии пользователя (просмотреть экран в режиме «Теневой копии») на Windows Server 2008?
Чтобы наблюдать за другим сеансом необходимо использовать встроенную утилиту Shadow.
Например:
Имеется VDS сервер с ОС Windows Server 2008 Standart.
На нём созданы два пользователя Администратор и User.
Допустим имя нашей учётной записи администратор и мы хотим посмотреть экран сеанса пользователя user.
Чтобы узнать ID сеанса, введите команду query user в командной строке:
Итак, зная ID сеанса, подключимся к пользователю user в режиме «Теневой копии»:
Нажмите «Пуск» —→ «Выполнить» —→ «shadow 3» —→ «Ок»:
Далее увидите следующее сообщение:
В этот момент у пользователя user всплывет окно запроса удаленного управления:
У нас появится доступ, как только пользователь user примет запрос.
Параметры подключения
Чтобы подключаться без запроса, необходимо изменить параметры удалённого управления конкретного пользователя, в данном примере это user.
Перейдите по ветке: «Пуск» —→ «Администрирование» —→ «Управление компьютером» —→ «Локальные пользователи и группы» —→ «Пользователи».
Кликните дважды по имени пользователя и выберите вкладку «Удалённое управление»:
В параметре «Запрашивать разрешение пользователя» снимите галочку и выберите желаемый уровень управления сеансом пользователя.
Нажмите «Применить» —→ «Ок»

Научиться настраивать MikroTik с нуля или систематизировать уже имеющиеся знания можно на углубленном курсе по администрированию MikroTik. Автор курса, сертифицированный тренер MikroTik Дмитрий Скоромнов, лично проверяет лабораторные работы и контролирует прогресс каждого своего студента. В три раза больше информации, чем в вендорской программе MTCNA, более 20 часов практики и доступ навсегда.
Теневое копирование — специальный механизм, позволяющий делать копии файлов соответствующее определенному моменту времени, даже если они открыты или заблокированы системой. Теневые копии позволяют просматривать содержимое общих папок по состоянию на тот или иной момент времени в прошлом.
Теневые копии могут быть использованы для восстановления случайно удаленных и случайно перезаписанных файлов, а также позволяет сравнить несколько версий одного файла. Следует помнить, что теневые копии не могут служить заменой резервному копированию в силу ряда ограничений и особенностей о которых мы поговорим ниже.
Теневое копирование поддерживают серверные ОС начиная с Windows Server 2003, клиентское ПО для работы с теневыми копиями доступно начиная с Windows XP SP2.
При использовании теневых копий следует учитывать следующие ограничения:
- При превышении лимита выделенного дискового пространства старые теневые копии будут удалены без возможности восстановления.
- На одном томе может быть не более 64 теневых копий для каждого файла.
- Теневое копирование включается на уровне тома, т.е. нельзя выбрать общие папки и файлы для которых будет или не будет выполнятся теневое копирование.
- На компьютерах с двумя ОС при загрузке более старой системы или при подключении тома к другому ПК теневые копии могут быть повреждены.
Перед тем, как настраивать теневое копирование, следует продумать расписание. Для этого нужно проанализировать активность пользователей и критичность данных, найдя компромисс между частотой создания теневых копий и промежутком времени который должно охватывать теневое копирование. При этом следует отталкиваться от того, потерю какого промежутка рабочего времени можно считать допустимым, после чего рассчитать за какой промежуток времени будет достигнут предел, составляющий 64 копии. Не рекомендуется делать теневые копии чаще чем раз в час. Также продумайте расписание таким образом, чтобы копии делались только в рабочее время.
Для включения теневых копий перейдите в оснастку Управление компьютером в меню Администрирование.
В левой части окна найдите пункт Общие папки и, щелкнув правой кнопкой мыши, выберите Все задачи — Настроить теневые копии.
В открывшемся окне выберите том, на котором вы будете включать теневое копирование для общих папок и нажмите Включить, первая теневая копия будет создана немедленно.
Затем нажмите на кнопку Параметры и укажите размер дискового пространства, выделяемый для хранения теневых копий.
Следующим шагом задайте расписание.
Теперь самое время проверить работу теневых копий в действии. В обучающих целях мы установили небольшой промежуток между созданием теневых копий и провели несколько типовых действий с файлами в общей папке.
Самая распространенная и труднорешаемая проблема — файл перезаписали.
Открываем свойства файла, переходим на закладку Предыдущие версии и выбираем одну из доступных теневых копий (в нашем случае только одна).
Мы можем открыть, восстановить или скопировать файл. Для начала просто откроем.
Убедившись, что перед нами необходимая версия файла, мы можем ее восстановить или скопировать, если нам нужны оба варианта файлов.
Для восстановления удаленных файлов откройте свойства папки и выберите одну из ее теневых копий, затем вы можете просмотреть содержащиеся в ней файлы и восстановить нужные. Помните, что из теневой копии файлы можно открыть только на чтение.
Как видим, теневое копирование дает пользователям и администратору богатые возможности по работе предыдущими версиями файлов и папок. Данная технология, в сочетании с правильно настроенным резервным копированием, позволяет обеспечить высокую доступность данных и свести риск их потери к разумному минимуму.
Научиться настраивать MikroTik с нуля или систематизировать уже имеющиеся знания можно на углубленном курсе по администрированию MikroTik. Автор курса, сертифицированный тренер MikroTik Дмитрий Скоромнов, лично проверяет лабораторные работы и контролирует прогресс каждого своего студента. В три раза больше информации, чем в вендорской программе MTCNA, более 20 часов практики и доступ навсегда.
- Home
- Microsoft
- Setup Shadow Copies On Server 2008 Guide
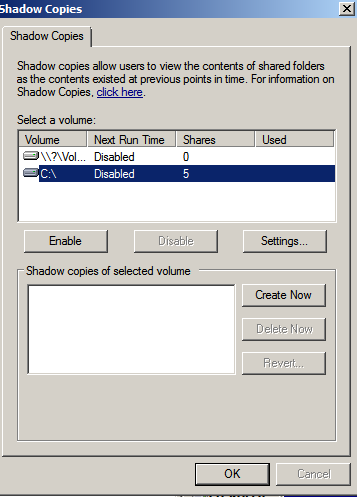
Written by Allen White on May 22, 2012. Posted in Microsoft, Server 2008
How To Enable Shadow Copies On A Drive
If you want to enable shadow copies on a drive which has shares then go through the following steps. This s a useful feature if you would like your users to be able to go back to previous versions of files, for either restores or comparisons.There is a step by step video guide to setting up shadow copies at the end of the article.
1. Start Computer Management by right clicking computer and selecting manage.
2. On the left hand side,, browse to Storage then select Disk Management. Information on your drives will be showin tin the centre details section.
setup volume shadow copies guide
3. Right-click Disk Management > All Tasks >Configure Shadow Copies.
4. Then select the volume to would like to enable shadow copies on.
enable shadow copies
5. Click Settings to setup how much space you would like shadow copies to use. The more space the better as it means you will be able to keep more data and for longer. You can also setup the schedule here as to when you would like to take your copies. I would recommend daily out of work hours so users can restore a previous days work.
set shadow copies schedule
6. Finally select enable and accept the warning.
Restore Shadow Copies Back To A Drive Or Share
Now presuming you have been running shadow copies for a day or so, you should have some previous version available for restore. To pull back a previous version of a file then do the following from a clients pc.
1.Instruct the user to go to the share where they would like to restore the previous file versions, then choose Properties > Previous Versions.
restore a shadow copy file or folder
2. If you have been running shadow copies for a while , you will see various version with different dates. Select the version you would like to work with.
3. Then click teither open, save or restore. Open will show you the file there and then to view, copy will allow you to copy the file to a desired area and restore will overwrite the current file with the version you have chosen.
Tags: VSS
Allen White
Allen is an IT Consultant and holds the following accreditations. MCSA, MCSE, MCTS, MCITP, CCA, CCSP, VCP 4,5, 6 and HP ASE, AIS — Network Infrastructure.
Search
- Remove From My Forums

Управление теневыми копиями в отказоустойчивом кластере.
-
Вопрос
-
Заходим в «диспетчер отказоустойчивости кластеров» — «хранилище», выбираем том, заходим в его свойства, выбираем закладку теневые копии. В этой закладке можно включить-отключить копирование и настроить
расписание. А где настройка размера и места хранения? Вопрос именно о теневом копировании средствами отказоустойчивого кластера. Где и как это настраивается локально на отдельно взятом сервере, мне известно.Буду рад любой информациии по этой теме, т.к. в интернетах ничего не нашлось.
Ответы
-
В итоге: из оснастки кластера включаем задачу теневого копирования и настраиваем расписание, а перед этим из командной строки настраиваем хранилище для теневых копий и его размер (c помощью vssadmin).
Всем участвовавшим спасибо и отдельное спасибо someparty — за направление мыслей в правильное русло.
-
Помечено в качестве ответа
16 сентября 2014 г. 11:42
-
Помечено в качестве ответа

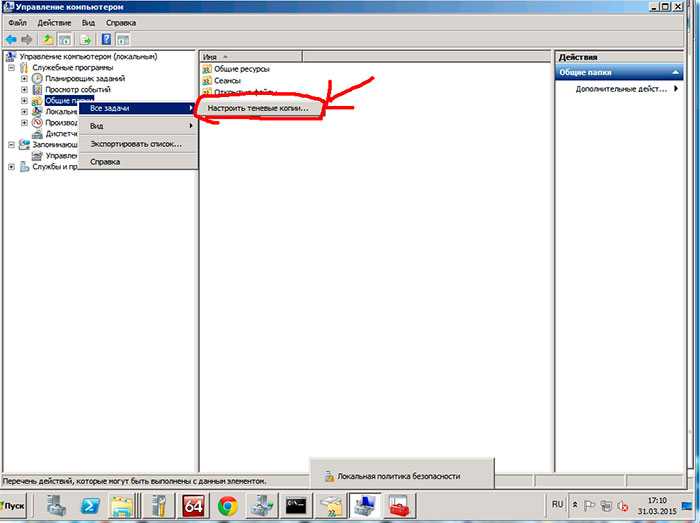

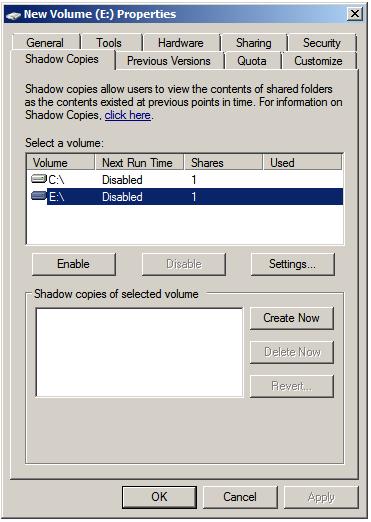
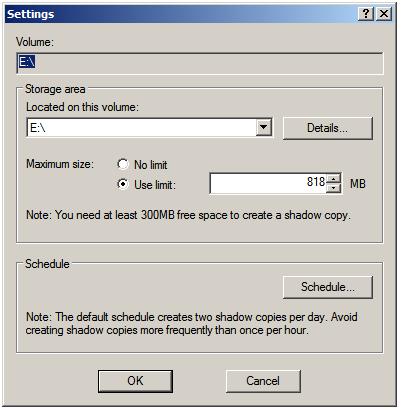
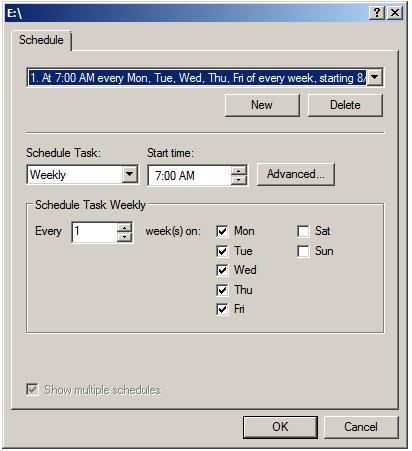
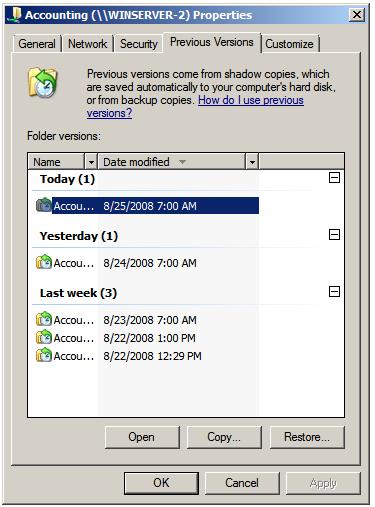
.jpg)
.jpg)
.jpg)